| File name: | bottok-main.zip |
| Full analysis: | https://app.any.run/tasks/11ab4124-ff82-408f-aa88-adc3f35d5e81 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 02:21:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | C6A9A777E729DC115DDB1AE481CBE7AB |
| SHA1: | 1E26BD029C7E94FE4B7B905E8BF73199B1EF8461 |
| SHA256: | E451B579FF56C5DB11D15ADBB734AC21A1CFEC8FE046230C57577E09A2B5DF75 |
| SSDEEP: | 98304:+mPPfeA+aK9PL+/s/7bK18uj9nNKQ/H4OWZ+ECs8H94Lh2TqTP51QVE4NjYXmUG9:tuF74kQ5hDWo/9e75aTMQt |
MALICIOUS
Generic archive extractor
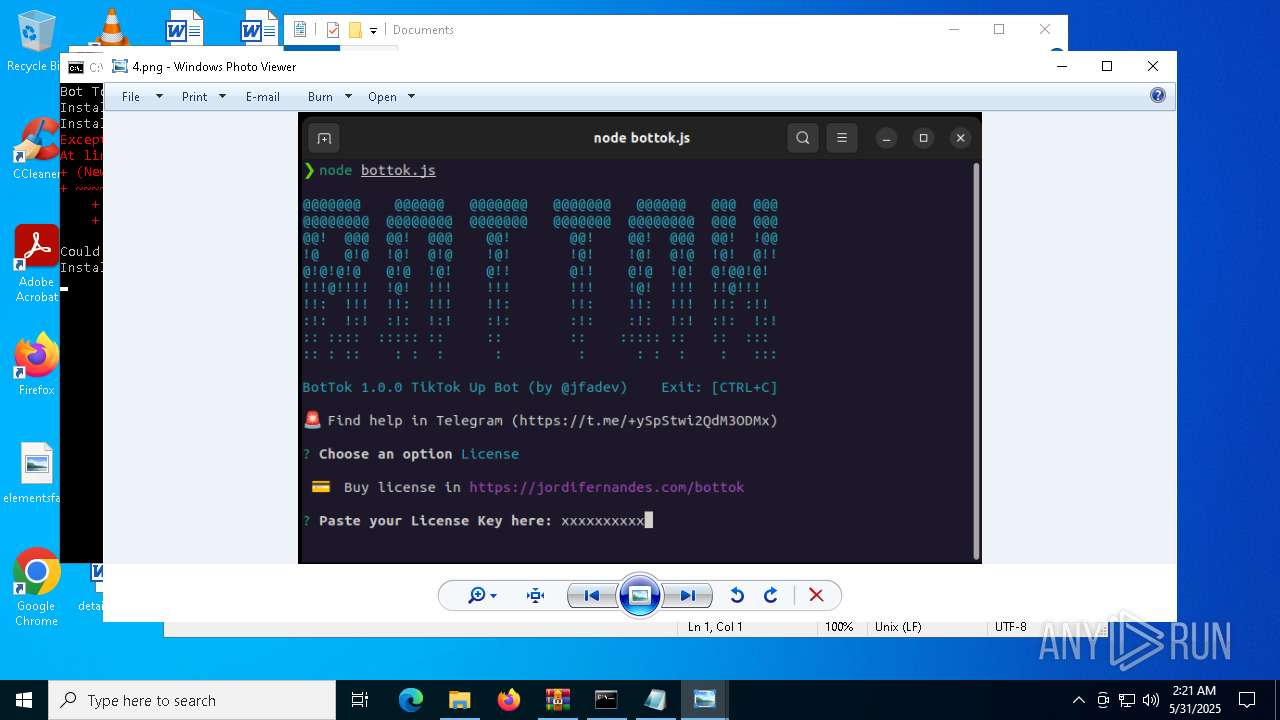
- WinRAR.exe (PID: 5972)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7980)
- powershell.exe (PID: 7308)
SUSPICIOUS
Probably download files using WebClient
- cmd.exe (PID: 5760)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5760)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5760)
Opens a file (MACROS)
- EXCEL.EXE (PID: 8076)
Reads data from a file (MACROS)
- EXCEL.EXE (PID: 8076)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 3896)
INFO
Manual execution by a user
- cmd.exe (PID: 4988)
- cmd.exe (PID: 5528)
- notepad.exe (PID: 6184)
- cmd.exe (PID: 5760)
- cmd.exe (PID: 7000)
- EXCEL.EXE (PID: 8076)
- rundll32.exe (PID: 7788)
- rundll32.exe (PID: 7440)
- OpenWith.exe (PID: 8132)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6184)
- rundll32.exe (PID: 7440)
- splwow64.exe (PID: 3896)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7980)
- powershell.exe (PID: 7308)
Reads the computer name
- msiexec.exe (PID: 7824)
Checks supported languages
- msiexec.exe (PID: 7824)
Failed to create an executable file in Windows directory
- powershell.exe (PID: 7308)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 7440)
- OpenWith.exe (PID: 8132)
Checks proxy server information
- slui.exe (PID: 1452)
Reads the software policy settings
- slui.exe (PID: 1452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:29 06:14:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | bottok-main/ |
Total processes
153
Monitored processes
24
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3896 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\win-update.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5528 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\win-bottok.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
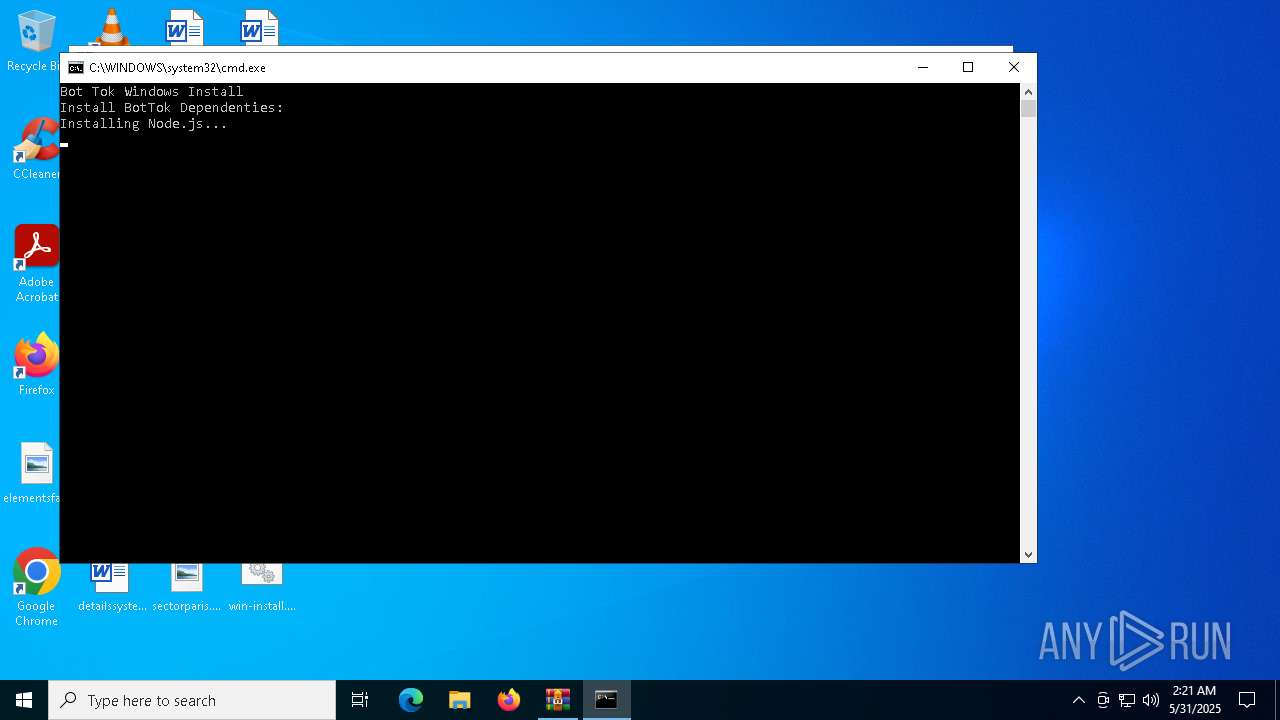
| 5760 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\win-install.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
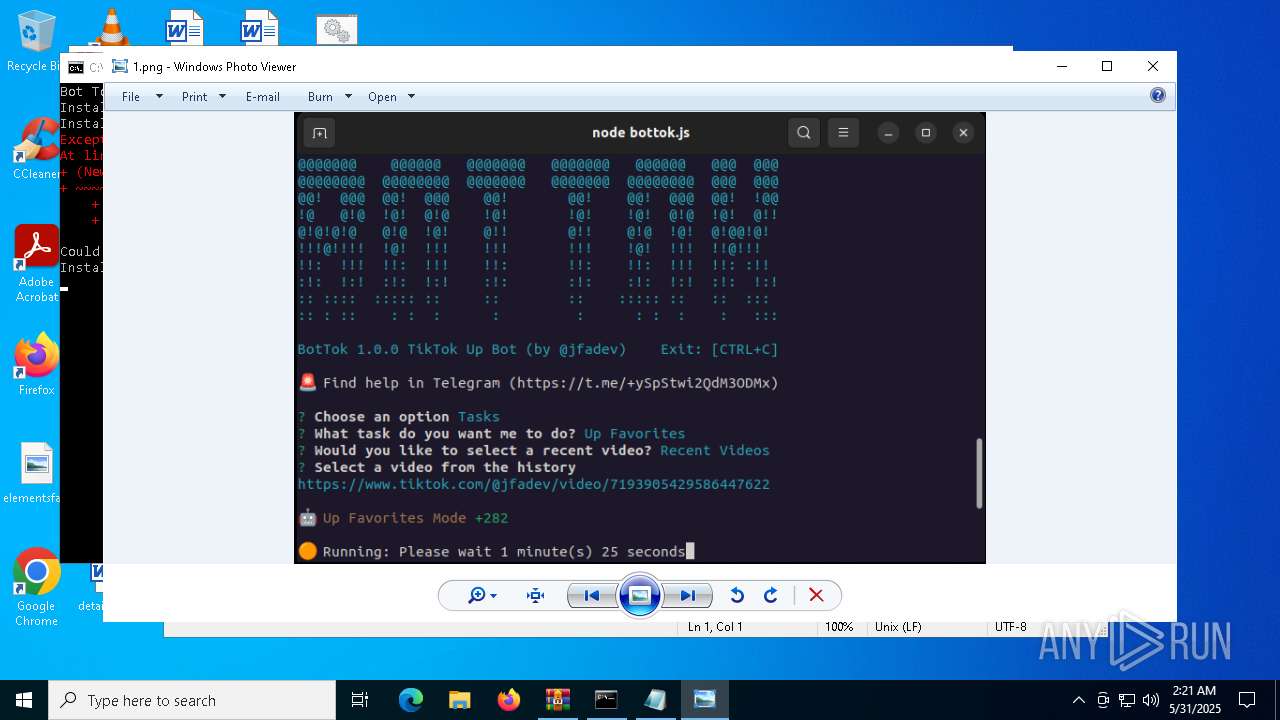
| 5972 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\bottok-main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5984 | where node | C:\Windows\System32\where.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
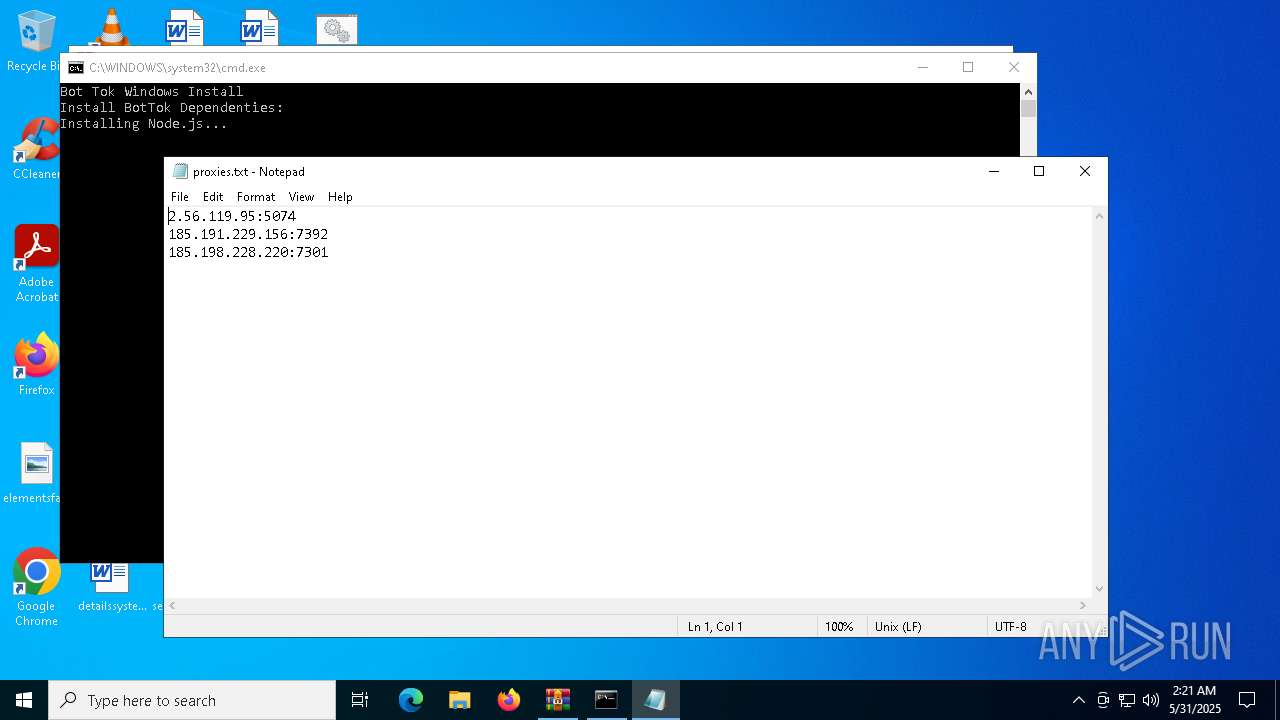
| 6184 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\proxies.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 216
Read events
26 964
Write events
231
Delete events
21
Modification events
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\bottok-main.zip | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
12
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xxaopwih.v0q.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms~RF127845.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:793A1500700F4C91B60E220ABA10804E | SHA256:FBBFC386D34FC1DAB7B4D5C2EF9B0551C084D306EFA7FDB571194475CE830438 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\tasks.csv.LNK | binary | |
MD5:EB06652AB7A81DF2BBC42285CDB510B9 | SHA256:28424FD3DA353A6962B13690F1E63CA9E1C5BB45B5A264FD343F105967C27FD7 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:25A3FD47226D73D0C8187C719A64F5DD | SHA256:F944B569C084EDB8C6B1DEF38F188C9EE8C7272CC253C2D5FCE26362F51A07B5 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PZ9JNYU02WTG0LR4ZNJC.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:F6A44CCE81A41EC2A212439CF7C06F41 | SHA256:6C4E521199396F5A2E5BE43D0C3518FE9E275C4F3379B4679A1583A1717177AE | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1P9C92XFQ789KEWBKSE9.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 8076 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 7308 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h1qqunlr.rsd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
36
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7184 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7184 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.109.76.240:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 179 Kb | whitelisted |
— | — | GET | 200 | 52.123.129.14:443 | https://ecs.office.com/config/v2/Office/excel/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=excel.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bA17BBA6A-E80A-47D5-8FD3-25947ACC42F5%7d&LabMachine=false | unknown | binary | 388 Kb | whitelisted |
— | — | GET | 200 | 52.111.231.13:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=1&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BA17BBA6A-E80A-47D5-8FD3-25947ACC42F5%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofaa1msspvo2xw31%22%7D | unknown | text | 542 b | whitelisted |
— | — | POST | 200 | 52.182.143.211:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 51.105.71.136:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 40.126.32.138:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7184 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7184 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
7184 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
8076 | EXCEL.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
8076 | EXCEL.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8076 | EXCEL.EXE | 52.111.231.13:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
8076 | EXCEL.EXE | 52.182.143.211:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |