| File name: | Lab2_01.exe |
| Full analysis: | https://app.any.run/tasks/9b76338e-7082-4da2-9137-4affd90d1b5b |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2024, 09:32:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C25E1B4F2BB13F24FFCFB66342D895F6 |
| SHA1: | 3B29C36CCB0FD00A0812896E61D3AE6CE18E5EEE |
| SHA256: | E447EE50D538C0F54CF1106EDB0D52FA6A7A2A23C63D765968857036D35D9CFD |
| SSDEEP: | 6144:eqT5dlSRVZo5RVYUn+GSC8CJBBT+MKe2ywkkBO+q/Qah1HF:DNdlSRVZK7zn+wTIbywbq/Qah1l |
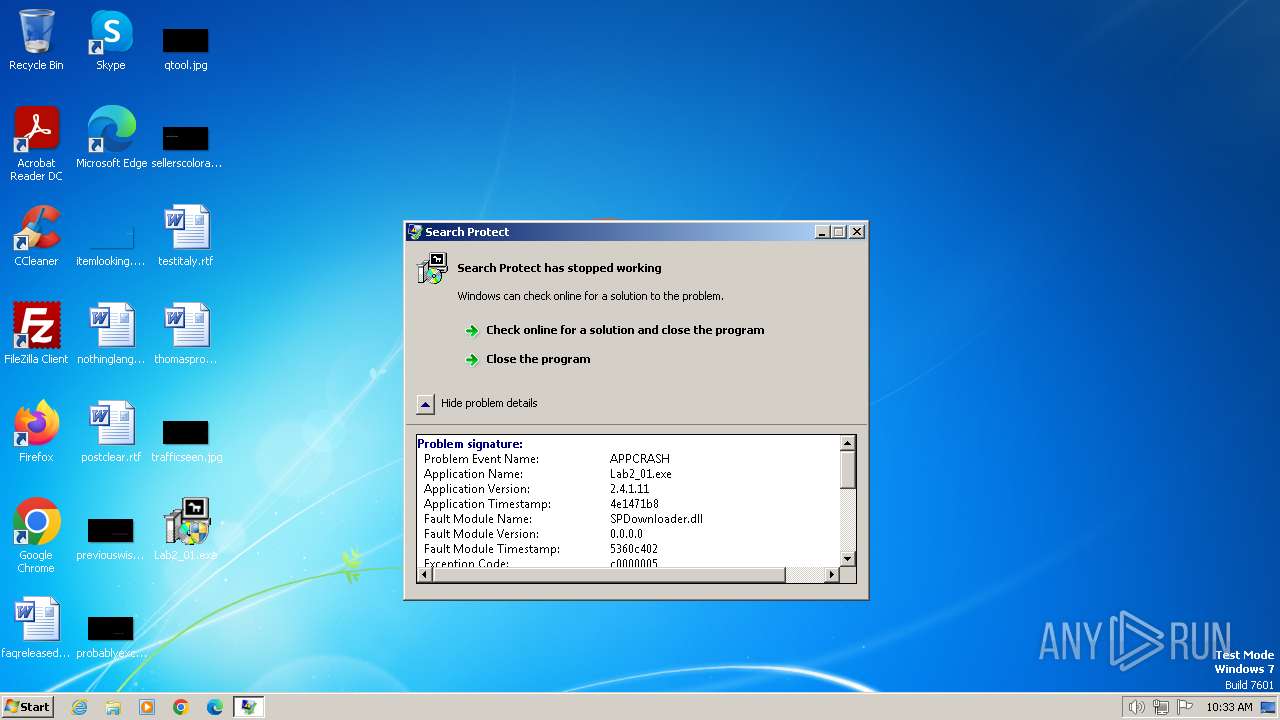
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- Lab2_01.exe (PID: 2720)
Malware-specific behavior (creating "System.dll" in Temp)
- Lab2_01.exe (PID: 2720)
- Lab2_01.exe (PID: 3012)
- Lab2_01.exe (PID: 2292)
Executable content was dropped or overwritten
- Lab2_01.exe (PID: 2720)
- Lab2_01.exe (PID: 3012)
- Lab2_01.exe (PID: 2292)
Potential Corporate Privacy Violation
- Lab2_01.exe (PID: 2720)
- Lab2_01.exe (PID: 3012)
- Lab2_01.exe (PID: 2292)
INFO
Checks supported languages
- Lab2_01.exe (PID: 2720)
Manual execution by a user
- wmpnscfg.exe (PID: 2200)
- Lab2_01.exe (PID: 3012)
- Lab2_01.exe (PID: 3496)
- Lab2_01.exe (PID: 3868)
- Lab2_01.exe (PID: 2292)
Reads the computer name
- Lab2_01.exe (PID: 2720)
Create files in a temporary directory
- Lab2_01.exe (PID: 2720)
Reads the machine GUID from the registry
- Lab2_01.exe (PID: 2720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:07:06 14:31:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 25600 |
| InitializedDataSize: | 431104 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x354b |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.4.1.11 |
| ProductVersionNumber: | 2.4.1.11 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Client Connect |
| FileDescription: | Search Protect |
| FileVersion: | 2.4.1.11 |
| LegalCopyright: | © 2014 Client Connect Ltd. |
Total processes
58
Monitored processes
7
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2200 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\Desktop\Lab2_01.exe" | C:\Users\admin\Desktop\Lab2_01.exe | explorer.exe | ||||||||||||
User: admin Company: Client Connect Integrity Level: HIGH Description: Search Protect Version: 2.4.1.11 Modules
| |||||||||||||||
| 2720 | "C:\Users\admin\Desktop\Lab2_01.exe" | C:\Users\admin\Desktop\Lab2_01.exe | explorer.exe | ||||||||||||
User: admin Company: Client Connect Integrity Level: HIGH Description: Search Protect Exit code: 3221225477 Version: 2.4.1.11 Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\Desktop\Lab2_01.exe" | C:\Users\admin\Desktop\Lab2_01.exe | — | explorer.exe | |||||||||||
User: admin Company: Client Connect Integrity Level: MEDIUM Description: Search Protect Exit code: 3221226540 Version: 2.4.1.11 Modules
| |||||||||||||||
| 3012 | "C:\Users\admin\Desktop\Lab2_01.exe" | C:\Users\admin\Desktop\Lab2_01.exe | explorer.exe | ||||||||||||
User: admin Company: Client Connect Integrity Level: HIGH Description: Search Protect Exit code: 3221225477 Version: 2.4.1.11 Modules
| |||||||||||||||
| 3496 | "C:\Users\admin\Desktop\Lab2_01.exe" | C:\Users\admin\Desktop\Lab2_01.exe | — | explorer.exe | |||||||||||
User: admin Company: Client Connect Integrity Level: MEDIUM Description: Search Protect Exit code: 3221226540 Version: 2.4.1.11 Modules
| |||||||||||||||
| 3868 | "C:\Users\admin\Desktop\Lab2_01.exe" | C:\Users\admin\Desktop\Lab2_01.exe | — | explorer.exe | |||||||||||
User: admin Company: Client Connect Integrity Level: MEDIUM Description: Search Protect Exit code: 3221226540 Version: 2.4.1.11 Modules
| |||||||||||||||
Total events
1 857
Read events
1 708
Write events
126
Delete events
23
Modification events
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (2720) Lab2_01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
18
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2720 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nshD5BC\SpSetup.txt | executable | |
MD5:2496C5295948C58519E6B4E5781364D4 | SHA256:FFF8E96C75AE538C93BC2F82D3C0E867A2E515689A6709FCF880F941598B20C3 | |||
| 2720 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nsjCD01.tmp\StubUtils.dll | executable | |
MD5:4F8222C1FB3F1575E225697E4ADF5D64 | SHA256:FECE9A45AF4798313886C2438030874F36CF3FA93EF93BA00E1285519C13F4D0 | |||
| 3012 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nsc22B1.tmp | binary | |
MD5:B5EEAF903E1DC8519C12067211DAB353 | SHA256:DB7C61F0B55CA5BFBC210D0C65080E59F740ED66B38DE5E82E414709DD4450C1 | |||
| 2292 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nsg6C3E.tmp\System.dll | executable | |
MD5:5CCDE6CBE28A74C393F2B7B6F5CC7458 | SHA256:2C2DB6B7CA5781A34C30C42C18EC1ECE1284B8D500FD0251FA383FD7B1EEB6E0 | |||
| 2720 | Lab2_01.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\OrbiterInstaller[1].exe | executable | |
MD5:2496C5295948C58519E6B4E5781364D4 | SHA256:FFF8E96C75AE538C93BC2F82D3C0E867A2E515689A6709FCF880F941598B20C3 | |||
| 3012 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nss22C2.tmp\SPDownloader.dll | executable | |
MD5:29F0F05AD153341D5FF3D757F37CBAB7 | SHA256:78B6A269BEBB7686A588F41A57C271C0EF10130055D2AAFB749F4D53B83A0A02 | |||
| 2292 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nsg6C3E.tmp\StubUtils.dll | executable | |
MD5:4F8222C1FB3F1575E225697E4ADF5D64 | SHA256:FECE9A45AF4798313886C2438030874F36CF3FA93EF93BA00E1285519C13F4D0 | |||
| 2292 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nsg6C3E.tmp\inetc.dll | executable | |
MD5:8326B29343614F3DB9D8E3DA200BDE36 | SHA256:7A438BFFDCADE504D71CA822CBD852D4F99F9A257493031E7340EEC0D0D44172 | |||
| 2292 | Lab2_01.exe | C:\Users\admin\AppData\Local\Temp\nsg6C3E.tmp\SPDownloader.dll | executable | |
MD5:29F0F05AD153341D5FF3D757F37CBAB7 | SHA256:78B6A269BEBB7686A588F41A57C271C0EF10130055D2AAFB749F4D53B83A0A02 | |||
| 2292 | Lab2_01.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\OrbiterInstaller[1].exe | executable | |
MD5:2496C5295948C58519E6B4E5781364D4 | SHA256:FFF8E96C75AE538C93BC2F82D3C0E867A2E515689A6709FCF880F941598B20C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
5
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2720 | Lab2_01.exe | GET | 200 | 54.159.253.65:80 | http://sp-download.spccint.com/download/CarrierId/DEFAULT/CarrierVersion/DEFAULT/CarrierType/DEFAULT/Brand/SP | unknown | — | — | unknown |
3012 | Lab2_01.exe | GET | 200 | 54.159.253.65:80 | http://sp-download.spccint.com/download/CarrierId/DEFAULT/CarrierVersion/DEFAULT/CarrierType/DEFAULT/Brand/SP | unknown | — | — | unknown |
2292 | Lab2_01.exe | GET | 200 | 54.159.253.65:80 | http://sp-download.spccint.com/download/CarrierId/DEFAULT/CarrierVersion/DEFAULT/CarrierType/DEFAULT/Brand/SP | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
2720 | Lab2_01.exe | 54.159.253.65:80 | sp-download.spccint.com | AMAZON-AES | US | suspicious |
3012 | Lab2_01.exe | 54.159.253.65:80 | sp-download.spccint.com | AMAZON-AES | US | suspicious |
1616 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2292 | Lab2_01.exe | 54.159.253.65:80 | sp-download.spccint.com | AMAZON-AES | US | suspicious |
1620 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
sp-installer.databssint.com |
| unknown |
sp-download.spccint.com |
| unknown |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2720 | Lab2_01.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2720 | Lab2_01.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2720 | Lab2_01.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3012 | Lab2_01.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3012 | Lab2_01.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3012 | Lab2_01.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2292 | Lab2_01.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2292 | Lab2_01.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2292 | Lab2_01.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |