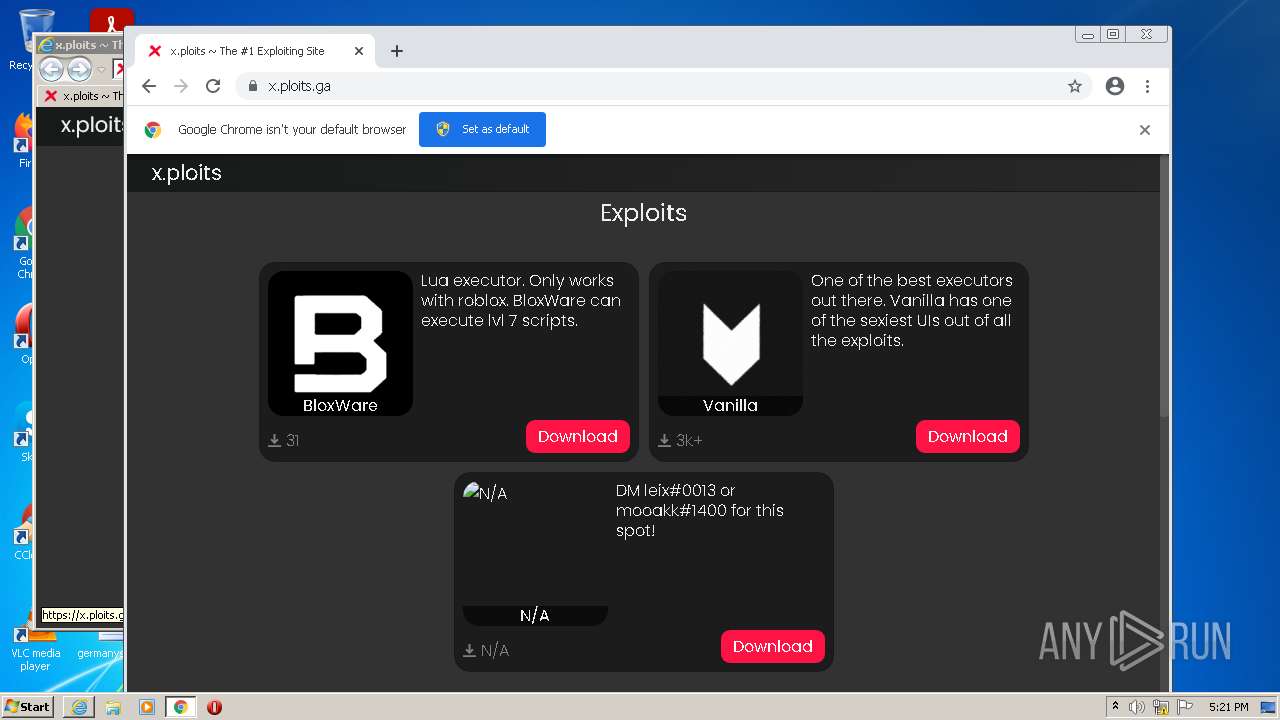
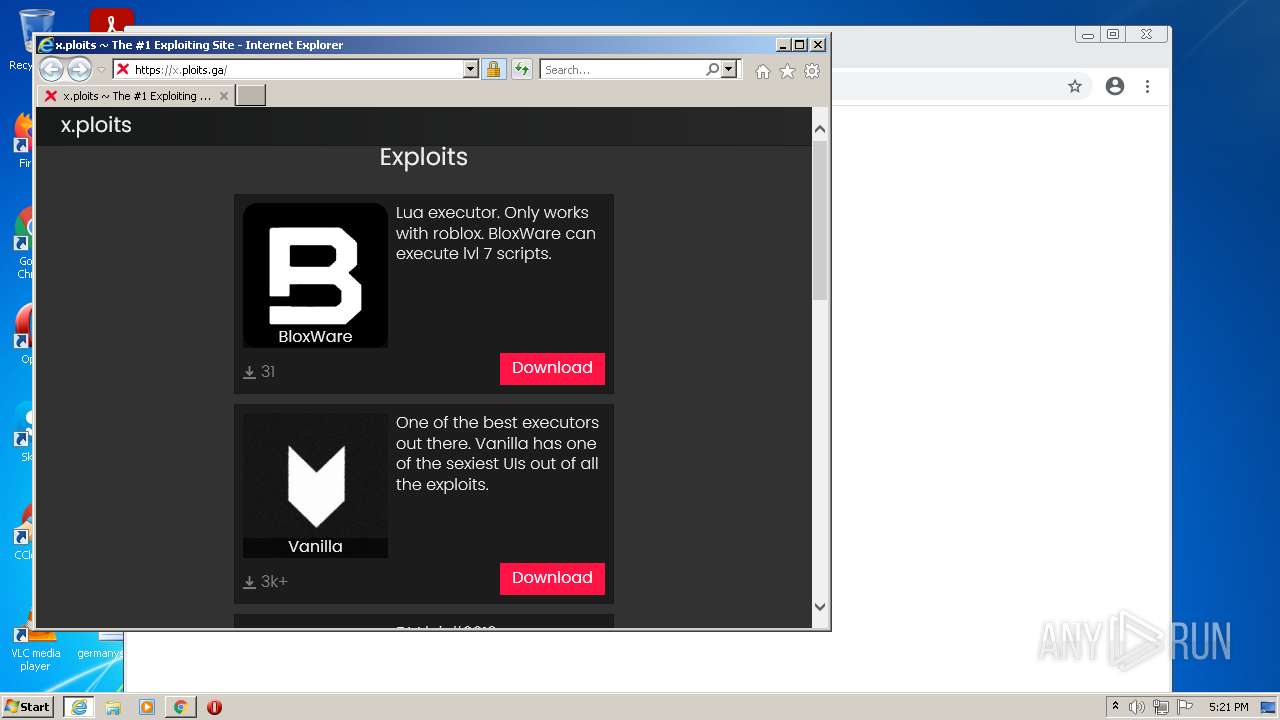
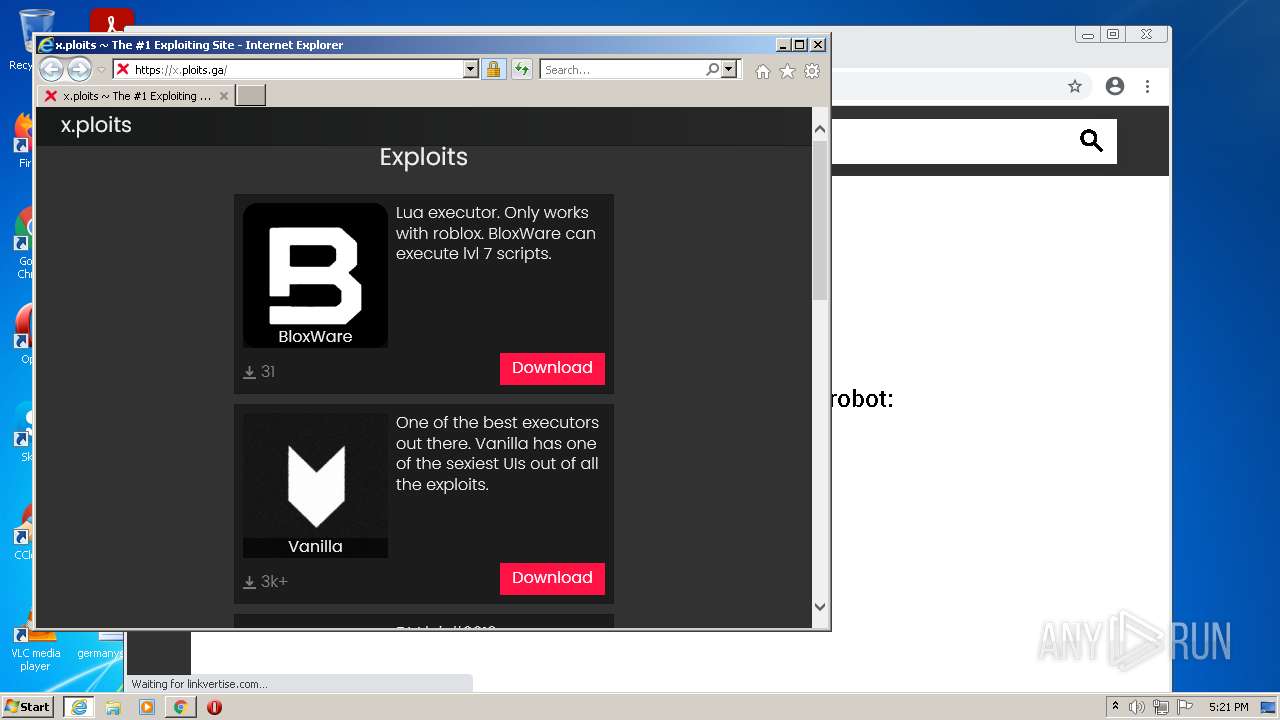
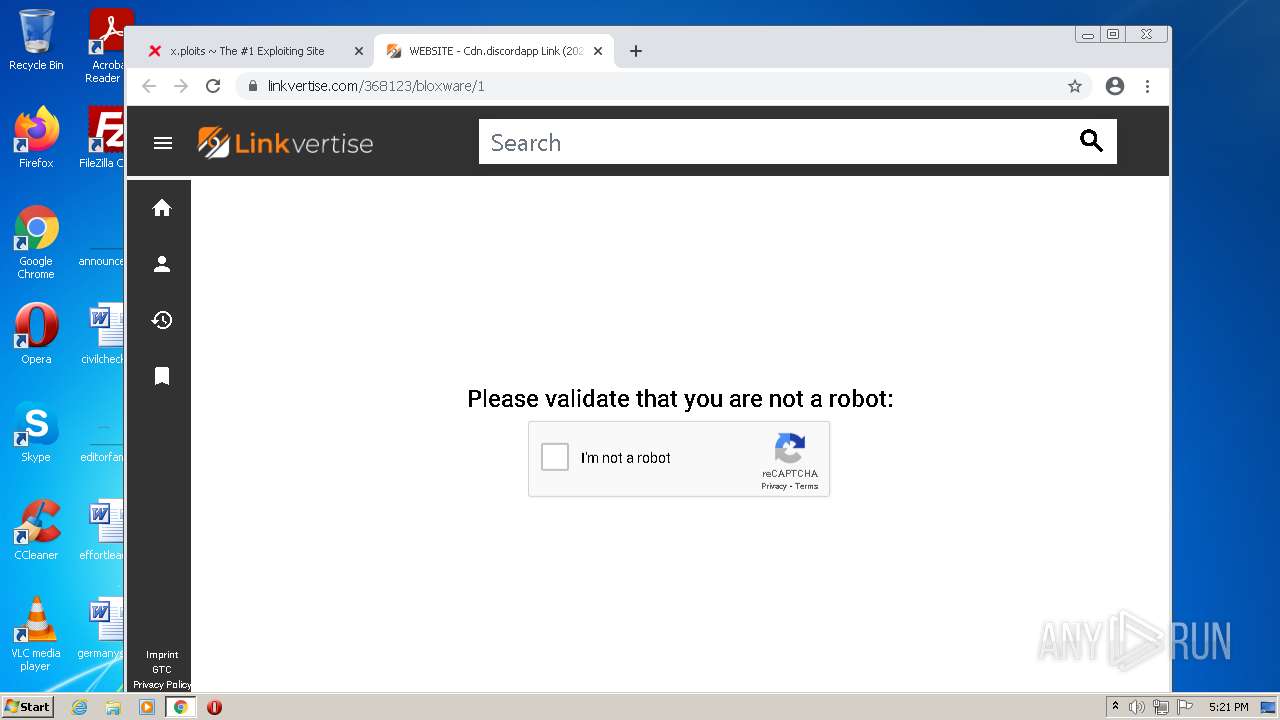
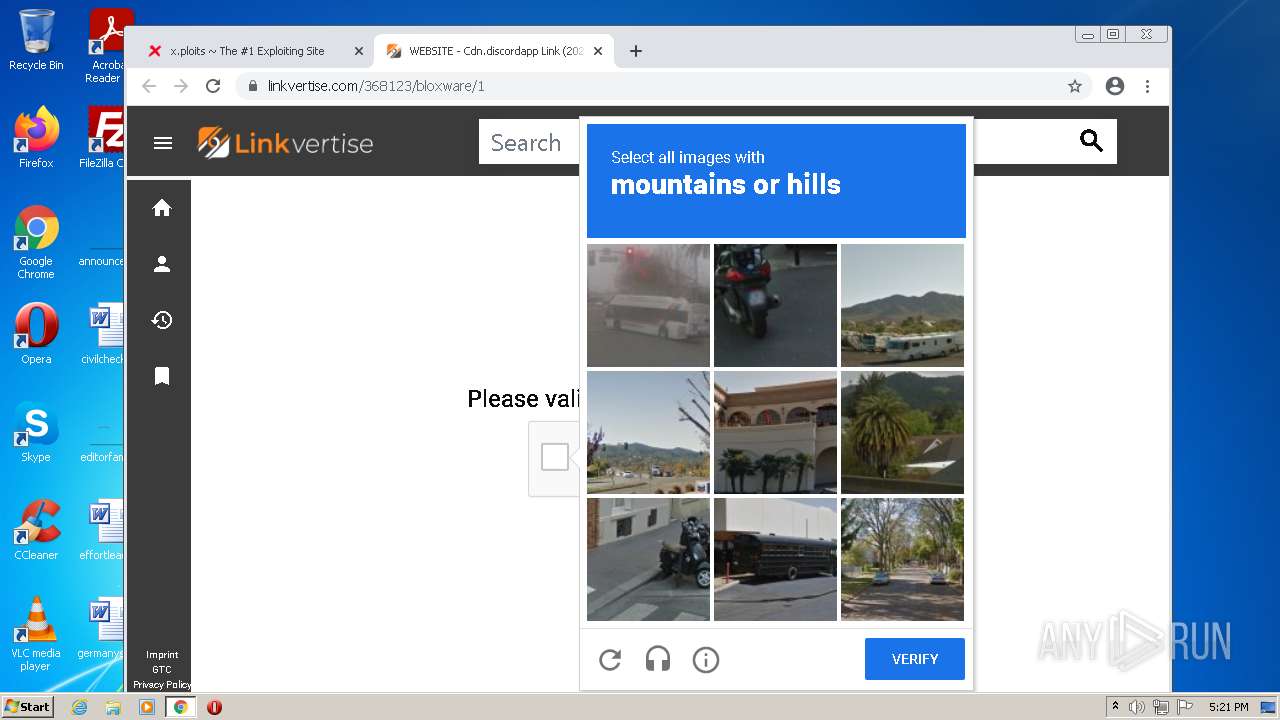
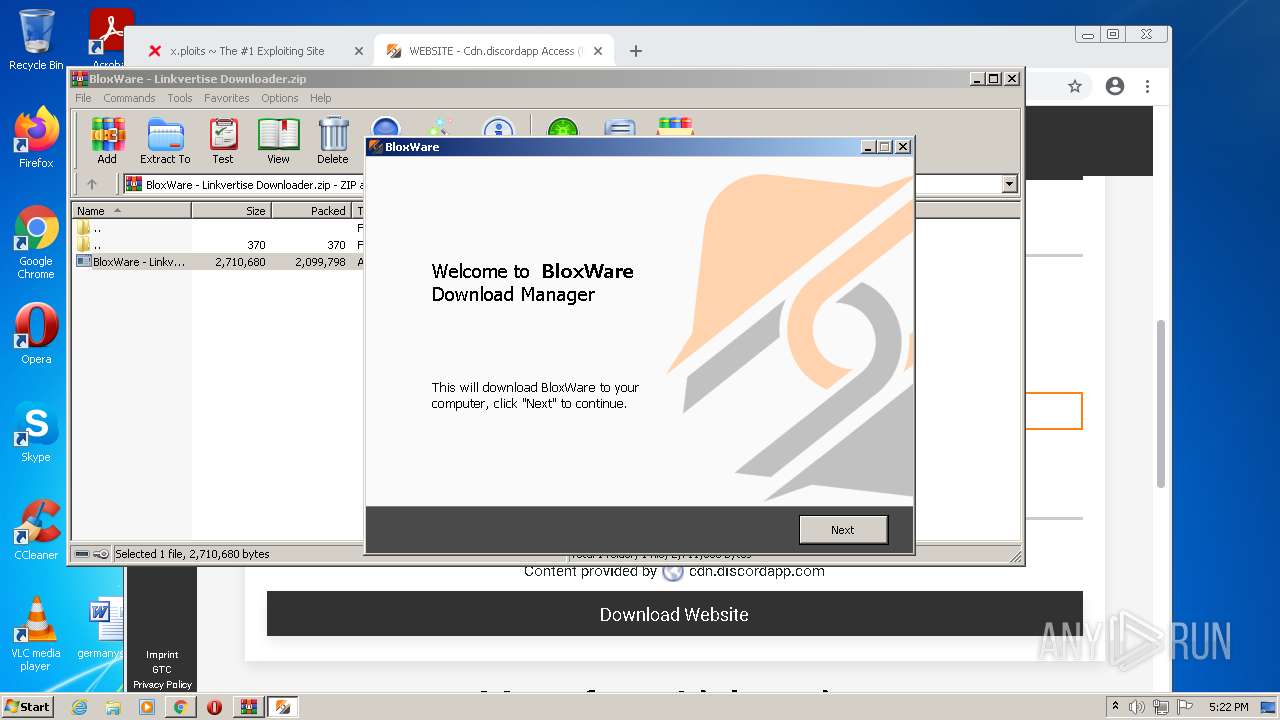
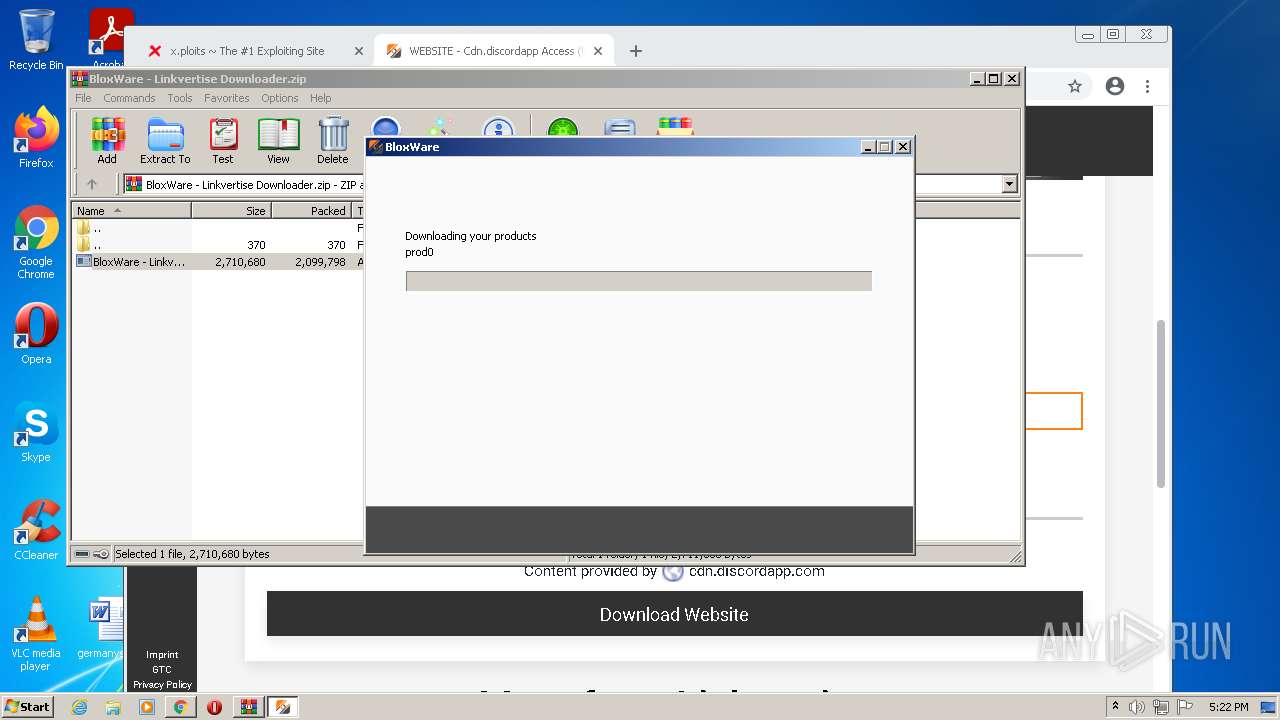
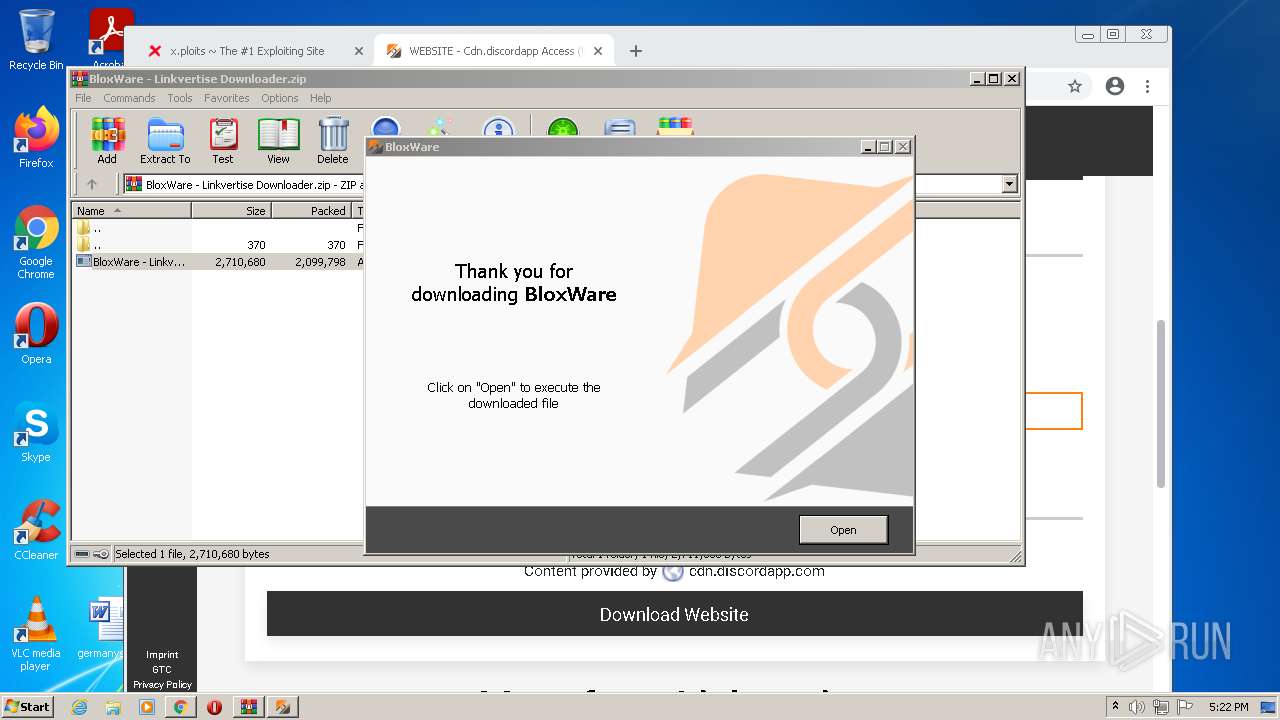
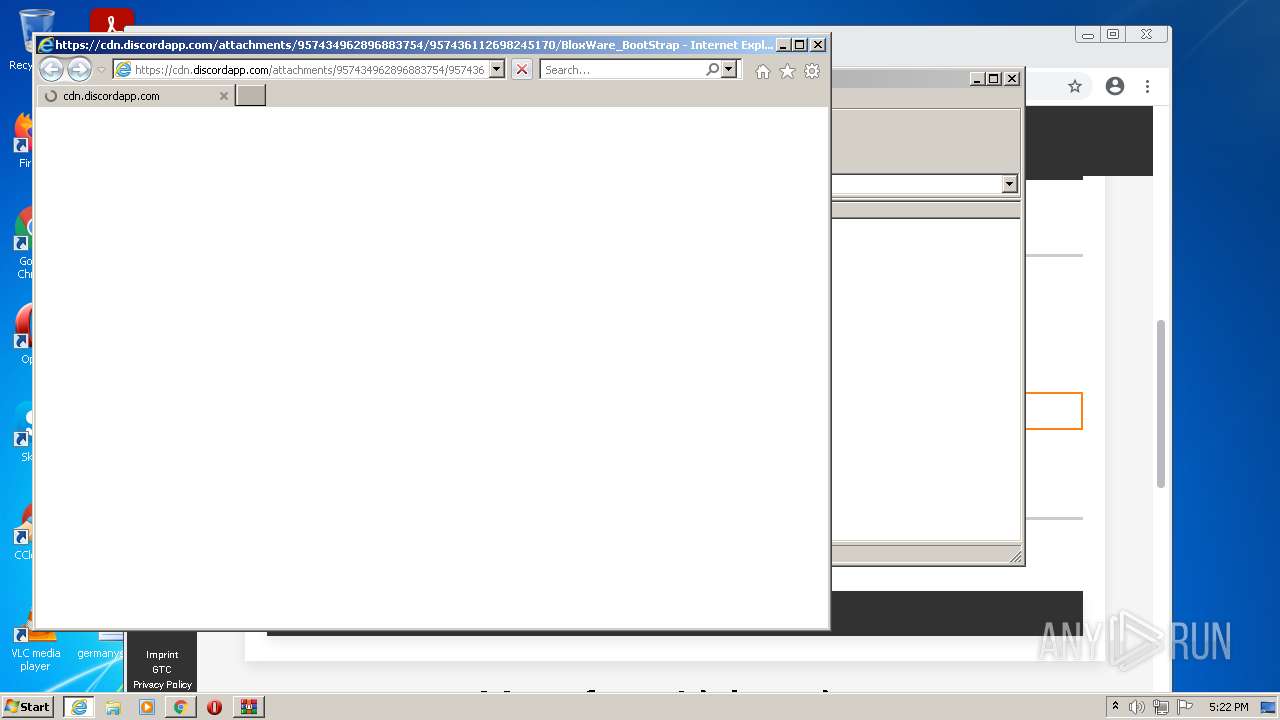
| URL: | https://x.ploits.ga/ |
| Full analysis: | https://app.any.run/tasks/01a1bf03-0668-4980-93a8-05beb814e2fe |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2022, 16:21:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 86E98CAA37DE76FF448A25D7A0F980FB |
| SHA1: | 37A1A83FB8D53D3C8BCF7EC8F036DF4701AF770A |
| SHA256: | E487C0ADDE4694CC161126C4BEC955173631D5D1BD49712B819E60E2E93F0D4F |
| SSDEEP: | 3:N8njOqn:2jt |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3212)
- WinRAR.exe (PID: 5072)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 5900)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 3988)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 1536)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- iexplore.exe (PID: 5364)
- iexplore.exe (PID: 4808)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- ndp48-web.exe (PID: 5644)
- BloxWare_BootStrapper.exe (PID: 388)
- msiexec.exe (PID: 4184)
Application was dropped or rewritten from another process
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 5900)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 3988)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 1536)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- saBSI.exe (PID: 1900)
- BloxWare_BootStrapper.exe (PID: 388)
- ndp48-web.exe (PID: 5644)
- Setup.exe (PID: 6092)
- SetupUtility.exe (PID: 4308)
- SetupUtility.exe (PID: 5512)
- BloxWare.exe (PID: 4840)
- ServiceModelReg.exe (PID: 3504)
- regtlibv12.exe (PID: 4228)
- regtlibv12.exe (PID: 3316)
- regtlibv12.exe (PID: 564)
- regtlibv12.exe (PID: 2412)
- regtlibv12.exe (PID: 5376)
- regtlibv12.exe (PID: 5080)
- regtlibv12.exe (PID: 5748)
- aspnet_regiis.exe (PID: 2884)
Changes settings of System certificates
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- saBSI.exe (PID: 1900)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- Setup.exe (PID: 6092)
Loads dropped or rewritten executable
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- Setup.exe (PID: 6092)
- SearchProtocolHost.exe (PID: 5872)
- BloxWare.exe (PID: 4840)
- BloxWare_BootStrapper.exe (PID: 388)
- svchost.exe (PID: 748)
- aspnet_regiis.exe (PID: 2884)
Changes the autorun value in the registry
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
Actions looks like stealing of personal data
- ndp48-web.exe (PID: 5644)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 884)
- iexplore.exe (PID: 5364)
Modifies files in Chrome extension folder
- chrome.exe (PID: 568)
Reads the computer name
- WinRAR.exe (PID: 5072)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 6132)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- saBSI.exe (PID: 1900)
- BloxWare_BootStrapper.exe (PID: 388)
- ndp48-web.exe (PID: 5644)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- Setup.exe (PID: 6092)
- SetupUtility.exe (PID: 4308)
- SetupUtility.exe (PID: 5512)
- TMP6E0C.tmp.exe (PID: 2324)
- BloxWare.exe (PID: 4840)
- msiexec.exe (PID: 4184)
- MsiExec.exe (PID: 5648)
- MsiExec.exe (PID: 3396)
- ServiceModelReg.exe (PID: 3504)
- mofcomp.exe (PID: 3168)
- aspnet_regiis.exe (PID: 2884)
- mofcomp.exe (PID: 3004)
- mofcomp.exe (PID: 5572)
Drops a file with a compile date too recent
- chrome.exe (PID: 3212)
- WinRAR.exe (PID: 5072)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 5900)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 3988)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 1536)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- iexplore.exe (PID: 5364)
- iexplore.exe (PID: 4808)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- ndp48-web.exe (PID: 5644)
- BloxWare_BootStrapper.exe (PID: 388)
- msiexec.exe (PID: 4184)
Executable content was dropped or overwritten
- chrome.exe (PID: 3212)
- WinRAR.exe (PID: 5072)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 5900)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 3988)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 1536)
- iexplore.exe (PID: 5364)
- iexplore.exe (PID: 4808)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- ndp48-web.exe (PID: 5644)
- BloxWare_BootStrapper.exe (PID: 388)
- TMP6E0C.tmp.exe (PID: 2324)
- Setup.exe (PID: 6092)
- msiexec.exe (PID: 4184)
Checks supported languages
- WinRAR.exe (PID: 5072)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 5900)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 6132)
- BloxWare - Linkvertise Downloader_q-HqBB1.exe (PID: 3988)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 1536)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- saBSI.exe (PID: 1900)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- BloxWare_BootStrapper.exe (PID: 388)
- ndp48-web.exe (PID: 5644)
- Setup.exe (PID: 6092)
- SetupUtility.exe (PID: 4308)
- SetupUtility.exe (PID: 5512)
- TMP6E0C.tmp.exe (PID: 2324)
- BloxWare.exe (PID: 4840)
- msiexec.exe (PID: 4184)
- MsiExec.exe (PID: 5648)
- MsiExec.exe (PID: 3396)
- ServiceModelReg.exe (PID: 3504)
- regtlibv12.exe (PID: 4228)
- regtlibv12.exe (PID: 3316)
- regtlibv12.exe (PID: 564)
- regtlibv12.exe (PID: 5376)
- regtlibv12.exe (PID: 2412)
- regtlibv12.exe (PID: 5080)
- regtlibv12.exe (PID: 5748)
- mofcomp.exe (PID: 3168)
- mofcomp.exe (PID: 5572)
- aspnet_regiis.exe (PID: 2884)
- mofcomp.exe (PID: 3004)
Reads the Windows organization settings
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- msiexec.exe (PID: 4184)
Reads Windows owner or organization settings
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- msiexec.exe (PID: 4184)
Creates files in the Windows directory
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 1536)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- msiexec.exe (PID: 4184)
- lodctr.exe (PID: 4016)
- aspnet_regiis.exe (PID: 2884)
Adds / modifies Windows certificates
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- saBSI.exe (PID: 1900)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
Creates files in the program directory
- saBSI.exe (PID: 1900)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
Searches for installed software
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
Reads Environment values
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- BloxWare_BootStrapper.exe (PID: 388)
- Setup.exe (PID: 6092)
Starts itself from another location
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
Starts Internet Explorer
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
Creates a software uninstall entry
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
Removes files from Windows directory
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- msiexec.exe (PID: 4184)
- lodctr.exe (PID: 4016)
- aspnet_regiis.exe (PID: 2884)
Reads CPU info
- Setup.exe (PID: 6092)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 4184)
- aspnet_regiis.exe (PID: 2884)
Changes the autorun value in the registry
- msiexec.exe (PID: 4184)
Checks for the .NET to be installed
- msiexec.exe (PID: 4184)
INFO
Reads settings of System Certificates
- iexplore.exe (PID: 884)
- iexplore.exe (PID: 2956)
- chrome.exe (PID: 3600)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- saBSI.exe (PID: 1900)
- iexplore.exe (PID: 5364)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- BloxWare_BootStrapper.exe (PID: 388)
- Setup.exe (PID: 6092)
- msiexec.exe (PID: 4184)
- iexplore.exe (PID: 4808)
Checks supported languages
- iexplore.exe (PID: 2956)
- iexplore.exe (PID: 884)
- chrome.exe (PID: 568)
- chrome.exe (PID: 3036)
- chrome.exe (PID: 3252)
- chrome.exe (PID: 3600)
- chrome.exe (PID: 3312)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 2388)
- chrome.exe (PID: 2172)
- chrome.exe (PID: 4064)
- chrome.exe (PID: 3708)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 3504)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 2988)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 1860)
- chrome.exe (PID: 2476)
- chrome.exe (PID: 2324)
- chrome.exe (PID: 128)
- chrome.exe (PID: 1968)
- chrome.exe (PID: 3116)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 1788)
- chrome.exe (PID: 3720)
- chrome.exe (PID: 3316)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 1060)
- chrome.exe (PID: 3772)
- chrome.exe (PID: 2236)
- chrome.exe (PID: 580)
- chrome.exe (PID: 240)
- chrome.exe (PID: 3692)
- chrome.exe (PID: 1596)
- chrome.exe (PID: 3248)
- chrome.exe (PID: 3156)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 2296)
- chrome.exe (PID: 328)
- chrome.exe (PID: 2376)
- chrome.exe (PID: 1232)
- chrome.exe (PID: 596)
- chrome.exe (PID: 2904)
- chrome.exe (PID: 5268)
- chrome.exe (PID: 4752)
- chrome.exe (PID: 5292)
- chrome.exe (PID: 5316)
- chrome.exe (PID: 876)
- chrome.exe (PID: 5492)
- chrome.exe (PID: 2284)
- chrome.exe (PID: 4500)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 4900)
- chrome.exe (PID: 4592)
- SearchProtocolHost.exe (PID: 5872)
- chrome.exe (PID: 5036)
- chrome.exe (PID: 5828)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 2716)
- chrome.exe (PID: 5756)
- chrome.exe (PID: 4356)
- iexplore.exe (PID: 4808)
- iexplore.exe (PID: 5364)
- chrome.exe (PID: 4112)
- WISPTIS.EXE (PID: 5704)
- chrome.exe (PID: 4628)
- chrome.exe (PID: 2924)
- WISPTIS.EXE (PID: 5832)
- wevtutil.exe (PID: 5372)
- wevtutil.exe (PID: 1148)
- lodctr.exe (PID: 4016)
Reads the computer name
- iexplore.exe (PID: 2956)
- chrome.exe (PID: 3252)
- iexplore.exe (PID: 884)
- chrome.exe (PID: 568)
- chrome.exe (PID: 3600)
- chrome.exe (PID: 3504)
- chrome.exe (PID: 876)
- chrome.exe (PID: 1788)
- chrome.exe (PID: 3116)
- chrome.exe (PID: 2236)
- chrome.exe (PID: 4752)
- chrome.exe (PID: 2384)
- SearchProtocolHost.exe (PID: 5872)
- chrome.exe (PID: 2716)
- iexplore.exe (PID: 5364)
- WISPTIS.EXE (PID: 5704)
- iexplore.exe (PID: 4808)
- WISPTIS.EXE (PID: 5832)
- wevtutil.exe (PID: 5372)
- wevtutil.exe (PID: 1148)
- lodctr.exe (PID: 4016)
Checks Windows Trust Settings
- iexplore.exe (PID: 884)
- iexplore.exe (PID: 2956)
- saBSI.exe (PID: 1900)
- iexplore.exe (PID: 5364)
- HotspotShield-10.22.5-hss-821-siis.exe (PID: 2444)
- HSS-10.22.5-install-hss-821-siis.exe (PID: 2644)
- Setup.exe (PID: 6092)
- msiexec.exe (PID: 4184)
- iexplore.exe (PID: 4808)
Changes internet zones settings
- iexplore.exe (PID: 2956)
- iexplore.exe (PID: 4808)
Reads the hosts file
- chrome.exe (PID: 568)
- chrome.exe (PID: 3600)
Application launched itself
- iexplore.exe (PID: 2956)
- chrome.exe (PID: 568)
- iexplore.exe (PID: 4808)
- msiexec.exe (PID: 4184)
Manual execution by user
- chrome.exe (PID: 568)
- BloxWare.exe (PID: 4840)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2956)
Reads internet explorer settings
- iexplore.exe (PID: 884)
Changes settings of System certificates
- iexplore.exe (PID: 2956)
Reads the date of Windows installation
- iexplore.exe (PID: 2956)
- chrome.exe (PID: 4752)
- iexplore.exe (PID: 4808)
Application was dropped or rewritten from another process
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 6132)
Loads dropped or rewritten executable
- BloxWare - Linkvertise Downloader_q-HqBB1.tmp (PID: 5976)
- MsiExec.exe (PID: 5648)
- MsiExec.exe (PID: 3396)
- msiexec.exe (PID: 4184)
Modifies the phishing filter of IE
- iexplore.exe (PID: 4808)
Dropped object may contain Bitcoin addresses
- Setup.exe (PID: 6092)
- svchost.exe (PID: 748)
- chrome.exe (PID: 568)
- msiexec.exe (PID: 4184)
Creates files in the user directory
- iexplore.exe (PID: 4808)
Creates a software uninstall entry
- msiexec.exe (PID: 4184)
Searches for installed software
- msiexec.exe (PID: 4184)
Creates or modifies windows services
- msiexec.exe (PID: 4184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
170
Monitored processes
106
Malicious processes
20
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,12858088905191930715,1529607696501565810,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2332 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,12858088905191930715,1529607696501565810,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5116 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,12858088905191930715,1529607696501565810,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5392 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 388 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\BloxWare_BootStrapper.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\BloxWare_BootStrapper.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Project Horizon Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 564 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorlib.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,12858088905191930715,1529607696501565810,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5052 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,12858088905191930715,1529607696501565810,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=42 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5420 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 748 | C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1016,12858088905191930715,1529607696501565810,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2760 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
122 681
Read events
110 311
Write events
12 234
Delete events
136
Modification events
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30955712 | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30955712 | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1 915
Suspicious files
367
Text files
574
Unknown types
53
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6266CA7E-238.pma | — | |
MD5:— | SHA256:— | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9821.tmp | cat | |
MD5:— | SHA256:— | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9820.tmp | compressed | |
MD5:— | SHA256:— | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9833.tmp | cat | |
MD5:— | SHA256:— | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9832.tmp | compressed | |
MD5:— | SHA256:— | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 884 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
318
DNS requests
226
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | — | — | whitelisted |
884 | iexplore.exe | GET | — | 142.250.184.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | — | — | whitelisted |
884 | iexplore.exe | GET | 200 | 184.24.77.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgT2A3UAZacFqtvZWaq%2FaUoyRQ%3D%3D | US | der | 503 b | shared |
884 | iexplore.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?451cebcf8c116463 | US | compressed | 59.5 Kb | whitelisted |
884 | iexplore.exe | GET | 200 | 184.24.77.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgRvXEsJ%2BkRba2kCxedwTYQzOQ%3D%3D | US | der | 503 b | shared |
884 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGw1Yik%2BBw9wCsFmPcXqpzQ%3D | US | der | 471 b | whitelisted |
2956 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | binary | 9.70 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | binary | 9.69 Kb | whitelisted |
3600 | chrome.exe | GET | 200 | 192.124.249.24:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
884 | iexplore.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
2956 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3600 | chrome.exe | 142.250.74.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3600 | chrome.exe | 142.250.185.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
3600 | chrome.exe | 142.250.184.193:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3600 | chrome.exe | 142.250.74.196:443 | www.google.com | Google Inc. | US | whitelisted |
884 | iexplore.exe | 184.24.77.48:80 | r3.o.lencr.org | Time Warner Cable Internet LLC | US | unknown |
3600 | chrome.exe | 142.250.185.77:443 | accounts.google.com | Google Inc. | US | suspicious |
884 | iexplore.exe | 142.250.184.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3600 | chrome.exe | 142.250.185.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
x.ploits.ga |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.ga) in TLS SNI |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
884 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
2956 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
2956 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-KQUJN.tmp\prod1_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-KQUJN.tmp\prod1_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-KQUJN.tmp\prod1_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-KQUJN.tmp\prod1_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-KQUJN.tmp\prod1_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-KQUJN.tmp\prod1_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|