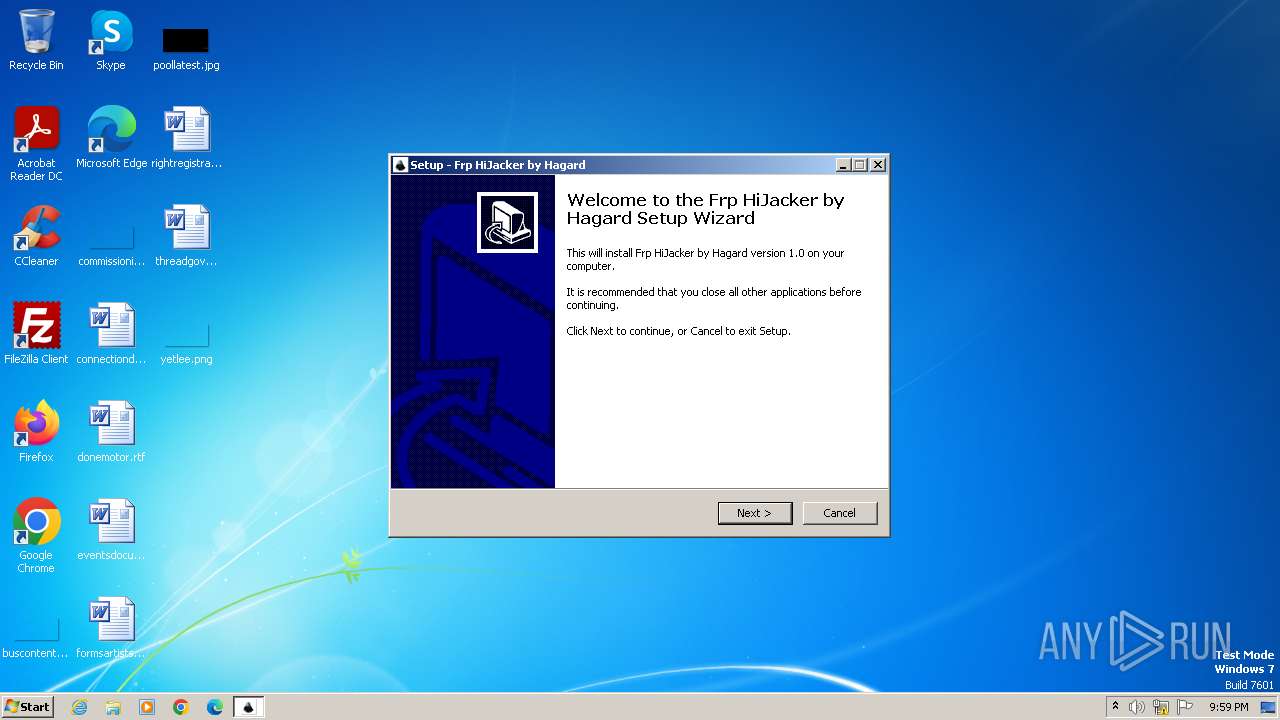
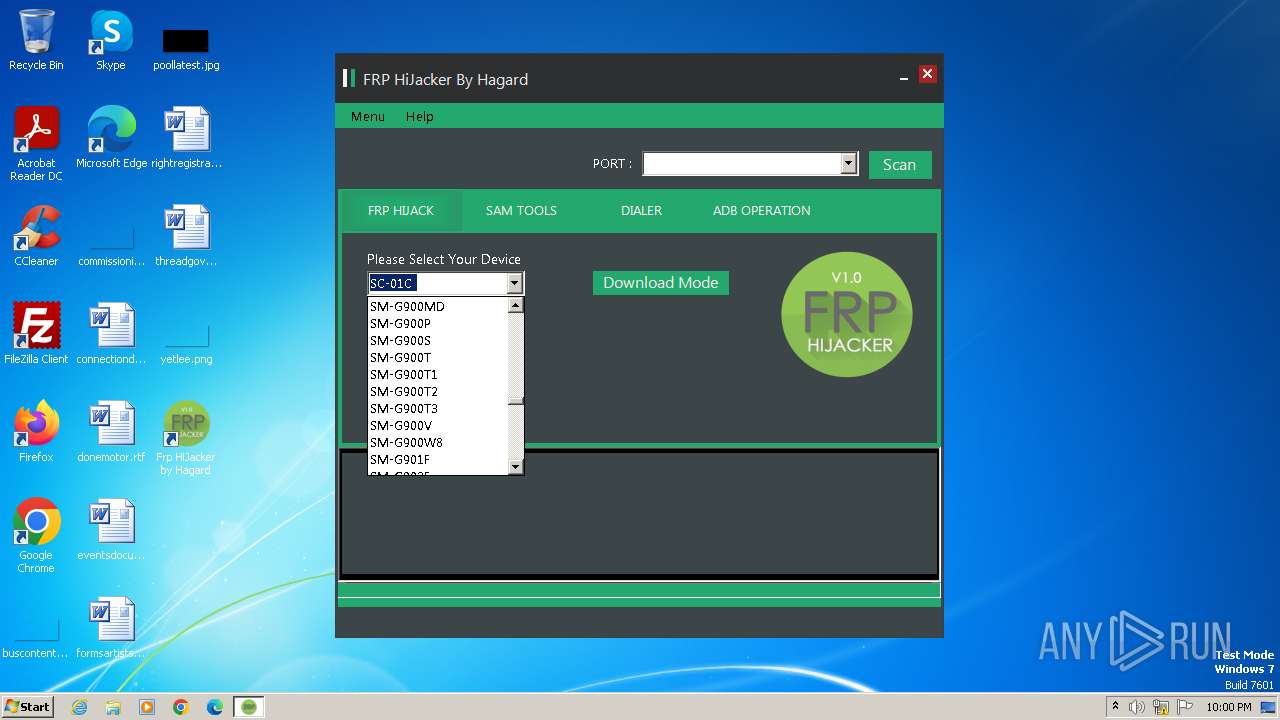
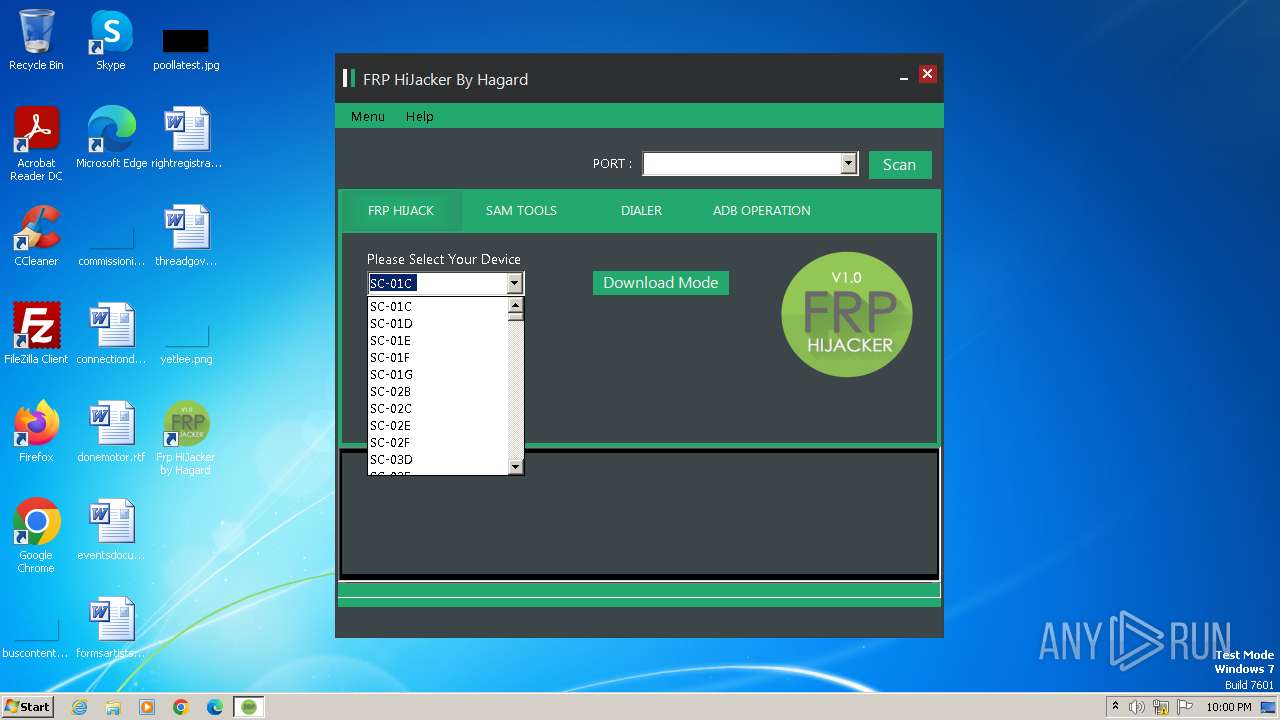
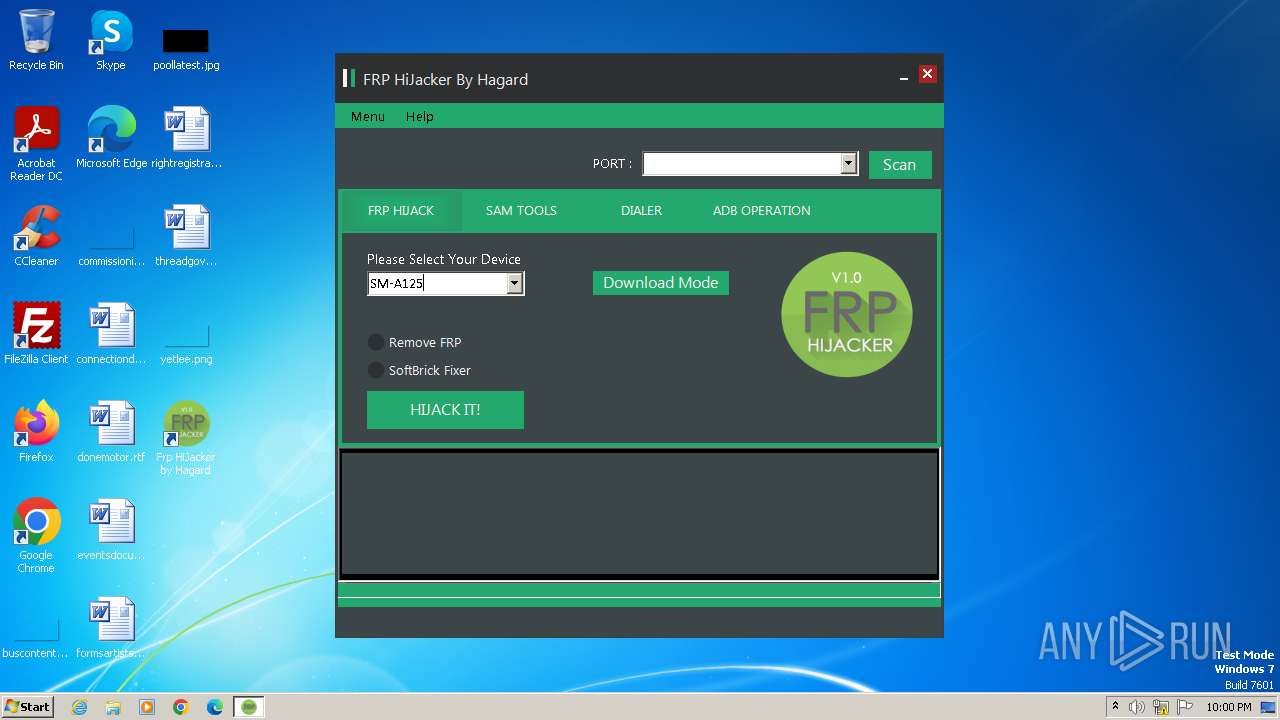
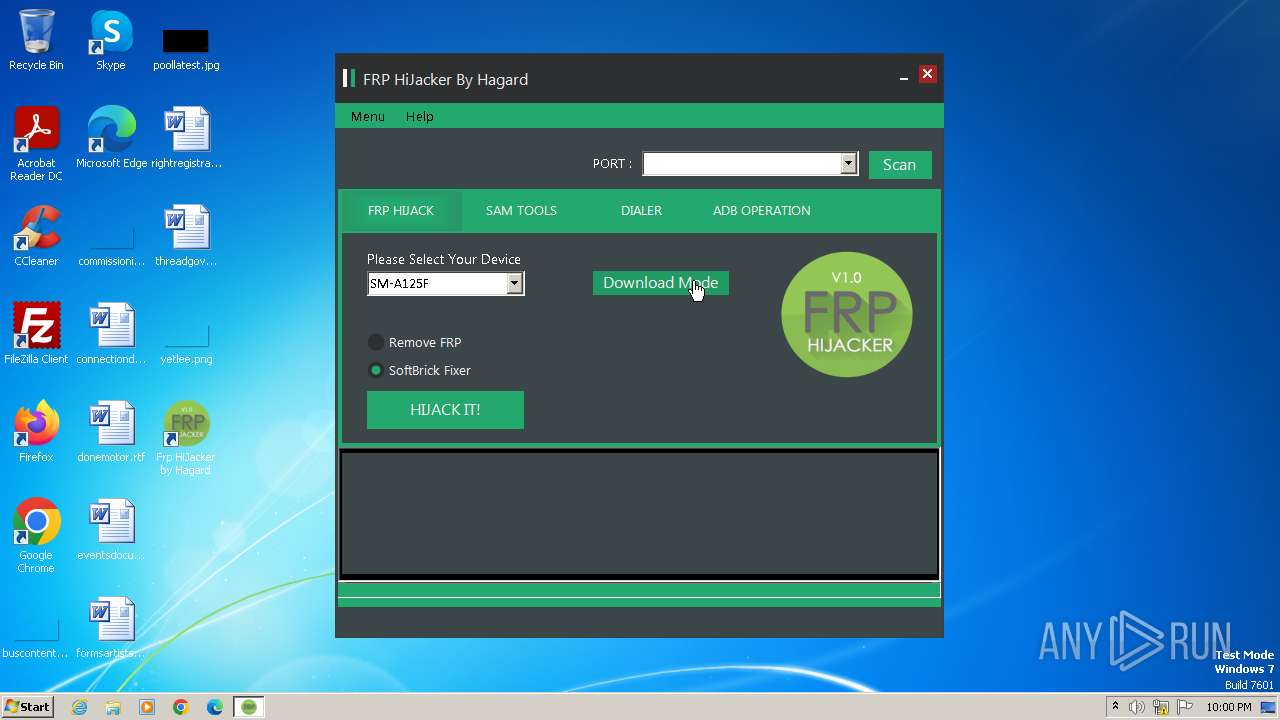
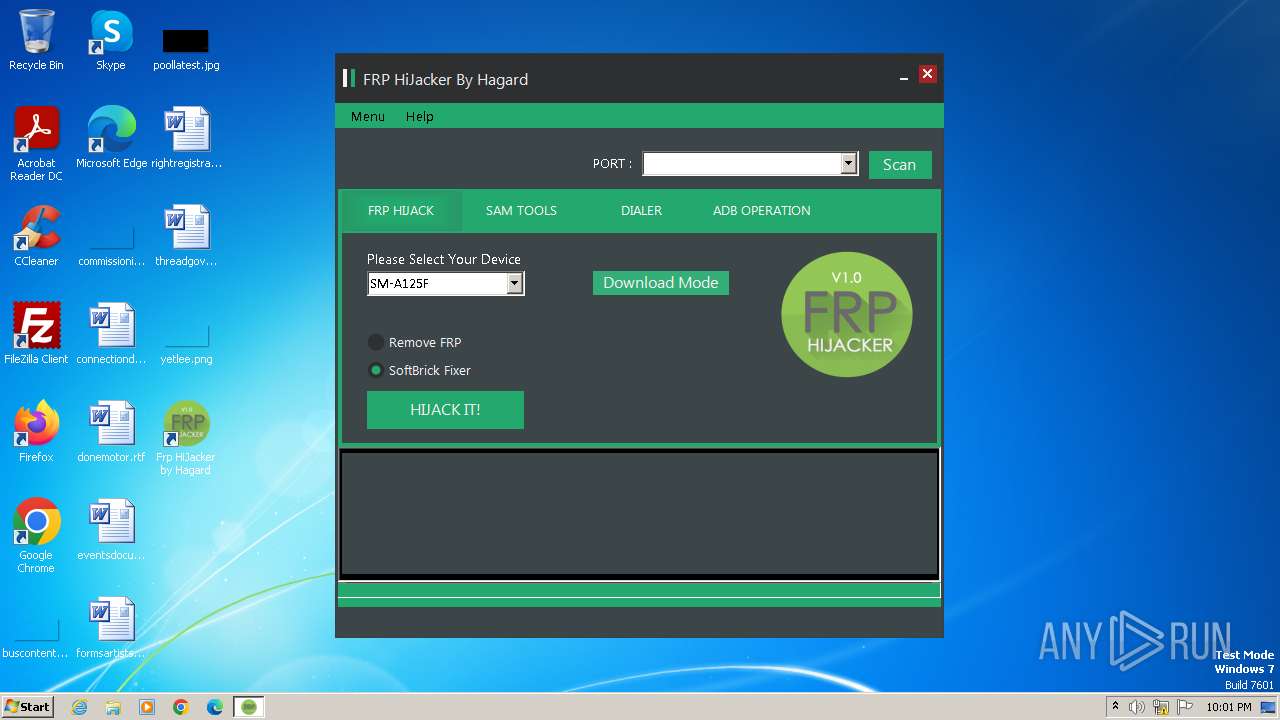
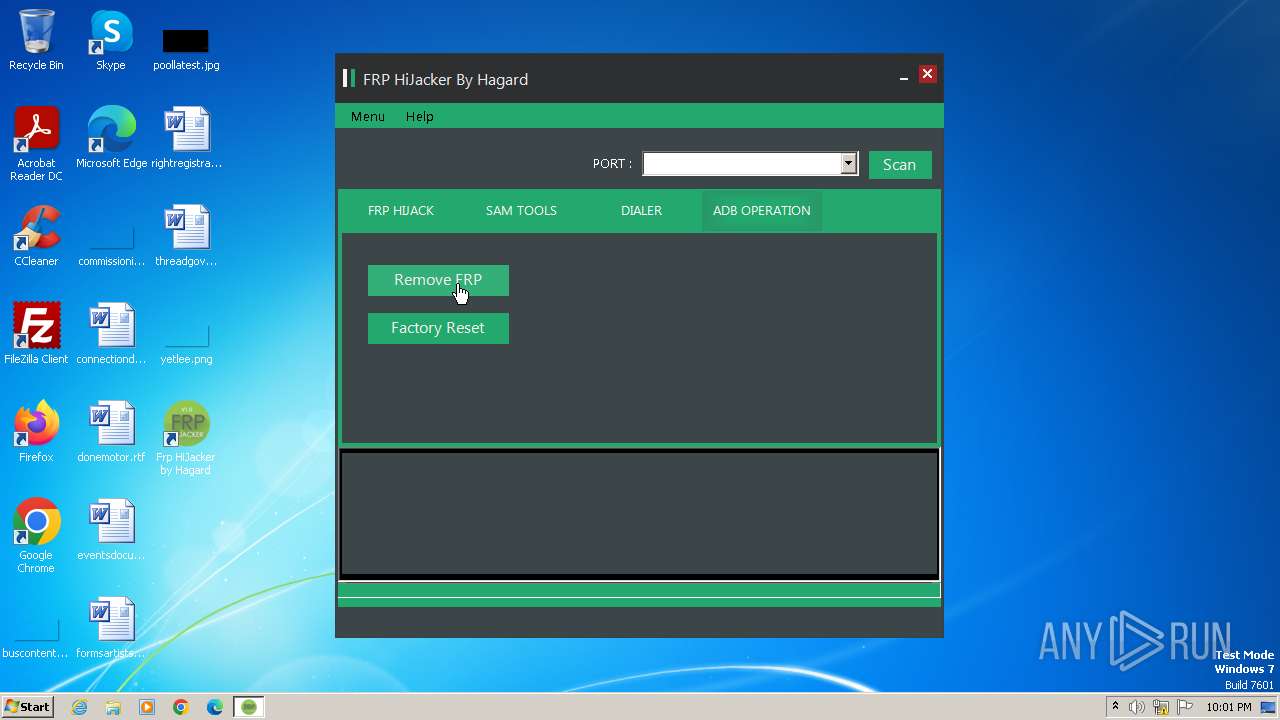
| File name: | Frp Hijacker by Hagard V1.0 setup.exe |
| Full analysis: | https://app.any.run/tasks/047e4ea3-192f-4b6b-8cf2-660e390a1296 |
| Verdict: | Malicious activity |
| Analysis date: | June 01, 2024, 20:59:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 385674B94BEFA4586707D78A1F335430 |
| SHA1: | 3AF786A96EA5762FCC1C6698D0F76AB161DD9E6D |
| SHA256: | E4CD4902E523D9DE131AA4A908E3E1EF8B7210C6833455DB8A3CB19AFBA7EB37 |
| SSDEEP: | 24576:ZQilUwJ+4yz1rc1dDUPaxyiEUr7UBizEdl6BeJF4DLieeoLf:Z9OoYJOQdouloLf |
MALICIOUS
Drops the executable file immediately after the start
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 3964)
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 1024)
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
- FRP Hijacker.exe (PID: 728)
SUSPICIOUS
Executable content was dropped or overwritten
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 3964)
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 1024)
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
- FRP Hijacker.exe (PID: 728)
Process drops legitimate windows executable
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
Reads the Windows owner or organization settings
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
Application launched itself
- adb.exe (PID: 1640)
INFO
Checks supported languages
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 3964)
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 3980)
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 1024)
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
- FRP Hijacker.exe (PID: 728)
- adb.exe (PID: 1640)
- adb.exe (PID: 2276)
- adb.exe (PID: 188)
Reads the computer name
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 3980)
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
- FRP Hijacker.exe (PID: 728)
- adb.exe (PID: 2276)
Create files in a temporary directory
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 1024)
- Frp Hijacker by Hagard V1.0 setup.exe (PID: 3964)
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
- FRP Hijacker.exe (PID: 728)
- adb.exe (PID: 2276)
Creates files in the program directory
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
Creates a software uninstall entry
- Frp Hijacker by Hagard V1.0 setup.tmp (PID: 1020)
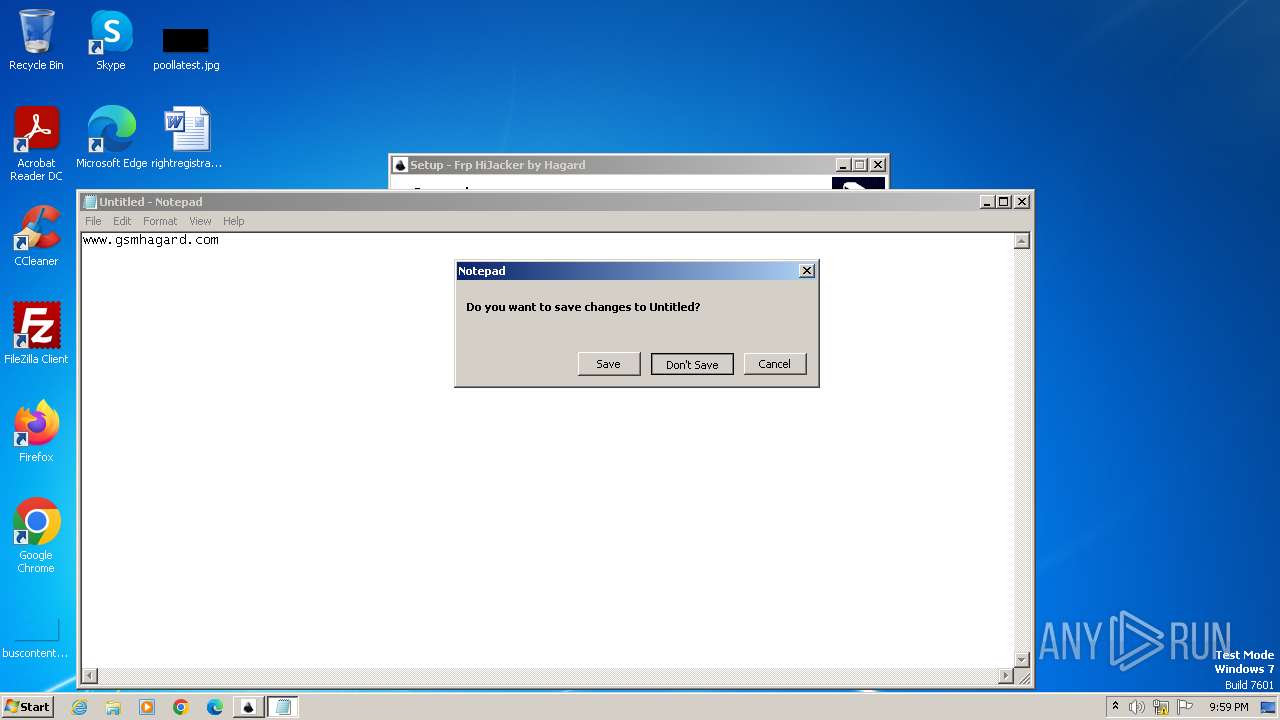
Manual execution by a user
- notepad.exe (PID: 2136)
Reads the machine GUID from the registry
- FRP Hijacker.exe (PID: 728)
- adb.exe (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (71.1) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.1) |
| .scr | | | Windows screen saver (8.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.2) |
| .exe | | | Win32 Executable (generic) (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 59392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Gsmhagard |
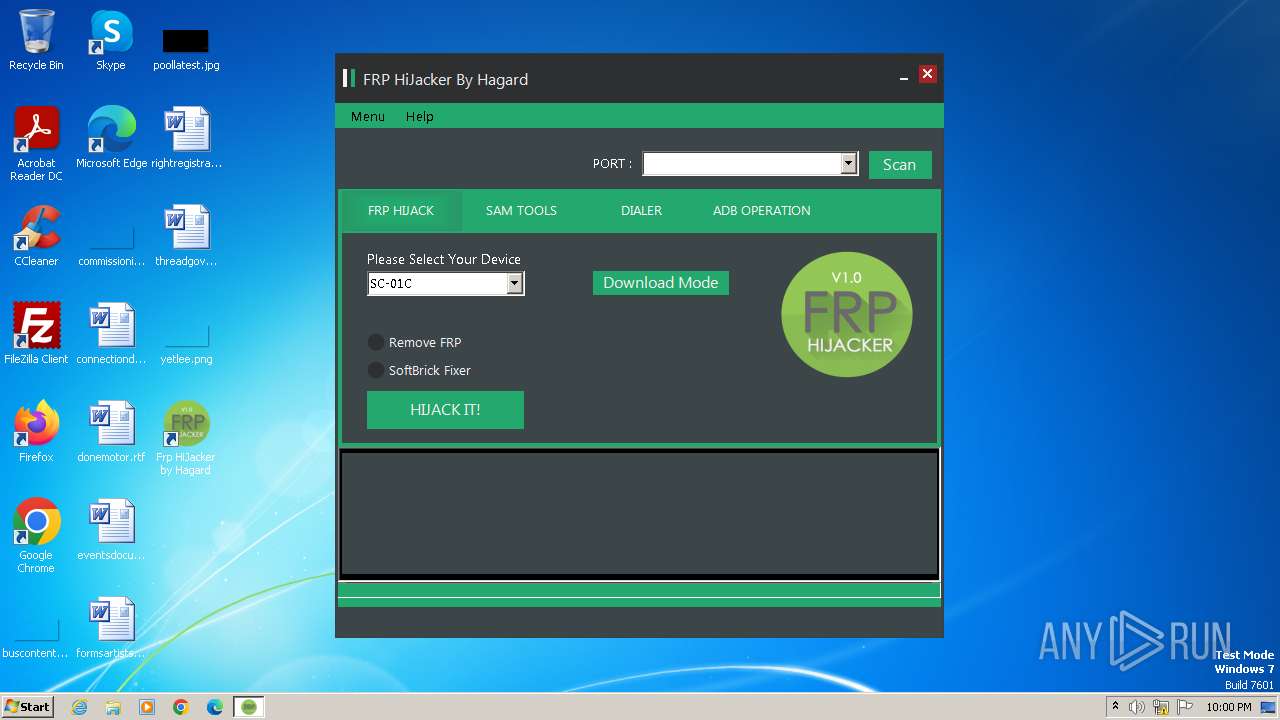
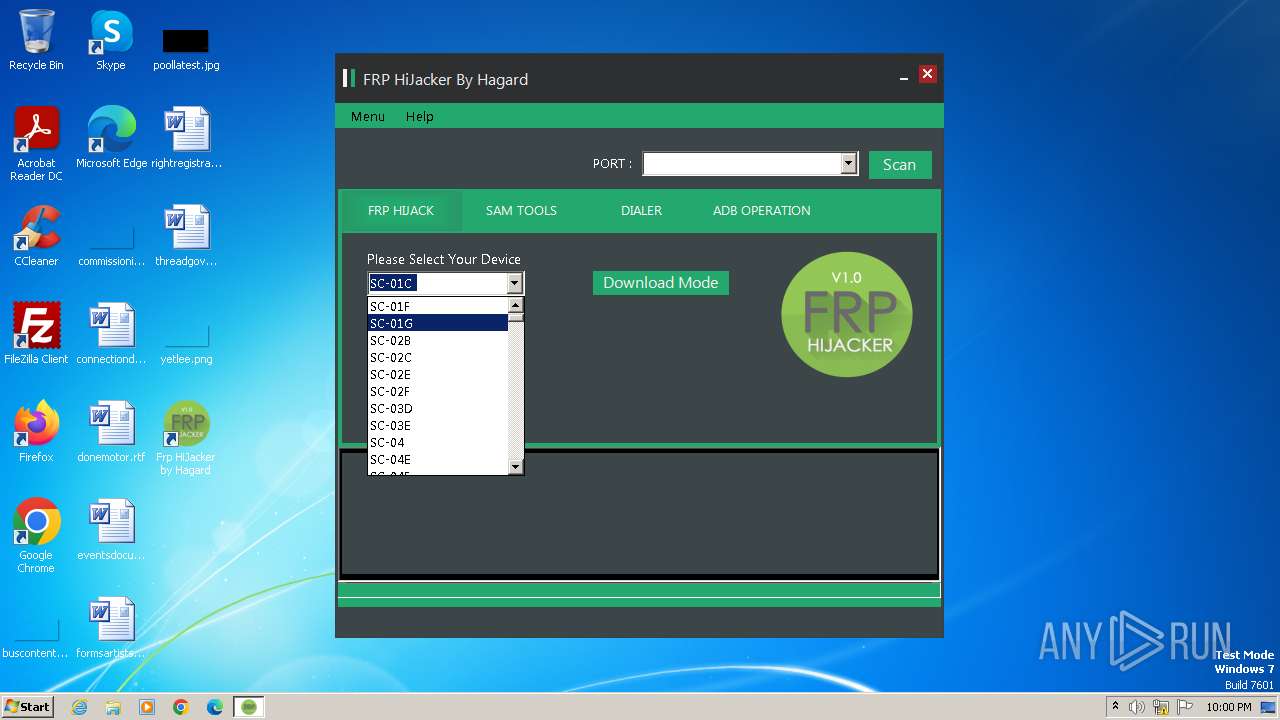
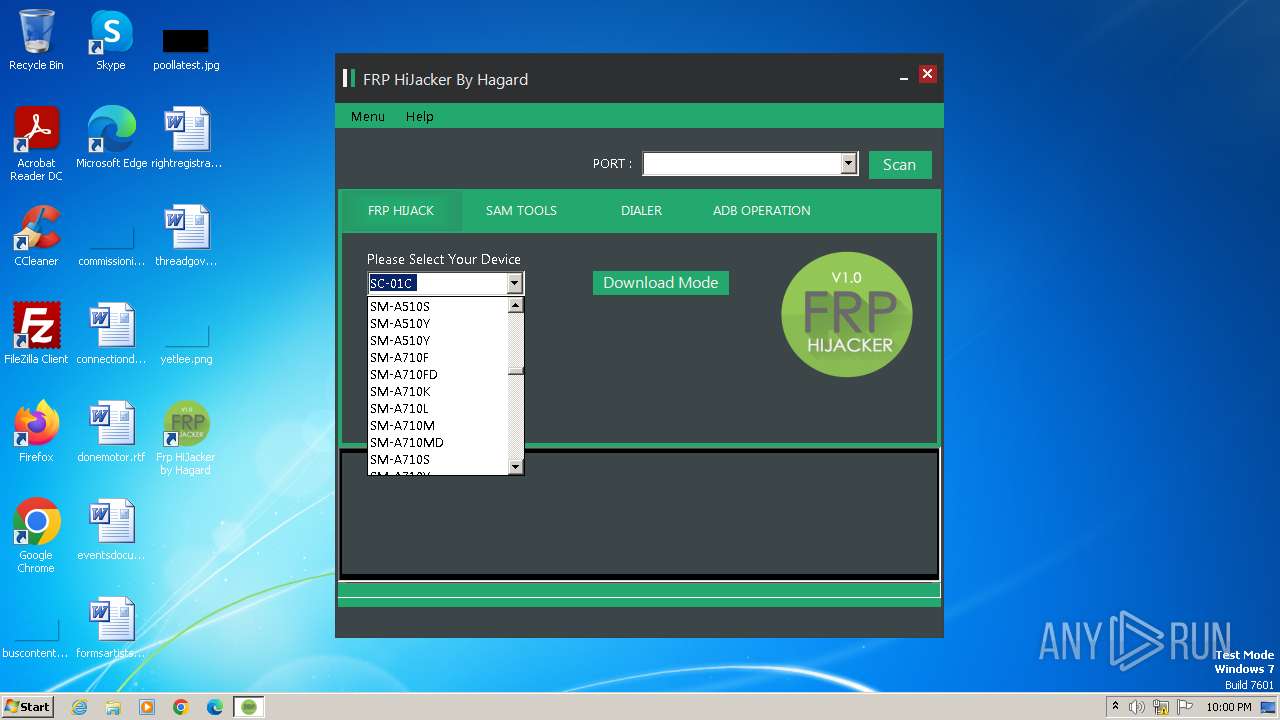
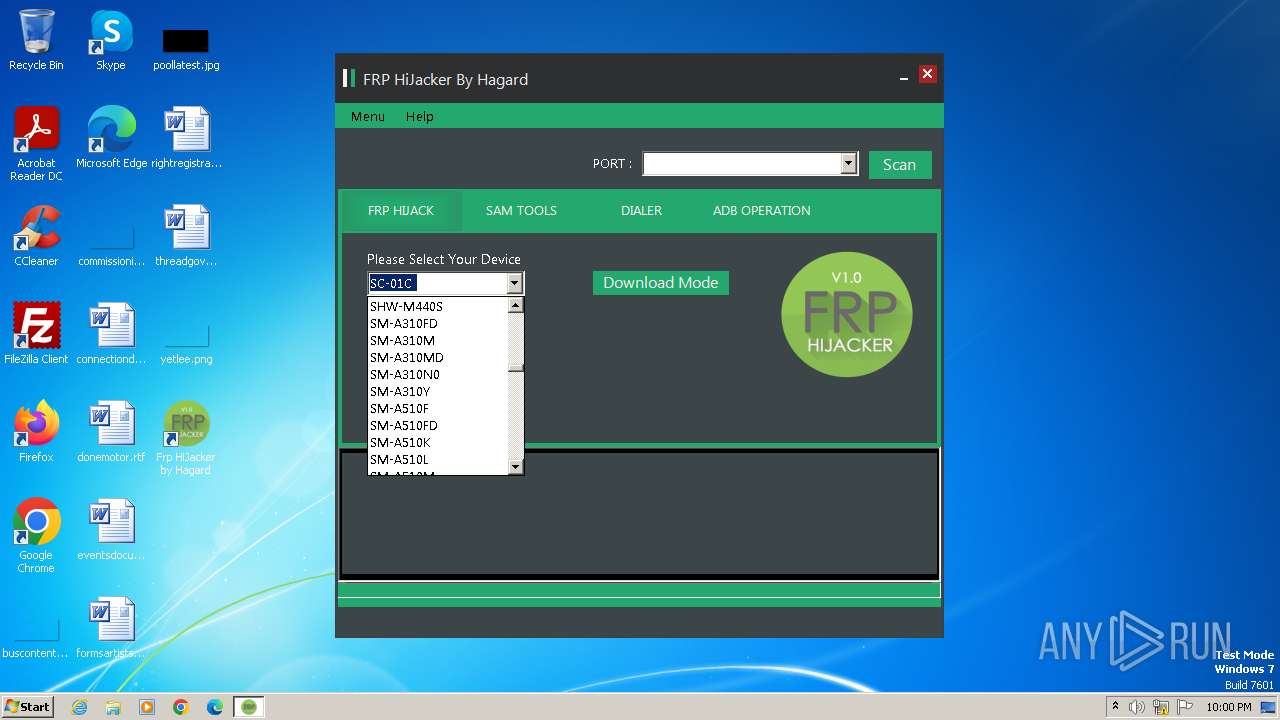
| FileDescription: | Frp HiJacker by Hagard Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | Frp HiJacker by Hagard |
| ProductVersion: | 1.0 |
Total processes
49
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\\Adb\adb.exe" devices | C:\Users\admin\AppData\Local\Temp\Adb\adb.exe | — | FRP Hijacker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 728 | "C:\Program Files\Frp HiJacker by Hagard\FRP Hijacker.exe" | C:\Program Files\Frp HiJacker by Hagard\FRP Hijacker.exe | Frp Hijacker by Hagard V1.0 setup.tmp | ||||||||||||
User: admin Company: CellularWorld Integrity Level: MEDIUM Description: FRP Hijacker Version: 1.0.0.0 Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\Temp\is-IRQN9.tmp\Frp Hijacker by Hagard V1.0 setup.tmp" /SL5="$30130,929610,100864,C:\Users\admin\AppData\Local\Temp\Frp Hijacker by Hagard V1.0 setup.exe" /SPAWNWND=$20134 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\is-IRQN9.tmp\Frp Hijacker by Hagard V1.0 setup.tmp | Frp Hijacker by Hagard V1.0 setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1024 | "C:\Users\admin\AppData\Local\Temp\Frp Hijacker by Hagard V1.0 setup.exe" /SPAWNWND=$20134 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\Frp Hijacker by Hagard V1.0 setup.exe | Frp Hijacker by Hagard V1.0 setup.tmp | ||||||||||||
User: admin Company: Gsmhagard Integrity Level: HIGH Description: Frp HiJacker by Hagard Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1640 | "C:\Users\admin\AppData\Local\Temp\\Adb\adb.exe" start-server | C:\Users\admin\AppData\Local\Temp\Adb\adb.exe | — | FRP Hijacker.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2136 | "C:\Windows\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2276 | adb fork-server server | C:\Users\admin\AppData\Local\Temp\Adb\adb.exe | — | adb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3964 | "C:\Users\admin\AppData\Local\Temp\Frp Hijacker by Hagard V1.0 setup.exe" | C:\Users\admin\AppData\Local\Temp\Frp Hijacker by Hagard V1.0 setup.exe | explorer.exe | ||||||||||||
User: admin Company: Gsmhagard Integrity Level: MEDIUM Description: Frp HiJacker by Hagard Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\is-JDL78.tmp\Frp Hijacker by Hagard V1.0 setup.tmp" /SL5="$20138,929610,100864,C:\Users\admin\AppData\Local\Temp\Frp Hijacker by Hagard V1.0 setup.exe" | C:\Users\admin\AppData\Local\Temp\is-JDL78.tmp\Frp Hijacker by Hagard V1.0 setup.tmp | — | Frp Hijacker by Hagard V1.0 setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
4 348
Read events
4 315
Write events
27
Delete events
6
Modification events
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: FC030000EEB15D9266B4DA01 | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 0815715FE0BEFB0D982C9A7B60E6897C733E40EC569474654A751EC1C3F69280 | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Frp HiJacker by Hagard\FRP Hijacker.exe | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: CBDE24B00EBB7ED3F8BB33C3D43F6521FEC98F7A058C0433F31E9AB520565F87 | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{380B9CC0-79B1-4E93-A69A-D1D6E0E3C90B}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.5 (a) | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{380B9CC0-79B1-4E93-A69A-D1D6E0E3C90B}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Frp HiJacker by Hagard | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{380B9CC0-79B1-4E93-A69A-D1D6E0E3C90B}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Frp HiJacker by Hagard\ | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{380B9CC0-79B1-4E93-A69A-D1D6E0E3C90B}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Frp HiJacker by Hagard | |||
| (PID) Process: | (1020) Frp Hijacker by Hagard V1.0 setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{380B9CC0-79B1-4E93-A69A-D1D6E0E3C90B}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
18
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Users\admin\AppData\Local\Temp\is-GCEUM.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\is-E3RLH.tmp | executable | |
MD5:74DAE2F5E1DE39283006E81FCD55A32E | SHA256:6C1B668476DDE1973AD68DE3CF8C30B497BE3AD935A3F3C4B9B25B8103CB1624 | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\is-255VA.tmp | executable | |
MD5:1735C418FDDE7B2597473DA92850397C | SHA256:2108DA7491DE3AF23848EF01A455913B7B7BBF4A76ED8373838FAB9D8DAE79E7 | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\is-U2A2Q.tmp | executable | |
MD5:74DAE2F5E1DE39283006E81FCD55A32E | SHA256:6C1B668476DDE1973AD68DE3CF8C30B497BE3AD935A3F3C4B9B25B8103CB1624 | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\FRP Hijacker.exe | executable | |
MD5:74DAE2F5E1DE39283006E81FCD55A32E | SHA256:6C1B668476DDE1973AD68DE3CF8C30B497BE3AD935A3F3C4B9B25B8103CB1624 | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\unins000.exe | executable | |
MD5:1735C418FDDE7B2597473DA92850397C | SHA256:2108DA7491DE3AF23848EF01A455913B7B7BBF4A76ED8373838FAB9D8DAE79E7 | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\is-JH8BQ.tmp | executable | |
MD5:D1159B6A57743D5EB8EC1045C05021FB | SHA256:B007BCCDC733DA270B8A96D887FB7578C78A885FA945382FBF1B52FED9483EF3 | |||
| 3964 | Frp Hijacker by Hagard V1.0 setup.exe | C:\Users\admin\AppData\Local\Temp\is-JDL78.tmp\Frp Hijacker by Hagard V1.0 setup.tmp | executable | |
MD5:B93D9B7207F7D9C02FCB9F943D73F40C | SHA256:576DA3D6C2D5EB3016D91C610EFC6BCE437BFD7BF6E8DCB81F09A4EFF450C5CA | |||
| 1024 | Frp Hijacker by Hagard V1.0 setup.exe | C:\Users\admin\AppData\Local\Temp\is-IRQN9.tmp\Frp Hijacker by Hagard V1.0 setup.tmp | executable | |
MD5:B93D9B7207F7D9C02FCB9F943D73F40C | SHA256:576DA3D6C2D5EB3016D91C610EFC6BCE437BFD7BF6E8DCB81F09A4EFF450C5CA | |||
| 1020 | Frp Hijacker by Hagard V1.0 setup.tmp | C:\Program Files\Frp HiJacker by Hagard\is-NBO46.tmp | executable | |
MD5:E9D5A4EBC40E297166605ED64E315BD0 | SHA256:8CD400DDEF8173D76C6DE69A924F60FF9DB4C80076E4C015E4C92CDD70D67D92 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |