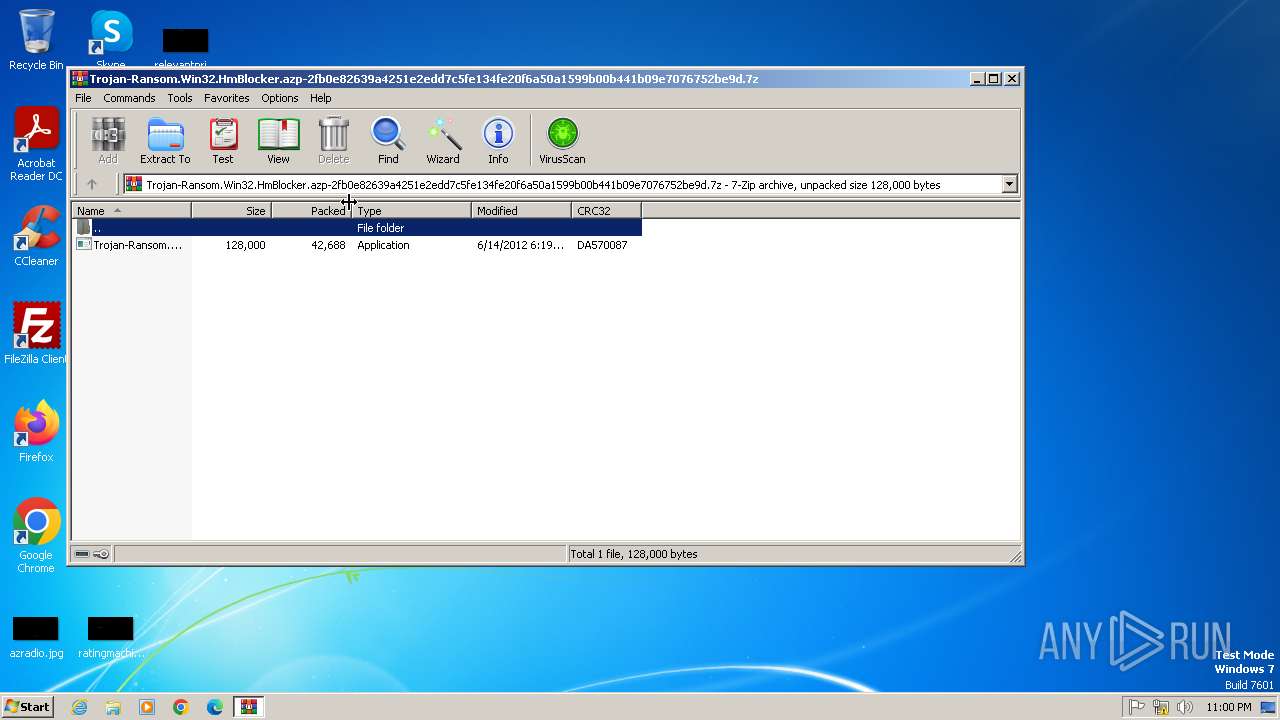
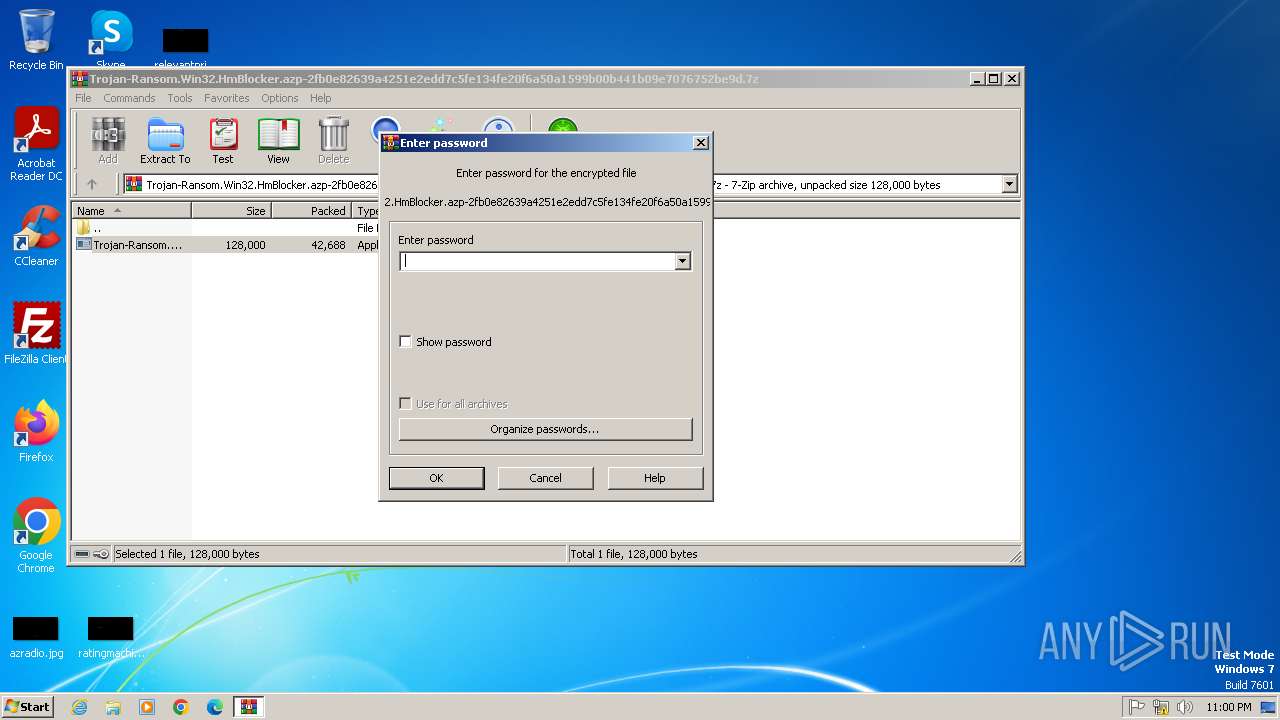
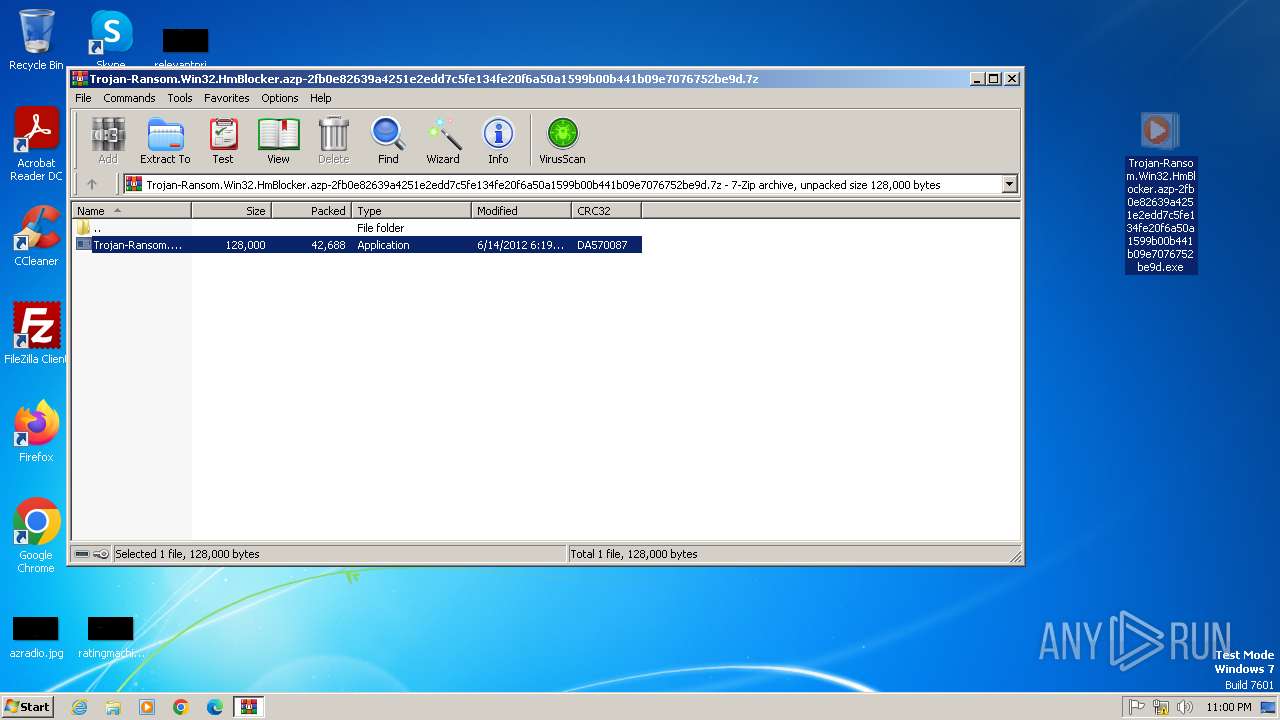
| File name: | Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.7z |
| Full analysis: | https://app.any.run/tasks/9efe9cf5-ac1f-4ec1-af4b-d90a106e12d9 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 22:00:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | F46A07A6BDE8D74D099A23D1BFDE8A93 |
| SHA1: | 024B6026737FCD9D25AFFC81DC583C237BB2BC07 |
| SHA256: | E2FAD368A00AA419A65CB406FB48B65D7CA1A8B84ACE54926E5371BE77840E93 |
| SSDEEP: | 768:Lbd8qrD1hjpR6f3jW9+GNtu0WcPH4Ry9vCdVA1kIqHZBOqhunJt7z1ot:fd1tp8f3pEHyA9EVARsb4Jt7Bot |
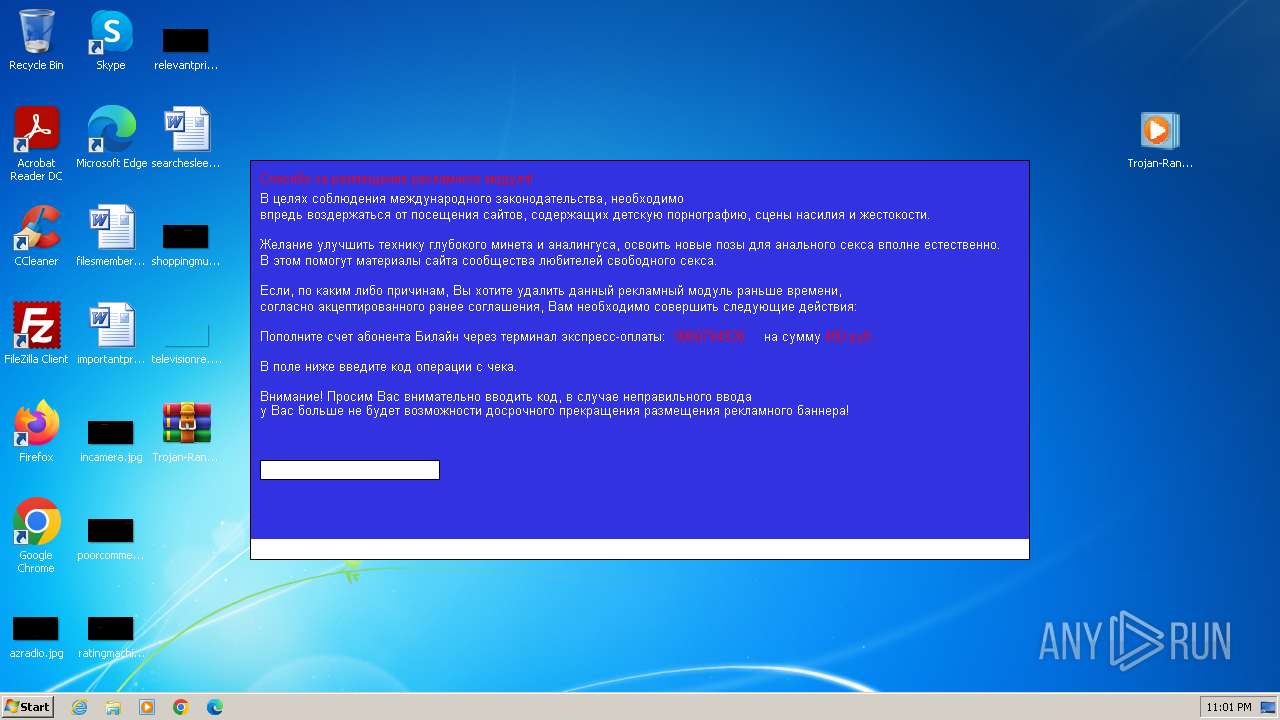
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 2420)
SUSPICIOUS
Reads the Internet Settings
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
- sipnotify.exe (PID: 288)
Starts CMD.EXE for commands execution
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2744)
Reads security settings of Internet Explorer
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
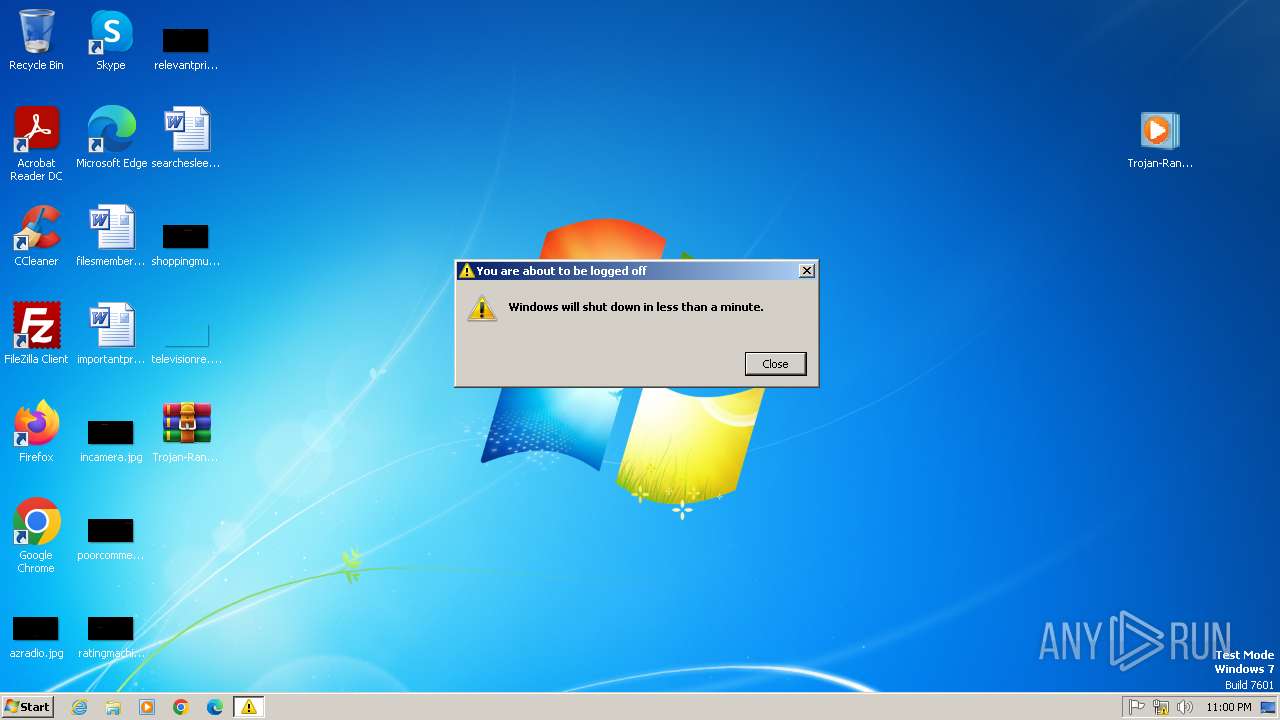
The system shut down or reboot
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
The process executes via Task Scheduler
- sipnotify.exe (PID: 288)
- ctfmon.exe (PID: 1832)
INFO
Checks supported languages
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
- IMEKLMG.EXE (PID: 2144)
- IMEKLMG.EXE (PID: 2152)
- 1886015021.EXE (PID: 2172)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
Manual execution by a user
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
- IMEKLMG.EXE (PID: 2144)
- IMEKLMG.EXE (PID: 2152)
- 1886015021.EXE (PID: 2172)
Reads the computer name
- Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe (PID: 328)
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2144)
- 1886015021.EXE (PID: 2172)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2144)
- IMEKLMG.EXE (PID: 2152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2012:06:14 17:19:26+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe |
Total processes
92
Monitored processes
10
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 328 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 704 | "C:\Windows\System32\shutdown.exe" /R /T 04 /F | C:\Windows\System32\shutdown.exe | — | Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2172 | "C:\Users\admin\1886015021\1886015021.EXE" | C:\Users\admin\1886015021\1886015021.EXE | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2420 | rEg aDd HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v f18860150211886015021a1886015021 /d "C:\Users\admin\1886015021\1886015021.EXE" /F | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | "C:\Windows\System32\cmd.exe" /C rEg aDd HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v f18860150211886015021a1886015021 /d "C:\Users\admin\1886015021\1886015021.EXE" /F | C:\Windows\System32\cmd.exe | — | Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2840 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 325
Read events
2 282
Write events
42
Delete events
1
Modification events
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.7z | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2840.33044\Trojan-Ransom.Win32.HmBlocker.azp-2fb0e82639a4251e2edd7c5fe134fe20f6a50a1599b00b441b09e7076752be9d.exe | executable | |
MD5:6783BAE7B65102AB0840CE24819060A3 | SHA256:95BCBCF97C7E70ABBD5226E9C4835A0F481FCB69F653396A8AA7B0E67BAADC1A | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\en-us.html | html | |
MD5:5001C5247AF7E35AC35ACE61B87E8040 | SHA256:2920ED0DDFE475884703A5AE7B835F40398E509AA26B52A8DDD7F25DCD4B3D2E | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\main.jpg | image | |
MD5:C8BCC2041232DA45C1367F1FEED51370 | SHA256:C0EC6771F923E7B85F6E2E7AA58D6BA51D322E78F53CEE8108DBBFD352BE7B25 | |||
| 2172 | 1886015021.EXE | C:\Users\admin\1886015021\z | text | |
MD5:CEE631121C2EC9232F3A2F028AD5C89B | SHA256:0604CD3138FEED202EF293E062DA2F4720F77A05D25EE036A7A01C9CFCDD1F0A | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\microsoft-logo.png | image | |
MD5:B7C73A0CFBA68CC70C35EF9C63703CE4 | SHA256:1D8B27A0266FF526CF95447F3701592A908848467D37C09A00A2516C1F29A013 | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:253EDC8EC7674BD78293FF3B21866074 | SHA256:51C3A033F0160A30C1773F1E5A9CD01AB018B151EDA1BB64D0226B2437106A56 | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 288 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\default.cab | compressed | |
MD5:340674F6A3D1562E28A011EC11E40D83 | SHA256:259880E2346D986ABEED46AA9C2917C53E969AAE6927F2CA0A2AD0967736DF98 | |||
| 2172 | 1886015021.EXE | C:\Users\admin\1886015021\d | text | |
MD5:3D6CF41728C82A8A0701BB2DEA37CCD1 | SHA256:62D21A51A17A0256FD332F744E40E2FF36E29FE897D18A46F106F9AB88F9701D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
288 | sipnotify.exe | HEAD | 503 | 104.82.90.147:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133895772656400000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1440 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
288 | sipnotify.exe | 104.82.90.147:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |