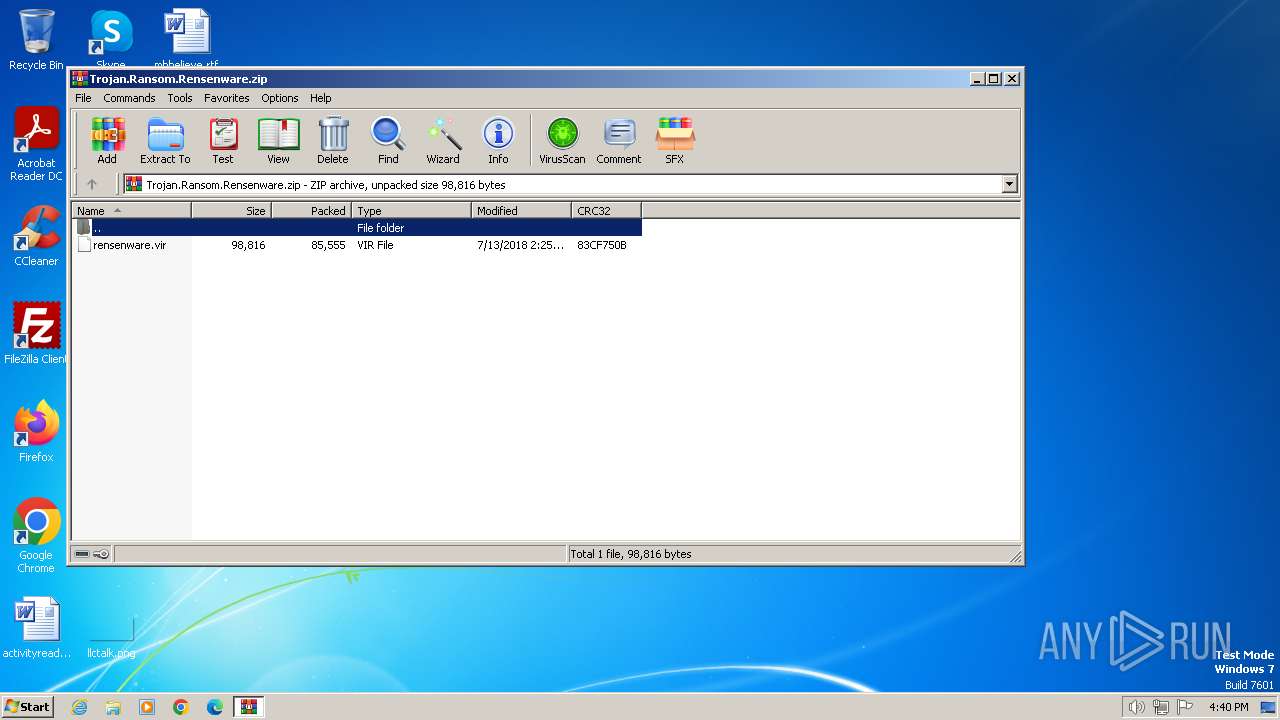
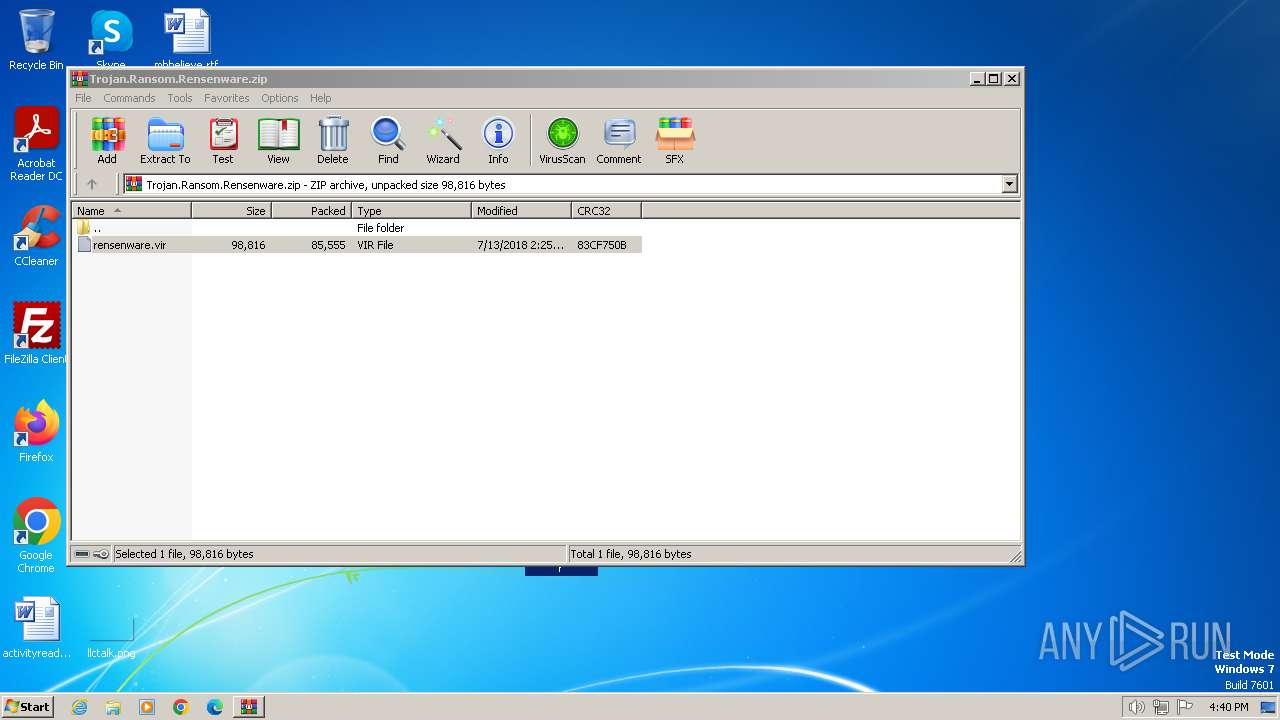
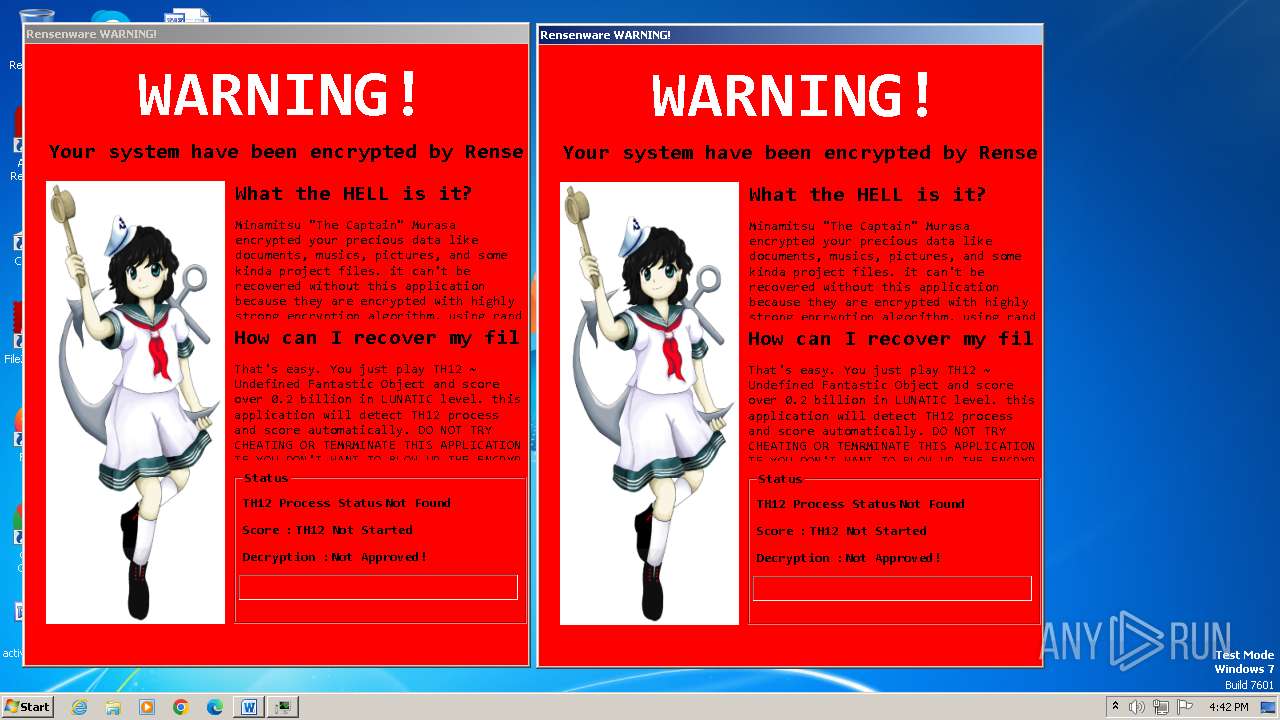
| File name: | Trojan.Ransom.Rensenware.zip |
| Full analysis: | https://app.any.run/tasks/11b9024a-031e-4999-a9c2-c5c0ed7103b5 |
| Verdict: | Malicious activity |
| Analysis date: | March 27, 2024, 16:40:30 |
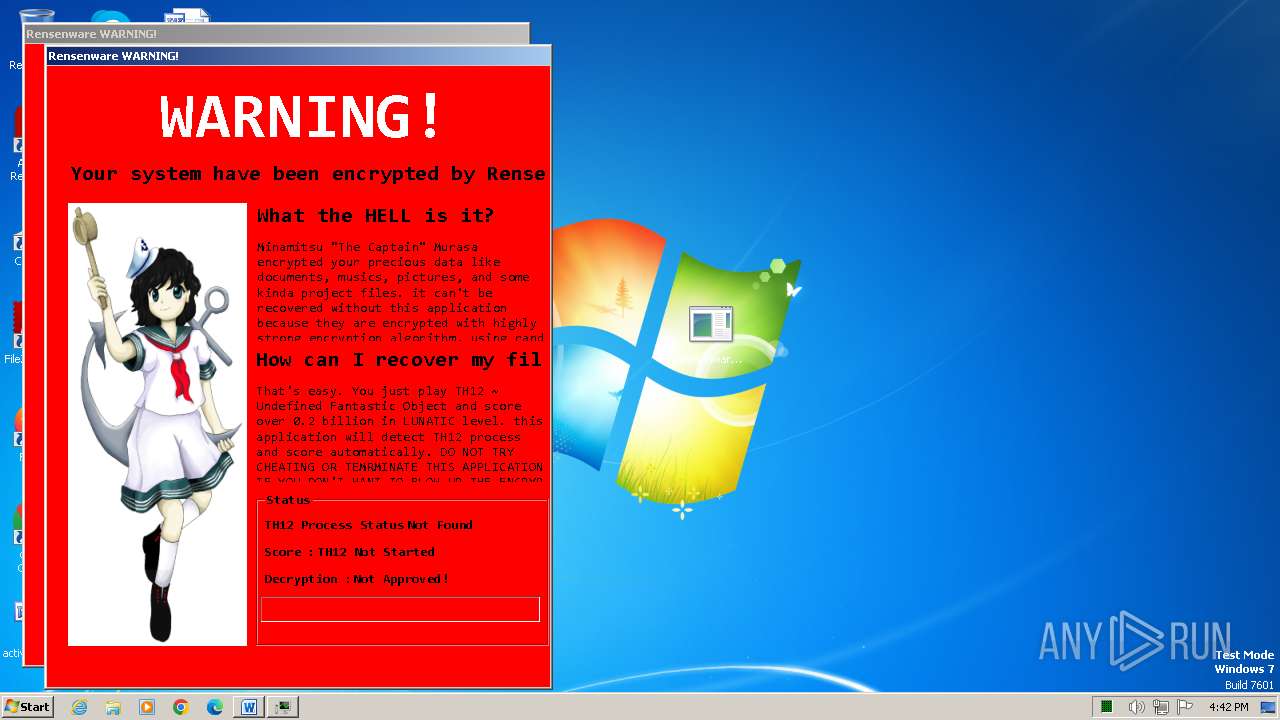
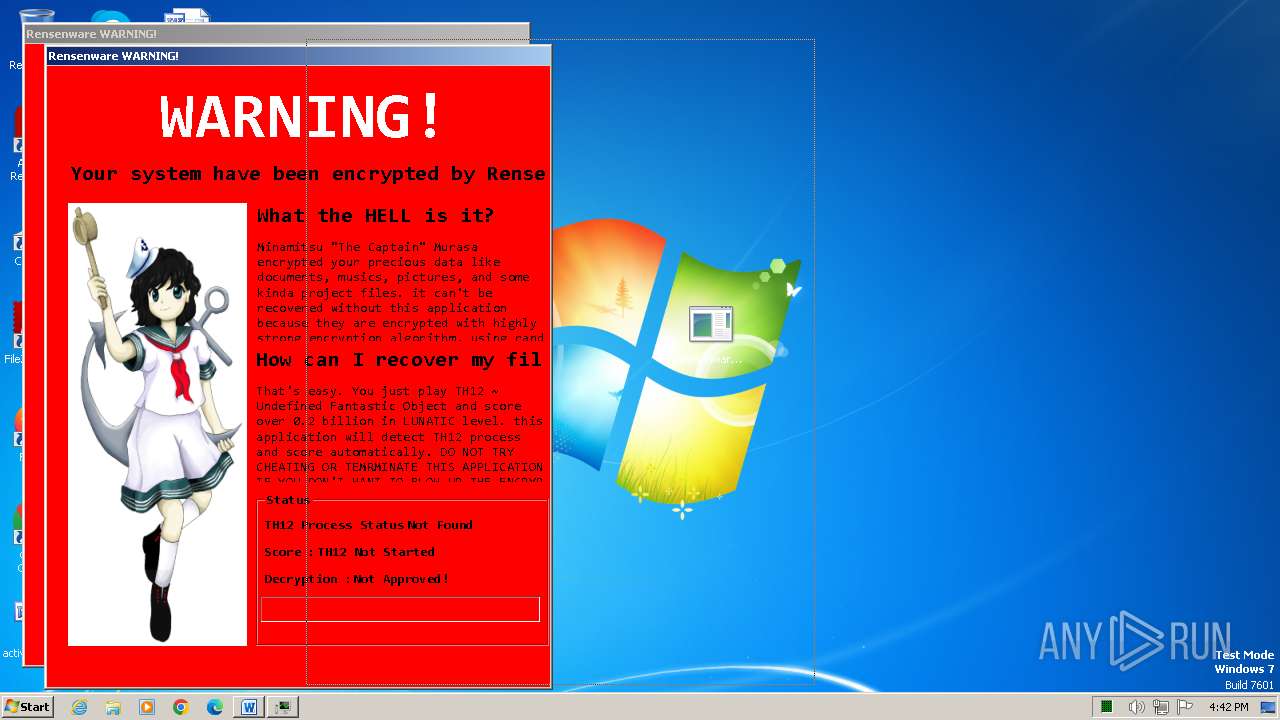
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 402482F136B96429DB19870DD8EAD97D |
| SHA1: | 5B111C52D8D5ED70ABD677CD8A94C6EA52D031B7 |
| SHA256: | E426F4B7D3F94F090D98A7BB23C55F907DF7BC251A0933C66E919DAF47D2109B |
| SSDEEP: | 1536:S4KW7qVPrtiPRIY2kCRraSf9DeqkJtuRkGw+gF1aDDCH4C3ZMyBtd9WdU:b7qVBi5KnmiypJtCkGwZ1EDKnDh |
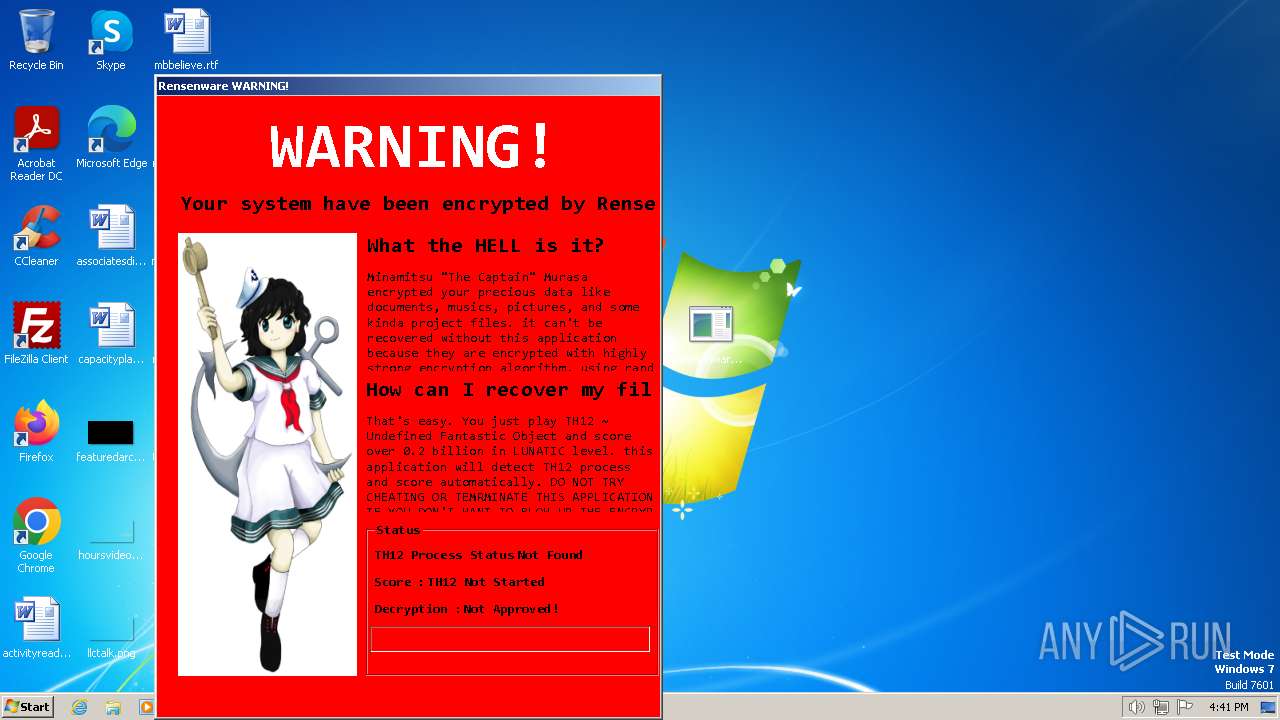
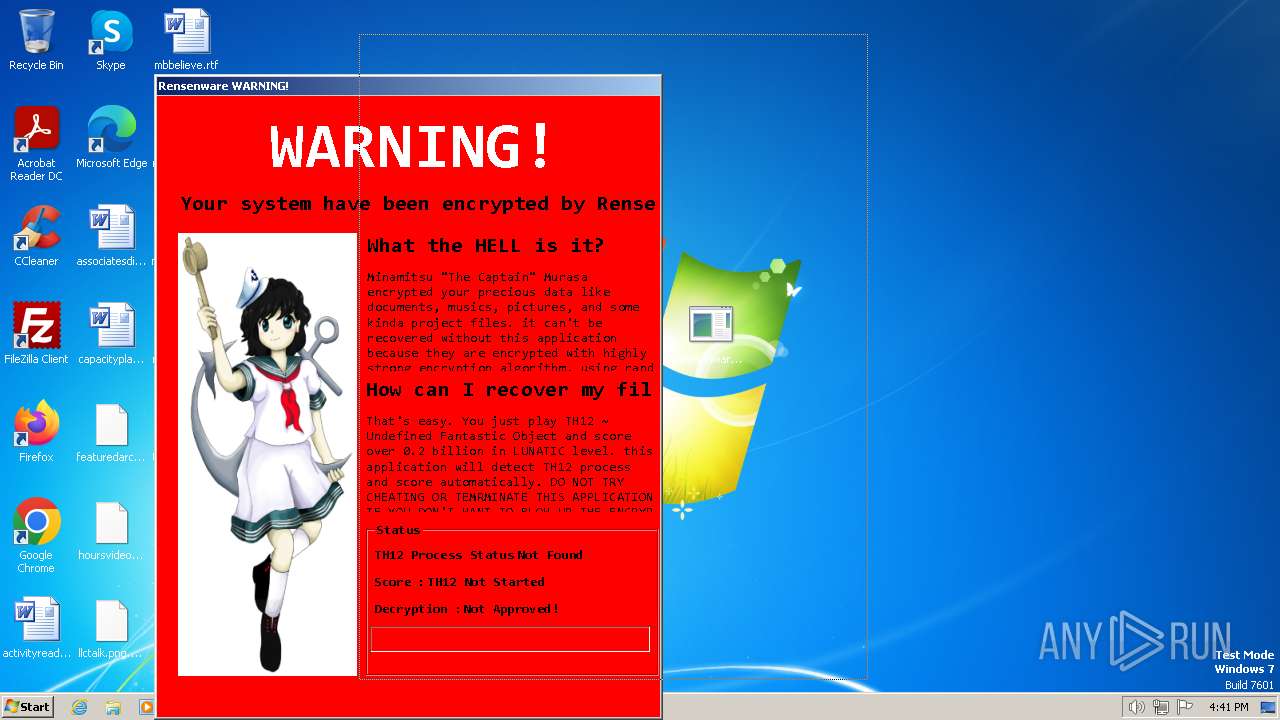
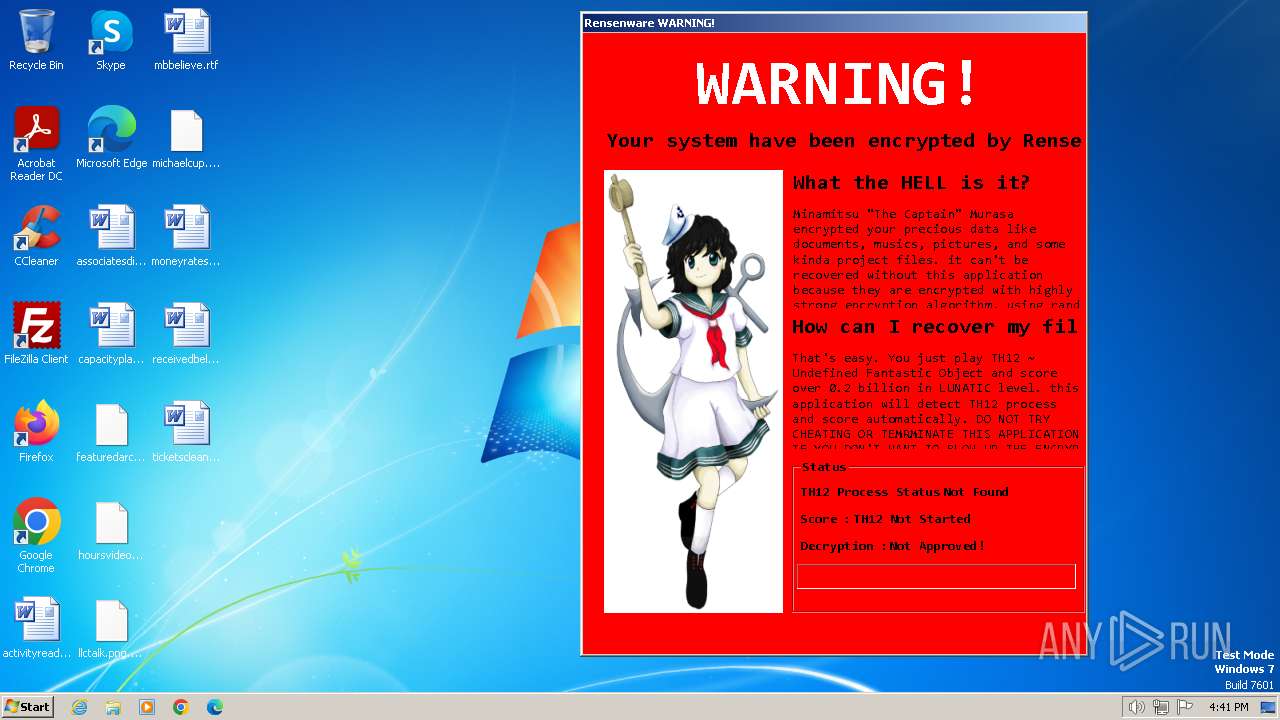
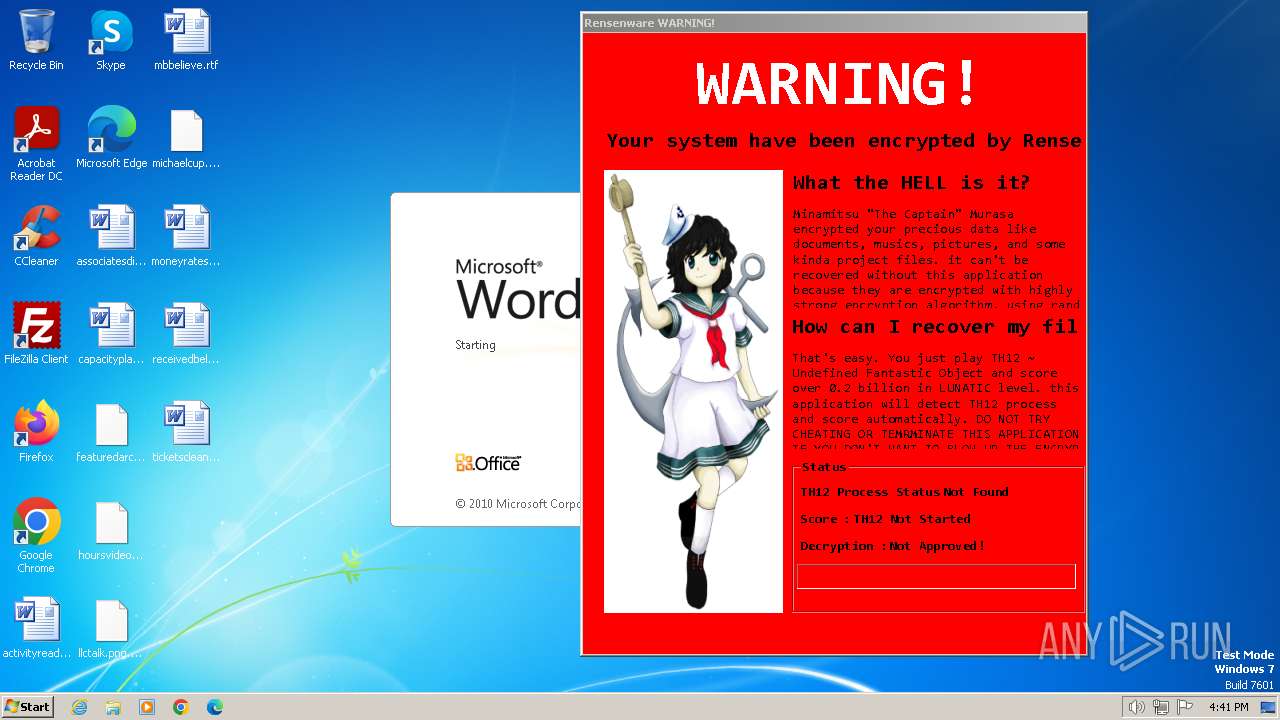
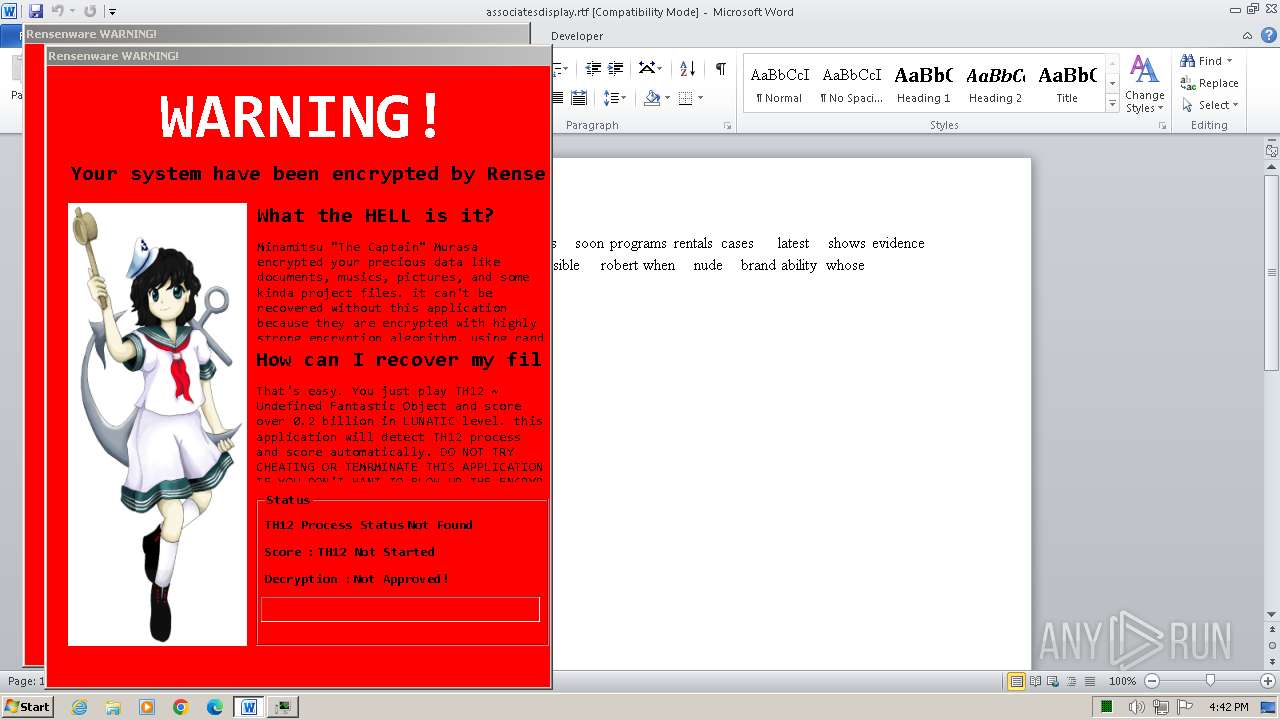
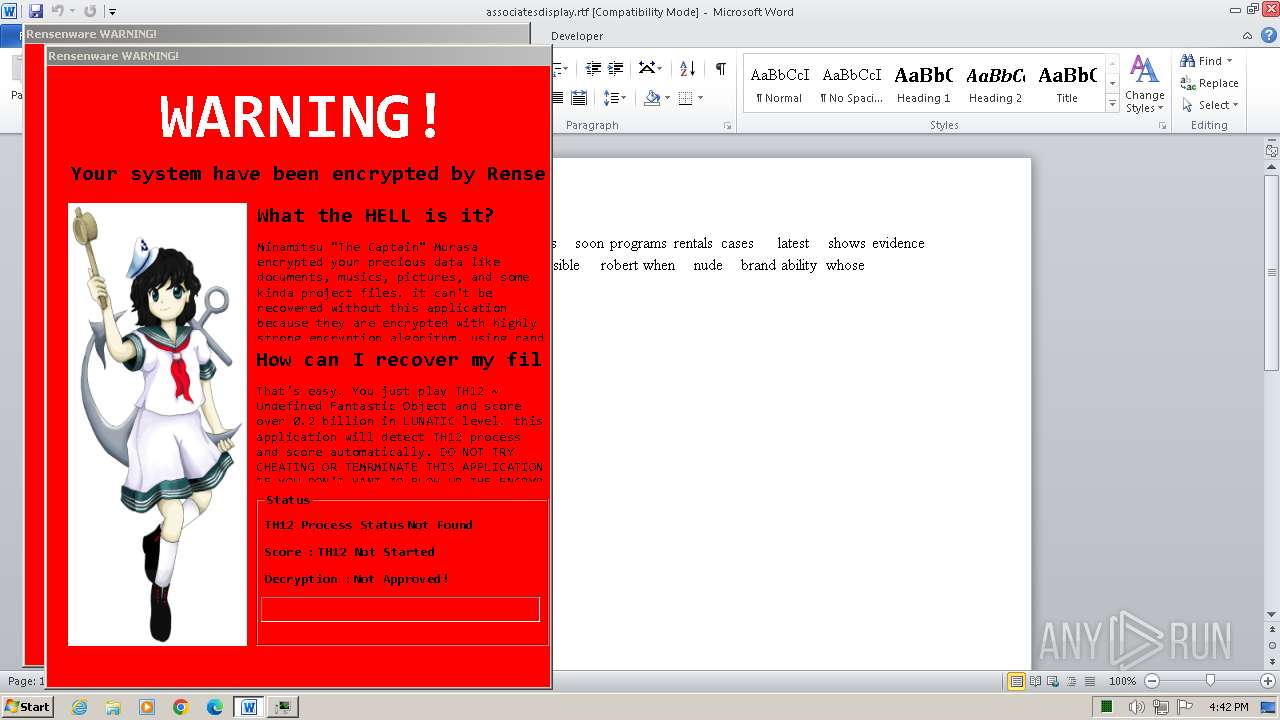
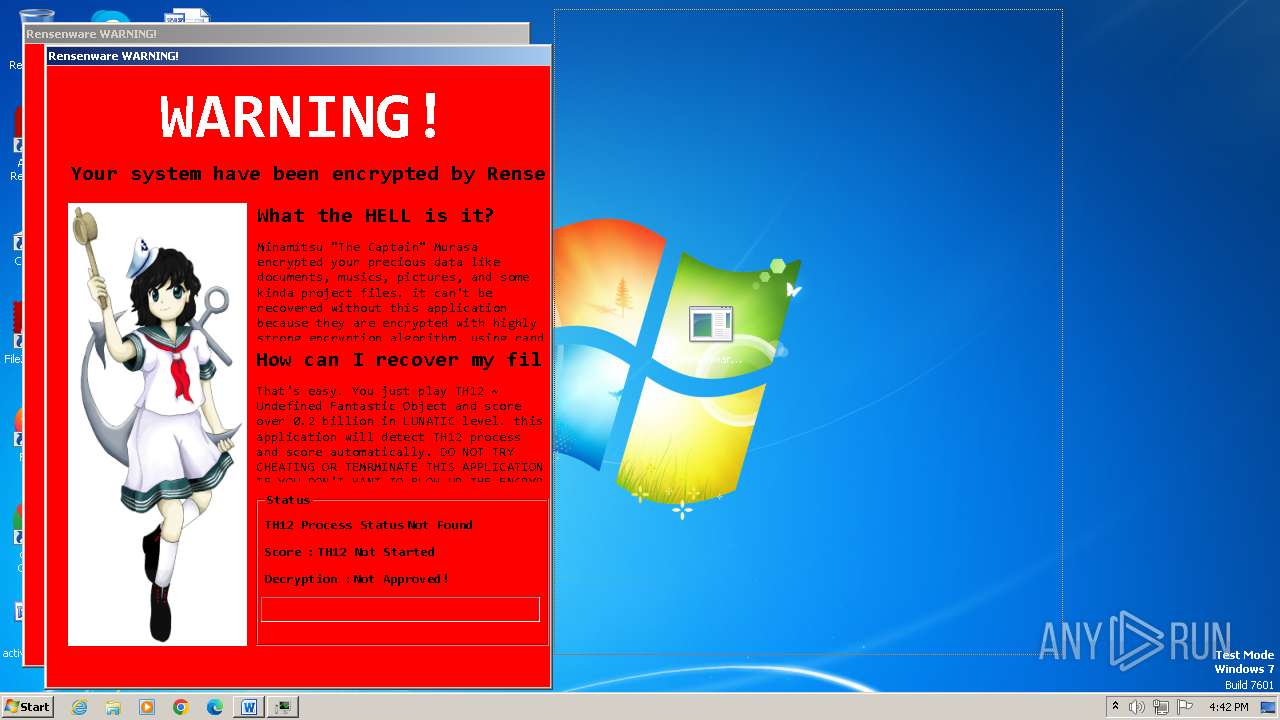
MALICIOUS
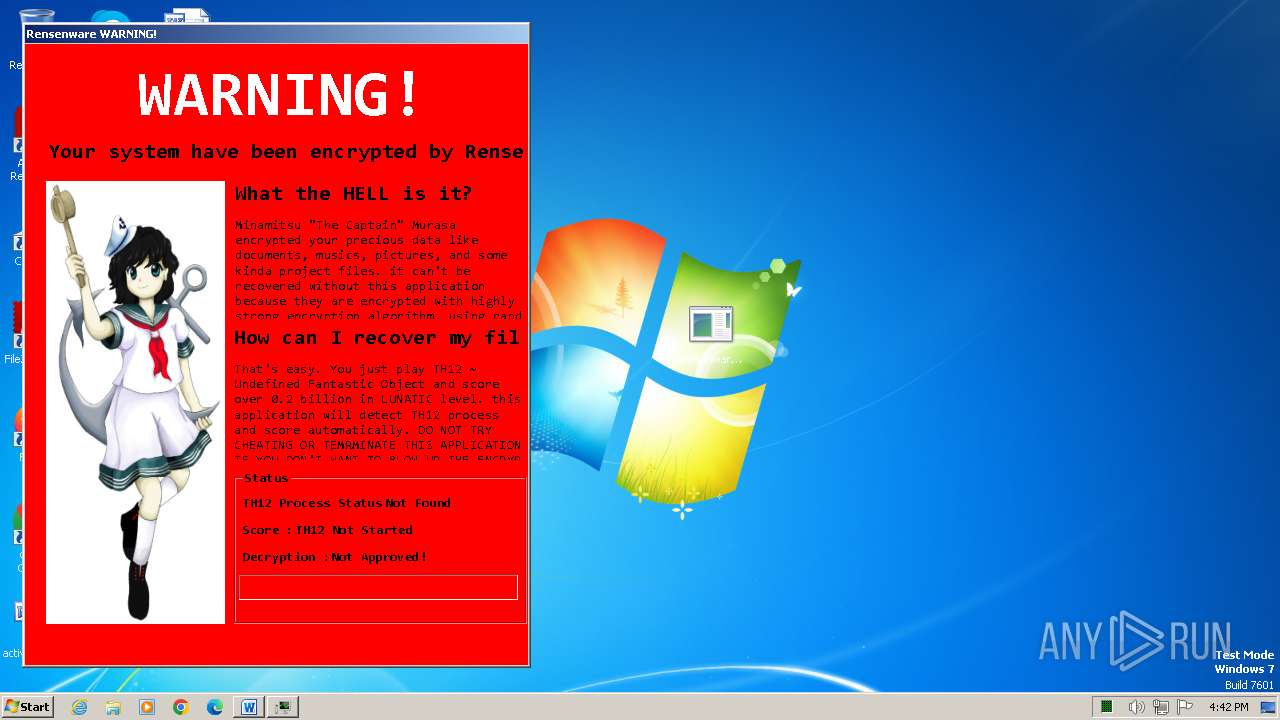
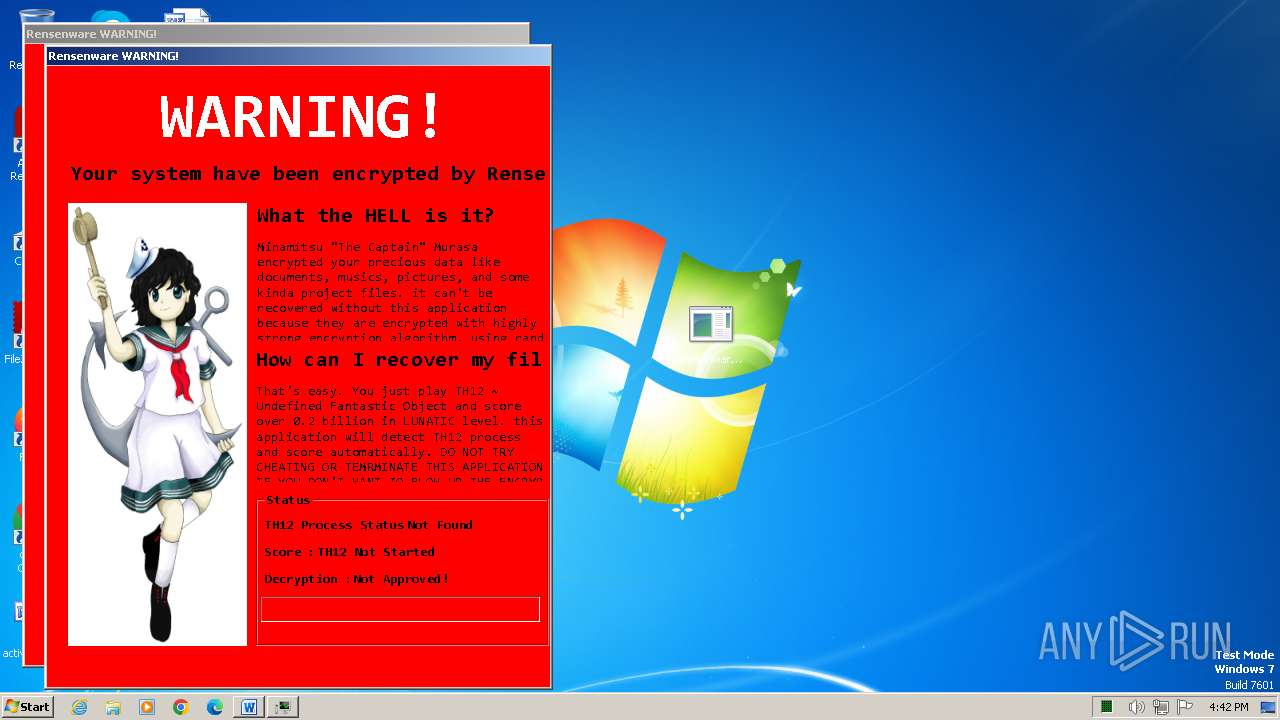
Actions looks like stealing of personal data
- rensenware.exe (PID: 2064)
- rensenware.exe (PID: 492)
- rensenware.exe (PID: 2248)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3956)
SUSPICIOUS
Non-standard symbols in registry
- WINWORD.EXE (PID: 1928)
INFO
Checks supported languages
- rensenware.exe (PID: 2064)
- rensenware.exe (PID: 492)
- rensenware.exe (PID: 2248)
Reads the machine GUID from the registry
- rensenware.exe (PID: 2064)
- rensenware.exe (PID: 492)
- rensenware.exe (PID: 2248)
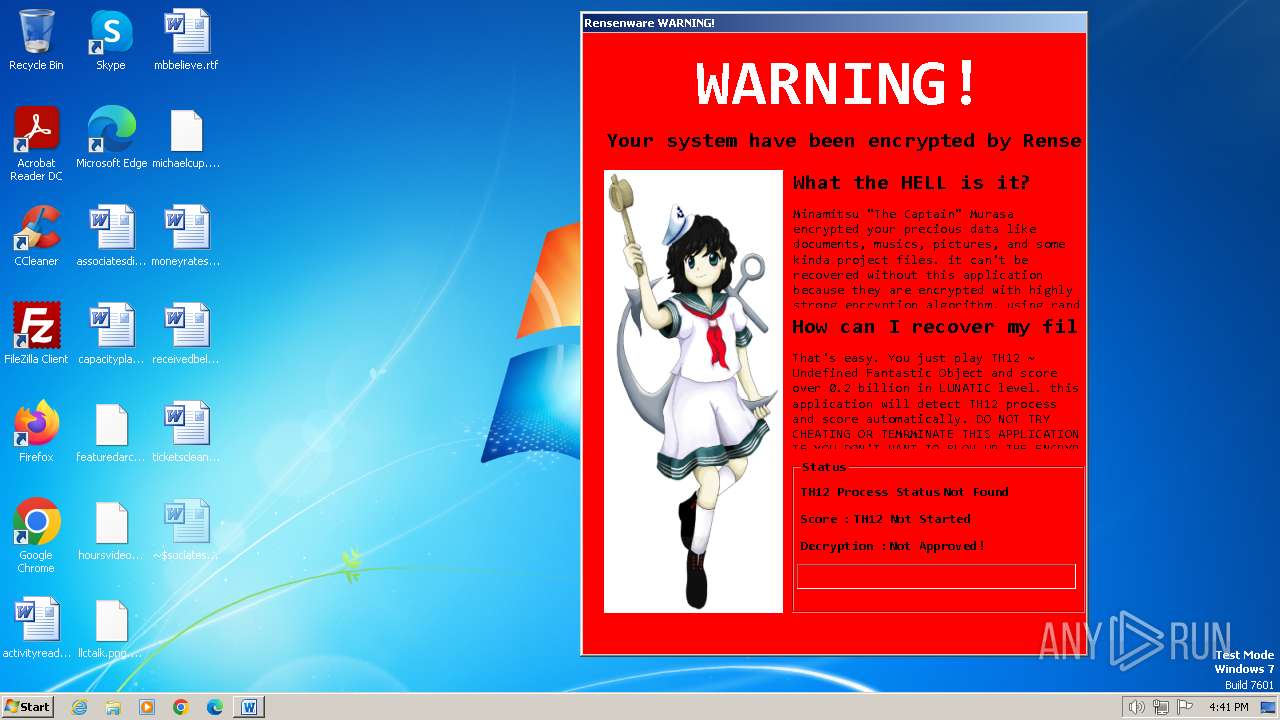
Manual execution by a user
- rensenware.exe (PID: 2064)
- WINWORD.EXE (PID: 1928)
- taskmgr.exe (PID: 2100)
- rensenware.exe (PID: 492)
- rensenware.exe (PID: 2248)
Reads the computer name
- rensenware.exe (PID: 2064)
- rensenware.exe (PID: 492)
- rensenware.exe (PID: 2248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:07:13 14:25:22 |
| ZipCRC: | 0x83cf750b |
| ZipCompressedSize: | 85555 |
| ZipUncompressedSize: | 98816 |
| ZipFileName: | rensenware.vir |
Total processes
45
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "C:\Users\admin\Desktop\rensenware.exe" | C:\Users\admin\Desktop\rensenware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Rensenware Application Version: 1.0.0.0 Modules
| |||||||||||||||
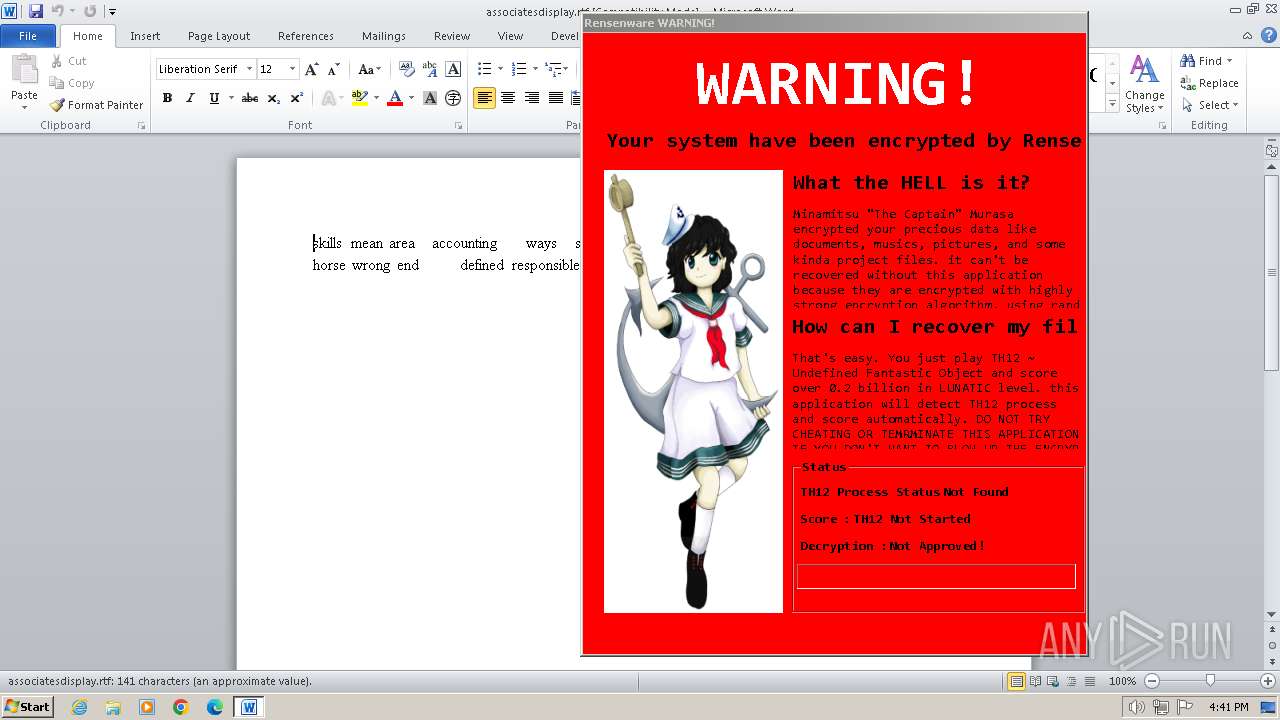
| 1928 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\associatesdisplay.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\rensenware.exe" | C:\Users\admin\Desktop\rensenware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Rensenware Application Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2100 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2248 | "C:\Users\admin\Desktop\rensenware.exe" | C:\Users\admin\Desktop\rensenware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Rensenware Application Version: 1.0.0.0 Modules
| |||||||||||||||
| 3956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Trojan.Ransom.Rensenware.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 086
Read events
9 205
Write events
571
Delete events
310
Modification events
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Trojan.Ransom.Rensenware.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3956.13616\rensenware.vir | executable | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Desktop\featuredarchitecture.jpg.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Desktop\hoursvideos.png.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Desktop\llctalk.png.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Desktop\michaelcup.png.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Downloads\believecompare.jpg.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Downloads\noneapproach.png.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Downloads\operatingstudent.png.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Downloads\sampletravel.jpg.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
| 2064 | rensenware.exe | C:\Users\admin\Pictures\alternativeplay.jpg.RENSENWARE | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |