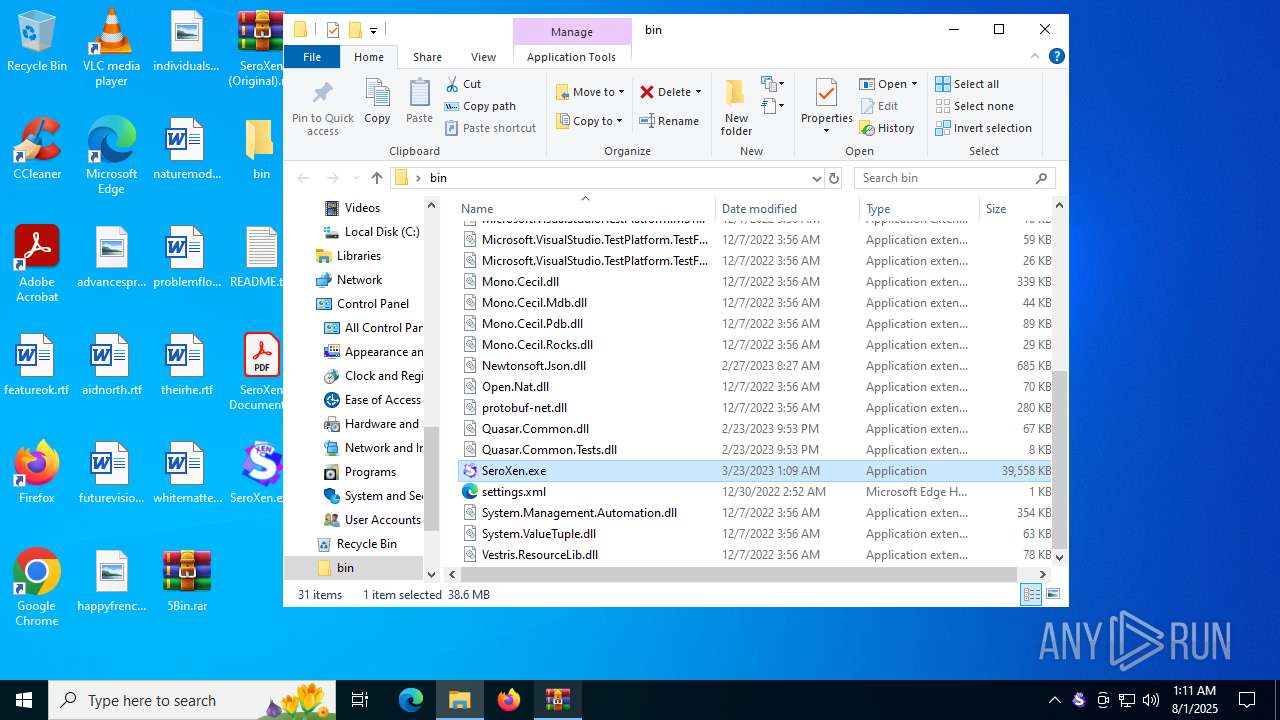
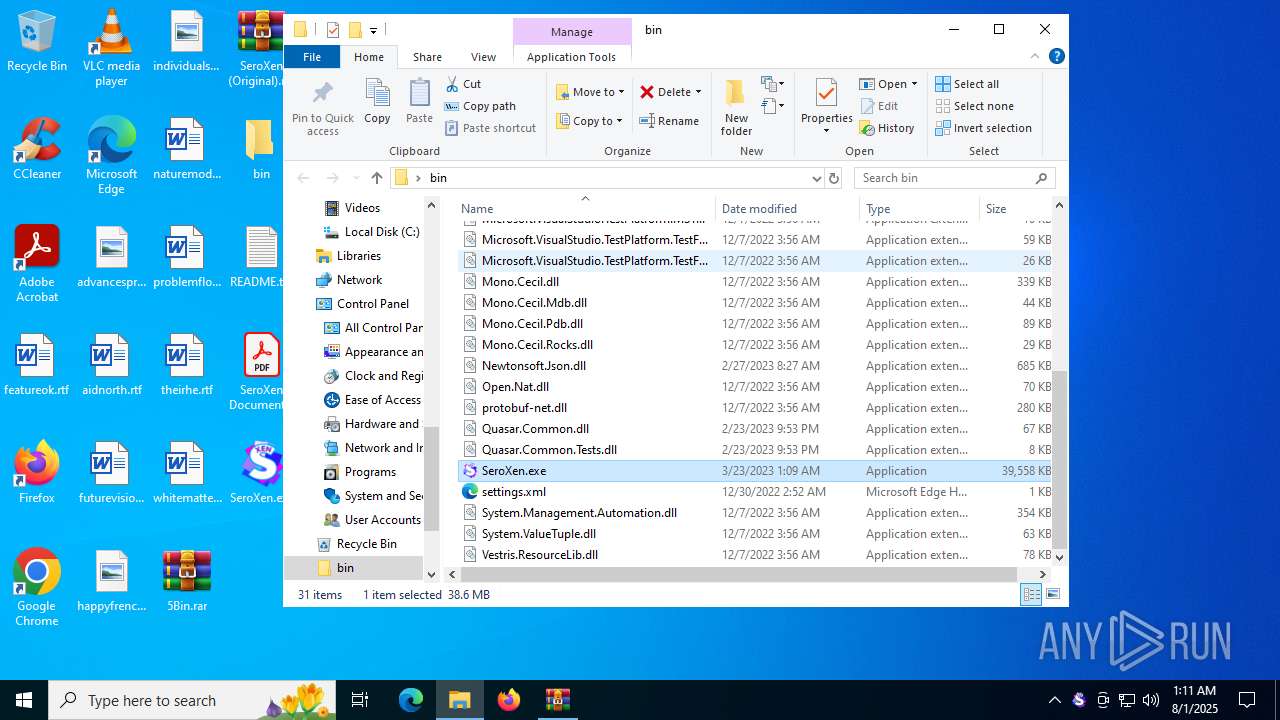
| File name: | 5Bin.rar |
| Full analysis: | https://app.any.run/tasks/a87dd893-c10a-416a-8929-a5ddb6f49674 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 01:09:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 033A171A537F4C9A30F0724739E3F83C |
| SHA1: | A4B24EC3492F586BEDFA4235745838BDC8E6ADEA |
| SHA256: | E469C2E098CBB729003E9AD2114649CE9DADF8D5A3D019DC271828F993DCE2B4 |
| SSDEEP: | 98304:k9TsWDWrjvhOINxrMqLwaCUxn70BMvuVg/dRgipKDuvJHw9vFdLx5M3Ymd5Seew8:+Omyc5lnSNSfB |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1380)
Process drops legitimate windows executable
- WinRAR.exe (PID: 1380)
Reads the BIOS version
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 2664)
- SeroXen.exe (PID: 7084)
Executable content was dropped or overwritten
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 7084)
Reads the date of Windows installation
- SeroXen.exe (PID: 1740)
Reads security settings of Internet Explorer
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
Connects to unusual port
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
INFO
Manual execution by a user
- SeroXen.exe (PID: 1740)
- WinRAR.exe (PID: 1380)
- SeroXen.exe (PID: 2664)
Create files in a temporary directory
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 2664)
- SeroXen.exe (PID: 7084)
The sample compiled with chinese language support
- WinRAR.exe (PID: 2976)
Checks supported languages
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1380)
Reads the computer name
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
Reads the machine GUID from the registry
- SeroXen.exe (PID: 1740)
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
Process checks computer location settings
- SeroXen.exe (PID: 1740)
Reads Environment values
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
Reads the software policy settings
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
- slui.exe (PID: 6264)
Creates files or folders in the user directory
- SeroXen.exe (PID: 7084)
- SeroXen.exe (PID: 2664)
Checks proxy server information
- slui.exe (PID: 6264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 349369 |
| UncompressedSize: | 625626 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Plugins/mstsc.exe |
Total processes
142
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\SeroXen (Original).rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\Desktop\SeroXen.exe" | C:\Users\admin\Desktop\SeroXen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: SeroXen Launcher Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
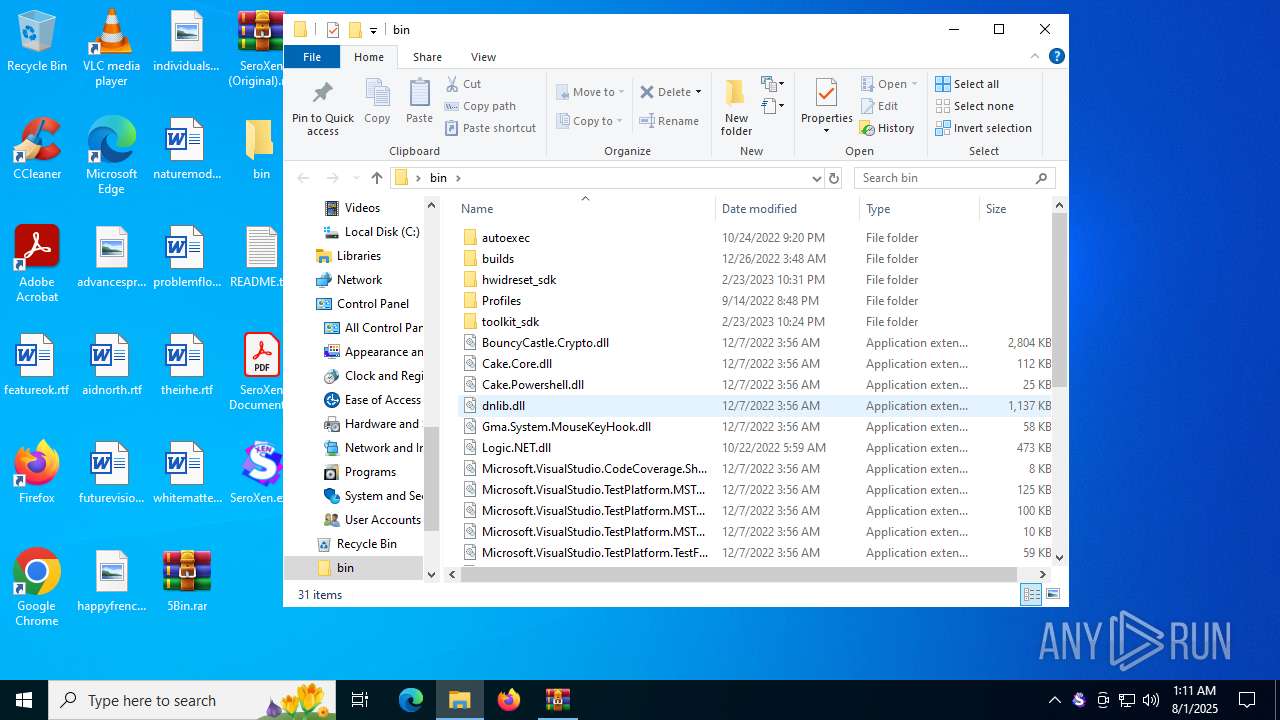
| 2664 | "C:\Users\admin\Desktop\bin\SeroXen.exe" | C:\Users\admin\Desktop\bin\SeroXen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Server Exit code: 4294967295 Version: 1.4.0 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\5Bin.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6264 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | "C:\Users\admin\Desktop\bin\SeroXen.exe" | C:\Users\admin\Desktop\bin\SeroXen.exe | SeroXen.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Server Exit code: 4294967295 Version: 1.4.0 Modules
| |||||||||||||||
Total events
16 907
Read events
16 895
Write events
12
Delete events
0
Modification events
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\5Bin.rar | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
32
Suspicious files
1
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\BouncyCastle.Crypto.dll | executable | |
MD5:0B2AA376251567DBDC15B3A2A0D10C65 | SHA256:E1B52566D7AA215EE5583D5A5D2CFBC6CFDCD881C47C7785318552BCB41B7CFF | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\C5VM.dll | executable | |
MD5:C70E1B8F7A64EF818720E03D84941EF2 | SHA256:EDB140F3DDF2578EFE2E1D7510679F0B7B8B06A8894009CDB55D8DD1FAC2911D | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\dnlib.dll | executable | |
MD5:C044F897673C5D72F631204D36D0DCAD | SHA256:6D6EF70286BDC71C9973AAE7069B038BB245FFB83234F98A56359B613810D392 | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\hwidreset_sdk\C5VM.dll | executable | |
MD5:B6BBC070370DA0AB86F7A4DC15F5F86D | SHA256:7575359BA4828B7CB1D34B8FBFBF647CC15C54183AE28F83E595E5E7940DDB6B | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\Cake.Powershell.dll | executable | |
MD5:271C0AD2A4F25C06D437254AD2D91D68 | SHA256:D3494C0A006915C348D57CCE502A0E56D01D6DC1631907604E95E7C323D54112 | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\Logic.NET.dll | executable | |
MD5:F7C48E31A7B79A58CDD0A41B6D57147D | SHA256:ADC96B974AB1520EA0A18B7223F2E0084A52FEDC4841F4074C738007FCF3B39D | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\Gma.System.MouseKeyHook.dll | executable | |
MD5:0BF4660C28D0DDF365934C1333C62C2D | SHA256:A62784297FF461A71E549DD75D0437D37B1CF8D2B88305C6C028CED7555213F7 | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\SeroXen.exe | — | |
MD5:— | SHA256:— | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\Cake.Core.dll | executable | |
MD5:C547895E4F6A86BF9DB103260D5CE792 | SHA256:25FCB11500BFFC21F1AE6CF3F5C4FF2E9450F41F01B6B02BCB5873F6F9B279F0 | |||
| 1380 | WinRAR.exe | C:\Users\admin\Desktop\bin\Mono.Cecil.dll | executable | |
MD5:6930BA212FE20AED8DA228FC4C9EE3C0 | SHA256:2F7AF51F2F4DADDB812DC0662D1CBCCA7709009A50402AB42E93853CE5A5231F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5084 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4748 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4748 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1352 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5084 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |