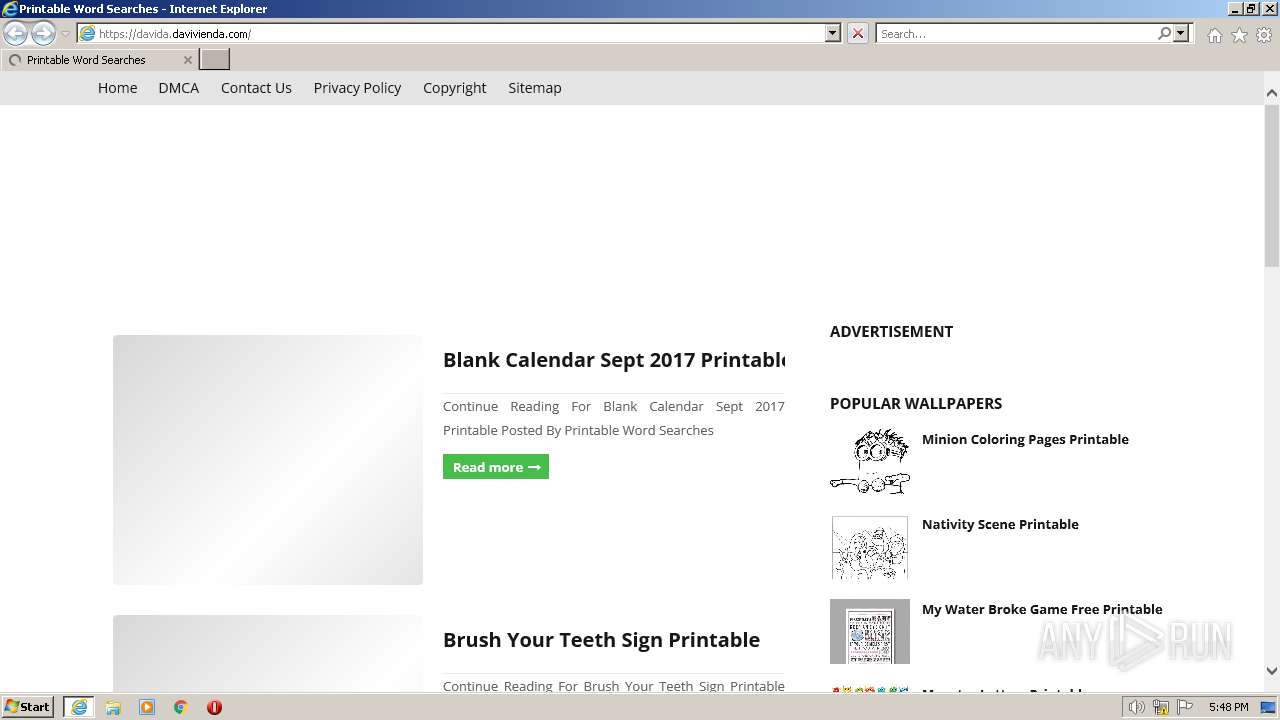
| URL: | https://davida.davivienda.com |
| Full analysis: | https://app.any.run/tasks/fd6a0012-bc71-4736-bd7f-cefdddf0966d |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2023, 16:47:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BE30617A0AC65B0DE454C210F204CE7B |
| SHA1: | 902673876CEE83835AA27B9FF660758BCA18A06B |
| SHA256: | E48F54B68E907A5A985B7A859600FA87476326F23DECA8C3C2D5C44E126DFEB5 |
| SSDEEP: | 3:N8c/TBO2:2cl |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3956)
Create files in a temporary directory
- iexplore.exe (PID: 3956)
- iexplore.exe (PID: 1924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1924 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3956 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2768 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3956 CREDAT:4134192 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3956 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://davida.davivienda.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 976
Read events
19 836
Write events
136
Delete events
4
Modification events
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
64
Text files
76
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:5391652220583D1A2F48063795A7A94B | SHA256:F5A6D3F5F55EB1967699AF981918A18ECF2235D6149D1F127C27122FAAC8008C | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:0E2E06D0744AF07C9D6121386AE69F30 | SHA256:34CE3E773496E8401E5621BC017FDB8A9AFC6D9303322A3278353E814AD539FB | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:6F0835E0B604365199EDF07D23C0C95E | SHA256:FFB634C4367A567FFFF78DC35BF1B81FF59CADFBE1907DAC97C82B26368F82C0 | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:BF678D43BBD236FD060359D91C06C924 | SHA256:7D3443A1A3482744AF95701FB202F91BCB2E28D8F0D9E6CB9CB48AA6DB1561D5 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabDE8A.tmp | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:7BED8BEDD8DD91D39A5A9AD1D5EF0504 | SHA256:B14CDD417AF890F8EDC1D0BAA8078CF3E86CA54120BA4C705DB98A418E914FB9 | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
139
DNS requests
46
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1924 | iexplore.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | — | — | whitelisted |
1924 | iexplore.exe | GET | — | 173.208.212.194:80 | http://cliparts.co/cliparts/rTj/KbG/rTjKbG9Gc.png | US | — | — | whitelisted |
1924 | iexplore.exe | GET | — | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | — | — | whitelisted |
1924 | iexplore.exe | GET | 301 | 2.16.202.66:80 | http://img1.etsystatic.com/023/0/5129215/il_570xN.491070157_twdm.jpg | NL | — | — | whitelisted |
1924 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | binary | 2.18 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEFoW3QBjIOSij34d9pz9yYA%3D | US | der | 471 b | whitelisted |
1924 | iexplore.exe | GET | 301 | 162.241.225.24:80 | http://www.theprintablecalendar.com/printable-calendar-images/september-2017-printable-calendar.gif | US | html | 308 b | suspicious |
1924 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?feed70357a64a6f6 | US | compressed | 62.3 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 23.201.254.55:80 | http://x1.c.lencr.org/ | CH | binary | 717 b | whitelisted |
3956 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1924 | iexplore.exe | 45.33.115.165:443 | davida.davivienda.com | Linode, LLC | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3388 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1924 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3956 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
1924 | iexplore.exe | 23.201.254.55:80 | x1.c.lencr.org | AKAMAI-AS | CH | unknown |
3956 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1924 | iexplore.exe | 172.217.23.106:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
davida.davivienda.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ij-scan-utility.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
stackpath.bootstrapcdn.com |
| whitelisted |
www.theprintablecalendar.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1924 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1924 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |