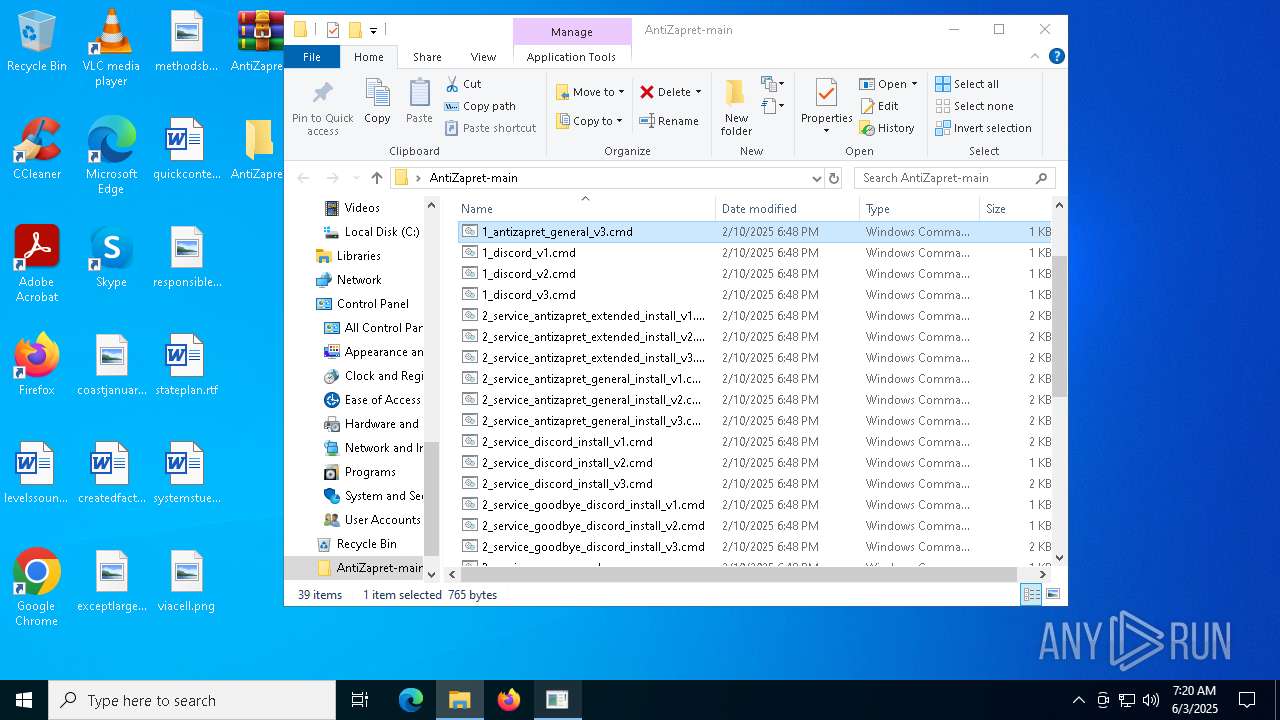
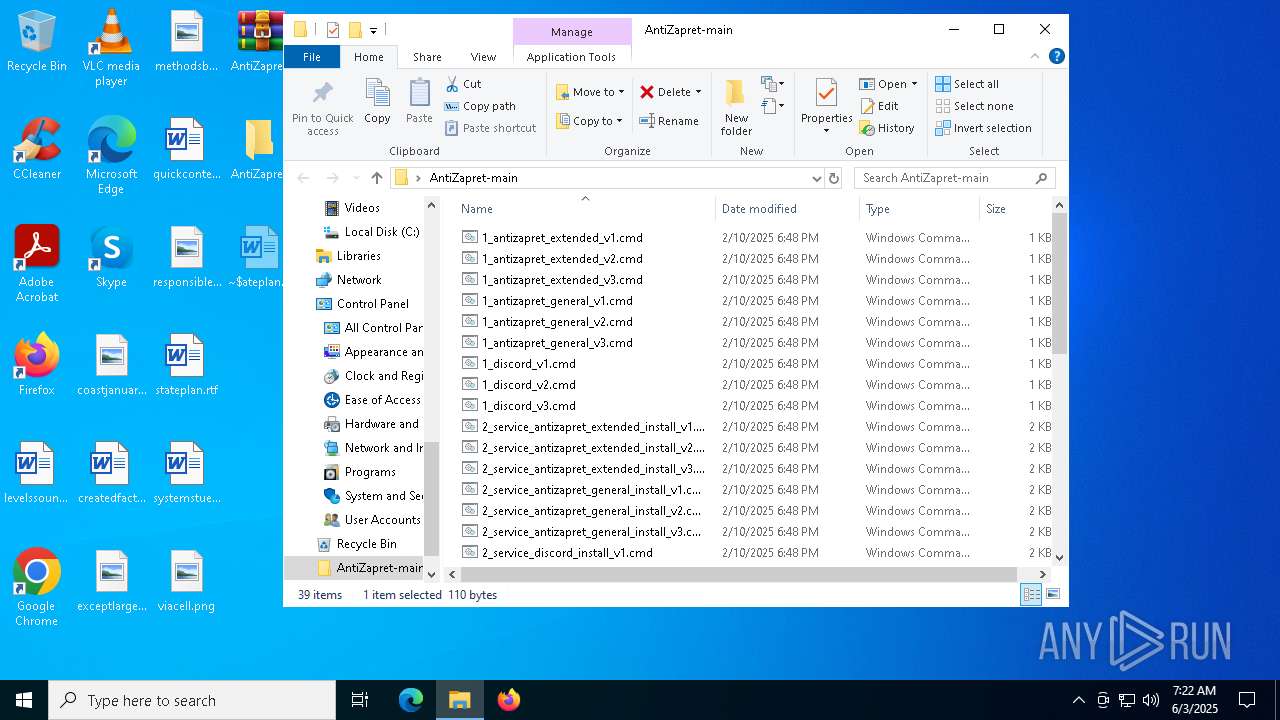
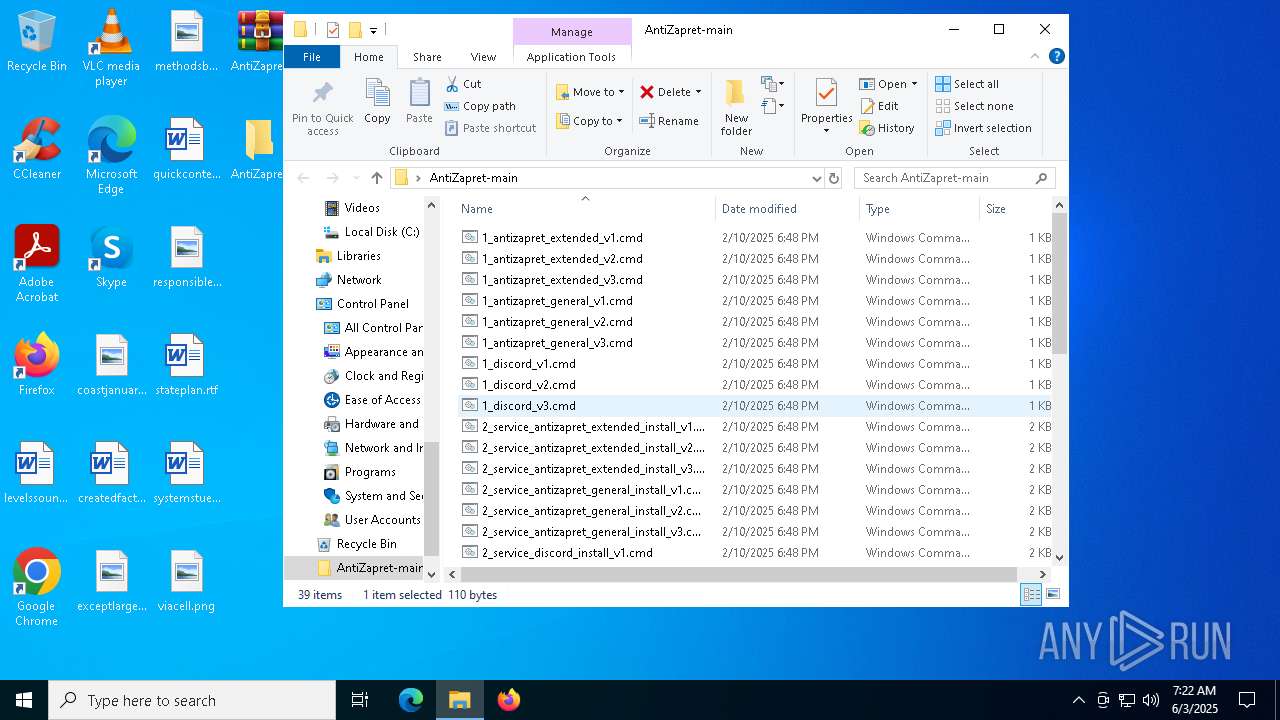
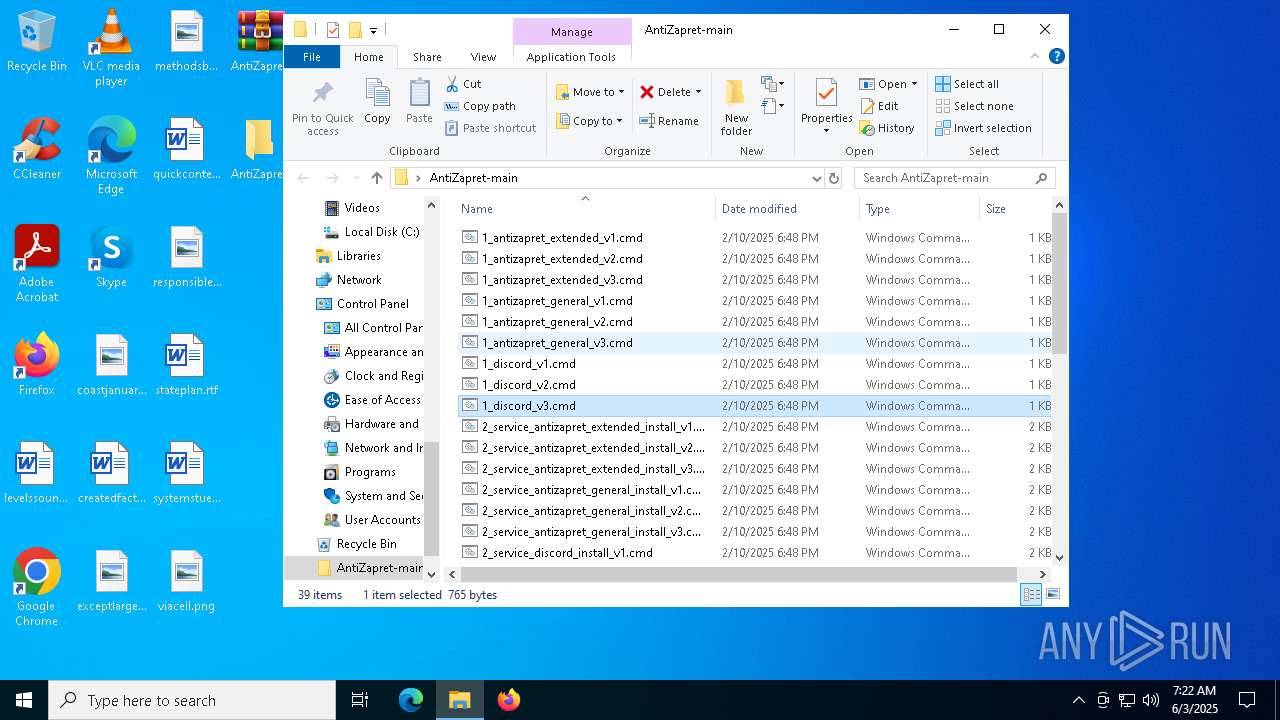
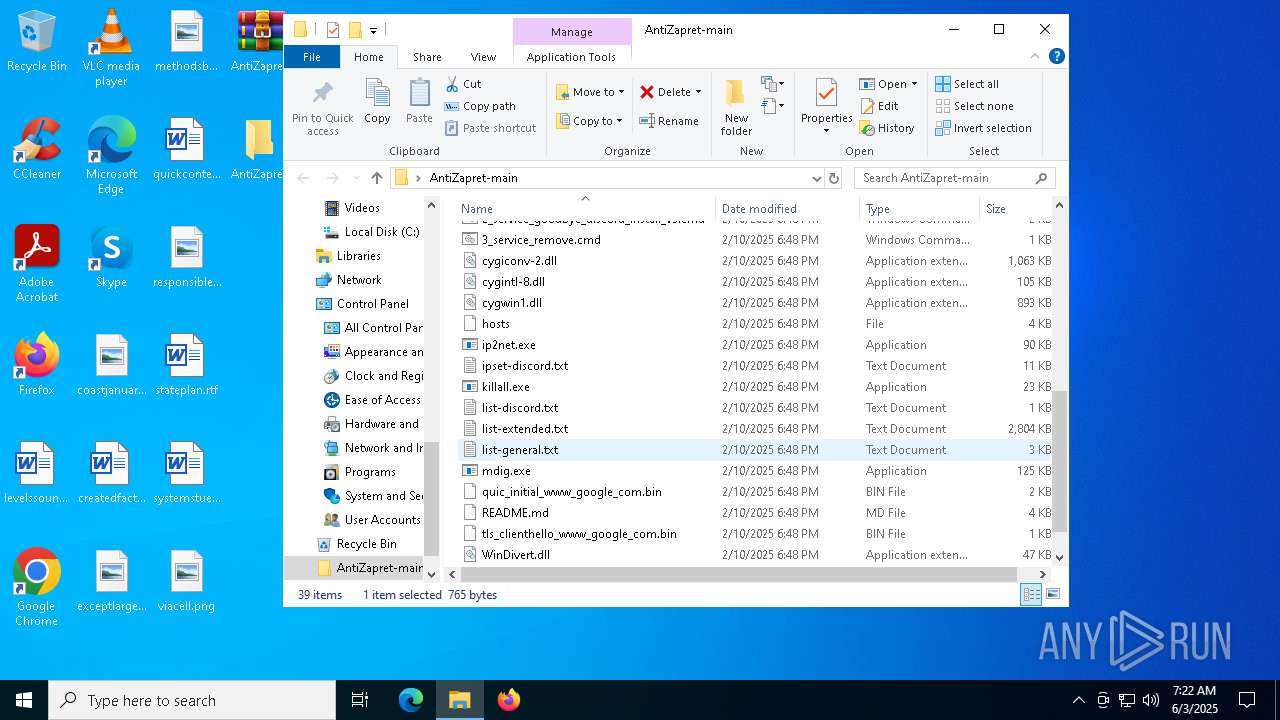
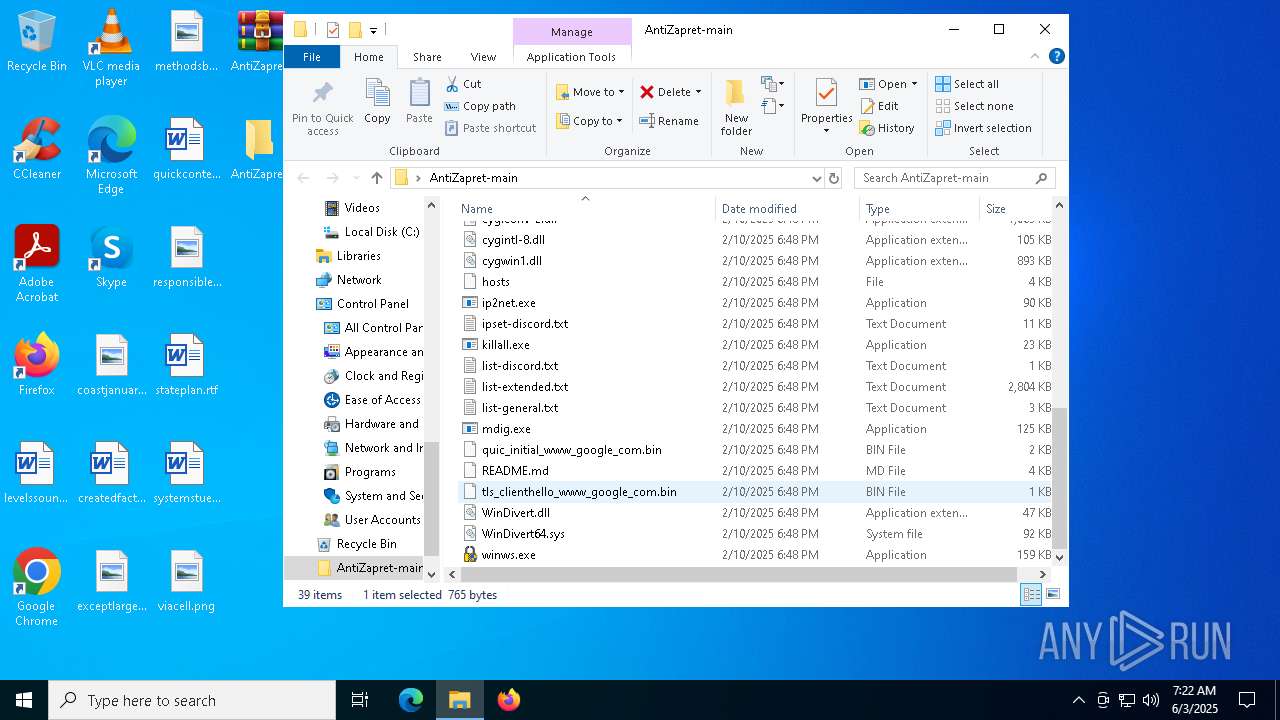
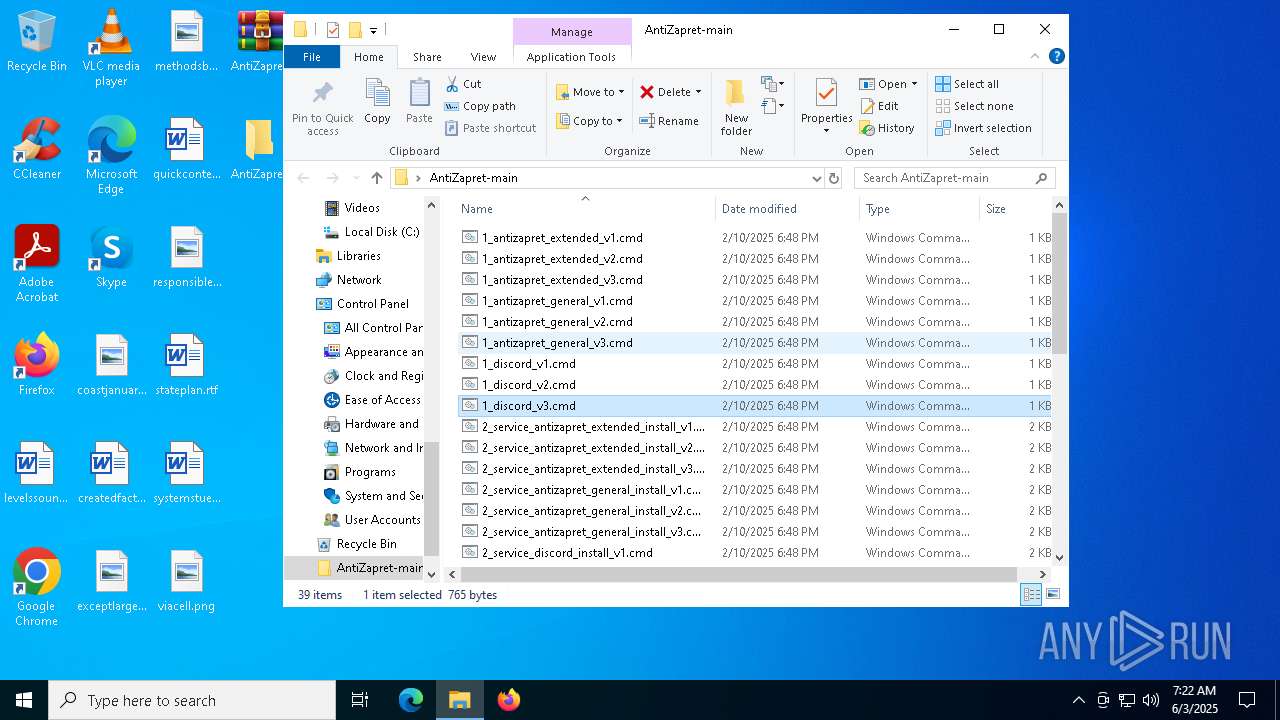
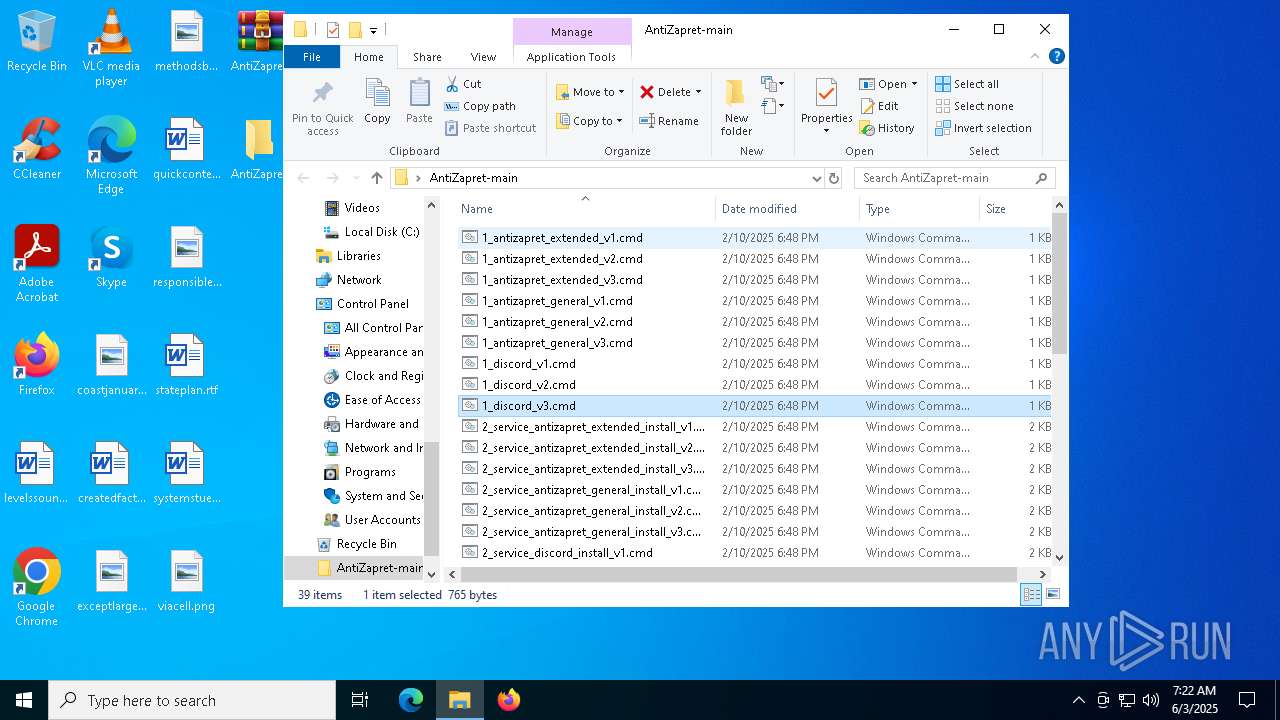
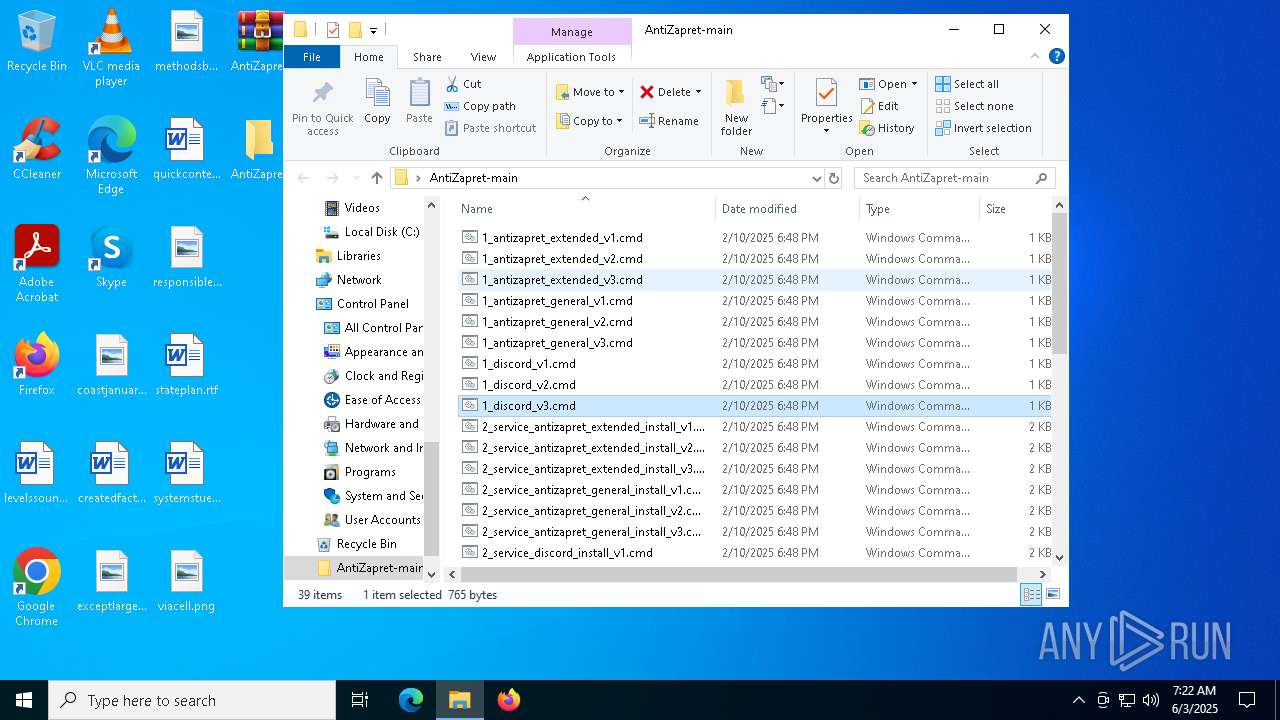
| File name: | AntiZapret-main.zip |
| Full analysis: | https://app.any.run/tasks/ce4c8edd-e48e-4b1e-9dfe-ebb37168635a |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2025, 07:20:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 98DFF4C351D71ED6F61C220435EDAE87 |
| SHA1: | A3D895FB8D51BC6A792B7509E695292B539E6ED7 |
| SHA256: | E4796F39ACD77E0CB3FE79F24D2AE6C599571FE9EBCBC1378B1427EAB06C0273 |
| SSDEEP: | 98304:KsqAZEcMug/1wWNWBKKBgD9fZ+WSMIEZBh4zXBNEmIfC81YudWUCeQ4Sm/7yc8Cp:yGvGV6g |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 7724)
Malicious driver has been detected
- WinRAR.exe (PID: 7724)
Starts NET.EXE for service management
- cmd.exe (PID: 6132)
- net.exe (PID: 7788)
SUSPICIOUS
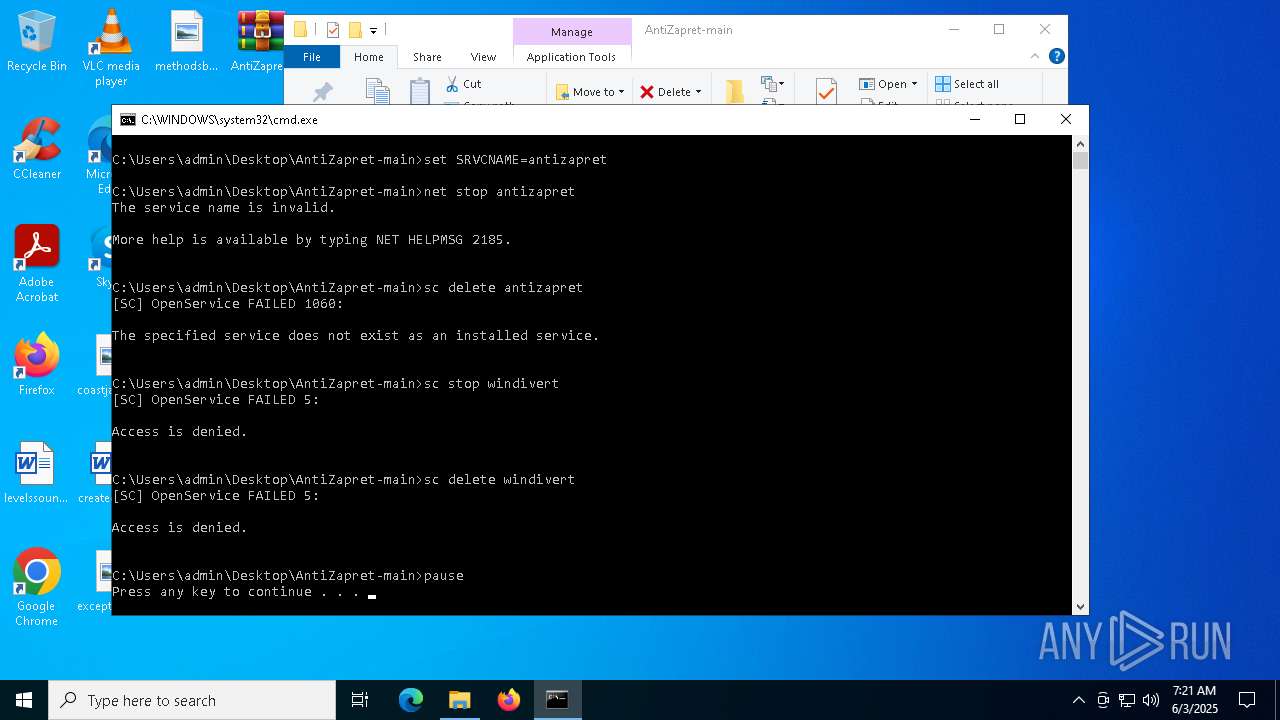
Stops a currently running service
- sc.exe (PID: 7348)
Windows service management via SC.EXE
- sc.exe (PID: 7268)
- sc.exe (PID: 8172)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7724)
Starts SC.EXE for service management
- cmd.exe (PID: 6132)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7724)
Checks supported languages
- winws.exe (PID: 3996)
- winws.exe (PID: 6496)
Manual execution by a user
- cmd.exe (PID: 6132)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 6028)
- WINWORD.EXE (PID: 7832)
The sample compiled with english language support
- WinRAR.exe (PID: 7724)
UPX packer has been detected
- winws.exe (PID: 6496)
- winws.exe (PID: 3996)
Reads the computer name
- winws.exe (PID: 3996)
- winws.exe (PID: 6496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:10 10:48:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | AntiZapret-main/ |
Total processes
160
Monitored processes
28
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
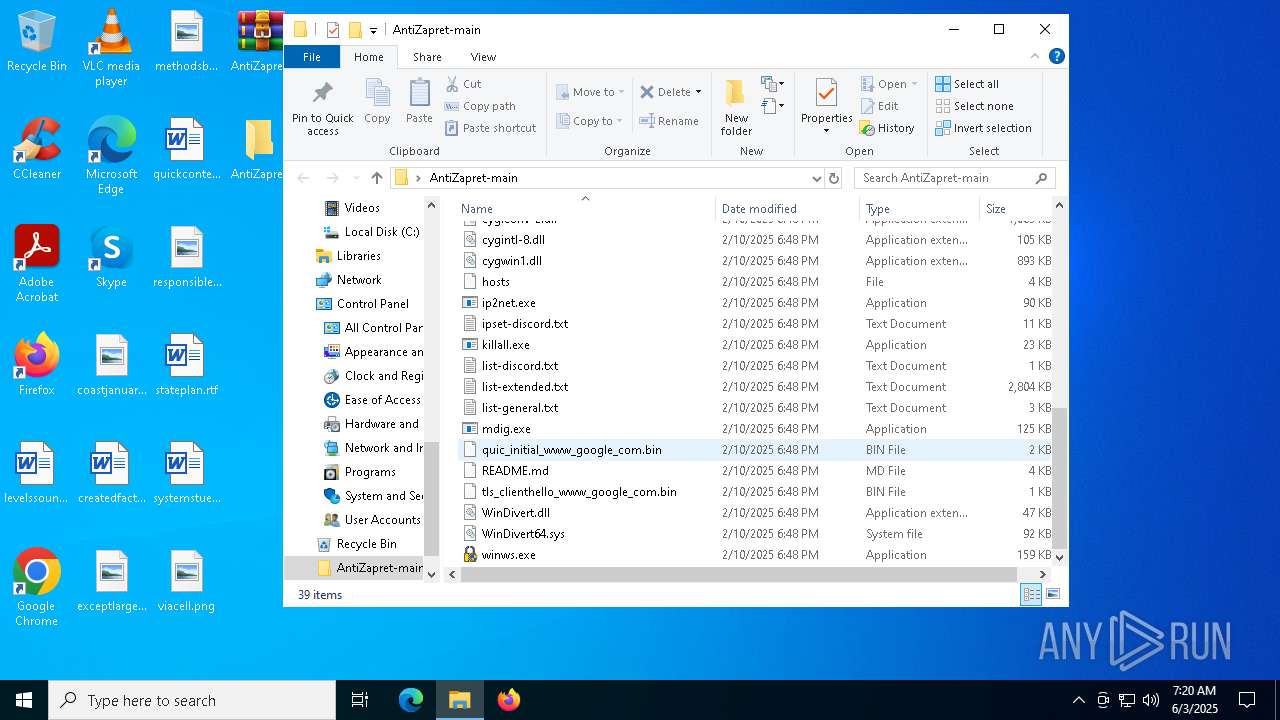
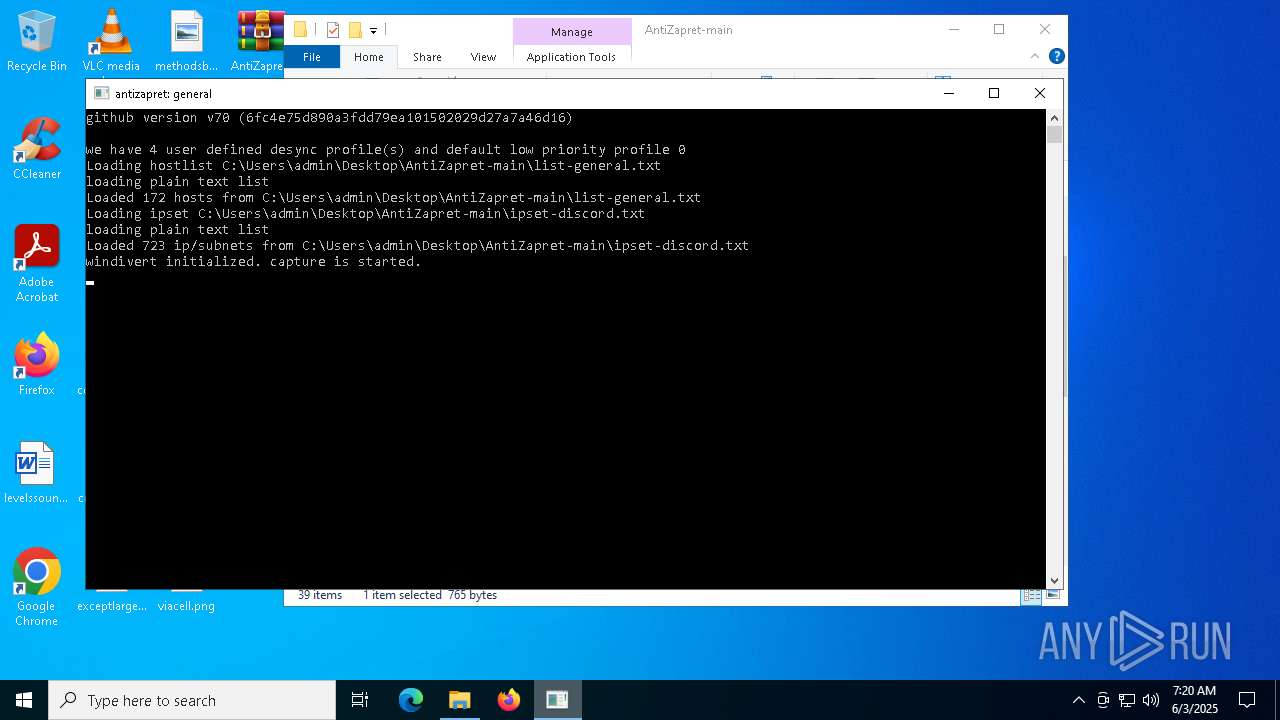
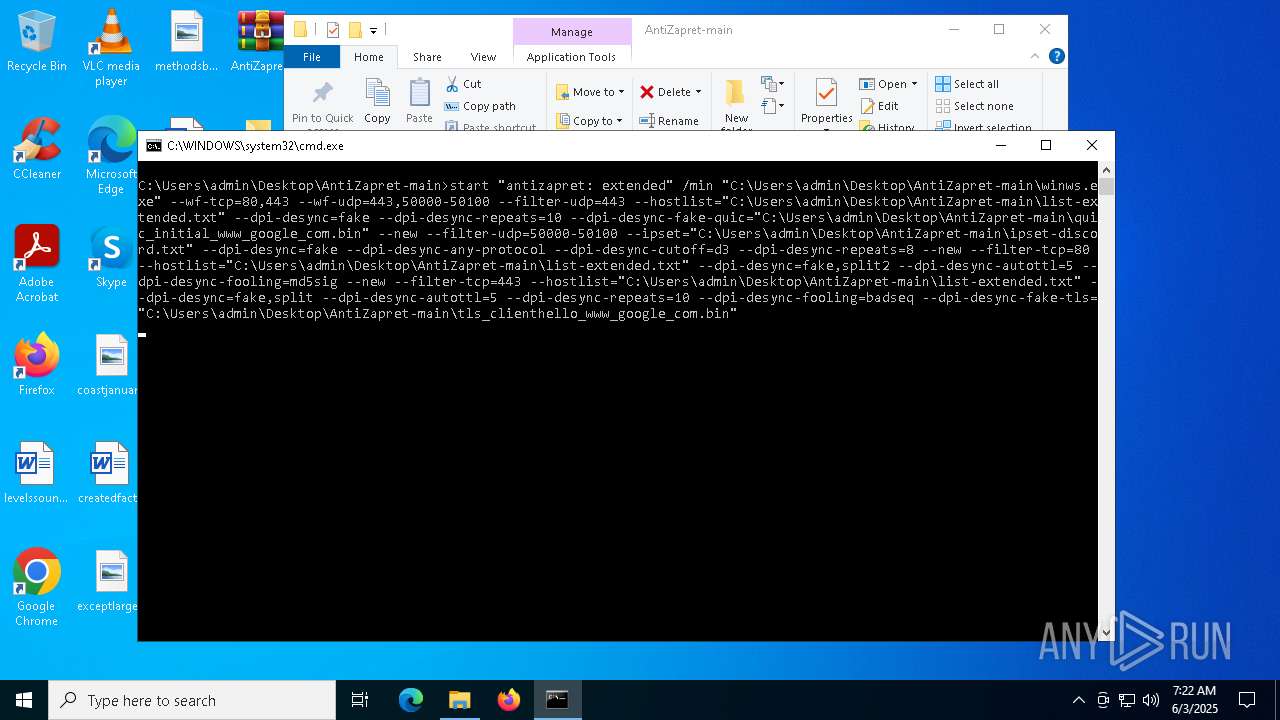
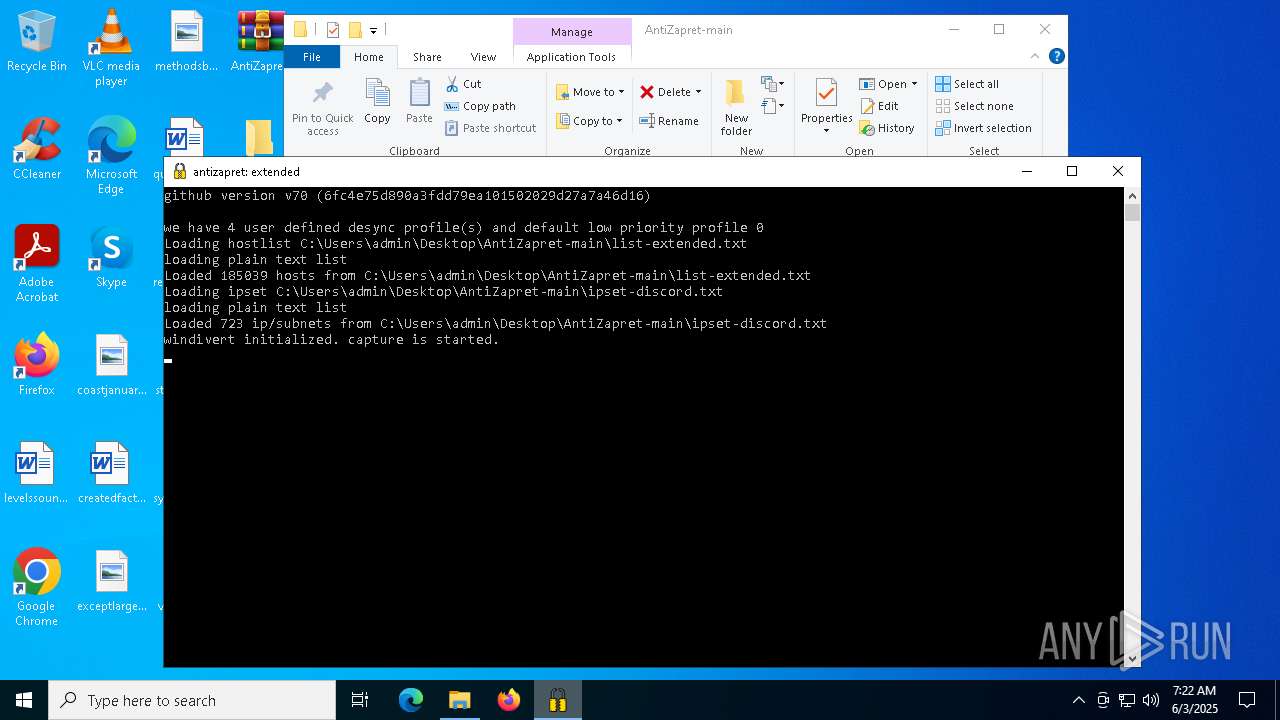
| 680 | "C:\Users\admin\Desktop\AntiZapret-main\winws.exe" --wf-tcp=80,443 --wf-udp=443,50000-50100 --filter-udp=443 --hostlist="C:\Users\admin\Desktop\AntiZapret-main\list-extended.txt" --dpi-desync=fake --dpi-desync-repeats=10 --dpi-desync-fake-quic="C:\Users\admin\Desktop\AntiZapret-main\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --ipset="C:\Users\admin\Desktop\AntiZapret-main\ipset-discord.txt" --dpi-desync=fake --dpi-desync-any-protocol --dpi-desync-cutoff=d3 --dpi-desync-repeats=8 --new --filter-tcp=80 --hostlist="C:\Users\admin\Desktop\AntiZapret-main\list-extended.txt" --dpi-desync=fake,split2 --dpi-desync-autottl=5 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Desktop\AntiZapret-main\list-extended.txt" --dpi-desync=fake,split --dpi-desync-autottl=5 --dpi-desync-repeats=10 --dpi-desync-fooling=badseq --dpi-desync-fake-tls="C:\Users\admin\Desktop\AntiZapret-main\tls_clienthello_www_google_com.bin" | C:\Users\admin\Desktop\AntiZapret-main\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3996 | "C:\Users\admin\Desktop\AntiZapret-main\winws.exe" --wf-tcp=80,443 --wf-udp=443,50000-50100 --filter-udp=443 --hostlist="C:\Users\admin\Desktop\AntiZapret-main\list-general.txt" --dpi-desync=fake --dpi-desync-repeats=10 --dpi-desync-fake-quic="C:\Users\admin\Desktop\AntiZapret-main\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --ipset="C:\Users\admin\Desktop\AntiZapret-main\ipset-discord.txt" --dpi-desync=fake --dpi-desync-any-protocol --dpi-desync-cutoff=d3 --dpi-desync-repeats=8 --new --filter-tcp=80 --hostlist="C:\Users\admin\Desktop\AntiZapret-main\list-general.txt" --dpi-desync=fake,split2 --dpi-desync-autottl=5 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Desktop\AntiZapret-main\list-general.txt" --dpi-desync=fake,split --dpi-desync-autottl=5 --dpi-desync-repeats=10 --dpi-desync-fooling=badseq --dpi-desync-fake-tls="C:\Users\admin\Desktop\AntiZapret-main\tls_clienthello_www_google_com.bin" | C:\Users\admin\Desktop\AntiZapret-main\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 4120 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\AntiZapret-main\1_antizapret_general_v3.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winws.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winws.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\AntiZapret-main\1_antizapret_extended_v3.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6028 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\AntiZapret-main\1_antizapret_extended_v3.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 157
Read events
7 040
Write events
96
Delete events
21
Modification events
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AntiZapret-main.zip | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (7724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
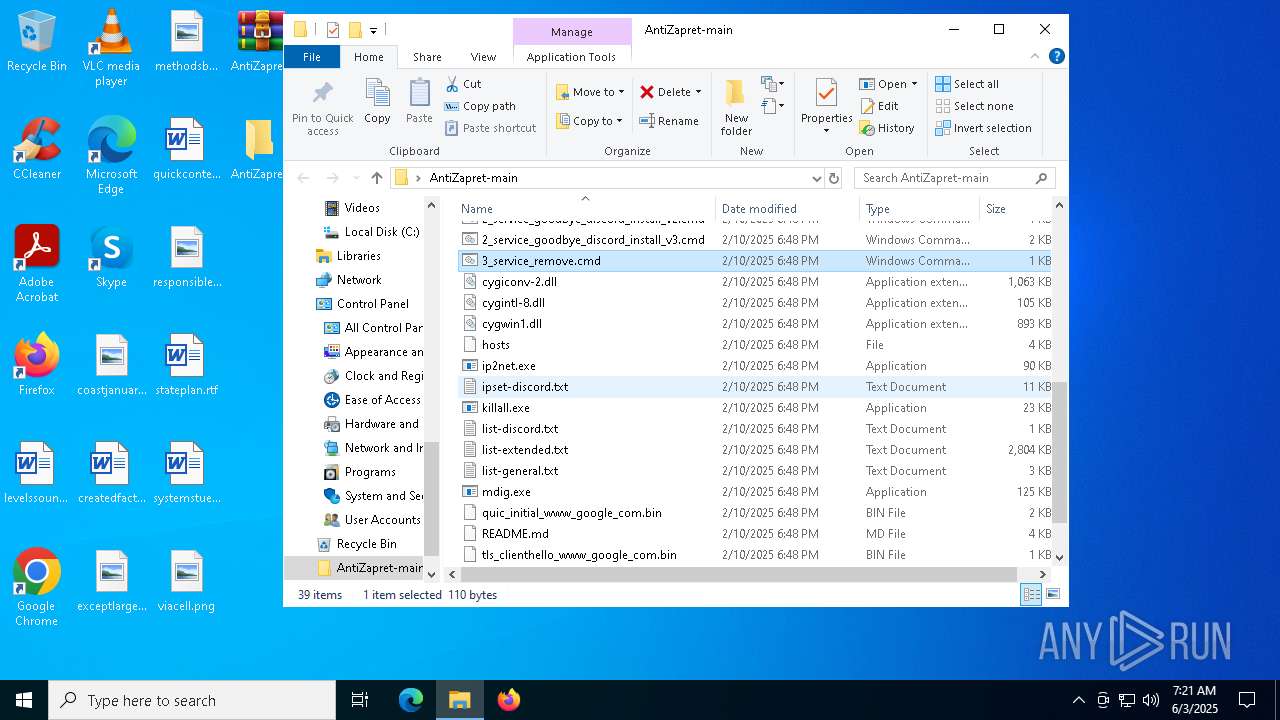
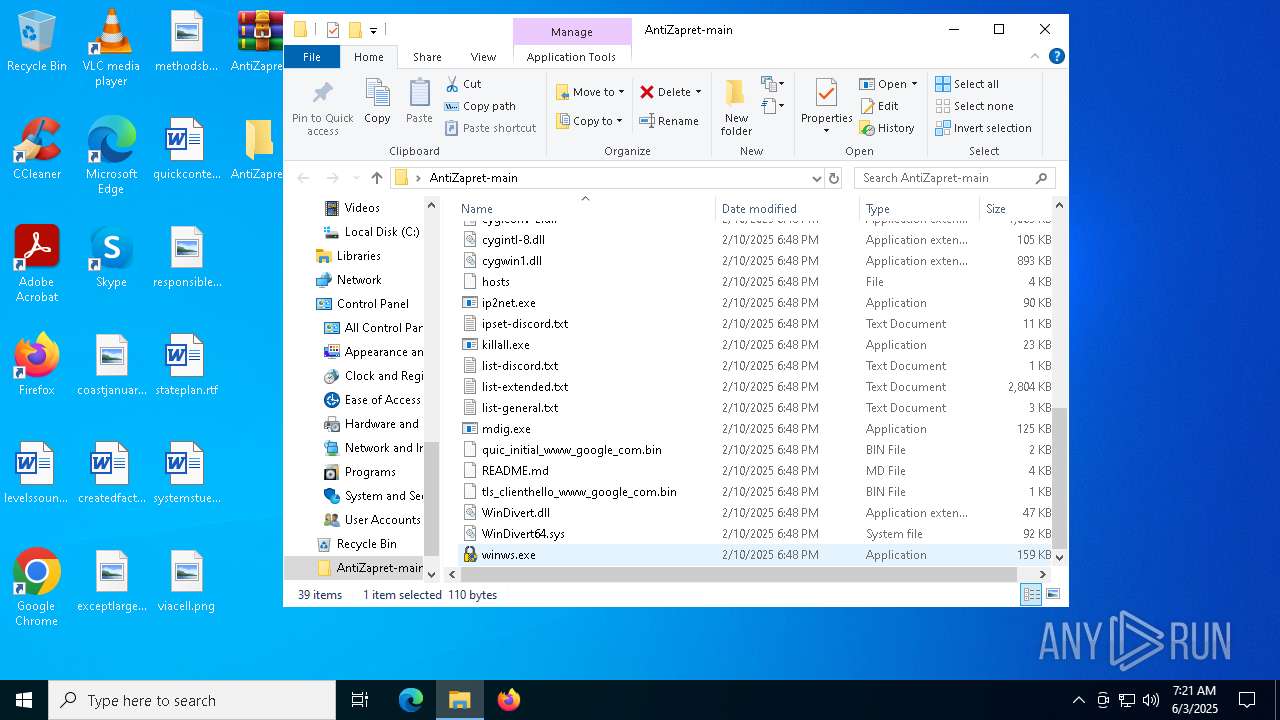
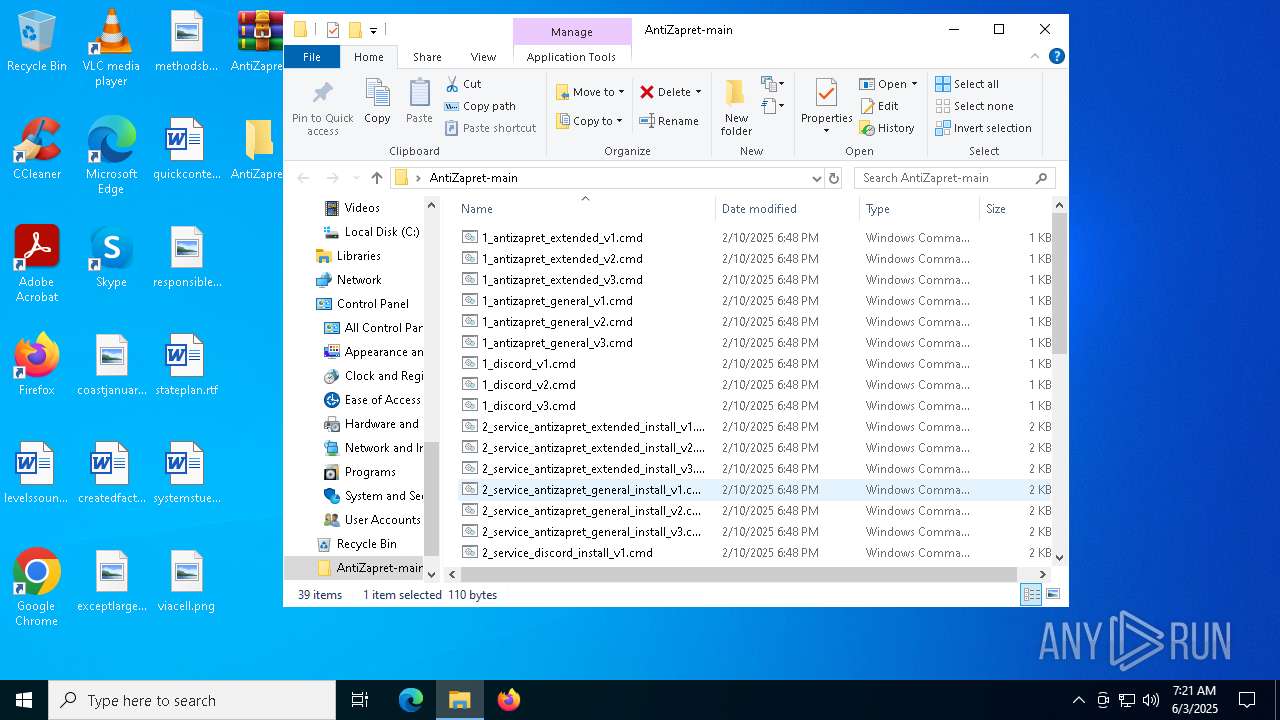
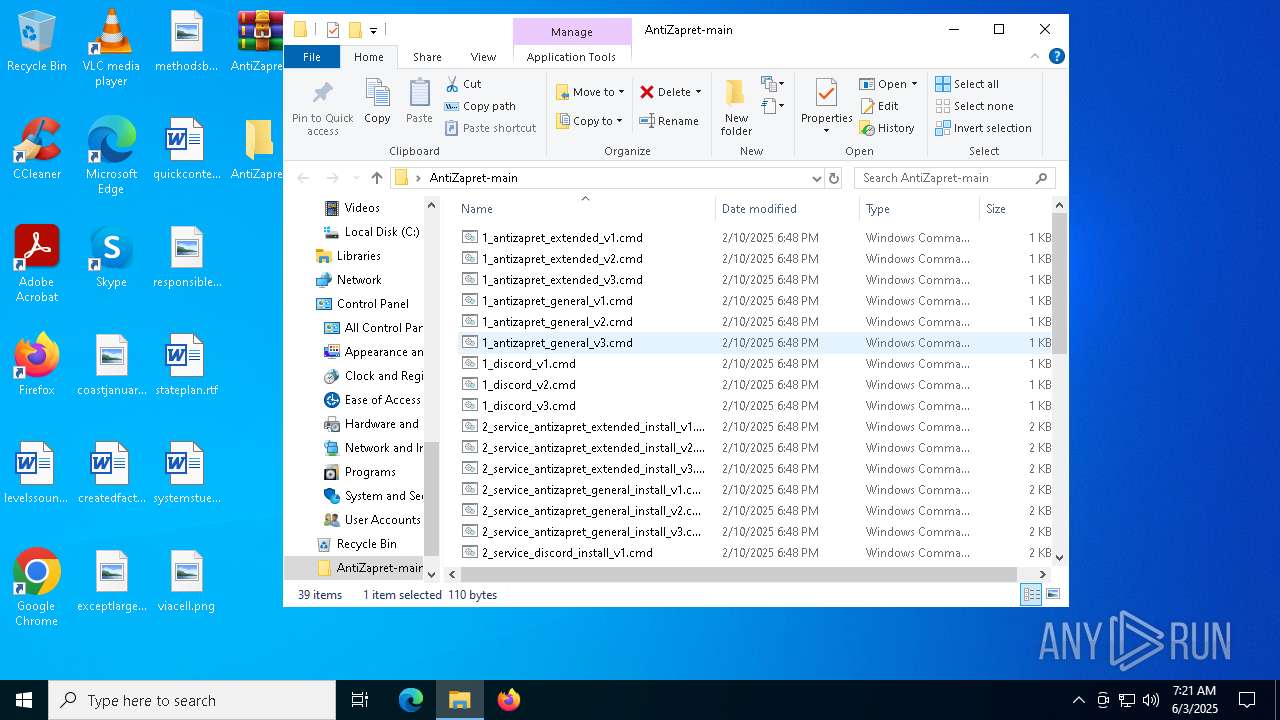
Executable files
9
Suspicious files
15
Text files
28
Unknown types
0
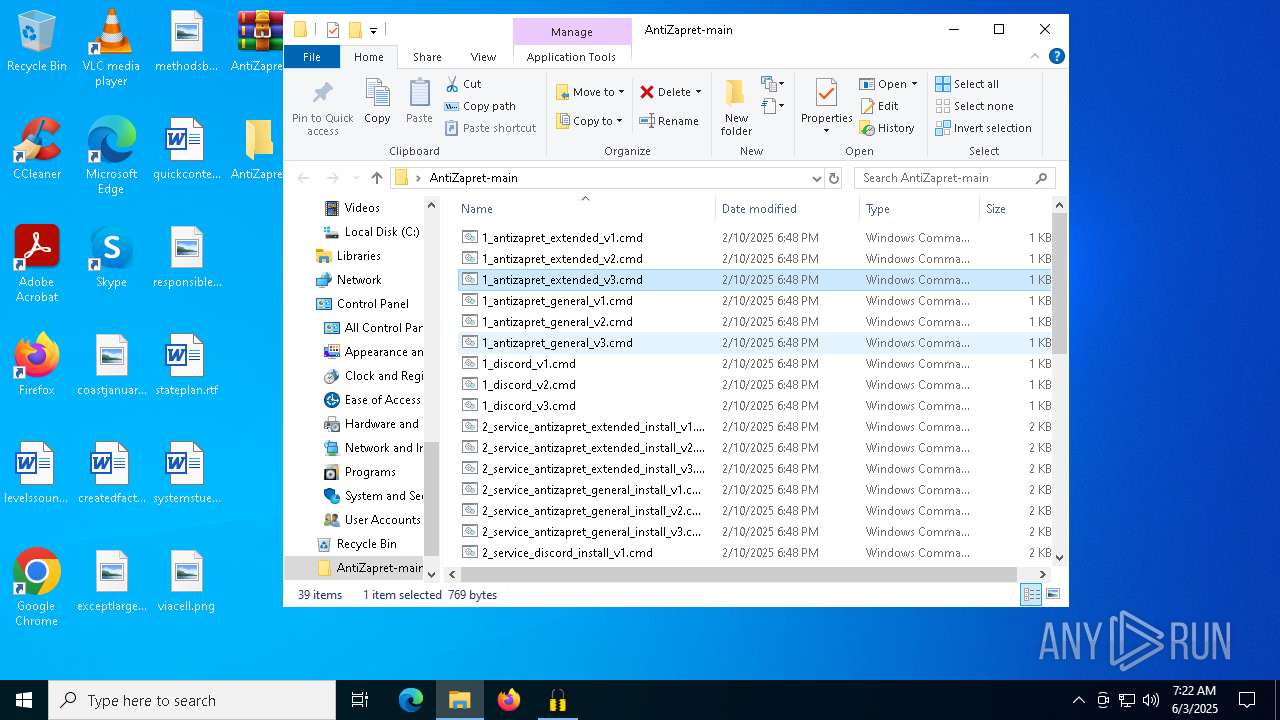
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\1_antizapret_general_v3.cmd | text | |
MD5:19416A00660900ACA12B8DEAF1B66F41 | SHA256:C6606B404AFD0757F5DBE608D6360D2B112D3DA4765B1D6435D69FED01EBC163 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\2_service_discord_install_v2.cmd | text | |
MD5:872CE75D0883994438E9BDD22A050310 | SHA256:4E36DFD7E0B8468AF58468CFF0D9B62303C3DB362EDC47378F9C9093C1F34F23 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\2_service_discord_install_v3.cmd | text | |
MD5:158F0D873354CB439C006E7137AC75EC | SHA256:0FF4E3DA1A1F96C989AE1EE2B5D39BD18CD65FF94C638EAF70206A06BE09497D | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\2_service_antizapret_extended_install_v1.cmd | text | |
MD5:900BAADE2CAD19083A26C3E779199056 | SHA256:A2BDB532204E4AF6C85E2F4F7F6BABB5BE58C3B98F04D01CCE634DBC0BD64CC2 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\1_antizapret_general_v1.cmd | text | |
MD5:203FA7F9D29D4A449DA5B9FB2B10D6B5 | SHA256:B28F48DD979880BCE13B185958F692627C1FB8954FF3632D1DBEB1C3ADAF6D5D | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\1_antizapret_extended_v1.cmd | text | |
MD5:3E04058DE35EAF24CD3B0845D2CF5BC4 | SHA256:E33484A14A0BE20761EB9EAFE3EE45810F48A123D4CB555EC3F28201E4180F02 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\1_antizapret_extended_v3.cmd | text | |
MD5:D96419CA91F0EDA57DCD00FEB26C4AC3 | SHA256:C881518C088B025480B84E07F3F98640C0D4E8647153EF17E29698A88459BA87 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\2_service_goodbye_discord_install_v2.cmd | text | |
MD5:F0E39B6BDC4AFB71F8179DBE29073A67 | SHA256:FABC0AA3DABFD39F5D06B641AAAB7121B0EBC164B6844E5D1F68AB4D9EF2FF18 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\2_service_antizapret_extended_install_v3.cmd | text | |
MD5:A1D5865208B078A511D09649F0A2376F | SHA256:EFB6047C47C8747D4FA11EB63171F223F0E71DC35092E682C06D06A435D56E09 | |||
| 7724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7724.2688\AntiZapret-main\2_service_discord_install_v1.cmd | text | |
MD5:A590A5CD168D70FD96D0DBAE63AB42F0 | SHA256:348BCA915EDAD2CC67B689C454766EBB467776E34DA11918E876BCF384B268C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7600 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7332 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7600 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7600 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5556 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |