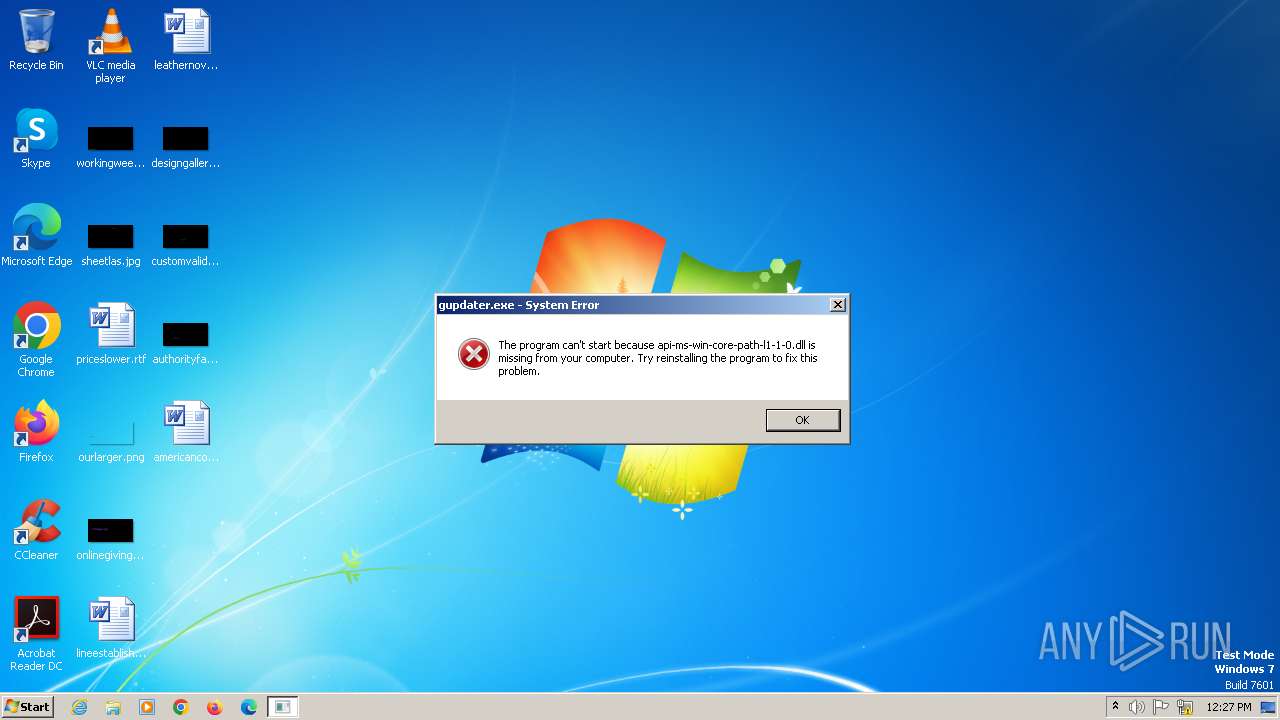
| File name: | updater.exe |
| Full analysis: | https://app.any.run/tasks/1094670c-75fd-49b6-8e23-0f88120dc7d6 |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2023, 12:27:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 8589B564A5ED7920BE4B1B08F3D6D8ED |
| SHA1: | 6F73743F61238A9746BA9E6EF3B5BF495F22F4A3 |
| SHA256: | E380482FC3D8C4FE11073F9734238D60AB66385E3261231358F7D02082B235CD |
| SSDEEP: | 196608:h1pjCaBTtz/IeWcOpVTlMv/KBcKuo2dTu+kvHM2Z3KQXe2:h1pjCaVtz/VWvpxlAilDWT1qPh |
MALICIOUS
Drops the executable file immediately after the start
- updater.exe (PID: 2228)
- gupdater.exe (PID: 2612)
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Application was injected by another process
- svchost.exe (PID: 692)
- lsm.exe (PID: 508)
- services.exe (PID: 484)
- lsass.exe (PID: 500)
- svchost.exe (PID: 1056)
- spoolsv.exe (PID: 1028)
- svchost.exe (PID: 1956)
- svchost.exe (PID: 1708)
- svchost.exe (PID: 852)
- svchost.exe (PID: 824)
- IMEDICTUPDATE.EXE (PID: 1244)
- svchost.exe (PID: 1184)
- wmpnetwk.exe (PID: 1104)
- svchost.exe (PID: 1656)
- dllhost.exe (PID: 952)
- dllhost.exe (PID: 2688)
- svchost.exe (PID: 608)
- winlogon.exe (PID: 448)
- svchost.exe (PID: 780)
- svchost.exe (PID: 884)
- svchost.exe (PID: 324)
- explorer.exe (PID: 1944)
- conhost.exe (PID: 584)
- TrustedInstaller.exe (PID: 2684)
- dllhost.exe (PID: 2052)
- conhost.exe (PID: 1660)
- conhost.exe (PID: 2284)
- conhost.exe (PID: 3068)
- conhost.exe (PID: 2268)
- conhost.exe (PID: 2040)
- dwm.exe (PID: 1884)
- conhost.exe (PID: 2388)
- conhost.exe (PID: 712)
- WmiPrvSE.exe (PID: 2656)
- conhost.exe (PID: 2852)
Adds extension to the Windows Defender exclusion list
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Runs injected code in another process
- dialer.exe (PID: 2972)
- dialer.exe (PID: 2764)
Creates a writable file the system directory
- powershell.exe (PID: 1788)
- TrustedInstaller.exe (PID: 2684)
SUSPICIOUS
Searches for installed software
- svchost.exe (PID: 824)
BASE64 encoded PowerShell command has been detected
- updater.exe (PID: 2228)
Reads the Internet Settings
- updater.exe (PID: 2228)
- powershell.exe (PID: 3008)
Starts POWERSHELL.EXE for commands execution
- updater.exe (PID: 2228)
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Process drops legitimate windows executable
- updater.exe (PID: 2228)
- gupdater.exe (PID: 2612)
Base64-obfuscated command line is found
- updater.exe (PID: 2228)
Application launched itself
- gupdater.exe (PID: 2612)
Loads Python modules
- gupdater.exe (PID: 568)
Adds/modifies Windows certificates
- updater.exe (PID: 2228)
- services.exe (PID: 484)
Starts CMD.EXE for commands execution
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Script adds exclusion extension to Windows Defender
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Starts SC.EXE for service management
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Script adds exclusion path to Windows Defender
- mupdater.exe (PID: 2904)
- fgqgjrcfhjsu.exe (PID: 2820)
Executes as Windows Service
- fgqgjrcfhjsu.exe (PID: 2820)
Drops a system driver (possible attempt to evade defenses)
- fgqgjrcfhjsu.exe (PID: 2820)
Connects to unusual port
- dialer.exe (PID: 1844)
The Powershell connects to the Internet
- powershell.exe (PID: 1788)
Checks Windows Trust Settings
- TrustedInstaller.exe (PID: 2684)
Unusual connection from system programs
- powershell.exe (PID: 1788)
The process drops C-runtime libraries
- gupdater.exe (PID: 2612)
INFO
Checks supported languages
- updater.exe (PID: 2228)
- gupdater.exe (PID: 2612)
- gupdater.exe (PID: 568)
- mupdater.exe (PID: 2904)
- TrustedInstaller.exe (PID: 2684)
- fgqgjrcfhjsu.exe (PID: 2820)
Reads the computer name
- updater.exe (PID: 2228)
- gupdater.exe (PID: 2612)
- TrustedInstaller.exe (PID: 2684)
Create files in a temporary directory
- updater.exe (PID: 2228)
- gupdater.exe (PID: 2612)
Creates files in the program directory
- mupdater.exe (PID: 2904)
Reads the machine GUID from the registry
- TrustedInstaller.exe (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2048 |
| InitializedDataSize: | 12895232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14d1 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 114.0.5735.135 |
| ProductVersionNumber: | 114.0.5735.135 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Google Chrome |
| FileTitle: | - |
| FileDescription: | Google Chrome |
| FileVersion: | 114,0,5735,135 |
| LegalCopyright: | Copyright 2023 Google LLC. All rights reserved. |
| LegalTrademark: | - |
| ProductName: | Google LLC |
| ProductVersion: | 114,0,5735,135 |
Total processes
88
Monitored processes
68
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | C:\Windows\system32\sc.exe stop wuauserv | C:\Windows\System32\sc.exe | — | fgqgjrcfhjsu.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 1062 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 484 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 500 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7601.23915 (win7sp1_ldr.170913-0600) Modules
| |||||||||||||||
| 508 | C:\Windows\system32\lsm.exe | C:\Windows\System32\lsm.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Users\admin\AppData\Local\Temp\gupdater.exe" | C:\Users\admin\AppData\Local\Temp\gupdater.exe | — | gupdater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Security Center Elevated UI App Exit code: 0 Version: 10.0.19041.1949 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 584 | \??\C:\Windows\system32\conhost.exe "-694631943173716261876801617518926192292658369110195015681694301531490977172" | C:\Windows\System32\conhost.exe | csrss.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 608 | C:\Windows\system32\svchost.exe -k DcomLaunch | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 692 | C:\Windows\system32\svchost.exe -k RPCSS | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
43 844
Read events
43 735
Write events
109
Delete events
0
Modification events
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A000000000200000000001066000000010000200000003A7AE26404D75DF41C31FF40C5EA8CE90BAF74FA9E9BD7A9ACA34C7048350C1E000000000E8000000002000020000000BD2D56D46506C12C41A6A70B10E79EE53CB79EF36FD2BA8CDD2460CB8F4BE86A300000009B5D1418CBF2EB49F3C4BD4C21D58CA55B82FA3D3ED08AF0EF59D6C7ECAFC1055FA323A80FF7C154B1C9B60253392B6640000000DED9FDCC168073324C3013F1BB125E066EB1A2F09FD2C8E7CC7A793AA992E21EF1C942BF7294D04E036428704009B863B1CB981B97312E2530E3E816780CF7C9 | |||
| (PID) Process: | (884) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-3896776584-4254864009-862391680-1000 |
| Operation: | write | Name: | RefCount |
Value: 5 | |||
| (PID) Process: | (884) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-3896776584-4254864009-862391680-1000 |
| Operation: | write | Name: | RefCount |
Value: 6 | |||
| (PID) Process: | (2228) updater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2228) updater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2228) updater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2228) updater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1296) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1296) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E81D000000010000001000000073B6876195F5D18E048510422AEF04E314000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E090000000100000016000000301406082B0601050507030206082B060105050703010B000000010000001A0000004900530052004700200052006F006F007400200058003100000062000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C620000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (1296) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6362000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F0074002000580031000000090000000100000016000000301406082B0601050507030206082B0601050507030114000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E3030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E820000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
Executable files
22
Suspicious files
15
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\_bz2.pyd | executable | |
MD5:2D461B41F6E9A305DDE68E9C59E4110A | SHA256:ABBE3933A34A9653A757244E8E55B0D7D3A108527A3E9E8A7F2013B5F2A9EFF4 | |||
| 2228 | updater.exe | C:\Users\admin\AppData\Local\Temp\mupdater.exe | executable | |
MD5:74F468BBFEA77390B32D574FA2980FB8 | SHA256:0BBFE17F684A3946B76FC48FD788B632CAC3AD8B4A60AB6207A35D0D80584758 | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\base_library.zip | compressed | |
MD5:D0C4A6ABB0467F290879FFC87C1B4340 | SHA256:E4B50592185744830D7706D4B53DF4FA5E37F8A52F36E58BD46516BE92BB1E2D | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\_queue.pyd | executable | |
MD5:DECDABACA104520549B0F66C136A9DC1 | SHA256:9D4880F7D0129B1DE95BECD8EA8BBBF0C044D63E87764D18F9EC00D382E43F84 | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\blank.aes | binary | |
MD5:79C3F541D1536B03C6B88D9987300145 | SHA256:424FB8AC515ED91209664FFC28CFCC402003F039DD7BEC856478A7EB37F9C98D | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\_ssl.pyd | executable | |
MD5:2089768E25606262921E4424A590FF05 | SHA256:3E6E9FC56E1A9FE5EDB39EE03E5D47FA0E3F6ADB17BE1F087DC6F891D3B0BBCA | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\_socket.pyd | executable | |
MD5:BCC3E26A18D59D76FD6CF7CD64E9E14D | SHA256:4E19F29266A3D6C127E5E8DE01D2C9B68BC55075DD3D6AABE22CF0DE4B946A98 | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\_sqlite3.pyd | executable | |
MD5:EB6313B94292C827A5758EEA82D018D9 | SHA256:6B41DFD7D6AC12AFE523D74A68F8BD984A75E438DCF2DAA23A1F934CA02E89DA | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\libcrypto-1_1.dll | executable | |
MD5:DFFCAB08F94E627DE159E5B27326D2FC | SHA256:135B115E77479EEDD908D7A782E004ECE6DD900BB1CA05CC1260D5DD6273EF15 | |||
| 2612 | gupdater.exe | C:\Users\admin\AppData\Local\Temp\_MEI26122\libssl-1_1.dll | executable | |
MD5:8E8A145E122A593AF7D6CDE06D2BB89F | SHA256:A6A14C1BECCBD4128763E78C3EC588F747640297FFB3CC5604A9728E8EF246B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1788 | powershell.exe | GET | 200 | 8.241.11.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?aaf63d5367c1b31c | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1788 | powershell.exe | 8.241.11.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
1844 | dialer.exe | 162.19.139.184:12222 | xmr.2miners.com | OVH SAS | FR | unknown |
1844 | dialer.exe | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
1844 | dialer.exe | 66.29.148.6:443 | online.badbull.pro | NAMECHEAP-NET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
xmr.2miners.com |
| unknown |
pastebin.com |
| shared |
online.badbull.pro |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER Observed DNS Query to Cryptocurrency Mining Pool Domain (xmr .2miners .com) |