| File name: | set-up.exe |
| Full analysis: | https://app.any.run/tasks/feaee571-b5be-4ea9-9699-fbbbb5810278 |
| Verdict: | Malicious activity |
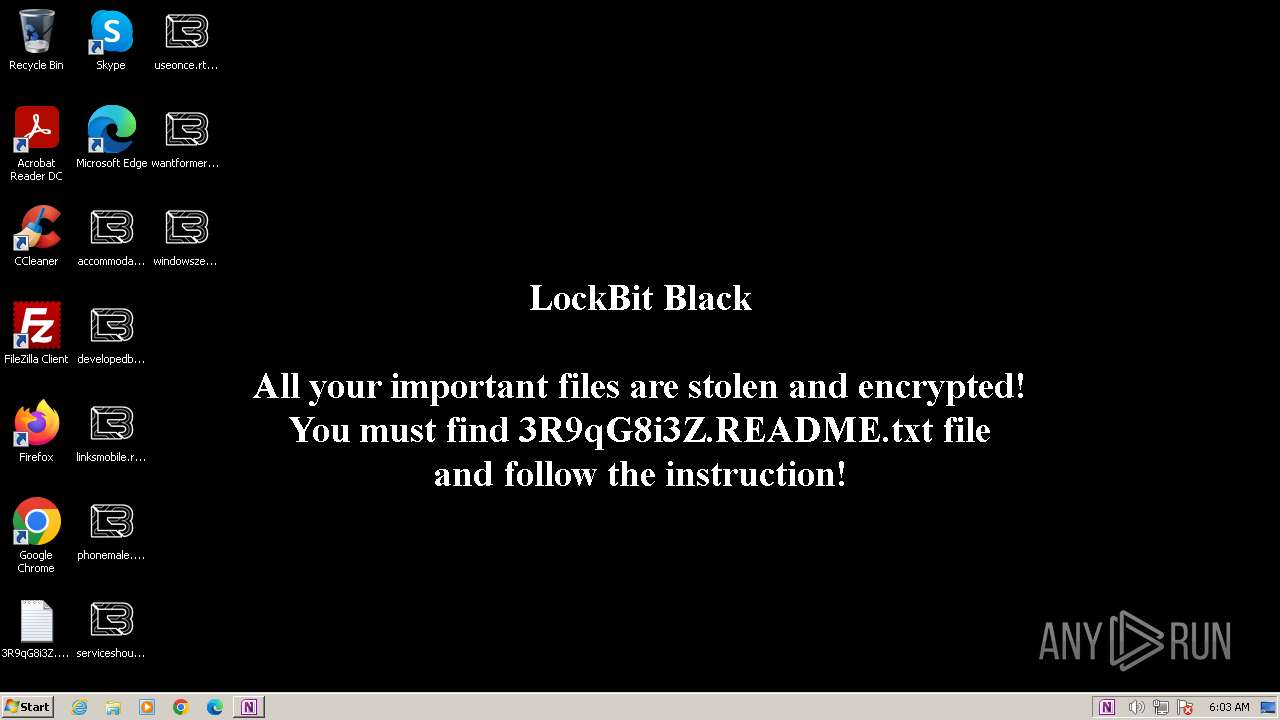
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | January 09, 2024, 06:00:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3D49478072BF18339EF810C8EA7546B2 |
| SHA1: | C1047D72D4CDCE21AF4BB989AD1BEE437EDB7F80 |
| SHA256: | E3300E30997C5A355F02CA6972711B2CA843D00A393B62C75818A43C27FF128D |
| SSDEEP: | 3072:EmhXodguLP/5qUpfDT6zT73u3WudeP7cqp1Xro:cKzO3QcO |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 2208)
Renames files like ransomware
- set-up.exe (PID: 1380)
Creates a writable file in the system directory
- printfilterpipelinesvc.exe (PID: 1600)
- set-up.exe (PID: 1380)
[YARA] LockBit is detected
- set-up.exe (PID: 1380)
Steals credentials from Web Browsers
- set-up.exe (PID: 1380)
Actions looks like stealing of personal data
- set-up.exe (PID: 1380)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- set-up.exe (PID: 1380)
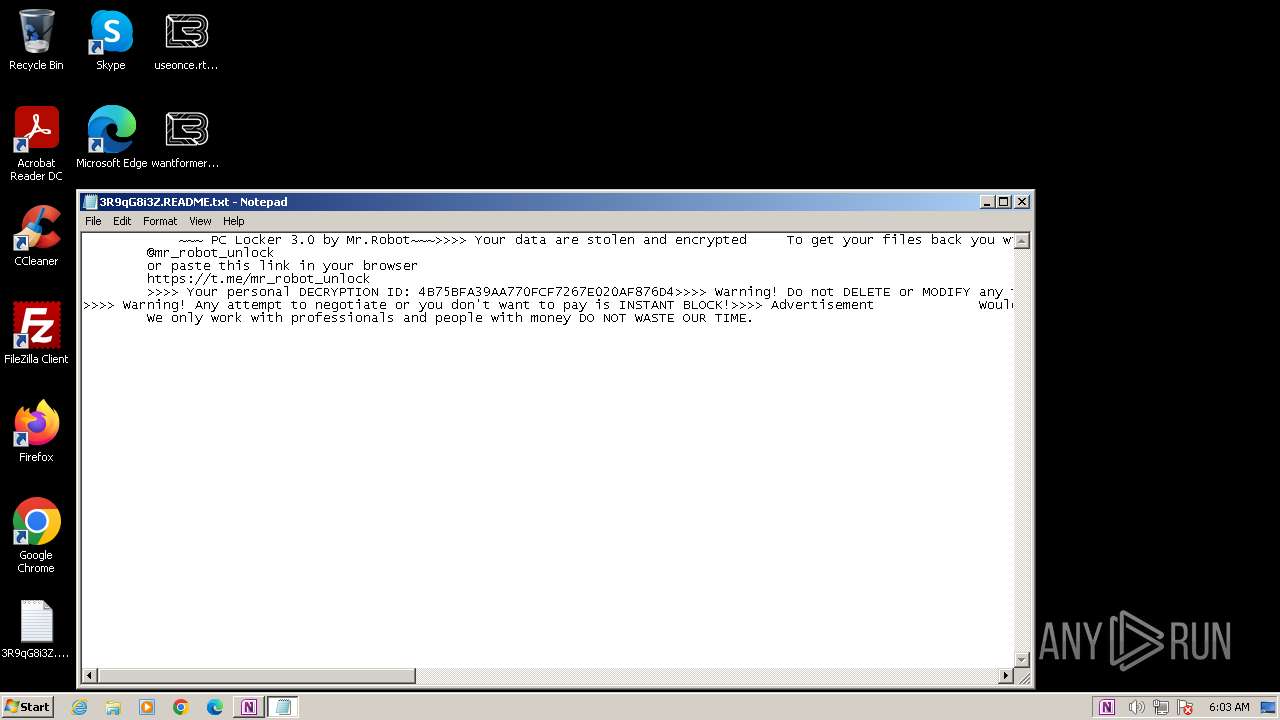
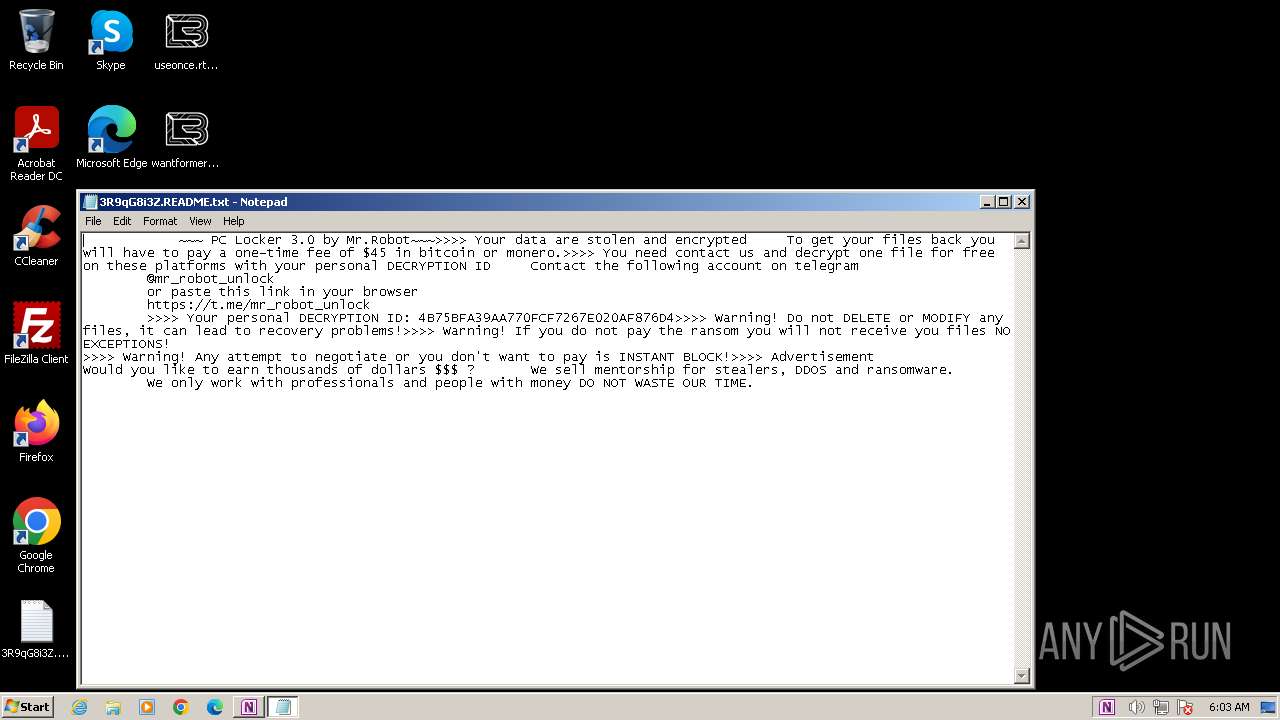
Creates files like ransomware instruction
- set-up.exe (PID: 1380)
Changes the desktop background image
- set-up.exe (PID: 1380)
Starts application with an unusual extension
- set-up.exe (PID: 1380)
Reads browser cookies
- set-up.exe (PID: 1380)
Starts CMD.EXE for commands execution
- 9477.tmp (PID: 2404)
Reads the Internet Settings
- 9477.tmp (PID: 2404)
INFO
Checks supported languages
- set-up.exe (PID: 2040)
- set-up.exe (PID: 1380)
- ONENOTE.EXE (PID: 2760)
- 9477.tmp (PID: 2404)
- ONENOTEM.EXE (PID: 2536)
Reads the computer name
- set-up.exe (PID: 2040)
- set-up.exe (PID: 1380)
- 9477.tmp (PID: 2404)
- ONENOTE.EXE (PID: 2760)
Drops the executable file immediately after the start
- set-up.exe (PID: 2040)
- set-up.exe (PID: 1380)
Checks transactions between databases Windows and Oracle
- set-up.exe (PID: 2040)
Reads the machine GUID from the registry
- set-up.exe (PID: 2040)
- set-up.exe (PID: 1380)
- ONENOTE.EXE (PID: 2760)
Creates files in the program directory
- set-up.exe (PID: 1380)
Dropped object may contain TOR URL's
- set-up.exe (PID: 1380)
Creates files or folders in the user directory
- set-up.exe (PID: 1380)
- ONENOTE.EXE (PID: 2760)
- printfilterpipelinesvc.exe (PID: 1600)
Create files in a temporary directory
- set-up.exe (PID: 1380)
- ONENOTE.EXE (PID: 2760)
Reads Environment values
- ONENOTE.EXE (PID: 2760)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 2760)
Manual execution by a user
- notepad.exe (PID: 2492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:09 03:27:01+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.12 |
| CodeSize: | 99328 |
| InitializedDataSize: | 50688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1946f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
56
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | "C:\Windows\System32\cmd.exe" /C DEL /F /Q C:\PROGRA~2\9477.tmp >> NUL | C:\Windows\System32\cmd.exe | — | 9477.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1380 | "C:\Users\admin\AppData\Local\Temp\set-up.exe" | C:\Users\admin\AppData\Local\Temp\set-up.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1600 | C:\Windows\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Exit code: 0 Version: 6.1.7601.24537 (win7sp1_ldr_escrow.191114-1547) Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\set-up.exe" | C:\Users\admin\AppData\Local\Temp\set-up.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2208 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | "C:\ProgramData\9477.tmp" | C:\ProgramData\9477.tmp | — | set-up.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2492 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\3R9qG8i3Z.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2536 | /tsr | C:\Program Files\Microsoft Office\Office14\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Quick Launcher Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 2760 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{7B338FFF-1912-43D4-883D-73CA9F42A0E8}.xps" 133492536999990000 | C:\Program Files\Microsoft Office\Office14\ONENOTE.EXE | — | printfilterpipelinesvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Exit code: 0 Version: 14.0.6022.1000 Modules
| |||||||||||||||
Total events
3 784
Read events
2 736
Write events
1 043
Delete events
5
Modification events
| (PID) Process: | (2208) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2208) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2208) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2208) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1380) set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 115 | |||
| (PID) Process: | (1380) set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Analytic |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (1380) set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Analytic |
| Operation: | write | Name: | ChannelAccess |
Value: O:BAG:SYD:(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x7;;;SO)(A;;0x3;;;IU)(A;;0x3;;;SU)(A;;0x3;;;S-1-5-3)(A;;0x3;;;S-1-5-33)(A;;0x1;;;S-1-5-32-573) | |||
| (PID) Process: | (1380) set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\DirectShowFilterGraph |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (1380) set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\DirectShowFilterGraph |
| Operation: | write | Name: | ChannelAccess |
Value: O:BAG:SYD:(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x7;;;SO)(A;;0x3;;;IU)(A;;0x3;;;SU)(A;;0x3;;;S-1-5-3)(A;;0x3;;;S-1-5-33)(A;;0x1;;;S-1-5-32-573) | |||
| (PID) Process: | (1380) set-up.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\DirectShowPluginControl |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
19
Suspicious files
1 400
Text files
958
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1380 | set-up.exe | C:\Users\Administrator\Searches\3R9qG8i3Z.README.txt | text | |
MD5:F4E7892C14B6E67ED0980A17F1262D85 | SHA256:469F1CD80F044C849534D0212ED919AC42787598438A9ABBB8D6080A940B3CAC | |||
| 1380 | set-up.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\IIIIIIIIIII | binary | |
MD5:58E9957ABF24E9E3A7C04442CDC5E270 | SHA256:83C475EC67731F663DEDF9C5776A67FE28CB740134749546B2C49F3D494BD0C8 | |||
| 1380 | set-up.exe | C:\ProgramData\3R9qG8i3Z.ico | image | |
MD5:88D9337C4C9CFE2D9AFF8A2C718EC76B | SHA256:95E059EF72686460884B9AEA5C292C22917F75D56FE737D43BE440F82034F438 | |||
| 1380 | set-up.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\KKKKKKKKKKK | binary | |
MD5:58E9957ABF24E9E3A7C04442CDC5E270 | SHA256:83C475EC67731F663DEDF9C5776A67FE28CB740134749546B2C49F3D494BD0C8 | |||
| 1380 | set-up.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\LLLLLLLLLLL | binary | |
MD5:58E9957ABF24E9E3A7C04442CDC5E270 | SHA256:83C475EC67731F663DEDF9C5776A67FE28CB740134749546B2C49F3D494BD0C8 | |||
| 1380 | set-up.exe | C:\3R9qG8i3Z.README.txt | text | |
MD5:F4E7892C14B6E67ED0980A17F1262D85 | SHA256:469F1CD80F044C849534D0212ED919AC42787598438A9ABBB8D6080A940B3CAC | |||
| 1380 | set-up.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini | binary | |
MD5:58E9957ABF24E9E3A7C04442CDC5E270 | SHA256:83C475EC67731F663DEDF9C5776A67FE28CB740134749546B2C49F3D494BD0C8 | |||
| 1380 | set-up.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\AAAAAAAAAAA | binary | |
MD5:58E9957ABF24E9E3A7C04442CDC5E270 | SHA256:83C475EC67731F663DEDF9C5776A67FE28CB740134749546B2C49F3D494BD0C8 | |||
| 1380 | set-up.exe | C:\Users\3R9qG8i3Z.README.txt | text | |
MD5:F4E7892C14B6E67ED0980A17F1262D85 | SHA256:469F1CD80F044C849534D0212ED919AC42787598438A9ABBB8D6080A940B3CAC | |||
| 1380 | set-up.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\CCCCCCCCCCC | binary | |
MD5:58E9957ABF24E9E3A7C04442CDC5E270 | SHA256:83C475EC67731F663DEDF9C5776A67FE28CB740134749546B2C49F3D494BD0C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |