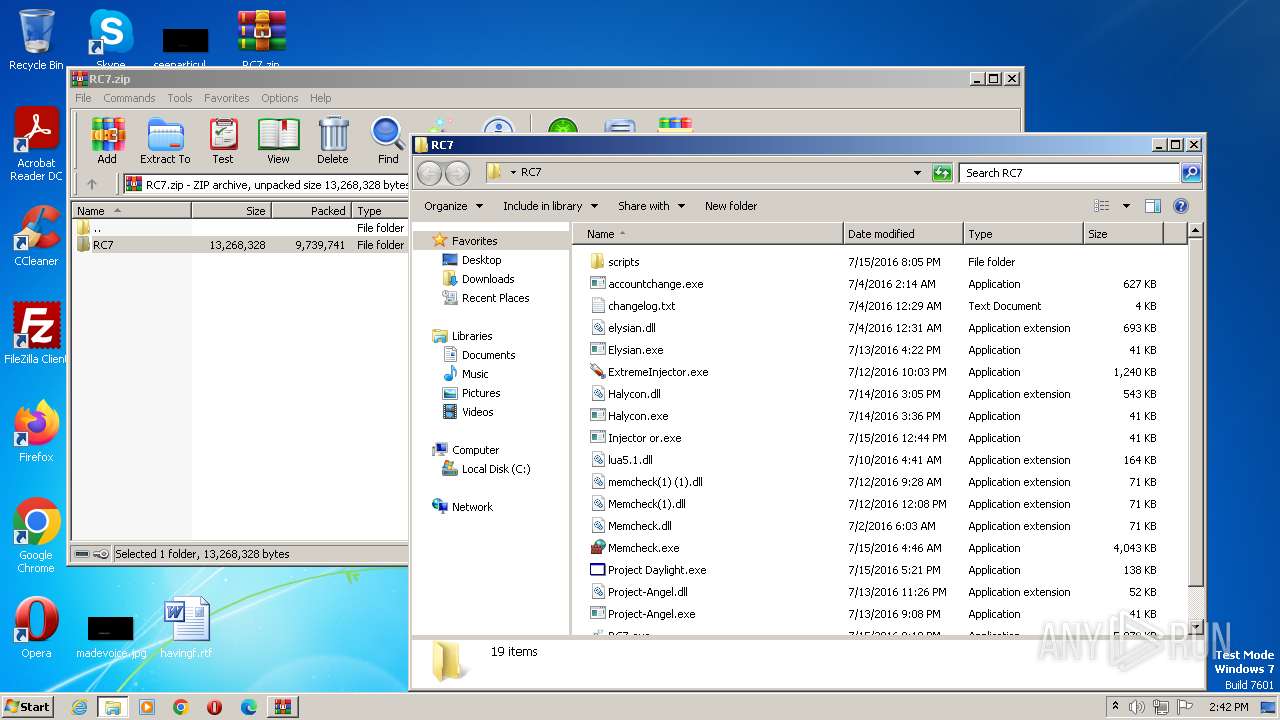
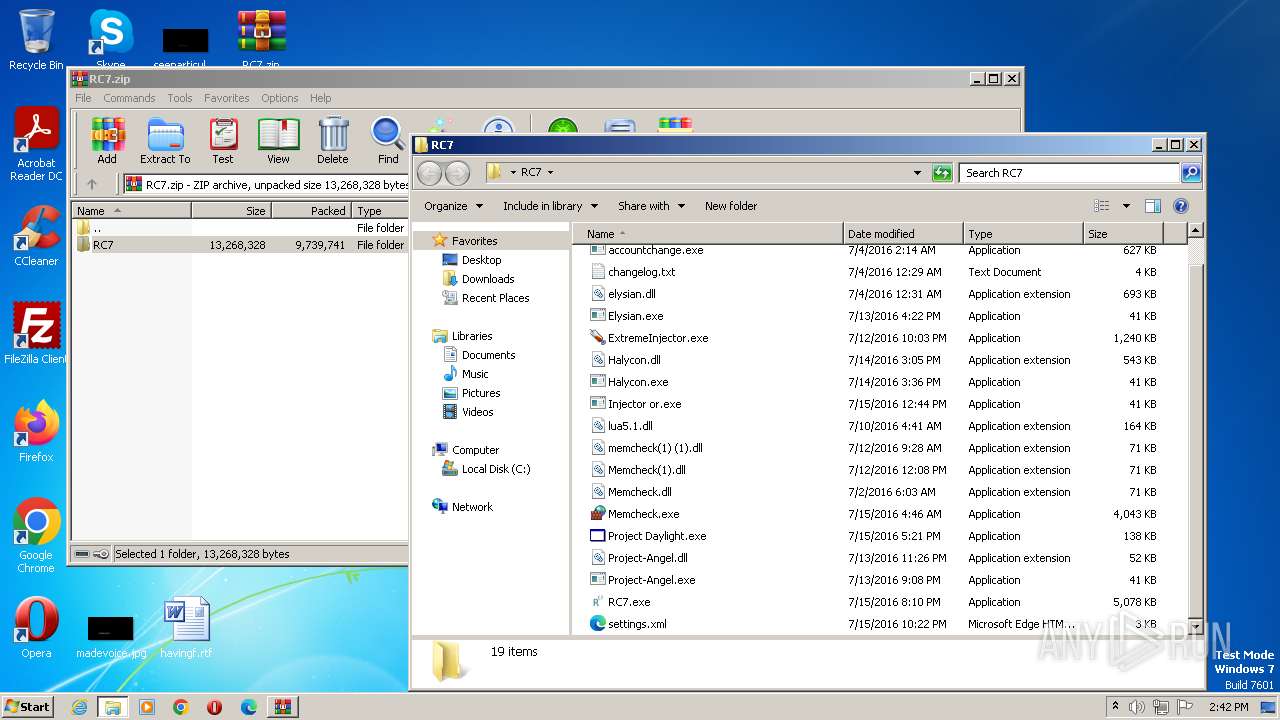
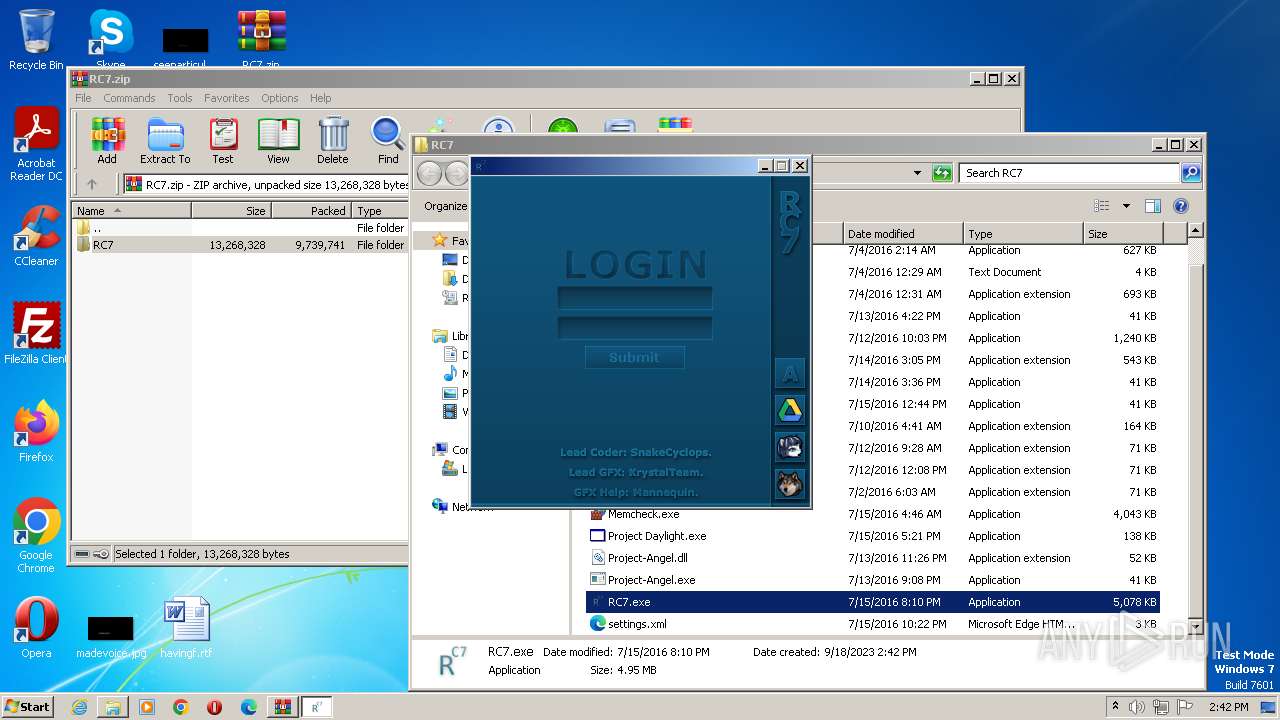
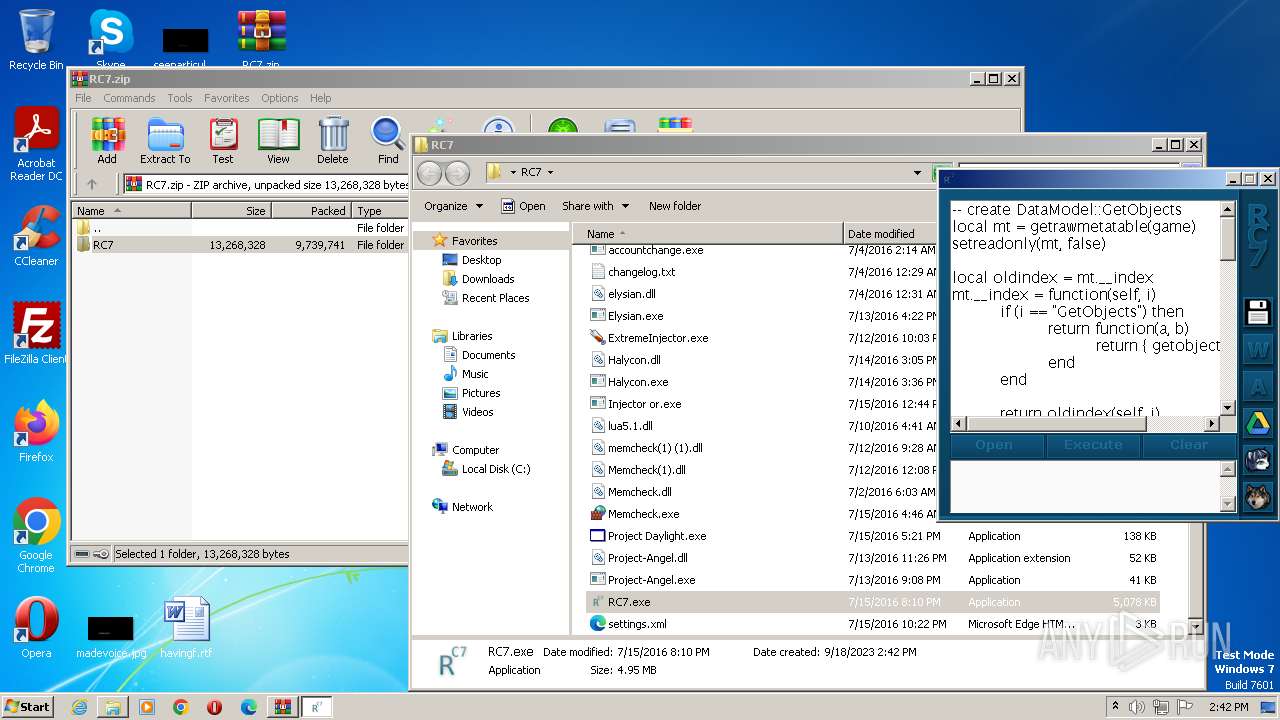
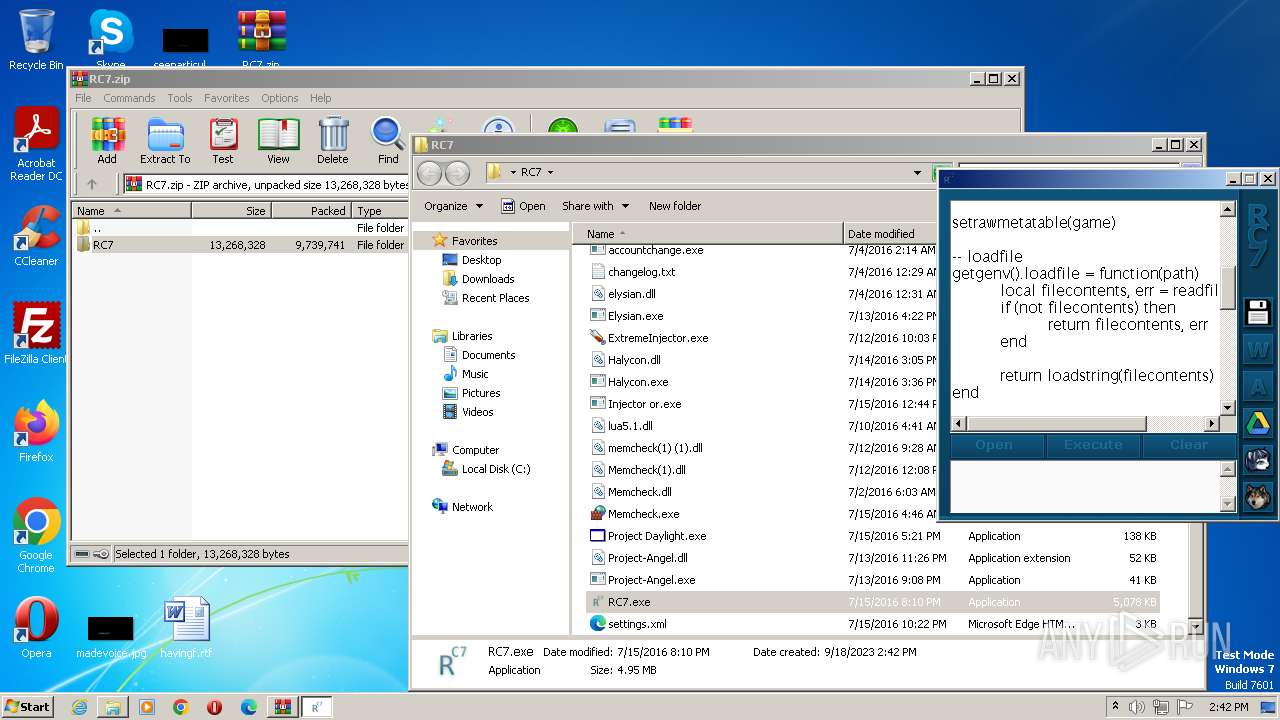
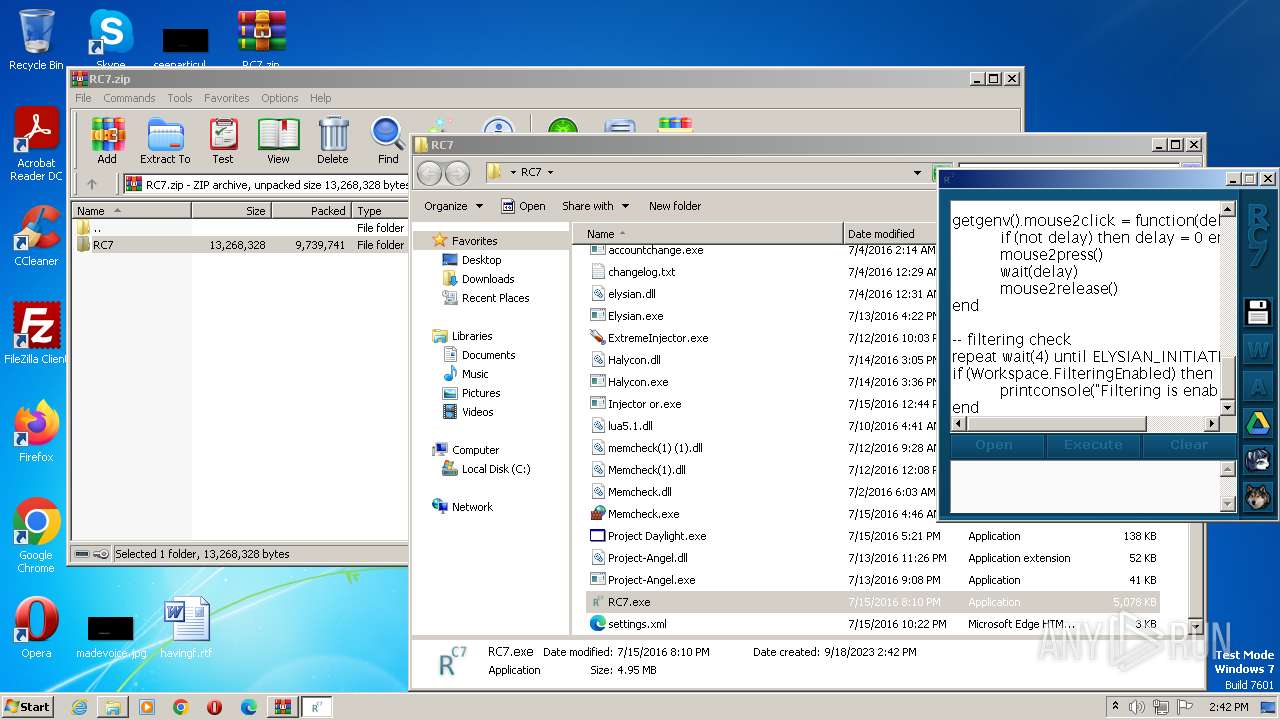
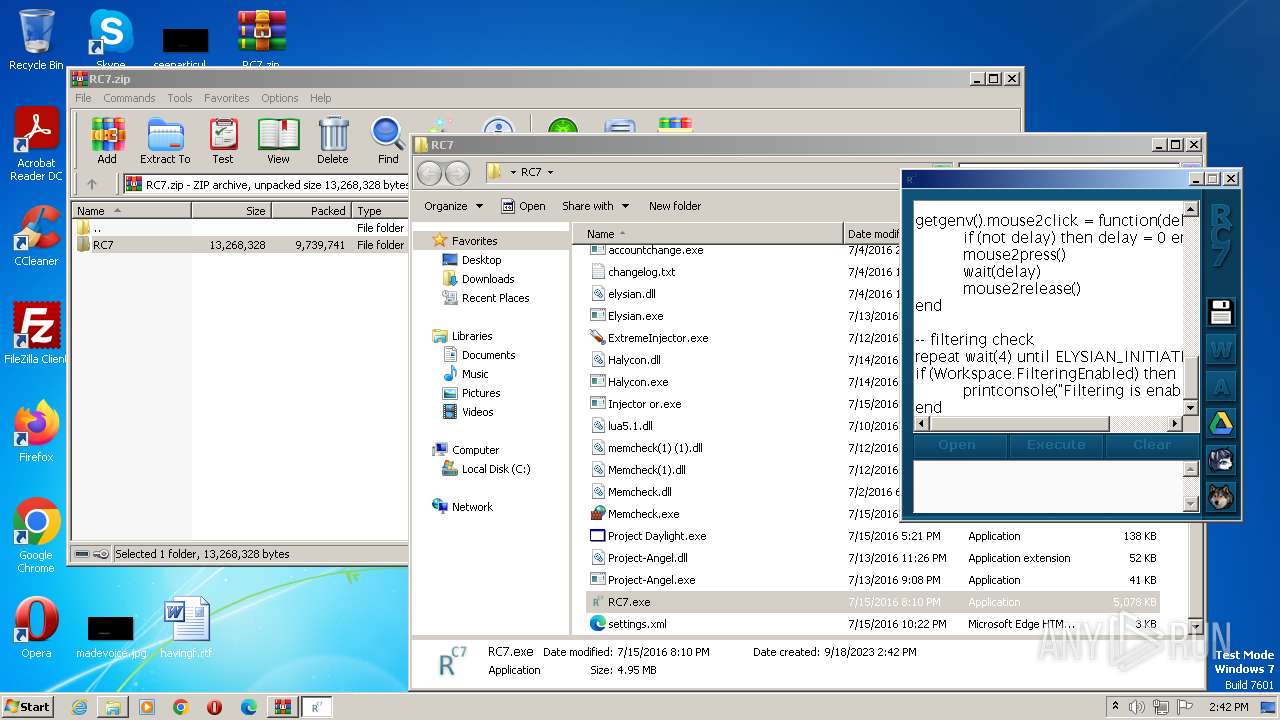
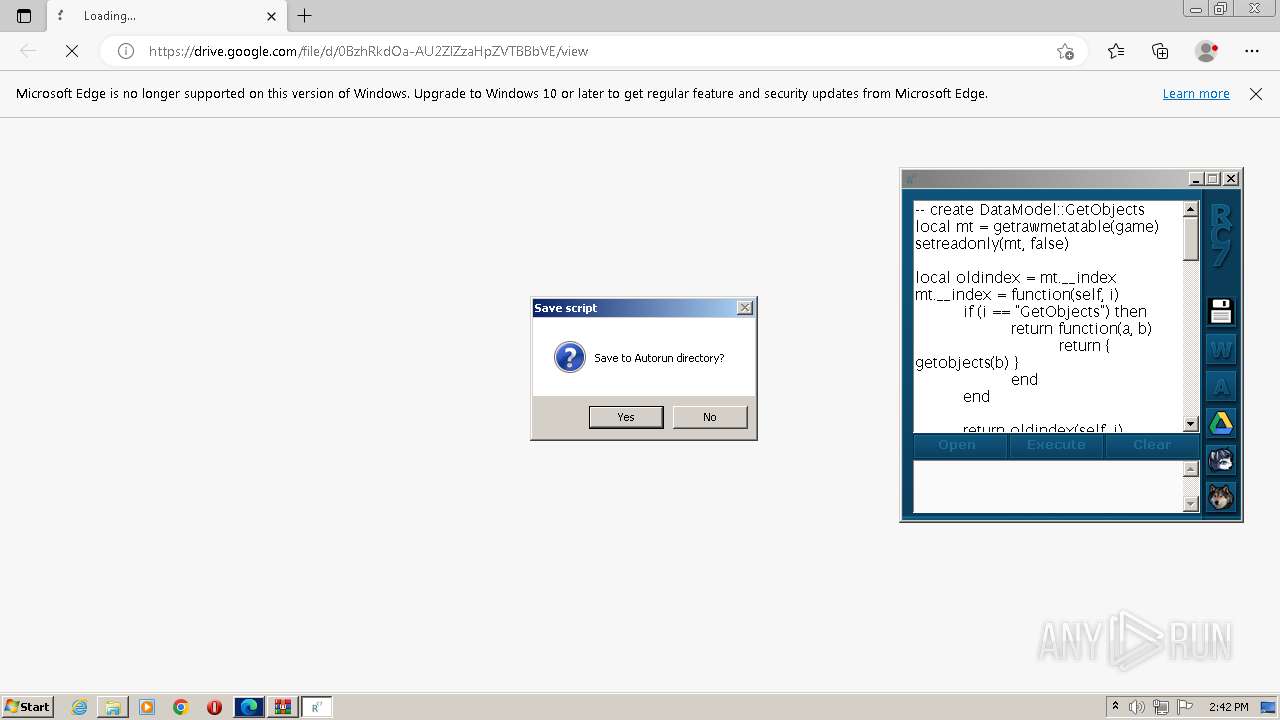
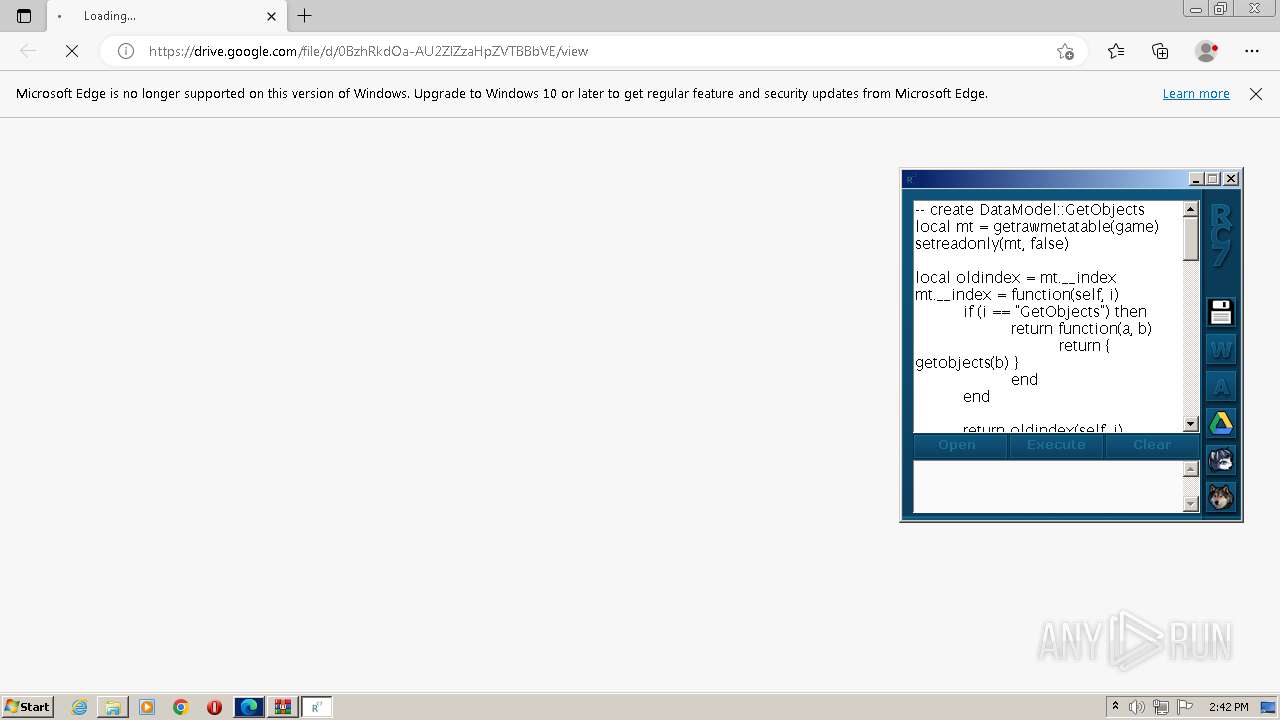
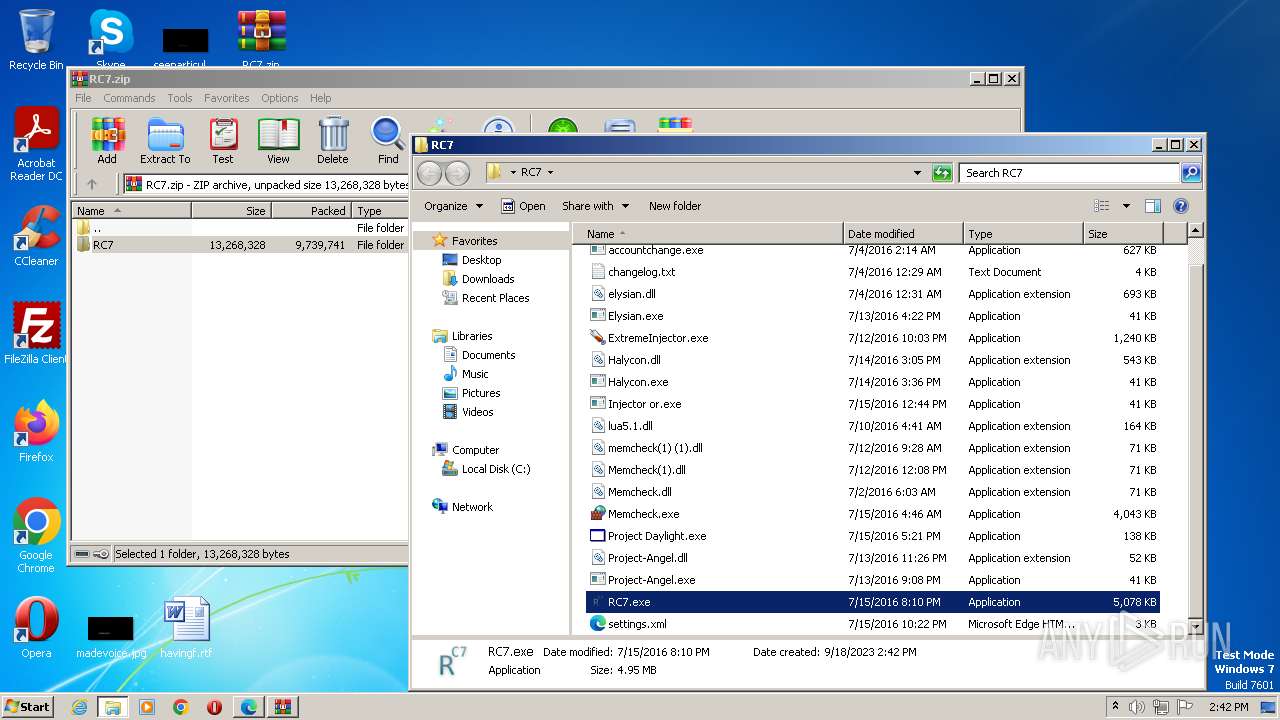
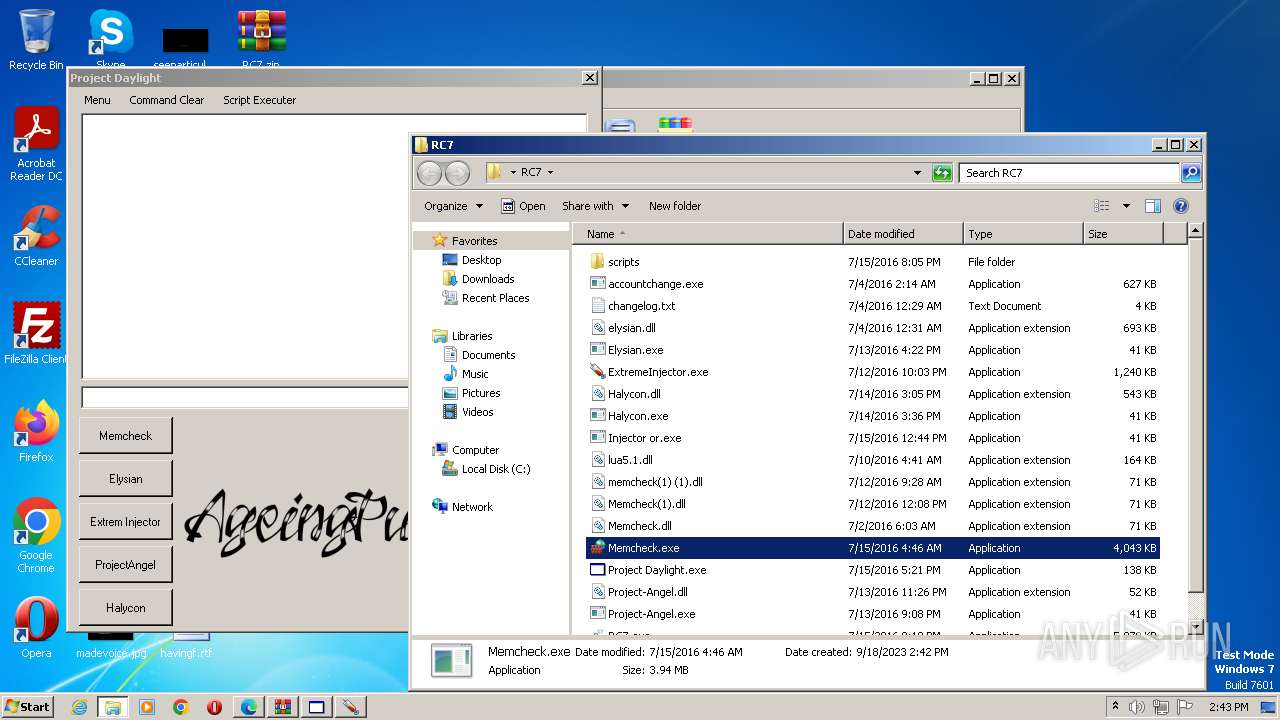
| File name: | RC7.zip |
| Full analysis: | https://app.any.run/tasks/c46a1633-4bf5-49c4-a765-9ca4c3fa877c |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2023, 13:41:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 969E35B7E89E91FC8FE43AAF37522BF1 |
| SHA1: | 3DB5217B148790102F8BD5DC78055042CF81650D |
| SHA256: | E3DDD5E0BE260F532C9FB7EEB5315B377859E5164943BB1577A2477C97D750EF |
| SSDEEP: | 196608:cKi6ANPUJ9Xyvy7CUq1+akdzD3z67EEI2l4NZZm/5fJYwqm:u5NspyvFgpzP64EIJN7m/5RYw9 |
MALICIOUS
Application was dropped or rewritten from another process
- RC7.exe (PID: 2012)
- Memcheck.exe (PID: 3576)
- Project Daylight.exe (PID: 2772)
- Memcheck.exe (PID: 2084)
- Memcheck.exe (PID: 2480)
- Elysian.exe (PID: 540)
- ExtremeInjector.exe (PID: 2560)
- ExtremeInjector.exe (PID: 2724)
- accountchange.exe (PID: 4068)
- Halycon.exe (PID: 1788)
- RC7.exe (PID: 1848)
Loads dropped or rewritten executable
- RC7.exe (PID: 2012)
- Memcheck.exe (PID: 2480)
- RC7.exe (PID: 1848)
SUSPICIOUS
Reads the Internet Settings
- RC7.exe (PID: 2012)
- Project Daylight.exe (PID: 2772)
- ExtremeInjector.exe (PID: 2560)
- ExtremeInjector.exe (PID: 2724)
Application launched itself
- ExtremeInjector.exe (PID: 2560)
INFO
Reads the machine GUID from the registry
- RC7.exe (PID: 2012)
- ExtremeInjector.exe (PID: 2560)
- ExtremeInjector.exe (PID: 2724)
Manual execution by a user
- RC7.exe (PID: 2012)
- Project Daylight.exe (PID: 2772)
- accountchange.exe (PID: 4068)
Reads the computer name
- RC7.exe (PID: 2012)
- Project Daylight.exe (PID: 2772)
- Memcheck.exe (PID: 2084)
- Memcheck.exe (PID: 2480)
- ExtremeInjector.exe (PID: 2724)
- ExtremeInjector.exe (PID: 2560)
- RC7.exe (PID: 1848)
- accountchange.exe (PID: 4068)
Checks supported languages
- RC7.exe (PID: 2012)
- Project Daylight.exe (PID: 2772)
- Memcheck.exe (PID: 2608)
- Memcheck.exe (PID: 2084)
- Memcheck.exe (PID: 2480)
- ExtremeInjector.exe (PID: 2560)
- ExtremeInjector.exe (PID: 2724)
- accountchange.exe (PID: 4068)
- RC7.exe (PID: 1848)
Application launched itself
- msedge.exe (PID: 2768)
Create files in a temporary directory
- Memcheck.exe (PID: 2084)
- Memcheck.exe (PID: 2608)
- ExtremeInjector.exe (PID: 2724)
Reads Environment values
- ExtremeInjector.exe (PID: 2724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | RC7/accountchange.exe |
|---|---|
| ZipUncompressedSize: | 642048 |
| ZipCompressedSize: | 236083 |
| ZipCRC: | 0x10375708 |
| ZipModifyDate: | 2016:07:04 02:14:28 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
70
Monitored processes
26
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
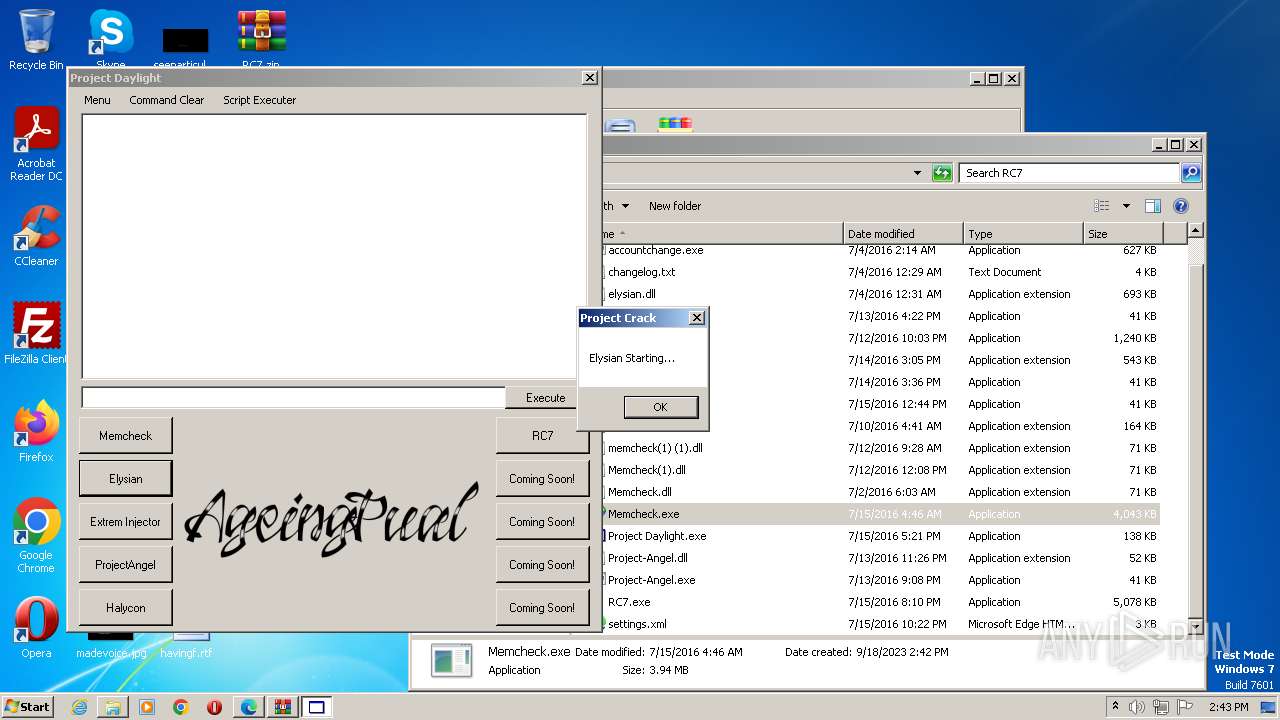
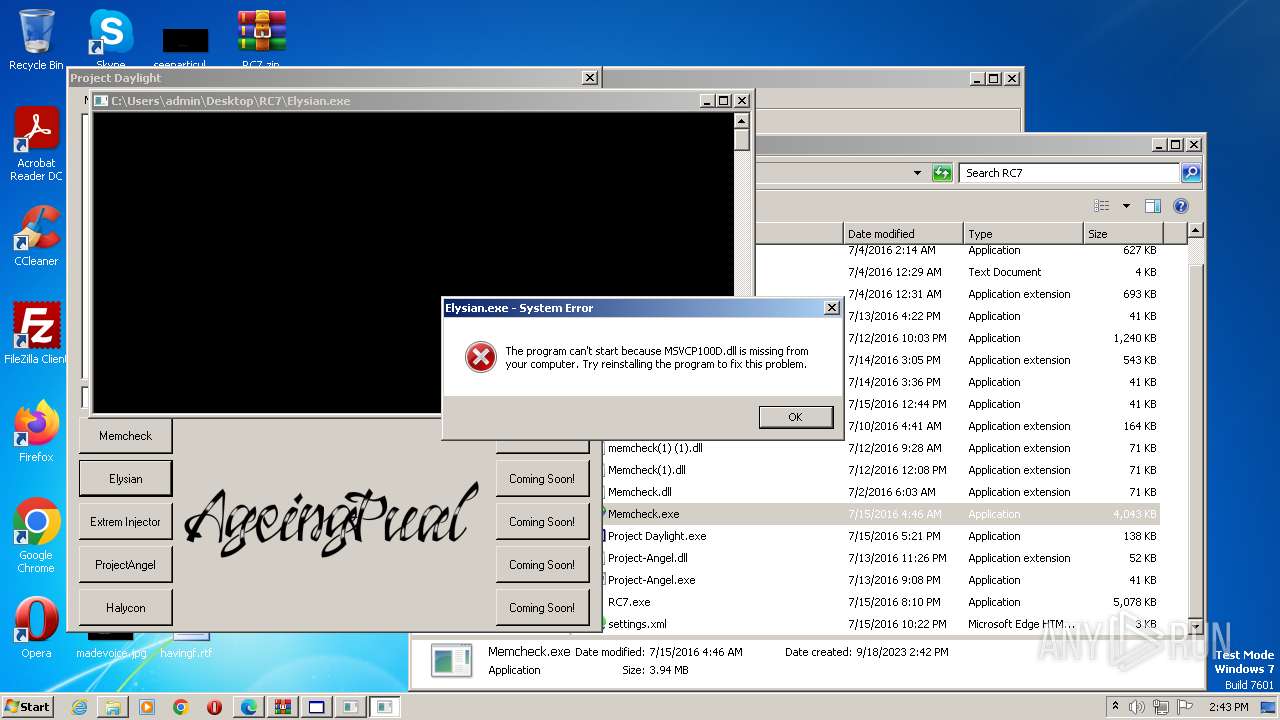
| 540 | "C:\Users\admin\Desktop\RC7\Elysian.exe" | C:\Users\admin\Desktop\RC7\Elysian.exe | — | Project Daylight.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 1528 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1412 --field-trial-handle=1328,i,9972145990188867017,2262720744741652140,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=1492 --field-trial-handle=1328,i,9972145990188867017,2262720744741652140,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1788 | "C:\Users\admin\Desktop\RC7\Halycon.exe" | C:\Users\admin\Desktop\RC7\Halycon.exe | — | Project Daylight.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 1848 | "C:\Users\admin\Desktop\RC7\RC7.exe" | C:\Users\admin\Desktop\RC7\RC7.exe | — | Project Daylight.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2012 | "C:\Users\admin\Desktop\RC7\RC7.exe" | C:\Users\admin\Desktop\RC7\RC7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1300 --field-trial-handle=1328,i,9972145990188867017,2262720744741652140,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\Desktop\RC7\Memcheck.exe" | C:\Users\admin\Desktop\RC7\Memcheck.exe | Project Daylight.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2480 | C:\Users\admin\AppData\Local\Temp\cetrainers\CET76B8.tmp\extracted\Memcheck.exe "C:\Users\admin\AppData\Local\Temp\cetrainers\CET76B8.tmp\extracted\CET_TRAINER.CETRAINER" "-ORIGIN:C:\Users\admin\Desktop\RC7\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CET76B8.tmp\extracted\Memcheck.exe | Memcheck.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 6.5.0.4590 Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\Desktop\RC7\ExtremeInjector.exe" | C:\Users\admin\Desktop\RC7\ExtremeInjector.exe | — | Project Daylight.exe | |||||||||||
User: admin Company: master131 Integrity Level: MEDIUM Description: Extreme Injector Exit code: 0 Version: 3.6.1.0 Modules
| |||||||||||||||
Total events
9 402
Read events
9 268
Write events
130
Delete events
4
Modification events
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3748) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2564) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2012) RC7.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
20
Suspicious files
21
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\changelog.txt | text | |
MD5:398E942C79BDB2590E08FB023EB76EE7 | SHA256:0B5513EA4E05042A2844EEEE760B8E0A7C72363DEB1EE713503D7A9C3C38E15E | |||
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\ExtremeInjector.exe | executable | |
MD5:03E95431DDC771FF719A5D5FF3D46136 | SHA256:FDA70123008180F3DCDFC6ED3C74F5EB1FA2B9E7DC76C4D149AD351B158E4376 | |||
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\Halycon.dll | executable | |
MD5:681F38EE66E5DC9566FEB9B306AE8FD8 | SHA256:4F098ECEE5BD2D92B167434FAC56D55AD51A2582AD24CE17A7B3DF92624487E1 | |||
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\Halycon.exe | executable | |
MD5:60AD7C5084375C0DD19B1ECC43EEE3B2 | SHA256:BA9083A3732C0EA3B8A3141B89C999BAB6074FF7F1E81C838AD820787EE7AF6F | |||
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\Memcheck(1).dll | executable | |
MD5:8D2EBBC526125E43A6203983F7C71E61 | SHA256:43AE9D049DE8287160475A1288AD7ACAADCE278B088279EAEA869886E9A43FAB | |||
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\accountchange.exe | executable | |
MD5:C4F8790EC53D25C9271BCA94D3E7553A | SHA256:56066AE5481C334937483DD0EE1874D44C97B87263BD7D81E6AFC414AFB6363A | |||
| 3748 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3748.984\RC7\Elysian.exe | executable | |
MD5:80D85AE9C0B8ECBDF20AA9FC6185273C | SHA256:7EAF50D65994FA43937CCE8F030094E199F84AED76A3D4B6EBDBA178663DFF17 | |||
| 2768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1037cb.TMP | — | |
MD5:— | SHA256:— | |||
| 2768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:6BBE1BFA3A9FEDA71E860D7BEE338526 | SHA256:A7D313A5230EA1B2C67C3ACDC75D66F87D214E760AEBD7B2228A9EEBBAB5C897 | |||
| 2768 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
28
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2768 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1528 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1528 | msedge.exe | 142.250.184.206:443 | drive.google.com | GOOGLE | US | whitelisted |
1528 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1528 | msedge.exe | 20.105.73.143:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1528 | msedge.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1528 | msedge.exe | 152.199.21.175:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | EDGECAST | DE | whitelisted |
1528 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
drive.google.com |
| shared |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Memcheck.exe | sizeof fxstate = 512 |
Memcheck.exe | Offset of LBR_Count=760 |
Memcheck.exe | TSymhandler.create 3 |
Memcheck.exe | TSymhandler.create 1 |
Memcheck.exe | TSymhandler.create 2 |
Memcheck.exe | TSymhandler.create exit |
Memcheck.exe | TSymhandler.create 2 |
Memcheck.exe | TSymhandler.create 1 |
Memcheck.exe | TSymhandler.create |
Memcheck.exe | TSymbolListHandler.create exit |