| File name: | ADVERTENCIA_17092.msi |
| Full analysis: | https://app.any.run/tasks/cdec208c-2a48-4381-aa37-1296ddf3b0b5 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2023, 21:55:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
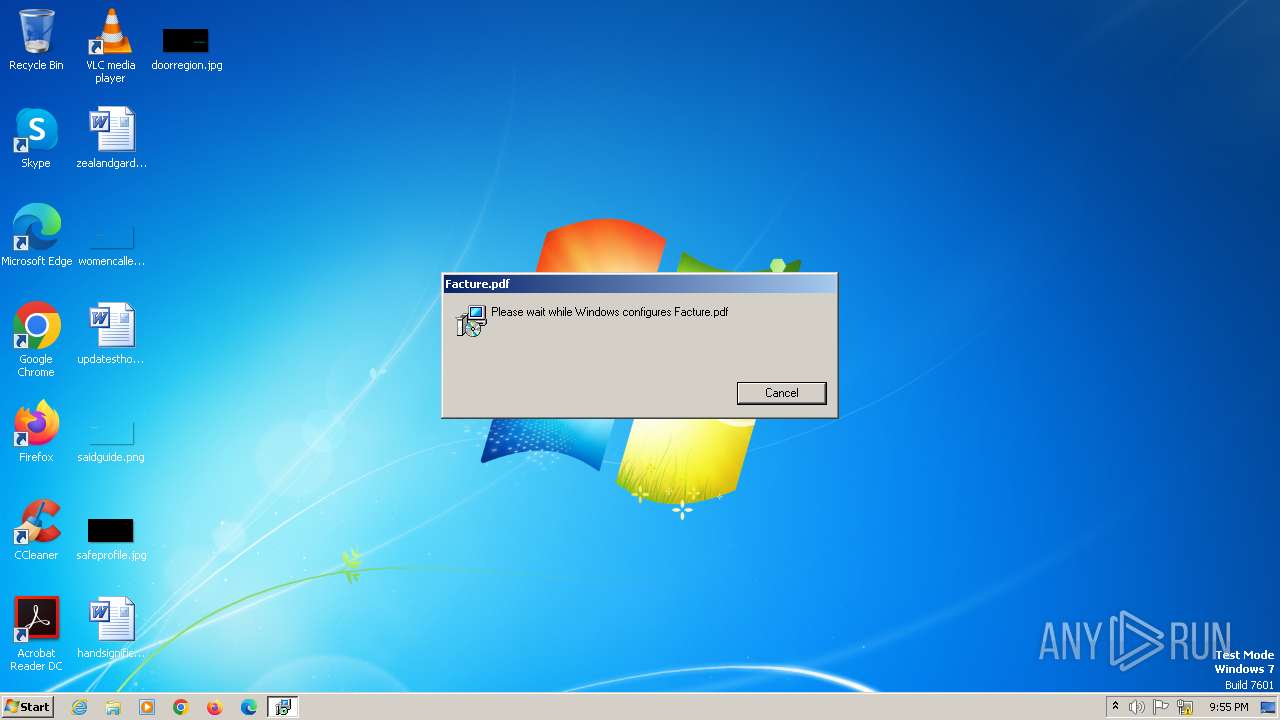
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 15:06:51 2020, Security: 0, Code page: 1252, Revision Number: {FC87A4D0-764F-4B78-8EF6-C0C159C56D6B}, Number of Words: 10, Subject: Facture.pdf, Author: Facture.pdf, Name of Creating Application: Advanced Installer 18.7 build 0a7fdead, Template: ;1033, Comments: This installer database contains the logic and data required to install Facture.pdf., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 47551653A59690565E93CAD6C132015E |
| SHA1: | 90AC63B5ED4ED536A623B63D312B0BE8C10B12C9 |
| SHA256: | E4DA4DB027FD66D0BDF38996463E34B3832FB46C13012A4EE5909F4E2C9583F2 |
| SSDEEP: | 12288:02Oo9IdHt+DorqxetLtzVaKmK+EPimr0C2txtnJ2adZjTtYKV139Aecy:02n9IdHWosK+EqC2t92aZjT6KV |
MALICIOUS
Checks whether a specified folder exists (SCRIPT)
- msiexec.exe (PID: 332)
Gets %appdata% folder path (SCRIPT)
- msiexec.exe (PID: 332)
Accesses environment variables (SCRIPT)
- msiexec.exe (PID: 332)
Creates internet connection object (SCRIPT)
- msiexec.exe (PID: 332)
Opens an HTTP connection (SCRIPT)
- msiexec.exe (PID: 332)
Sends HTTP request (SCRIPT)
- msiexec.exe (PID: 332)
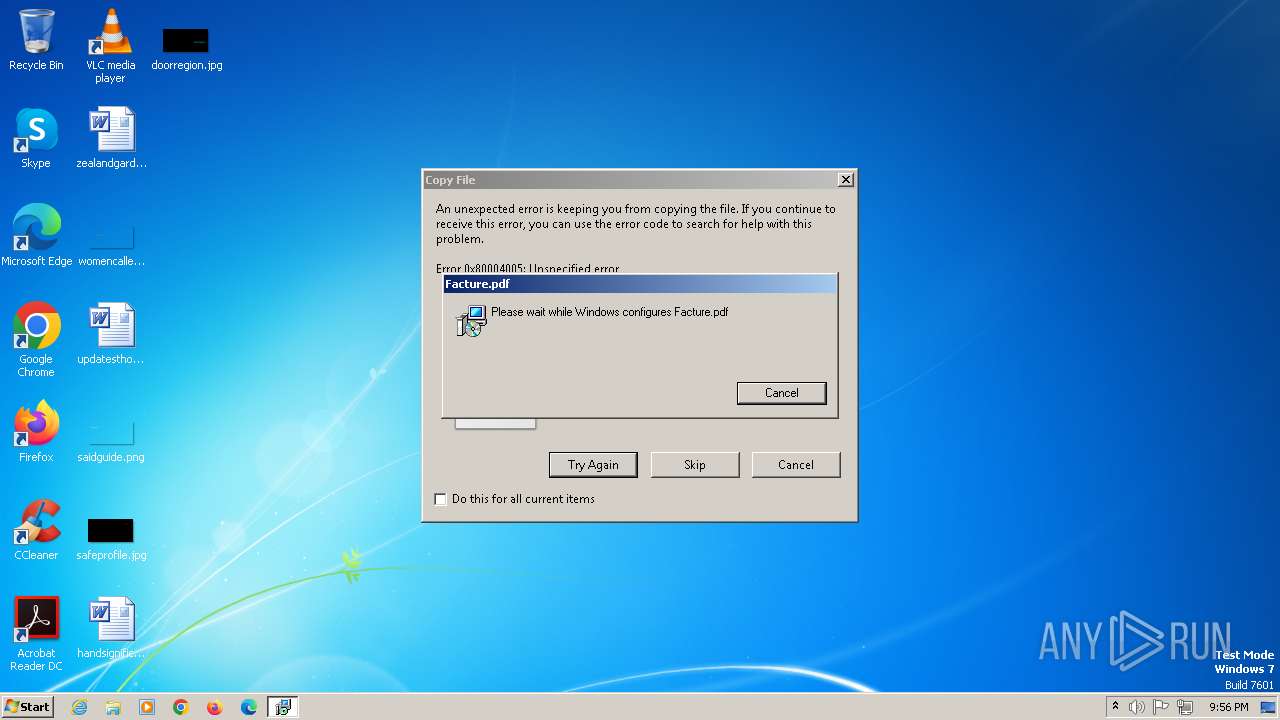
Deletes a file (SCRIPT)
- msiexec.exe (PID: 332)
Drops the executable file immediately after the start
- msiexec.exe (PID: 332)
- msiexec.exe (PID: 2072)
Create files in the Startup directory
- msiexec.exe (PID: 332)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 332)
Checks whether a specific file exists (SCRIPT)
- msiexec.exe (PID: 332)
Writes binary data to a Stream object (SCRIPT)
- msiexec.exe (PID: 332)
Reads the Internet Settings
- msiexec.exe (PID: 332)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- msiexec.exe (PID: 332)
Saves data to a binary file (SCRIPT)
- msiexec.exe (PID: 332)
Creates a Folder object (SCRIPT)
- msiexec.exe (PID: 332)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 332)
INFO
Reads the computer name
- msiexec.exe (PID: 332)
- msiexec.exe (PID: 2072)
Checks supported languages
- msiexec.exe (PID: 332)
- msiexec.exe (PID: 2072)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 332)
Reads Environment values
- msiexec.exe (PID: 332)
Creates files or folders in the user directory
- msiexec.exe (PID: 332)
- msiexec.exe (PID: 2072)
Create files in a temporary directory
- msiexec.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {FC87A4D0-764F-4B78-8EF6-C0C159C56D6B} |
| Words: | 10 |
| Subject: | Facture.pdf |
| Author: | Facture.pdf |
| LastModifiedBy: | - |
| Software: | Advanced Installer 18.7 build 0a7fdead |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Facture.pdf. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
35
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | C:\Windows\syswow64\MsiExec.exe -Embedding 81C16EE91C0E5276D9C703FCFC5EA851 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
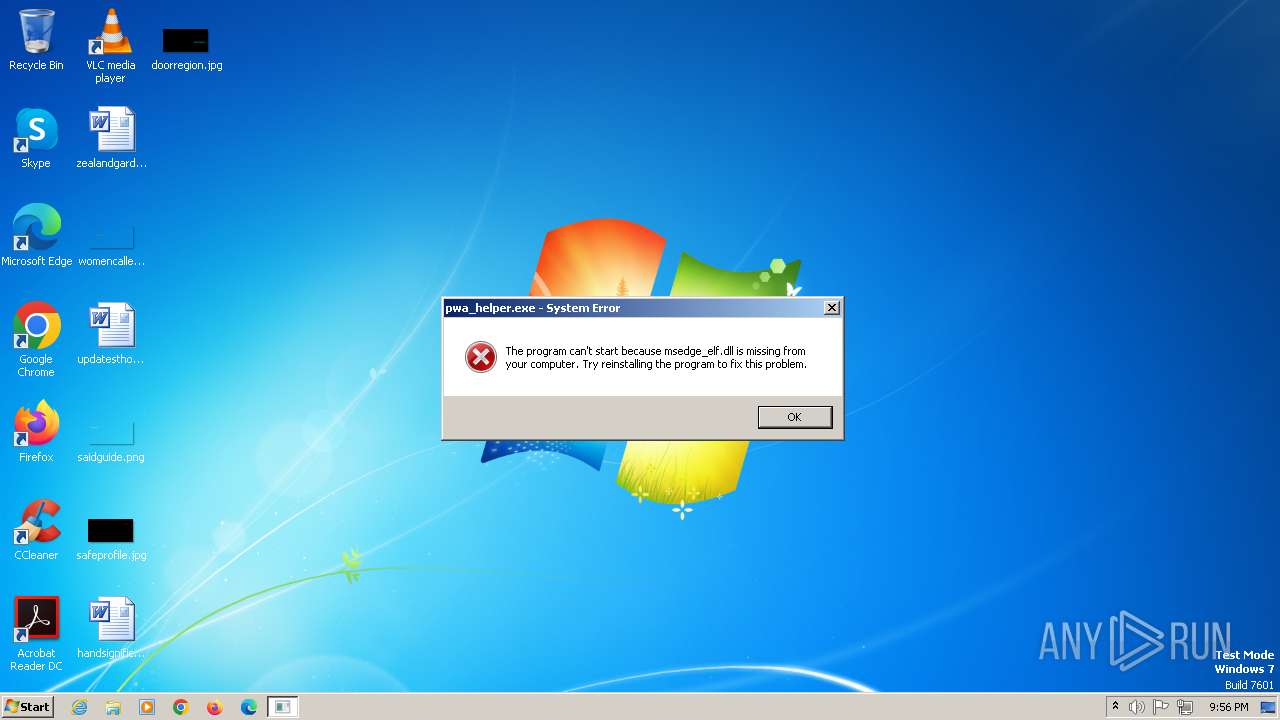
| 1800 | "C:\Users\admin\AppData\Roaming\Microsoft\pwa_helper.exe" | C:\Users\admin\AppData\Roaming\Microsoft\pwa_helper.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 2072 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2308 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ADVERTENCIA_17092.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 746
Read events
3 722
Write events
14
Delete events
10
Modification events
| (PID) Process: | (332) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (332) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (332) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (332) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (332) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (332) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E7070C0002000500150038000F00BA03010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-3896776584-4254864009-862391680-1000_CLASSES\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-3896776584-4254864009-862391680-1000_CLASSES\Local Settings\MuiCache\15A |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | delete value | Name: | C:\Config.Msi\22bb20.rbs |
Value: 31074245 | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
8
Suspicious files
11
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 332 | msiexec.exe | C:\Users\admin\AppData\Roaming\MICROS~1\pwa_helper.exe | executable | |
MD5:D5124F98199F99AF52AB19B23D8E8971 | SHA256:AA7400BD5BC2B21169B34F61B678BE7162061E68031CCBF80321DB119977F078 | |||
| 332 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\IRSOTM.zip | compressed | |
MD5:27BD14DF7B03FAE33B74D0E5204D11F3 | SHA256:3E64202FBF3ED3B3E4FCC5BB45001A1124A88E56F41EDE9495988413BF74841B | |||
| 332 | msiexec.exe | C:\Users\admin\AppData\Roaming\MICROS~1\msedge_elf.dll | executable | |
MD5:71D22B90FBF05D7E382BDF9BC99A7545 | SHA256:600BFCDFF8E1C5758DC0C354DE97DFB98620FDC1D149EA7A09A129D963494066 | |||
| 332 | msiexec.exe | C:\Users\admin\AppData\Roaming\MICROS~1\libEGL.dll | executable | |
MD5:765C3D953263F3682EF467C12027C36F | SHA256:0823402A0F1B947CF327FED3138BF3D4F6C567A0AC2ADA648112EFA6056237D7 | |||
| 2072 | msiexec.exe | C:\Windows\Installer\MSI12A3.tmp | executable | |
MD5:3D24A2AF1FB93F9960A17D6394484802 | SHA256:8D23754E6B8BB933D79861540B50DECA42E33AC4C3A6669C99FB368913B66D88 | |||
| 332 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B5E07AF15F3B6E48EDF7575279F2E80B | binary | |
MD5:785D7C4EE1D76425FF3DD0C337C3A9DC | SHA256:2B7C11DF76143FD05D7557ED65D28A9EF687FAD720E4A7E88824EBFFB88BF0B2 | |||
| 332 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\pwa_helper.lnk | binary | |
MD5:EABDE50EE43FDE73746593DA2DF1CD2A | SHA256:210D74F32A1DC2D8AF0CD2A980F4F56BA9FC74197F62D4705AD136D2FED9F96C | |||
| 332 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\nglb.ps1 | text | |
MD5:A067F5EC97BA51B576825B69BC855E58 | SHA256:CF3E339D25C3C023C9417FFC5D8E73F1DA828B18FEECAF14FDB9C24D04E49BA0 | |||
| 2072 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF546BD55FB20AA000.TMP | binary | |
MD5:5CFAABE7DF7CA2AA780A10679E6A13DD | SHA256:802B2807CCB6BA3A1C9156D2CA1BDC2FD6627E0A87BB9A781EBD0A44799E9694 | |||
| 2072 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Installer\{AD98D31D-3589-40C3-8F3A-CE6489D07AD2}\putty.exe | image | |
MD5:B115B4A1541BF759B027C6BAF81A9DFC | SHA256:1E88D81AEAA776D5D402F118571F60EBCDBA6B76F62E994AEB215C2F64E11D2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
332 | msiexec.exe | GET | 200 | 104.18.21.226:80 | http://secure.globalsign.com/cacert/alphasslcasha256g4.crt | unknown | binary | 1.14 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
332 | msiexec.exe | 186.202.153.99:443 | shopinkfast.com | Locaweb Servicos de Internet SA | BR | unknown |
332 | msiexec.exe | 104.18.21.226:80 | secure.globalsign.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
shopinkfast.com |
| unknown |
secure.globalsign.com |
| whitelisted |