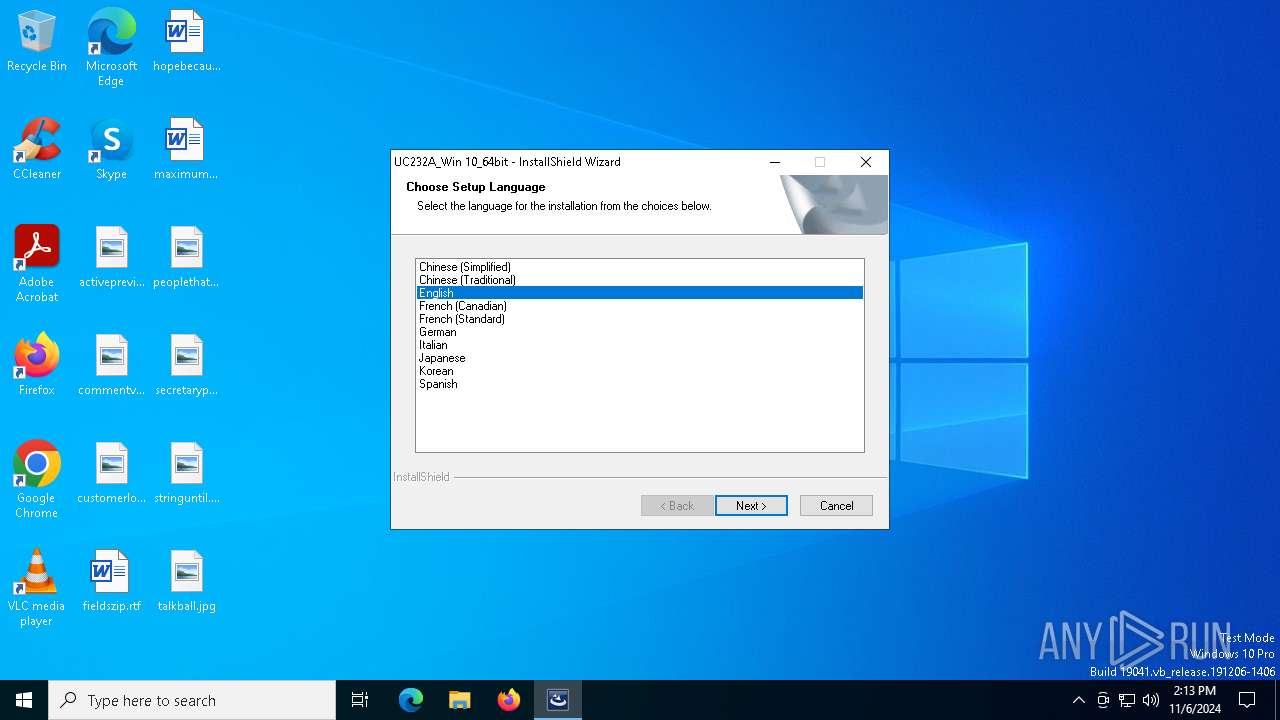
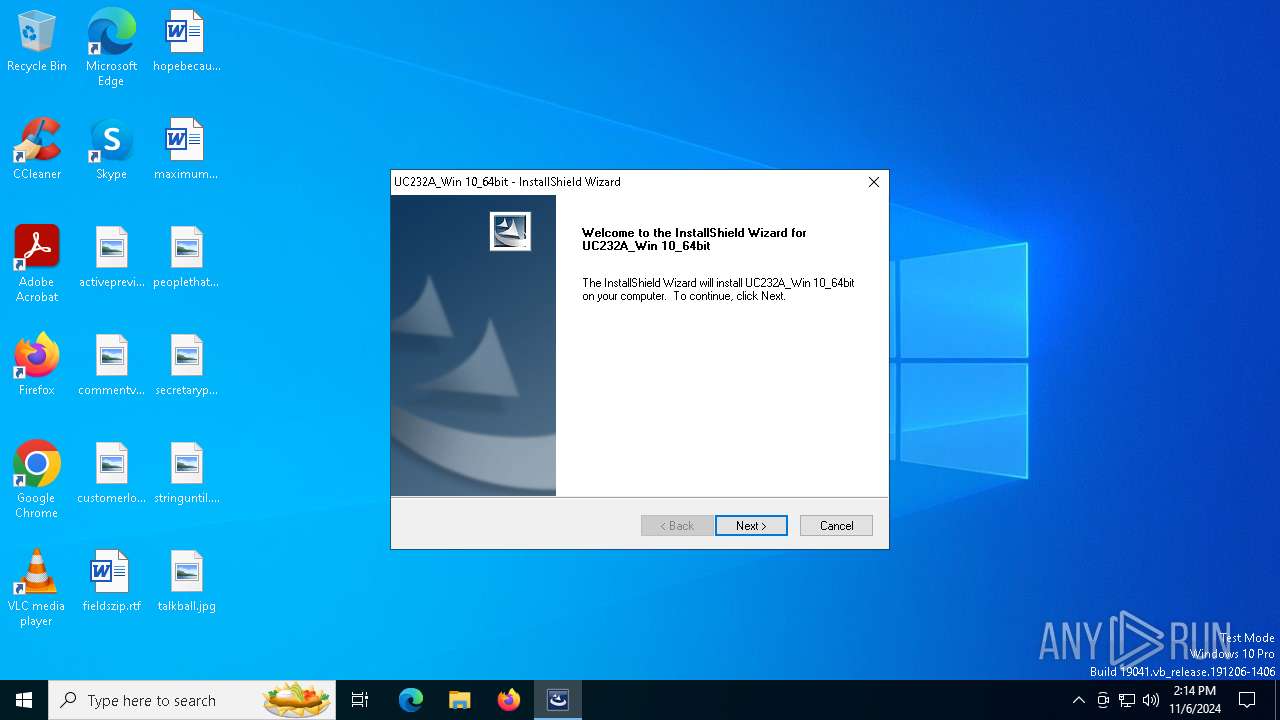
| File name: | UC232A_Windows_Setup.exe |
| Full analysis: | https://app.any.run/tasks/d5e17d68-bda1-4000-bdd6-41a8c5675a33 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2024, 14:13:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 537A4C44ABDAD58EBD87F59065B14284 |
| SHA1: | 9B52616D3EAB21E1F0C4DD70D57D18EF188FE67E |
| SHA256: | E45BFA5AAA25E8DBCE0A377E2346AEE387754BFF1271C5FB082FB521D3D43FE2 |
| SSDEEP: | 196608:XXavH/eVg7z3F0eJRWkmKMZ9VPrndaHG7Q+ZMKmU:XXavHGczV9R4VHV5UzyMpU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- UC232A_Windows_Setup.exe (PID: 6836)
- Win10_x64.exe (PID: 6224)
- DPInst_x64.exe (PID: 7040)
- drvinst.exe (PID: 1452)
- drvinst.exe (PID: 6204)
- DPInst_x64.exe (PID: 2444)
Reads security settings of Internet Explorer
- UC232A_Windows_Setup.exe (PID: 6836)
Process drops legitimate windows executable
- Win10_x64.exe (PID: 6224)
- DPInst_x64.exe (PID: 7040)
- drvinst.exe (PID: 1452)
Executes as Windows Service
- VSSVC.exe (PID: 1712)
Drops a system driver (possible attempt to evade defenses)
- Win10_x64.exe (PID: 6224)
- DPInst_x64.exe (PID: 7040)
- drvinst.exe (PID: 1452)
- DPInst_x64.exe (PID: 2444)
- drvinst.exe (PID: 6204)
INFO
Checks supported languages
- UC232A_Windows_Setup.exe (PID: 6836)
Sends debugging messages
- UC232A_Windows_Setup.exe (PID: 6836)
Create files in a temporary directory
- UC232A_Windows_Setup.exe (PID: 6836)
Reads the computer name
- UC232A_Windows_Setup.exe (PID: 6836)
Process checks computer location settings
- UC232A_Windows_Setup.exe (PID: 6836)
The process uses the downloaded file
- UC232A_Windows_Setup.exe (PID: 6836)
Manages system restore points
- SrTasks.exe (PID: 6152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:05:26 11:50:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 7655424 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 88170496 |
| EntryPoint: | 0x5b62920 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.87.0 |
| ProductVersionNumber: | 1.0.82.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Aten International Co., Ltd. |
| FileDescription: | UC232A_Windows_Setup |
| FileVersion: | 1,0,087 |
| InternalName: | Win32 |
| LegalCopyright: | Copyright (R) 2020 Aten International Co., Ltd. All rights reserved. |
| OriginalFileName: | UC232A_Windows_Setup |
| ProductName: | UC232A |
| ProductVersion: | 1,0,087 |
Total processes
146
Monitored processes
13
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Users\admin\AppData\Local\Temp\Win10_x64.exe" | C:\Users\admin\AppData\Local\Temp\Win10_x64.exe | — | UC232A_Windows_Setup.exe | |||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 15.0.498 Modules
| |||||||||||||||
| 1452 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{735bd851-b141-2744-8e2b-74b702a61647}\ser2at.inf" "9" "47aed4baf" "0000000000000170" "WinSta0\Default" "00000000000001E4" "208" "c:\program files (x86)\aten international co., ltd\uc232a_win 10_64bit\old" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 3758096967 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 1712 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2444 | "C:\Program Files (x86)\Aten International Co., Ltd\UC232A_Win 10_64bit\new\DPInst_x64.exe" | C:\Program Files (x86)\Aten International Co., Ltd\UC232A_Win 10_64bit\new\DPInst_x64.exe | Win10_x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 | |||||||||||||||
| 2708 | C:\Users\admin\AppData\Local\Temp\{44E9F608-ABBC-4BF5-A95B-00124729F3B7}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{4C55C6ED-1F36-4065-A60F-57AC42605B95} | C:\Users\admin\AppData\Local\Temp\{44E9F608-ABBC-4BF5-A95B-00124729F3B7}\ISBEW64.exe | — | Win10_x64.exe | |||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 15.0.498 Modules
| |||||||||||||||
| 3508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6152 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6204 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{9e6cc564-1816-bb45-90e6-4ce641dec7bb}\plser.inf" "9" "4045707f7" "0000000000000200" "WinSta0\Default" "0000000000000204" "208" "c:\program files (x86)\aten international co., ltd\uc232a_win 10_64bit\new" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6224 | "C:\Users\admin\AppData\Local\Temp\Win10_x64.exe" | C:\Users\admin\AppData\Local\Temp\Win10_x64.exe | UC232A_Windows_Setup.exe | ||||||||||||
User: admin Company: Acresso Software Inc. Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 15.0.498 Modules
| |||||||||||||||
| 6552 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
Total events
1 482
Read events
1 420
Write events
53
Delete events
9
Modification events
| (PID) Process: | (6224) Win10_x64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000D6369E2E5630DB0150180000481A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000FA99A02E5630DB01E01B000080100000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000590E132F5630DB01E01B000080100000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000590E132F5630DB01E01B000080100000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000D8D7172F5630DB01E01B000080100000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000CB8F1C2F5630DB01E01B000080100000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000727DA42F5630DB01E01B000080100000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7136) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D7E2A62F5630DB01E01B00009C180000E8030000010000000000000000000000ED75B1C4F02D8347A2003337BAD761F500000000000000000000000000000000 | |||
| (PID) Process: | (1712) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BEC4B22F5630DB01B006000050110000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
66
Suspicious files
38
Text files
25
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\Disk1\layout.bin | binary | |
MD5:A45AE16F267194D496657DB36853EEC7 | SHA256:DCD2543DEA70D243D78C526AB66AD2A23AD37332A603505899EEAC53FB9EE31F | |||
| 6836 | UC232A_Windows_Setup.exe | C:\Users\admin\AppData\Local\Temp\Win10_x64.exe | executable | |
MD5:C81160D34C4042233B00808D71BB921D | SHA256:4409E2DD0BE970274D19261311028343CB6375E1BDC43DF539A12360044987DC | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\Disk1\data1.cab | compressed | |
MD5:4482636958AF88E84D94949076505C97 | SHA256:2F8096A1593BABACAA38CA8EF95BA647A6EF279A623B5380D70B670F521B4A99 | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\Disk1\data1.hdr | compressed | |
MD5:AE382B0A494FC46E349680FA3A5503BE | SHA256:2502586CC509B6D602865FB24D4A17F4A3D62C3BA5C24FCB3A711111757A085F | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\Disk1\ISSetup.dll | executable | |
MD5:C5B13B3C260393E7D64506B7399A2A11 | SHA256:508022BC8B0473AA960694FE4FE82BB98485DC9958A2BD2C7F6604BD60387213 | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\setup.ini | text | |
MD5:453C94C4010F63E133CEEB68394D2E90 | SHA256:DC028A6AF459B1E33DDEF7144B776CBD3E0AEAC593D911F1C195C753FCA80A6D | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\_Setup.dll | executable | |
MD5:7DE2D19C870587B8FFC5A446E9B6E29A | SHA256:35EEF33D1890A6E34D647F86F24C730B4F741C9D33FCCE01CFB12D2B8E55B5D1 | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{1292D677-F571-4549-A64C-41DB5B2ACFE4}\Disk1\_Setup.dll | executable | |
MD5:7DE2D19C870587B8FFC5A446E9B6E29A | SHA256:35EEF33D1890A6E34D647F86F24C730B4F741C9D33FCCE01CFB12D2B8E55B5D1 | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{44E9F608-ABBC-4BF5-A95B-00124729F3B7}\{680FF7B7-9645-48D3-9DCA-B8C756CC9E35}\setup.inx | binary | |
MD5:B1A67C8555BD23920E72BCD43D5F28C6 | SHA256:714E2FBD1F019AD49945FCD4D069713336AB69504B305E4854894E2F8C92F56B | |||
| 6224 | Win10_x64.exe | C:\Users\admin\AppData\Local\Temp\{44E9F608-ABBC-4BF5-A95B-00124729F3B7}\{680FF7B7-9645-48D3-9DCA-B8C756CC9E35}\setu4e81.rra | binary | |
MD5:B1A67C8555BD23920E72BCD43D5F28C6 | SHA256:714E2FBD1F019AD49945FCD4D069713336AB69504B305E4854894E2F8C92F56B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
49
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5756 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5756 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.209.161:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
7048 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
UC232A_Windows_Setup.exe | C:\Users\admin\AppData\Local\Temp\setup.iss.install |