| File name: | Win11Debloat-master (1).zip |
| Full analysis: | https://app.any.run/tasks/9604f2da-add0-4252-ae32-ce3ed8989554 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 19:14:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 0D0CD950101BA2EBD3E5A6B80284FCAA |
| SHA1: | 406485C7E578E601578E6EBAA54EEC3D815418E1 |
| SHA256: | E42CC30284975B9CC50BC9F10DAF39B87527D1960444B3C737E1BF54070F0CF5 |
| SSDEEP: | 3072:r4lD1sAryxD/rNVEwbdFlaiB/lAEOHvpuxQzZ:rMyxDXdFlaiB/lEcCt |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7516)
- powershell.exe (PID: 7796)
Changes powershell execution policy (Bypass)
- WinRAR.exe (PID: 6048)
- powershell.exe (PID: 7516)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6048)
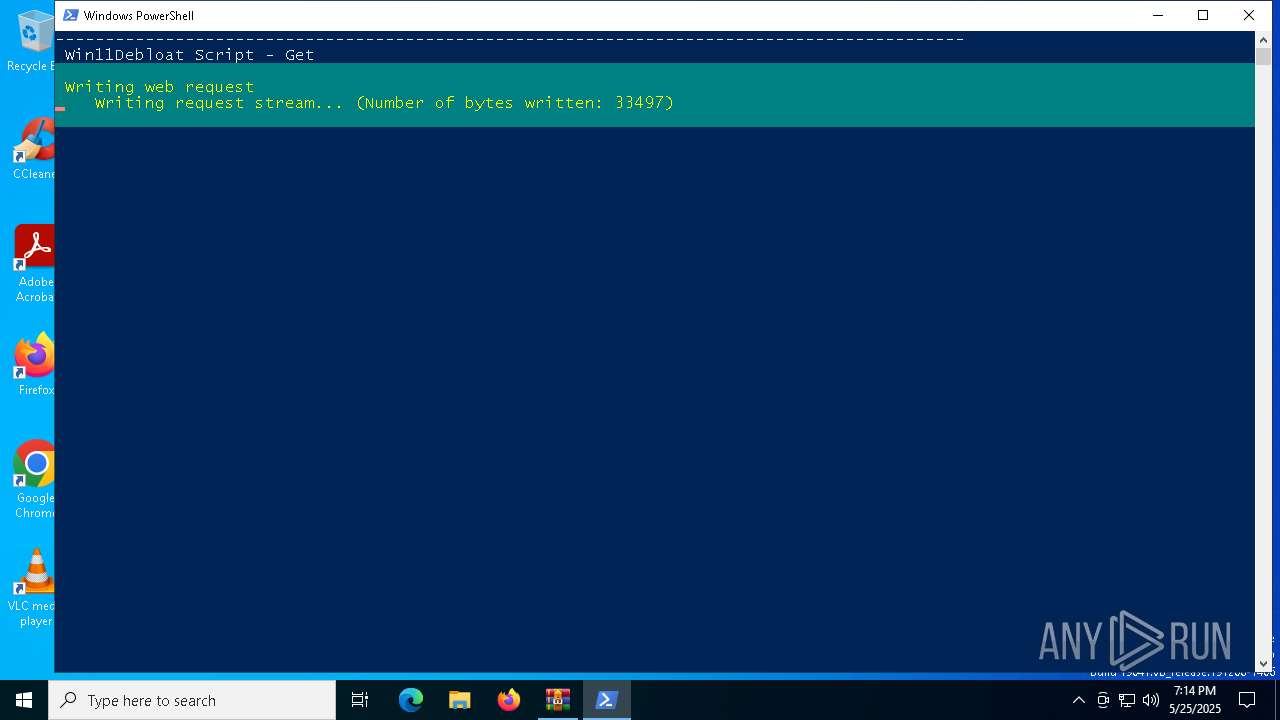
The process executes Powershell scripts
- WinRAR.exe (PID: 6048)
- powershell.exe (PID: 7516)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 6048)
- powershell.exe (PID: 7516)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 7516)
Application launched itself
- powershell.exe (PID: 7516)
Executes as Windows Service
- VSSVC.exe (PID: 5556)
Searches for installed software
- dllhost.exe (PID: 4980)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 4188)
- DismHost.exe (PID: 3268)
- DismHost.exe (PID: 5600)
- DismHost.exe (PID: 4944)
- DismHost.exe (PID: 6652)
- DismHost.exe (PID: 4436)
- DismHost.exe (PID: 8104)
- DismHost.exe (PID: 1052)
- DismHost.exe (PID: 8176)
- DismHost.exe (PID: 896)
Executable content was dropped or overwritten
- powershell.exe (PID: 7796)
Process drops legitimate windows executable
- powershell.exe (PID: 7796)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6048)
Disables trace logs
- powershell.exe (PID: 7516)
Checks proxy server information
- powershell.exe (PID: 7516)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7516)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7516)
- powershell.exe (PID: 7796)
Manages system restore points
- SrTasks.exe (PID: 7444)
The sample compiled with english language support
- powershell.exe (PID: 7796)
The executable file from the user directory is run by the Powershell process
- DismHost.exe (PID: 6652)
- DismHost.exe (PID: 3268)
- DismHost.exe (PID: 4188)
- DismHost.exe (PID: 4944)
- DismHost.exe (PID: 5600)
- DismHost.exe (PID: 4436)
- DismHost.exe (PID: 8176)
- DismHost.exe (PID: 8104)
- DismHost.exe (PID: 1052)
- DismHost.exe (PID: 896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:21 12:57:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Win11Debloat-master/ |
Total processes
156
Monitored processes
21
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | C:\Users\admin\AppData\Local\Temp\F753FA58-B8B4-464E-998B-CE64F57E674A\dismhost.exe {5D130E53-EC59-42BB-8E29-2D2E12988FA6} | C:\Users\admin\AppData\Local\Temp\F753FA58-B8B4-464E-998B-CE64F57E674A\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | C:\Users\admin\AppData\Local\Temp\6D4384D8-9271-4028-94D0-D5B3BB725C73\dismhost.exe {D53B1F3F-8A9A-4CBD-93F2-D0F0A1676706} | C:\Users\admin\AppData\Local\Temp\6D4384D8-9271-4028-94D0-D5B3BB725C73\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | C:\Users\admin\AppData\Local\Temp\B0B85844-51EE-4660-B2C9-5144CC2290CF\dismhost.exe {4E55D916-30DA-4E8A-9A62-B76C56EA4B35} | C:\Users\admin\AppData\Local\Temp\B0B85844-51EE-4660-B2C9-5144CC2290CF\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4188 | C:\Users\admin\AppData\Local\Temp\E44D27E3-4B40-4064-ADD4-010C9952E5CE\dismhost.exe {D3D9ECB0-81EA-4B32-B0D4-98E0A149CA35} | C:\Users\admin\AppData\Local\Temp\E44D27E3-4B40-4064-ADD4-010C9952E5CE\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4436 | C:\Users\admin\AppData\Local\Temp\91EA0E66-6087-452B-8E66-CD550EE80B5D\dismhost.exe {E59264DB-4158-4A3A-838E-7416B111225D} | C:\Users\admin\AppData\Local\Temp\91EA0E66-6087-452B-8E66-CD550EE80B5D\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | C:\Users\admin\AppData\Local\Temp\ACE5FAB6-5BC3-43EB-BCD7-C5D75E3DE2BF\dismhost.exe {389EEC64-F53F-4457-B39D-E0DA8F15FBE0} | C:\Users\admin\AppData\Local\Temp\ACE5FAB6-5BC3-43EB-BCD7-C5D75E3DE2BF\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4980 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5600 | C:\Users\admin\AppData\Local\Temp\BD4BAC18-DD41-42BD-A791-AC60B860899C\dismhost.exe {2EB0AE67-C768-404C-B75F-5BD7C4C45473} | C:\Users\admin\AppData\Local\Temp\BD4BAC18-DD41-42BD-A791-AC60B860899C\DismHost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Win11Debloat-master (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
19 116
Read events
18 905
Write events
193
Delete events
18
Modification events
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Win11Debloat-master (1).zip | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ps1\OpenWithProgids |
| Operation: | write | Name: | Microsoft.PowerShellConsole.1 |
Value: | |||
| (PID) Process: | (4980) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000001E591049A9CDDB017413000094100000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
528
Suspicious files
11
Text files
131
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x5wx3zks.awg.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7516 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10d35f.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Win11Debloat\Raphire-Win11Debloat-44c28be\.github\ISSUE_TEMPLATE\feature_request.md | text | |
MD5:174545E1D9DAFF8020525FDD1E020411 | SHA256:1F48C52F209A971B8E7EAE4120144D28FCF8EE38A7778A7B4D8CF1AB356617D2 | |||
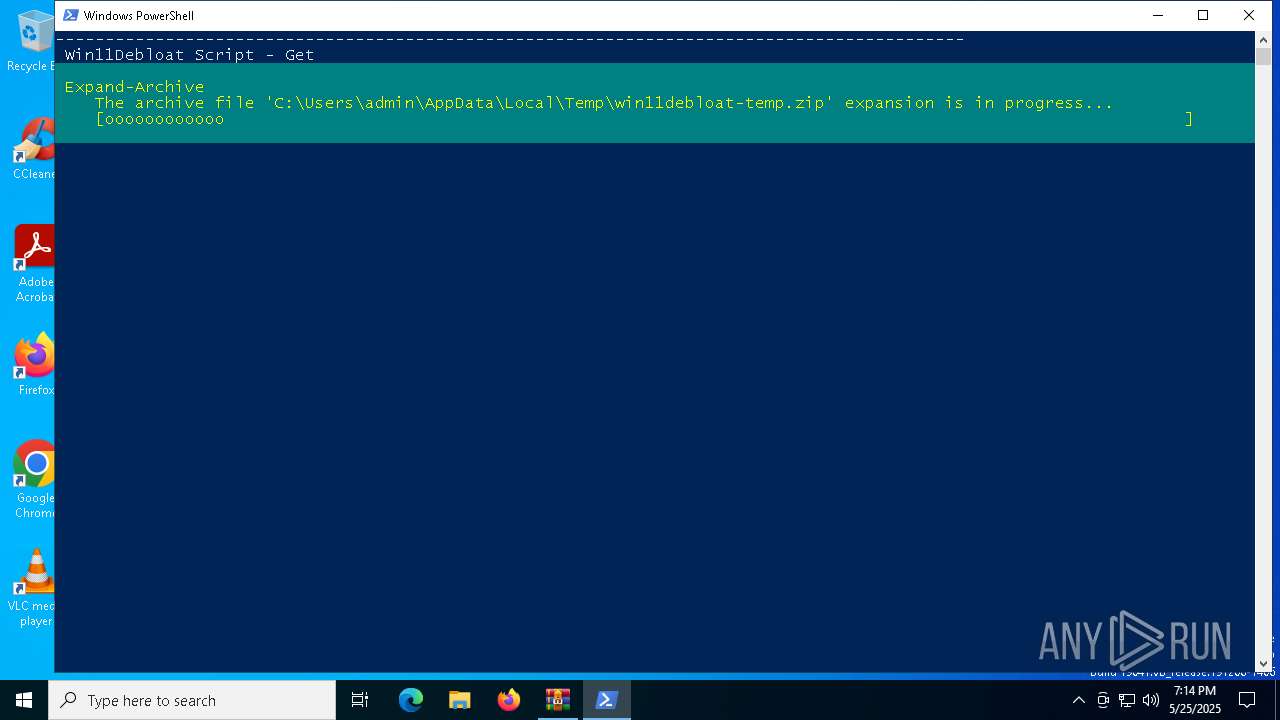
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\win11debloat-temp.zip | compressed | |
MD5:FA61AC2734DECD8D03BCE15681B54787 | SHA256:79711A9ED7467CDEDAEC7DD5AA973D73DB5B398892E80A4F5E7F96611184157E | |||
| 6048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6048.27470\Get.ps1 | text | |
MD5:3B020AF4219AC1528A39D379F9B29472 | SHA256:8028470BB6F664DDD91E89191704A38B2CB51F9E55F3115B2319AD9ABF98E74F | |||
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Win11Debloat\Raphire-Win11Debloat-44c28be\.github\FUNDING.yml | text | |
MD5:CE14B493F9279DE26175B9F3B3453B2B | SHA256:2230EA5712492396FE26C35023D05B560213B19C8247AE6289F3FE6663C088CE | |||
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Win11Debloat\Raphire-Win11Debloat-44c28be\.github\ISSUE_TEMPLATE\bug_report.md | text | |
MD5:B2789232920B9E799162EAE6DA814073 | SHA256:6B8985DBAC1605AFAE6997A7EE8B3FC729D0DFC530E2E3D846825B88D53E5029 | |||
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Win11Debloat\Raphire-Win11Debloat-44c28be\Assets\Menus\DefaultSettings | text | |
MD5:650357F4EAF4B88F9A0091B23B7B444D | SHA256:33CB97F61F1F3C4A99B78844CF8C846F252CDC9AB0146F6518BB9727C62941F9 | |||
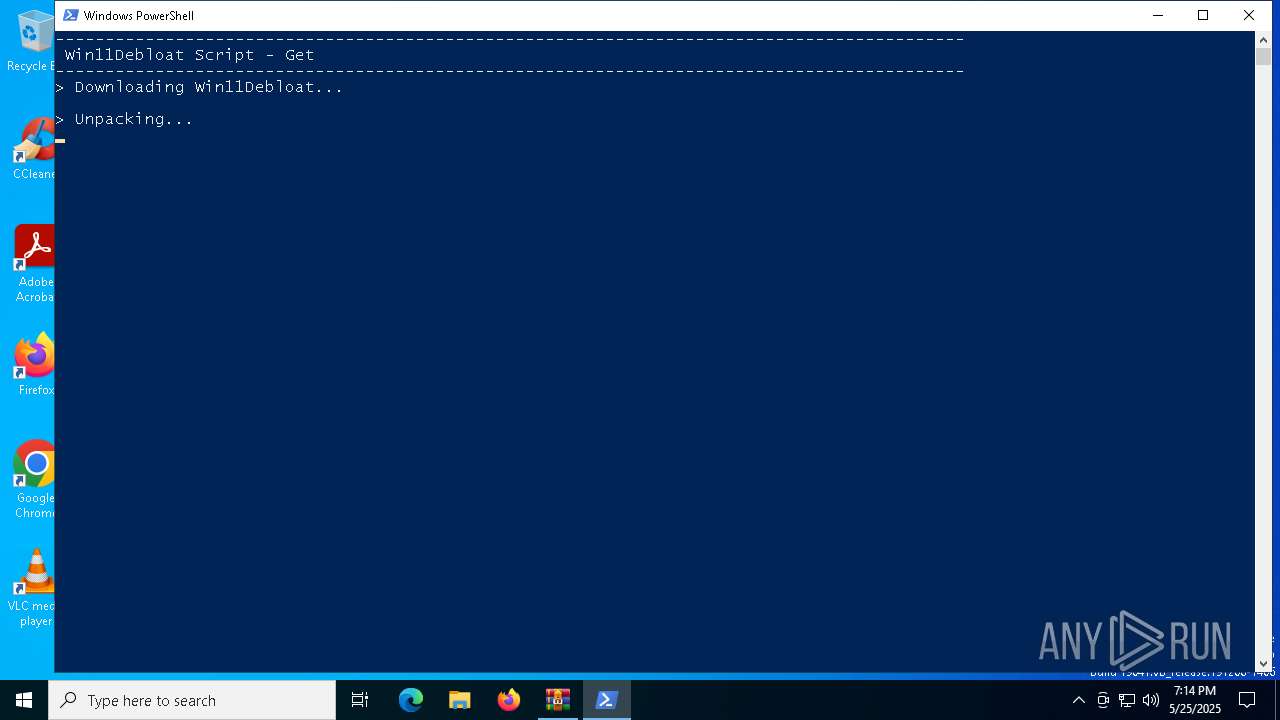
| 7516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Win11Debloat\Raphire-Win11Debloat-44c28be\Get.ps1 | text | |
MD5:CC710CFC860F86B86B479B267792FC73 | SHA256:3CCEF90A023328964995CE7007379B63894AA4CC76A759A7FC62A4BBA783F2AF | |||
| 7516 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:C03C92A29271DD4FE5EC2D87C5075978 | SHA256:E6343A3C0A09BEC26BB4BF3394E9A2D2647357908D45BEF792F98E709DDE2C42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8160 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8160 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7516 | powershell.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.com |
| whitelisted |
codeload.github.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |