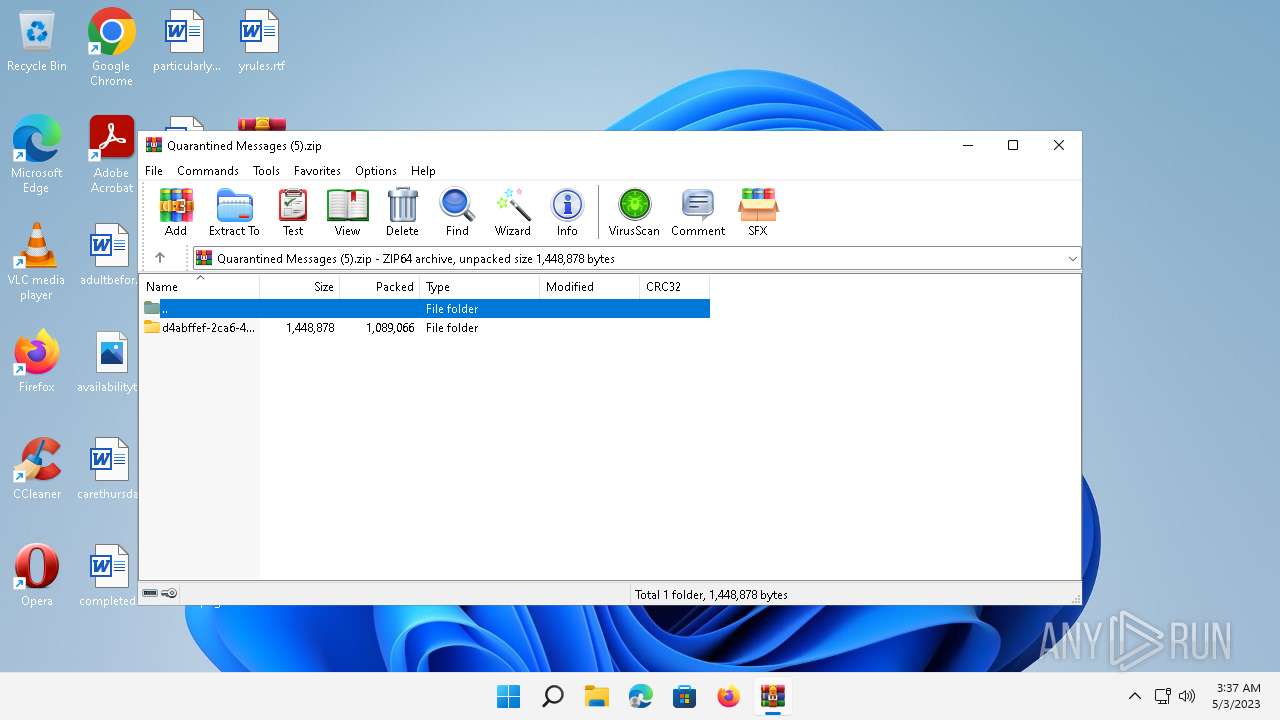
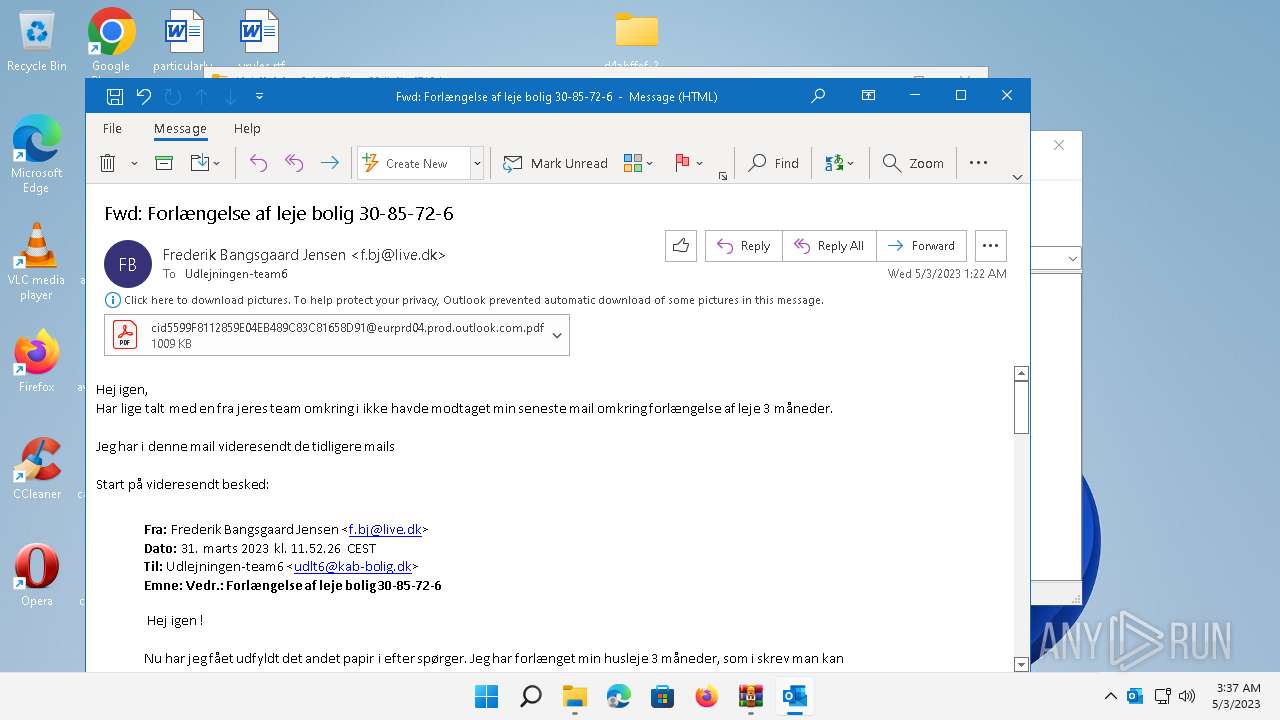
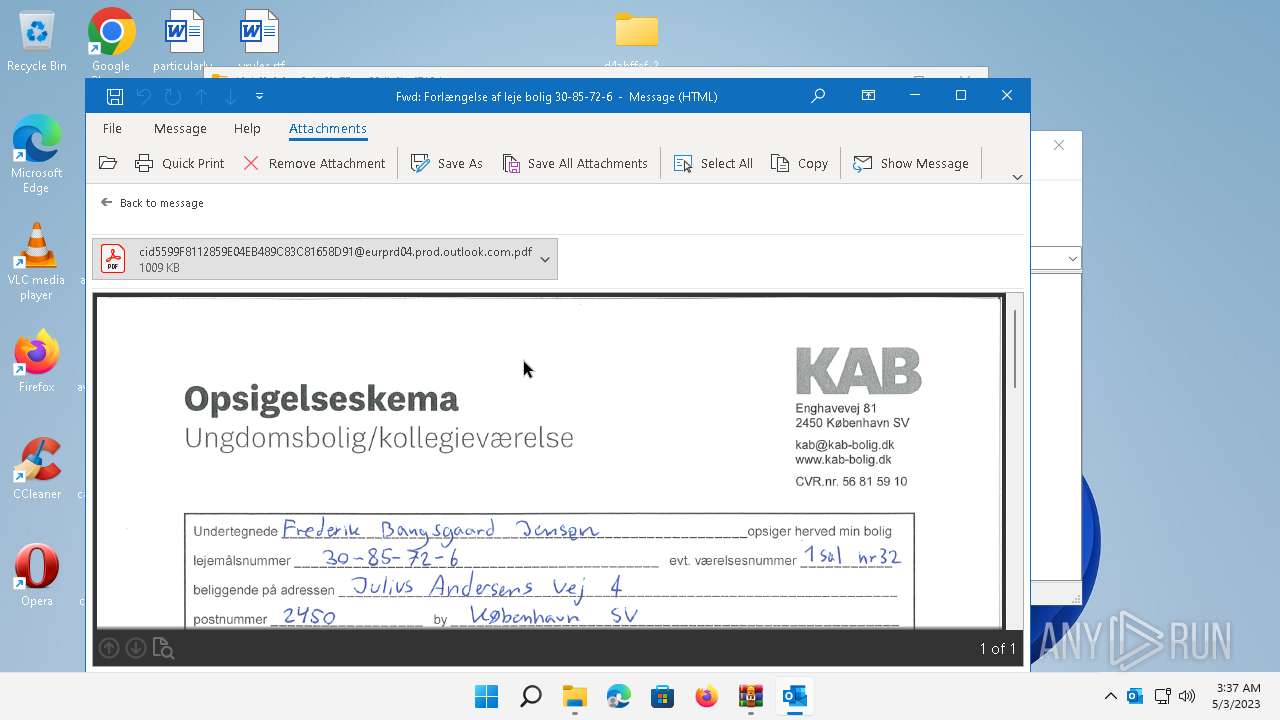
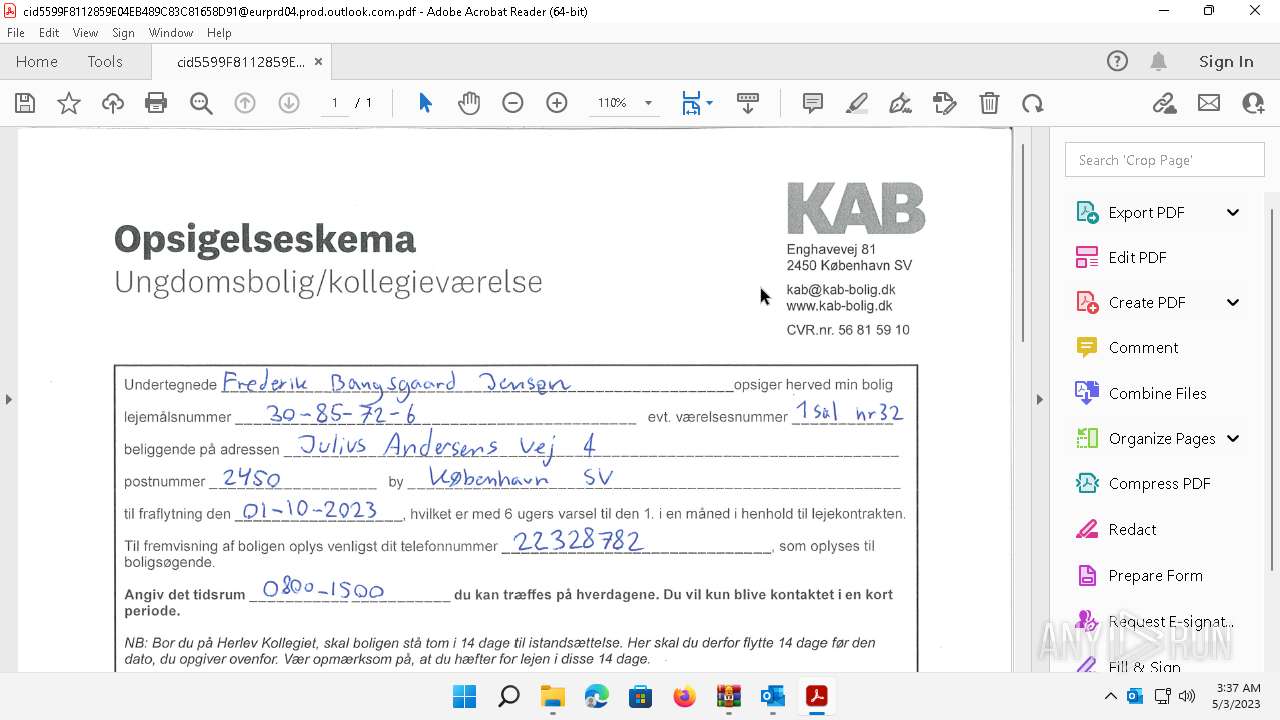
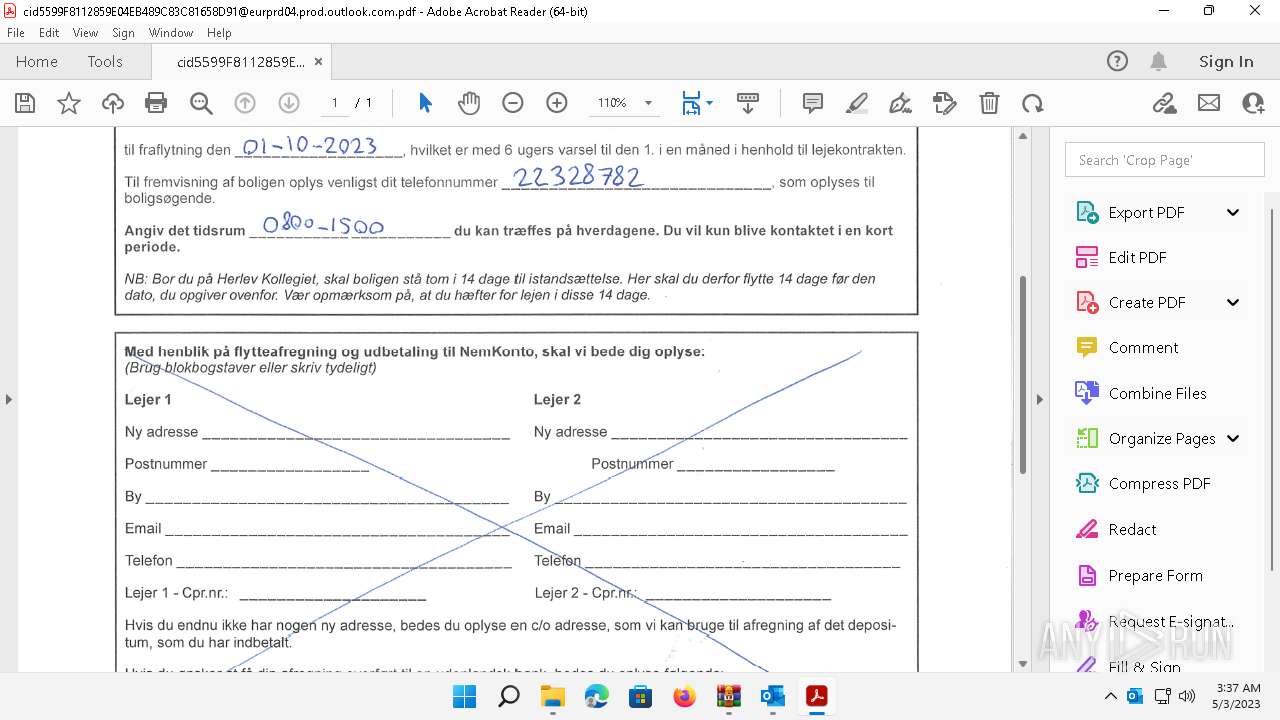
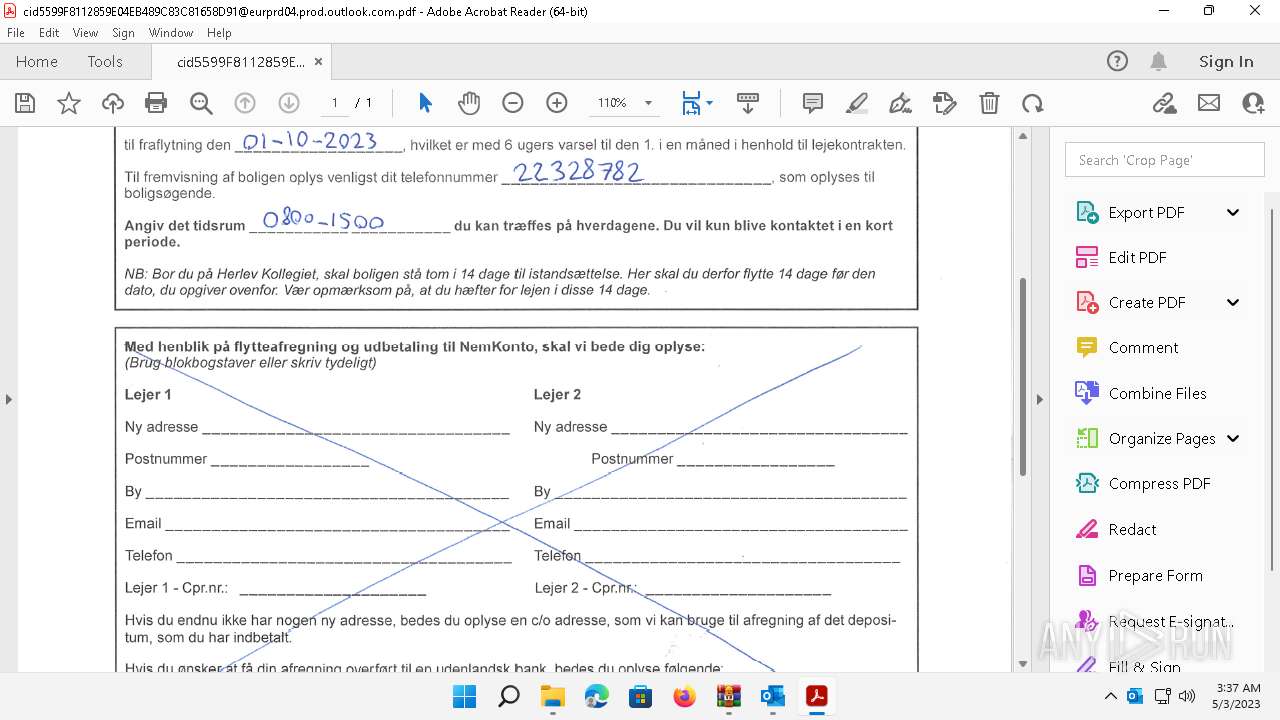
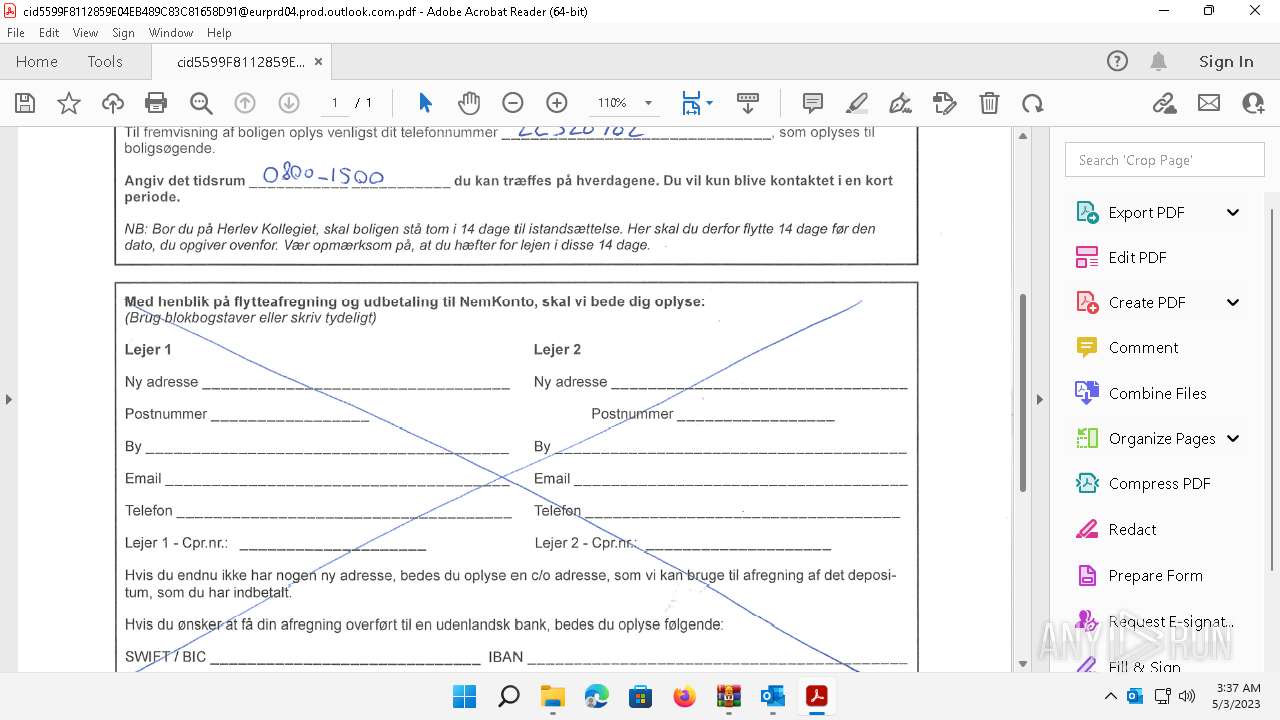
| File name: | Quarantined Messages (5).zip |
| Full analysis: | https://app.any.run/tasks/fa762817-4c87-4423-b179-5631c5a27487 |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2023, 10:36:50 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | E373AE46BAAC05887C0B3A8EC6BA7742 |
| SHA1: | 07848E2421FE55D0742842321A059949BFA88433 |
| SHA256: | E4DE5CC1FB1050071882673EE10D9897EFD7A353F97F39F44E167D9BB2B9CDD8 |
| SSDEEP: | 24576:5LxRMxi/+dTR0zwfNfU3UnpFylYFj2ebb6kTnNCyZL/:NxvrEU34FyCFLxjZL/ |
MALICIOUS
Unusual execution from MS Office
- OUTLOOK.EXE (PID: 4280)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- OpenWith.exe (PID: 6476)
Reads the Internet Settings
- OpenWith.exe (PID: 6476)
Reads Microsoft Outlook installation path
- OpenWith.exe (PID: 6476)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6476)
- Acrobat.exe (PID: 8056)
The process checks LSA protection
- OpenWith.exe (PID: 6476)
- prevhost.exe (PID: 5892)
Reads product name
- OUTLOOK.EXE (PID: 4280)
Application launched itself
- Acrobat.exe (PID: 7816)
- Acrobat.exe (PID: 6924)
- AcroCEF.exe (PID: 7692)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 4280)
Checks supported languages
- acrobat_sl.exe (PID: 8108)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 7804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
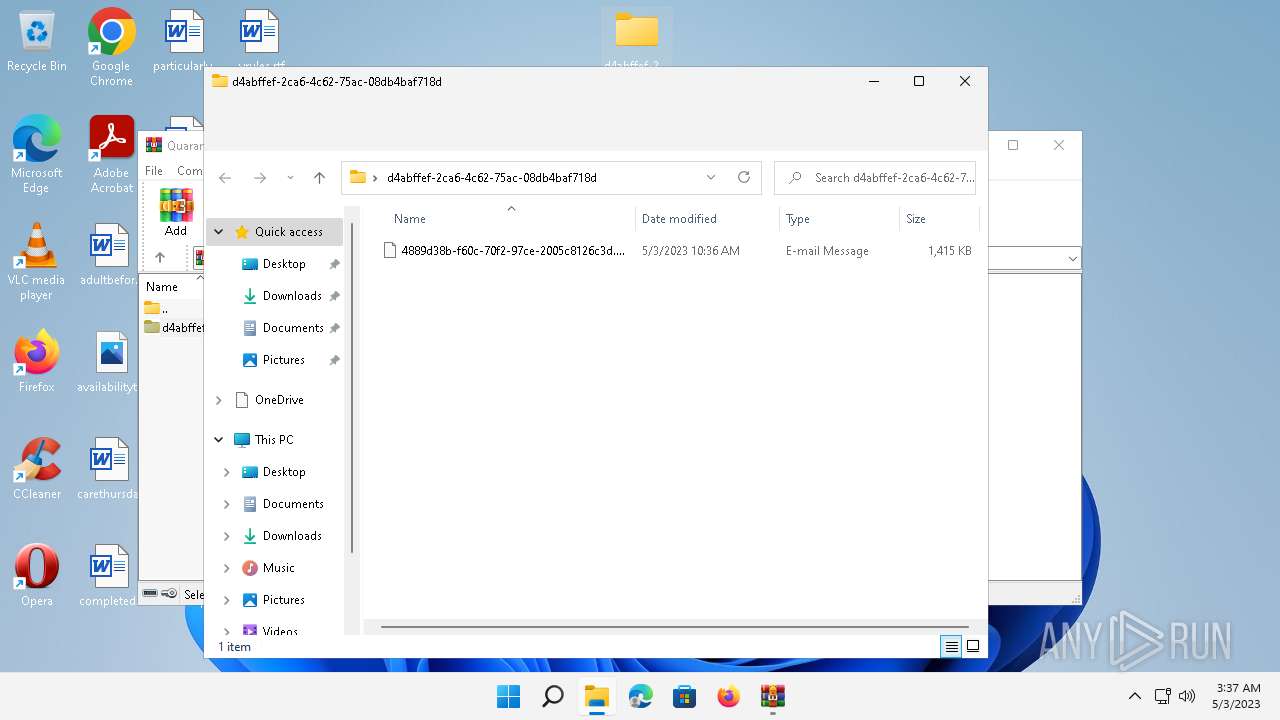
| ZipFileName: | d4abffef-2ca6-4c62-75ac-08db4baf718d/4889d38b-f60c-70f2-97ce-2005c8126c3d.eml |
|---|---|
| ZipUncompressedSize: | 4294967295 |
| ZipCompressedSize: | 4294967295 |
| ZipCRC: | 0x28231976 |
| ZipModifyDate: | 2023:05:03 10:36:06 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 45 |
Total processes
151
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1384 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=1728 --field-trial-handle=1588,i,7506379358649580831,14196960082568435541,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 2024 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Quarantined Messages (5).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2768 --field-trial-handle=1588,i,7506379358649580831,14196960082568435541,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 3920 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 /b /id 5892_2077350253 /if pdfshell_prev507d881c-2f04-4497-89bc-3e71297cad99 /CR | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
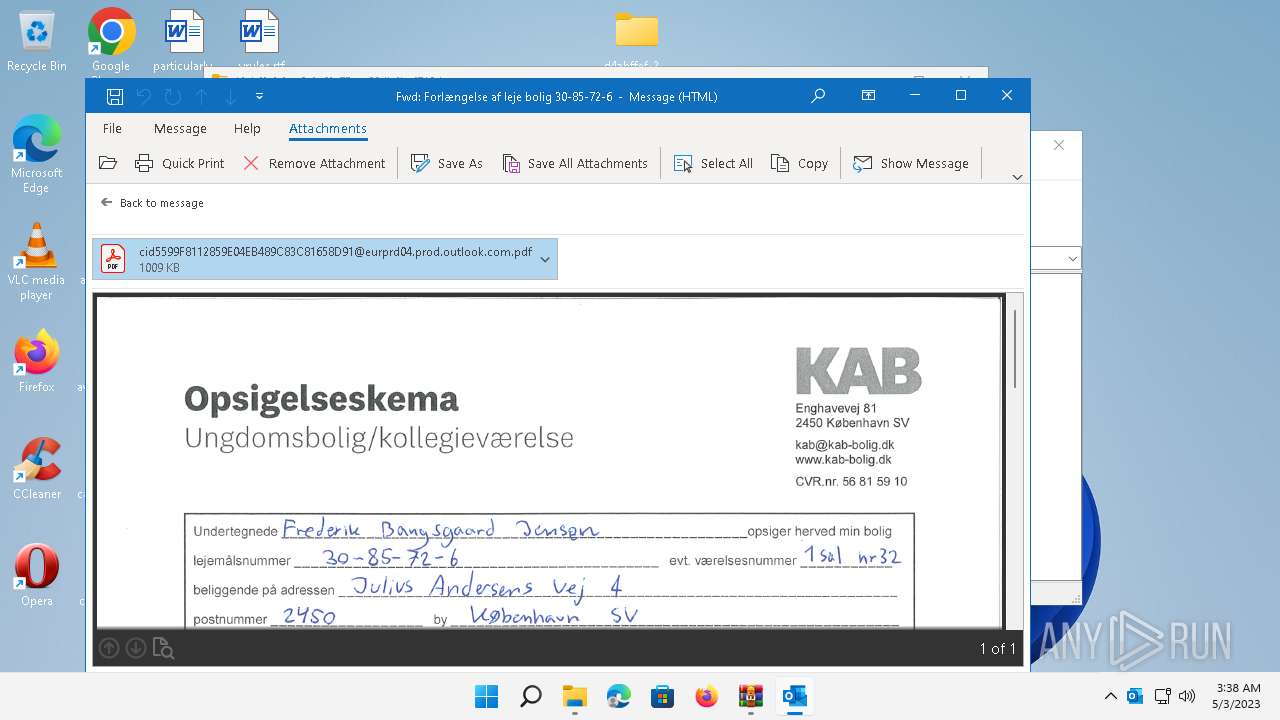
| 4280 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\d4abffef-2ca6-4c62-75ac-08db4baf718d\4889d38b-f60c-70f2-97ce-2005c8126c3d.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | OpenWith.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.15601.20142 Modules
| |||||||||||||||
| 5892 | C:\Windows\system32\prevhost.exe {DC6EFB56-9CFA-464D-8880-44885D7DC193} -Embedding | C:\Windows\System32\prevhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Preview Handler Surrogate Host Exit code: 0 Version: 10.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1732 --field-trial-handle=1588,i,7506379358649580831,14196960082568435541,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 6476 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6924 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" /b /id 5892_2077350253 /if pdfshell_prev507d881c-2f04-4497-89bc-3e71297cad99 /CR | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | prevhost.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 7188 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1748 --field-trial-handle=1588,i,7506379358649580831,14196960082568435541,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
Total events
33 360
Read events
32 700
Write events
392
Delete events
268
Modification events
| (PID) Process: | (2024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 000B0600C647D6C8AFF6D801 | |||
| (PID) Process: | (2024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6476) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6476) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6476) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6476) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6476) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | Zvpebfbsg.Bssvpr.BHGYBBX.RKR.15 |
Value: 000000000700000006000000640A0300000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFC0C092D0BDF6D80100000000 | |||
Executable files
2
Suspicious files
414
Text files
80
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4280 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - No Account.pst | — | |
MD5:— | SHA256:— | |||
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\C1512022-95E1-41E4-9D53-6F21B5D71CC2 | xml | |
MD5:54F65178693C51A8F1D5028DB0ABE1EB | SHA256:3F780B4A64A36C72464533D5E429311DF796EC1730AC1826FE374E2349770E31 | |||
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:25BDC5D75695B9F148B66030548EA3BD | SHA256:AF59C03DBDFF7F2D462713410DCE183522410F8B9968304D51028FFD683A3ACC | |||
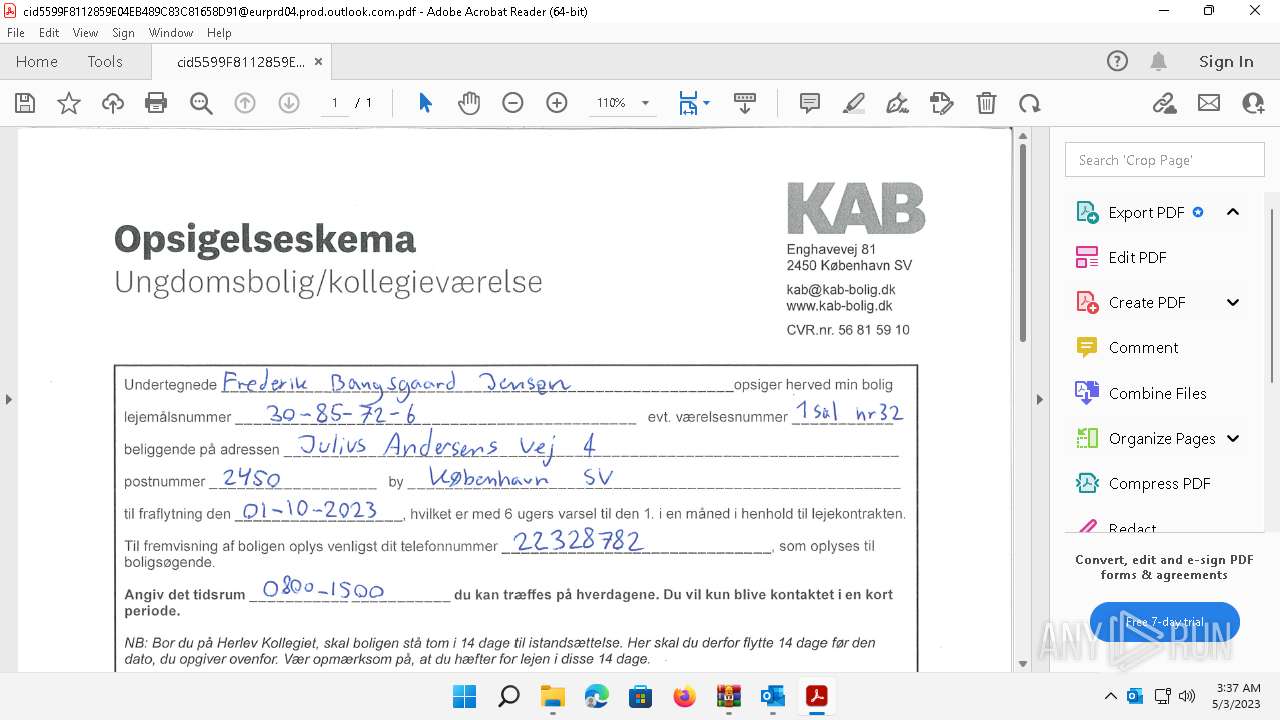
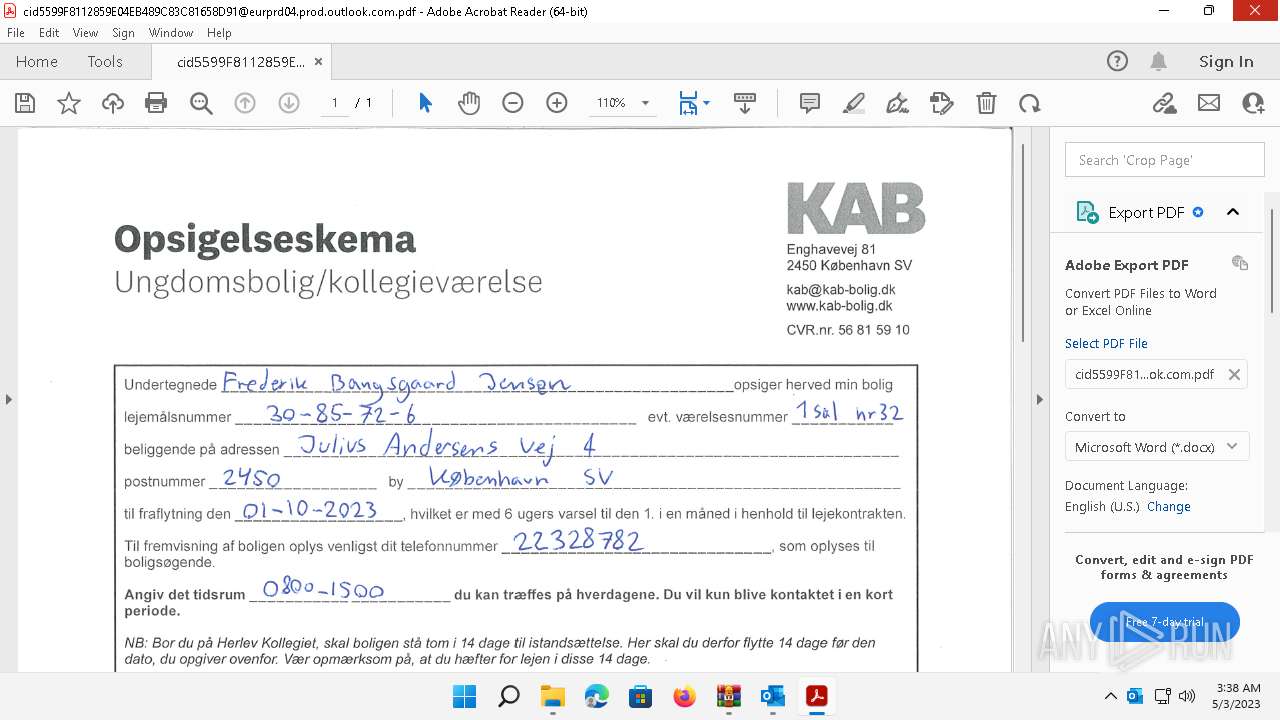
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\FSGYU8XC\cid5599F8112859E04EB489C83C81658D91@eurprd04.prod.outlook.com.pdf | ||
MD5:E0F7F77B0D0CA80869AFCD2AA53A13CD | SHA256:B51A36C037B102968B9AEB0669C04FE72F975DB3160396C7AB27243B764D5111 | |||
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:264D6EBA0B2BA3937B8DC8039ACD1E1C | SHA256:F6BA15E2257765FC29D19418169E5280832D9EF6794C8FADA66BC9FB9A71E5C3 | |||
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkF35C.tmp | binary | |
MD5:AD36954E1ABCD5B84338330C8A471C7D | SHA256:29E3BD0636619DD086844A5961518587E93BC165D910DA88A9C2838CE41D32D7 | |||
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:AF1EA7B68D3850DC6370F22F4923DE67 | SHA256:6CC4471957DA1E617326E5E61E9701E6CC1A962EF42143C3175AE90CBFDF4F27 | |||
| 2024 | WinRAR.exe | C:\USERS\ADMIN\APPDATA\ROAMING\WINRAR\VERSION.DAT | binary | |
MD5:92DB2DA3374350E492E363A8A81643BC | SHA256:854BF0BDF1FD9638CCCA8713A61514B658321556B8957FC5EDC56169DB0622EC | |||
| 4280 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\FSGYU8XC\cid5599F8112859E04EB489C83C81658D91@eurprd04.prod.outlook.com (002).pdf:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 4280 | OUTLOOK.EXE | C:\ProgramData\Microsoft\Office\Licenses\5\Perpetual\21661362613116367064193984360 | binary | |
MD5:B62A65FB2585144CA09561E0074DD33B | SHA256:417D4539712BB9B4C7E97A3B24271A9430D5C90990FCA6D33FFCC3B5288320A7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
29
DNS requests
23
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6316 | svchost.exe | GET | 304 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8b53cdf880faa446 | US | — | — | whitelisted |
6924 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAHfQJBoQn4xgYEKiBpnK%2Bc%3D | US | der | 471 b | whitelisted |
1480 | svchost.exe | GET | 200 | 13.107.4.52:80 | http://www.msftconnecttest.com/connecttest.txt | US | text | 22 b | whitelisted |
7804 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | US | binary | 471 b | whitelisted |
6316 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1480 | svchost.exe | GET | 200 | 13.107.4.52:80 | http://www.msftconnecttest.com/connecttest.txt | US | text | 22 b | whitelisted |
7804 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEARSlvj82CmnXclClPWkFaQ%3D | US | binary | 727 b | whitelisted |
4280 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
6924 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
7804 | AdobeARM.exe | GET | 200 | 2.19.126.76:80 | http://acroipm2.adobe.com/assets/Owner/arm/2023/5/OwnerAPI/Rdr.txt | DE | text | 4 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1480 | svchost.exe | 13.107.4.52:80 | www.msftconnecttest.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
— | — | 23.216.77.69:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6316 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
5708 | svchost.exe | 23.35.236.109:443 | fs.microsoft.com | AKAMAI-AS | DE | malicious |
4280 | OUTLOOK.EXE | 52.109.32.24:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | suspicious |
4280 | OUTLOOK.EXE | 52.109.88.193:443 | odc.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | suspicious |
6924 | Acrobat.exe | 54.194.243.238:443 | cc-api-data.adobe.io | AMAZON-02 | IE | suspicious |
6924 | Acrobat.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.msftconnecttest.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
ols.officeapps.live.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |