| File name: | game.exe |
| Full analysis: | https://app.any.run/tasks/0dd1319e-89ba-4ad7-91e5-27c37f972da9 |
| Verdict: | Malicious activity |
| Analysis date: | May 08, 2018, 14:47:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 148682AE7A0801A398899E9686AF00CD |
| SHA1: | 663EED7587AACB9653EB613A6D843F270DBBA07E |
| SHA256: | E4D32871F428AF47D595B110518722009DE5D3978C5959A02B7E34D22E18E63F |
| SSDEEP: | 24576:zNY8Q4G6asn/LH3AGn6E52X0+ifmrVqQTLzKgB:zNmyupamRKgB |
MALICIOUS
Uses SVCHOST.EXE for hidden code execution
- JQA61Z2AC7.exe (PID: 2232)
Uses Task Scheduler to run other applications
- game.exe (PID: 2932)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2812)
SUSPICIOUS
Starts CMD.EXE for commands execution
- game.exe (PID: 2932)
Creates files in the program directory
- game.exe (PID: 2932)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2968)
Starts itself from another location
- game.exe (PID: 2932)
INFO
Dropped object may contain URL's
- game.exe (PID: 2932)
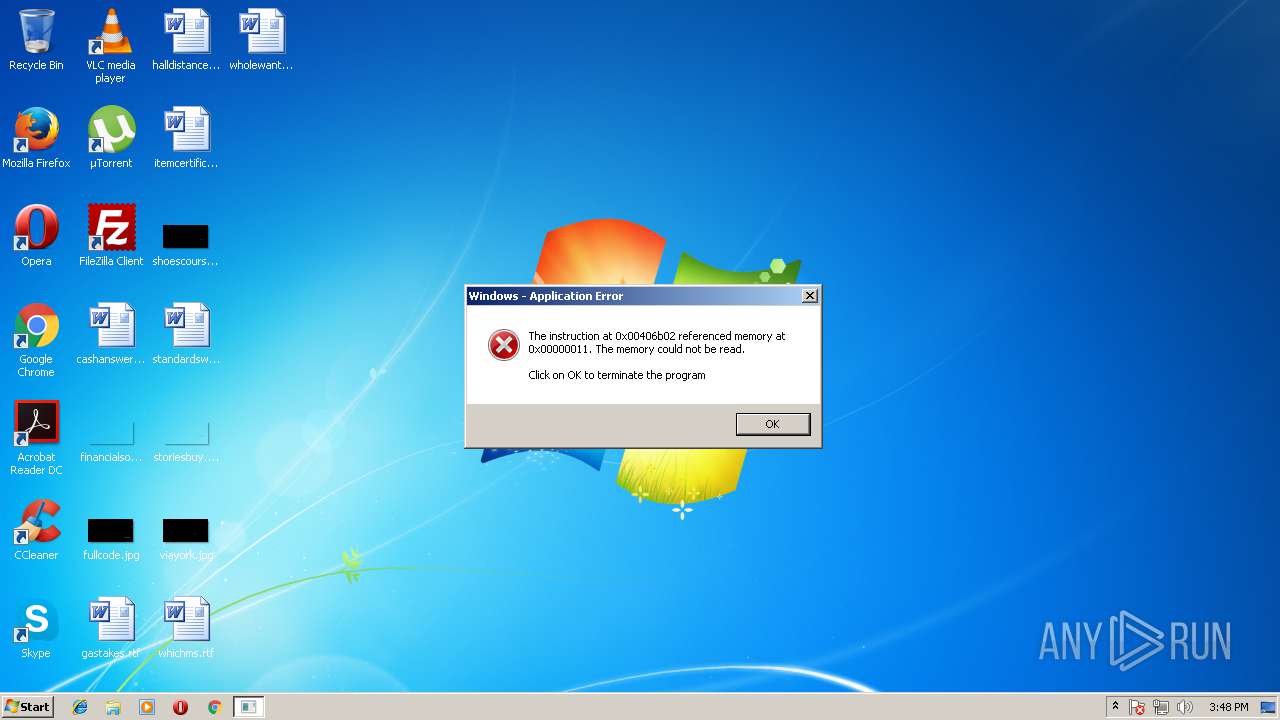
Application was crashed
- svchost.exe (PID: 2312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:05:02 17:40:10+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 141312 |
| InitializedDataSize: | 278016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2f0000 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.14.18.9 |
| ProductVersionNumber: | 1.14.18.9 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Conexant Systems, Inc |
| FileDescription: | SAII Command Line Application |
| FileVersion: | 1.14.18.9 |
| InternalName: | SAIICmd.exe |
| LegalCopyright: | © 2011,2012 Conexant Systems, Inc. |
| OriginalFileName: | SAIICmd.exe |
| ProductName: | SAII Command Line Application |
| ProductVersion: | 1.14.18.9 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-May-2018 15:40:10 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 02-May-2018 15:40:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x00001000 | 0x00032000 | 0x00015400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.98007 | |
.rsrc | 0x00033000 | 0x00035A0F | 0x0000F800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.81071 |
.idata | 0x00069000 | 0x00001000 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.30872 |
0x0006A000 | 0x00180000 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.260771 | |
aovbkots | 0x001EA000 | 0x00106000 | 0x00105600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.91332 |
noimsazc | 0x002F0000 | 0x00001000 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.77267 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.94904 | 607 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 6.20525 | 3240 | UNKNOWN | English - United States | RT_ICON |
3 | 4.06506 | 1384 | UNKNOWN | English - United States | RT_ICON |
4 | 5.53227 | 872 | UNKNOWN | English - United States | RT_ICON |
5 | 4.26355 | 3752 | UNKNOWN | English - United States | RT_ICON |
6 | 6.19929 | 7336 | UNKNOWN | English - United States | RT_ICON |
7 | 4.22811 | 5672 | UNKNOWN | English - United States | RT_ICON |
8 | 6.26499 | 12840 | UNKNOWN | English - United States | RT_ICON |
9 | 6.31296 | 51240 | UNKNOWN | English - United States | RT_ICON |
10 | 3.92942 | 19496 | UNKNOWN | English - United States | RT_ICON |
Imports
comctl32.dll |
kernel32.dll |
Total processes
42
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2232 | "C:\ProgramData\{PSNME0E4-DUB7-GXNK-0STQERB63N19}\JQA61Z2AC7.exe" | C:\ProgramData\{PSNME0E4-DUB7-GXNK-0STQERB63N19}\JQA61Z2AC7.exe | game.exe | ||||||||||||
User: admin Company: Conexant Systems, Inc Integrity Level: MEDIUM Description: SAII Command Line Application Exit code: 0 Version: 1.14.18.9 Modules
| |||||||||||||||
| 2292 | taskkill /im game.exe /f | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2312 | "C:\Windows\System32\svchost.exe" | C:\Windows\System32\svchost.exe | JQA61Z2AC7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2812 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /MO 45 /TN "L3BSPLWC0E4RVSMVXM" /TR "C:\ProgramData\{0ZNXXWG3-L3BS-H716-872XCB3U2AMZ}\UCPAQN04.vbs" /F | C:\Windows\System32\schtasks.exe | — | game.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2932 | "C:\Users\admin\AppData\Local\Temp\game.exe" | C:\Users\admin\AppData\Local\Temp\game.exe | explorer.exe | ||||||||||||
User: admin Company: Conexant Systems, Inc Integrity Level: MEDIUM Description: SAII Command Line Application Exit code: 0 Version: 1.14.18.9 Modules
| |||||||||||||||
| 2968 | "C:\Windows\System32\cmd.exe" /c taskkill /im game.exe /f & erase C:\Users\admin\AppData\Local\Temp\game.exe & exit | C:\Windows\System32\cmd.exe | — | game.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
101
Read events
96
Write events
5
Delete events
0
Modification events
| (PID) Process: | (2932) game.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2932) game.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2312) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: C:\ProgramData\{PSNME0E4-DUB7-GXNK-0STQERB63N19}\JQA61Z2AC7.exe | |||
Executable files
1
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2932 | game.exe | C:\ProgramData\nmtemp | text | |
MD5:— | SHA256:— | |||
| 2932 | game.exe | C:\ProgramData\{0ZNXXWG3-L3BS-H716-872XCB3U2AMZ}\UCPAQN04.vbs | text | |
MD5:— | SHA256:— | |||
| 2932 | game.exe | C:\ProgramData\{0ZNXXWG3-L3BS-H716-872XCB3U2AMZ}\L4D0VL3G.bat | text | |
MD5:— | SHA256:— | |||
| 2932 | game.exe | C:\ProgramData\{PSNME0E4-DUB7-GXNK-0STQERB63N19}\JQA61Z2AC7.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 31.41.40.14:80 | http://game.nedmann.pro/gate/checkConnection.php | RU | text | 12 b | malicious |
— | — | POST | 200 | 31.41.40.14:80 | http://game.nedmann.pro/gate/check.php | RU | text | 8 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 31.41.40.14:80 | game.nedmann.pro | Relink LTD | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
game.nedmann.pro |
| malicious |
Threats
Process | Message |
|---|---|
game.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
JQA61Z2AC7.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
svchost.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|