| File name: | installer.exe |
| Full analysis: | https://app.any.run/tasks/45770fa7-b032-4749-932d-7f69c8670400 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 31, 2022, 01:18:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 93E23E5BED552C0500856641D19729A8 |
| SHA1: | 7E14CDF808DCD21D766A4054935C87C89C037445 |
| SHA256: | E4B23EBEB82594979325357CE20F14F70143D98FF49A9D5A2E6258FBFB33E555 |
| SSDEEP: | 196608:PBXWySxHnUIYfGp0N6k7jn3R655p0aRnk6bAEzV1d:pXc6rf6Q3ipdnkqAEzVf |
MALICIOUS
Drops executable file immediately after starts
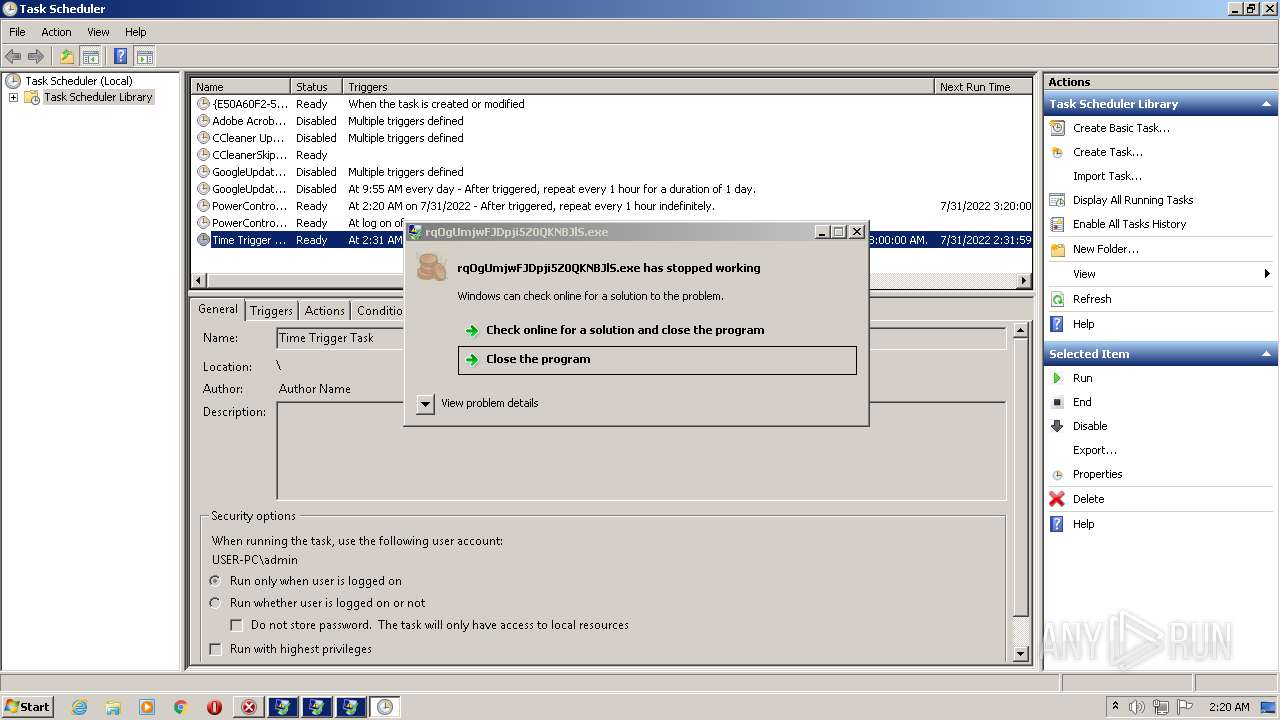
- installer.exe (PID: 1980)
- md9_1sjm.exe (PID: 3320)
- Folder.exe (PID: 2436)
- File.exe (PID: 2408)
- ZuM5UAa6rTuGUK5xwdmcwVWS.exe (PID: 1480)
- pxZfkUmYXpSR_IDEloOWbWVp.exe (PID: 4000)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- Install.exe (PID: 124900)
- YwggLDtXC7ZpnQBtZp2FRaUX.exe (PID: 122720)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
Application was dropped or rewritten from another process
- pub2.exe (PID: 2588)
- md9_1sjm.exe (PID: 3320)
- File.exe (PID: 2084)
- FoxSBrowser.exe (PID: 3564)
- File.exe (PID: 2408)
- Graphics.exe (PID: 2336)
- Updbdate.exe (PID: 3848)
- Folder.exe (PID: 2204)
- Folder.exe (PID: 2436)
- Install.exe (PID: 3844)
- Install.exe (PID: 988)
- ZuM5UAa6rTuGUK5xwdmcwVWS.exe (PID: 1480)
- pxZfkUmYXpSR_IDEloOWbWVp.exe (PID: 4000)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 2340)
- rqOgUmjwFJDpji5Z0QKNBJlS.exe (PID: 1032)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- 9UwrvAyPQQq9yb_RYqvTKMZ1.exe (PID: 3956)
- f2guGoDSo0QZFYgeQIFojEdm.exe (PID: 2896)
- ccHdrQA3kTjQFkkFF9l2O9A1.exe (PID: 3096)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- H4ndGP3BO7bJ3KovOe3qi5q1.exe (PID: 3116)
- a99OIJskZmR9o3UJFdTuxxni.exe (PID: 492)
- 5F0E43HCJ403JJH.exe (PID: 16464)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 93772)
- 6ACL0HF44JJFJ8G.exe (PID: 111144)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- build2.exe (PID: 35288)
- build2.exe (PID: 111944)
- GcVc6WW9dxQK8Ide2WT95XXl.exe (PID: 114492)
- urf41cFzXDjcSsZDkmLffF_W.exe (PID: 118772)
- UpncvBYMvYzpenOmxW6oJgf5.exe (PID: 119036)
- 7rEVGTnKtw8XpQTbVLhDUV3p.exe (PID: 117832)
- lakYeWtJYkMHujhQtUY3irSi.exe (PID: 119512)
- ZAwkM4yEBwUfVXG71V3jPxPb.exe (PID: 118492)
- YwggLDtXC7ZpnQBtZp2FRaUX.exe (PID: 122720)
- Install.exe (PID: 124900)
- Install.exe (PID: 125464)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 130220)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
Connects to CnC server
- md9_1sjm.exe (PID: 3320)
- File.exe (PID: 2408)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- AppLaunch.exe (PID: 305688)
- AppLaunch.exe (PID: 111620)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
Steals credentials from Web Browsers
- md9_1sjm.exe (PID: 3320)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- AppLaunch.exe (PID: 305688)
- AppLaunch.exe (PID: 111620)
Loads dropped or rewritten executable
- rUNdlL32.eXe (PID: 1868)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
Runs injected code in another process
- rUNdlL32.eXe (PID: 1868)
Application was injected by another process
- svchost.exe (PID: 912)
Actions looks like stealing of personal data
- md9_1sjm.exe (PID: 3320)
- H4ndGP3BO7bJ3KovOe3qi5q1.exe (PID: 3116)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- AppLaunch.exe (PID: 305688)
- AppLaunch.exe (PID: 111620)
- build2.exe (PID: 111944)
- UpncvBYMvYzpenOmxW6oJgf5.exe (PID: 119036)
REDLINE detected by memory dumps
- Updbdate.exe (PID: 3848)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
SOCELARS was detected
- File.exe (PID: 2408)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
Changes settings of System certificates
- Install.exe (PID: 988)
- File.exe (PID: 2408)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
Disables Windows Defender
- File.exe (PID: 2408)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
REDLINE was detected
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- AppLaunch.exe (PID: 305688)
- AppLaunch.exe (PID: 111620)
Modifies files in Chrome extension folder
- H4ndGP3BO7bJ3KovOe3qi5q1.exe (PID: 3116)
Changes the autorun value in the registry
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- ZAwkM4yEBwUfVXG71V3jPxPb.exe (PID: 118492)
- urf41cFzXDjcSsZDkmLffF_W.exe (PID: 118772)
Stealing of credential data
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- build2.exe (PID: 111944)
STOP was detected
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
Renames files like Ransomware
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
SUSPICIOUS
Reads the computer name
- installer.exe (PID: 1980)
- FoxSBrowser.exe (PID: 3564)
- md9_1sjm.exe (PID: 3320)
- Install.exe (PID: 3844)
- Folder.exe (PID: 2204)
- File.exe (PID: 2408)
- Folder.exe (PID: 2436)
- Updbdate.exe (PID: 3848)
- Install.exe (PID: 988)
- Graphics.exe (PID: 2336)
- IELowutil.exe (PID: 2864)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- 9UwrvAyPQQq9yb_RYqvTKMZ1.exe (PID: 3956)
- pxZfkUmYXpSR_IDEloOWbWVp.exe (PID: 4000)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- f2guGoDSo0QZFYgeQIFojEdm.exe (PID: 2896)
- a99OIJskZmR9o3UJFdTuxxni.exe (PID: 492)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- H4ndGP3BO7bJ3KovOe3qi5q1.exe (PID: 3116)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- 6ACL0HF44JJFJ8G.exe (PID: 111144)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- AppLaunch.exe (PID: 305688)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- AppLaunch.exe (PID: 111620)
- build2.exe (PID: 111944)
- 7rEVGTnKtw8XpQTbVLhDUV3p.exe (PID: 117832)
- UpncvBYMvYzpenOmxW6oJgf5.exe (PID: 119036)
- Install.exe (PID: 125464)
- lakYeWtJYkMHujhQtUY3irSi.exe (PID: 119512)
- Voglio.exe.pif (PID: 126276)
- Marito.exe.pif (PID: 126888)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
- powershell.EXE (PID: 133968)
Executable content was dropped or overwritten
- installer.exe (PID: 1980)
- md9_1sjm.exe (PID: 3320)
- Folder.exe (PID: 2436)
- File.exe (PID: 2408)
- ZuM5UAa6rTuGUK5xwdmcwVWS.exe (PID: 1480)
- pxZfkUmYXpSR_IDEloOWbWVp.exe (PID: 4000)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- YwggLDtXC7ZpnQBtZp2FRaUX.exe (PID: 122720)
- Install.exe (PID: 124900)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
Checks supported languages
- FoxSBrowser.exe (PID: 3564)
- installer.exe (PID: 1980)
- Graphics.exe (PID: 2336)
- Install.exe (PID: 3844)
- Folder.exe (PID: 2204)
- Updbdate.exe (PID: 3848)
- md9_1sjm.exe (PID: 3320)
- File.exe (PID: 2408)
- pub2.exe (PID: 2588)
- Folder.exe (PID: 2436)
- Install.exe (PID: 988)
- IELowutil.exe (PID: 2864)
- ZuM5UAa6rTuGUK5xwdmcwVWS.exe (PID: 1480)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- pxZfkUmYXpSR_IDEloOWbWVp.exe (PID: 4000)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 2340)
- 9UwrvAyPQQq9yb_RYqvTKMZ1.exe (PID: 3956)
- rqOgUmjwFJDpji5Z0QKNBJlS.exe (PID: 1032)
- f2guGoDSo0QZFYgeQIFojEdm.exe (PID: 2896)
- H4ndGP3BO7bJ3KovOe3qi5q1.exe (PID: 3116)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- a99OIJskZmR9o3UJFdTuxxni.exe (PID: 492)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- ccHdrQA3kTjQFkkFF9l2O9A1.exe (PID: 3096)
- 5F0E43HCJ403JJH.exe (PID: 16464)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- svchost.exe (PID: 912)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 93772)
- 6ACL0HF44JJFJ8G.exe (PID: 111144)
- cmd.exe (PID: 125968)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- AppLaunch.exe (PID: 305688)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- build2.exe (PID: 35288)
- AppLaunch.exe (PID: 111620)
- build2.exe (PID: 111944)
- cmd.exe (PID: 70676)
- 7rEVGTnKtw8XpQTbVLhDUV3p.exe (PID: 117832)
- ZAwkM4yEBwUfVXG71V3jPxPb.exe (PID: 118492)
- urf41cFzXDjcSsZDkmLffF_W.exe (PID: 118772)
- lakYeWtJYkMHujhQtUY3irSi.exe (PID: 119512)
- GcVc6WW9dxQK8Ide2WT95XXl.exe (PID: 114492)
- cmd.exe (PID: 122176)
- YwggLDtXC7ZpnQBtZp2FRaUX.exe (PID: 122720)
- cmd.exe (PID: 121256)
- cmd.exe (PID: 122156)
- cmd.exe (PID: 123312)
- UpncvBYMvYzpenOmxW6oJgf5.exe (PID: 119036)
- Install.exe (PID: 124900)
- Install.exe (PID: 125464)
- Voglio.exe.pif (PID: 126276)
- Marito.exe.pif (PID: 126888)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 130220)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
- cmd.exe (PID: 132660)
- cmd.exe (PID: 127804)
- powershell.EXE (PID: 133968)
Drops a file with a compile date too recent
- installer.exe (PID: 1980)
- md9_1sjm.exe (PID: 3320)
- Folder.exe (PID: 2436)
- File.exe (PID: 2408)
- ZuM5UAa6rTuGUK5xwdmcwVWS.exe (PID: 1480)
- pxZfkUmYXpSR_IDEloOWbWVp.exe (PID: 4000)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- YwggLDtXC7ZpnQBtZp2FRaUX.exe (PID: 122720)
- Install.exe (PID: 124900)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
Reads Environment values
- FoxSBrowser.exe (PID: 3564)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- AppLaunch.exe (PID: 305688)
- AppLaunch.exe (PID: 111620)
- build2.exe (PID: 111944)
Application launched itself
- Folder.exe (PID: 2204)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 2340)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- 6ACL0HF44JJFJ8G.exe (PID: 111144)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 93772)
- build2.exe (PID: 35288)
- cmd.exe (PID: 121256)
- cmd.exe (PID: 122156)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 130220)
Executed via COM
- DllHost.exe (PID: 3324)
Executed via WMI
- rUNdlL32.eXe (PID: 1868)
Adds / modifies Windows certificates
- Install.exe (PID: 988)
- File.exe (PID: 2408)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
Checks for external IP
- File.exe (PID: 2408)
- Install.exe (PID: 988)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
Creates files in the program directory
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- build2.exe (PID: 111944)
Creates a directory in Program Files
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
Searches for installed software
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
- 1Xpm9t8P6JvLmqAsGQ382Hq3.exe (PID: 756)
- KMm8qsMe1OOaJzoFMPN6fra8.exe (PID: 2580)
- 6ACL0HF44JJFJ8G.exe (PID: 125828)
- AppLaunch.exe (PID: 111620)
- AppLaunch.exe (PID: 305688)
- build2.exe (PID: 111944)
Reads CPU info
- build2.exe (PID: 111944)
Starts application with an unusual extension
- cmd.exe (PID: 122176)
- cmd.exe (PID: 123312)
Starts itself from another location
- YwggLDtXC7ZpnQBtZp2FRaUX.exe (PID: 122720)
Reads mouse settings
- Voglio.exe.pif (PID: 126276)
- Marito.exe.pif (PID: 126888)
Executed via Task Scheduler
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 130220)
- powershell.EXE (PID: 133968)
Reads the date of Windows installation
- powershell.EXE (PID: 133968)
INFO
Reads settings of System Certificates
- md9_1sjm.exe (PID: 3320)
- File.exe (PID: 2408)
- Install.exe (PID: 988)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- AppLaunch.exe (PID: 305688)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- build2.exe (PID: 111944)
- AppLaunch.exe (PID: 111620)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
Reads the computer name
- DllHost.exe (PID: 3324)
- rUNdlL32.eXe (PID: 1868)
- PING.EXE (PID: 74160)
- icacls.exe (PID: 83160)
- control.exe (PID: 118400)
- taskkill.exe (PID: 131280)
- schtasks.exe (PID: 30624)
- schtasks.exe (PID: 29188)
- mmc.exe (PID: 116464)
- tasklist.exe (PID: 123876)
- tasklist.exe (PID: 123584)
- PING.EXE (PID: 126916)
- PING.EXE (PID: 128396)
- PING.EXE (PID: 126292)
- PING.EXE (PID: 131972)
- PING.EXE (PID: 132228)
- schtasks.exe (PID: 133336)
- schtasks.exe (PID: 133668)
- gpupdate.exe (PID: 135520)
- taskkill.exe (PID: 133080)
Checks supported languages
- DllHost.exe (PID: 3324)
- rUNdlL32.eXe (PID: 1868)
- icacls.exe (PID: 83160)
- control.exe (PID: 118400)
- PING.EXE (PID: 74160)
- rundll32.exe (PID: 121016)
- taskkill.exe (PID: 131280)
- schtasks.exe (PID: 30624)
- schtasks.exe (PID: 29188)
- mmc.exe (PID: 116464)
- where.exe (PID: 120452)
- where.exe (PID: 120432)
- find.exe (PID: 123664)
- tasklist.exe (PID: 123876)
- tasklist.exe (PID: 123584)
- findstr.exe (PID: 125320)
- findstr.exe (PID: 125340)
- PING.EXE (PID: 126292)
- find.exe (PID: 124264)
- PING.EXE (PID: 126916)
- PING.EXE (PID: 128396)
- forfiles.exe (PID: 127148)
- forfiles.exe (PID: 128864)
- reg.exe (PID: 129424)
- cmd.exe (PID: 129156)
- PING.EXE (PID: 131972)
- PING.EXE (PID: 132228)
- taskkill.exe (PID: 133080)
- cmd.exe (PID: 129392)
- reg.exe (PID: 129948)
- schtasks.exe (PID: 133668)
- gpupdate.exe (PID: 135520)
- schtasks.exe (PID: 133336)
Checks Windows Trust Settings
- Install.exe (PID: 988)
- File.exe (PID: 2408)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 50372)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 171764)
- _djaCrLZmVfRDrIazTh70fLe.exe (PID: 2940)
- build2.exe (PID: 111944)
- sBz4z47HDuDIMvFa6RVn7a12.exe (PID: 28764)
- jDpm15Z_SpxNF9vyAV7nAKj4.exe (PID: 131088)
- powershell.EXE (PID: 133968)
Dropped object may contain Bitcoin addresses
- DmVSlYn0aw_CbcfEfk4qMN6G.exe (PID: 852)
Manual execution by user
- mmc.exe (PID: 115496)
- mmc.exe (PID: 116464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3848) Updbdate.exe
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
C2 (1)45.9.20.20:13441
BotnetUDP
Err_msg
Auth_value
US (117)
UNKNOWN
.
1
cmyredmyit_cmyardmys
my
as21
\
Host
Port
:
User
Pass
MANGO
Environment
%USEWanaLifeRPROFILE%\AppDaWanaLifeta\LWanaLifeocal
WanaLife
Def
Win
String.Replace
String.Remove
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
BCrypt.BCryptImportKey() failed with status code:{0}
BCrypt.BCryptGetProperty() (get size) failed with status code:{0}
BCrypt.BCryptGetProperty() failed with status code:{0}
-
net.tcp://
/
localhost
|
Yandex\YaAddon
HSUnByY9UyosMUYQIyM8GT8IOF4qAlxP
BTQgIw==
Sarring
ToString
asf
*wallet*
Atomic
\atomic
*
Binance
\Binance
*app-store*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
Collection
String
Replace
Message
BPOTE6AJI
System.UI
File.IO
Warning
Exception
string.Replace
Guarda
\Guarda
File.WriteMFile.WriteoFile.WritenFile.WriteerFile.Writeo
File.Write
StringBuilder
\MMemoryStreamonMemoryStreameMemoryStreamro\MemoryStreamwaMemoryStreamlleMemoryStreamts
MemoryStream
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
Handler
npvo*
%USERPstring.ReplaceROFILE%\Apstring.ReplacepData\Locastring.Replacel
(
UNIQUE
"
Width
Height
CopyFromScreen
kernel32
user32.dll
GetConsoleWindow
ShowWindow
SELECT * FROM Win32_Processor
Name
NumberOfCores
root\CIMV2
SELECT * FROM Win32_VideoController
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELECT * FROM Win32_DiskDrive
SerialNumber
'
FileSystem
ExecutablePath
[
]
0 Mb or 0
SELECT * FROM Win32_OperatingSystem
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
(PID) Process(756) 1Xpm9t8P6JvLmqAsGQ382Hq3.exe
C2 (1)89.39.104.85:24947
Botnet
Err_msg
Auth_value377805d7b8d0085bf33ea4323a33d720
US (162)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Pass
Port
User
Host
:
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
377805d7b8d0085bf33ea4323a33d720
Authorization
ns1
CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd
Fain
FwwvByM1ClM=
EnumerateFiles
FullName
Replace
Directory
ExpandEnvironmentVariables
Id2
Id1
Id3
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
UNIQUE
(
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
CopyFromScreen
Width
Height
|
https://api.ip.sb/ip
81
80
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
CSDVersion
ProductName
Unknown
_[
C2 (1)89.39.104.85:24947
Botnet
Err_msg
Auth_value377805d7b8d0085bf33ea4323a33d720
US (162)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Pass
Port
User
Host
:
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
377805d7b8d0085bf33ea4323a33d720
Authorization
ns1
CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd
Fain
FwwvByM1ClM=
EnumerateFiles
FullName
Replace
Directory
ExpandEnvironmentVariables
Id2
Id1
Id3
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
UNIQUE
(
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
CopyFromScreen
Width
Height
|
https://api.ip.sb/ip
81
80
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
CSDVersion
ProductName
Unknown
_[
C2 (1)89.39.104.85:24947
Botnet
Err_msg
Auth_value377805d7b8d0085bf33ea4323a33d720
US (162)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Pass
Port
User
Host
:
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
377805d7b8d0085bf33ea4323a33d720
Authorization
ns1
CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd
Fain
FwwvByM1ClM=
EnumerateFiles
FullName
Replace
Directory
ExpandEnvironmentVariables
Id2
Id1
Id3
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
UNIQUE
(
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
CopyFromScreen
Width
Height
|
https://api.ip.sb/ip
81
80
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
CSDVersion
ProductName
Unknown
_[
C2 (1)89.39.104.85:24947
Botnet
Err_msg
Auth_value377805d7b8d0085bf33ea4323a33d720
US (162)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Pass
Port
User
Host
:
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
377805d7b8d0085bf33ea4323a33d720
Authorization
ns1
CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd
Fain
FwwvByM1ClM=
EnumerateFiles
FullName
Replace
Directory
ExpandEnvironmentVariables
Id2
Id1
Id3
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
UNIQUE
(
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
CopyFromScreen
Width
Height
|
https://api.ip.sb/ip
81
80
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
CSDVersion
ProductName
Unknown
_[
(PID) Process(2580) KMm8qsMe1OOaJzoFMPN6fra8.exe
C2 (1)193.106.191.165:39482
Botnetruzki
Err_msg
Auth_value71a0558c0eea274a5bd617ea85786884
US (199)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
71a0558c0eea274a5bd617ea85786884
Authorization
ns1
DCMFCQ0dKwQPHloLDiMrBgwjN0IOHSNGDzMJCg==
Ihk4RSBFBU4=
Awns
Id3
EnumerateFiles
ExpandEnvironmentVariables
Id2
Id1
FullName
Replace
Directory
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
92ihtg1d793.01ojt3i8s
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
System.Reflection.ReflectionContext
m_ptr
m_pData
System.Reflection.RuntimeModule
clrjit.dll
__
ghpxqkw0m1wk.1thdkx9
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Process
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
C2 (1)193.106.191.165:39482
Botnetruzki
Err_msg
Auth_value71a0558c0eea274a5bd617ea85786884
US (199)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
71a0558c0eea274a5bd617ea85786884
Authorization
ns1
DCMFCQ0dKwQPHloLDiMrBgwjN0IOHSNGDzMJCg==
Ihk4RSBFBU4=
Awns
Id3
EnumerateFiles
ExpandEnvironmentVariables
Id2
Id1
FullName
Replace
Directory
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
92ihtg1d793.01ojt3i8s
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
System.Reflection.ReflectionContext
m_ptr
m_pData
System.Reflection.RuntimeModule
clrjit.dll
__
ghpxqkw0m1wk.1thdkx9
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Process
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
C2 (1)193.106.191.165:39482
Botnetruzki
Err_msg
Auth_value71a0558c0eea274a5bd617ea85786884
US (199)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
71a0558c0eea274a5bd617ea85786884
Authorization
ns1
DCMFCQ0dKwQPHloLDiMrBgwjN0IOHSNGDzMJCg==
Ihk4RSBFBU4=
Awns
Id3
EnumerateFiles
ExpandEnvironmentVariables
Id2
Id1
FullName
Replace
Directory
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
92ihtg1d793.01ojt3i8s
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
System.Reflection.ReflectionContext
m_ptr
m_pData
System.Reflection.RuntimeModule
clrjit.dll
__
ghpxqkw0m1wk.1thdkx9
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Process
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
C2 (1)193.106.191.165:39482
Botnetruzki
Err_msg
Auth_value71a0558c0eea274a5bd617ea85786884
US (199)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
71a0558c0eea274a5bd617ea85786884
Authorization
ns1
DCMFCQ0dKwQPHloLDiMrBgwjN0IOHSNGDzMJCg==
Ihk4RSBFBU4=
Awns
Id3
EnumerateFiles
ExpandEnvironmentVariables
Id2
Id1
FullName
Replace
Directory
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
92ihtg1d793.01ojt3i8s
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
System.Reflection.ReflectionContext
m_ptr
m_pData
System.Reflection.RuntimeModule
clrjit.dll
__
ghpxqkw0m1wk.1thdkx9
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Process
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
(PID) Process(125828) 6ACL0HF44JJFJ8G.exe
C2 (1)185.215.113.216:21921
BotnetLyla29.07
Err_msg
Auth_valuece5605b2c036c2c3b7bdfb23dcf5f5a2
US (165)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
String.Replace
String.Remove
net.tcp://
/
localhost
ce5605b2c036c2c3b7bdfb23dcf5f5a2
Authorization
ns1
AzsUVCsLMDYhIFEfLC0DGj4PIlM2JCYLKjMoAQ==
GicfFj41MHsjGSRU
Nosegay
Id3
EnumerateFiles
ExpandEnvironmentVariables
Id2
Id1
FullName
Replace
Directory
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
AddRange
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x1ec40 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 143360 |
| CodeSize: | 201216 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| TimeStamp: | 2020:12:01 19:00:55+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Dec-2020 18:00:55 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 01-Dec-2020 18:00:55 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000310EA | 0x00031200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70808 |
.rdata | 0x00033000 | 0x0000A612 | 0x0000A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.22174 |
.data | 0x0003E000 | 0x00023728 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.70882 |
.didat | 0x00062000 | 0x00000188 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.29825 |
.rsrc | 0x00063000 | 0x00015168 | 0x00015200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.24093 |
.reloc | 0x00079000 | 0x00002268 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.55486 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | Latin 1 / Western European | English - United States | RT_MANIFEST |
7 | 3.1586 | 482 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 3.11685 | 460 | Latin 1 / Western European | English - United States | RT_STRING |
9 | 3.11236 | 440 | Latin 1 / Western European | English - United States | RT_STRING |
10 | 2.99727 | 326 | Latin 1 / Western European | English - United States | RT_STRING |
11 | 3.2036 | 1094 | Latin 1 / Western European | English - United States | RT_STRING |
12 | 3.12889 | 358 | Latin 1 / Western European | English - United States | RT_STRING |
13 | 3.01704 | 338 | Latin 1 / Western European | English - United States | RT_STRING |
14 | 2.94627 | 266 | Latin 1 / Western European | English - United States | RT_STRING |
15 | 2.83619 | 188 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
171
Monitored processes
94
Malicious processes
38
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "C:\Users\admin\Pictures\Adobe Films\a99OIJskZmR9o3UJFdTuxxni.exe" | C:\Users\admin\Pictures\Adobe Films\a99OIJskZmR9o3UJFdTuxxni.exe | — | File.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 756 | "C:\Users\admin\Pictures\Adobe Films\1Xpm9t8P6JvLmqAsGQ382Hq3.exe" | C:\Users\admin\Pictures\Adobe Films\1Xpm9t8P6JvLmqAsGQ382Hq3.exe | File.exe | ||||||||||||
User: admin Company: Cho-Chun Huang, CH Biotech R&D Co Ltd Integrity Level: HIGH Description: Sales Department Exit code: 0 Version: 6.2.6.0 Modules
RedLine(PID) Process(756) 1Xpm9t8P6JvLmqAsGQ382Hq3.exe C2 (1)89.39.104.85:24947 Botnet Err_msg Auth_value377805d7b8d0085bf33ea4323a33d720 US (162) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN . 1 cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Network\ Pass Port User Host : cookies.sqlite String.Replace String.Remove net.tcp:// / localhost 377805d7b8d0085bf33ea4323a33d720 Authorization ns1 CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd Fain FwwvByM1ClM= EnumerateFiles FullName Replace Directory ExpandEnvironmentVariables Id2 Id1 Id3 wa l et d a t *wallet* _ T e gr am ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata \Discord\Local Storage\leveldb *.loSystem.Collections.Genericg System.Collections.Generic String string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections Microsoft\Windоws - ToString AddRange % UNIQUE ( " bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrbyte[]yptDesbyte[]troyKbyte[]ey byte[] BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob {0} gasdl94ja;sdiasdl94ja;s32 asdl94ja;s Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds asdl94jlajsd CopyFromScreen Width Height | https://api.ip.sb/ip 81 80 0.0.0.0 SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms Name NumberOfCores roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' System.Text.RegularExpressions ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion CSDVersion ProductName Unknown _[ (PID) Process(756) 1Xpm9t8P6JvLmqAsGQ382Hq3.exe C2 (1)89.39.104.85:24947 Botnet Err_msg Auth_value377805d7b8d0085bf33ea4323a33d720 US (162) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN . 1 cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Network\ Pass Port User Host : cookies.sqlite String.Replace String.Remove net.tcp:// / localhost 377805d7b8d0085bf33ea4323a33d720 Authorization ns1 CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd Fain FwwvByM1ClM= EnumerateFiles FullName Replace Directory ExpandEnvironmentVariables Id2 Id1 Id3 wa l et d a t *wallet* _ T e gr am ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata \Discord\Local Storage\leveldb *.loSystem.Collections.Genericg System.Collections.Generic String string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections Microsoft\Windоws - ToString AddRange % UNIQUE ( " bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrbyte[]yptDesbyte[]troyKbyte[]ey byte[] BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob {0} gasdl94ja;sdiasdl94ja;s32 asdl94ja;s Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds asdl94jlajsd CopyFromScreen Width Height | https://api.ip.sb/ip 81 80 0.0.0.0 SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms Name NumberOfCores roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' System.Text.RegularExpressions ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion CSDVersion ProductName Unknown _[ (PID) Process(756) 1Xpm9t8P6JvLmqAsGQ382Hq3.exe C2 (1)89.39.104.85:24947 Botnet Err_msg Auth_value377805d7b8d0085bf33ea4323a33d720 US (162) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN . 1 cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Network\ Pass Port User Host : cookies.sqlite String.Replace String.Remove net.tcp:// / localhost 377805d7b8d0085bf33ea4323a33d720 Authorization ns1 CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd Fain FwwvByM1ClM= EnumerateFiles FullName Replace Directory ExpandEnvironmentVariables Id2 Id1 Id3 wa l et d a t *wallet* _ T e gr am ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata \Discord\Local Storage\leveldb *.loSystem.Collections.Genericg System.Collections.Generic String string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections Microsoft\Windоws - ToString AddRange % UNIQUE ( " bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrbyte[]yptDesbyte[]troyKbyte[]ey byte[] BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob {0} gasdl94ja;sdiasdl94ja;s32 asdl94ja;s Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds asdl94jlajsd CopyFromScreen Width Height | https://api.ip.sb/ip 81 80 0.0.0.0 SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms Name NumberOfCores roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' System.Text.RegularExpressions ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion CSDVersion ProductName Unknown _[ (PID) Process(756) 1Xpm9t8P6JvLmqAsGQ382Hq3.exe C2 (1)89.39.104.85:24947 Botnet Err_msg Auth_value377805d7b8d0085bf33ea4323a33d720 US (162) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN . 1 cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Network\ Pass Port User Host : cookies.sqlite String.Replace String.Remove net.tcp:// / localhost 377805d7b8d0085bf33ea4323a33d720 Authorization ns1 CSUCGwsbAhsLNSheCgsOXwkLIF4JNThd Fain FwwvByM1ClM= EnumerateFiles FullName Replace Directory ExpandEnvironmentVariables Id2 Id1 Id3 wa l et d a t *wallet* _ T e gr am ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata \Discord\Local Storage\leveldb *.loSystem.Collections.Genericg System.Collections.Generic String string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections Microsoft\Windоws - ToString AddRange % UNIQUE ( " bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrbyte[]yptDesbyte[]troyKbyte[]ey byte[] BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob {0} gasdl94ja;sdiasdl94ja;s32 asdl94ja;s Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds asdl94jlajsd CopyFromScreen Width Height | https://api.ip.sb/ip 81 80 0.0.0.0 SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms Name NumberOfCores roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' System.Text.RegularExpressions ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion CSDVersion ProductName Unknown _[ | |||||||||||||||
| 852 | "C:\Users\admin\Pictures\Adobe Films\DmVSlYn0aw_CbcfEfk4qMN6G.exe" | C:\Users\admin\Pictures\Adobe Films\DmVSlYn0aw_CbcfEfk4qMN6G.exe | File.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 912 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | DllHost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1032 | "C:\Users\admin\Pictures\Adobe Films\rqOgUmjwFJDpji5Z0QKNBJlS.exe" | C:\Users\admin\Pictures\Adobe Films\rqOgUmjwFJDpji5Z0QKNBJlS.exe | File.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\Pictures\Adobe Films\ZuM5UAa6rTuGUK5xwdmcwVWS.exe" | C:\Users\admin\Pictures\Adobe Films\ZuM5UAa6rTuGUK5xwdmcwVWS.exe | File.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1868 | rUNdlL32.eXe "C:\Users\admin\AppData\Local\Temp\axhub.dll",main | C:\Windows\system32\rUNdlL32.eXe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1980 | "C:\Users\admin\Desktop\installer.exe" | C:\Users\admin\Desktop\installer.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | — | installer.exe | |||||||||||
User: admin Company: Yoko Integrity Level: MEDIUM Description: Yoko Exit code: 3221226540 Version: 35.205.10001.50000 Modules
| |||||||||||||||
Total events
66 248
Read events
65 395
Write events
837
Delete events
16
Modification events
| (PID) Process: | (1980) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1980) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1980) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1980) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2204) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2204) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2204) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2204) Folder.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3564) FoxSBrowser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FoxSBrowser_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3564) FoxSBrowser.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FoxSBrowser_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
89
Suspicious files
105
Text files
98
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 912 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 3320 | md9_1sjm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3320 | md9_1sjm.exe | C:\Users\admin\Desktop\tmp.edb | — | |
MD5:— | SHA256:— | |||
| 3320 | md9_1sjm.exe | C:\Users\admin\AppData\Local\Temp\Cab7342.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3320 | md9_1sjm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3320 | md9_1sjm.exe | C:\Users\admin\AppData\Local\Temp\Tar7343.tmp | cat | |
MD5:— | SHA256:— | |||
| 1980 | installer.exe | C:\Users\admin\Desktop\Folder.exe | executable | |
MD5:B89068659CA07AB9B39F1C580A6F9D39 | SHA256:9D225182E9A8F073E8CF1D60A8258369A394BCAE5FBC52D845D71A0FA440539C | |||
| 1980 | installer.exe | C:\Users\admin\Desktop\File.exe | executable | |
MD5:ECE476206E52016ED4E0553D05B05160 | SHA256:EBC2784E2648E4FF72F48A6251FF28EEE69003C8BD4AB604F5B43553A4140F4B | |||
| 1980 | installer.exe | C:\Users\admin\Desktop\pub2.exe | executable | |
MD5:F9D940AB072678A0226EA5E6BD98EBFA | SHA256:0BE77F05A9C4D30F2EC4F5636179F0E2F85E3F5441F5854A0872DE4F63ACEFFD | |||
| 1980 | installer.exe | C:\Users\admin\Desktop\Files.exe | executable | |
MD5:37DB6DB82813DDC8EEB42C58553DA2DE | SHA256:65302460BBDCCB8268BC6C23434BCD7D710D0E800FE11D87A1597FDEDFC2A9C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
189
DNS requests
48
Threats
208
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2408 | File.exe | GET | — | 45.133.1.182:80 | http://45.133.1.182/proxies.txt | unknown | — | — | suspicious |
2408 | File.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
2408 | File.exe | HEAD | 200 | 212.193.0.28:80 | http://212.193.0.28/load.php?pub=mixruzki | RU | — | — | suspicious |
2408 | File.exe | HEAD | 200 | 62.204.41.178:80 | http://62.204.41.178/newfile.exe | GB | — | — | suspicious |
2408 | File.exe | HEAD | 200 | 193.106.191.165:80 | http://193.106.191.165/SetupMX.exe | RU | — | — | malicious |
3320 | md9_1sjm.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6953d89e78902888 | US | compressed | 60.2 Kb | whitelisted |
2408 | File.exe | POST | 200 | 212.193.30.115:80 | http://212.193.30.115/base/api/getData.php | RU | text | 108 b | malicious |
2408 | File.exe | GET | 200 | 212.193.30.115:80 | http://212.193.30.115/base/api/statistics.php | RU | binary | 95 b | malicious |
2408 | File.exe | POST | 200 | 212.193.30.115:80 | http://212.193.30.115/base/api/getData.php | RU | text | 108 b | malicious |
2408 | File.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3564 | FoxSBrowser.exe | 35.205.61.67:443 | premium-s0ftwar3875.bar | Google Inc. | US | malicious |
3320 | md9_1sjm.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
988 | Install.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
988 | Install.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
988 | Install.exe | 184.24.77.48:80 | r3.o.lencr.org | Time Warner Cable Internet LLC | US | unknown |
988 | Install.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
2408 | File.exe | 45.133.1.107:80 | — | — | — | malicious |
2408 | File.exe | 212.193.30.115:80 | — | — | RU | malicious |
2408 | File.exe | 45.133.1.182:80 | — | — | — | suspicious |
3848 | Updbdate.exe | 45.9.20.20:13441 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
guidereviews.bar |
| malicious |
auto-repair-solutions.bar |
| whitelisted |
onepremiumstore.bar |
| malicious |
premium-s0ftwar3875.bar |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
www.listincode.com |
| whitelisted |
google.vrthcobj.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
iplogger.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3320 | md9_1sjm.exe | A Network Trojan was detected | ET TROJAN Win32/FFDroider CnC Activity M2 |
3320 | md9_1sjm.exe | A Network Trojan was detected | AV TROJAN Win32/Masson CnC Activity |
— | — | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in DNS Lookup) |
988 | Install.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
2408 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2408 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2408 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2408 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2408 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
25 ETPRO signatures available at the full report
Process | Message |
|---|---|
H4ndGP3BO7bJ3KovOe3qi5q1.exe | [DEBUGINFO][SETCRX] Chrome path = C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Secure Preferences
|
H4ndGP3BO7bJ3KovOe3qi5q1.exe | [DEBUGINFO][SETCRX] Chrome bExit = 0
|
H4ndGP3BO7bJ3KovOe3qi5q1.exe | [DEBUGINFO][SETCRX] Chrome hash = 27C382525716EC9BAD21C34AF3E41CE3C92B7CFAF9B90258BC6F84C05B622BFE
|
H4ndGP3BO7bJ3KovOe3qi5q1.exe | [DEBUGINFO][SETCRX] write json ok
|
H4ndGP3BO7bJ3KovOe3qi5q1.exe | [DEBUGINFO][SETCRX] un7zfile pluginpath = C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extensions\lfelcnpnijonhoildblmakjglenlmcic\3.21.4_0
|
H4ndGP3BO7bJ3KovOe3qi5q1.exe | [DEBUGINFO][SETCRX] write file ok
|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|