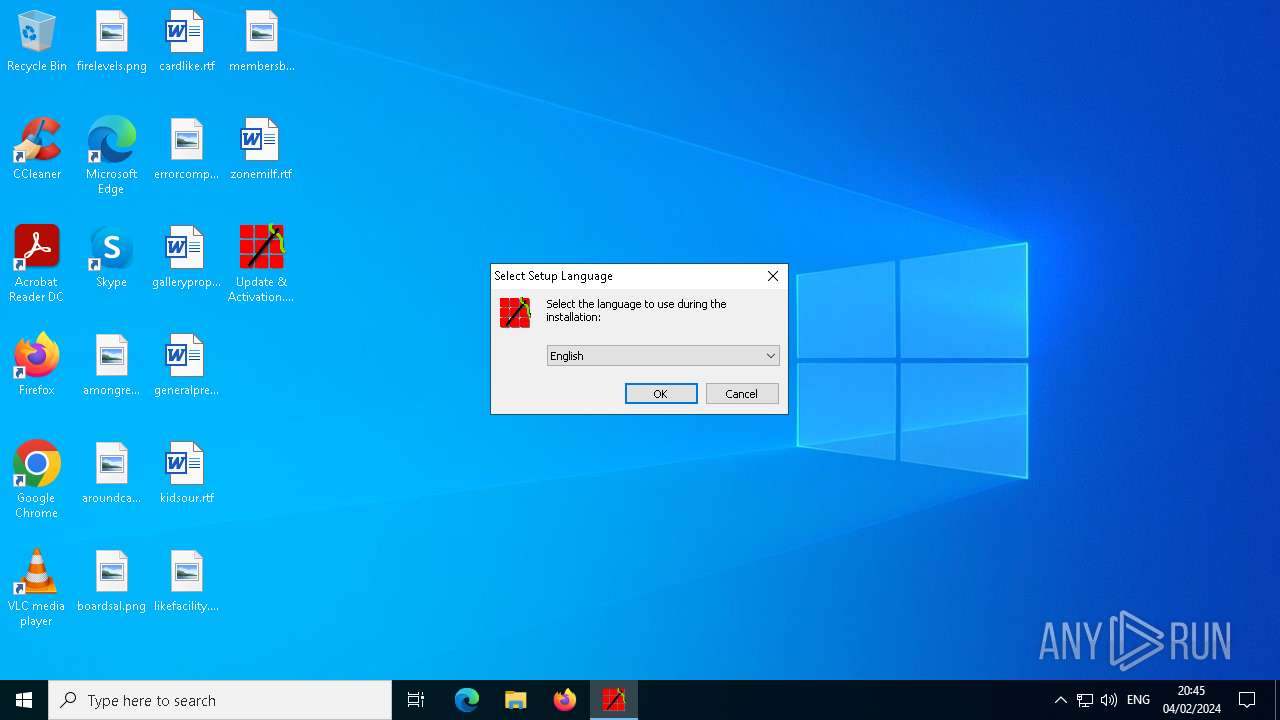
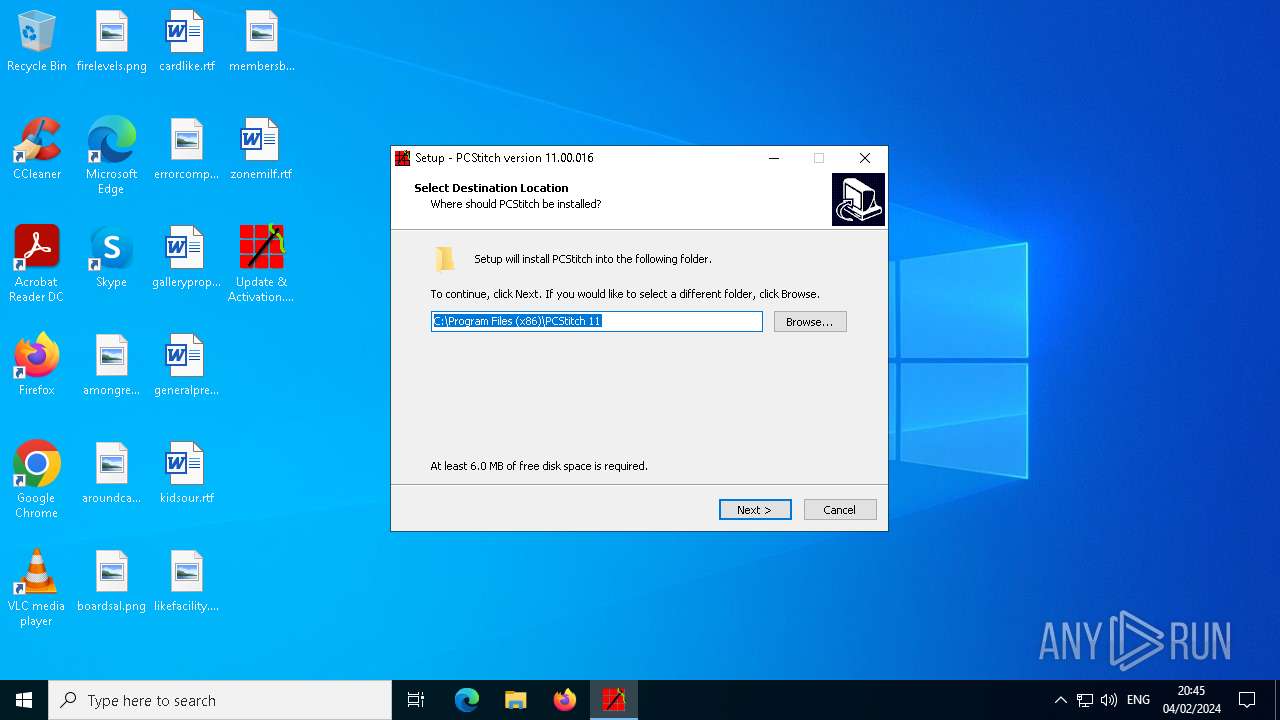
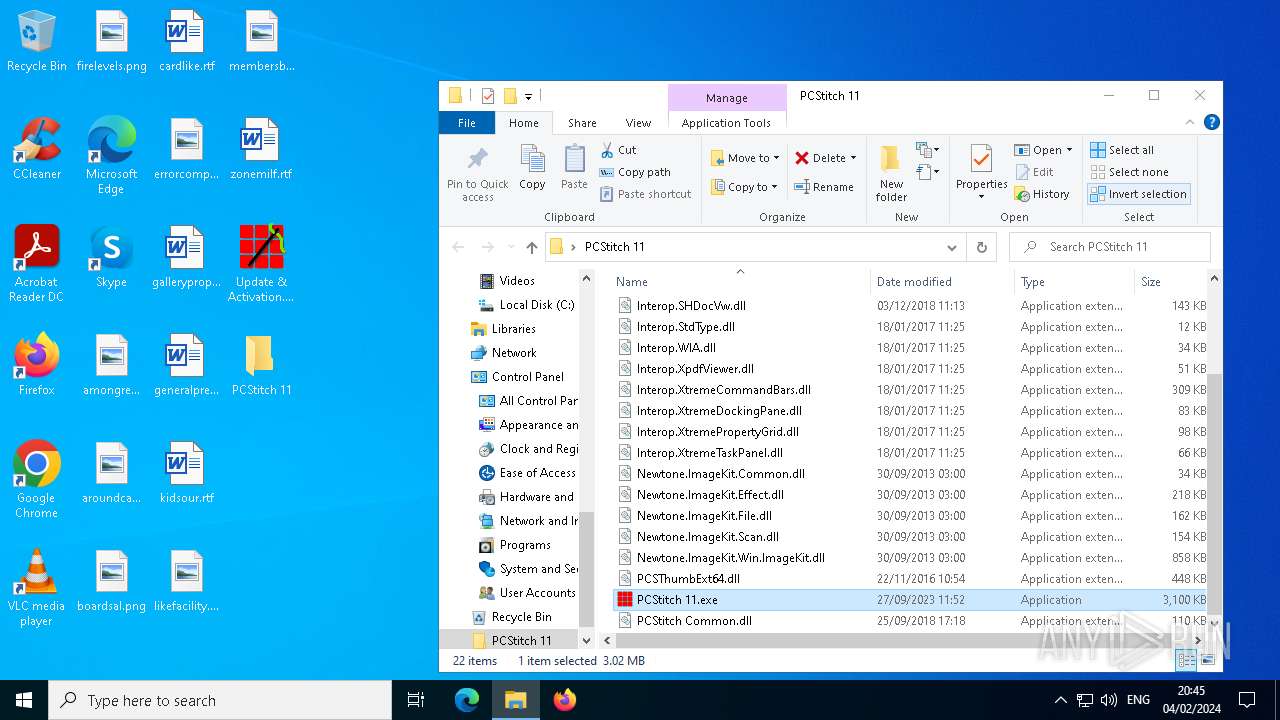
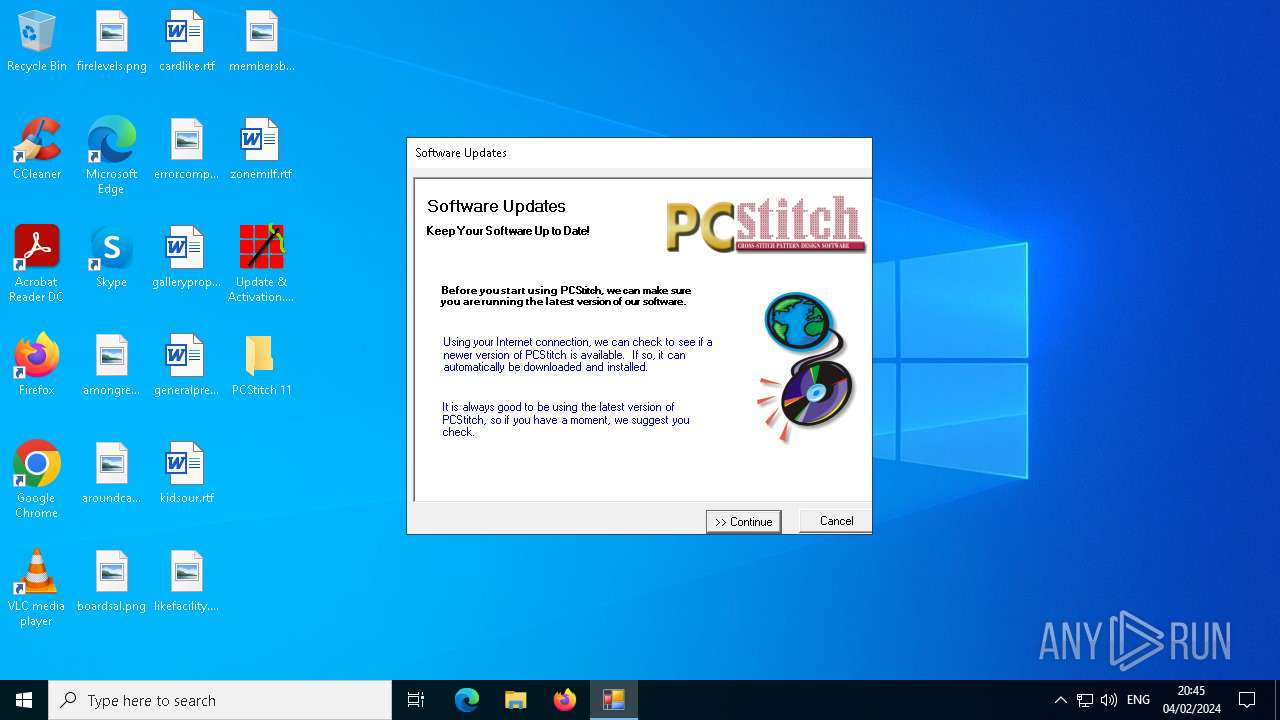
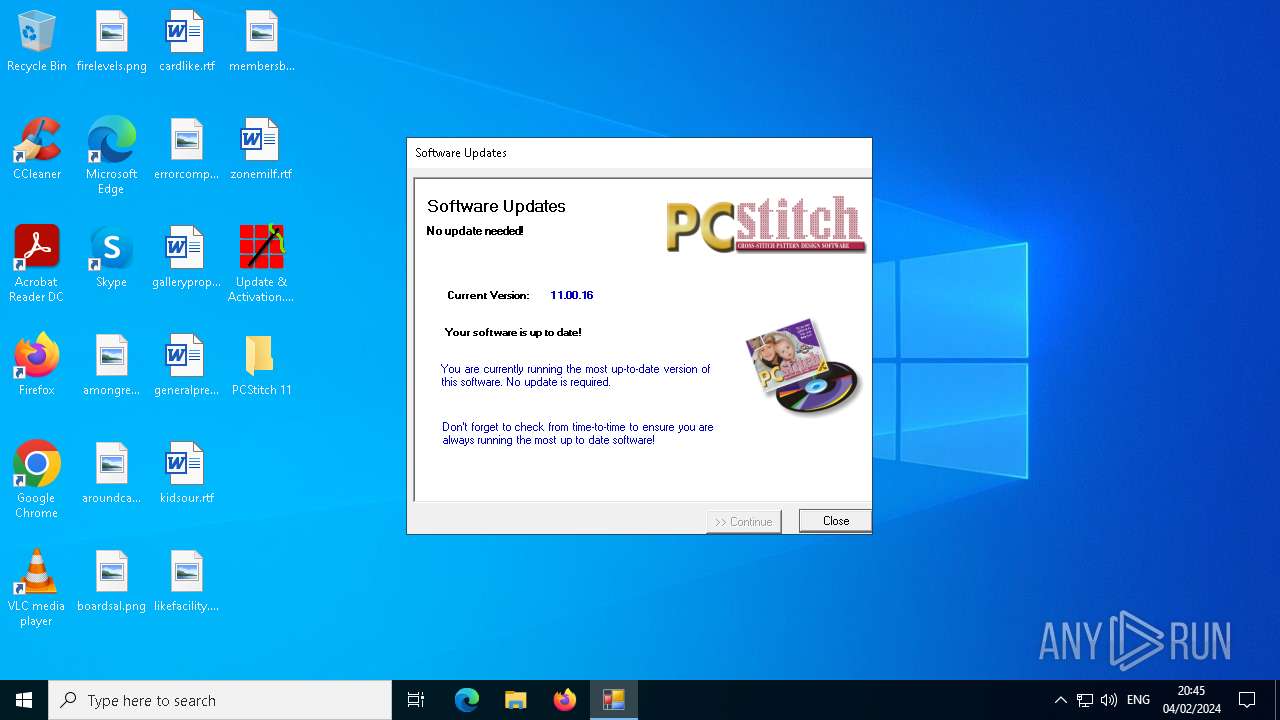
| File name: | Update & Activation.exe |
| Full analysis: | https://app.any.run/tasks/6ee8b2ea-a07e-41d3-9971-55f786343131 |
| Verdict: | Malicious activity |
| Analysis date: | February 04, 2024, 20:44:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A3980159AFED25451DD375FF96674E91 |
| SHA1: | BF30387F3068FBC51F88ADBC3D53F18D4D11A871 |
| SHA256: | E316170C1A844B25DE55E7BE40345F31BA62A12CB157B301B91CDB913B461AE1 |
| SSDEEP: | 98304:ia7BL3n+C+iZjb7JGe/V8/EAGXMYbZeYgMqM5D4QvxLNgzP+btRc9DeaR3YIIdf3:7RxVxLmE |
MALICIOUS
Drops the executable file immediately after the start
- Update & Activation.exe (PID: 6200)
- Update & Activation.exe (PID: 6700)
- Update & Activation.exe (PID: 2200)
- Update & Activation.exe (PID: 2588)
- Update & Activation.tmp (PID: 4100)
- Update & Activation.tmp (PID: 5448)
SUSPICIOUS
Executable content was dropped or overwritten
- Update & Activation.exe (PID: 6200)
- Update & Activation.exe (PID: 6700)
- Update & Activation.tmp (PID: 4100)
- Update & Activation.exe (PID: 2588)
- Update & Activation.exe (PID: 2200)
- Update & Activation.tmp (PID: 5448)
Reads the date of Windows installation
- Update & Activation.tmp (PID: 1124)
- Update & Activation.tmp (PID: 5820)
Reads the Windows owner or organization settings
- Update & Activation.tmp (PID: 4100)
- Update & Activation.tmp (PID: 5448)
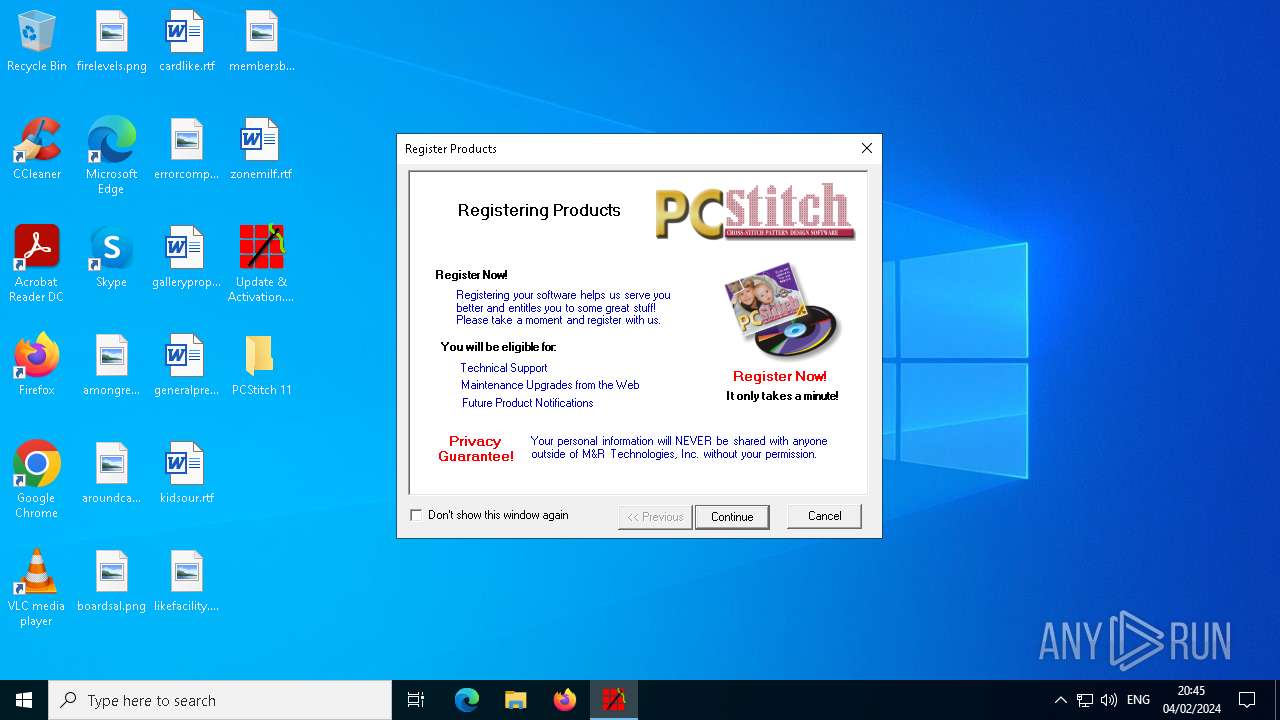
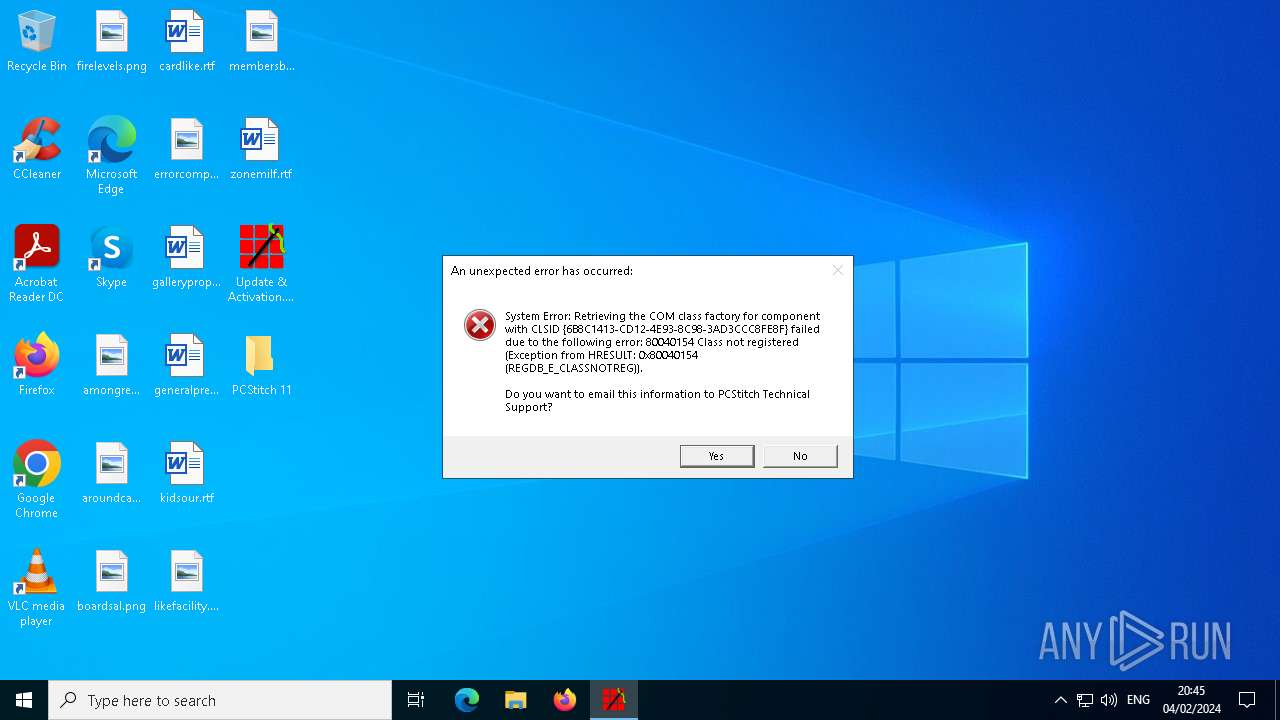
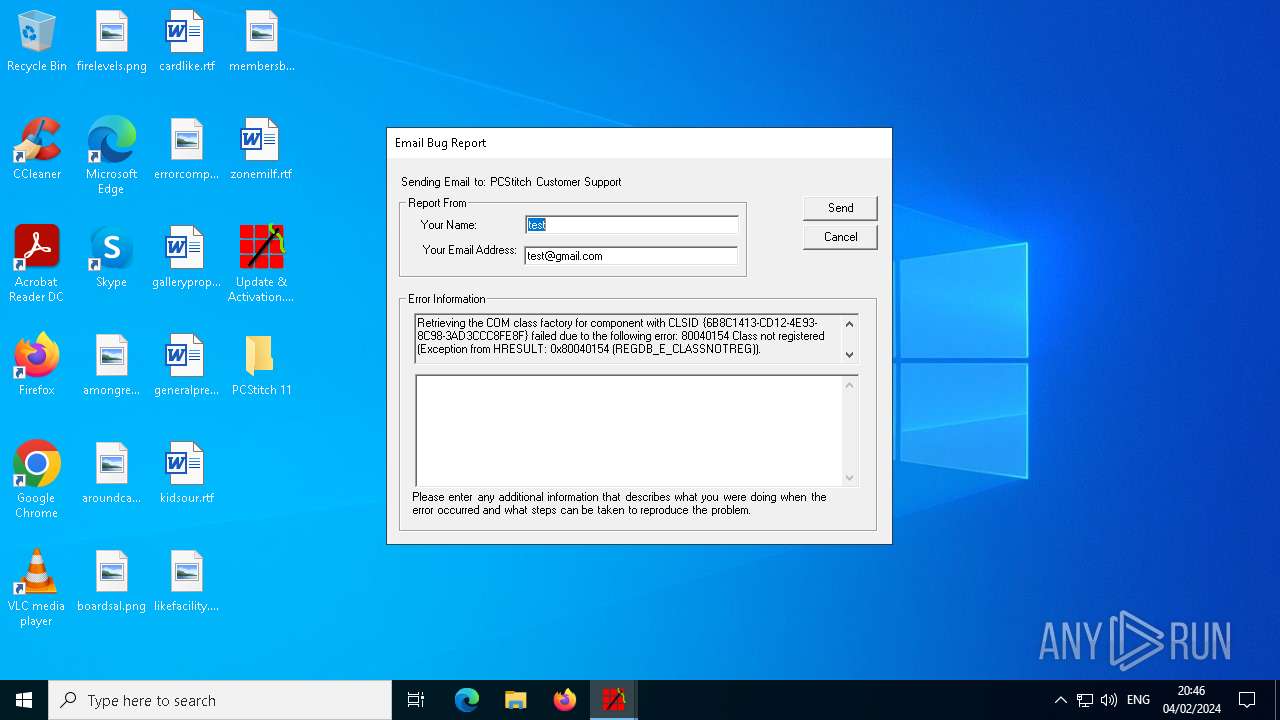
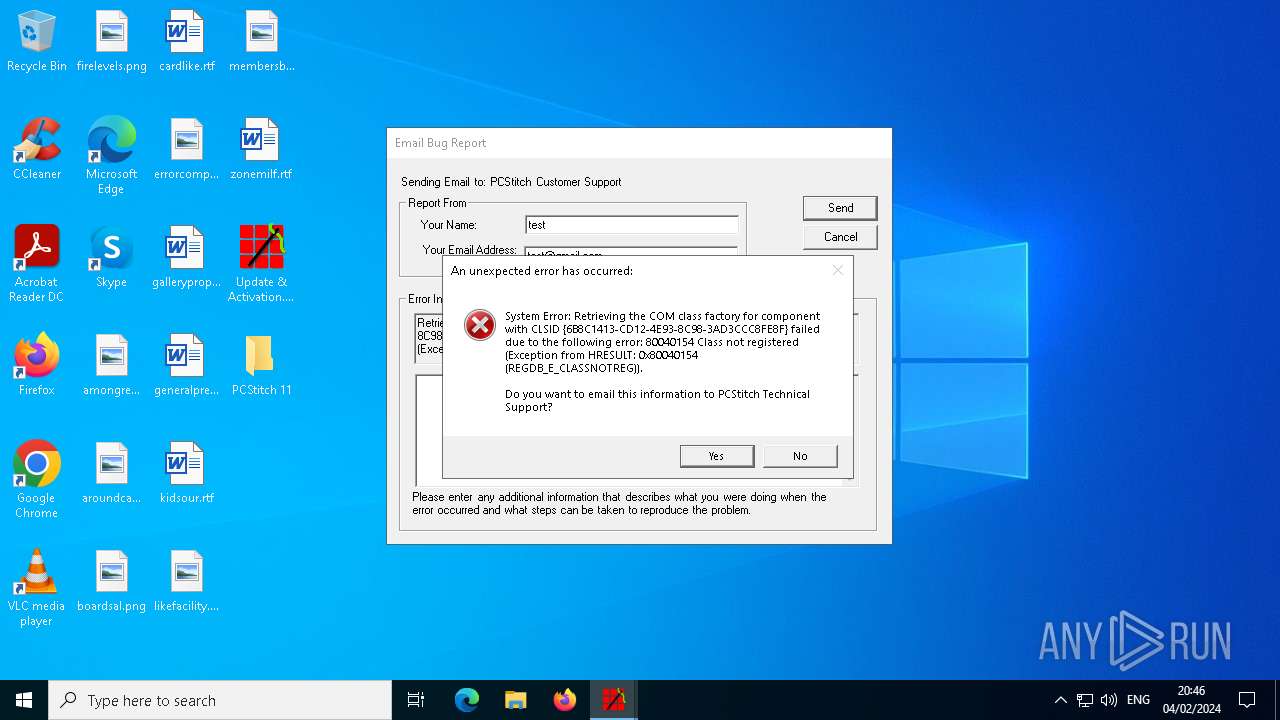
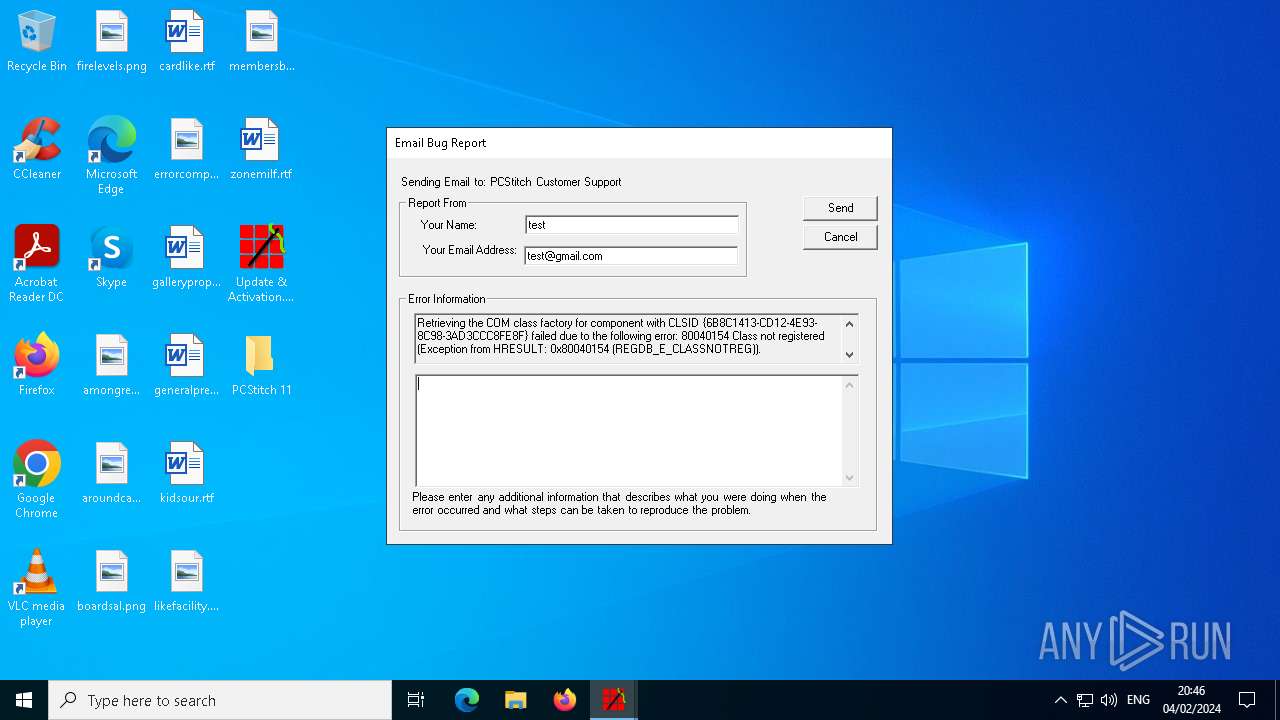
Executes application which crashes
- PCStitch 11.exe (PID: 6288)
INFO
Checks supported languages
- Update & Activation.exe (PID: 6200)
- Update & Activation.tmp (PID: 1124)
- Update & Activation.exe (PID: 6700)
- Update & Activation.exe (PID: 2588)
- Update & Activation.tmp (PID: 4100)
- Update & Activation.tmp (PID: 5820)
- Update & Activation.exe (PID: 2200)
- Update & Activation.tmp (PID: 5448)
- PCStitch 11.exe (PID: 6288)
- ShellExperienceHost.exe (PID: 3176)
Create files in a temporary directory
- Update & Activation.exe (PID: 6200)
- Update & Activation.exe (PID: 6700)
- Update & Activation.tmp (PID: 4100)
- Update & Activation.exe (PID: 2588)
- Update & Activation.exe (PID: 2200)
- Update & Activation.tmp (PID: 5448)
Manual execution by a user
- Update & Activation.exe (PID: 2588)
- PCStitch 11.exe (PID: 6288)
Reads the computer name
- Update & Activation.tmp (PID: 1124)
- Update & Activation.tmp (PID: 4100)
- Update & Activation.tmp (PID: 5820)
- Update & Activation.tmp (PID: 5448)
- PCStitch 11.exe (PID: 6288)
- ShellExperienceHost.exe (PID: 3176)
Creates files in the program directory
- Update & Activation.tmp (PID: 4100)
Reads Environment values
- PCStitch 11.exe (PID: 6288)
Reads the machine GUID from the registry
- PCStitch 11.exe (PID: 6288)
Checks proxy server information
- PCStitch 11.exe (PID: 6288)
- WerFault.exe (PID: 472)
Reads the software policy settings
- PCStitch 11.exe (PID: 6288)
- WerFault.exe (PID: 472)
Creates files or folders in the user directory
- WerFault.exe (PID: 472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41984 |
| InitializedDataSize: | 14336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaad0 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | M&R Technologies |
| FileDescription: | PCStitch Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | PCStitch |
| ProductVersion: | 11.00.016 |
Total processes
160
Monitored processes
12
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6288 -s 2760 | C:\Windows\SysWOW64\WerFault.exe | PCStitch 11.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1081 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1124 | "C:\Users\admin\AppData\Local\Temp\is-1UDDV.tmp\Update & Activation.tmp" /SL5="$60240,2480078,57344,C:\Users\admin\Desktop\Update & Activation.exe" | C:\Users\admin\AppData\Local\Temp\is-1UDDV.tmp\Update & Activation.tmp | — | Update & Activation.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2200 | "C:\Users\admin\Desktop\Update & Activation.exe" /SPAWNWND=$901F0 /NOTIFYWND=$90278 | C:\Users\admin\Desktop\Update & Activation.exe | Update & Activation.tmp | ||||||||||||
User: admin Company: M&R Technologies Integrity Level: HIGH Description: PCStitch Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2588 | "C:\Users\admin\Desktop\Update & Activation.exe" | C:\Users\admin\Desktop\Update & Activation.exe | explorer.exe | ||||||||||||
User: admin Company: M&R Technologies Integrity Level: MEDIUM Description: PCStitch Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3176 | "C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 0 Version: 10.0.19041.1151 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4100 | "C:\Users\admin\AppData\Local\Temp\is-RGECD.tmp\Update & Activation.tmp" /SL5="$A0206,2480078,57344,C:\Users\admin\Desktop\Update & Activation.exe" /SPAWNWND=$801C6 /NOTIFYWND=$60240 | C:\Users\admin\AppData\Local\Temp\is-RGECD.tmp\Update & Activation.tmp | Update & Activation.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 5324 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5448 | "C:\Users\admin\AppData\Local\Temp\is-43KI3.tmp\Update & Activation.tmp" /SL5="$1301BE,2480078,57344,C:\Users\admin\Desktop\Update & Activation.exe" /SPAWNWND=$901F0 /NOTIFYWND=$90278 | C:\Users\admin\AppData\Local\Temp\is-43KI3.tmp\Update & Activation.tmp | Update & Activation.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 5820 | "C:\Users\admin\AppData\Local\Temp\is-QNVVM.tmp\Update & Activation.tmp" /SL5="$90278,2480078,57344,C:\Users\admin\Desktop\Update & Activation.exe" | C:\Users\admin\AppData\Local\Temp\is-QNVVM.tmp\Update & Activation.tmp | — | Update & Activation.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 6200 | "C:\Users\admin\Desktop\Update & Activation.exe" | C:\Users\admin\Desktop\Update & Activation.exe | explorer.exe | ||||||||||||
User: admin Company: M&R Technologies Integrity Level: MEDIUM Description: PCStitch Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
10 740
Read events
10 720
Write events
8
Delete events
12
Modification events
| (PID) Process: | (4100) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: E62F77D5811E1CCD9215EF0F3F3BBF3F11F84DFF5288B741F184CD61D5C9C618 | |||
| (PID) Process: | (4100) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files (x86)\PCStitch 11\AxInterop.SHDocVw.dll | |||
| (PID) Process: | (4100) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4100) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: C817A24E086DF4058D4B98295871CAECEF11D7F46ADE699D23D545F34A02A014 | |||
| (PID) Process: | (4100) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 04100000A6A70F01AB57DA01 | |||
| (PID) Process: | (4100) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5448) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: AD86B4D7D97154F5F6B0B8C5DC955668D77A34AF819A23EC040F6BECD404D30D | |||
| (PID) Process: | (5448) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Users\admin\Desktop\PCStitch 11\AxInterop.SHDocVw.dll | |||
| (PID) Process: | (5448) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5448) Update & Activation.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 7A86E540C0521318093D39FFD9EFAAF46B6810F8DEC2E3FEE102423305F91892 | |||
Executable files
94
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6200 | Update & Activation.exe | C:\Users\admin\AppData\Local\Temp\is-1UDDV.tmp\Update & Activation.tmp | executable | |
MD5:604A8AF42EF41CE6A8B34F9B5BB079C4 | SHA256:028E855E3FFA2EDACF8AF423AD2004A7665E47CCDEA325C433FC759C9152DFC3 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\is-E3325.tmp | executable | |
MD5:4AB6198B02E3ED83396FCB5C4A1B06CB | SHA256:390BA64DDE2156D4ECFE69C8B7FDA2FF9D7BEE15930161B08F6ECD84E4BE0F41 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\is-GUGJF.tmp | executable | |
MD5:94FECD0D77402E1561F4802AAFF3EF11 | SHA256:59C54E6AD17614AC57847D933E1363080CA016E1560FE5498DF92268ED422FB1 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\AxInterop.XtremeCommandBars.dll | executable | |
MD5:4AB6198B02E3ED83396FCB5C4A1B06CB | SHA256:390BA64DDE2156D4ECFE69C8B7FDA2FF9D7BEE15930161B08F6ECD84E4BE0F41 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\AxInterop.SHDocVw.dll | executable | |
MD5:DDD507C6501BE1B478E26B7FBCCE20A2 | SHA256:72B94BB137962C33FB70192E400F637F387C4240A84358E91E6838B85A83E77E | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\is-Q3K3O.tmp | executable | |
MD5:DDD507C6501BE1B478E26B7FBCCE20A2 | SHA256:72B94BB137962C33FB70192E400F637F387C4240A84358E91E6838B85A83E77E | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\is-R61BU.tmp | executable | |
MD5:700A08398357B232BBC087232F7E0F8A | SHA256:676BDE9D2D48B39E64E8D948FDFC1756B59D49AEF89973597D121CDE423B1692 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\AxInterop.XpdfViewer.dll | executable | |
MD5:700A08398357B232BBC087232F7E0F8A | SHA256:676BDE9D2D48B39E64E8D948FDFC1756B59D49AEF89973597D121CDE423B1692 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\is-04LLA.tmp | executable | |
MD5:F574877FA3C0D19DEE28475E71D5D072 | SHA256:0BFD2099AF308D2FF082423EAF95DF086640931AD8923DBEA6AF1FF04D510D90 | |||
| 4100 | Update & Activation.tmp | C:\Program Files (x86)\PCStitch 11\AxInterop.XtremeDockingPane.dll | executable | |
MD5:94FECD0D77402E1561F4802AAFF3EF11 | SHA256:59C54E6AD17614AC57847D933E1363080CA016E1560FE5498DF92268ED422FB1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
77
TCP/UDP connections
26
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5028 | SearchApp.exe | GET | 200 | 13.107.213.45:443 | https://fp-afd.azurefd.net/apc/trans.gif?e6fdf9138c6b1482023f632c662c9f89 | unknown | — | — | unknown |
5028 | SearchApp.exe | GET | 200 | 150.171.22.254:443 | https://ln-ring.msedge.net/apc/trans.gif?3b69de1f26c1d4c4e904e5e54c31ea62 | unknown | image | 43 b | unknown |
1612 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
5612 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
1612 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
6492 | msedge.exe | GET | 302 | 23.35.229.160:443 | https://go.microsoft.com/fwlink/?linkid=2133855&bucket=15 | unknown | — | — | unknown |
5676 | svchost.exe | HEAD | 200 | 23.44.215.49:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707508670&P2=404&P3=2&P4=A1MV5CyNSjFaZvcq07AsuXiDslL98L0kOR3NVRkQJsVj6SmZ0CMtFkpTT3NihNe4qRcXo5bvr%2fZjnAaHANGqRQ%3d%3d | unknown | — | — | unknown |
5028 | SearchApp.exe | GET | 200 | 131.253.33.254:443 | https://a-ring-fallback.msedge.net/apc/trans.gif?3c9b74dce2ee2e72c7fe3e76afd0e461 | unknown | image | 43 b | unknown |
— | — | POST | 204 | 92.123.104.52:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
6492 | msedge.exe | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/111.0.1661.62?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig%2CEdgeDomainActions&osname=win&client=edge&channel=stable&scpfull=0&scpguard=0&scpfre=0&scpver=0&osarch=x86_64&osver=10.0.19044&wu=1&devicefamily=desktop&uma=0&sessionid=13&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245 | unknown | binary | 81.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5612 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1612 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5612 | MoUsoCoreWorker.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1612 | svchost.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
5612 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
5028 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5028 | SearchApp.exe | 150.171.22.254:443 | ln-ring.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5028 | SearchApp.exe | 13.107.246.45:443 | fp-afd.azurefd.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5028 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
ln-ring.msedge.net |
| unknown |
fp-afd.azurefd.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5028 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |