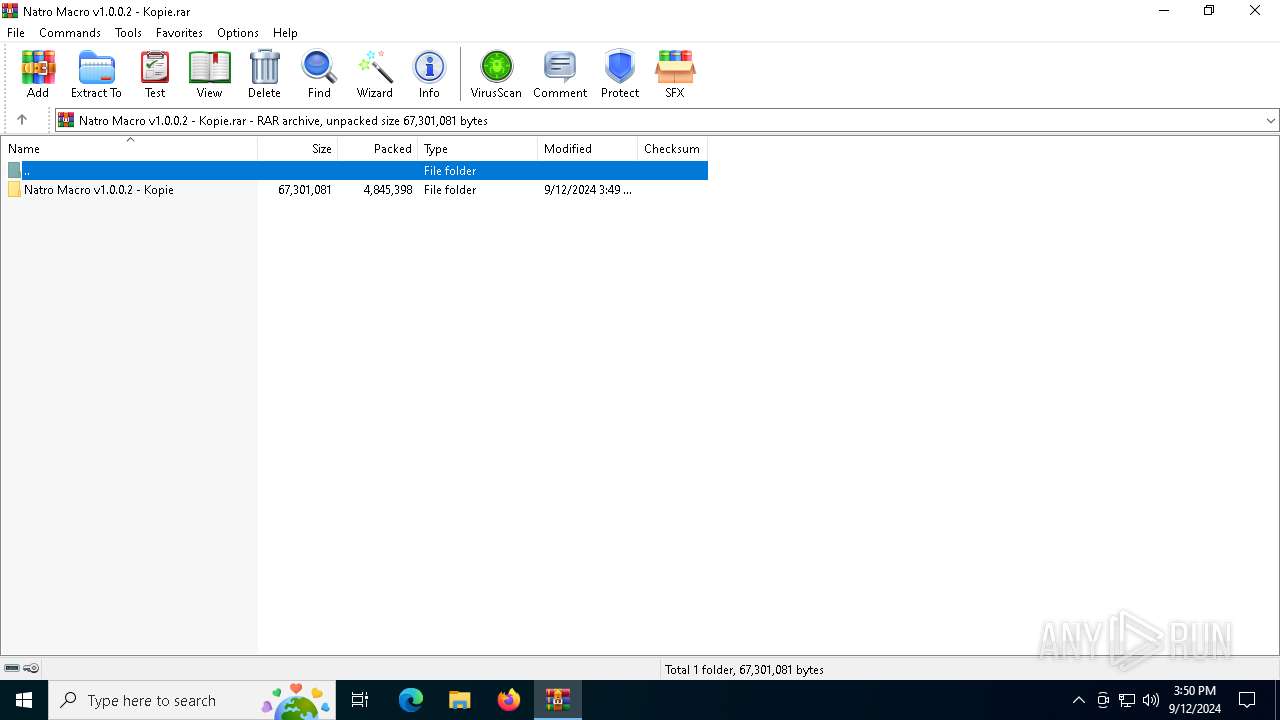
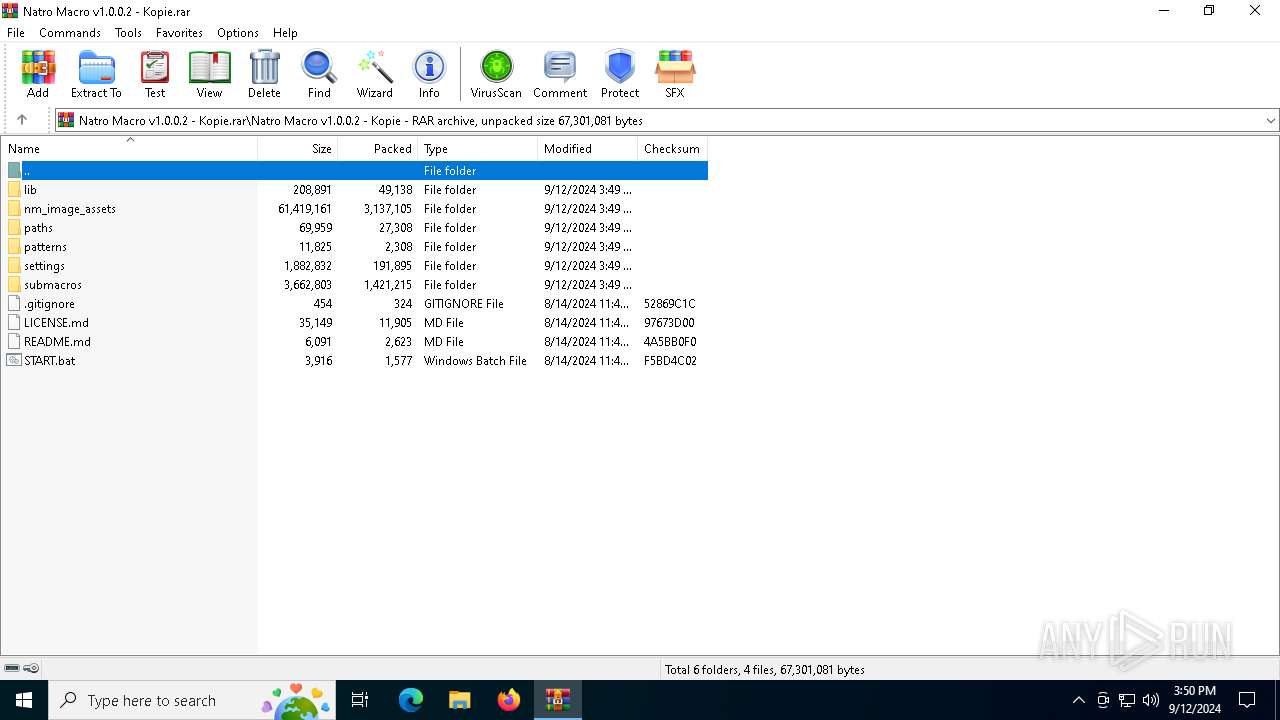
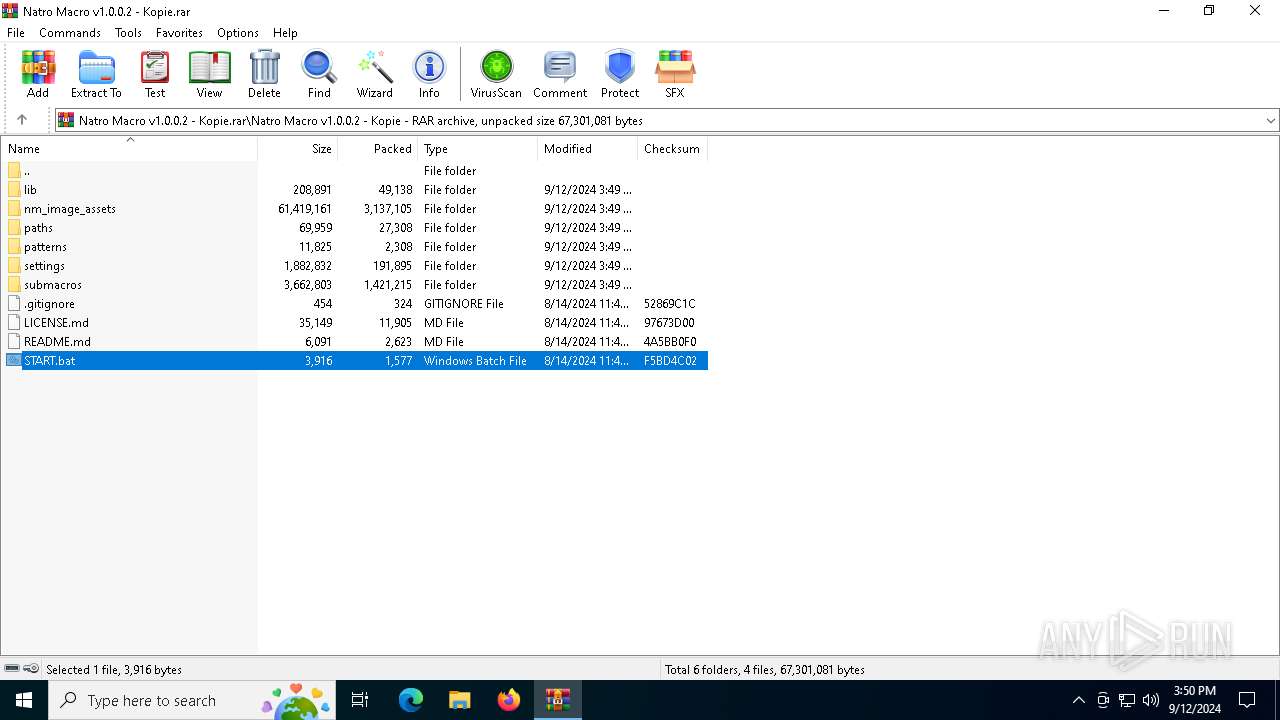
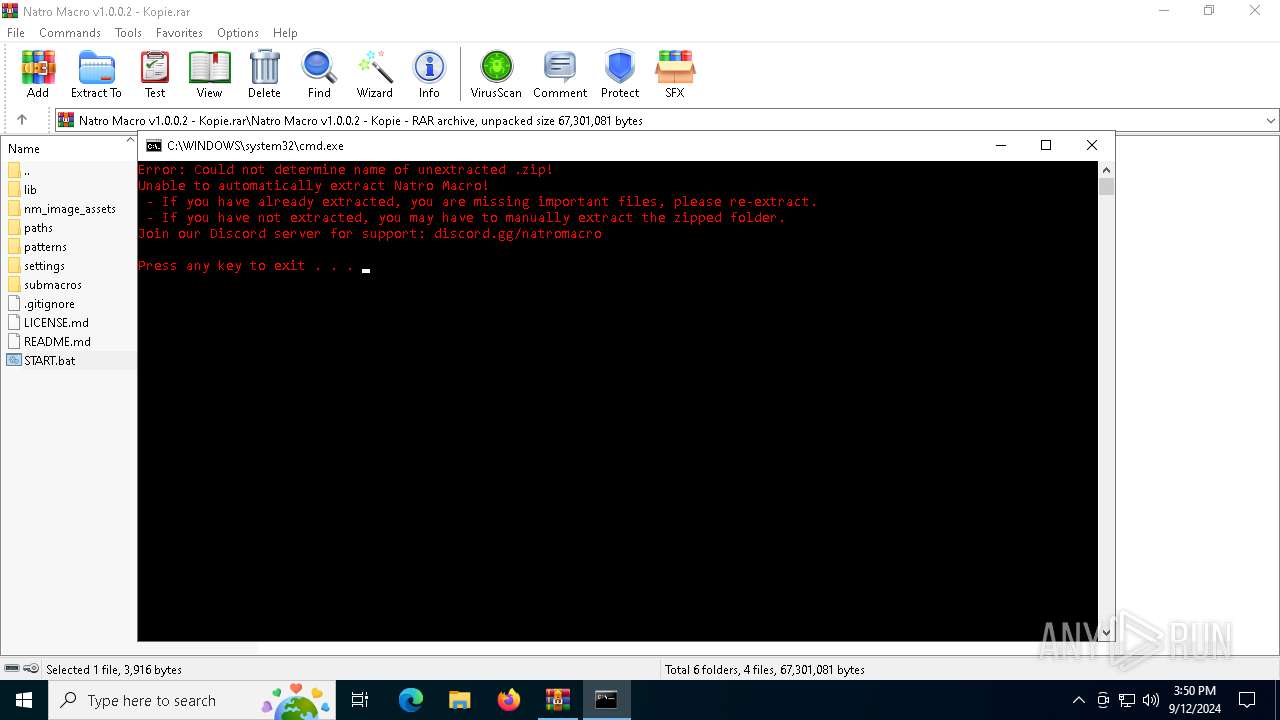
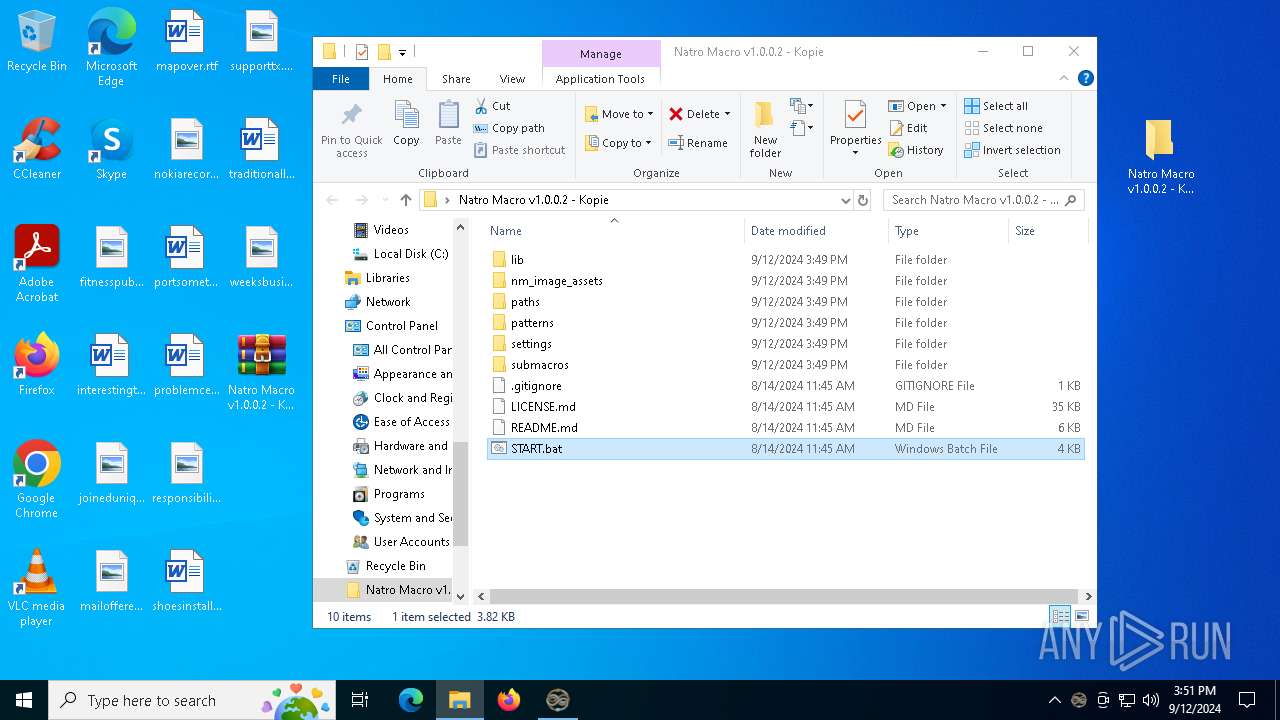
| File name: | Natro Macro v1.0.0.2 - Kopie.rar |
| Full analysis: | https://app.any.run/tasks/853843e9-81fb-4e6b-b413-79eb0bbb94be |
| Verdict: | Malicious activity |
| Analysis date: | September 12, 2024, 15:50:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 39CA5F5C0EA1D53057A12030B55BB391 |
| SHA1: | 5DCC8DD0F0FC64DBAC264244F294B3AA5C48C114 |
| SHA256: | E32A4FD0CC5401B17DEEDEBEECB15EBA6BEF849B70C01F305B5877EC9F9DD485 |
| SSDEEP: | 98304:Geznj9vv2IytR0xsweGcwsrTXs+XcxFkgomygg/KzHG/fQt1j9LIilZfLqJQbTji:jVytZ5zMpGwq |
MALICIOUS
No malicious indicators.SUSPICIOUS
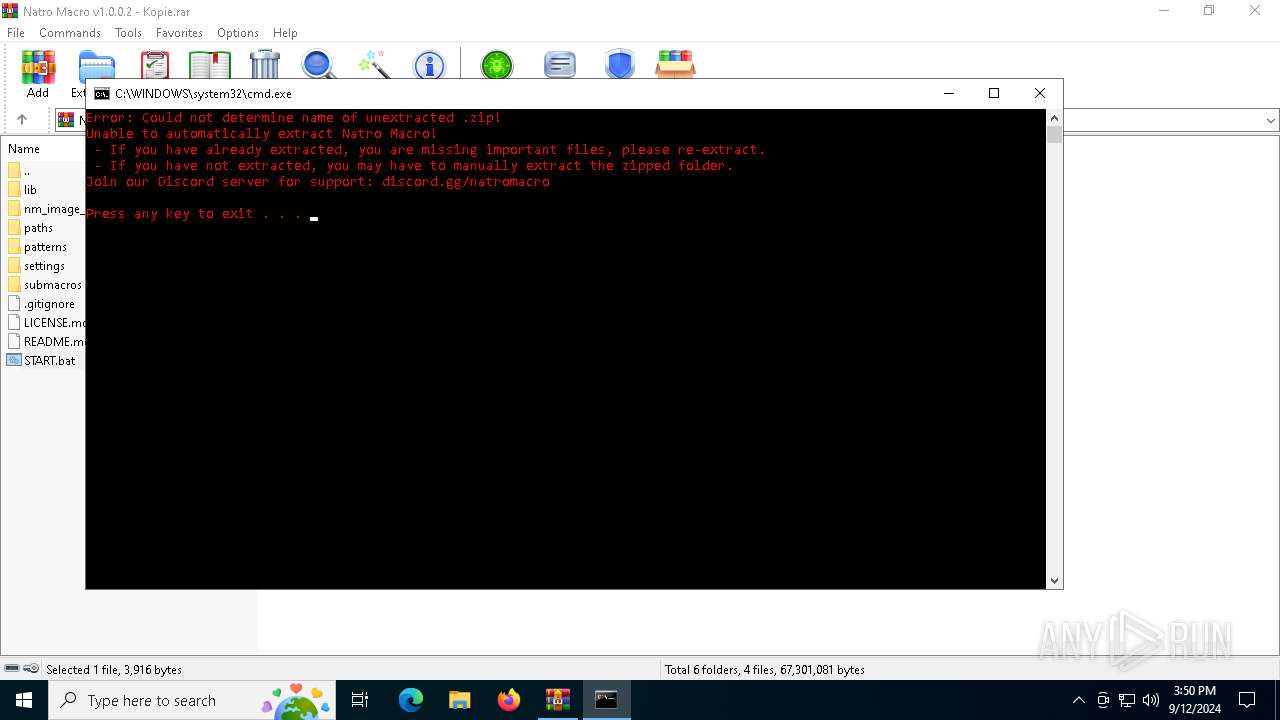
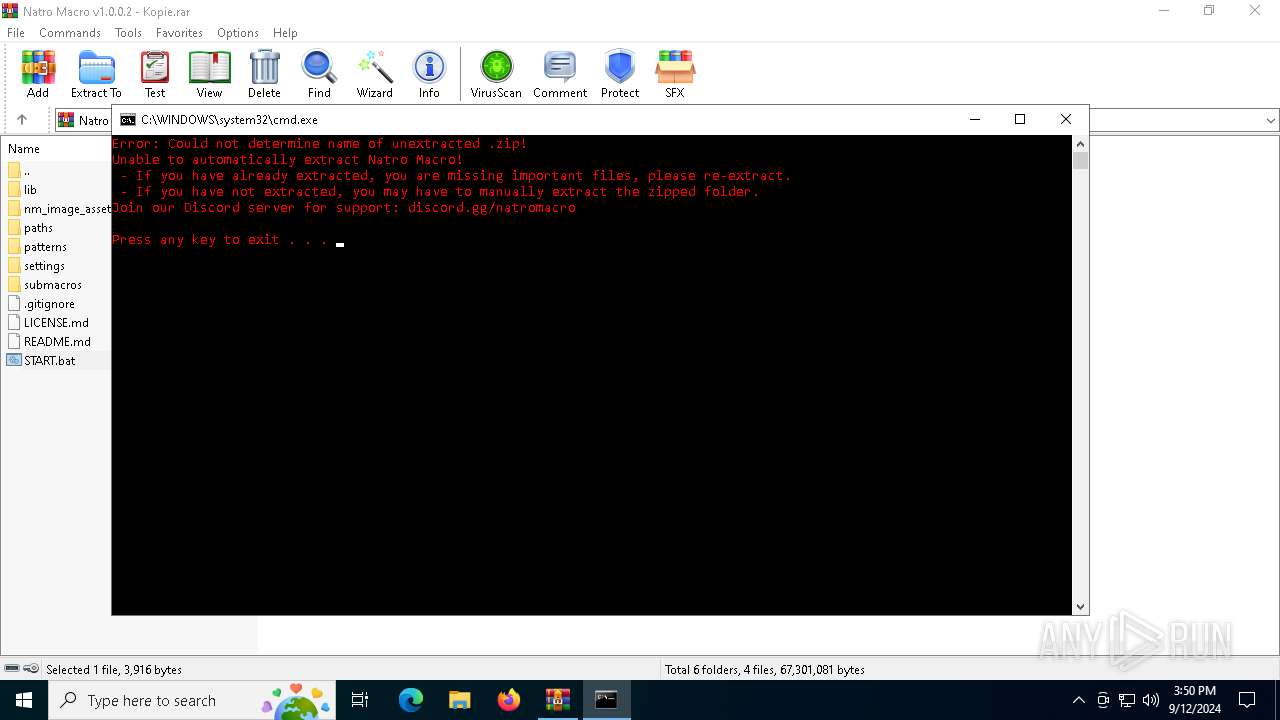
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3812)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 1124)
- cmd.exe (PID: 2056)
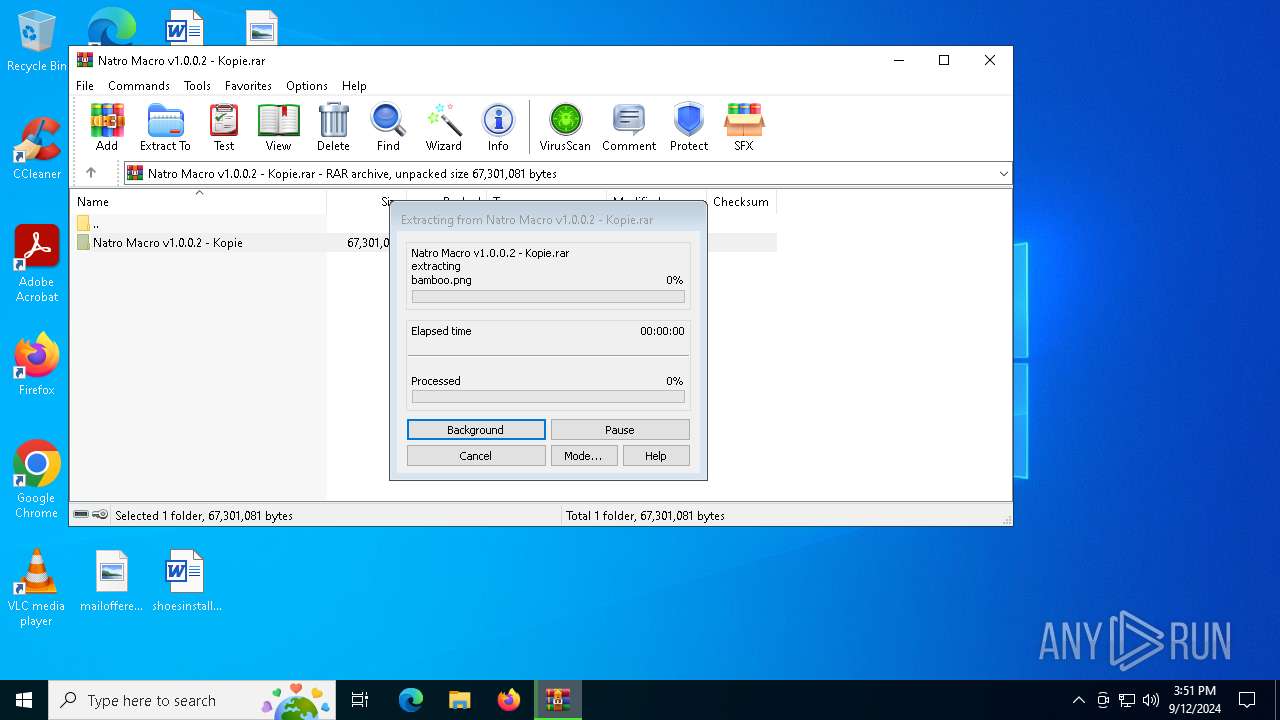
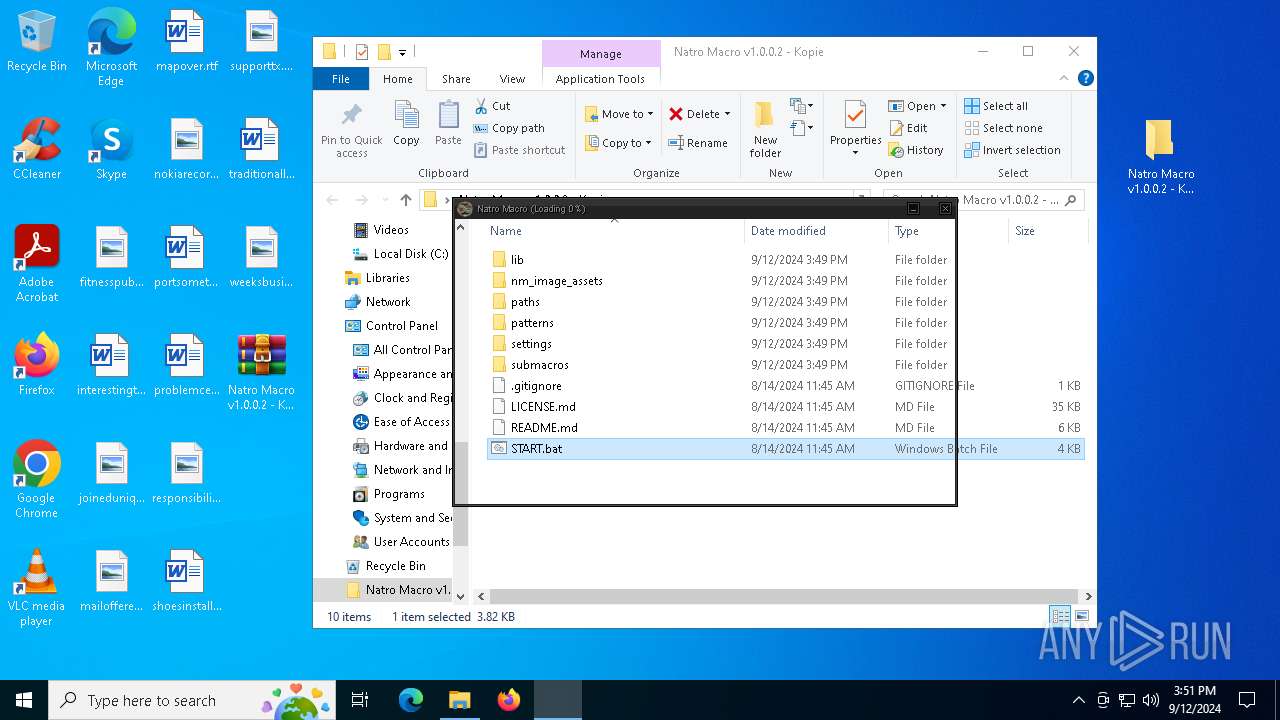
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3812)
Application launched itself
- cmd.exe (PID: 6236)
- cmd.exe (PID: 1124)
- cmd.exe (PID: 2056)
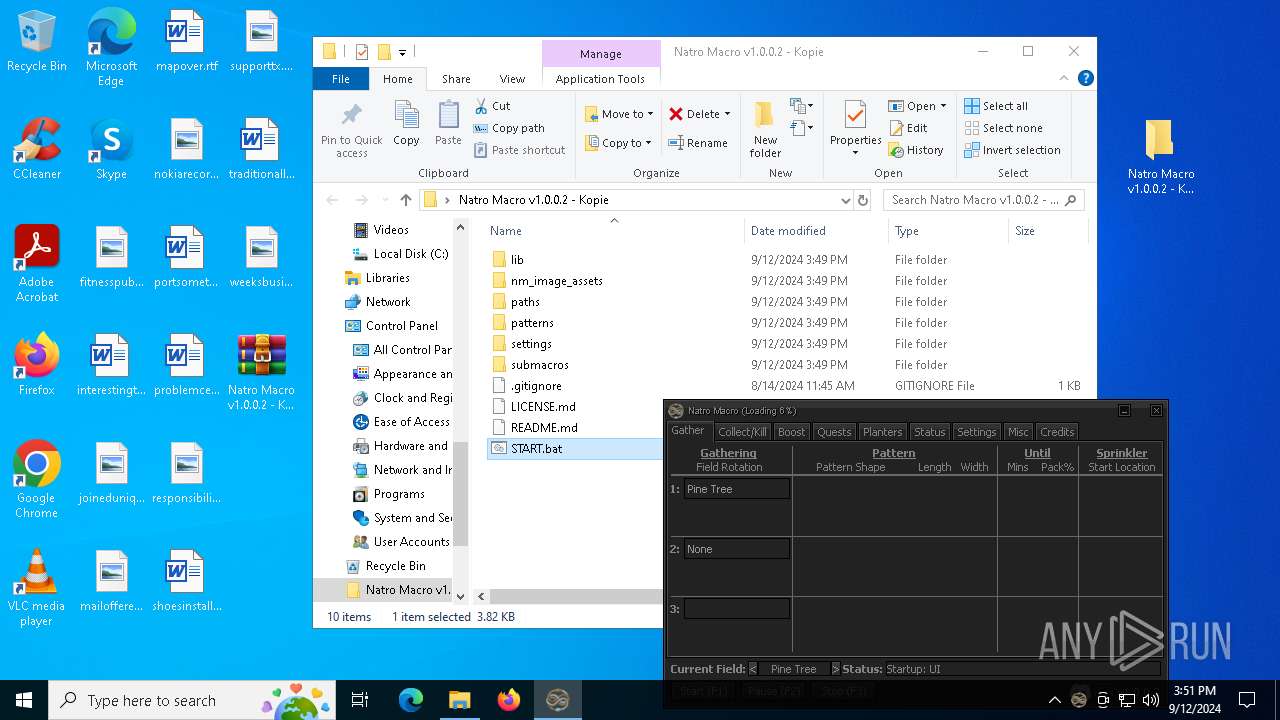
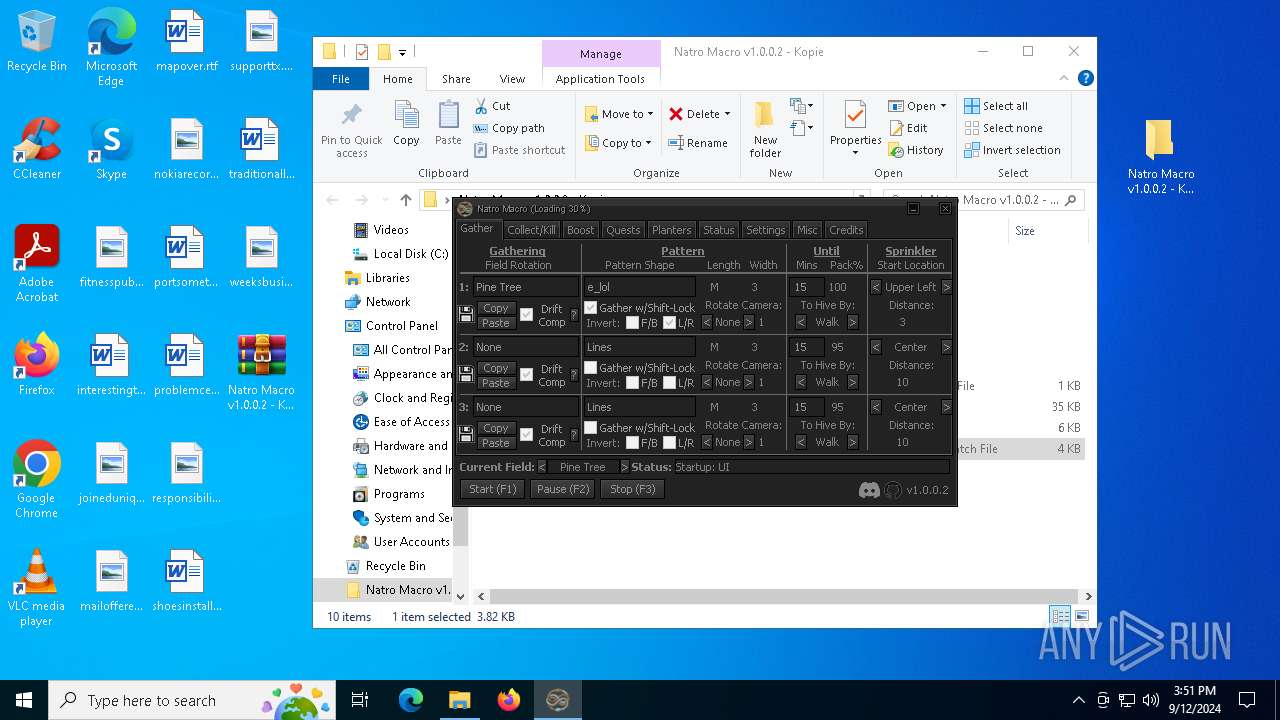
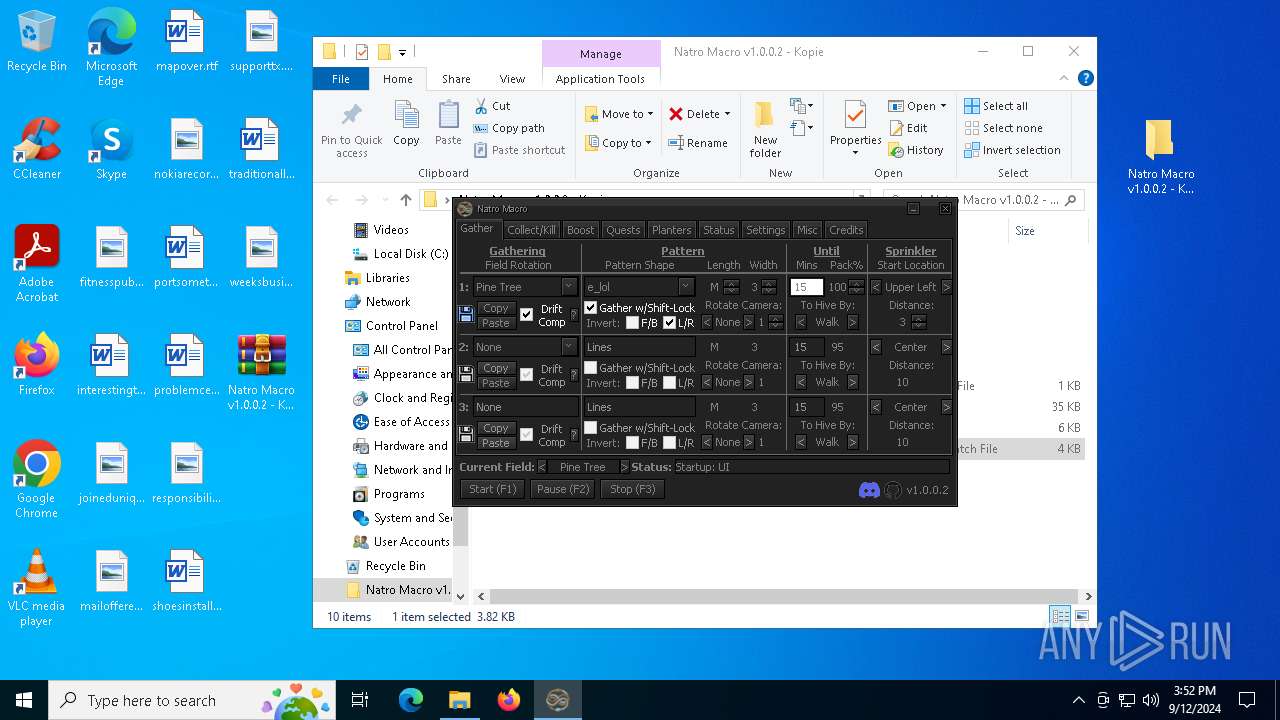
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
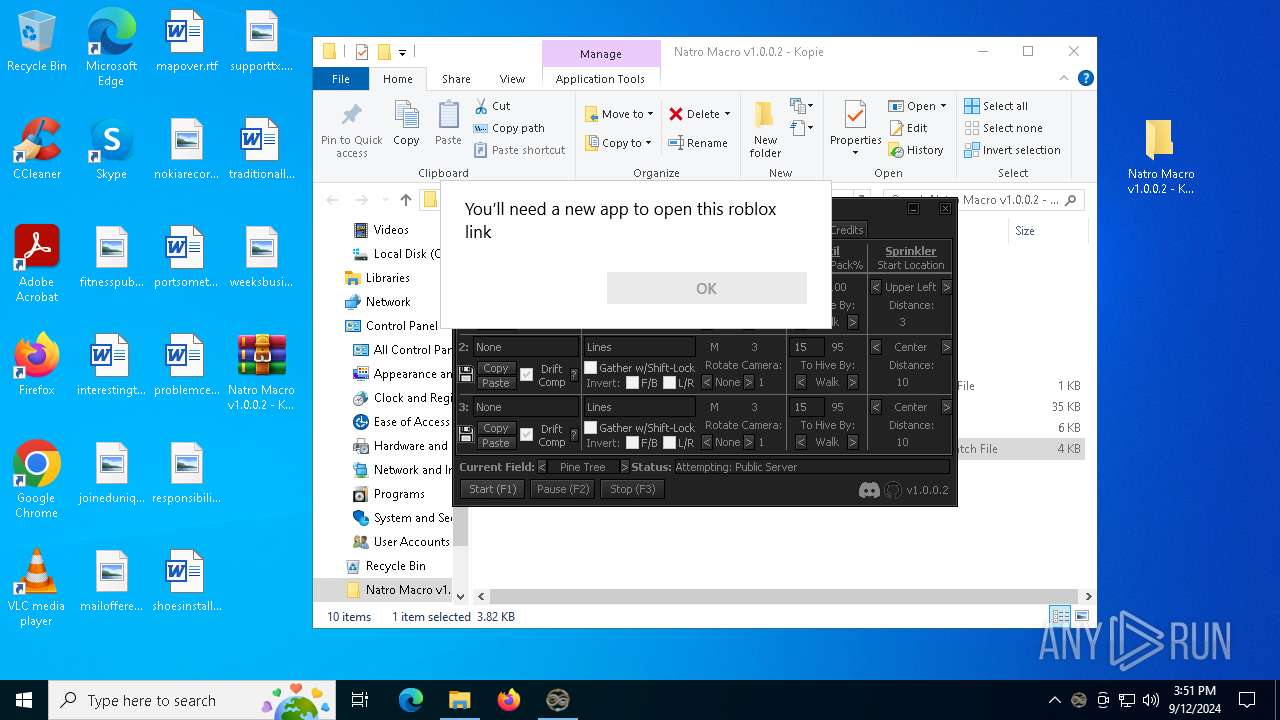
Starts application with an unusual extension
- cmd.exe (PID: 1124)
- cmd.exe (PID: 2056)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 2232)
- cmd.exe (PID: 6236)
Reads security settings of Internet Explorer
- AutoHotkey32.exe (PID: 7108)
- WinRAR.exe (PID: 3812)
- AutoHotkey32.exe (PID: 7156)
Checks Windows Trust Settings
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
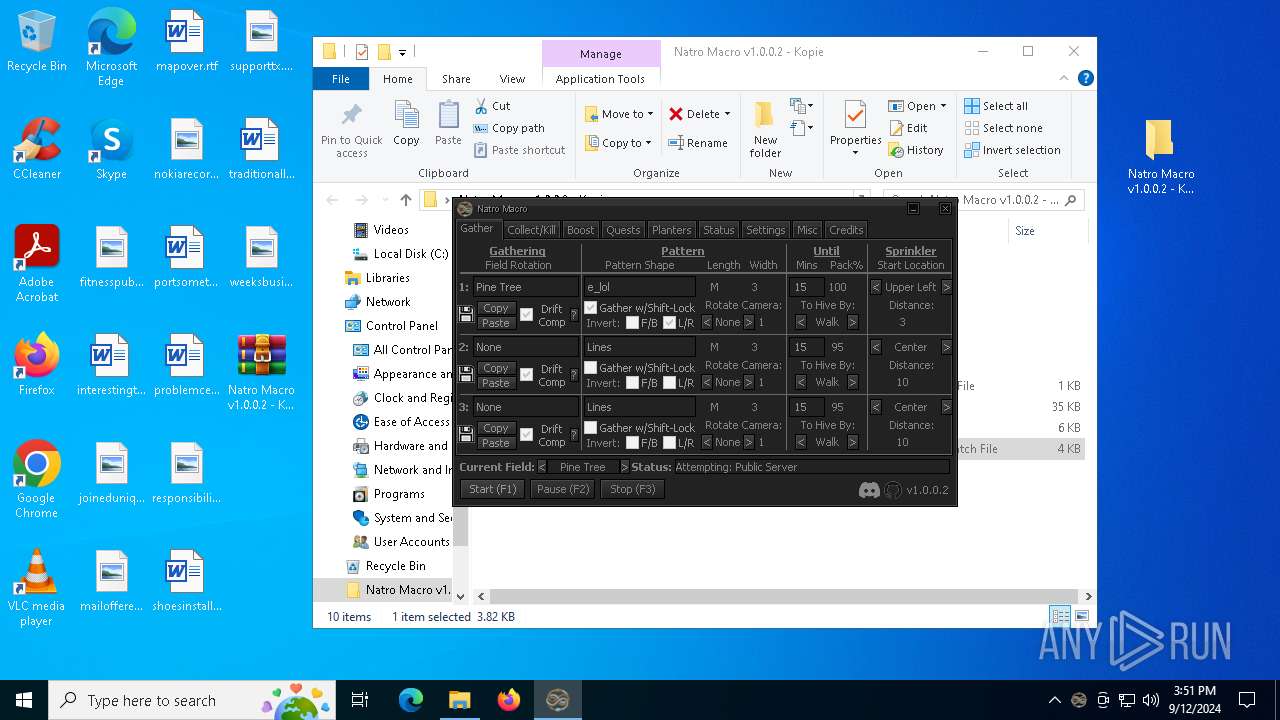
There is functionality for taking screenshot (YARA)
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 3812)
Checks supported languages
- chcp.com (PID: 1744)
- chcp.com (PID: 936)
- AutoHotkey32.exe (PID: 7108)
- chcp.com (PID: 3660)
- AutoHotkey32.exe (PID: 2724)
- AutoHotkey64.exe (PID: 5980)
- chcp.com (PID: 6244)
- AutoHotkey32.exe (PID: 7156)
- AutoHotkey32.exe (PID: 964)
- chcp.com (PID: 3180)
- AutoHotkey64.exe (PID: 6640)
Changes the display of characters in the console
- cmd.exe (PID: 1124)
- cmd.exe (PID: 2056)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 2232)
- cmd.exe (PID: 6236)
Manual execution by a user
- cmd.exe (PID: 2524)
- cmd.exe (PID: 2232)
Create files in a temporary directory
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
Reads the software policy settings
- AutoHotkey64.exe (PID: 5980)
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey64.exe (PID: 6640)
- AutoHotkey32.exe (PID: 7156)
Reads the machine GUID from the registry
- AutoHotkey64.exe (PID: 5980)
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
- AutoHotkey64.exe (PID: 6640)
Reads the computer name
- AutoHotkey64.exe (PID: 5980)
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
- AutoHotkey64.exe (PID: 6640)
Checks proxy server information
- AutoHotkey32.exe (PID: 7108)
- AutoHotkey32.exe (PID: 7156)
Attempting to use instant messaging service
- AutoHotkey64.exe (PID: 5980)
- AutoHotkey64.exe (PID: 6640)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 1640)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
147
Monitored processes
27
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | C:\WINDOWS\system32\cmd.exe /c "prompt #$E# & for %E in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | "C:\Users\admin\Desktop\Natro Macro v1.0.0.2 - Kopie\submacros\AutoHotkey32.exe" /script "C:\Users\admin\Desktop\Natro Macro v1.0.0.2 - Kopie\submacros\Heartbeat.ahk" | C:\Users\admin\Desktop\Natro Macro v1.0.0.2 - Kopie\submacros\AutoHotkey32.exe | — | AutoHotkey32.exe | |||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey 32-bit Version: 2.0.12 Modules
| |||||||||||||||
| 1124 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3812.5492\START.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3812.6393\START.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2232 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Natro Macro v1.0.0.2 - Kopie\START.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | C:\WINDOWS\system32\cmd.exe /c "prompt #$E# & for %E in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 048
Read events
16 022
Write events
26
Delete events
0
Modification events
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Natro Macro v1.0.0.2 - Kopie.rar | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
30
Suspicious files
0
Text files
444
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\Gdip_All.ahk | text | |
MD5:BDF3099831BFF1F4D7D57E0AEBE4AFE3 | SHA256:72DCC0FC9BADA8E76E8D2F4868F6B23F7A42DB3B675A7A490360AB2D96B30FFF | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\nm_InventorySearch.ahk | text | |
MD5:06EFD1811EE317D4C1595B6A6CB83451 | SHA256:469CCAE055CC92CA4B04989554AEF43CFEDD8E3B3CA0F89D8DCF0AFB3BD6C9C6 | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\Gdip_ImageSearch.ahk | text | |
MD5:8FFAFCFD0FB2247C45A6597A69C20432 | SHA256:25BD9B4B006A80E43DF94C30EED25DF33F3E27C1380280CEDD9559C8F00FAF70 | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\enum\EnumStr.ahk | text | |
MD5:178B6DB95EF550A82E9B441BB91AF76A | SHA256:E9F850288C5E3B0205C1E033D7C1D2B0EBC68D5C4D9DCFFCCD15C0ACF14AD1D9 | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\nm_OpenMenu.ahk | text | |
MD5:923D753BCC8F129B832CB9FB3C06E30E | SHA256:1285097ABDE439F5D37A48628480752D6D860F19F48AC3E78EB76CD27E9DD3DD | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3812.4273\START.bat | html | |
MD5:A58311373246197CE552CEBA70AD8B5C | SHA256:C48CD7DDF41DD81FAE4DB362C5C631EDB582F03FB170B1A858FA655D6CCADCE8 | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\Roblox.ahk | text | |
MD5:0A37E9909366C078D20B0105214FE743 | SHA256:9CECC5B3127D14B55E5CEDAE5DDAAA9EA516B322297210B931BD0C28582644C3 | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\HyperSleep.ahk | text | |
MD5:312B0170D0A84C7B88ACB6D4B6B66D93 | SHA256:D8F20B8B223BEF194B435F0F0875761CAC3B74F39433EB9D9FF7260996F06D8D | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\Walk.ahk | text | |
MD5:0174F8DC8ECCBF5492FB095E65F4E2F3 | SHA256:06FDE1BF7A0FC3350390A62802689D54DF658033CE3E143A183F934804A67F86 | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.7437\Natro Macro v1.0.0.2 - Kopie\lib\JSON.ahk | text | |
MD5:5D0F46B85B9851A4F2C0715001AEBE21 | SHA256:D1D9E2D5C8E492258461CA31F40199B2457DA2404C28FAED588BF3B76CE7EB80 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
32
DNS requests
7
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6856 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6856 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5980 | AutoHotkey64.exe | 162.159.128.233:443 | discord.com | CLOUDFLARENET | — | whitelisted |
7108 | AutoHotkey32.exe | 140.82.121.6:443 | api.github.com | GITHUB | US | whitelisted |
7108 | AutoHotkey32.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
discord.com |
| whitelisted |
api.github.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5980 | AutoHotkey64.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5980 | AutoHotkey64.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5980 | AutoHotkey64.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5980 | AutoHotkey64.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6640 | AutoHotkey64.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6640 | AutoHotkey64.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |