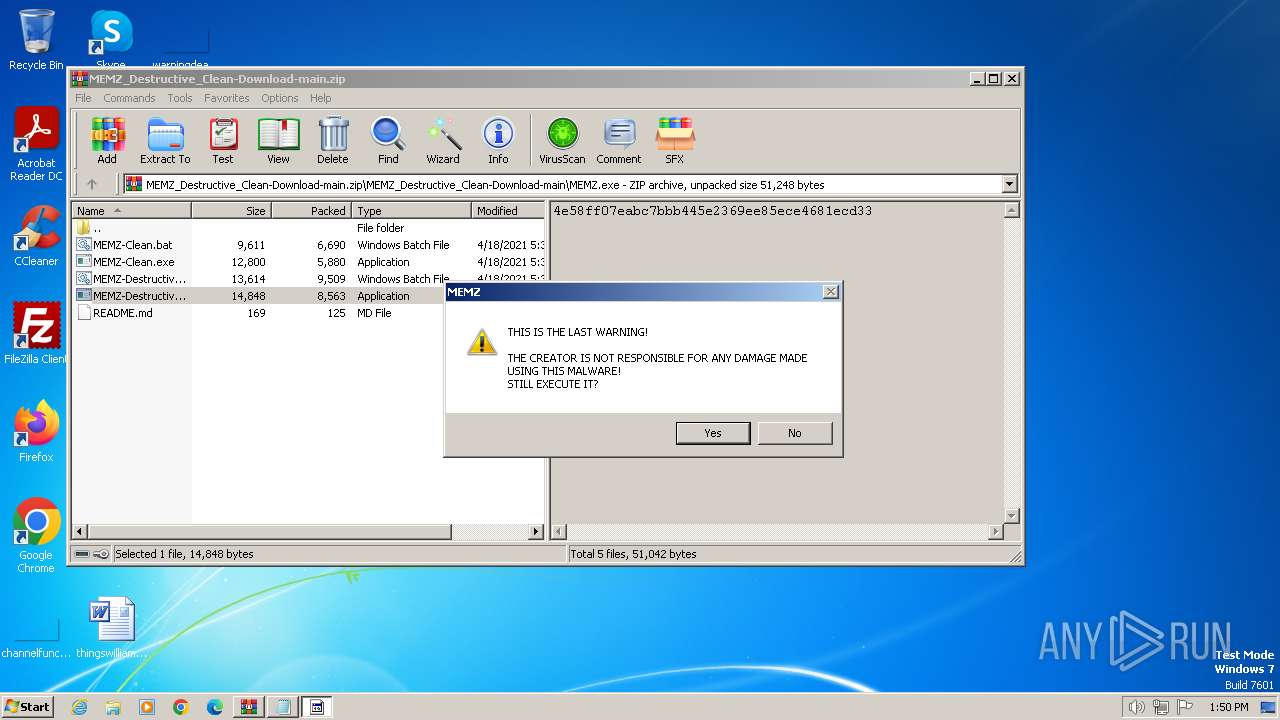
| File name: | MEMZ_Destructive_Clean-Download-main.zip |
| Full analysis: | https://app.any.run/tasks/9f02fd83-c35e-4517-a81a-b0e75f4a5383 |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2024, 13:49:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2B1F6A82C3F66401EF15250A934C18F0 |
| SHA1: | EF99308431D074E051E3936B4C4FD73497763493 |
| SHA256: | E4EA523EE22121A4A26160B2042907C9D008ABFCDED1671A86FA23E7872DA745 |
| SSDEEP: | 768:uKYtpP6T6s2Onw3pcoN1gILXVJ3+0qohnFXoXEKyuZSA+:PB52XLlHqohnIENA+ |
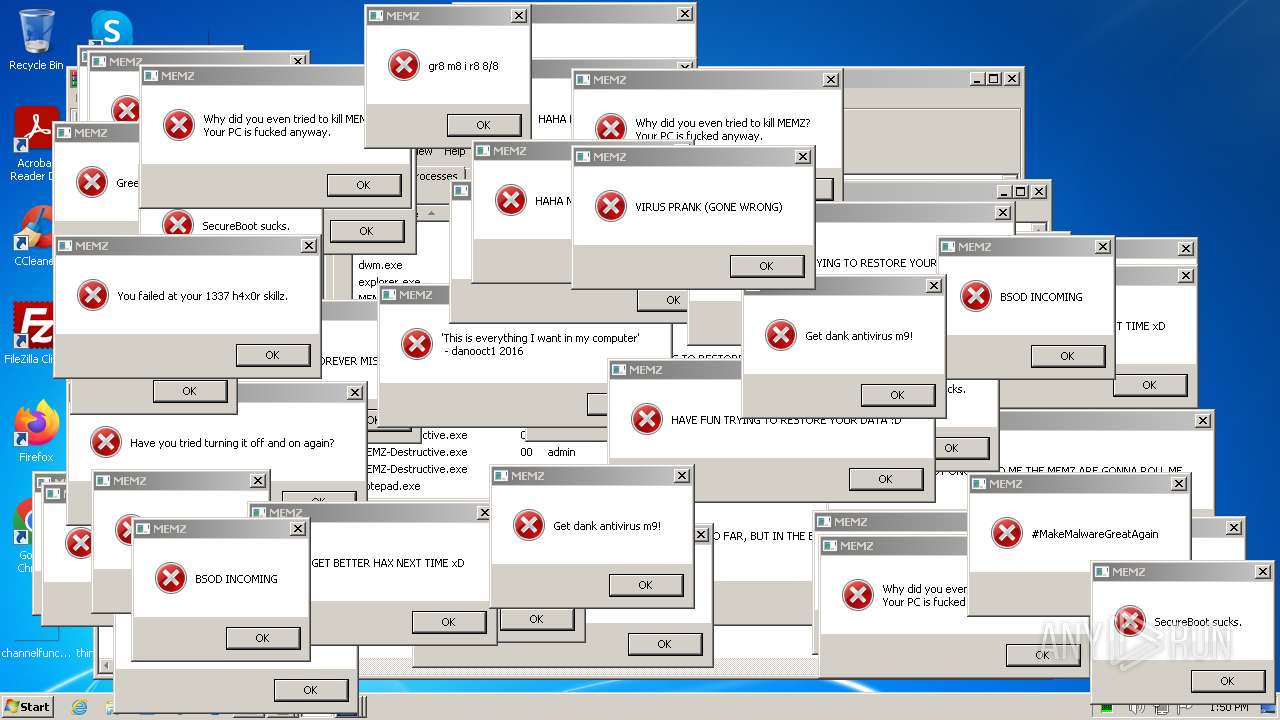
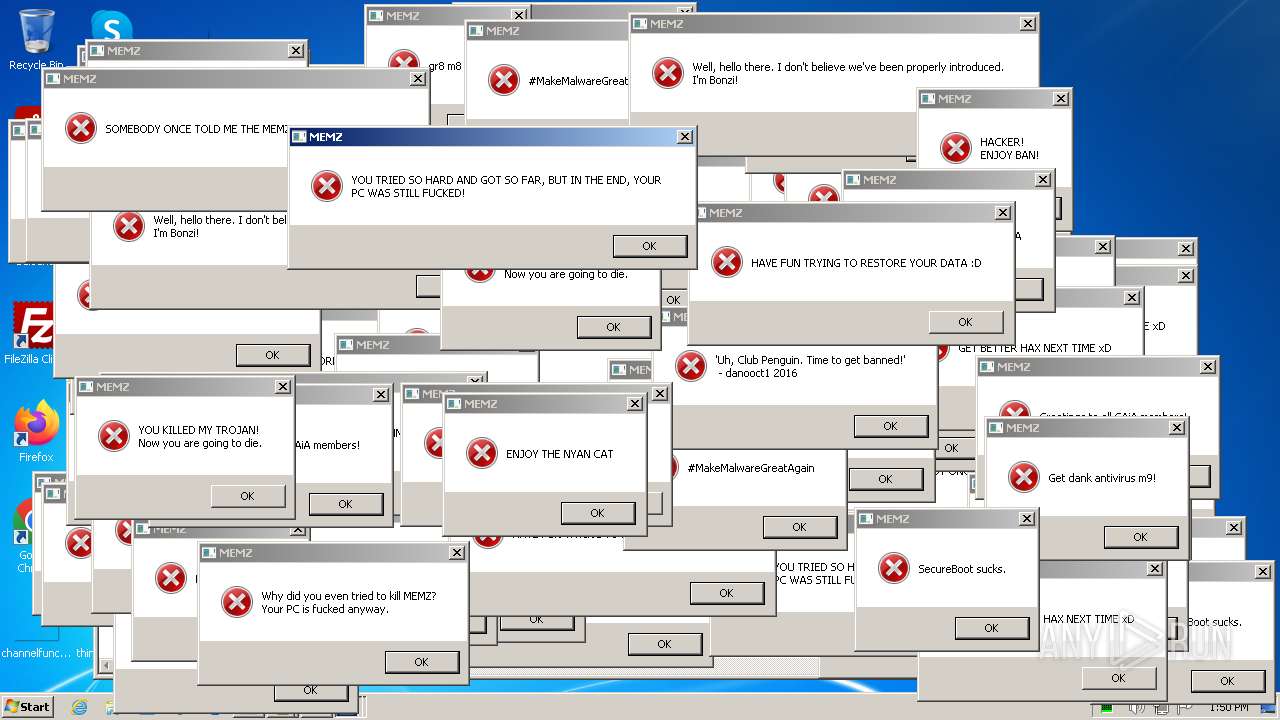
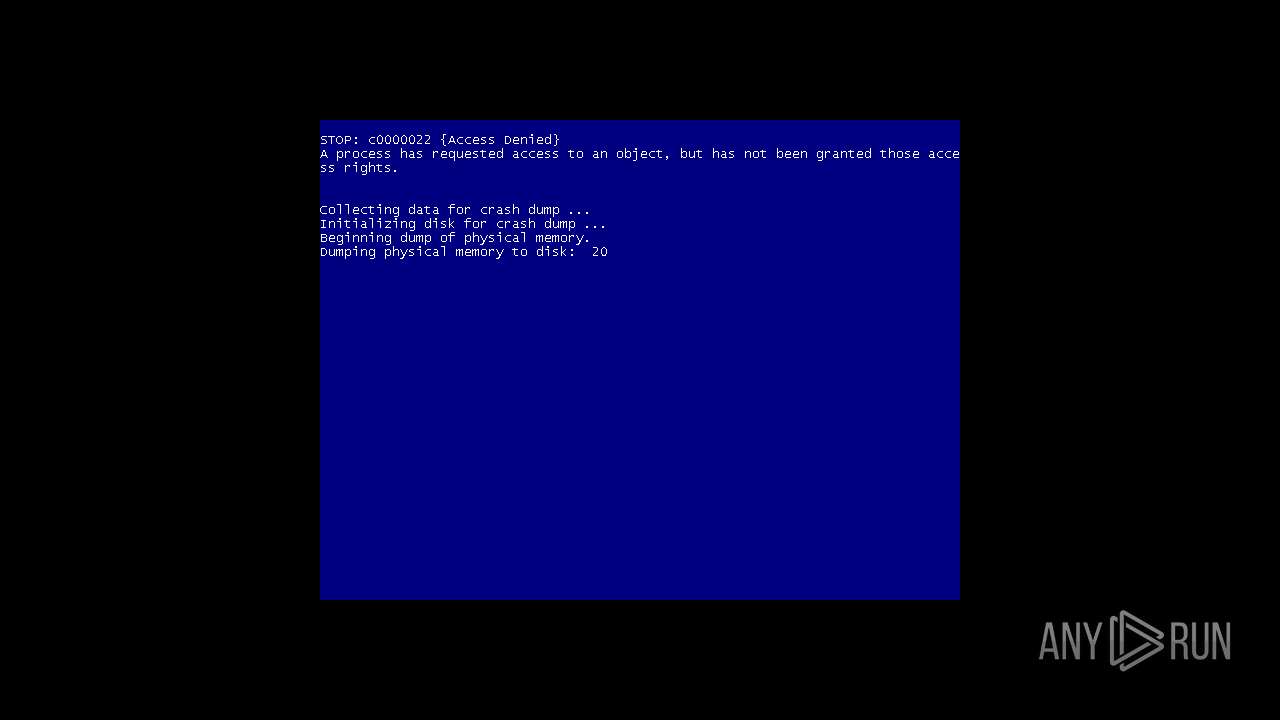
MALICIOUS
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 3892)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 3892)
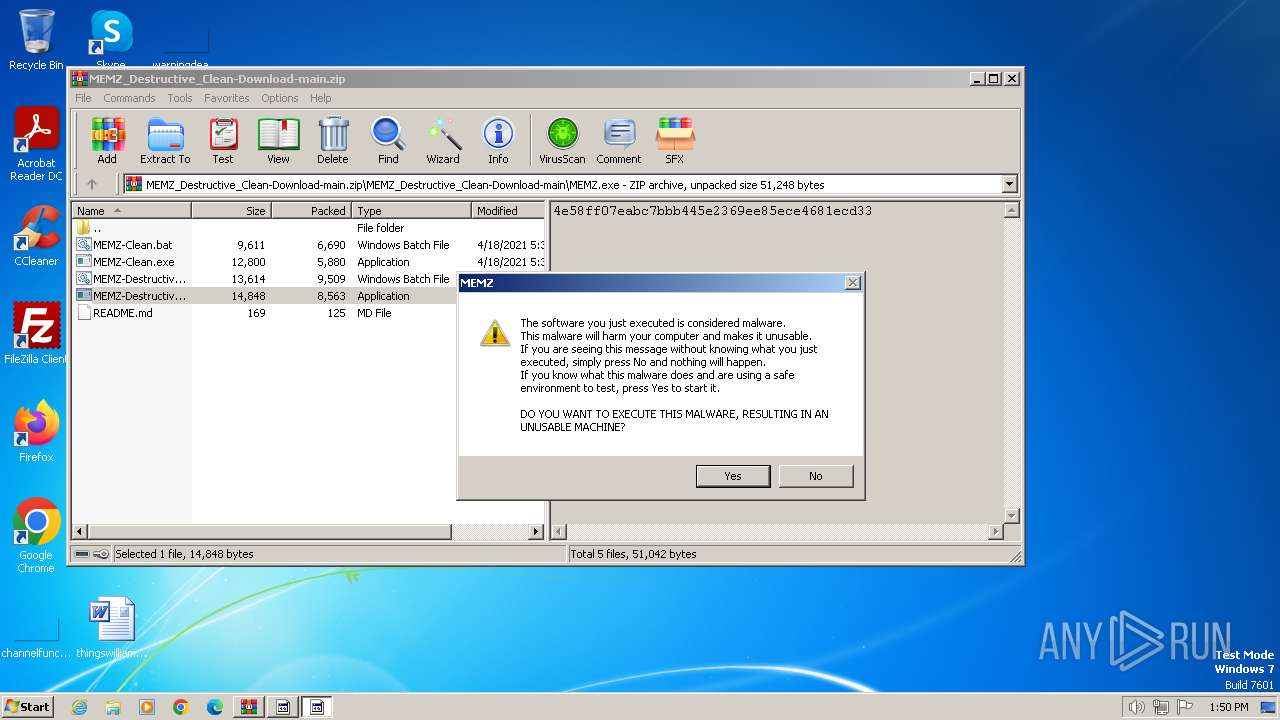
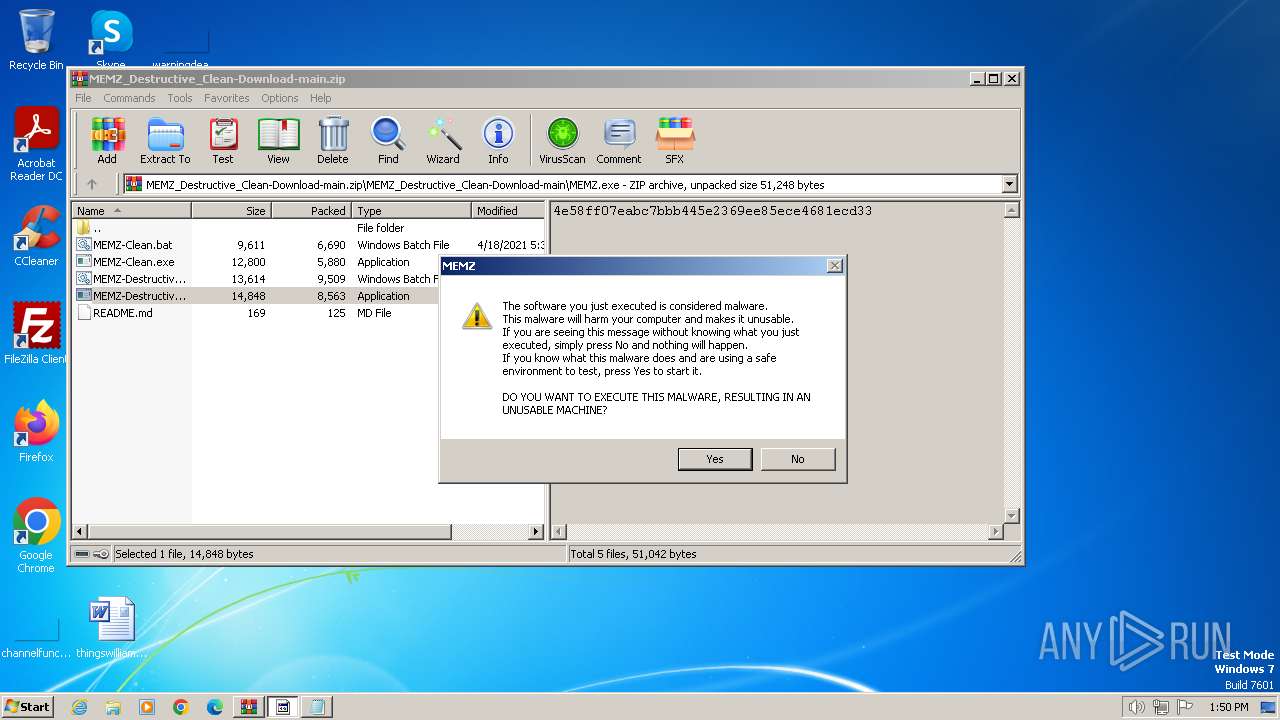
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3668)
SUSPICIOUS
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3668)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 3892)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3668)
- MEMZ-Destructive.exe (PID: 3996)
- MEMZ-Destructive.exe (PID: 3164)
- MEMZ.exe (PID: 2648)
- MEMZ.exe (PID: 3308)
The process executes JS scripts
- cmd.exe (PID: 3692)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3892)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3668)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 3892)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 3892)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 3892)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 3892)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 3892)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 3892)
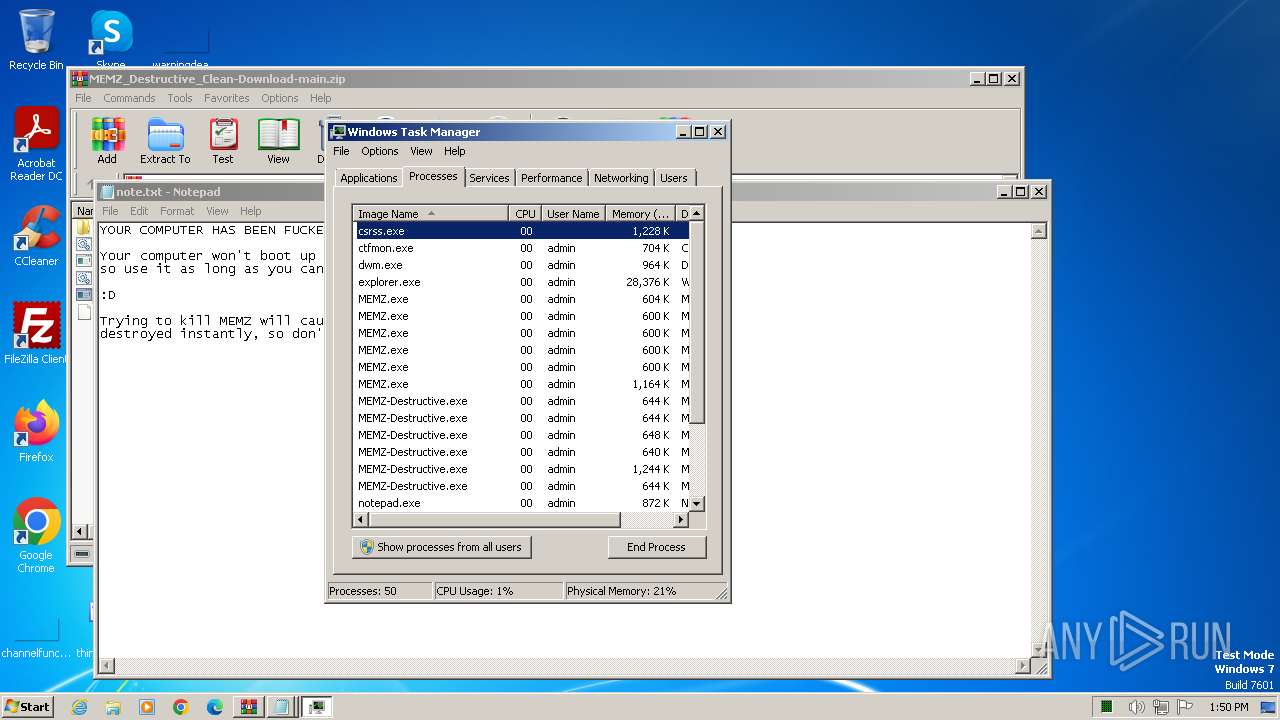
The executable file from the user directory is run by the CMD process
- MEMZ.exe (PID: 3460)
- MEMZ.exe (PID: 3228)
- MEMZ.exe (PID: 2648)
Executable content was dropped or overwritten
- cscript.exe (PID: 3892)
Reads the Internet Settings
- cmd.exe (PID: 3692)
- MEMZ-Destructive.exe (PID: 3996)
- cscript.exe (PID: 3892)
- MEMZ-Destructive.exe (PID: 3164)
- MEMZ.exe (PID: 2648)
- MEMZ.exe (PID: 3308)
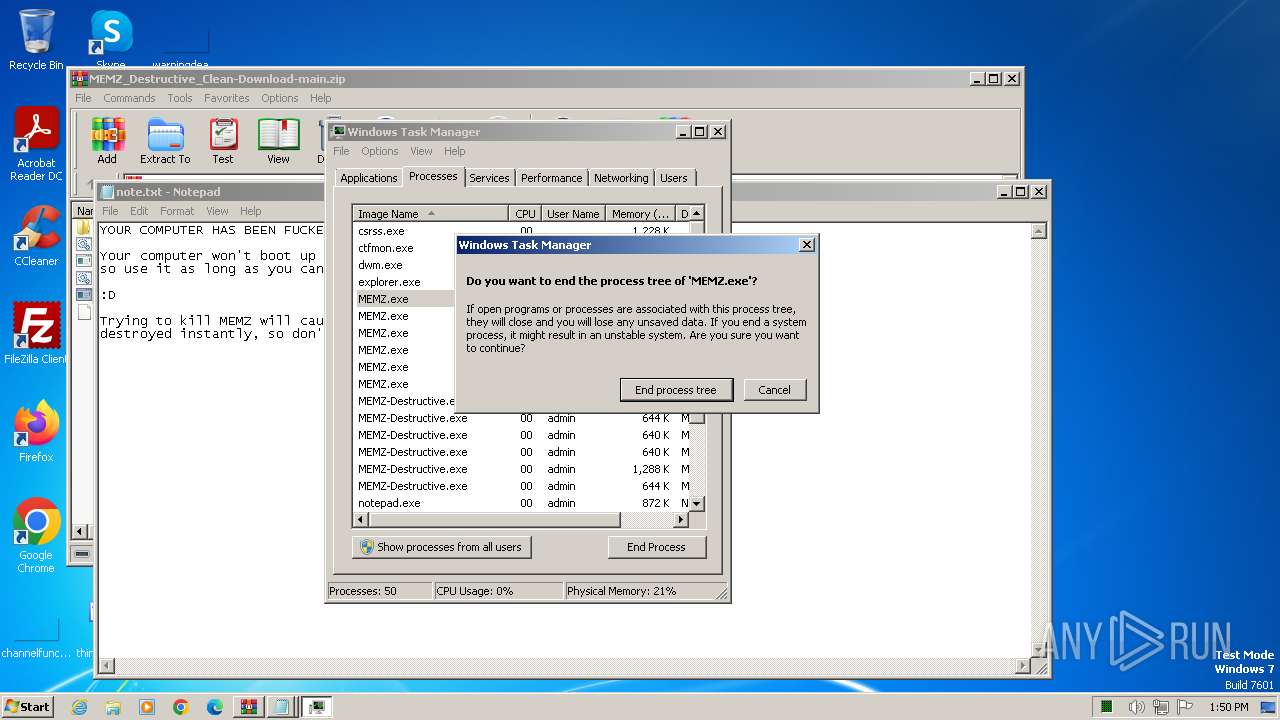
Application launched itself
- MEMZ-Destructive.exe (PID: 3996)
- MEMZ.exe (PID: 2648)
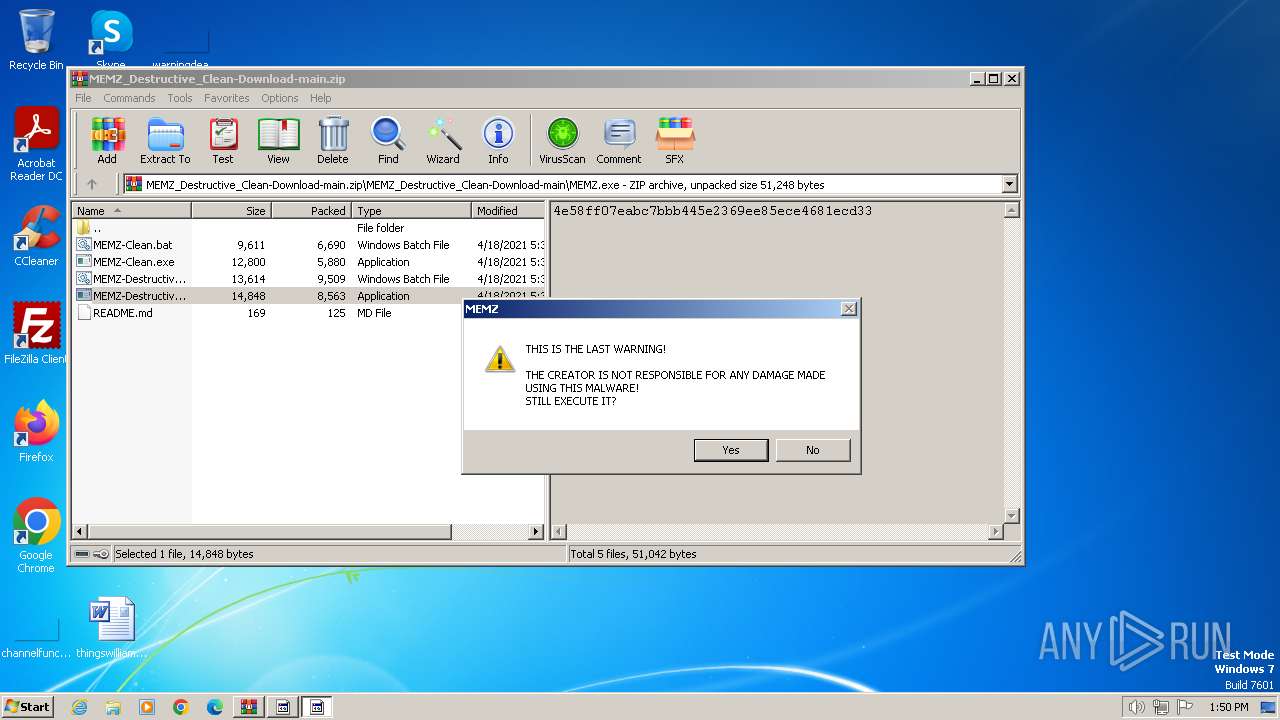
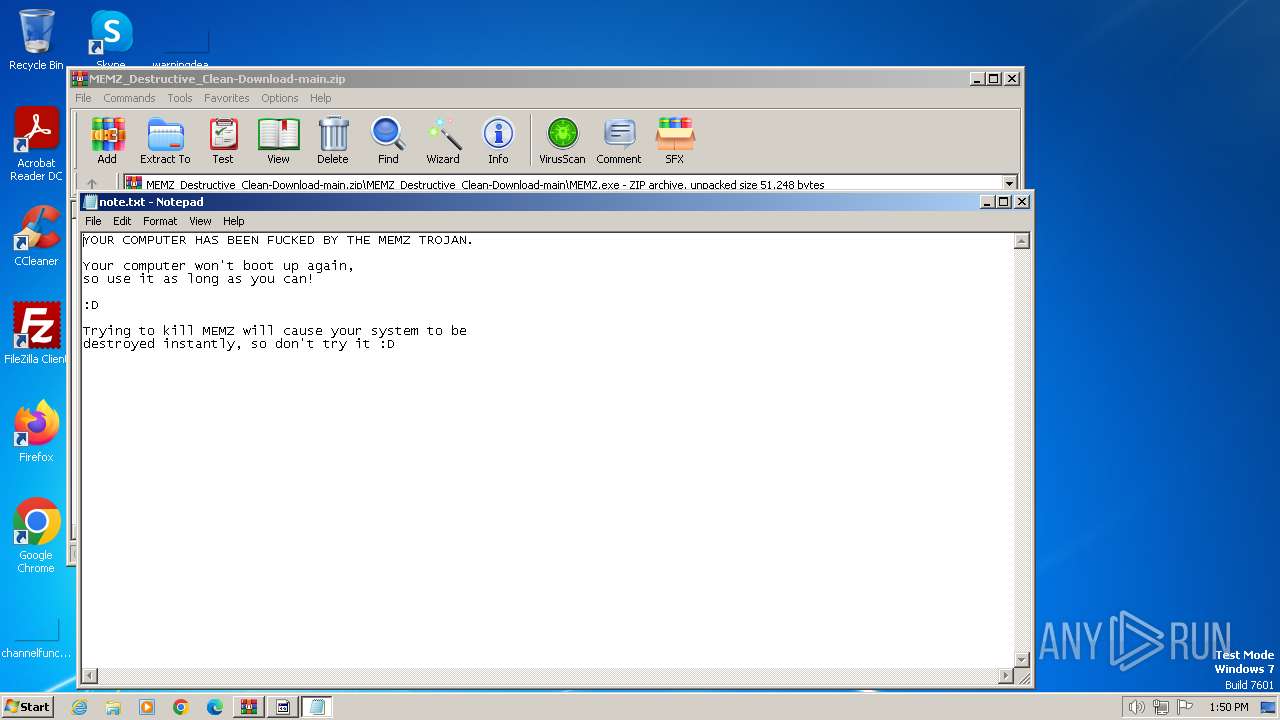
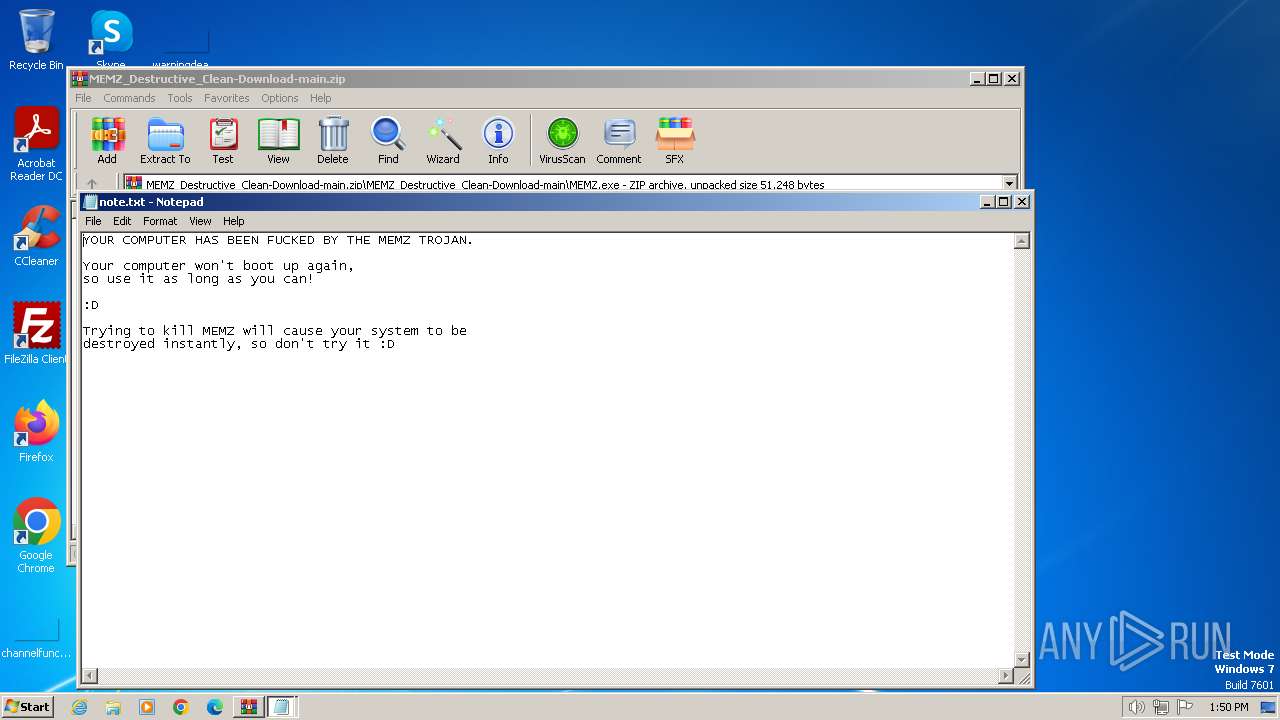
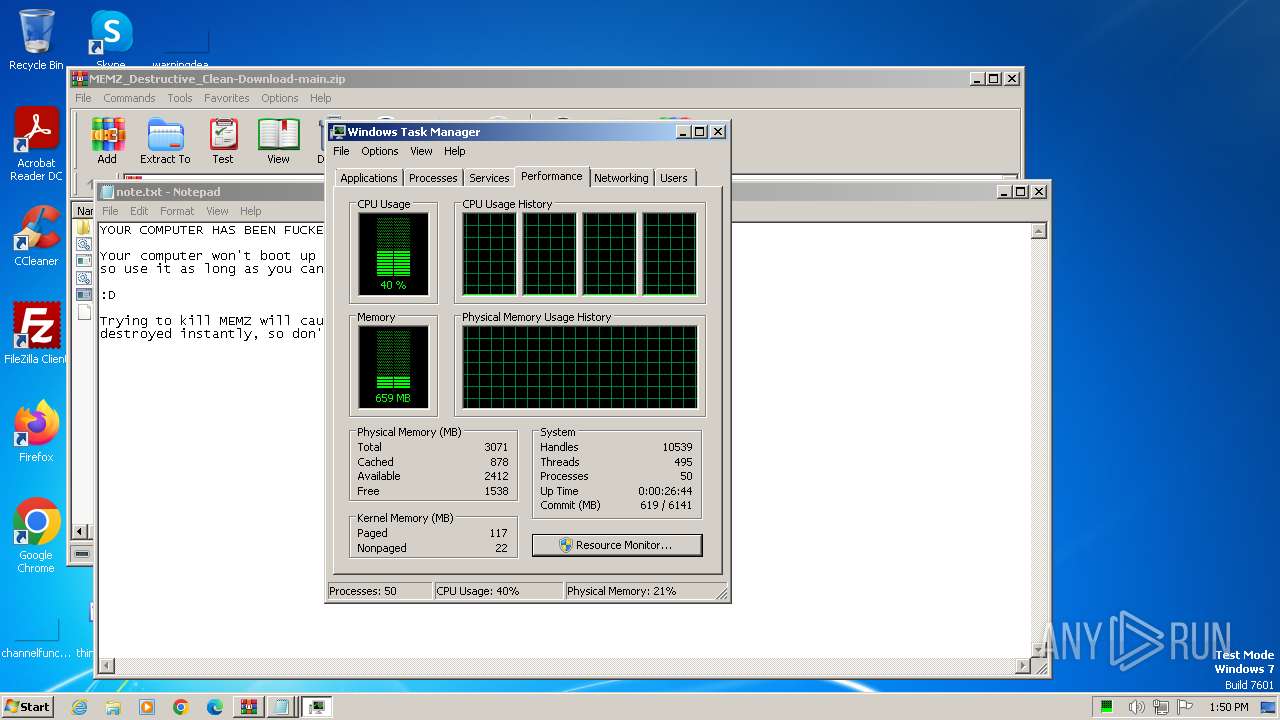
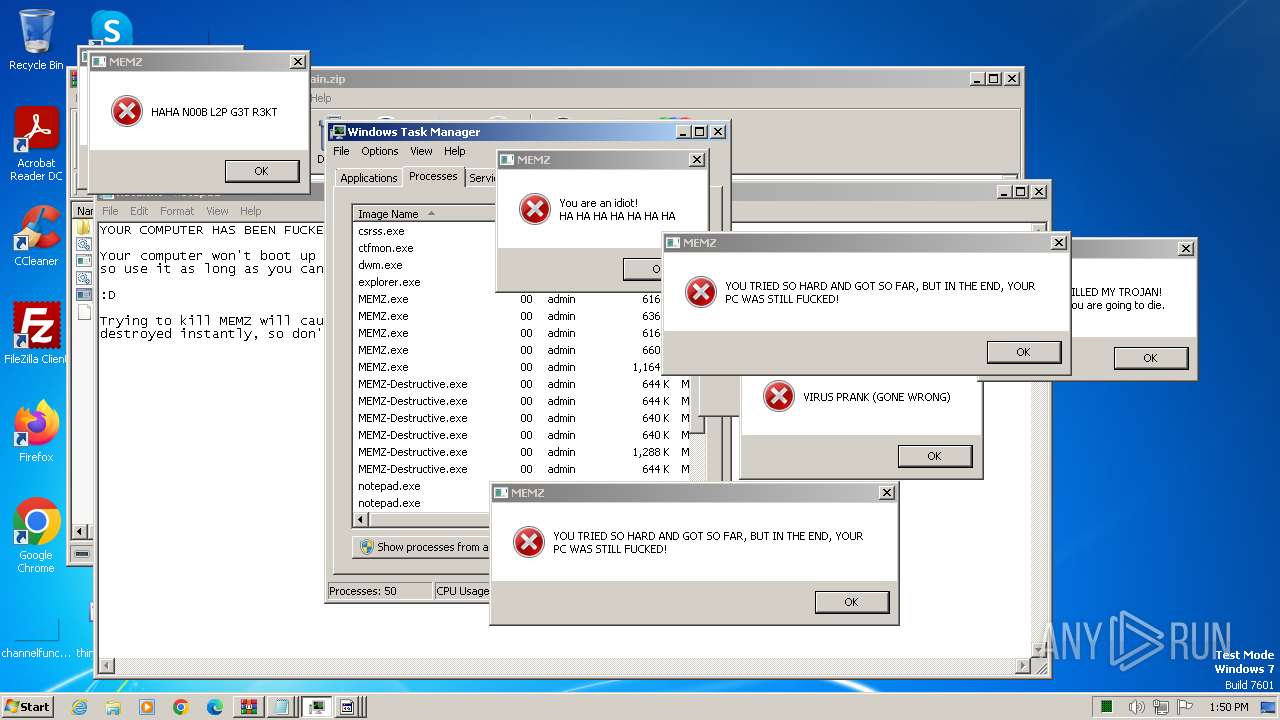
Start notepad (likely ransomware note)
- MEMZ-Destructive.exe (PID: 3164)
- MEMZ.exe (PID: 3308)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3536)
- MEMZ-Destructive.exe (PID: 3996)
- MEMZ-Destructive.exe (PID: 3164)
- MEMZ.exe (PID: 2648)
- MEMZ.exe (PID: 3308)
Checks supported languages
- wmpnscfg.exe (PID: 3536)
- MEMZ.exe (PID: 2648)
- MEMZ-Destructive.exe (PID: 3996)
- MEMZ-Destructive.exe (PID: 3180)
- MEMZ-Destructive.exe (PID: 2672)
- MEMZ-Destructive.exe (PID: 1496)
- MEMZ-Destructive.exe (PID: 2256)
- MEMZ-Destructive.exe (PID: 2908)
- MEMZ-Destructive.exe (PID: 3164)
- MEMZ.exe (PID: 1560)
- MEMZ.exe (PID: 1888)
- MEMZ.exe (PID: 2184)
- MEMZ.exe (PID: 240)
- MEMZ.exe (PID: 1992)
- MEMZ.exe (PID: 3308)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3892)
Manual execution by a user
- wmpnscfg.exe (PID: 3536)
- taskmgr.exe (PID: 1576)
Create files in a temporary directory
- cscript.exe (PID: 3892)
Drops the executable file immediately after the start
- cscript.exe (PID: 3892)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
Creates files or folders in the user directory
- cscript.exe (PID: 3892)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 1560)
- MEMZ.exe (PID: 1888)
- MEMZ.exe (PID: 1992)
- MEMZ.exe (PID: 2184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:04:17 21:30:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | MEMZ_Destructive_Clean-Download-main/ |
Total processes
64
Monitored processes
24
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1496 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1576 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1888 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1992 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
17 073
Read events
16 922
Write events
151
Delete events
0
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MEMZ_Destructive_Clean-Download-main.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3164 | MEMZ-Destructive.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 3308 | MEMZ.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 3892 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Clean.bat | text | |
MD5:BF12B1896241434CECFC09F9F23ECAEF | SHA256:6D81B7553BB5799CE01DD205E3CD6F11F6E5A98B4D52DF3115A04447588F101C | |||
| 3692 | cmd.exe | C:\Users\admin\AppData\Local\Temp\x | text | |
MD5:CFC1E7E18B9F9B70310C88F922E59B29 | SHA256:3DCF309E134AE67CAED27FA52782267C90646B405C4A9594041B284733B8E346 | |||
| 3892 | cscript.exe | C:\Users\admin\AppData\Local\Temp\z.zip | compressed | |
MD5:63EE4412B95D7AD64C54B4BA673470A7 | SHA256:44C1857B1C4894B3DFBACCBE04905652E634283DCF6B06C25A74B17021E2A268 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.bat | text | |
MD5:63C6EC6B042BCB00D2D832C0E4F25DCA | SHA256:DAE968F47476EF79B122E771CCD0A2BACDE2AC3535F68047239682FEFA3DFE50 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Clean.exe | executable | |
MD5:9C642C5B111EE85A6BCCFFC7AF896A51 | SHA256:4BBF7589615EBDB6C769D6D2E7BDCB26072BAC0CDA6E225A4133BA8819E688D5 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\README.md | text | |
MD5:A34AABCC20621D5069026FB2A2D65D73 | SHA256:0F7A7E5D7E7F301CF20EFF536302E2B02A5294A18A193BBEA3F963BB4C804F87 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3668.20294\MEMZ_Destructive_Clean-Download-main\MEMZ.exe\MEMZ-Destructive.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |