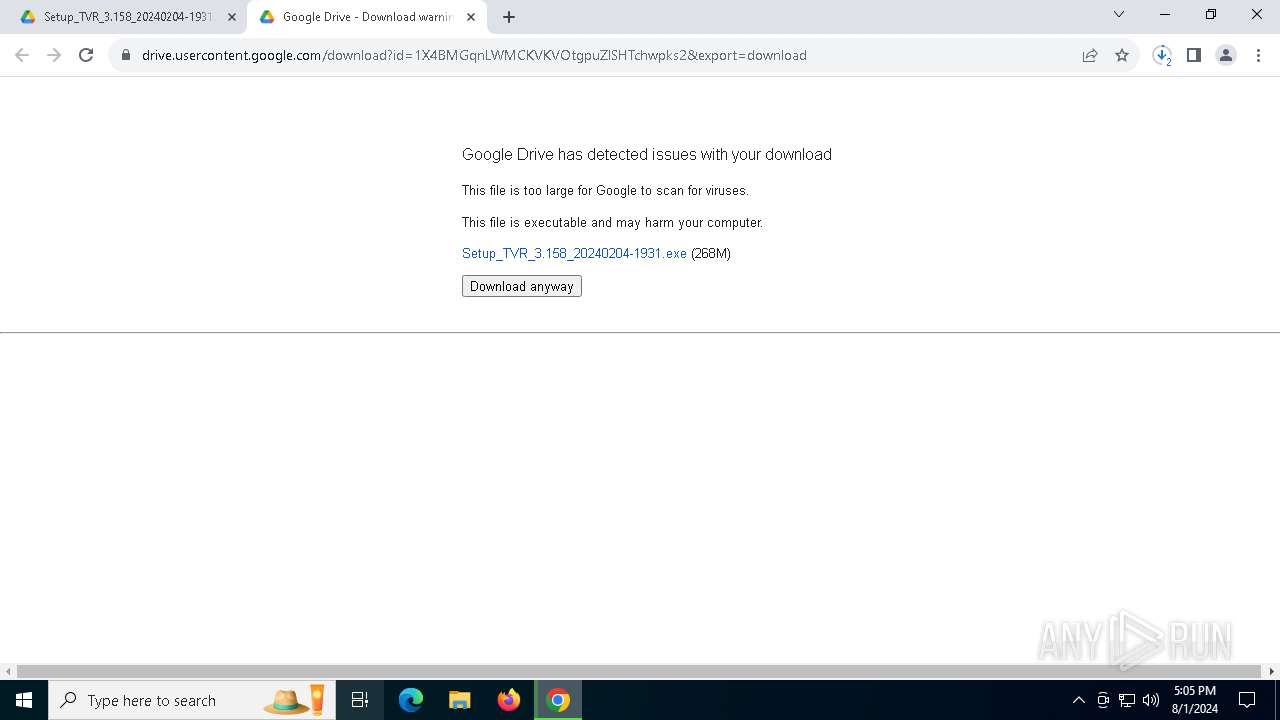
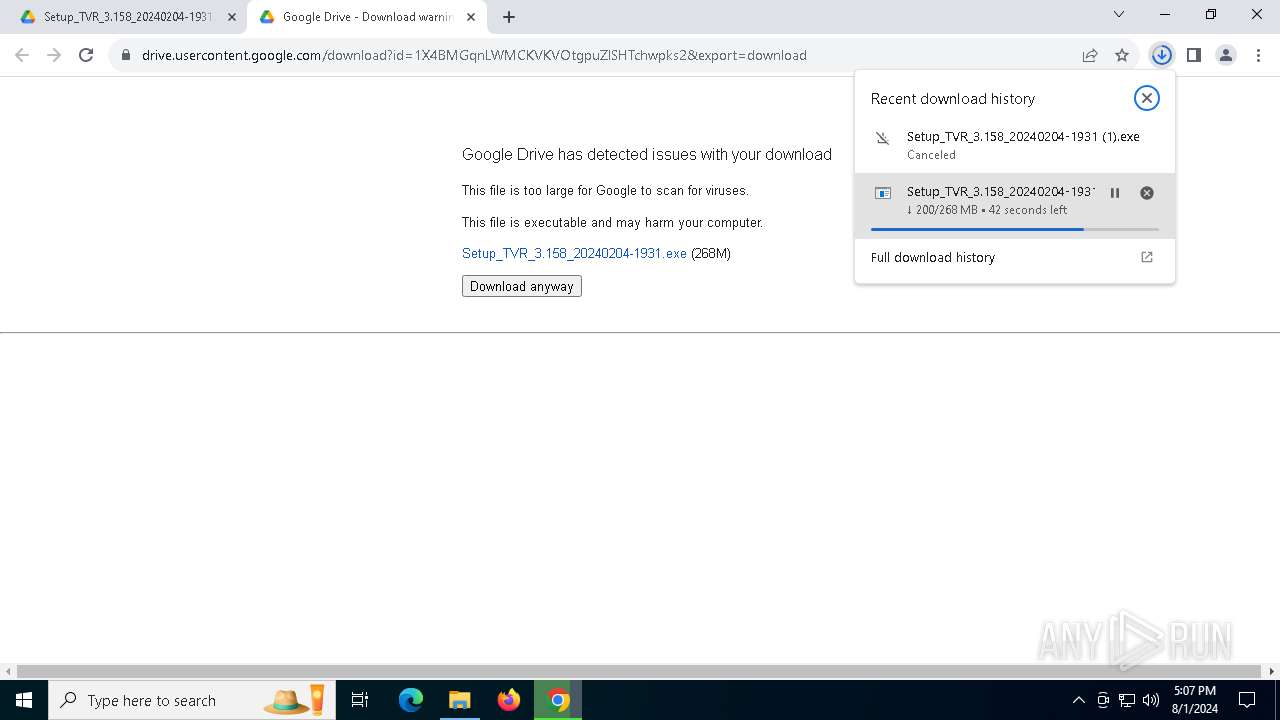
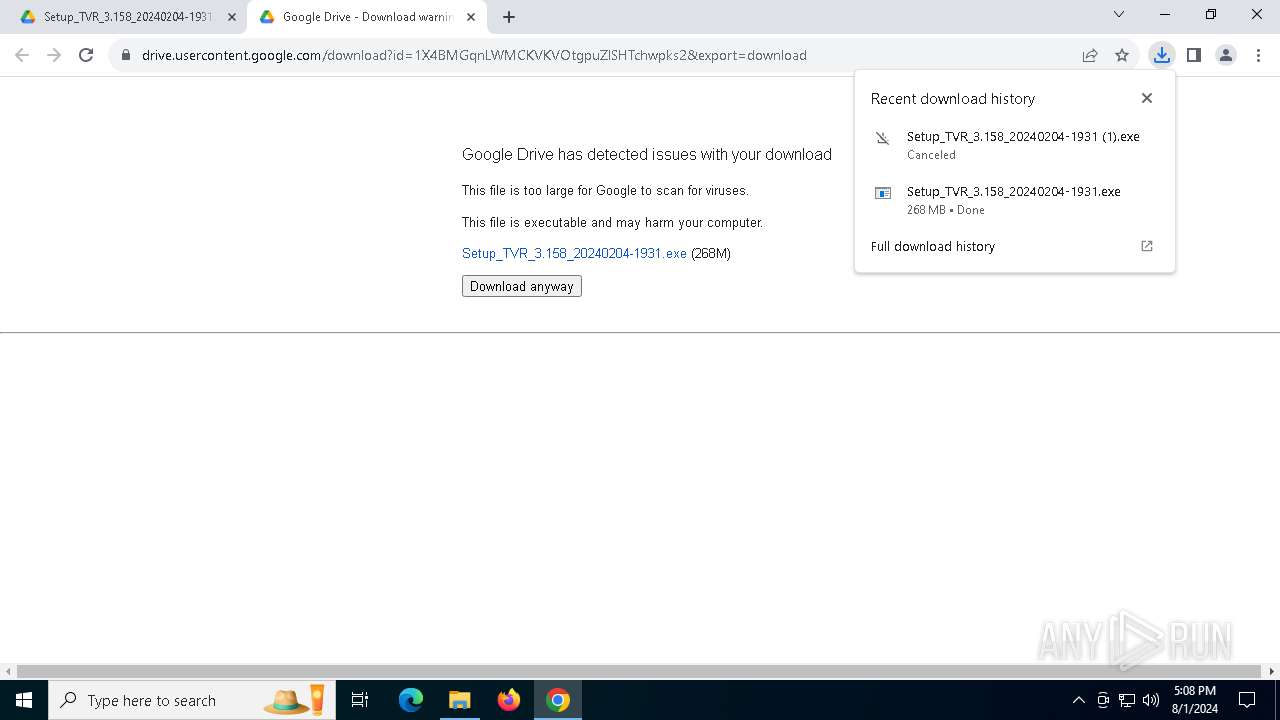
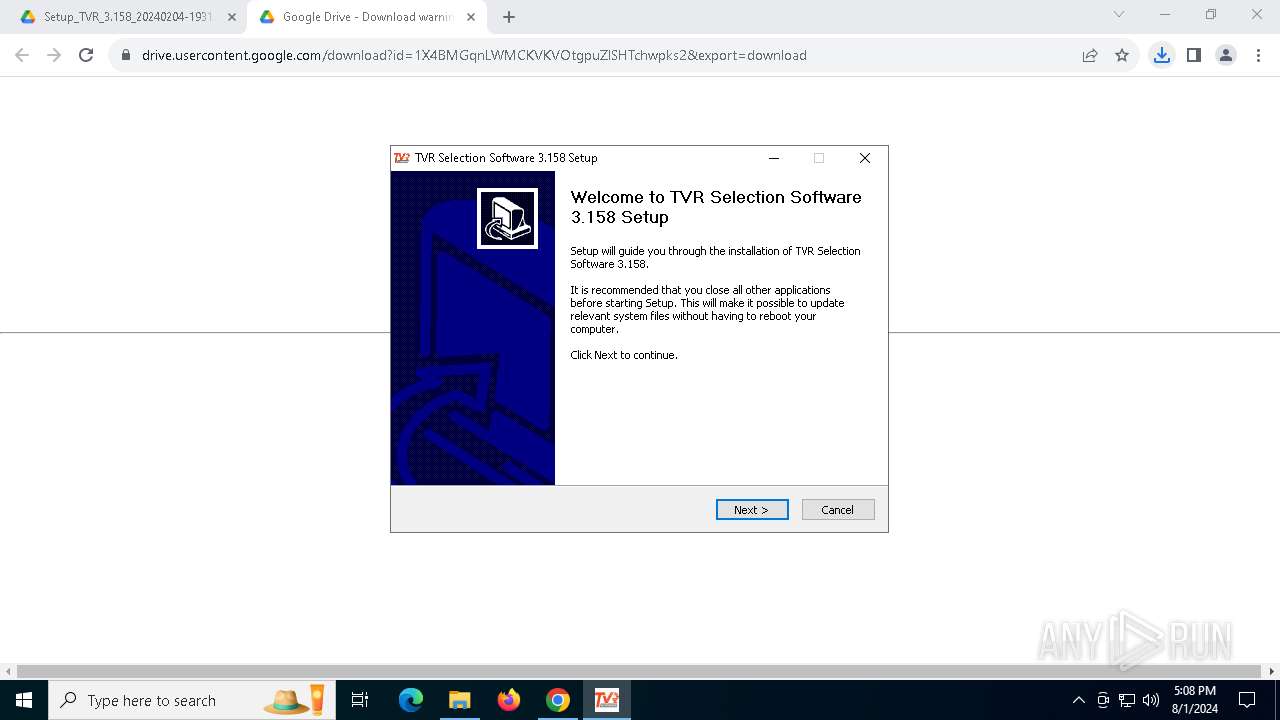
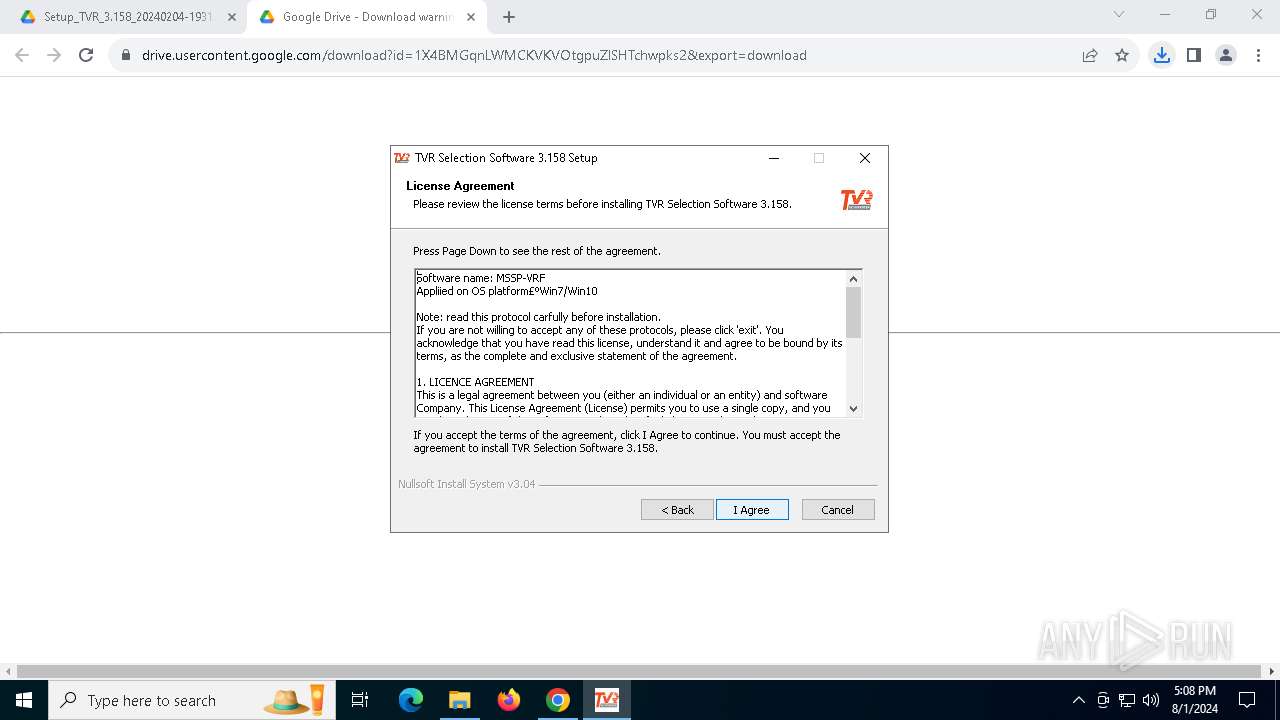
| URL: | https://track.mdrctr.com/track/link/key/106015-436-2965-59-2179-389681/signature/f303027053eab1d7d28573bf4ea3c48b/userid/3ad9f6888e1879541cfdebee4f3adef6 |
| Full analysis: | https://app.any.run/tasks/fead0f61-abd8-4441-9777-a6a1440f04b3 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 17:04:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 30557D0E77EC67FC5DD454E84A4F65AC |
| SHA1: | BC66130CDDB3A6FB1BB4A895FAA553936291CCA9 |
| SHA256: | E3D65BC702D6EA061AAEA453612339E963F47CE0CF25EF345CEBB834A681F226 |
| SSDEEP: | 3:N8fv3WpBEGTMhOAwIRUqzHLHCLERQXA7E6QnAGwQ3vdcDRTvEVjmkT:2n3WpyGAujqzHLHCLERCA7E7zFyJvEca |
MALICIOUS
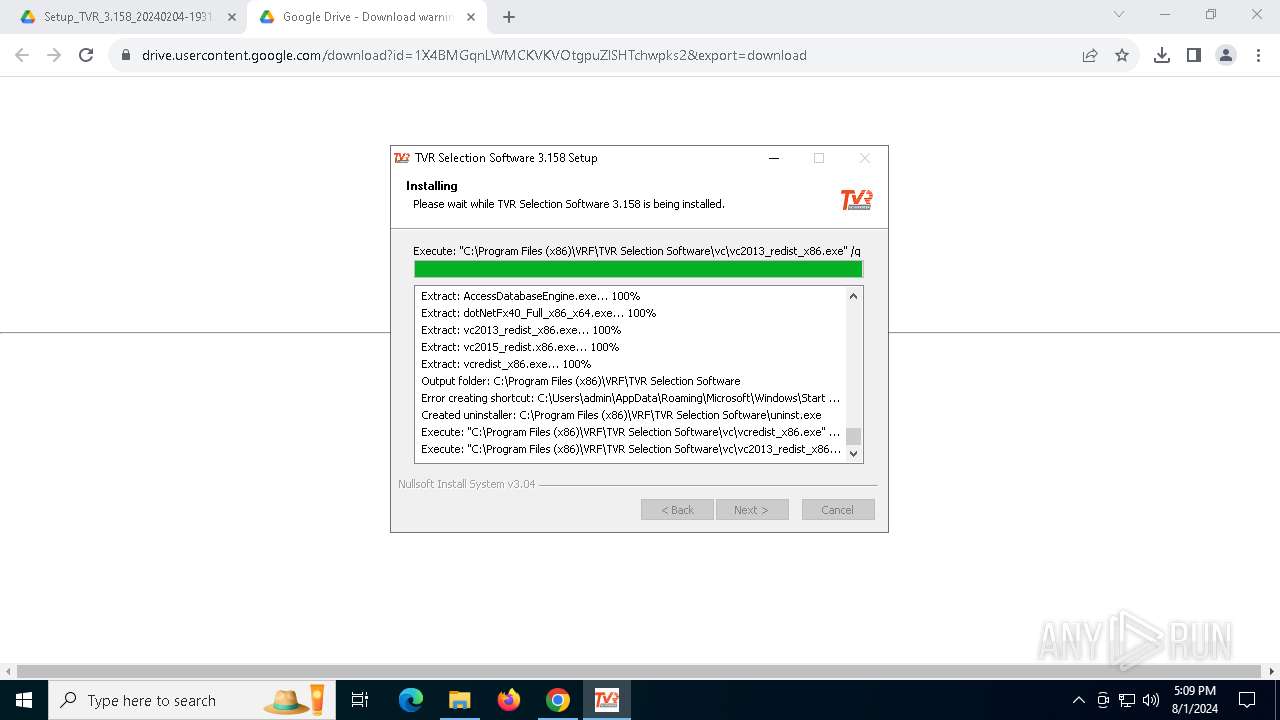
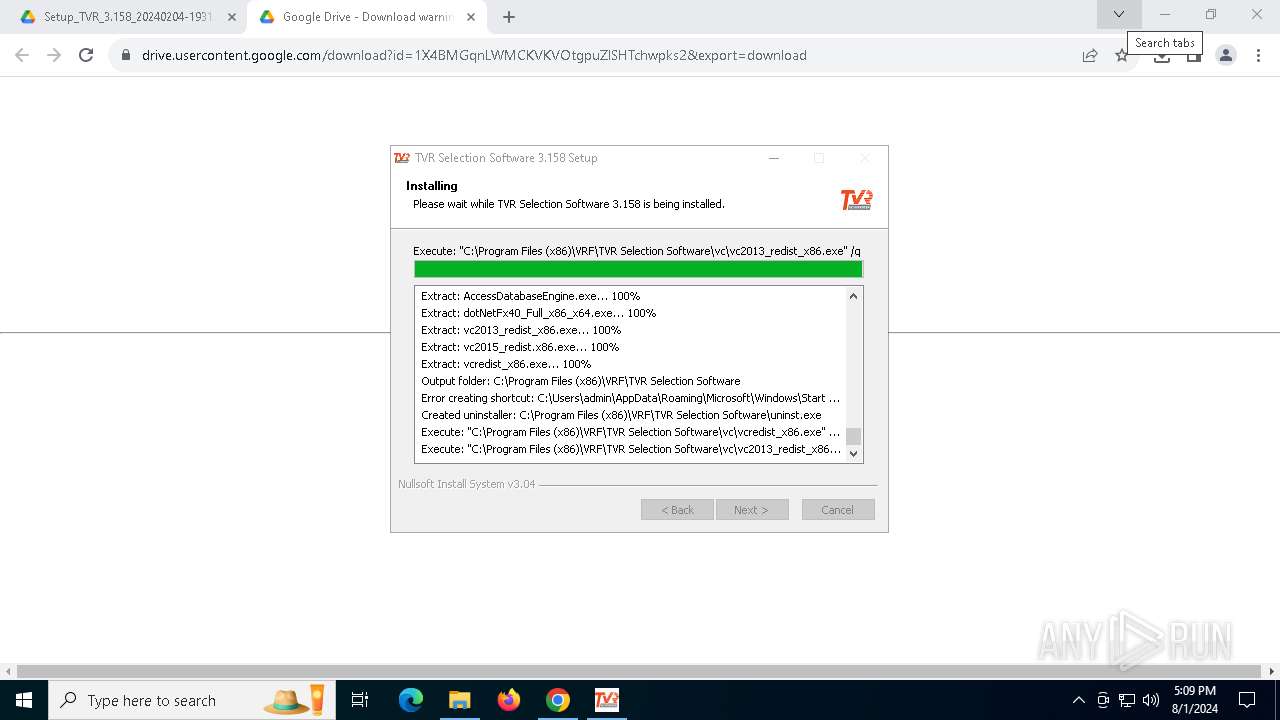
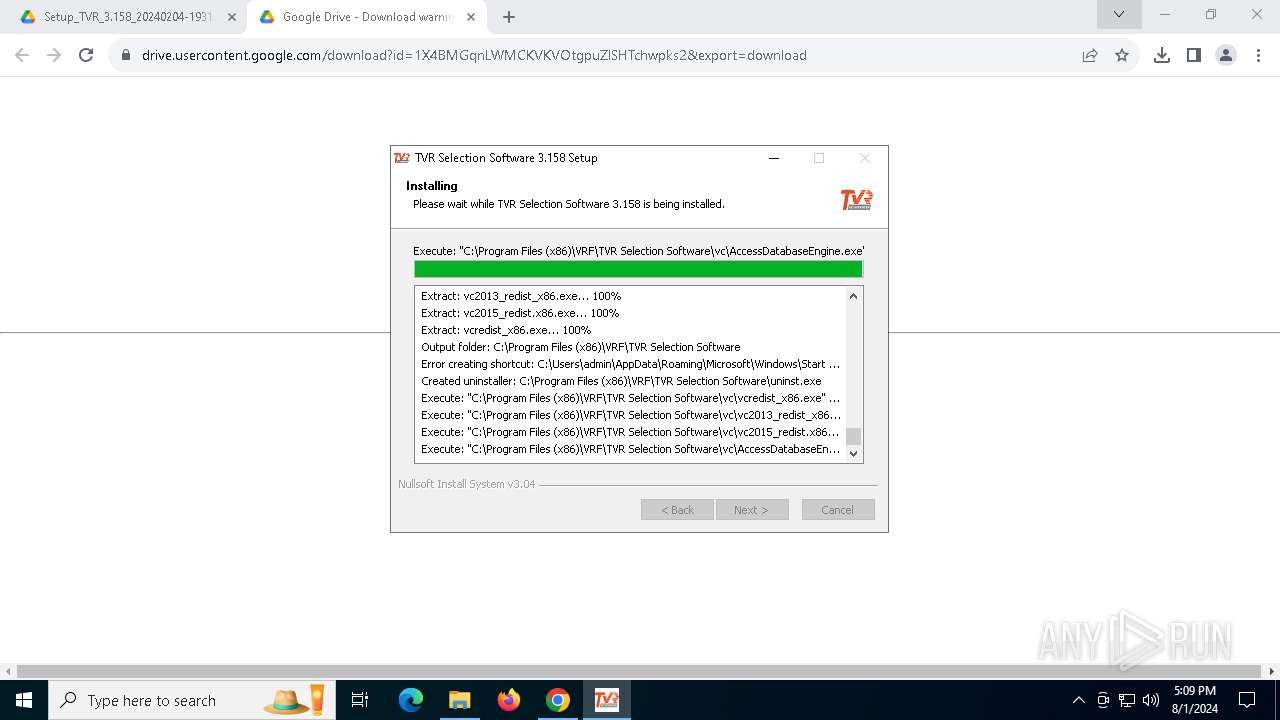
Drops the executable file immediately after the start
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vcredist_x86.exe (PID: 8100)
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 1292)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
- vc2015_redist.x86.exe (PID: 6272)
- TiWorker.exe (PID: 7696)
Changes the autorun value in the registry
- vc2013_redist_x86.exe (PID: 7180)
SUSPICIOUS
Executable content was dropped or overwritten
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vcredist_x86.exe (PID: 8100)
- vc2013_redist_x86.exe (PID: 1292)
- vc2013_redist_x86.exe (PID: 7180)
- vc2015_redist.x86.exe (PID: 6272)
- TiWorker.exe (PID: 7696)
Drops 7-zip archiver for unpacking
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
Creates a software uninstall entry
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vc2013_redist_x86.exe (PID: 7180)
Process drops legitimate windows executable
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vcredist_x86.exe (PID: 8100)
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 1292)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
- vc2015_redist.x86.exe (PID: 6272)
- TiWorker.exe (PID: 7696)
The process drops C-runtime libraries
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vcredist_x86.exe (PID: 8100)
- msiexec.exe (PID: 7272)
- msiexec.exe (PID: 1076)
- TiWorker.exe (PID: 7696)
Creates file in the systems drive root
- vcredist_x86.exe (PID: 8100)
Checks Windows Trust Settings
- Setup.exe (PID: 8060)
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
Reads security settings of Internet Explorer
- Setup.exe (PID: 8060)
- vc2013_redist_x86.exe (PID: 7180)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7272)
- msiexec.exe (PID: 1076)
Application launched itself
- vc2013_redist_x86.exe (PID: 7180)
- vc2015_redist.x86.exe (PID: 7412)
Searches for installed software
- vc2013_redist_x86.exe (PID: 7180)
- vc2013_redist_x86.exe (PID: 1292)
- dllhost.exe (PID: 3720)
- vc2015_redist.x86.exe (PID: 6272)
Executes as Windows Service
- VSSVC.exe (PID: 4760)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 1076)
Malware-specific behavior (creating "System.dll" in Temp)
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
INFO
Reads Microsoft Office registry keys
- chrome.exe (PID: 6504)
- msiexec.exe (PID: 1076)
- msiexec.exe (PID: 3324)
Executable content was dropped or overwritten
- chrome.exe (PID: 6504)
- msiexec.exe (PID: 7272)
- msiexec.exe (PID: 1076)
Application launched itself
- chrome.exe (PID: 6504)
Checks supported languages
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vcredist_x86.exe (PID: 8100)
- Setup.exe (PID: 8060)
- vc2013_redist_x86.exe (PID: 1292)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
- vc2015_redist.x86.exe (PID: 6272)
- vc2015_redist.x86.exe (PID: 7412)
- AccessDatabaseEngine.exe (PID: 4784)
- msiexec.exe (PID: 3324)
- msiexec.exe (PID: 7072)
- msiexec.exe (PID: 7272)
The process uses the downloaded file
- chrome.exe (PID: 6504)
- chrome.exe (PID: 6284)
Reads the machine GUID from the registry
- vcredist_x86.exe (PID: 8100)
- Setup.exe (PID: 8060)
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
Reads the computer name
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vcredist_x86.exe (PID: 8100)
- Setup.exe (PID: 8060)
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 1292)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
- vc2015_redist.x86.exe (PID: 6272)
- vc2015_redist.x86.exe (PID: 7412)
- AccessDatabaseEngine.exe (PID: 4784)
- msiexec.exe (PID: 3324)
- msiexec.exe (PID: 7072)
Create files in a temporary directory
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- Setup.exe (PID: 8060)
- vc2013_redist_x86.exe (PID: 1292)
- vc2013_redist_x86.exe (PID: 7180)
- vc2015_redist.x86.exe (PID: 6272)
- AccessDatabaseEngine.exe (PID: 4784)
Drops the executable file immediately after the start
- chrome.exe (PID: 6504)
Creates files in the program directory
- Setup_TVR_3.158_20240204-1931.exe (PID: 888)
- vc2013_redist_x86.exe (PID: 7180)
- AccessDatabaseEngine.exe (PID: 4784)
Reads the software policy settings
- Setup.exe (PID: 8060)
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 7180)
- msiexec.exe (PID: 1076)
Reads CPU info
- Setup.exe (PID: 8060)
Creates files or folders in the user directory
- msiexec.exe (PID: 7272)
- vc2013_redist_x86.exe (PID: 7180)
Creates a software uninstall entry
- msiexec.exe (PID: 7272)
- msiexec.exe (PID: 1076)
Checks proxy server information
- vc2013_redist_x86.exe (PID: 7180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
184
Monitored processes
41
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\Users\admin\Downloads\Setup_TVR_3.158_20240204-1931.exe" | C:\Users\admin\Downloads\Setup_TVR_3.158_20240204-1931.exe | chrome.exe | ||||||||||||
User: admin Company: TVR Selection Software Integrity Level: HIGH Description: TVR Selection Software Version: 3.158 Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\VRF\TVR Selection Software\vc\vc2013_redist_x86.exe" /q /norestart -burn.unelevated BurnPipe.{EB373F37-AD0A-42F3-A7F3-C6064634DFF6} {780603A8-7643-44EF-BF26-90B7E922875E} 7180 | C:\Program Files (x86)\VRF\TVR Selection Software\vc\vc2013_redist_x86.exe | vc2013_redist_x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2013 Redistributable (x86) - 12.0.30501 Exit code: 0 Version: 12.0.30501.0 Modules
| |||||||||||||||
| 3324 | C:\Windows\syswow64\MsiExec.exe -Embedding 20F53622E1AC220687D2BC35C6CC2197 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | "C:\Program Files (x86)\VRF\TVR Selection Software\vc\AccessDatabaseEngine.exe" /q /norestart | C:\Program Files (x86)\VRF\TVR Selection Software\vc\AccessDatabaseEngine.exe | — | Setup_TVR_3.158_20240204-1931.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 14.0.6119.5000 Modules
| |||||||||||||||
| 5032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5824 --field-trial-handle=1832,i,3097011679537740762,15770384057434684409,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4352 --field-trial-handle=1832,i,3097011679537740762,15770384057434684409,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4984 --field-trial-handle=1832,i,3097011679537740762,15770384057434684409,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
39 091
Read events
37 015
Write events
2 006
Delete events
70
Modification events
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6504) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
296
Suspicious files
572
Text files
526
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe5e58.TMP | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe5e67.TMP | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:A95974F48FC4A0E16E9D7729D7874157 | SHA256:926422473F59B7759EA8EB2064FD6DF9D00A88B548DEF1D5C3E08860357C03A2 | |||
| 6504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
83
DNS requests
65
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3160 | svchost.exe | GET | 304 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3160 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6992 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7908 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fhtuazrdjnqikxtln4pvzfahjq_20240720.656159207.14/obedbbhbpmojnkanicioggnmelmoomoc_20240720.656159207.14_all_ENUS500000_kewn2vupl47qk3g57fw5vpvpaq.crx3 | unknown | — | — | whitelisted |
6416 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7908 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fhtuazrdjnqikxtln4pvzfahjq_20240720.656159207.14/obedbbhbpmojnkanicioggnmelmoomoc_20240720.656159207.14_all_ENUS500000_kewn2vupl47qk3g57fw5vpvpaq.crx3 | unknown | — | — | whitelisted |
7908 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fhtuazrdjnqikxtln4pvzfahjq_20240720.656159207.14/obedbbhbpmojnkanicioggnmelmoomoc_20240720.656159207.14_all_ENUS500000_kewn2vupl47qk3g57fw5vpvpaq.crx3 | unknown | — | — | whitelisted |
7908 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fhtuazrdjnqikxtln4pvzfahjq_20240720.656159207.14/obedbbhbpmojnkanicioggnmelmoomoc_20240720.656159207.14_all_ENUS500000_kewn2vupl47qk3g57fw5vpvpaq.crx3 | unknown | — | — | whitelisted |
7908 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fhtuazrdjnqikxtln4pvzfahjq_20240720.656159207.14/obedbbhbpmojnkanicioggnmelmoomoc_20240720.656159207.14_all_ENUS500000_kewn2vupl47qk3g57fw5vpvpaq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3140 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4560 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6504 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6780 | chrome.exe | 62.97.140.24:443 | track.mdrctr.com | Prosodie Iberica Sl | ES | unknown |
6780 | chrome.exe | 74.125.128.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6780 | chrome.exe | 216.58.212.174:443 | drive.google.com | GOOGLE | US | whitelisted |
6780 | chrome.exe | 142.250.185.106:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
track.mdrctr.com |
| unknown |
accounts.google.com |
| whitelisted |
drive.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
play.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|