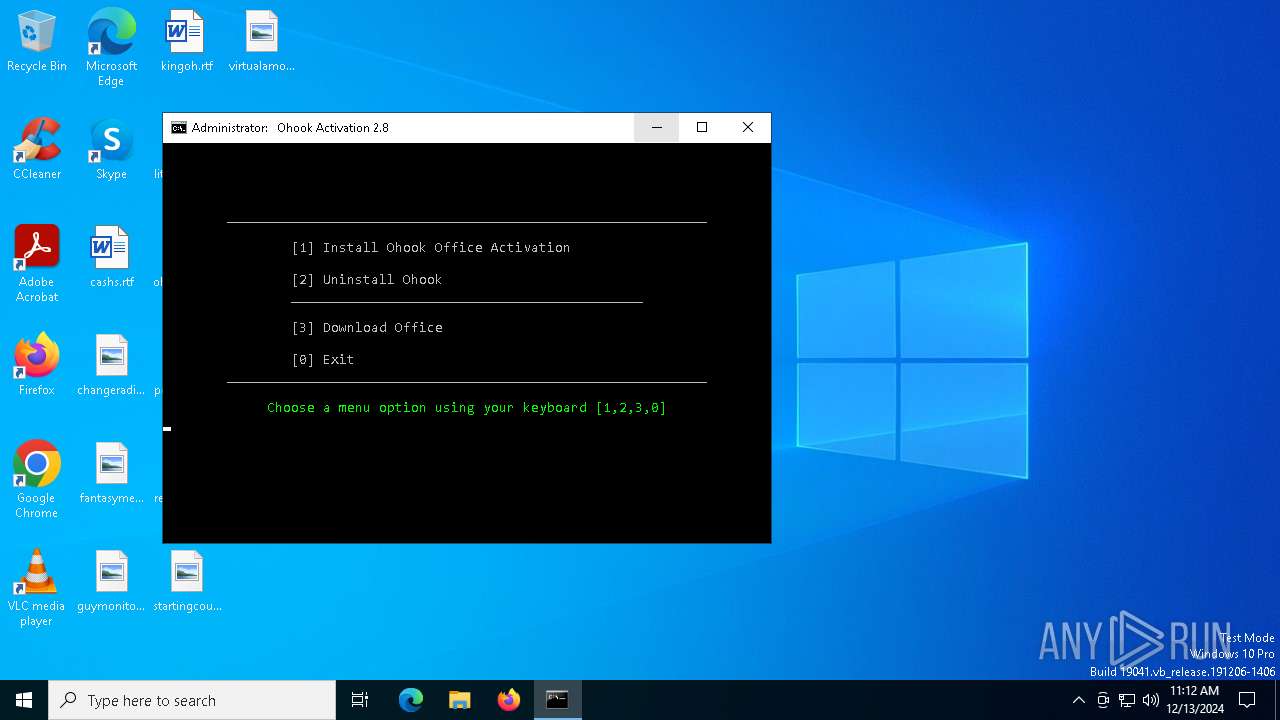
| File name: | Ohook_Activation_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/9c3d4319-1da0-450d-a191-f4f8cefb7852 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 11:12:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (452), with CRLF line terminators |
| MD5: | 1007B8D5559EB72788D5B5F4757AB916 |
| SHA1: | EE2DCC864075810DB1EE1D67B69092C3E61A23AA |
| SHA256: | E44ED8D3DBC49A9B7B4492389BC3A8C8A4970A790E7436B6D2C8A1900205ED1D |
| SSDEEP: | 1536:BIBR9cRya5qyM5R5dmx0wGCgLwI/JHFNdmu2/RYITFMGzbiSu7FrHnMQMvInnwT:BIBRKRZA5RvFw21VFaRYIzbGBMZgnnwT |
MALICIOUS
No malicious indicators.SUSPICIOUS
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6292)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6804)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 1536)
- cmd.exe (PID: 5268)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6528)
- cmd.exe (PID: 6292)
- powershell.exe (PID: 6956)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6528)
- powershell.exe (PID: 7024)
- cmd.exe (PID: 6600)
- cmd.exe (PID: 6208)
Starts SC.EXE for service management
- cmd.exe (PID: 6292)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6208)
Application launched itself
- cmd.exe (PID: 6528)
- cmd.exe (PID: 6292)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6528)
- cmd.exe (PID: 6600)
- powershell.exe (PID: 6820)
- cmd.exe (PID: 6208)
Executing commands from a ".bat" file
- cmd.exe (PID: 6292)
- powershell.exe (PID: 6956)
- cmd.exe (PID: 6016)
- powershell.exe (PID: 7024)
- cmd.exe (PID: 6208)
Executing commands from ".cmd" file
- cmd.exe (PID: 6292)
- powershell.exe (PID: 6956)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6208)
- powershell.exe (PID: 7024)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6636)
- cmd.exe (PID: 6292)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 6496)
- powershell.exe (PID: 6820)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 1576)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 1192)
- cmd.exe (PID: 6764)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6636)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 6496)
- cmd.exe (PID: 6208)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6636)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 6496)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 1192)
Hides command output
- cmd.exe (PID: 6804)
- cmd.exe (PID: 4556)
- cmd.exe (PID: 6496)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 6096)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 2120)
- cmd.exe (PID: 1576)
- cmd.exe (PID: 5752)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 6540)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 3220)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 1740)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 3808)
- cmd.exe (PID: 1536)
- cmd.exe (PID: 1192)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 5872)
- cmd.exe (PID: 6196)
- cmd.exe (PID: 4160)
- cmd.exe (PID: 5268)
- cmd.exe (PID: 6764)
- cmd.exe (PID: 4840)
- cmd.exe (PID: 6544)
- cmd.exe (PID: 4012)
Get information on the list of running processes
- cmd.exe (PID: 6804)
- cmd.exe (PID: 6208)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6208)
- cmd.exe (PID: 1536)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 3576)
- cmd.exe (PID: 6208)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 6820)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3632)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 4840)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6820)
Executable content was dropped or overwritten
- powershell.exe (PID: 5464)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 6208)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5464)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5464)
INFO
Checks operating system version
- cmd.exe (PID: 6292)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 6208)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 6764)
- powershell.exe (PID: 6796)
- powershell.exe (PID: 4500)
- powershell.exe (PID: 5464)
The process uses the downloaded file
- powershell.exe (PID: 6956)
Checks supported languages
- mode.com (PID: 6588)
Starts MODE.COM to configure console settings
- mode.com (PID: 6588)
- mode.com (PID: 6608)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3984)
Reads Microsoft Office registry keys
- reg.exe (PID: 5732)
Creates files in the program directory
- cmd.exe (PID: 6208)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1304)
The sample compiled with english language support
- powershell.exe (PID: 5464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
761
Monitored processes
633
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | reg query HKU\DEFTEMP-1078\Software | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | reg query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\15.0\ClickToRun /v InstallPath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | find /i "computersystem" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
119 269
Read events
119 254
Write events
3
Delete events
12
Modification events
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\BootTimeSkuOverride |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\CachedLicenseData |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\CurrentSkuIdAggregationForApp |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\LastKnownC2RProductReleaseId |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\LicensingNext |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing\OlsToken |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Licensing |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6232) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Identity\ServiceAuthInfoCache\CredStoreKeyToAuthScheme |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6232) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Identity\ServiceAuthInfoCache |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6232) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Identity |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
2
Suspicious files
1
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uhdalct1.mmv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4428 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mti2yu2i.lv1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lfoovpfl.4nf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7024 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p3yo5t1e.ztz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_31aigxhp.0bd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xvqwzs0z.qsw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0unhz2it.bbt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6184 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lbh5rhnr.do5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6184 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wfb4hc4r.qlh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nndimieo.0q1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
32
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6544 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6440 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6440 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1852 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.154:443 | — | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1852 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.209.156:443 | — | Akamai International B.V. | GB | unknown |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
updatecheck.massgrave.dev |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |