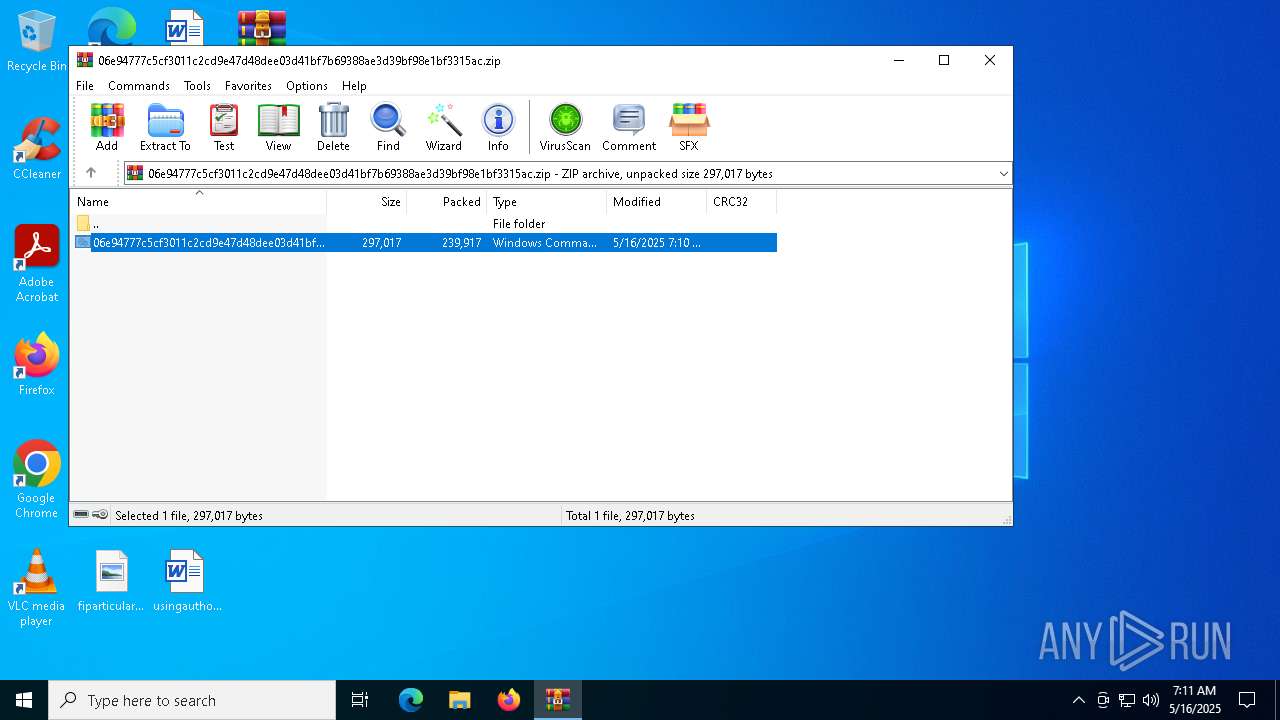
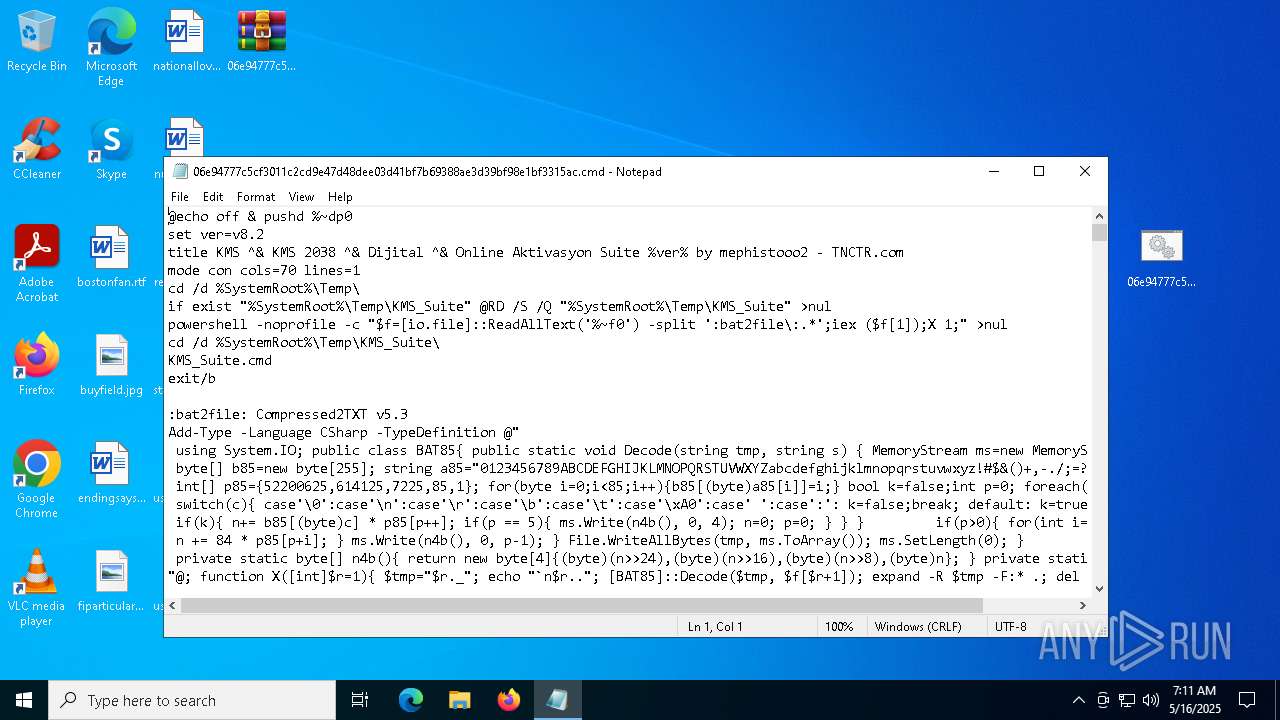
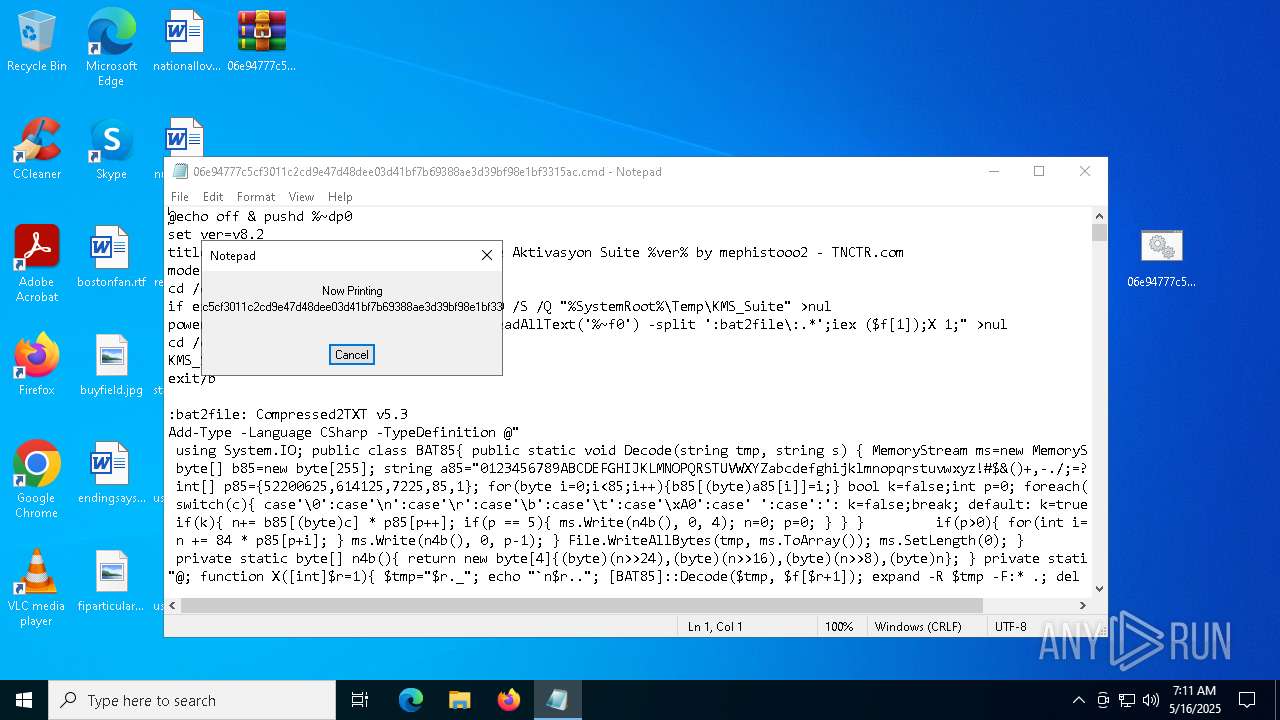
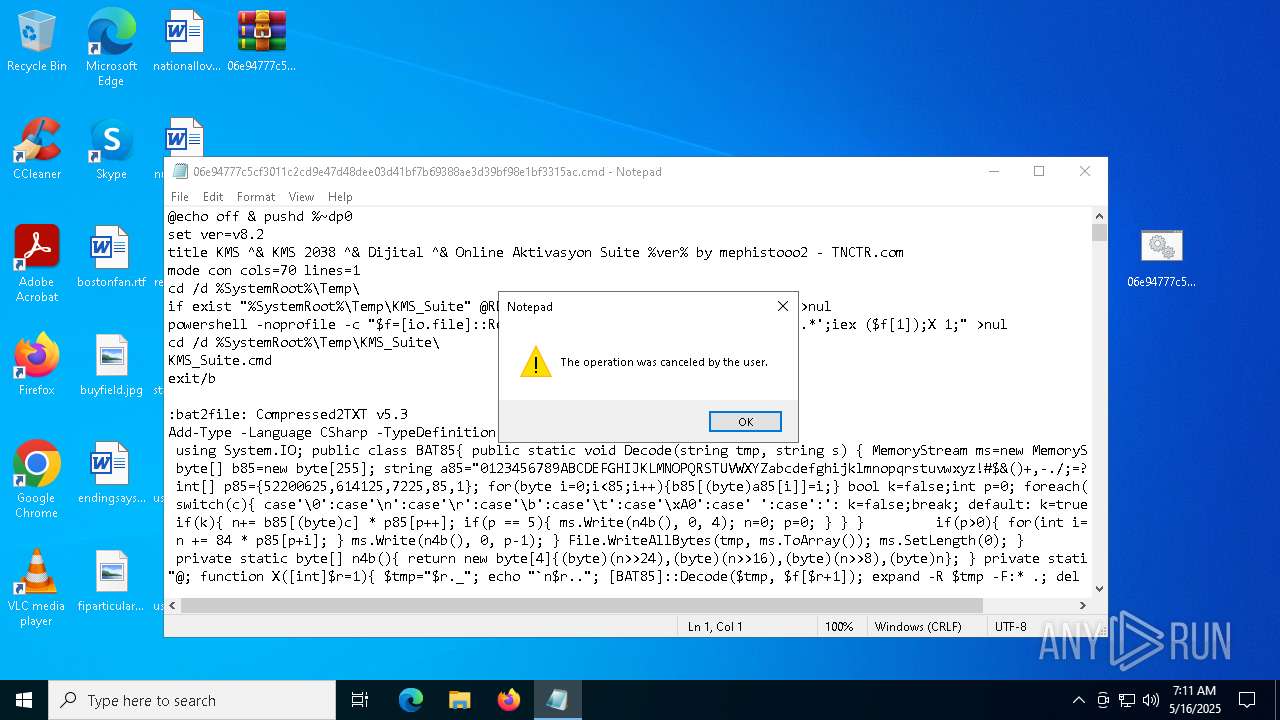
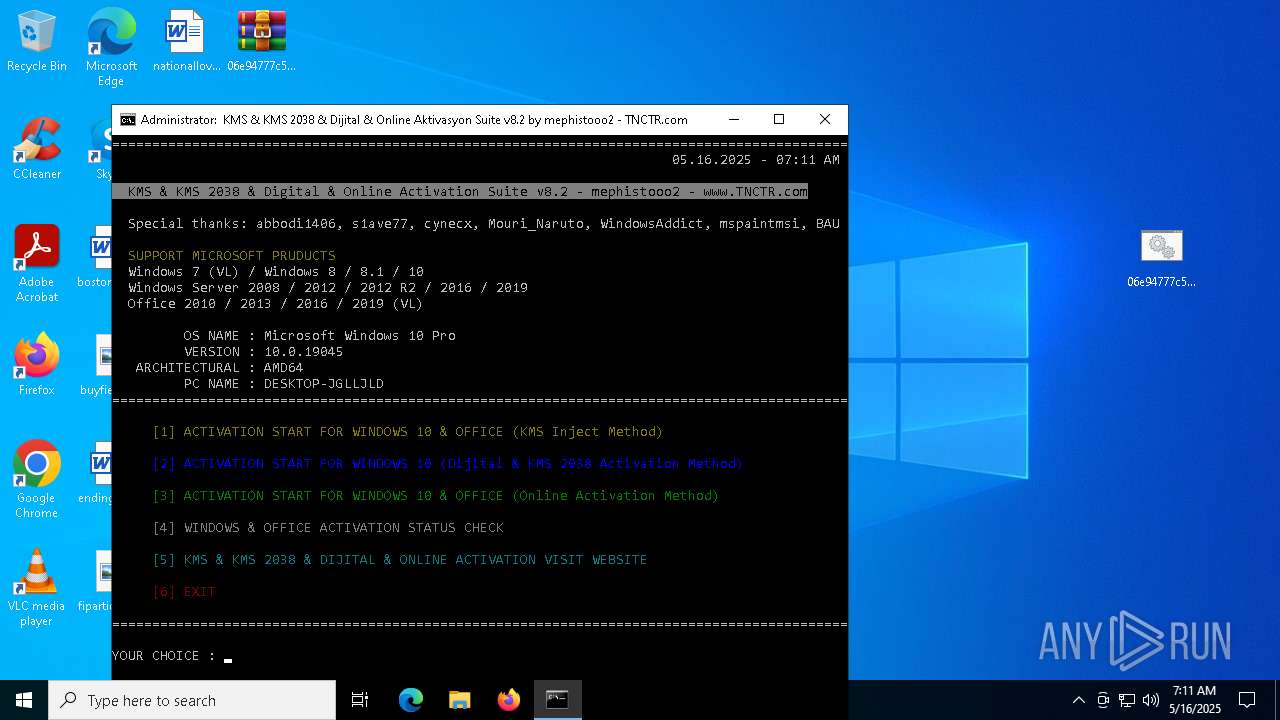
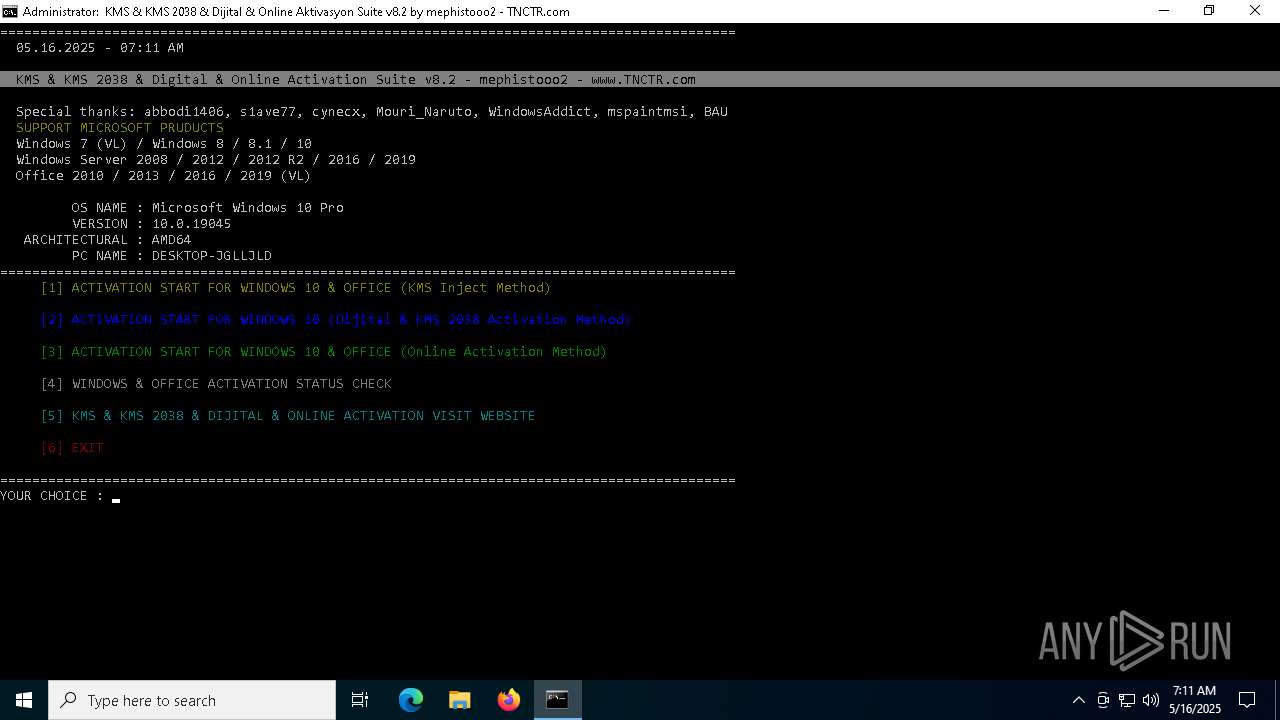
| File name: | 06e94777c5cf3011c2cd9e47d48dee03d41bf7b69388ae3d39bf98e1bf3315ac.zip |
| Full analysis: | https://app.any.run/tasks/0cd9812e-b094-45d3-9953-ca0be9596c93 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 07:10:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
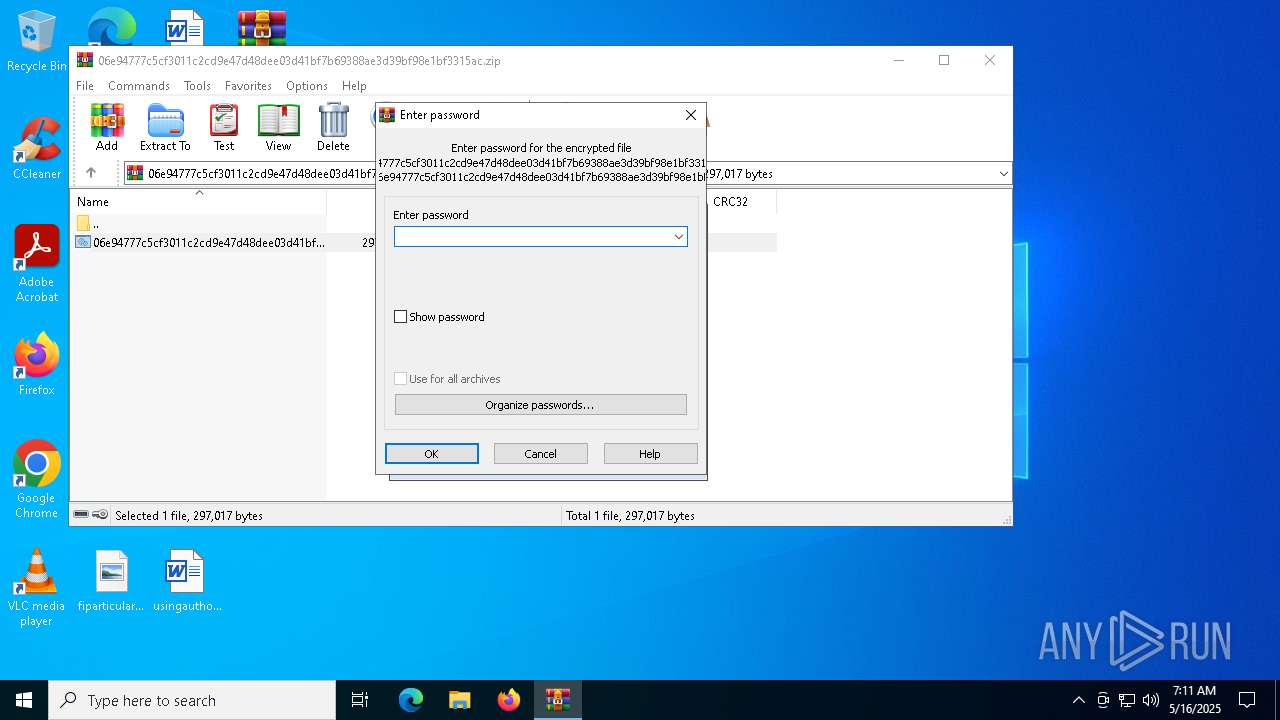
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 42F98CC2BB44627D97B609C21B8F86A4 |
| SHA1: | AF17F4676301D81AB98BDAACEDC5853D816D68B0 |
| SHA256: | E332FFEECBA06557E777A778F567CACD4FB3C6B041E49C2FA9BE29FA3A6F1A8D |
| SSDEEP: | 12288:HM3Vu8nxNDHr1UFf8XRnLPKjOJKvq1b0iIOdqV:HM33nxZ1UaX9SjNvub7IOdqV |
MALICIOUS
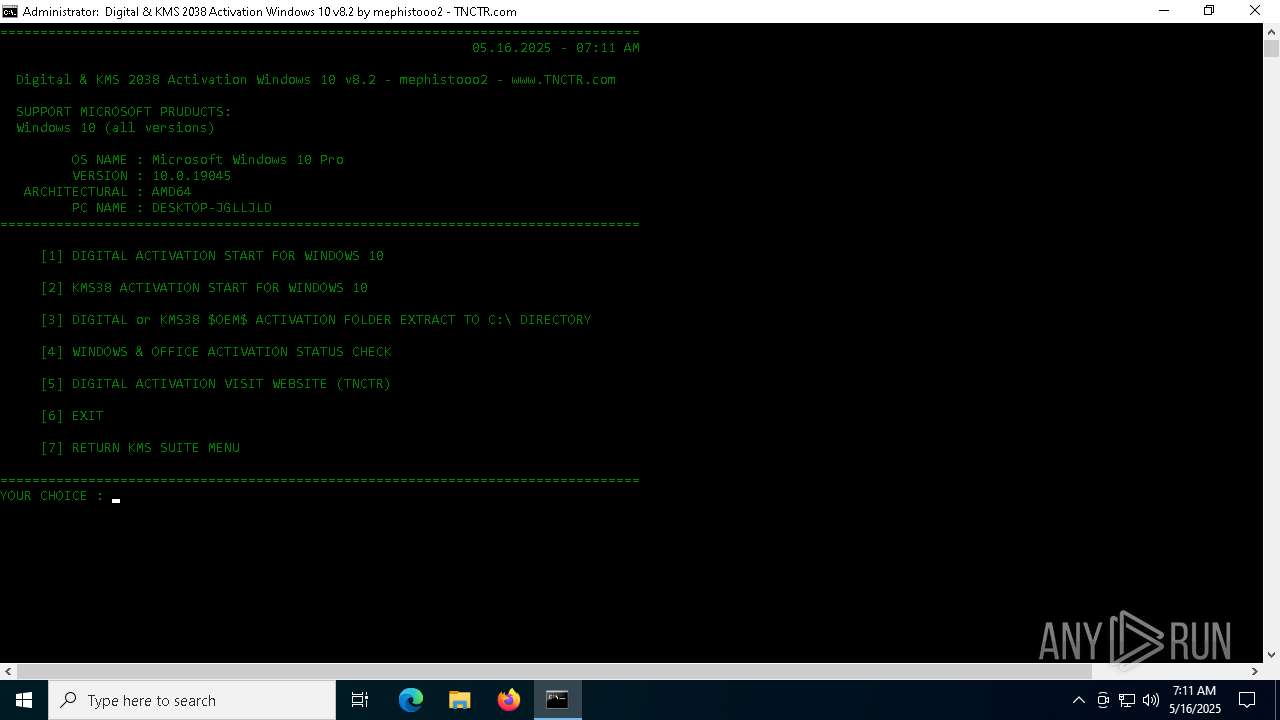
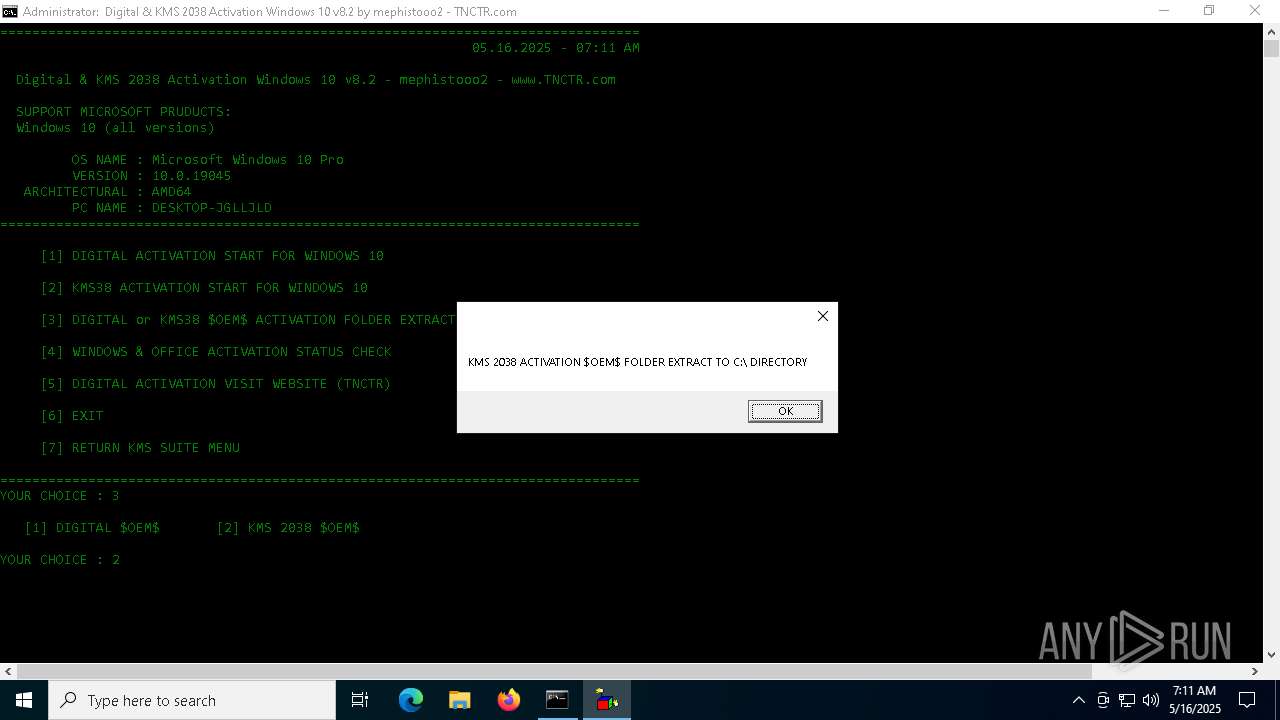
Generic archive extractor
- WinRAR.exe (PID: 5352)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1328)
- cmd.exe (PID: 6252)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1328)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1328)
Sets XML DOM element text (SCRIPT)
- notepad.exe (PID: 6816)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1328)
- cmd.exe (PID: 6252)
CSC.EXE is used to compile C# code
- csc.exe (PID: 812)
Unpacks CAB file
- expand.exe (PID: 4980)
Executable content was dropped or overwritten
- csc.exe (PID: 812)
- expand.exe (PID: 4980)
- xcopy.exe (PID: 6760)
- rundll32.exe (PID: 632)
Application launched itself
- cmd.exe (PID: 6252)
- ClipUp.exe (PID: 6816)
Process drops legitimate windows executable
- expand.exe (PID: 4980)
Runs shell command (SCRIPT)
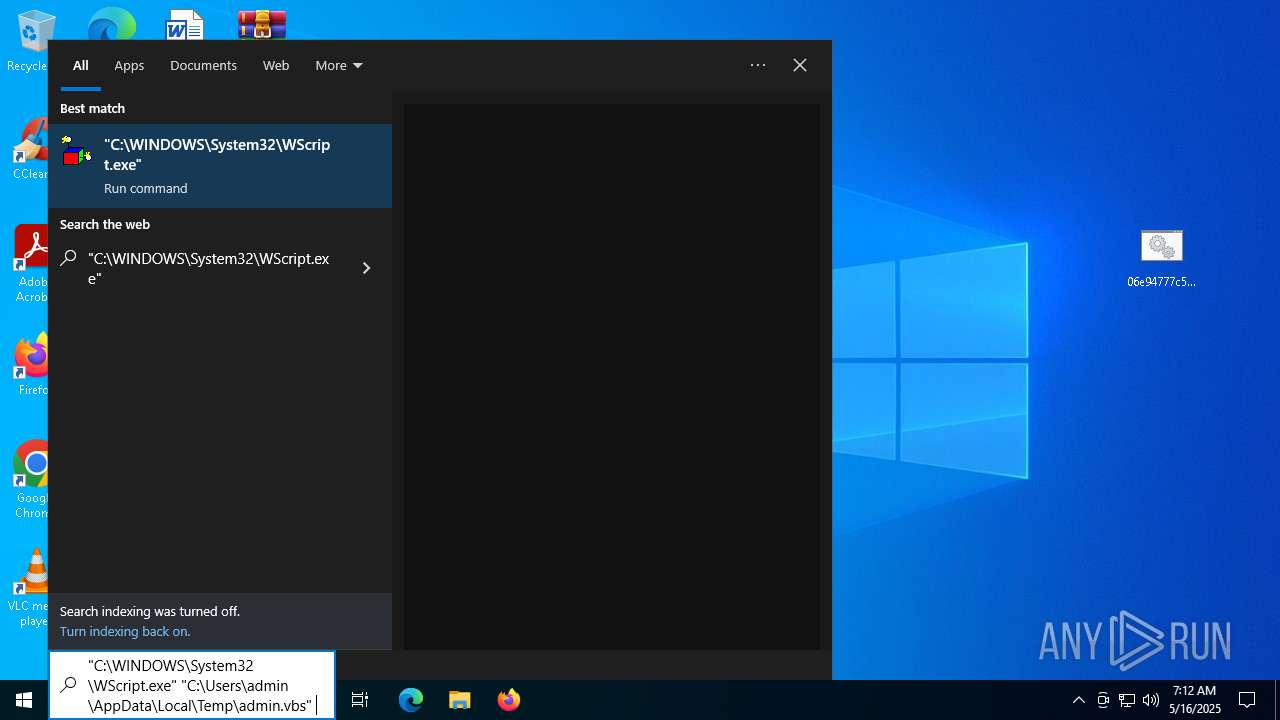
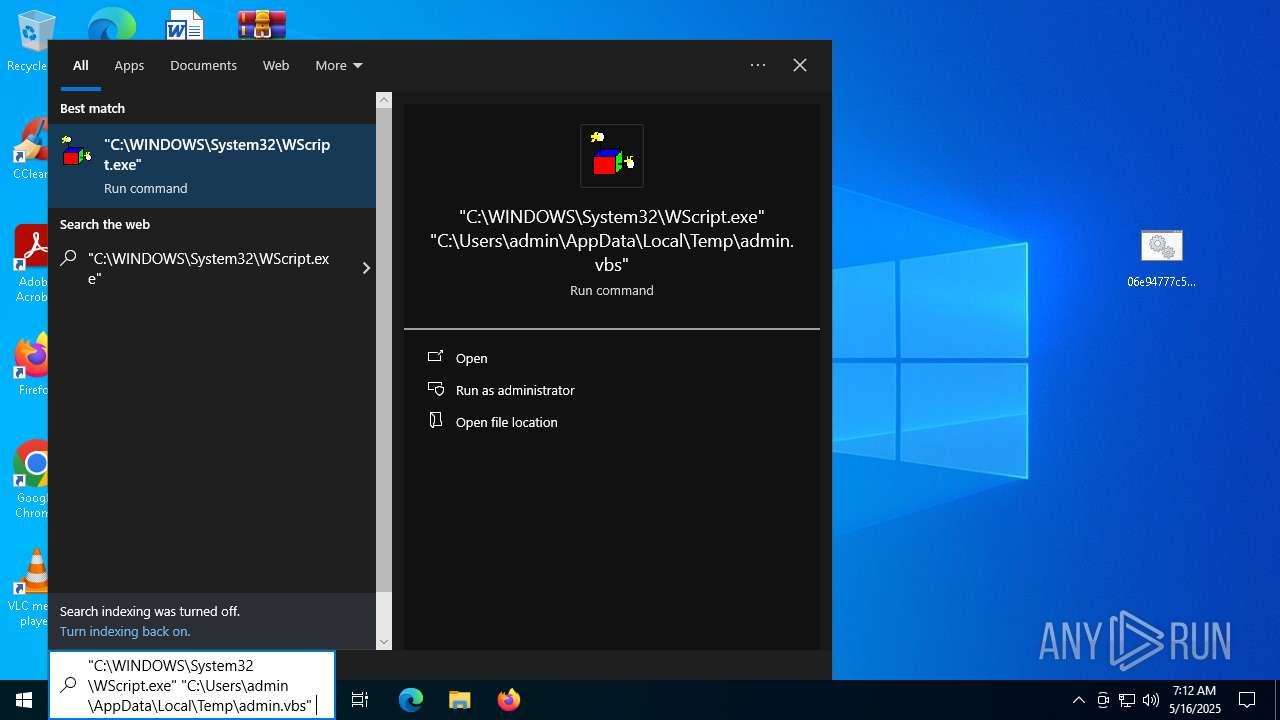
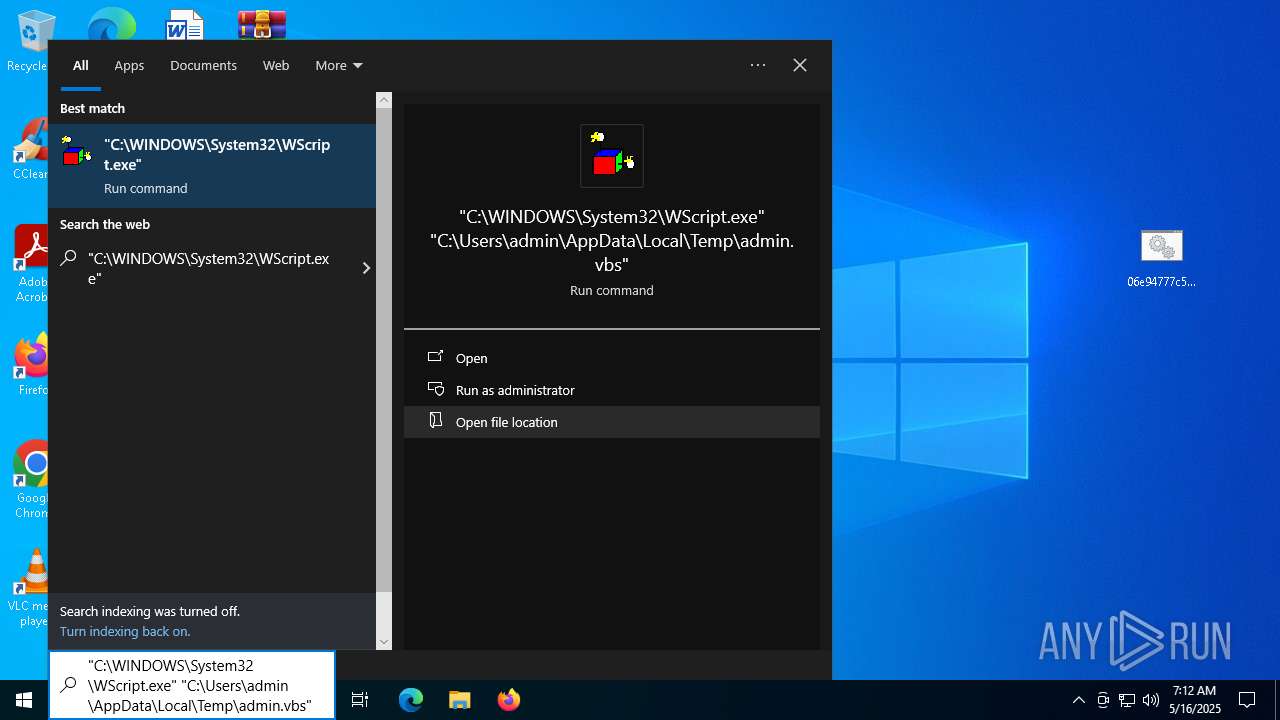
- wscript.exe (PID: 5728)
Executing commands from ".cmd" file
- wscript.exe (PID: 5728)
The process executes VB scripts
- cmd.exe (PID: 1328)
- cmd.exe (PID: 6252)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5728)
- cmd.exe (PID: 6252)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6252)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 208)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 6656)
- cmd.exe (PID: 5084)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 6644)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 4452)
Starts SC.EXE for service management
- cmd.exe (PID: 5304)
- cmd.exe (PID: 5968)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 4200)
- cmd.exe (PID: 6228)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 6252)
- cmd.exe (PID: 1184)
Windows service management via SC.EXE
- sc.exe (PID: 4436)
- sc.exe (PID: 2800)
- sc.exe (PID: 6576)
- sc.exe (PID: 6564)
- sc.exe (PID: 2092)
- sc.exe (PID: 7052)
- sc.exe (PID: 3676)
- sc.exe (PID: 856)
Sets the service to start on system boot
- sc.exe (PID: 6148)
Stops a currently running service
- sc.exe (PID: 3156)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4284)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2100)
- cscript.exe (PID: 6740)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 2100)
- cscript.exe (PID: 6740)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 2100)
- cscript.exe (PID: 6740)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6252)
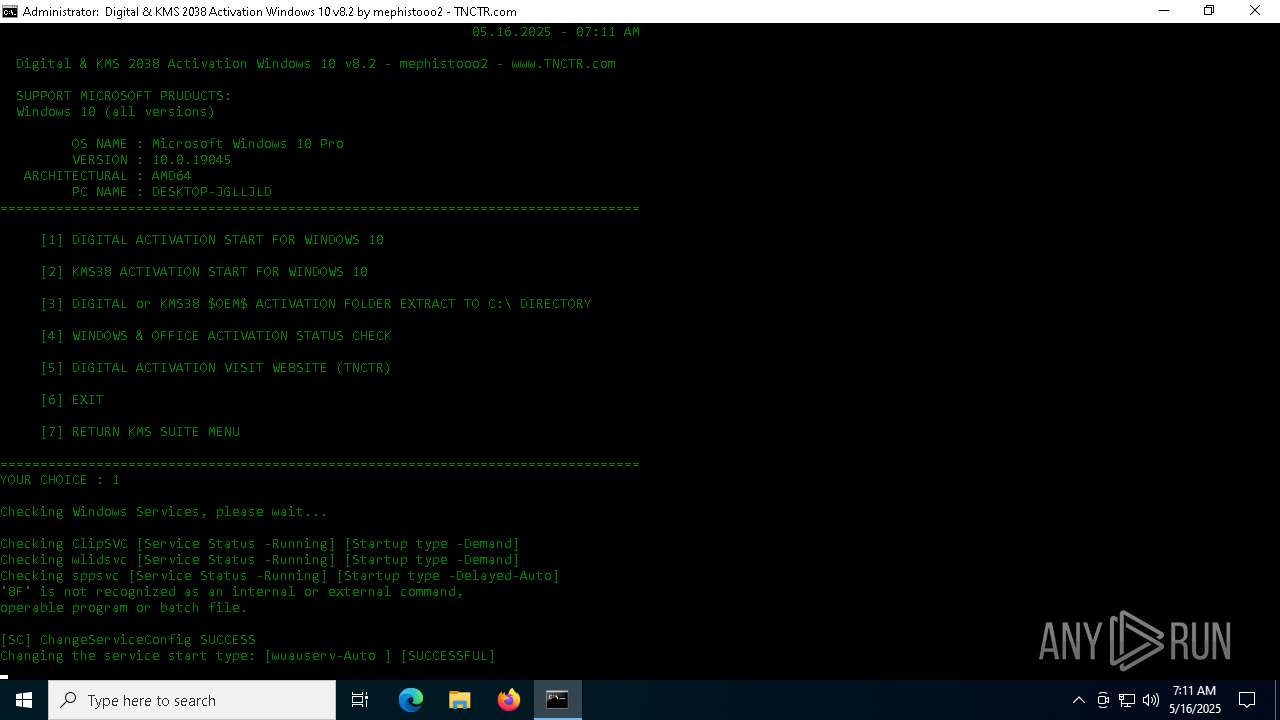
Starts a Microsoft application from unusual location
- gatherosstatemodified.exe (PID: 4000)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 6252)
INFO
Manual execution by a user
- cmd.exe (PID: 1328)
- notepad.exe (PID: 6816)
Starts MODE.COM to configure console settings
- mode.com (PID: 1040)
- mode.com (PID: 6268)
- mode.com (PID: 4040)
- mode.com (PID: 5244)
- mode.com (PID: 2268)
- mode.com (PID: 5200)
- mode.com (PID: 4188)
- mode.com (PID: 3968)
- mode.com (PID: 6960)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6816)
- WMIC.exe (PID: 6576)
- WMIC.exe (PID: 4980)
- WMIC.exe (PID: 1052)
- WMIC.exe (PID: 6512)
- WMIC.exe (PID: 208)
- WMIC.exe (PID: 2420)
- WMIC.exe (PID: 1116)
- WMIC.exe (PID: 2332)
- WMIC.exe (PID: 5132)
- WMIC.exe (PID: 2100)
- WMIC.exe (PID: 1616)
- WMIC.exe (PID: 4868)
- cscript.exe (PID: 2100)
- cscript.exe (PID: 6740)
Checks supported languages
- mode.com (PID: 1040)
- csc.exe (PID: 812)
- cvtres.exe (PID: 1452)
- expand.exe (PID: 4980)
- mode.com (PID: 4040)
- mode.com (PID: 6268)
- mode.com (PID: 5244)
- mode.com (PID: 5200)
- mode.com (PID: 2268)
- mode.com (PID: 4188)
- mode.com (PID: 3968)
- mode.com (PID: 6960)
- gatherosstatemodified.exe (PID: 4000)
Reads the machine GUID from the registry
- csc.exe (PID: 812)
- expand.exe (PID: 4980)
- gatherosstatemodified.exe (PID: 4000)
Create files in a temporary directory
- cvtres.exe (PID: 1452)
- csc.exe (PID: 812)
- ClipUp.exe (PID: 2240)
The sample compiled with english language support
- expand.exe (PID: 4980)
- xcopy.exe (PID: 6760)
- rundll32.exe (PID: 632)
Reads the software policy settings
- slui.exe (PID: 4784)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6972)
Reads the computer name
- gatherosstatemodified.exe (PID: 4000)
Creates files in the program directory
- ClipUp.exe (PID: 2240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:16 07:10:32 |
| ZipCRC: | 0x273f13a8 |
| ZipCompressedSize: | 239917 |
| ZipUncompressedSize: | 297017 |
| ZipFileName: | 06e94777c5cf3011c2cd9e47d48dee03d41bf7b69388ae3d39bf98e1bf3315ac.cmd |
Total processes
244
Monitored processes
106
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c "wmic Path Win32_OperatingSystem Get CSDVersion /format:LIST" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | wmic Path Win32_OperatingSystem Get Version /format:LIST | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | rundll32 "C:\Windows\Temp\KMS_Suite\bin\Digital\bin\slc.dll",PatchGatherosstate | C:\Windows\SysWOW64\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | findstr /v /a:2 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [3] ACTIVATION START FOR WINDOWS 10 & OFFICE (Online Activation Method)" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\3k02byue.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 856 | sc query sppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | findstr /v /a:3 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [5] KMS & KMS 2038 & DIJITAL & ONLINE ACTIVATION VISIT WEBSITE" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | mode con cols=70 lines=1 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | wmic path Win32_OperatingSystem get BuildNumber /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 222
Read events
20 163
Write events
58
Delete events
1
Modification events
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\06e94777c5cf3011c2cd9e47d48dee03d41bf7b69388ae3d39bf98e1bf3315ac.zip | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5352) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
16
Suspicious files
5
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5360 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hunycsva.b3s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5360 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3k02byue.cmdline | text | |
MD5:925115A37B254EFAC47C2F56109001A9 | SHA256:44F8818247AAEBD2DCF460936BF0F7D42006B31FB4086664FEF07C2877DBF728 | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\bin\Digital\OEM_KMS38\$OEM$\$\Setup\Scripts\SETUPCOMPLETE.cmd | text | |
MD5:C8B1E078FA12470D7A345F7681B33C8C | SHA256:C1A38B1B906A66686CF4F58FD878F1A31203126545F0711359EC1C7095E99E15 | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\bin\Digital\bin\slc.dll | executable | |
MD5:B21C40AAF16BA46B2732618D089DB3A4 | SHA256:9395A37C42E83568DC5ECB25D9E9FCA4C6C1C4F47E336FB6CCAE62DF5C696B4D | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\bin\Digital\OEM_Digital\$OEM$\$\Setup\Scripts\SETUPCOMPLETE.cmd | text | |
MD5:90A53A1DA9510C250BA348F06B3CDC50 | SHA256:3541AF0D0A371C198A15383364B53DAAB8346D8D4F3ED25C6C9C562D83F98421 | |||
| 5360 | powershell.exe | C:\Windows\Temp\1._ | compressed | |
MD5:6F0507EB23857BD70F093ED90D4E7E4E | SHA256:899313EE19E0FC0673B8A75A22E0A53974EDBCDE8238DB4803E46DA18A46ADA3 | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\bin\Digital\OEM_KMS38\$OEM$\$\Setup\Scripts\KMS38.cmd | text | |
MD5:6E1120E07065B18307CE17E80E9BCB74 | SHA256:1742509B84915FF27C54ABFE0C7BB21DF83FC743601A318407B0360D193719BC | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\bin\Inject\KMSInject.cmd | text | |
MD5:32B7BAD1F6071B9C261F7CF1A4873BE0 | SHA256:5D7350F9546153E39F62ED8D54790220F4249150F1F4B65B543C6BBC8CB27C50 | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\bin\Inject\$OEM$\$\Setup\Scripts\run.cmd | text | |
MD5:32B7BAD1F6071B9C261F7CF1A4873BE0 | SHA256:5D7350F9546153E39F62ED8D54790220F4249150F1F4B65B543C6BBC8CB27C50 | |||
| 4980 | expand.exe | C:\Windows\Temp\KMS_Suite\KMS_Suite.cmd | text | |
MD5:3F029B53357E6A66F47FE7F21EBE0B2B | SHA256:591D576498F73504A53D8B1D16982F829CA5CC6F862FE5B17A848E15A865E6F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5392 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |