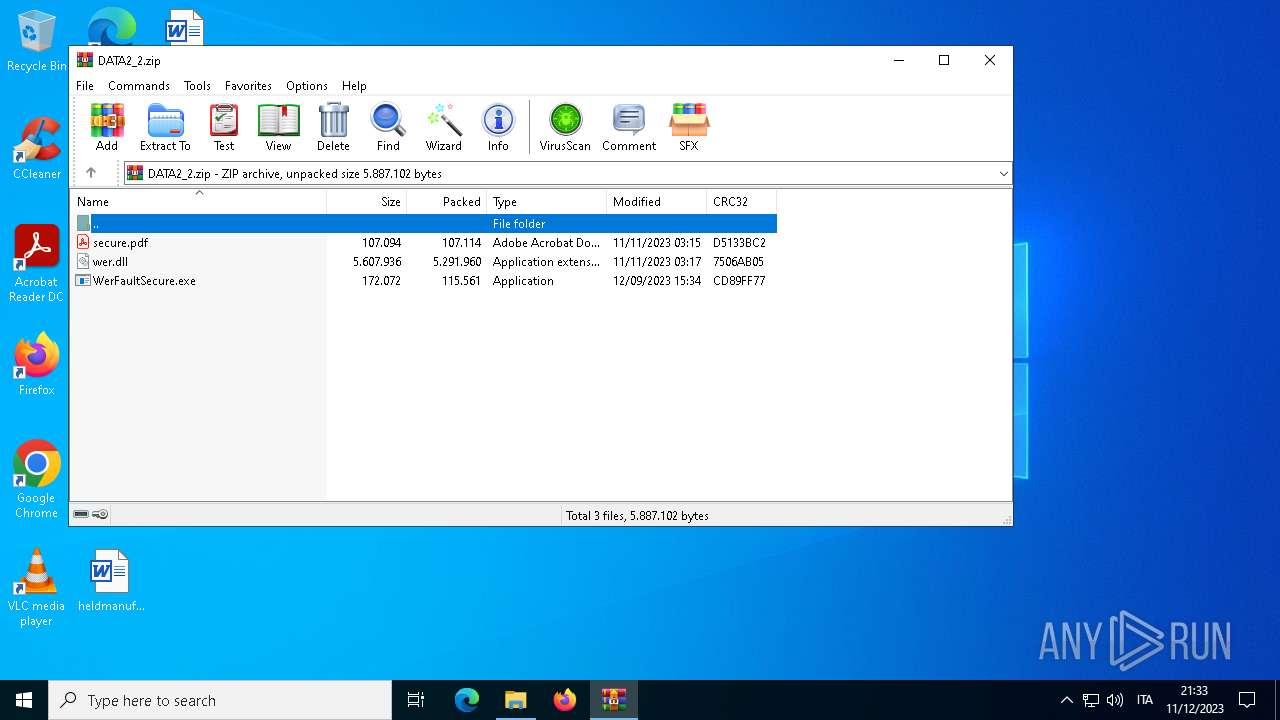
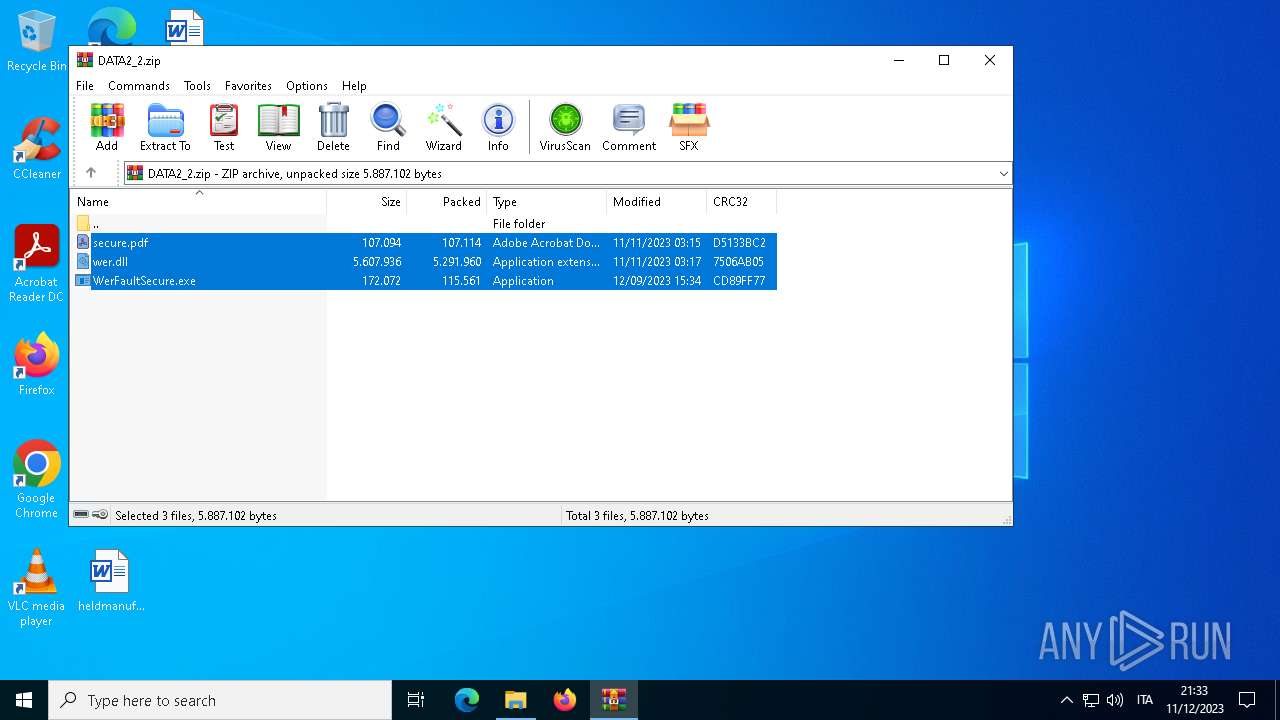
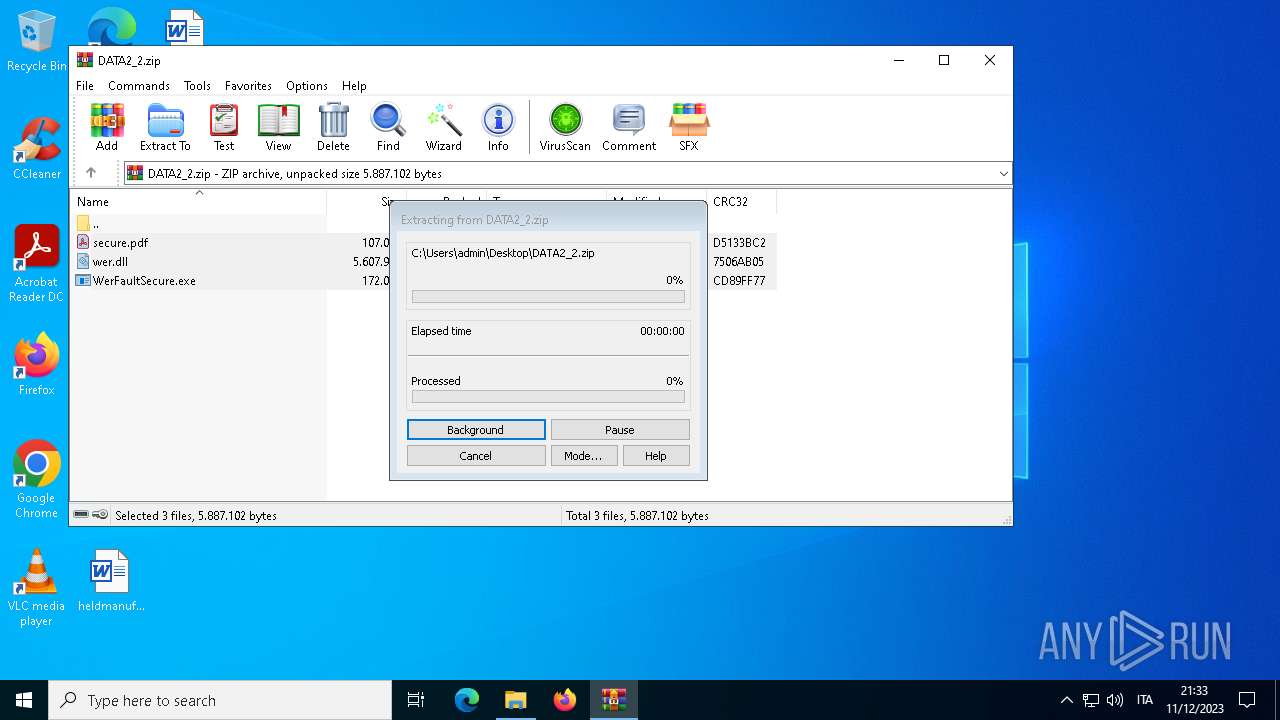
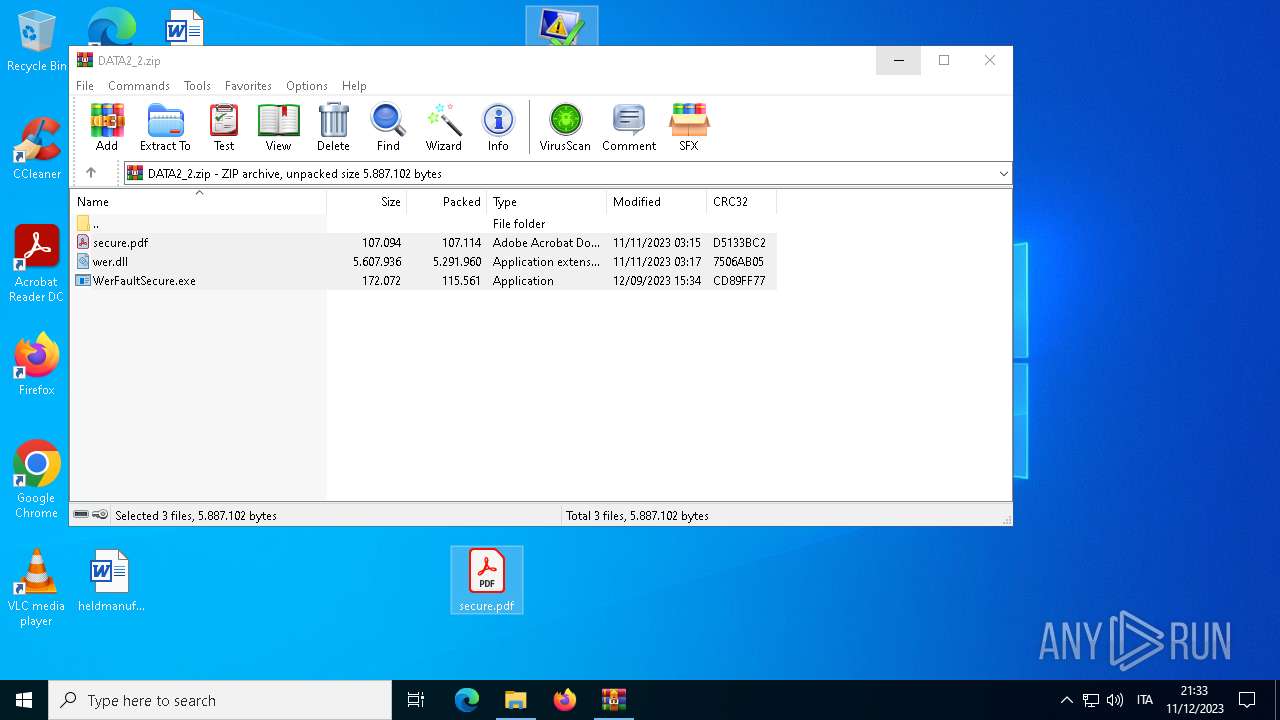
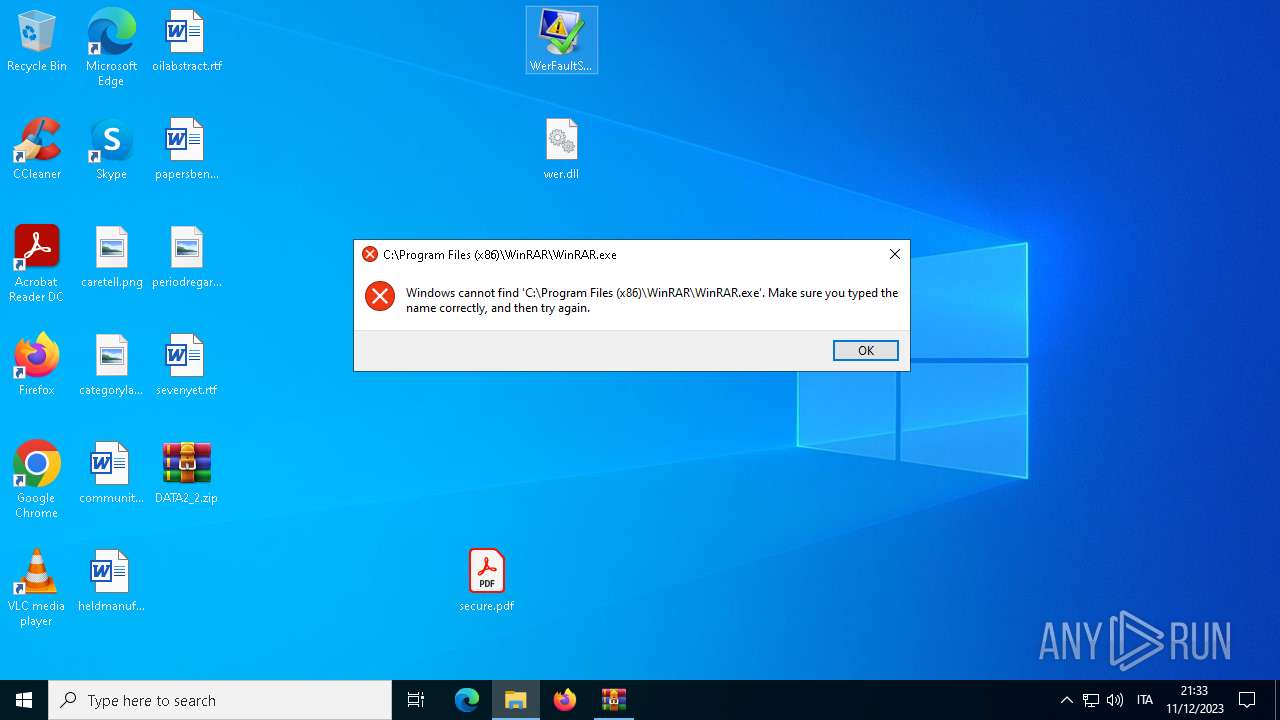
| File name: | DATA2_2.zip |
| Full analysis: | https://app.any.run/tasks/51a53014-c284-45ed-833b-be0cd453a51c |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2023, 20:33:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8904D6AD569095EF6FB1DAB561EDC420 |
| SHA1: | AA81AD9C00F6A60A0E09A3DB8C2E69092A49C863 |
| SHA256: | E326C1B9E61CCA6823300158E55381C6951B09D2327A89A8D841539CAD3B4DF3 |
| SSDEEP: | 98304:ph8q5GzZCtFD1jqf1TXDtByJZwq64OjIRgir5Qg7PHiYoFrc7qVTZUU9o7o4dam+:ZngASIRfFm3W8z6M |
MALICIOUS
Drops the executable file immediately after the start
- WerFaultSecure.exe (PID: 6520)
Steals credentials from Web Browsers
- WerFaultSecure.exe (PID: 6520)
The DLL Hijacking
- WerFaultSecure.exe (PID: 6520)
Uses Task Scheduler to run other applications
- WerFaultSecure.exe (PID: 6520)
Actions looks like stealing of personal data
- WerFaultSecure.exe (PID: 6520)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6700)
- WerFaultSecure.exe (PID: 6520)
Executes application which crashes
- WerFaultSecure.exe (PID: 6520)
Checks for external IP
- WerFaultSecure.exe (PID: 6520)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- WerFaultSecure.exe (PID: 6520)
The process checks if it is being run in the virtual environment
- WerFaultSecure.exe (PID: 6520)
INFO
Manual execution by a user
- WerFaultSecure.exe (PID: 6520)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6700)
Checks proxy server information
- WerFaultSecure.exe (PID: 6520)
Reads the computer name
- WerFaultSecure.exe (PID: 6520)
Reads Environment values
- WerFaultSecure.exe (PID: 6520)
Reads the machine GUID from the registry
- WerFaultSecure.exe (PID: 6520)
Checks supported languages
- WerFaultSecure.exe (PID: 6520)
Reads the software policy settings
- WerFaultSecure.exe (PID: 6520)
Reads product name
- WerFaultSecure.exe (PID: 6520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:11 05:17:36 |
| ZipCRC: | 0x7506ab05 |
| ZipCompressedSize: | 5291960 |
| ZipUncompressedSize: | 5607936 |
| ZipFileName: | wer.dll |
Total processes
143
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1932 | C:\WINDOWS\system32\WerFault.exe -u -p 6520 -s 1000 | C:\Windows\System32\WerFault.exe | — | WerFaultSecure.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2832 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 3752 | /F /CREATE /TN "Licensing2" /tr "C:\Users\Public\Libraries\Books\WerFaultSecure.exe" /sc minute /MO 90 | C:\Windows\System32\schtasks.exe | — | WerFaultSecure.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4956 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6520 | "C:\Users\admin\Desktop\WerFaultSecure.exe" | C:\Users\admin\Desktop\WerFaultSecure.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Fault Reporting Exit code: 3221225501 Version: 10.0.19041.1682 (WinBuild.160101.0800) Modules
| |||||||||||||||
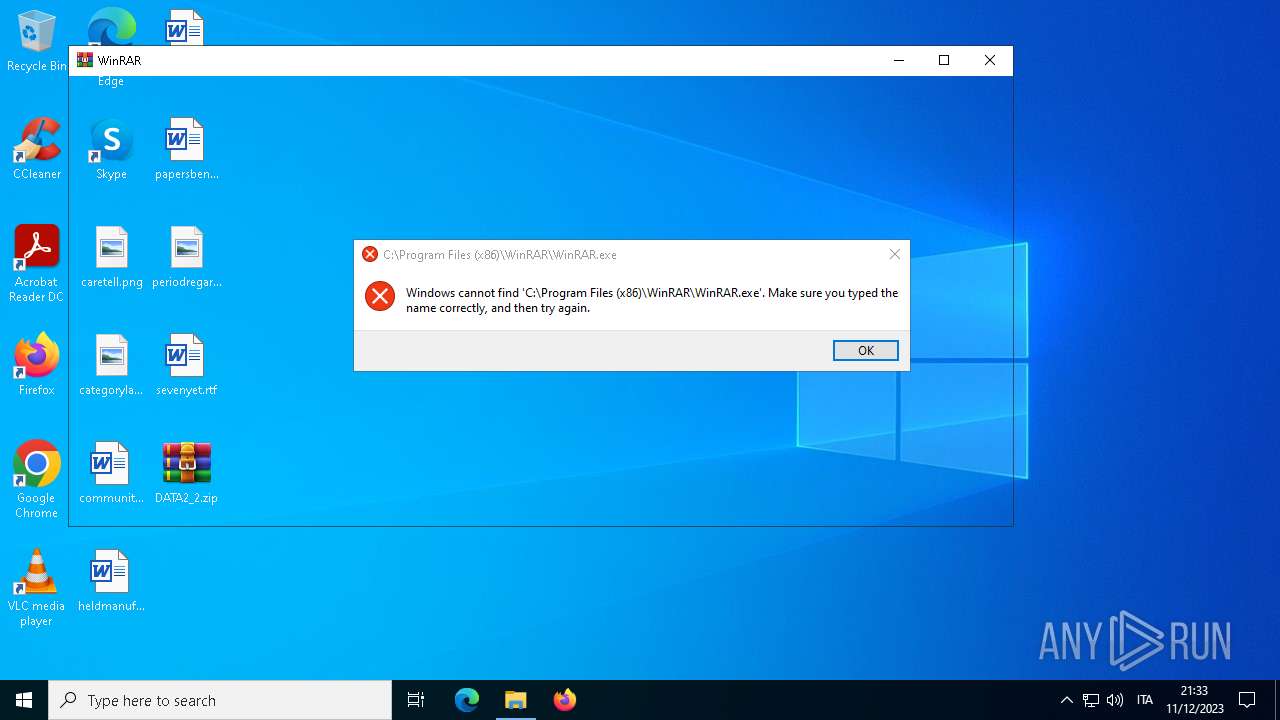
| 6700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\DATA2_2.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 819
Read events
3 811
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 003C050012F8FE6A437AD701 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\SpybotAntiBeaconPortable-safer-networking.org_3.7.0.paf.zip | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.cab | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.zip | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6520 | WerFaultSecure.exe | C:\Users\Public\Libraries\Books\secure.pdf | binary | |
MD5:5C2DC3E1AF236CAFC798C517414BE70D | SHA256:5ECAD303475E180F8879871D8571D1A7EEB99E0B3C63CC77FDD02CB9B8C51211 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.29106\wer.dll | executable | |
MD5:C90B04B9184F91575D4F12320B4A65AB | SHA256:568B4B868B225F06BB34DA0DC23603C9DEDCCC2B319353407C814983D5322563 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Roaming\WinRAR\version.dat | binary | |
MD5:2830CE76B311C17E25599ADD2DFEFFF5 | SHA256:D5BFDBB62B33DEA5D14001BEE1FFA8726DFAF7D48EC6C79E313587EDC492B137 | |||
| 6520 | WerFaultSecure.exe | C:\Users\Public\Libraries\Books\wer.dll | executable | |
MD5:C90B04B9184F91575D4F12320B4A65AB | SHA256:568B4B868B225F06BB34DA0DC23603C9DEDCCC2B319353407C814983D5322563 | |||
| 2832 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2023-12-11.2040.2832.1.odl | binary | |
MD5:2DF22C38812436D887D1EB2722E114BE | SHA256:2AE44B5C40F071AA0D8CB6B87B3DDA4FD9AF97F7AE7CC028EE16A7BF9AADA306 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.29106\WerFaultSecure.exe | executable | |
MD5:C86F71DAFB6589DC711DD2BC27373F5A | SHA256:5F1A027F1C1468F93671A4C7FC7B5DA00A3C559A9116F5417BAA6C1F89550D9F | |||
| 6520 | WerFaultSecure.exe | C:\Users\Public\Libraries\Books\WerFaultSecure.exe | executable | |
MD5:C86F71DAFB6589DC711DD2BC27373F5A | SHA256:5F1A027F1C1468F93671A4C7FC7B5DA00A3C559A9116F5417BAA6C1F89550D9F | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.29106\secure.pdf | binary | |
MD5:5C2DC3E1AF236CAFC798C517414BE70D | SHA256:5ECAD303475E180F8879871D8571D1A7EEB99E0B3C63CC77FDD02CB9B8C51211 | |||
| 2832 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2023-12-11.2040.2832.1.aodl | binary | |
MD5:923BF0E545D9C37CA8874C8D6C4A30E6 | SHA256:AB32C675D35DDBEBFCF8B11720C3E550024E8D0DF557838F17186377E3D0FE65 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
105
DNS requests
33
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2844 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
5980 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
6520 | WerFaultSecure.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=11827 | unknown | binary | 190 b | unknown |
1540 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
1540 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
2344 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | binary | 1.05 Kb | unknown |
2344 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicWinPCA_2010-07-06.crl | unknown | binary | 552 b | unknown |
2344 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
2152 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
928 | svchost.exe | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3764 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2844 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5980 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
5980 | backgroundTaskHost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6520 | WerFaultSecure.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2844 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6520 | WerFaultSecure.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ip-api.com |
| shared |
api.telegram.org |
| shared |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6520 | WerFaultSecure.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
6520 | WerFaultSecure.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2092 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6520 | WerFaultSecure.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6520 | WerFaultSecure.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
6520 | WerFaultSecure.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |