| download: | /ca.ps1 |
| Full analysis: | https://app.any.run/tasks/b62de84b-fa82-4c85-a46e-4168026669ad |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | May 19, 2025, 14:40:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-wine-extension-ini |
| File info: | Generic INItialization configuration [switch] |
| MD5: | 87835731775C39F0C5020115622AB52E |
| SHA1: | 9F0D2CA507F3B5FE1F16F83CB310F7A73A14BFC4 |
| SHA256: | E5074BB842A84350606896D0A95DE5E6941AAD69D66BD5D0F4B310E9386829BE |
| SSDEEP: | 1536:DhykjVVZ/frfdF4cq8AXY+nVGqNJob3yXhrulc+1ZV0GBzr9R6Llw74uhvNubnh5:DhykjVTpuf4YrulnVL9sUJvqnaTsp |
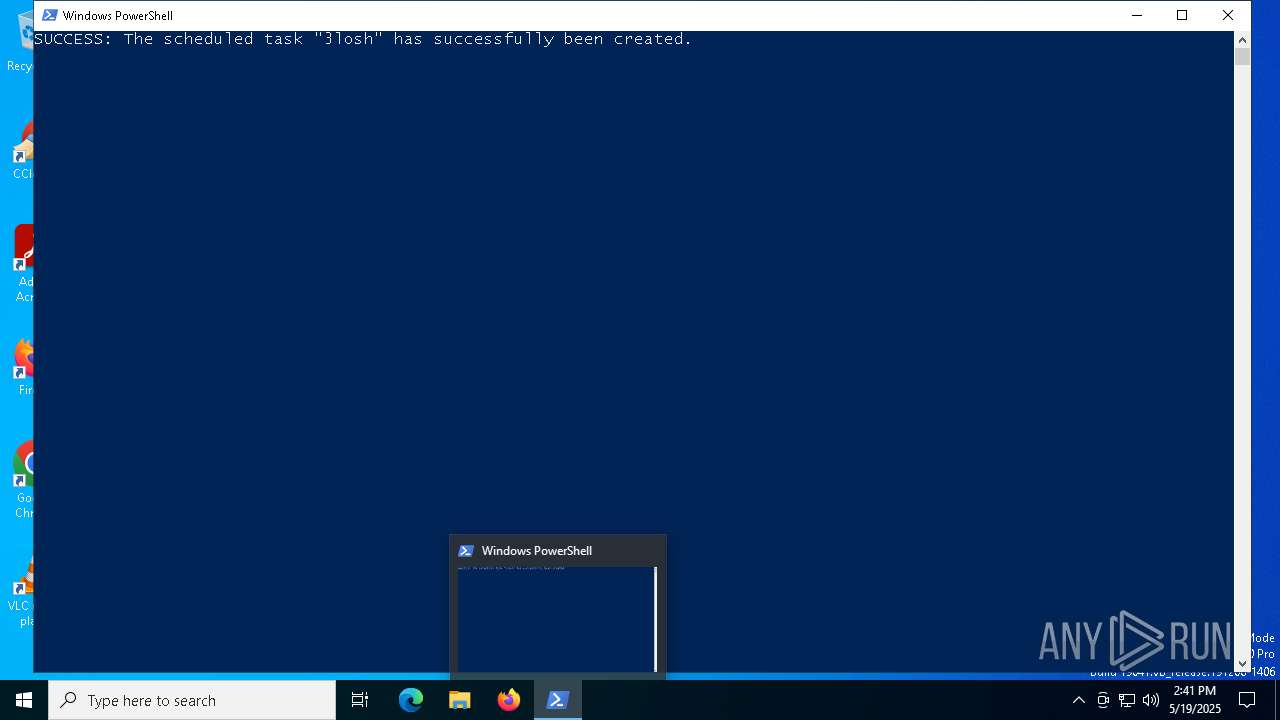
MALICIOUS
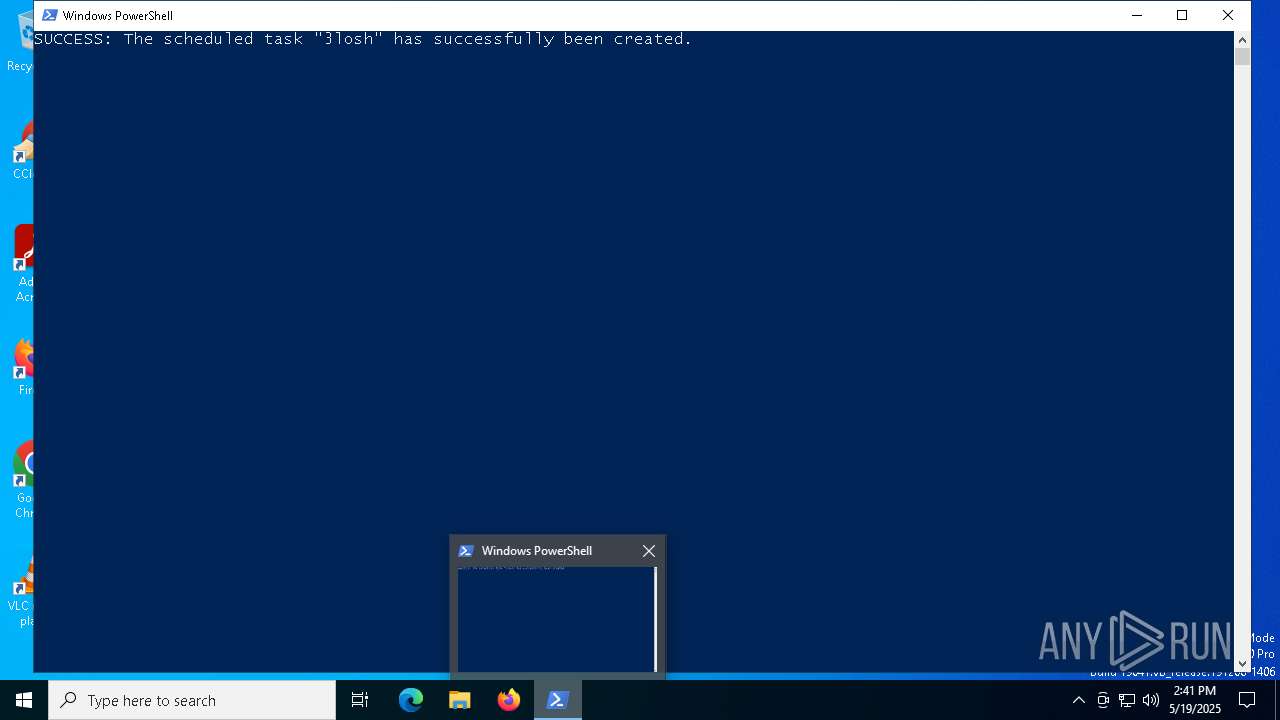
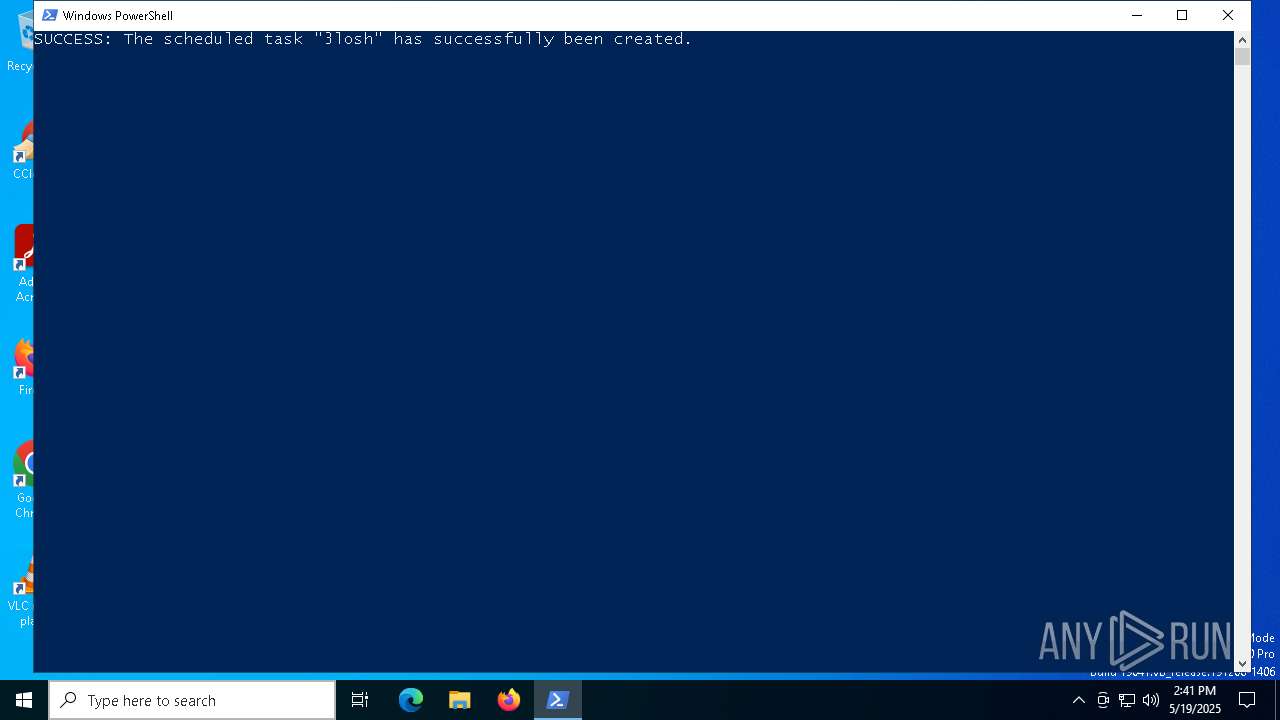
Uses Task Scheduler to run other applications
- powershell.exe (PID: 4008)
Bypass execution policy to execute commands
- powershell.exe (PID: 4008)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 4008)
XWORM has been detected (YARA)
- powershell.exe (PID: 4008)
SUSPICIOUS
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 4008)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 6192)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 4008)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4008)
Multiple wallet extension IDs have been found
- powershell.exe (PID: 4008)
Connects to unusual port
- powershell.exe (PID: 4008)
INFO
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4008)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4008)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4008)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4008)
Found Base64 encoded reference to WMI classes (YARA)
- powershell.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(4008) powershell.exe
C2mcmaster.giize.com:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
Mutex1mWeNxmu7vBuO255
Total processes
131
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\AppData\Local\Temp\ca.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
XWorm(PID) Process(4008) powershell.exe C2mcmaster.giize.com:7000 Keys AES<123456789> Options Splitter<Xwormmm> Sleep time3 USB drop nameXWorm V5.6 Mutex1mWeNxmu7vBuO255 | |||||||||||||||
| 5244 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | "C:\WINDOWS\system32\schtasks.exe" /create /tn 3losh /tr C:\Users\Public\c.vbs /sc once /st 14:45 /f | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6808 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 176
Read events
5 176
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4008 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10d033.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 4008 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\BFU207OT2SC16DX0TTNV.temp | binary | |
MD5:63E838E3BA81CDDF7B1274D31004D2D0 | SHA256:404B23F51E1D582C6C52B1886446E420E907ED7BD0EB6395C0E56216595C262F | |||
| 4008 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:63E838E3BA81CDDF7B1274D31004D2D0 | SHA256:404B23F51E1D582C6C52B1886446E420E907ED7BD0EB6395C0E56216595C262F | |||
| 4008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mhjqhzkd.kti.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z2sncnrn.1cg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4008 | powershell.exe | C:\Users\Public\q.ps1 | binary | |
MD5:87835731775C39F0C5020115622AB52E | SHA256:E5074BB842A84350606896D0A95DE5E6941AAD69D66BD5D0F4B310E9386829BE | |||
| 4008 | powershell.exe | C:\Users\Public\c.vbs | text | |
MD5:77279251C4B5CE463BD582D94C8B03D0 | SHA256:436E1CE76D3C329C36317DAD05A4298BCC31797BB31FD0CCCB640DACCA9A42C9 | |||
| 4008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Log.tmp | text | |
MD5:DCF9FA81F4D9A8F36353DE22B0D210E2 | SHA256:221F85C0E4B669579E93FE00904CAED223A7BB3B0C386DD5010FE5E1B51A6FB9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
45
DNS requests
14
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.29:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4008 | powershell.exe | 41.216.188.194:7000 | mcmaster.giize.com | Private-Hosting di Cipriano oscar | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
mcmaster.giize.com |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET DYN_DNS DNS Query to a *giize.com DYNAMIC_DNS Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Dynamic DNS Service (giize .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.giize .com Domain |