| URL: | https://cdn2.minitool.com/?p=pw&e=pw-free |
| Full analysis: | https://app.any.run/tasks/ff413ee7-c673-48f8-9170-500ed5160248 |
| Verdict: | Malicious activity |
| Analysis date: | September 15, 2020, 14:05:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 04BF21D4BD7B96C0360A5706602EFB70 |
| SHA1: | 9049DA7C55EA9B9193E675C7E7BDF18ACAAA602F |
| SHA256: | E4D09C904CA81D88D2438CDFC9E187CD712269033FEEFAC88B5FDADEEC10BE9C |
| SSDEEP: | 3:N8c4BTKq+Vn:2c1qCn |
MALICIOUS
Application was dropped or rewritten from another process
- pw12-free.exe (PID: 1844)
- pw12-free.exe (PID: 884)
- pwfree1201-32bit-online.exe (PID: 2524)
- updatechecker.exe (PID: 2336)
- AgentService.exe (PID: 2620)
- BootTrigger.exe (PID: 3844)
- AgentService.exe (PID: 3732)
- experience.exe (PID: 4072)
- AgentService.exe (PID: 3880)
- experience.exe (PID: 2852)
- partitionwizard.exe (PID: 3656)
- SchedulerService.exe (PID: 3352)
- SchedulerService.exe (PID: 2088)
- SchedulerService.exe (PID: 464)
Actions looks like stealing of personal data
- pw12-free.tmp (PID: 2600)
Loads dropped or rewritten executable
- updatechecker.exe (PID: 2336)
- experience.exe (PID: 4072)
- BootTrigger.exe (PID: 3844)
- AgentService.exe (PID: 2620)
- AgentService.exe (PID: 3732)
- AgentService.exe (PID: 3880)
- SchedulerService.exe (PID: 2088)
- SchedulerService.exe (PID: 3352)
- experience.exe (PID: 2852)
- SchedulerService.exe (PID: 464)
- partitionwizard.exe (PID: 3656)
Changes the autorun value in the registry
- pwfree1201-32bit-online.tmp (PID: 1172)
Loads the Task Scheduler COM API
- updatechecker.exe (PID: 2336)
- BootTrigger.exe (PID: 3844)
Changes settings of System certificates
- experience.exe (PID: 4072)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 4044)
- pw12-free.exe (PID: 884)
- pw12-free.exe (PID: 1844)
- pw12-free.tmp (PID: 2600)
- SmDownloader.exe (PID: 2660)
- pwfree1201-32bit-online.exe (PID: 2524)
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.exe (PID: 4024)
- pw_sm_setup_x86.tmp (PID: 2276)
- partitionwizard.exe (PID: 3656)
Reads Windows owner or organization settings
- pw12-free.tmp (PID: 2600)
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.tmp (PID: 2276)
Reads the Windows organization settings
- pw12-free.tmp (PID: 2600)
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.tmp (PID: 2276)
Reads Internet Cache Settings
- pw12-free.tmp (PID: 2600)
- experience.exe (PID: 4072)
- experience.exe (PID: 2852)
- partitionwizard.exe (PID: 3656)
Reads Environment values
- pw12-free.tmp (PID: 2600)
Reads internet explorer settings
- pw12-free.tmp (PID: 2600)
- experience.exe (PID: 4072)
- experience.exe (PID: 2852)
- partitionwizard.exe (PID: 3656)
Uses TASKKILL.EXE to kill process
- pw_sm_setup_x86.tmp (PID: 2276)
Executed as Windows Service
- AgentService.exe (PID: 3880)
- SchedulerService.exe (PID: 464)
- vds.exe (PID: 3164)
Creates files in the program directory
- AgentService.exe (PID: 3880)
- SchedulerService.exe (PID: 464)
- partitionwizard.exe (PID: 3656)
Changes IE settings (feature browser emulation)
- pw12-free.tmp (PID: 2600)
Creates files in the user directory
- experience.exe (PID: 2852)
- experience.exe (PID: 4072)
- partitionwizard.exe (PID: 3656)
Starts Internet Explorer
- pw12-free.tmp (PID: 2600)
Executed via COM
- vdsldr.exe (PID: 1344)
Low-level read access rights to disk partition
- vds.exe (PID: 3164)
Creates files in the Windows directory
- partitionwizard.exe (PID: 3656)
Adds / modifies Windows certificates
- experience.exe (PID: 4072)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 3360)
- iexplore.exe (PID: 3268)
Application launched itself
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3360)
Changes internet zones settings
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3360)
Creates files in the user directory
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3268)
Reads internet explorer settings
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 3268)
Modifies the phishing filter of IE
- iexplore.exe (PID: 4044)
Reads settings of System Certificates
- iexplore.exe (PID: 4044)
- experience.exe (PID: 2852)
- iexplore.exe (PID: 3268)
- partitionwizard.exe (PID: 3656)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3268)
Changes settings of System certificates
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3268)
Application was dropped or rewritten from another process
- pw12-free.tmp (PID: 2600)
- pw12-free.tmp (PID: 1784)
- SmDownloader.exe (PID: 2660)
- SmDownloader.exe (PID: 1532)
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.tmp (PID: 2276)
Creates files in the program directory
- pw12-free.tmp (PID: 2600)
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.tmp (PID: 2276)
Loads dropped or rewritten executable
- SmDownloader.exe (PID: 2660)
- pw12-free.tmp (PID: 2600)
- SmDownloader.exe (PID: 1532)
Dropped object may contain Bitcoin addresses
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.tmp (PID: 2276)
Creates a software uninstall entry
- pwfree1201-32bit-online.tmp (PID: 1172)
- pw_sm_setup_x86.tmp (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
81
Monitored processes
29
Malicious processes
19
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "taskkill.exe" /f /im "AgentService.exe" | C:\Windows\system32\taskkill.exe | — | pw_sm_setup_x86.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 464 | "C:\Program Files\MiniTool ShadowMaker\SchedulerService.exe" | C:\Program Files\MiniTool ShadowMaker\SchedulerService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 884 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe | iexplore.exe | ||||||||||||
User: admin Company: MiniTool Software Limited Integrity Level: MEDIUM Description: MiniTool Partition Wizard Free Setup Exit code: 0 Version: 12 Modules
| |||||||||||||||
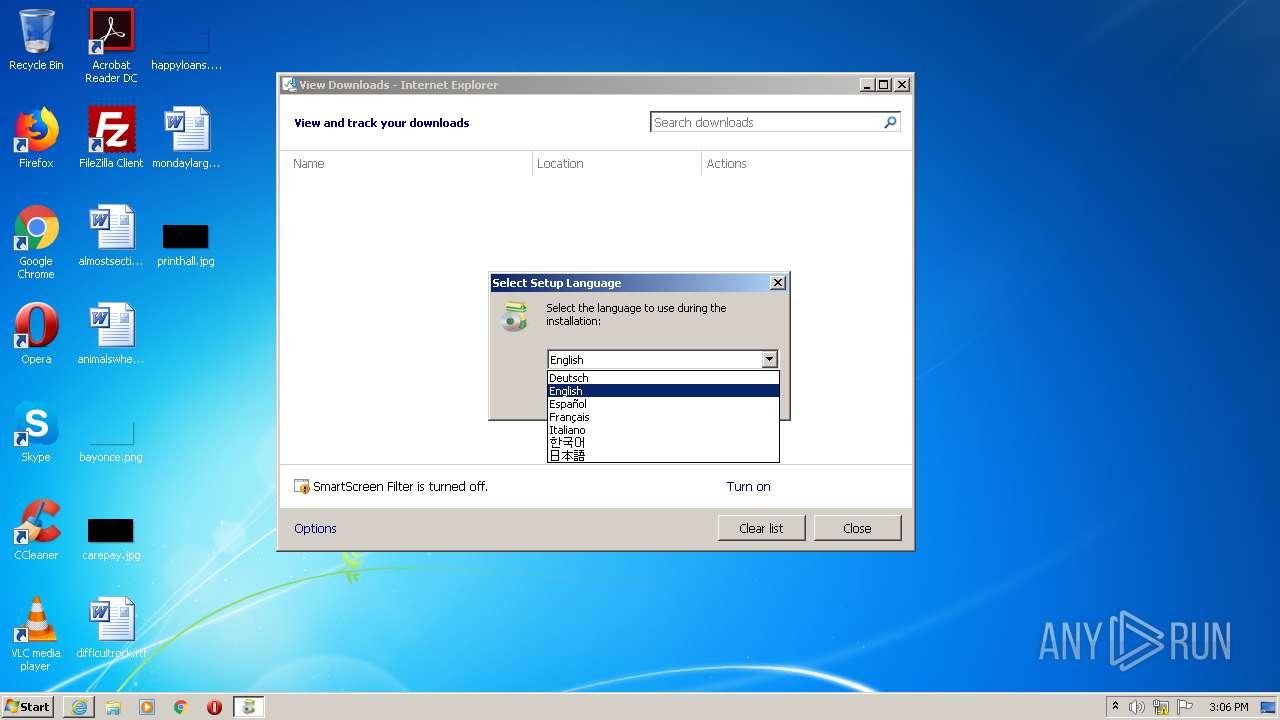
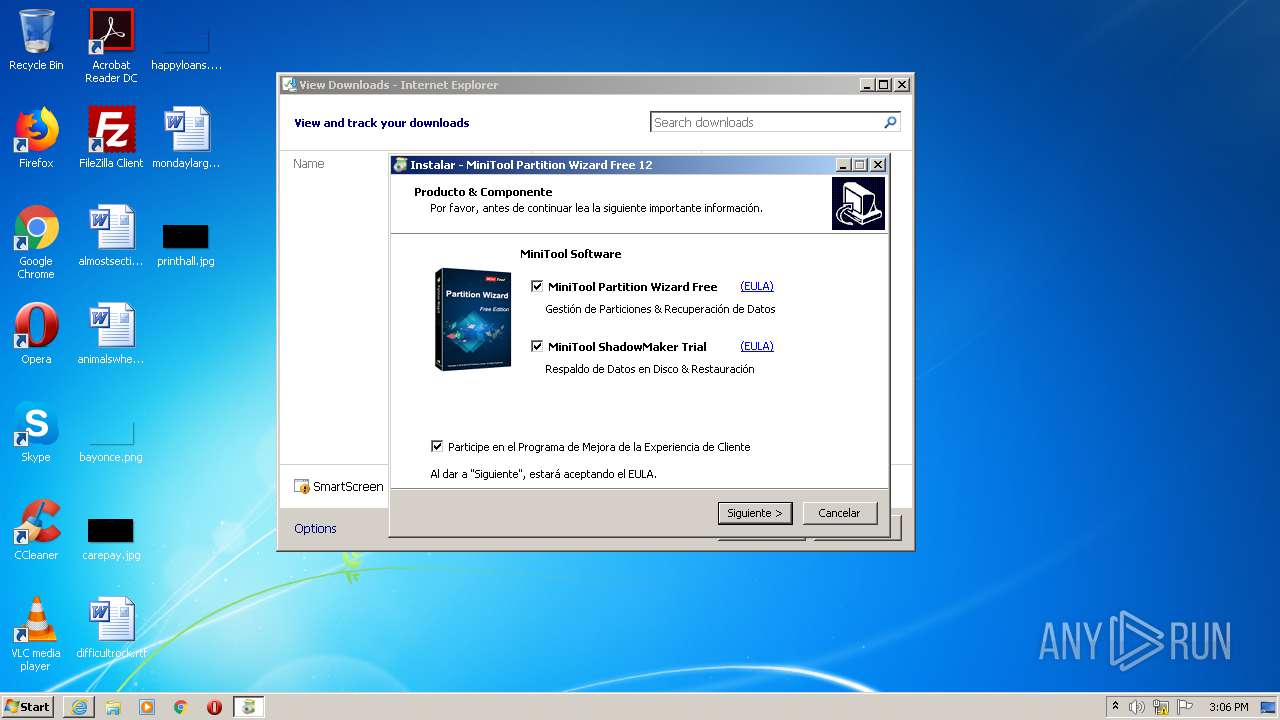
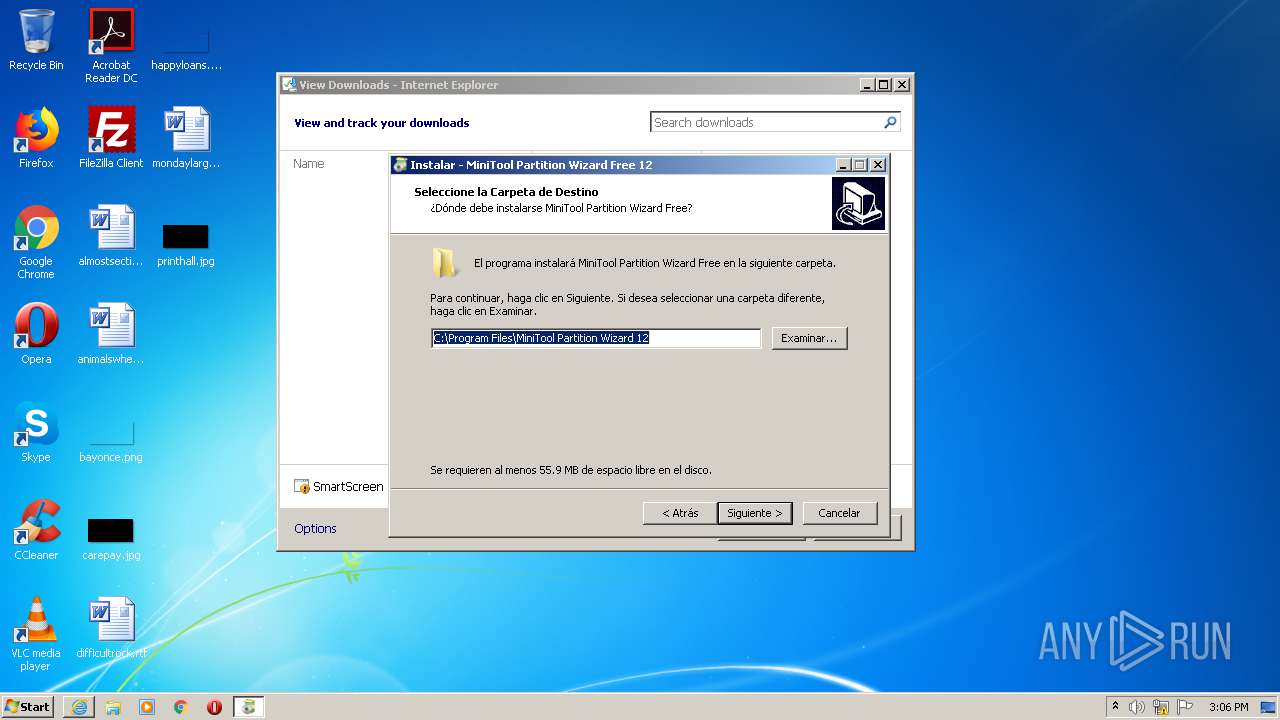
| 1172 | "C:\Users\admin\AppData\Local\Temp\is-G5LE1.tmp\pwfree1201-32bit-online.tmp" /SL5="$D0122,16020118,488960,C:\Users\admin\AppData\Local\Temp\pwfree1201-32bit-online.exe" /VERYSILENT /DIR="C:\Program Files\MiniTool Partition Wizard 12" /LANG=spanish | C:\Users\admin\AppData\Local\Temp\is-G5LE1.tmp\pwfree1201-32bit-online.tmp | pwfree1201-32bit-online.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1344 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1532 | "C:\Users\admin\AppData\Local\Temp\is-RGFDE.tmp\SmDownloader.exe" /HWND:393642 /PATH:"C:\Program Files\MiniTool Partition Wizard 12\..\MiniTool ShadowMaker" /URL:https://www.partitionwizard.com/download/online-setup-config/pwfree-v12-bundle-sm.ini /VERYSILENT /USERMSG:1439 /LANG:spanish | C:\Users\admin\AppData\Local\Temp\is-RGFDE.tmp\SmDownloader.exe | pw12-free.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1784 | "C:\Users\admin\AppData\Local\Temp\is-5MEVT.tmp\pw12-free.tmp" /SL5="$20194,4432956,488960,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe" | C:\Users\admin\AppData\Local\Temp\is-5MEVT.tmp\pw12-free.tmp | — | pw12-free.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1844 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe" /SPAWNWND=$4016C /NOTIFYWND=$20194 | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe | pw12-free.tmp | ||||||||||||
User: admin Company: MiniTool Software Limited Integrity Level: HIGH Description: MiniTool Partition Wizard Free Setup Exit code: 0 Version: 12 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\MiniTool ShadowMaker\SchedulerService.exe" -s | C:\Program Files\MiniTool ShadowMaker\SchedulerService.exe | — | pw_sm_setup_x86.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2180 | "taskkill.exe" /f /im "SchedulerService.exe" | C:\Windows\system32\taskkill.exe | — | pw_sm_setup_x86.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 752
Read events
2 436
Write events
297
Delete events
19
Modification events
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1728808486 | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30837609 | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
204
Suspicious files
103
Text files
155
Unknown types
145
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab353F.tmp | — | |
MD5:— | SHA256:— | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar3540.tmp | — | |
MD5:— | SHA256:— | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAC0AFC8AF6FD02D0.TMP | — | |
MD5:— | SHA256:— | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\pw12-free[1].exe | — | |
MD5:— | SHA256:— | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1671F9390BAD97B0.TMP | — | |
MD5:— | SHA256:— | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe.e1x0kjm.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2600 | pw12-free.tmp | C:\Users\admin\AppData\Local\Temp\000F7074.log | — | |
MD5:— | SHA256:— | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1BB09BEEC155258835C193A7AA85AA5B_022A63B69F040F39C88A29D588AE11F3 | binary | |
MD5:— | SHA256:— | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\pw12-free.exe.e1x0kjm.partial | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
58
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2600 | pw12-free.tmp | GET | 200 | 52.212.91.170:80 | http://vps.sihomuwe-ter.com/ | IE | — | — | malicious |
3768 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
3768 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | US | der | 727 b | whitelisted |
2600 | pw12-free.tmp | POST | 200 | 54.229.112.10:80 | http://ww1.sihomuwe-ter.com/ | IE | binary | 815 Kb | malicious |
1048 | svchost.exe | GET | 200 | 216.58.207.67:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjqTAc%2FHIGOD%2BaUx0%3D | US | der | 492 b | whitelisted |
4044 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
4044 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2600 | pw12-free.tmp | POST | 200 | 52.212.91.170:80 | http://vps.sihomuwe-ter.com/ | IE | — | — | malicious |
3768 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEQDV0%2FSv1ipafQFB%2B2ghUeOK | US | der | 472 b | whitelisted |
4072 | experience.exe | GET | 200 | 216.58.207.67:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAa5VhR9EEs0AgAAAAB5ZBM%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3768 | iexplore.exe | 104.20.144.70:443 | cdn2.minitool.com | Cloudflare Inc | US | suspicious |
3768 | iexplore.exe | 104.20.145.70:443 | cdn2.minitool.com | Cloudflare Inc | US | shared |
4044 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3768 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2600 | pw12-free.tmp | 52.212.91.170:80 | vps.sihomuwe-ter.com | Amazon.com, Inc. | IE | malicious |
2600 | pw12-free.tmp | 54.229.112.10:80 | ww1.sihomuwe-ter.com | Amazon.com, Inc. | IE | malicious |
4044 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
4044 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1532 | SmDownloader.exe | 104.20.7.9:443 | www.partitionwizard.com | Cloudflare Inc | US | shared |
1048 | svchost.exe | 216.58.207.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn2.minitool.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
vps.sihomuwe-ter.com |
| malicious |
ww1.sihomuwe-ter.com |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
Process | Message |
|---|---|
AgentService.exe | C:\Program Files\MiniTool ShadowMaker\log\sys.log |
partitionwizard.exe | QMetaObject::connectSlotsByName: No matching signal for on_action_change_lanuage()
|
partitionwizard.exe | QMetaObject::connectSlotsByName: No matching signal for on_caption_menu_button_clicked()
|
partitionwizard.exe | QMetaObject::connectSlotsByName: No matching signal for on_caption_menu_button_clicked()
|
partitionwizard.exe | QMetaObject::connectSlotsByName: No matching signal for on_append_partition_management_tab()
|
partitionwizard.exe | Unknown property flat-widget-border-color
|
partitionwizard.exe | Unknown property flat-widget-border-color
|
partitionwizard.exe | QMetaObject::connectSlotsByName: No matching signal for on_caption_menu_button_clicked()
|
partitionwizard.exe | libpng warning: iCCP: known incorrect sRGB profile
|
partitionwizard.exe | QMetaObject::connectSlotsByName: No matching signal for on_checking_license_exited(int)
|