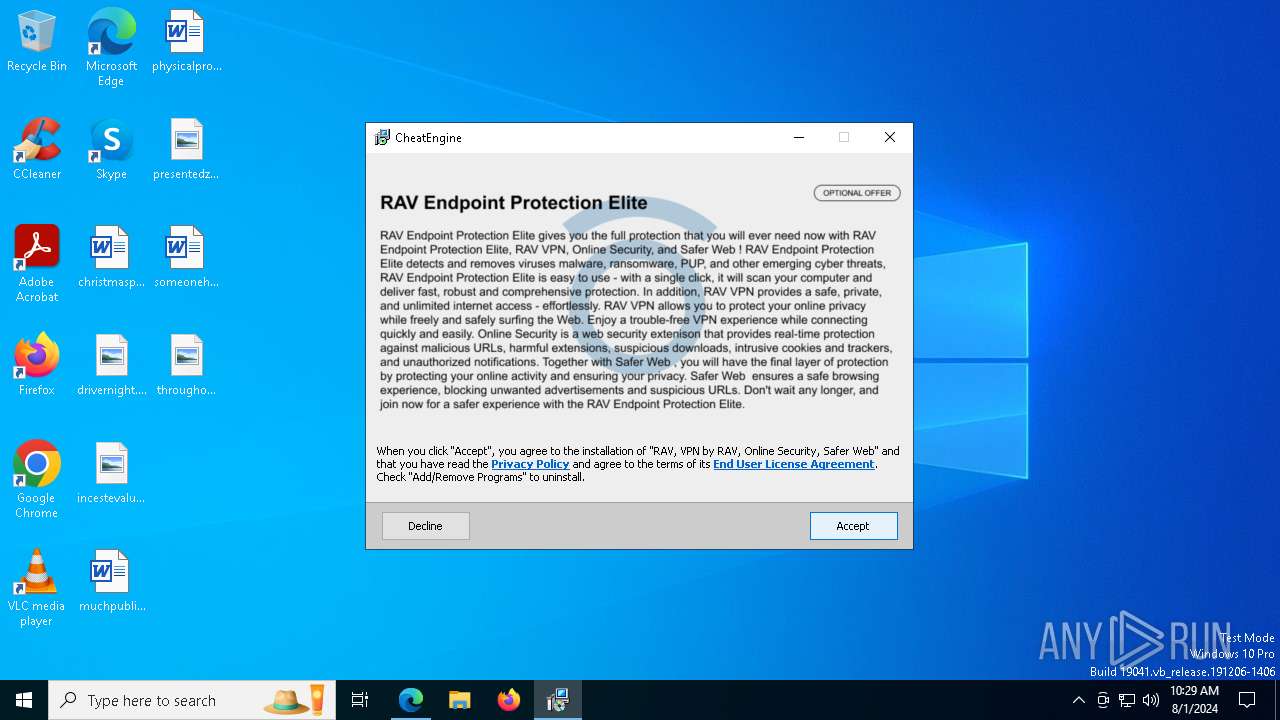
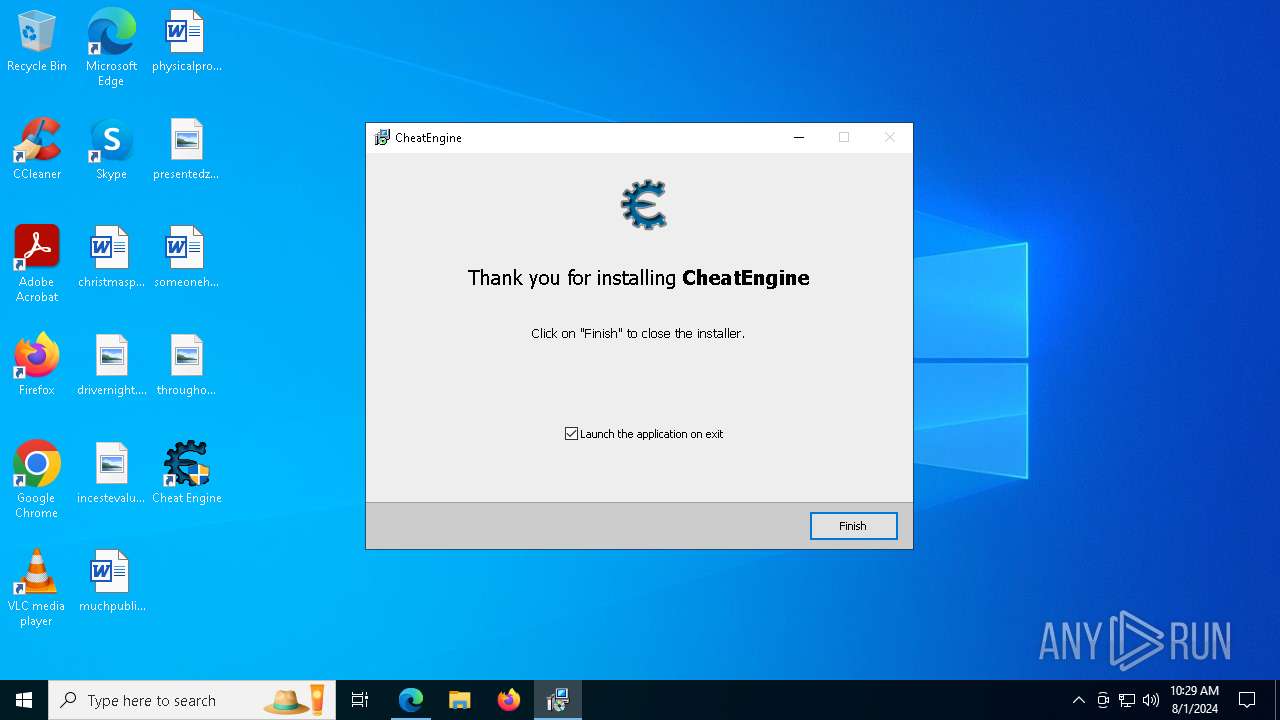
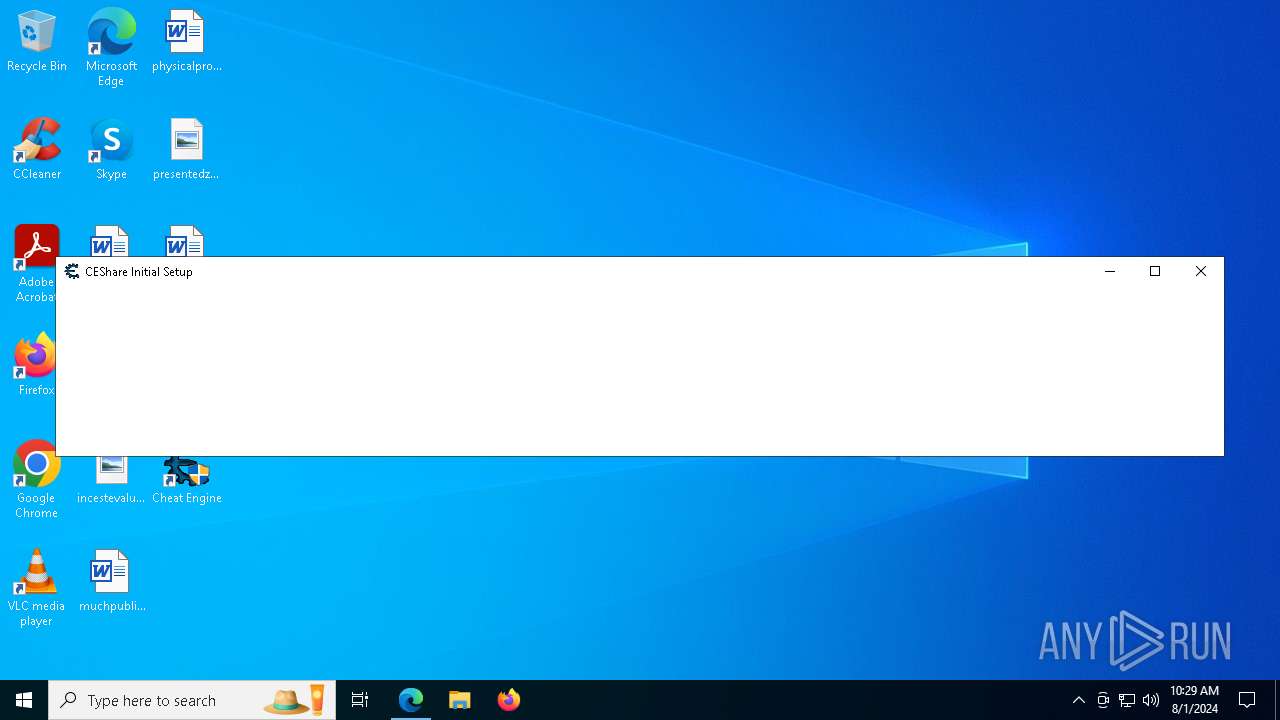
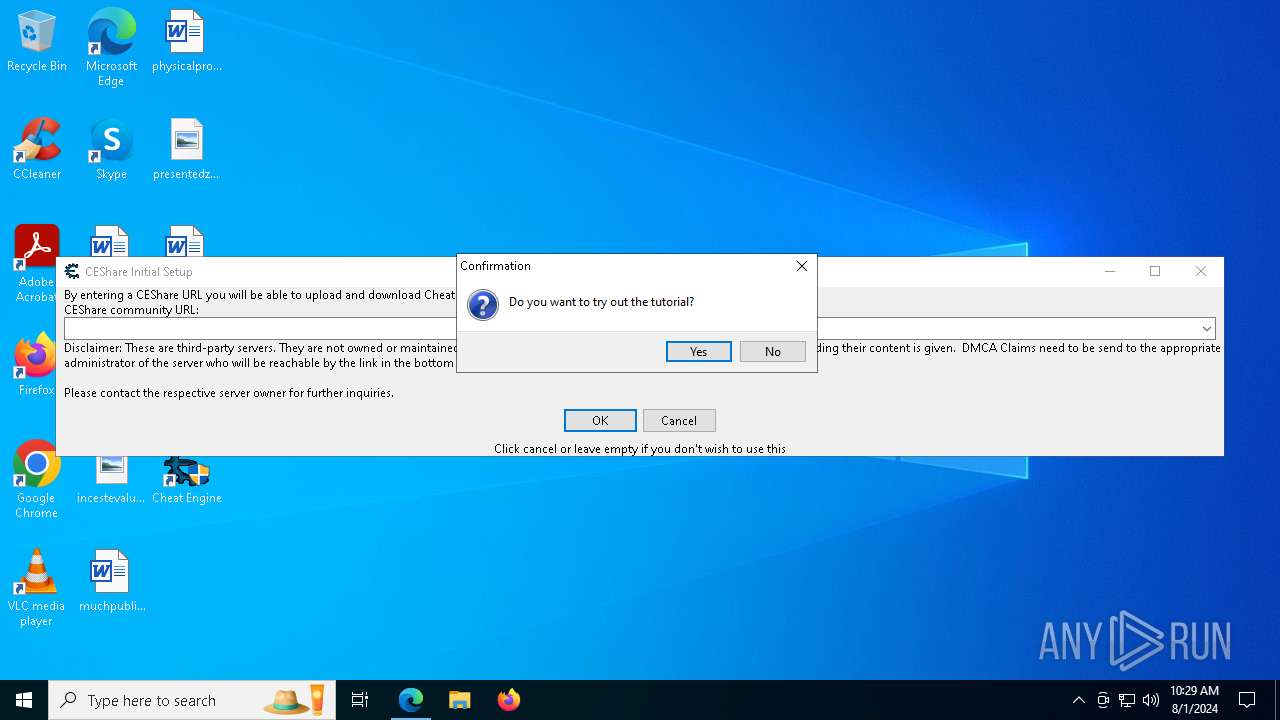
| URL: | https://www.cheatengine.org |
| Full analysis: | https://app.any.run/tasks/b8d26b8e-feb1-4d99-bffd-0df5423e60f1 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | August 01, 2024, 10:28:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 074644CB619C7D7A6FED51ED8397D8BF |
| SHA1: | 4DE130ECAAB27FD31DBC63BCEF13528F24C9A7AE |
| SHA256: | E34D72163557CE3472691207E46D68592B98F1291022F22A84C0315CE8790CD6 |
| SSDEEP: | 3:N8DSLHC:2OLHC |
MALICIOUS
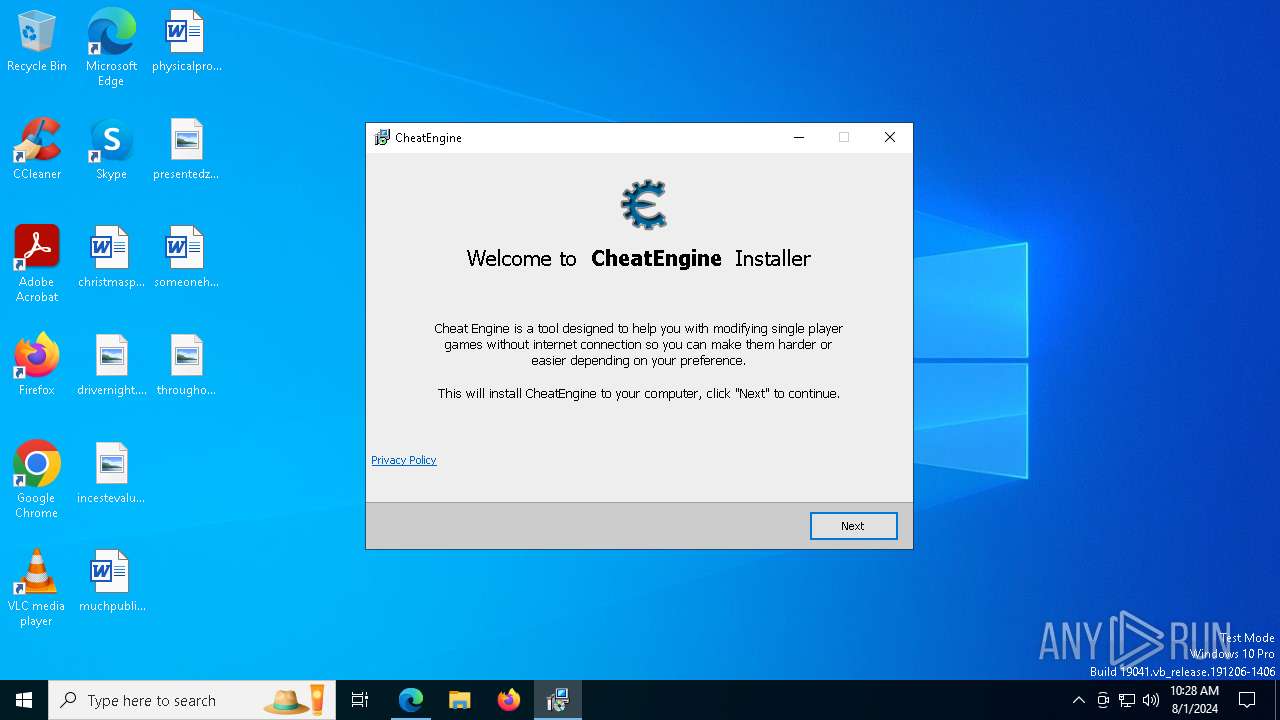
Drops the executable file immediately after the start
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.exe (PID: 7400)
- prod0.exe (PID: 3848)
- CheatEngine75.tmp (PID: 2436)
- 0j2phdx0.exe (PID: 5908)
- UnifiedStub-installer.exe (PID: 6044)
Starts NET.EXE for service management
- CheatEngine75.tmp (PID: 2436)
- net.exe (PID: 3140)
- net.exe (PID: 7888)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 6044)
- rsEngineSvc.exe (PID: 7212)
Changes the autorun value in the registry
- rundll32.exe (PID: 7376)
SUSPICIOUS
Reads security settings of Internet Explorer
- CheatEngine75.tmp (PID: 2532)
- cookie_exporter.exe (PID: 3700)
- CheatEngine75.tmp (PID: 3844)
- prod0.exe (PID: 3848)
- Cheat Engine.exe (PID: 7312)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- Cheat Engine.exe (PID: 3068)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 3164)
- rsWSC.exe (PID: 7832)
- UnifiedStub-installer.exe (PID: 6044)
- rsEngineSvc.exe (PID: 8148)
Executable content was dropped or overwritten
- CheatEngine75.exe (PID: 7776)
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.exe (PID: 2872)
- CheatEngine75.exe (PID: 7400)
- CheatEngine75.tmp (PID: 2436)
- prod0.exe (PID: 3848)
- 0j2phdx0.exe (PID: 5908)
- UnifiedStub-installer.exe (PID: 6044)
Reads the date of Windows installation
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.tmp (PID: 2532)
- prod0.exe (PID: 3848)
- Cheat Engine.exe (PID: 7312)
- Cheat Engine.exe (PID: 3068)
Reads the Windows owner or organization settings
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.tmp (PID: 2436)
Uses ICACLS.EXE to modify access control lists
- CheatEngine75.tmp (PID: 2436)
Starts SC.EXE for service management
- CheatEngine75.tmp (PID: 2436)
Process drops legitimate windows executable
- 0j2phdx0.exe (PID: 5908)
- CheatEngine75.tmp (PID: 2436)
- UnifiedStub-installer.exe (PID: 6044)
Process drops SQLite DLL files
- CheatEngine75.tmp (PID: 2436)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 6044)
Searches for installed software
- UnifiedStub-installer.exe (PID: 6044)
Executes as Windows Service
- rsSyncSvc.exe (PID: 7696)
- rsWSC.exe (PID: 240)
- rsClientSvc.exe (PID: 1812)
- rsEngineSvc.exe (PID: 7212)
Detected use of alternative data streams (AltDS)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 3164)
Checks Windows Trust Settings
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- UnifiedStub-installer.exe (PID: 6044)
- rsWSC.exe (PID: 7832)
- rsWSC.exe (PID: 240)
- rsEngineSvc.exe (PID: 8148)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 6044)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 6044)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 6044)
The process creates files with name similar to system file names
- UnifiedStub-installer.exe (PID: 6044)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 6044)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 6044)
- rundll32.exe (PID: 7376)
Adds/modifies Windows certificates
- UnifiedStub-installer.exe (PID: 6044)
- rsWSC.exe (PID: 7832)
There is functionality for communication over UDP network (YARA)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 3164)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 6044)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 6044)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 6328)
Reads the computer name
- cookie_exporter.exe (PID: 3700)
- identity_helper.exe (PID: 5760)
- CheatEngine75.tmp (PID: 2532)
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.tmp (PID: 2436)
- prod0.exe (PID: 3848)
- UnifiedStub-installer.exe (PID: 6044)
- rsSyncSvc.exe (PID: 2384)
- Kernelmoduleunloader.exe (PID: 1044)
- rsSyncSvc.exe (PID: 7696)
- Cheat Engine.exe (PID: 7312)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 3164)
- Cheat Engine.exe (PID: 3068)
- rsWSC.exe (PID: 7832)
- rsWSC.exe (PID: 240)
- rsClientSvc.exe (PID: 2180)
- rsEngineSvc.exe (PID: 7212)
- rsClientSvc.exe (PID: 1812)
- rsEngineSvc.exe (PID: 8148)
Reads Environment values
- cookie_exporter.exe (PID: 3700)
- identity_helper.exe (PID: 5760)
- prod0.exe (PID: 3848)
- UnifiedStub-installer.exe (PID: 6044)
- rsEngineSvc.exe (PID: 7212)
Checks proxy server information
- cookie_exporter.exe (PID: 3700)
- CheatEngine75.tmp (PID: 3844)
- prod0.exe (PID: 3848)
- UnifiedStub-installer.exe (PID: 6044)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- rsWSC.exe (PID: 7832)
Checks supported languages
- cookie_exporter.exe (PID: 3700)
- identity_helper.exe (PID: 5760)
- CheatEngine75.tmp (PID: 2532)
- CheatEngine75.exe (PID: 7776)
- prod0.exe (PID: 3848)
- CheatEngine75.exe (PID: 2872)
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.exe (PID: 7400)
- CheatEngine75.tmp (PID: 2436)
- _setup64.tmp (PID: 7128)
- 0j2phdx0.exe (PID: 5908)
- UnifiedStub-installer.exe (PID: 6044)
- rsSyncSvc.exe (PID: 2384)
- rsSyncSvc.exe (PID: 7696)
- Kernelmoduleunloader.exe (PID: 1044)
- Cheat Engine.exe (PID: 7312)
- windowsrepair.exe (PID: 7256)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 3164)
- Cheat Engine.exe (PID: 3068)
- rsWSC.exe (PID: 7832)
- rsWSC.exe (PID: 240)
- rsClientSvc.exe (PID: 2180)
- rsClientSvc.exe (PID: 1812)
- rsEngineSvc.exe (PID: 7212)
- rsEngineSvc.exe (PID: 8148)
Executable content was dropped or overwritten
- msedge.exe (PID: 6328)
- msedge.exe (PID: 6564)
Drops the executable file immediately after the start
- msedge.exe (PID: 6328)
- msedge.exe (PID: 6564)
The process uses the downloaded file
- msedge.exe (PID: 6328)
- msedge.exe (PID: 5372)
Create files in a temporary directory
- CheatEngine75.exe (PID: 7776)
- CheatEngine75.exe (PID: 2872)
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.exe (PID: 7400)
- prod0.exe (PID: 3848)
- CheatEngine75.tmp (PID: 2436)
- 0j2phdx0.exe (PID: 5908)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- UnifiedStub-installer.exe (PID: 6044)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 3164)
Reads the software policy settings
- CheatEngine75.tmp (PID: 3844)
- prod0.exe (PID: 3848)
- UnifiedStub-installer.exe (PID: 6044)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- rsWSC.exe (PID: 7832)
- rsEngineSvc.exe (PID: 7212)
- rsWSC.exe (PID: 240)
- rsEngineSvc.exe (PID: 8148)
Reads the machine GUID from the registry
- CheatEngine75.tmp (PID: 3844)
- prod0.exe (PID: 3848)
- UnifiedStub-installer.exe (PID: 6044)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- rsWSC.exe (PID: 7832)
- rsWSC.exe (PID: 240)
- rsEngineSvc.exe (PID: 7212)
- rsEngineSvc.exe (PID: 8148)
Process checks computer location settings
- CheatEngine75.tmp (PID: 3844)
- CheatEngine75.tmp (PID: 2532)
- prod0.exe (PID: 3848)
- Cheat Engine.exe (PID: 7312)
- Cheat Engine.exe (PID: 3068)
Disables trace logs
- prod0.exe (PID: 3848)
- UnifiedStub-installer.exe (PID: 6044)
- rsEngineSvc.exe (PID: 7212)
Application launched itself
- msedge.exe (PID: 6328)
Creates files in the program directory
- CheatEngine75.tmp (PID: 2436)
- UnifiedStub-installer.exe (PID: 6044)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- rsWSC.exe (PID: 7832)
- rsEngineSvc.exe (PID: 7212)
- rsEngineSvc.exe (PID: 8148)
Creates a software uninstall entry
- CheatEngine75.tmp (PID: 2436)
Creates files or folders in the user directory
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 1216)
- UnifiedStub-installer.exe (PID: 6044)
- rsWSC.exe (PID: 7832)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 6044)
Manual execution by a user
- Cheat Engine.exe (PID: 7140)
- Cheat Engine.exe (PID: 3068)
Reads the time zone
- runonce.exe (PID: 1172)
Reads security settings of Internet Explorer
- runonce.exe (PID: 1172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
245
Monitored processes
104
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6292 --field-trial-handle=2252,i,18364999002119939462,7185598151694098578,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 240 | "C:\Program Files\ReasonLabs\EPP\rsWSC.exe" | C:\Program Files\ReasonLabs\EPP\rsWSC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: rsWSC Version: 6.0.3.0 Modules
| |||||||||||||||
| 872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1504 --field-trial-handle=2252,i,18364999002119939462,7185598151694098578,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Cheat Engine 7.5\Kernelmoduleunloader.exe" /SETUP | C:\Program Files\Cheat Engine 7.5\Kernelmoduleunloader.exe | CheatEngine75.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1044 | "icacls" "C:\Program Files\Cheat Engine 7.5" /grant *S-1-15-2-1:(OI)(CI)(RX) | C:\Windows\System32\icacls.exe | — | CheatEngine75.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Cheat Engine 7.5\cheatengine-x86_64-SSE4-AVX2.exe" | C:\Program Files\Cheat Engine 7.5\cheatengine-x86_64-SSE4-AVX2.exe | Cheat Engine.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 7.5.0.7431 Modules
| |||||||||||||||
| 1448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rsClientSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
61 782
Read events
61 317
Write events
402
Delete events
63
Modification events
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31122429 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
626
Suspicious files
318
Text files
525
Unknown types
105
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe5649.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe5649.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe5649.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe5649.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe5659.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
196
DNS requests
204
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6564 | msedge.exe | GET | 304 | 2.16.241.15:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
6564 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
6564 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7356 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7408 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6328 | msedge.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
6328 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5240 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1860 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6328 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6564 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6564 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6564 | msedge.exe | 104.20.94.94:443 | www.cheatengine.org | CLOUDFLARENET | — | unknown |
6564 | msedge.exe | 13.107.246.60:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.cheatengine.org |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6564 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6564 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6564 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
Process | Message |
|---|---|
Kernelmoduleunloader.exe | Kernelmodule unloader |
Kernelmoduleunloader.exe | Running in wow64 |
Kernelmoduleunloader.exe | Setup. So do not show messages |
Kernelmoduleunloader.exe | attempting to unload |
Kernelmoduleunloader.exe | SCManager opened |
Kernelmoduleunloader.exe | count=0 |
Kernelmoduleunloader.exe | setup=true |
cheatengine-x86_64-SSE4-AVX2.exe | Lua thread terminated |