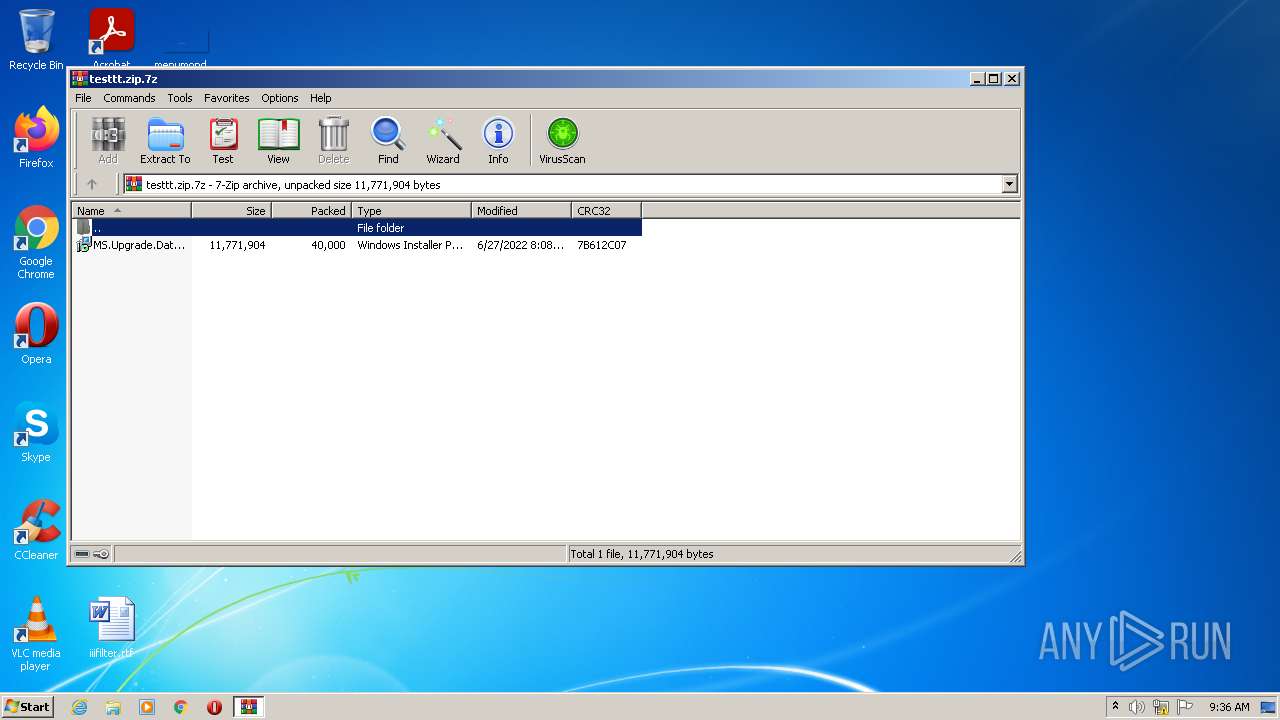
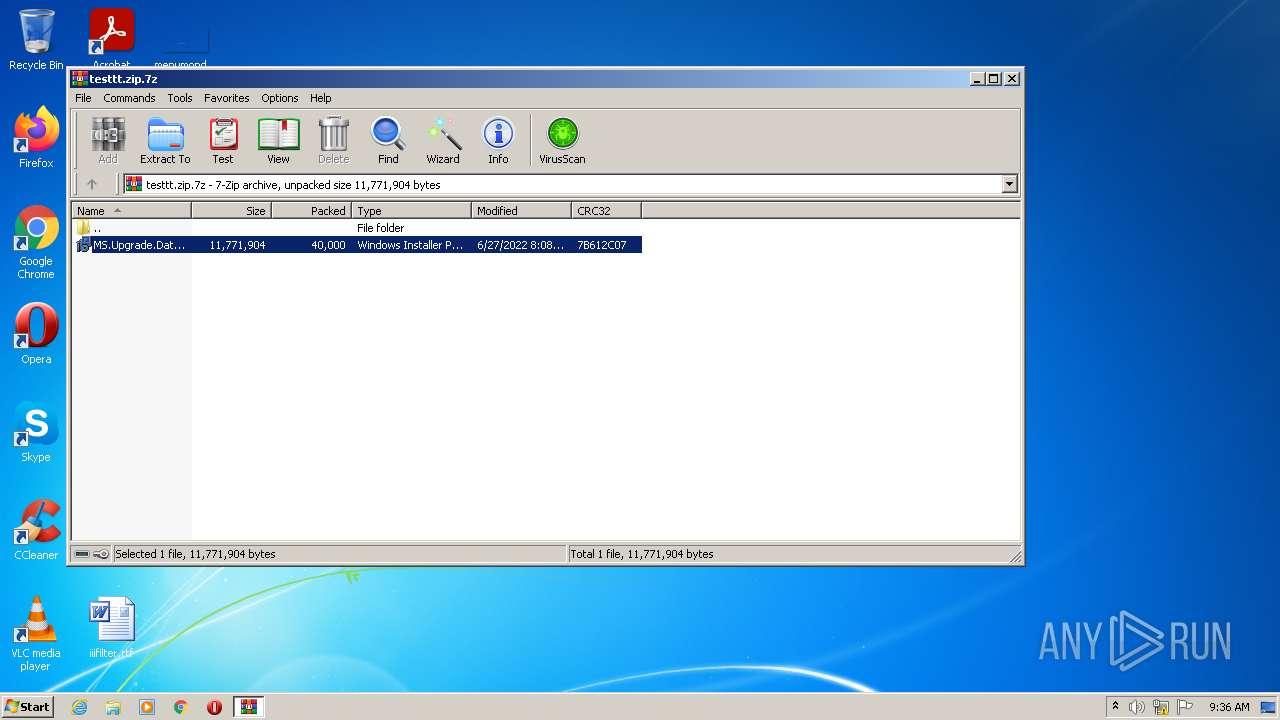
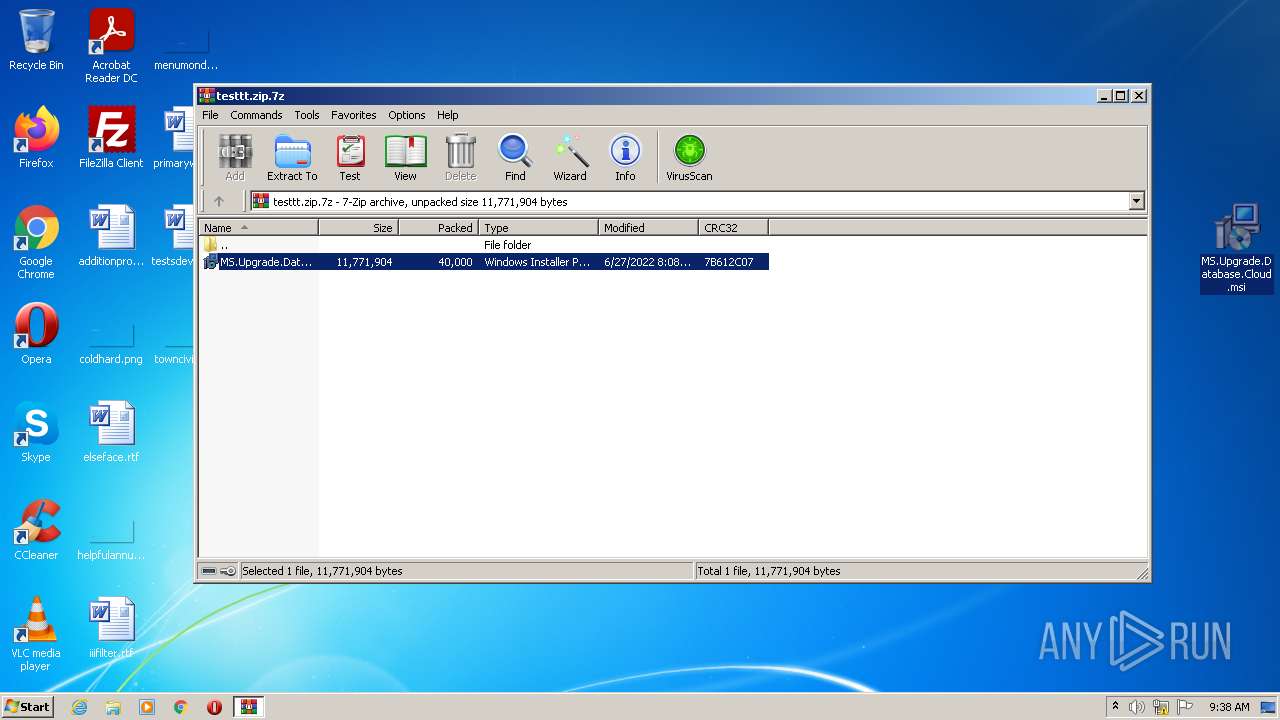
| File name: | testtt.zip |
| Full analysis: | https://app.any.run/tasks/de039655-bd98-4520-b49e-b4c9b019db94 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 08:36:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 20D6C8DE4B8D592FAF18E460B38ABEEC |
| SHA1: | 08C93DBCEE18ACC77ED882DB07D3B189834B45A3 |
| SHA256: | E453EF93937739A4B84D4BEE23D05074B0271F0C344220B09D737CA39935979B |
| SSDEEP: | 768:QLftW+tu3poETFz5EnuoEECA8j5m873V5DZUOOuZJJC55zCvsWA5TGcNLz:oftW+tu3FnnoOZzLbDZUOVriCvSTbP |
MALICIOUS
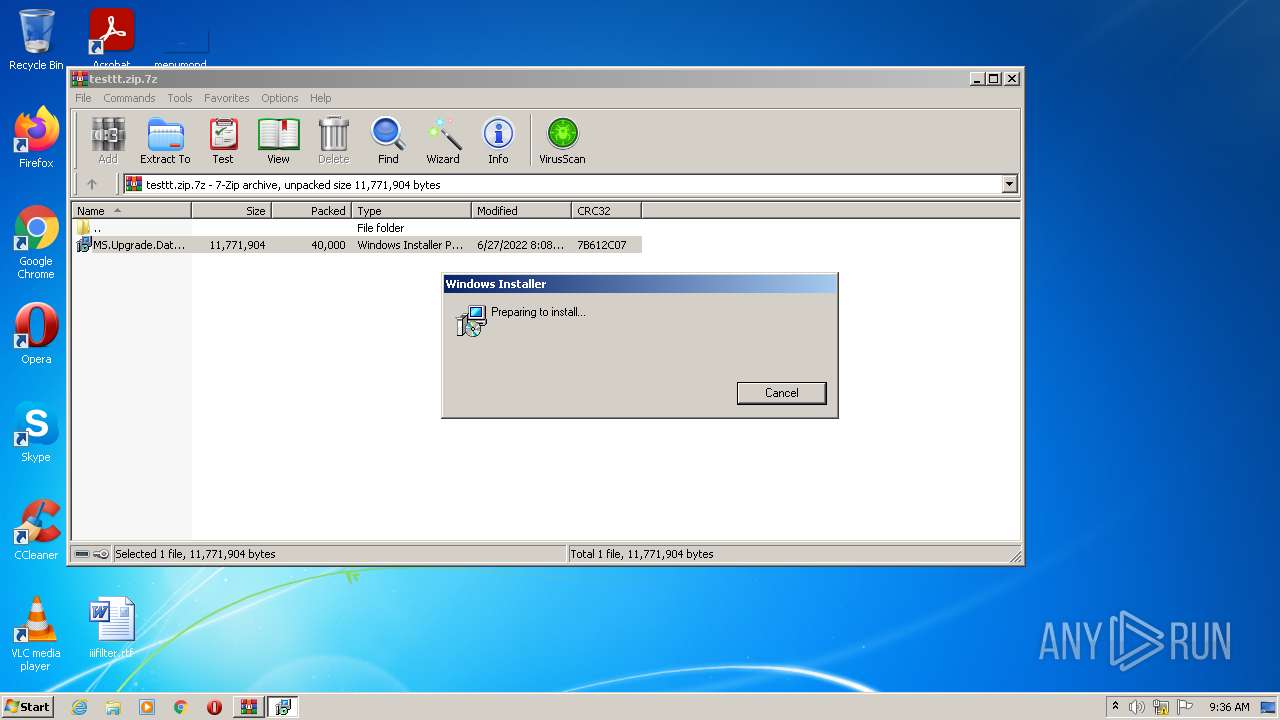
Drops executable file immediately after starts
- msiexec.exe (PID: 2300)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2444)
- msiexec.exe (PID: 2300)
- MsiExec.exe (PID: 1556)
- MsiExec.exe (PID: 1120)
Reads the computer name
- WinRAR.exe (PID: 2444)
- msiexec.exe (PID: 2300)
- MsiExec.exe (PID: 1556)
- MsiExec.exe (PID: 1120)
Starts Microsoft Installer
- WinRAR.exe (PID: 2444)
Reads the Windows organization settings
- msiexec.exe (PID: 708)
- msiexec.exe (PID: 2300)
- msiexec.exe (PID: 296)
Reads Windows owner or organization settings
- msiexec.exe (PID: 708)
- msiexec.exe (PID: 2300)
- msiexec.exe (PID: 296)
Executed as Windows Service
- vssvc.exe (PID: 2828)
Drops a file with a compile date too recent
- msiexec.exe (PID: 2300)
Reads Environment values
- vssvc.exe (PID: 2828)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2300)
INFO
Checks supported languages
- msiexec.exe (PID: 708)
- vssvc.exe (PID: 2828)
- msiexec.exe (PID: 296)
Reads the computer name
- msiexec.exe (PID: 708)
- vssvc.exe (PID: 2828)
- msiexec.exe (PID: 296)
Reads settings of System Certificates
- msiexec.exe (PID: 708)
- msiexec.exe (PID: 2300)
- msiexec.exe (PID: 296)
Checks Windows Trust Settings
- msiexec.exe (PID: 708)
- msiexec.exe (PID: 296)
- msiexec.exe (PID: 2300)
Application launched itself
- msiexec.exe (PID: 2300)
Manual execution by user
- msiexec.exe (PID: 296)
Searches for installed software
- msiexec.exe (PID: 2300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
43
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\MS.Upgrade.Database.Cloud.msi" | C:\Windows\System32\msiexec.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 708 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXb2444.14401\MS.Upgrade.Database.Cloud.msi" | C:\Windows\System32\msiexec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1120 | C:\Windows\system32\MsiExec.exe -Embedding A1C0291B52F9316E8515C09803C1A323 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | C:\Windows\system32\MsiExec.exe -Embedding 74FC99A7E1DB38AAC4178E4EF552D912 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\testtt.zip.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2828 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 189
Read events
14 823
Write events
358
Delete events
8
Modification events
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\testtt.zip.7z | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2444) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2444 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2444.14401\MS.Upgrade.Database.Cloud.msi | — | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\Windows\Installer\10d4b7.msi | — | |
MD5:— | SHA256:— | |||
| 2444 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2444.19430\MS.Upgrade.Database.Cloud.msi | — | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\Windows\Installer\10d4b8.msi | — | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{b3c8a12d-9720-4c4b-a235-a2f4b4372aa9}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{3685bc02-b0a2-41fe-95d5-bf7a62929edf}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\Windows\Installer\MSID6F9.tmp | executable | |
MD5:— | SHA256:— | |||
| 2300 | msiexec.exe | C:\Windows\Installer\MSI5A6D.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report