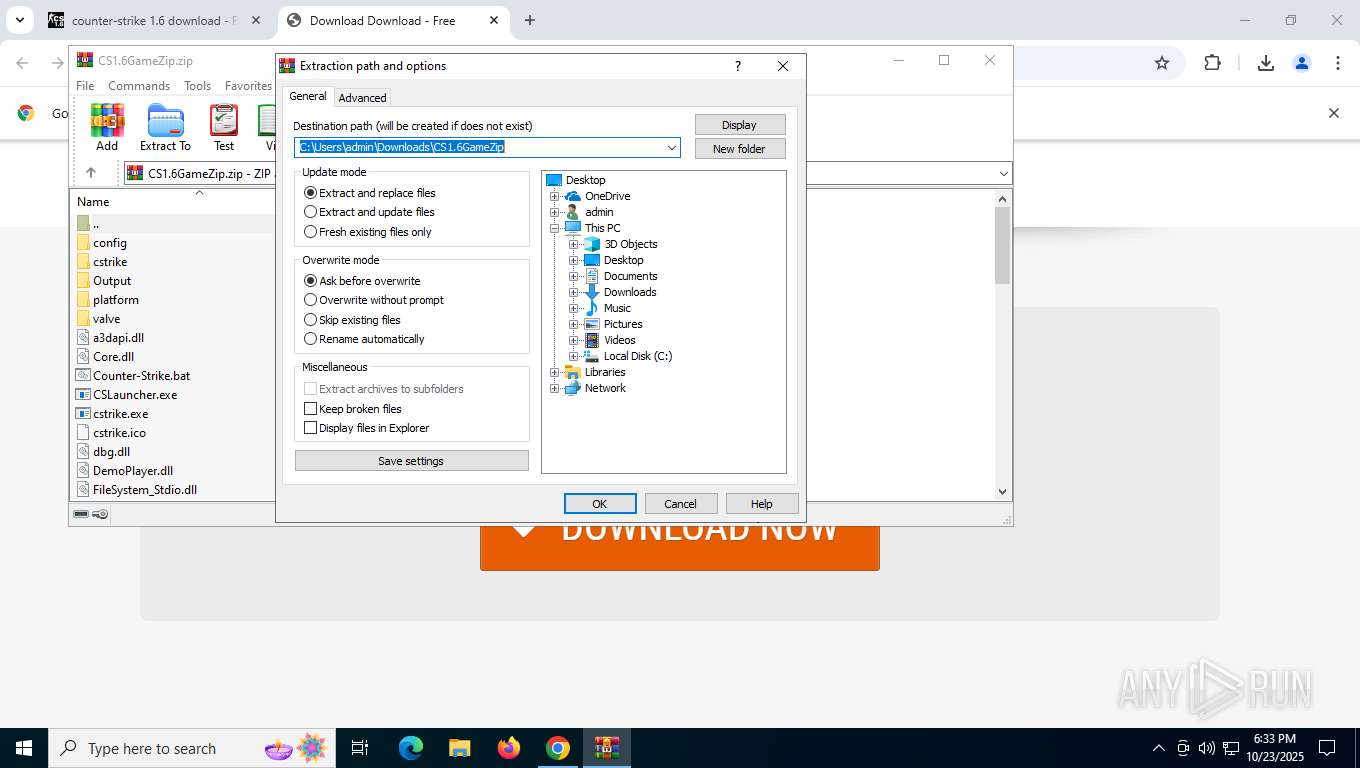
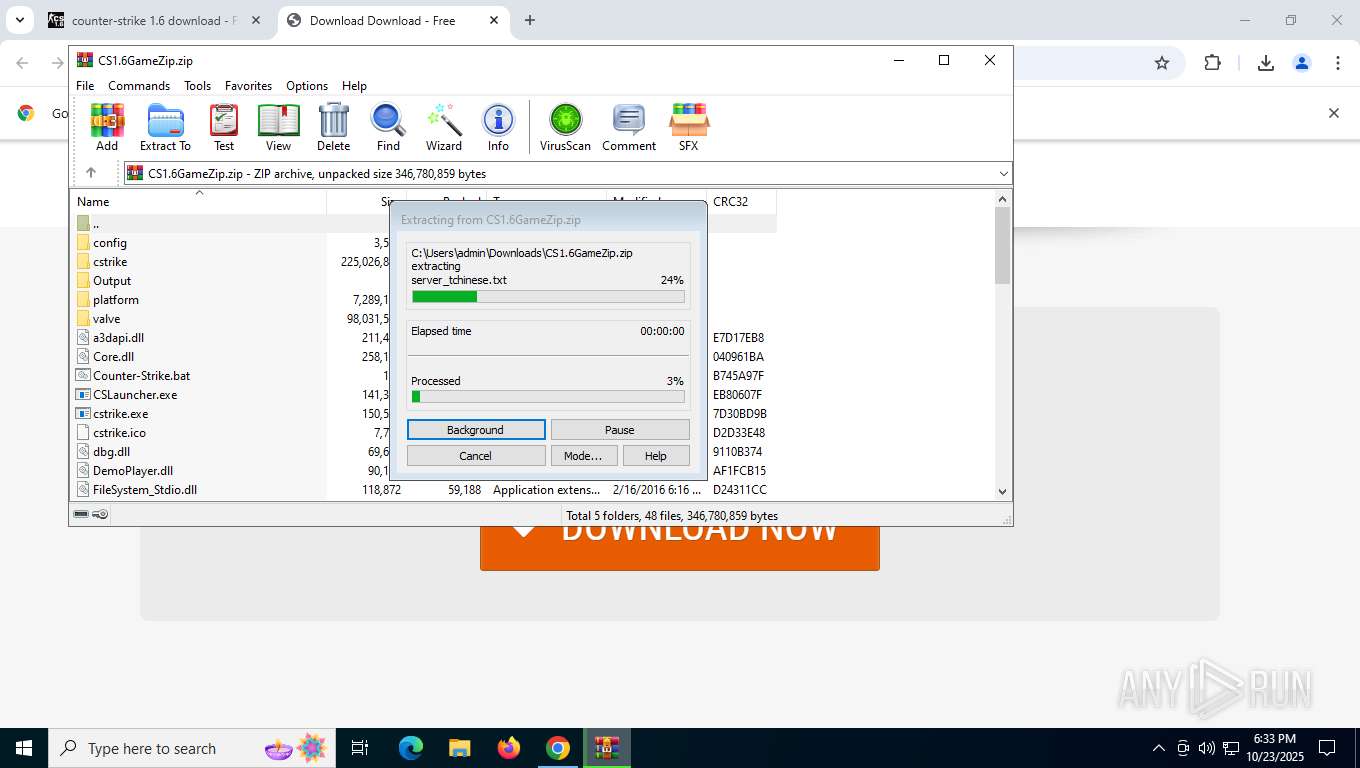
| URL: | https://csdownload.net/ |
| Full analysis: | https://app.any.run/tasks/71b90213-d9b5-4f01-81f1-5acf9a56a4ee |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2025, 18:32:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A1C25FA5751C334E5B3E984D85CB7BBE |
| SHA1: | 22E52D028160F1C6EC3DE3AE449B3EDE5CBAEABD |
| SHA256: | E2EA36C5E121AF5694D78CFF0F04D0A27DD62A7192229D8FE62E8E4EC5B4EF5F |
| SSDEEP: | 3:N8LDD0RK:2TX |
MALICIOUS
No malicious indicators.SUSPICIOUS
Windows service management via SC.EXE
- sc.exe (PID: 7264)
Starts CMD.EXE for commands execution
- CSLauncher.exe (PID: 8244)
Creates a new Windows service
- sc.exe (PID: 6664)
Reads security settings of Internet Explorer
- CSLauncher.exe (PID: 8244)
- GameBar.exe (PID: 8180)
Executes as Windows Service
- HLmonitor.exe (PID: 8892)
Non windows owned service launched
- HLmonitor.exe (PID: 8892)
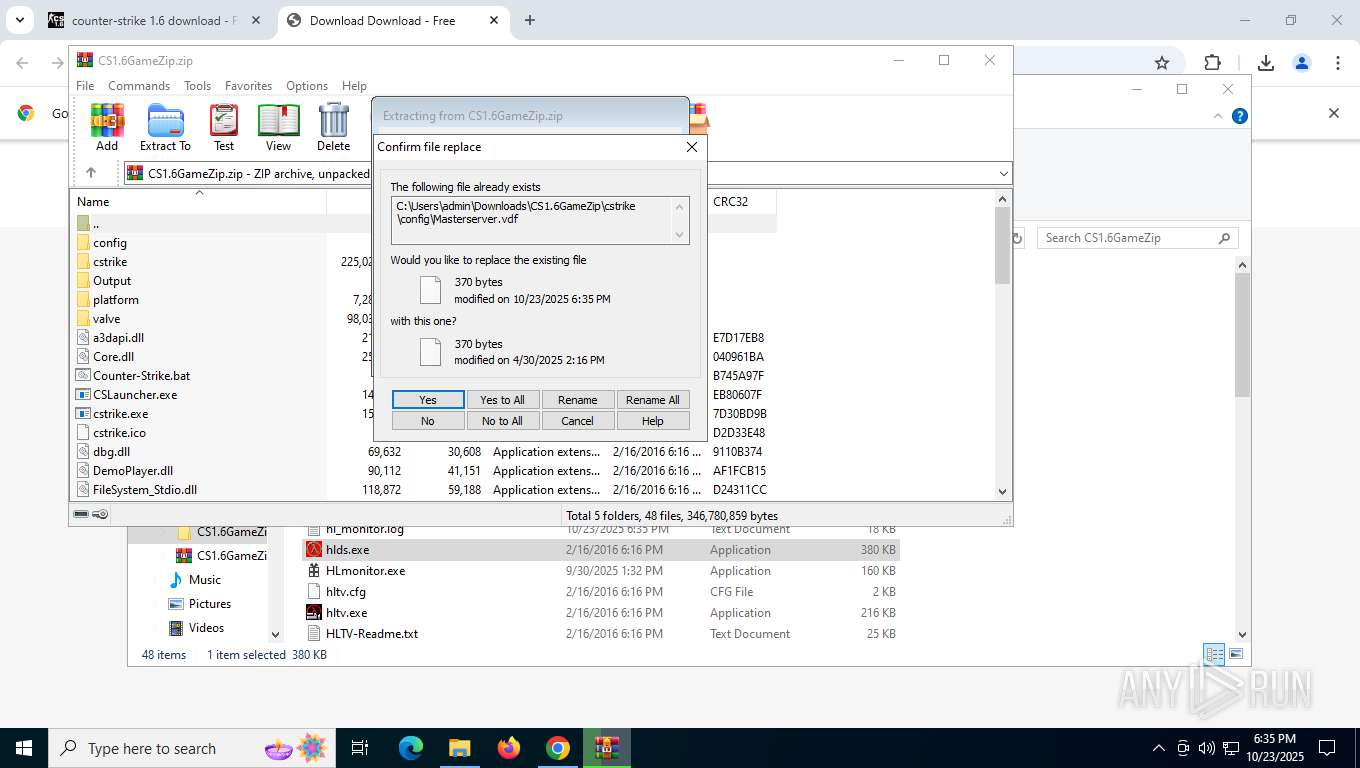
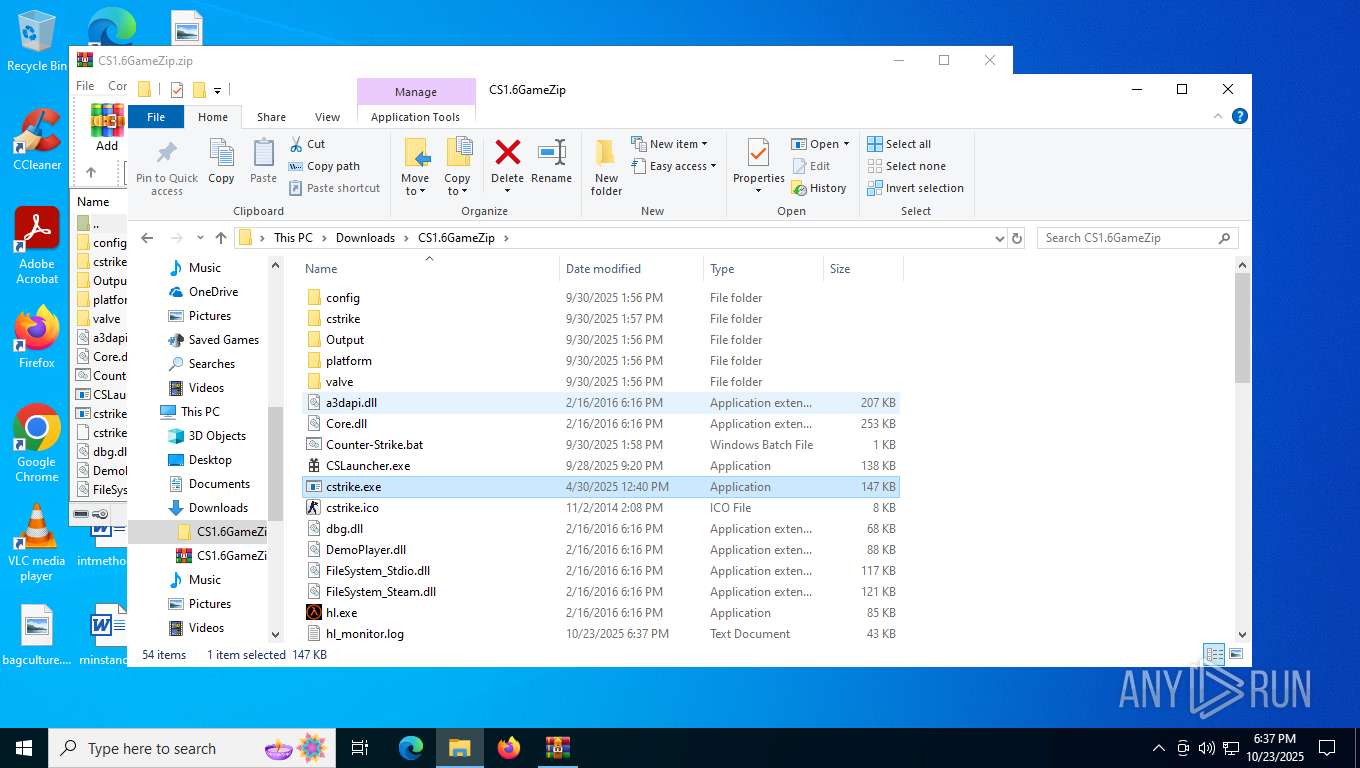
Executable content was dropped or overwritten
- hl.exe (PID: 8888)
- hl.exe (PID: 9064)
- hlds.exe (PID: 5232)
- hl.exe (PID: 8336)
- hl.exe (PID: 2468)
- hl.exe (PID: 132)
- hl.exe (PID: 4788)
- hl.exe (PID: 7412)
- hl.exe (PID: 7016)
There is functionality for taking screenshot (YARA)
- hlds.exe (PID: 5232)
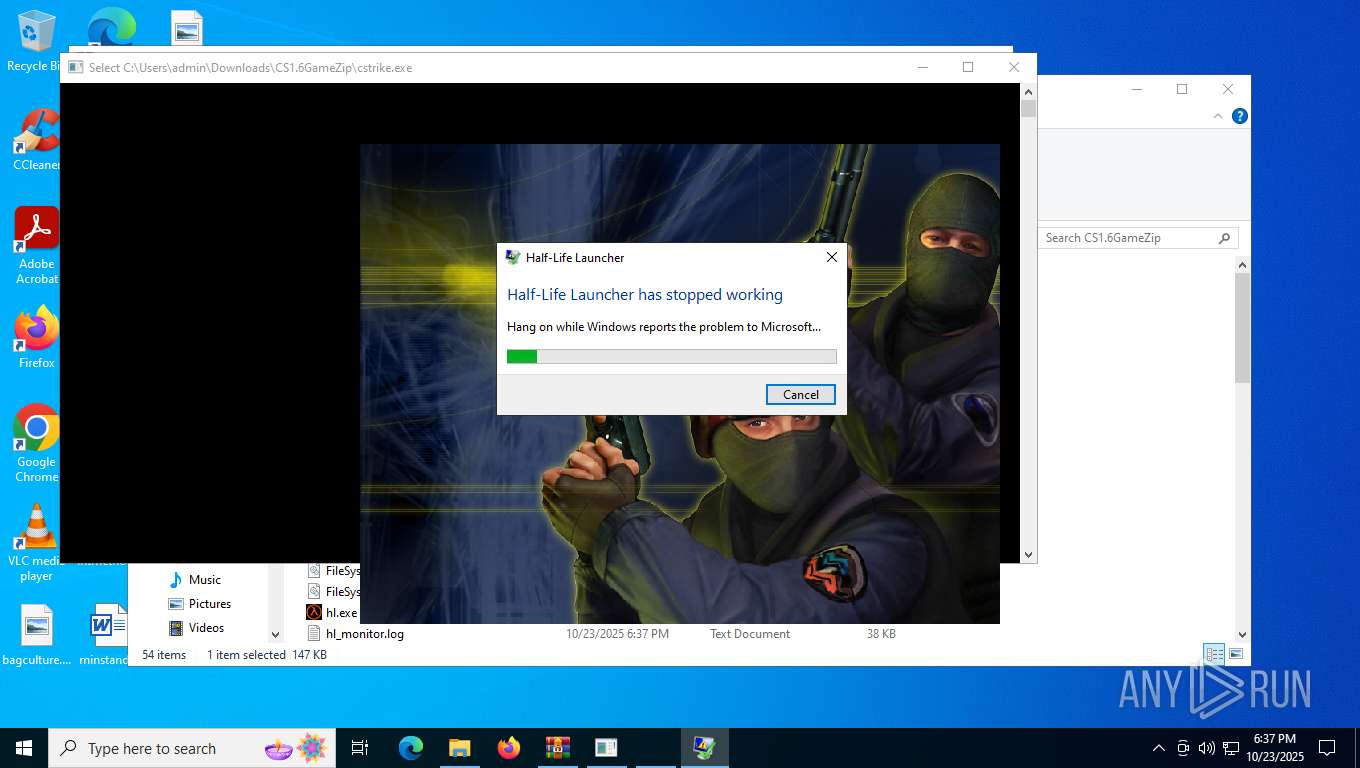
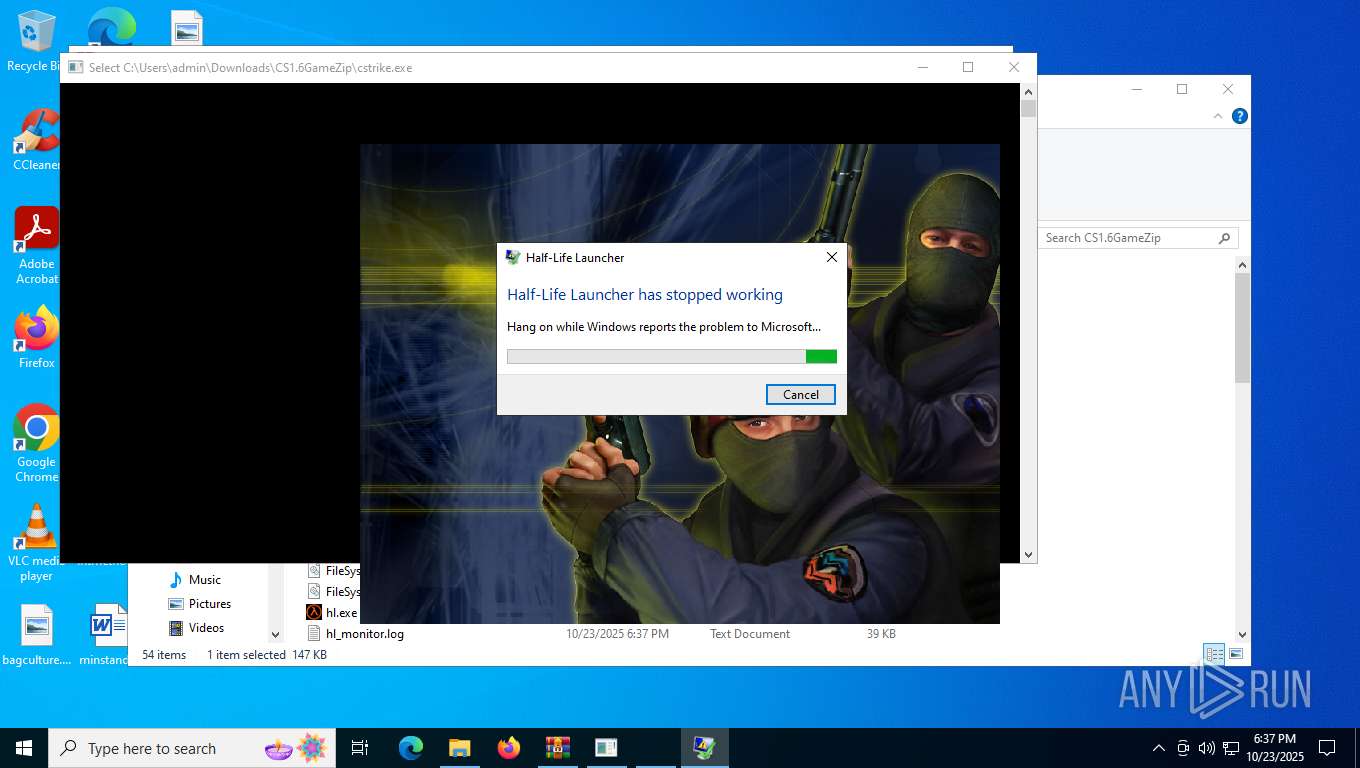
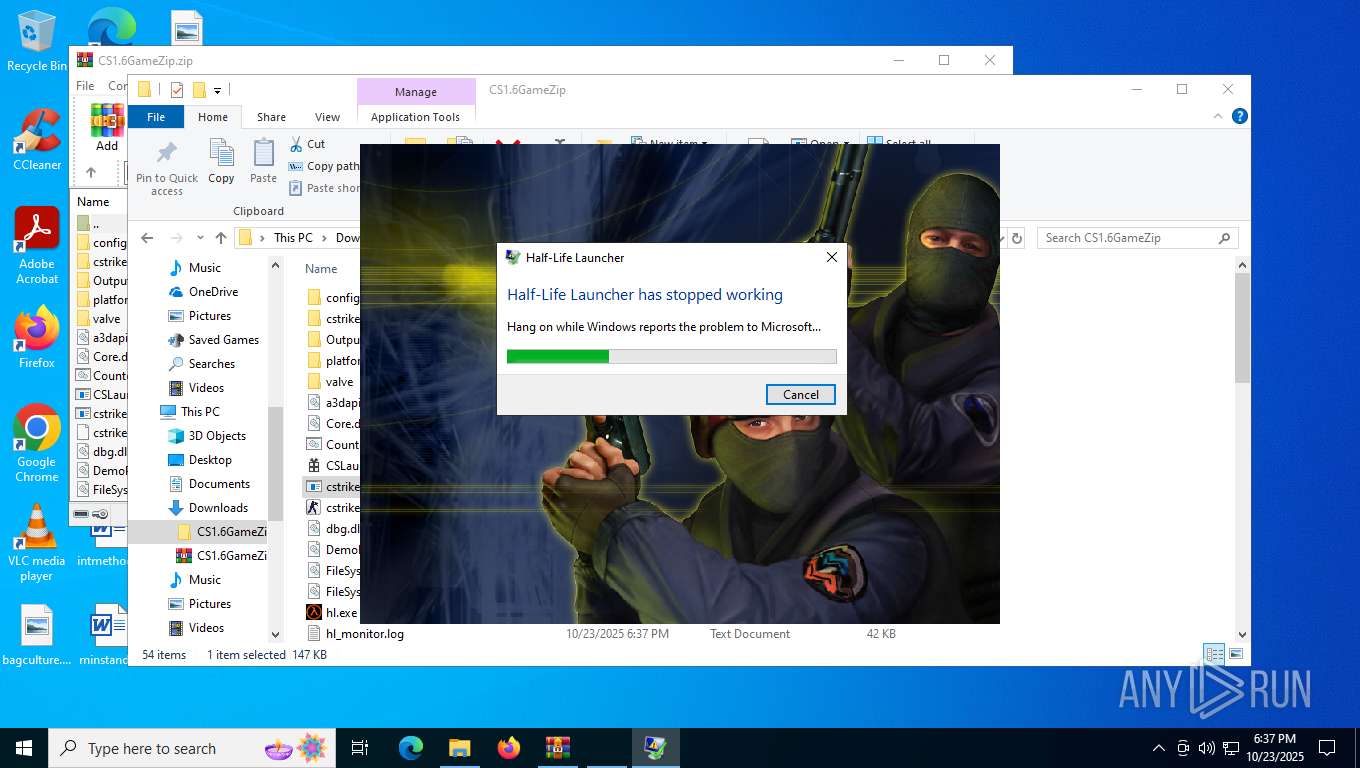
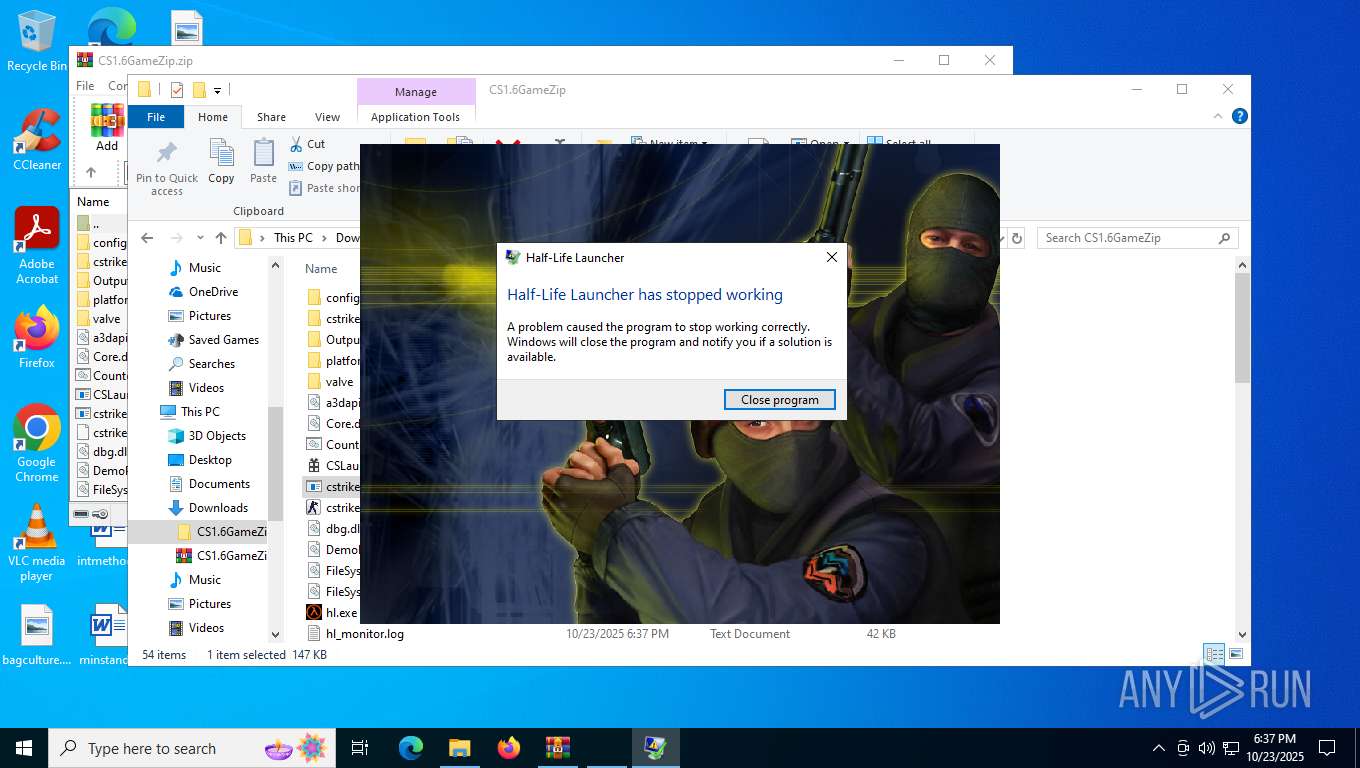
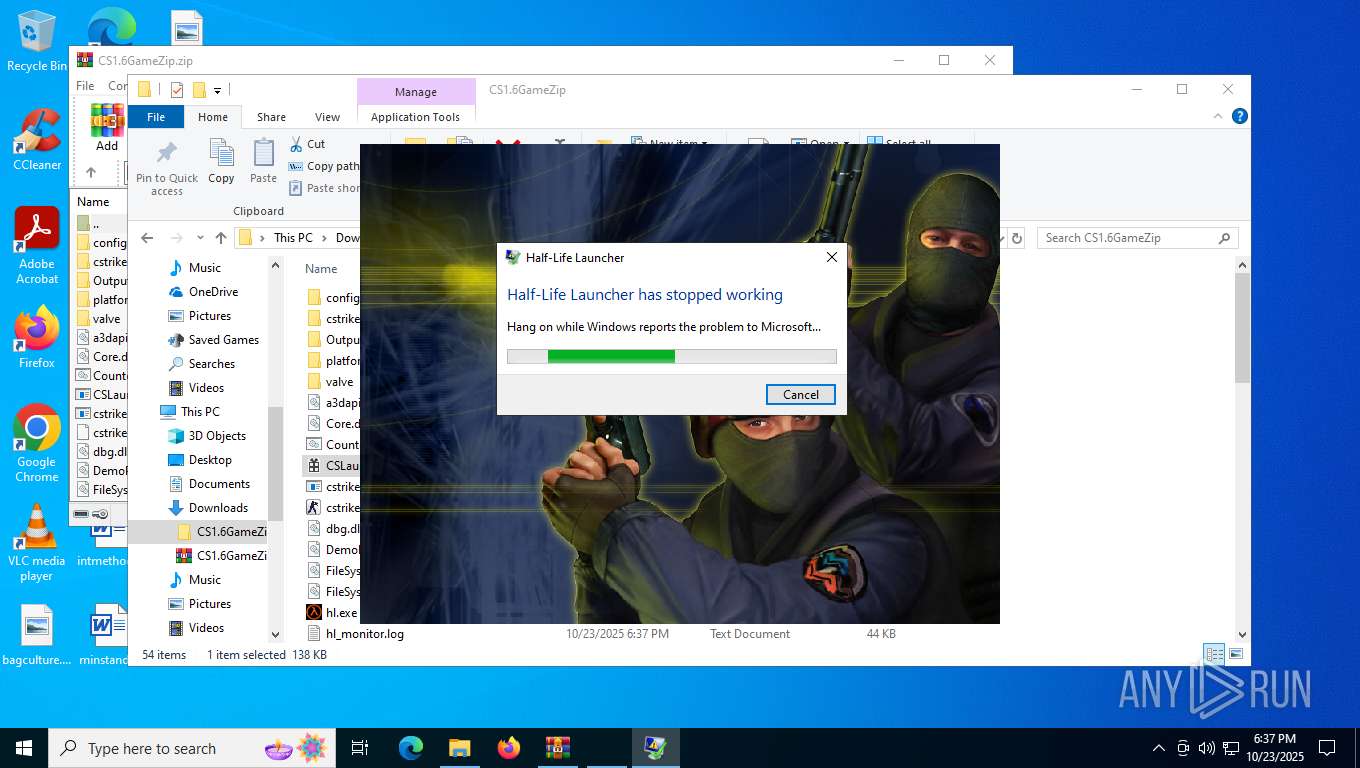
Executes application which crashes
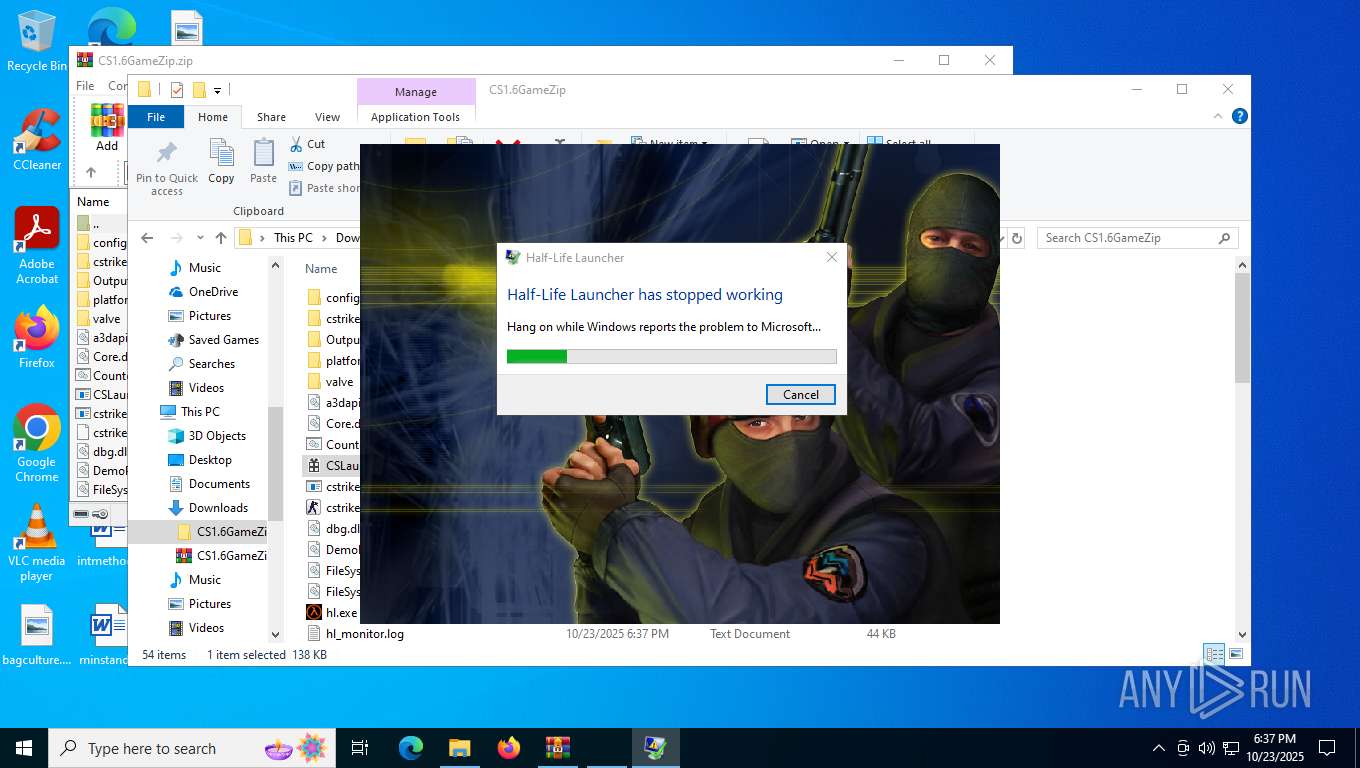
- hl.exe (PID: 4788)
- hl.exe (PID: 7016)
INFO
Application launched itself
- chrome.exe (PID: 7480)
The sample compiled with english language support
- WinRAR.exe (PID: 8524)
- chrome.exe (PID: 7480)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8524)
Reads the software policy settings
- slui.exe (PID: 9120)
- HLmonitor.exe (PID: 8892)
- WerFault.exe (PID: 6456)
- WerFault.exe (PID: 2524)
- WerFault.exe (PID: 468)
- WerFault.exe (PID: 8144)
Checks proxy server information
- slui.exe (PID: 9120)
- WerFault.exe (PID: 6456)
- WerFault.exe (PID: 468)
- WerFault.exe (PID: 8144)
- WerFault.exe (PID: 2524)
Process checks computer location settings
- CSLauncher.exe (PID: 8244)
Reads the computer name
- hl.exe (PID: 8888)
- CSLauncher.exe (PID: 8244)
- HLmonitor.exe (PID: 8892)
- GameBar.exe (PID: 8180)
- hl.exe (PID: 8336)
- hl.exe (PID: 9064)
- hlds.exe (PID: 5232)
- hl.exe (PID: 7412)
- hl.exe (PID: 2468)
- CSLauncher.exe (PID: 4916)
- hl.exe (PID: 132)
- hl.exe (PID: 4788)
- CSLauncher.exe (PID: 8772)
- hl.exe (PID: 7016)
Manual execution by a user
- CSLauncher.exe (PID: 8244)
- hl.exe (PID: 7412)
- hl.exe (PID: 9064)
- hlds.exe (PID: 5232)
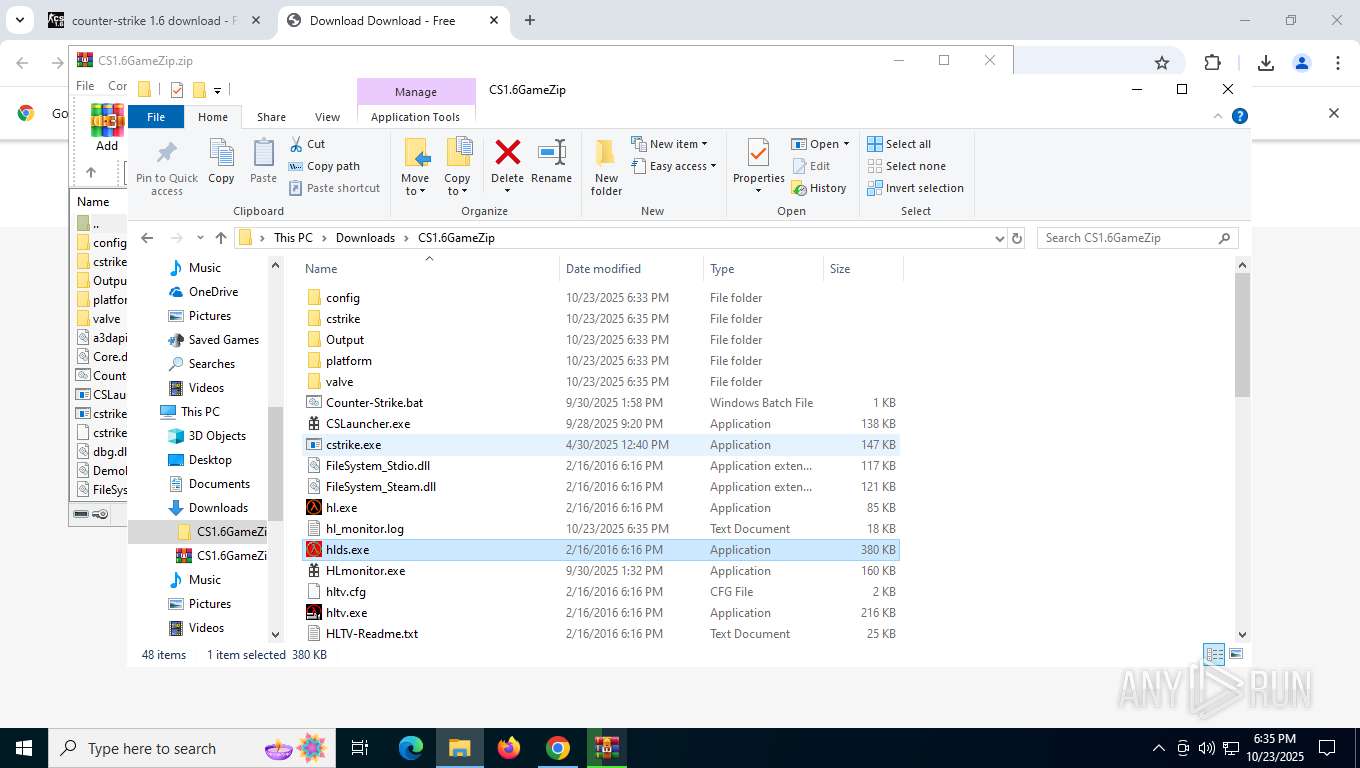
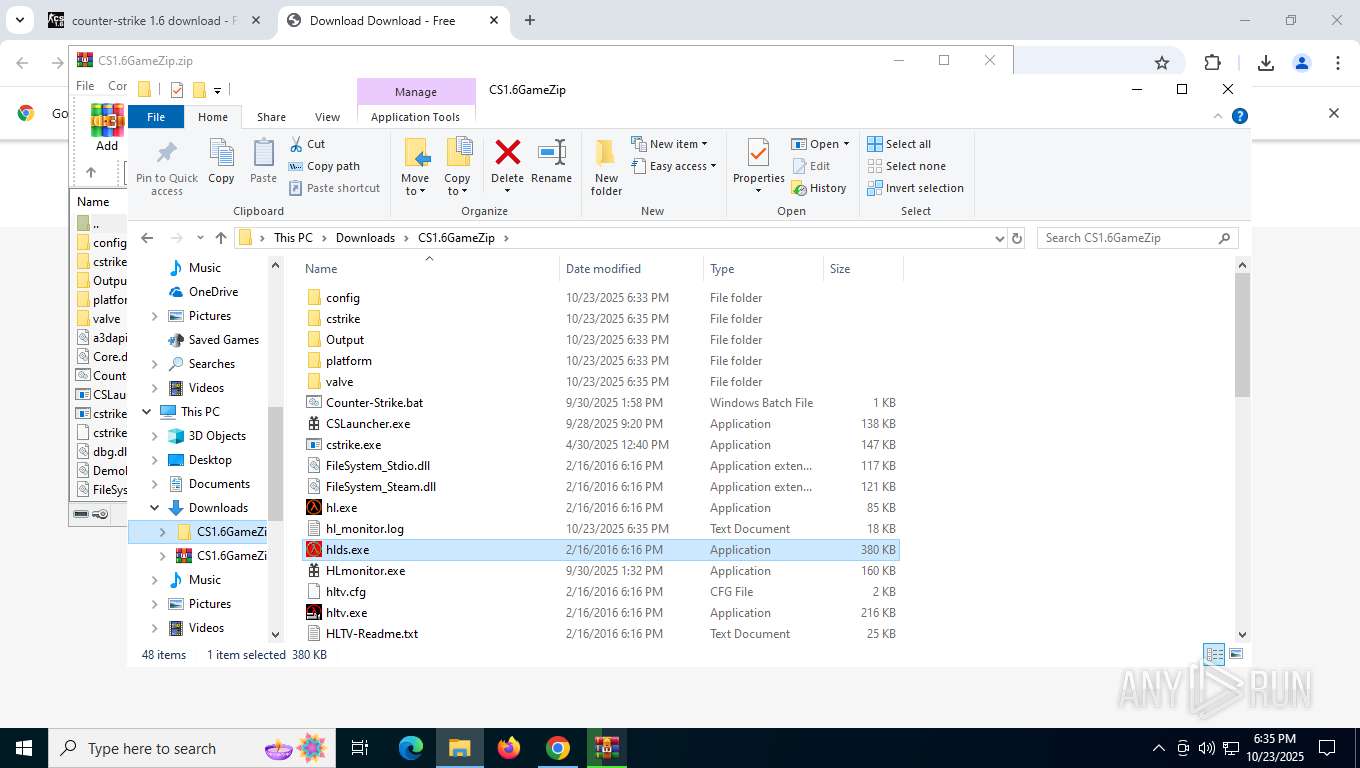
- cstrike.exe (PID: 8936)
- cmd.exe (PID: 9068)
- cstrike.exe (PID: 1404)
- hl.exe (PID: 2468)
- CSLauncher.exe (PID: 8772)
Checks supported languages
- HLmonitor.exe (PID: 8892)
- CSLauncher.exe (PID: 8244)
- hl.exe (PID: 8888)
- GameBar.exe (PID: 8180)
- hl.exe (PID: 9064)
- hlds.exe (PID: 5232)
- hl.exe (PID: 7412)
- hl.exe (PID: 8336)
- cstrike.exe (PID: 8936)
- hl.exe (PID: 2468)
- CSLauncher.exe (PID: 4916)
- hl.exe (PID: 132)
- hl.exe (PID: 4788)
- cstrike.exe (PID: 1404)
- CSLauncher.exe (PID: 8772)
- hl.exe (PID: 7016)
Creates files or folders in the user directory
- WerFault.exe (PID: 6456)
- WerFault.exe (PID: 2524)
- WerFault.exe (PID: 468)
- WerFault.exe (PID: 8144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
218
Monitored processes
59
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Users\admin\Downloads\CS1.6GameZip\hl.exe" -game cstrike -noipx -nojoy -noforcemspd -noforcemparms -noforcemaccel -high | C:\Users\admin\Downloads\CS1.6GameZip\hl.exe | CSLauncher.exe | ||||||||||||
User: admin Company: Valve Integrity Level: MEDIUM Description: Half-Life Launcher Exit code: 4294967295 Version: 1, 1, 1, 1 Modules
| |||||||||||||||
| 468 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7016 -s 1268 | C:\Windows\SysWOW64\WerFault.exe | hl.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1404 | "C:\Users\admin\Downloads\CS1.6GameZip\cstrike.exe" | C:\Users\admin\Downloads\CS1.6GameZip\cstrike.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cstrike.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\Downloads\CS1.6GameZip\hl.exe" | C:\Users\admin\Downloads\CS1.6GameZip\hl.exe | explorer.exe | ||||||||||||
User: admin Company: Valve Integrity Level: MEDIUM Description: Half-Life Launcher Exit code: 4294967295 Version: 1, 1, 1, 1 Modules
| |||||||||||||||
| 2524 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4788 -s 900 | C:\Windows\SysWOW64\WerFault.exe | hl.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=3 --enable-main-frame-before-activation --renderer-client-id=12 --field-trial-handle=4972,i,2553263431546853081,9750059962783303180,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4944 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=3 --enable-main-frame-before-activation --renderer-client-id=15 --field-trial-handle=5772,i,2553263431546853081,9750059962783303180,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 4784 | "C:\WINDOWS\SysWOW64\cmd.exe" /c sc start HLMonitor && exit /b 0 | C:\Windows\SysWOW64\cmd.exe | CSLauncher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 426
Read events
24 310
Write events
103
Delete events
13
Modification events
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\CS1.6GameZip.zip | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (8524) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
61
Suspicious files
3 041
Text files
1 130
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RFfb8f6.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RFfb8f6.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SignalDB\LOG.old~RFfb906.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SignalDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RFfb906.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RFfb906.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RFfb8f6.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
438
DNS requests
185
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7088 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7760 | chrome.exe | GET | 200 | 142.250.186.46:80 | http://clients2.google.com/time/1/current?cup2key=8:4Mbum_vH6bL89bS0udAV5vamdBSWL_Mn5Yii5DvZA3w&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2616 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2616 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5484 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
644 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8824 | SIHClient.exe | GET | 200 | 23.53.113.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
9192 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzFkOTU2ODctM2JiNS00NDJhLTg2ZmEtYjM0ODZiM2YxNmVm/1.0.0.19_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
8824 | SIHClient.exe | GET | 200 | 23.53.113.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
9192 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzFkOTU2ODctM2JiNS00NDJhLTg2ZmEtYjM0ODZiM2YxNmVm/1.0.0.19_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4400 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5596 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7760 | chrome.exe | 142.250.181.234:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
7760 | chrome.exe | 142.250.186.46:80 | clients2.google.com | GOOGLE | US | whitelisted |
7760 | chrome.exe | 188.114.97.3:443 | csdownload.net | CLOUDFLARENET | NL | whitelisted |
7760 | chrome.exe | 173.194.76.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
7760 | chrome.exe | 142.250.186.98:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
7760 | chrome.exe | 142.250.184.226:443 | googleads.g.doubleclick.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
csdownload.net |
| unknown |
accounts.google.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
tpc.googlesyndication.com |
| whitelisted |
dh8azcl753e1e.cloudfront.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7760 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7760 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7760 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Possible Domain Associated with Malware Distribution (ukankingwithea .com) |
7760 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Possible Domain Associated with Malware Distribution (ghabovethec .info) |
7760 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Possible Malicious CrossDomain (highperformanceformat .com) |
7760 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
— | — | Attempted Information Leak | SUSPICIOUS [ANY.RUN] FingerprintJS Usage Observed in HTTP response |
— | — | Attempted Information Leak | SUSPICIOUS [ANY.RUN] FingerprintJS Usage Observed in HTTP response |
— | — | Attempted Information Leak | SUSPICIOUS [ANY.RUN] FingerprintJS Usage Observed in HTTP response |
— | — | Attempted Information Leak | SUSPICIOUS [ANY.RUN] FingerprintJS Usage Observed in HTTP response |
Process | Message |
|---|---|
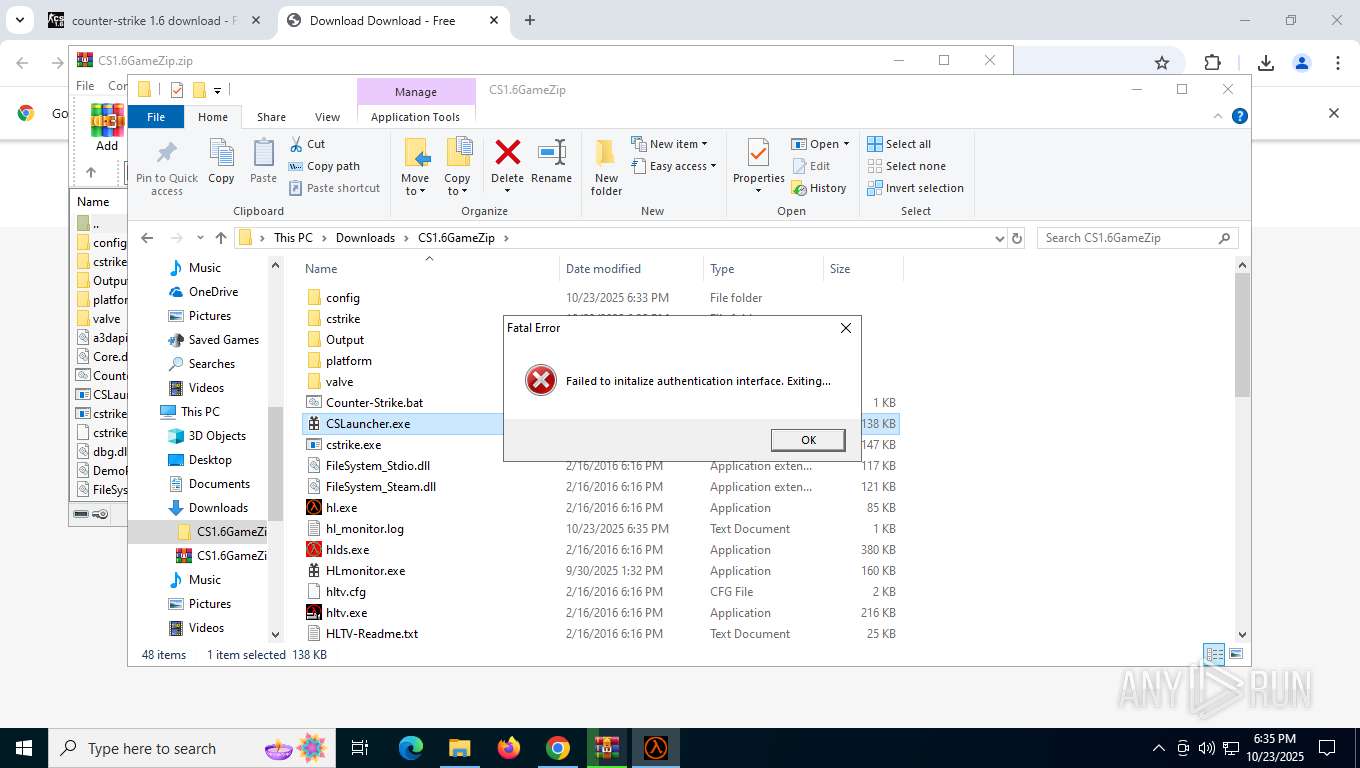
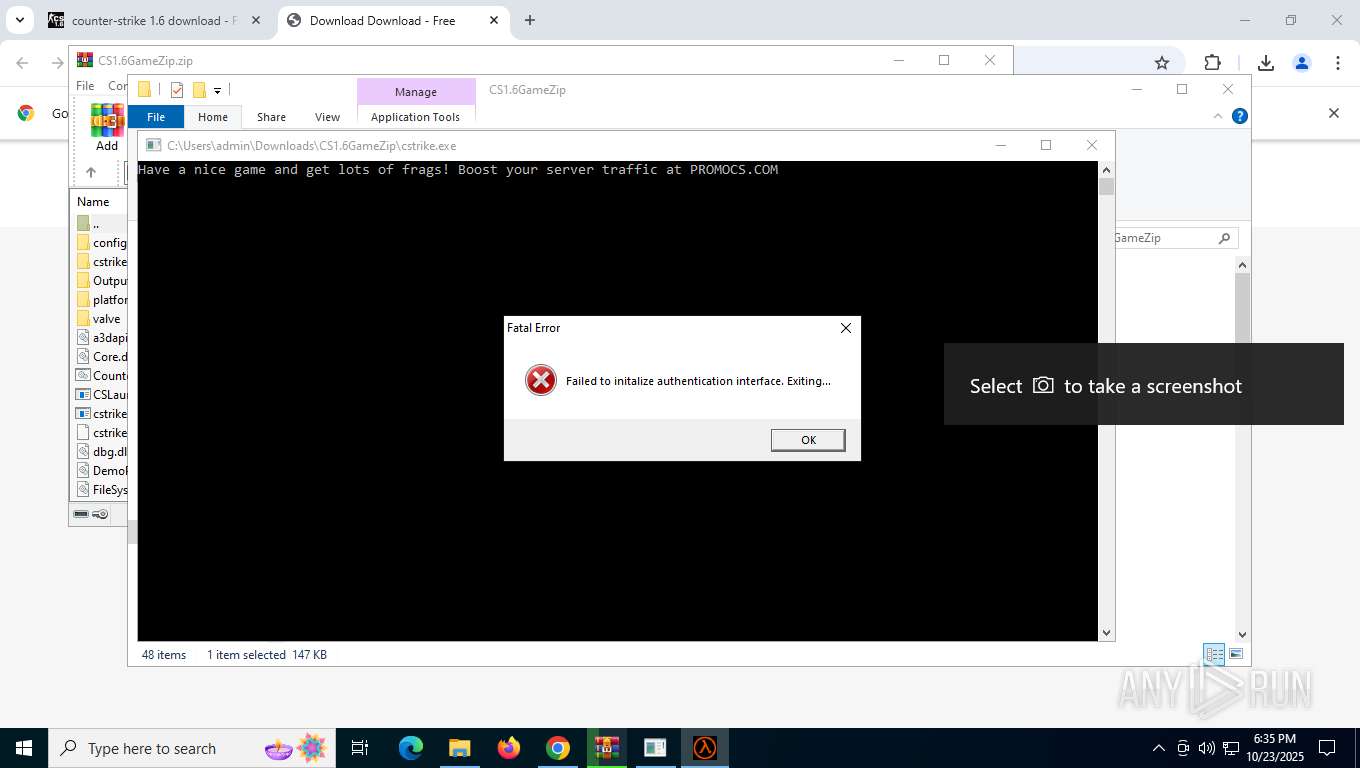
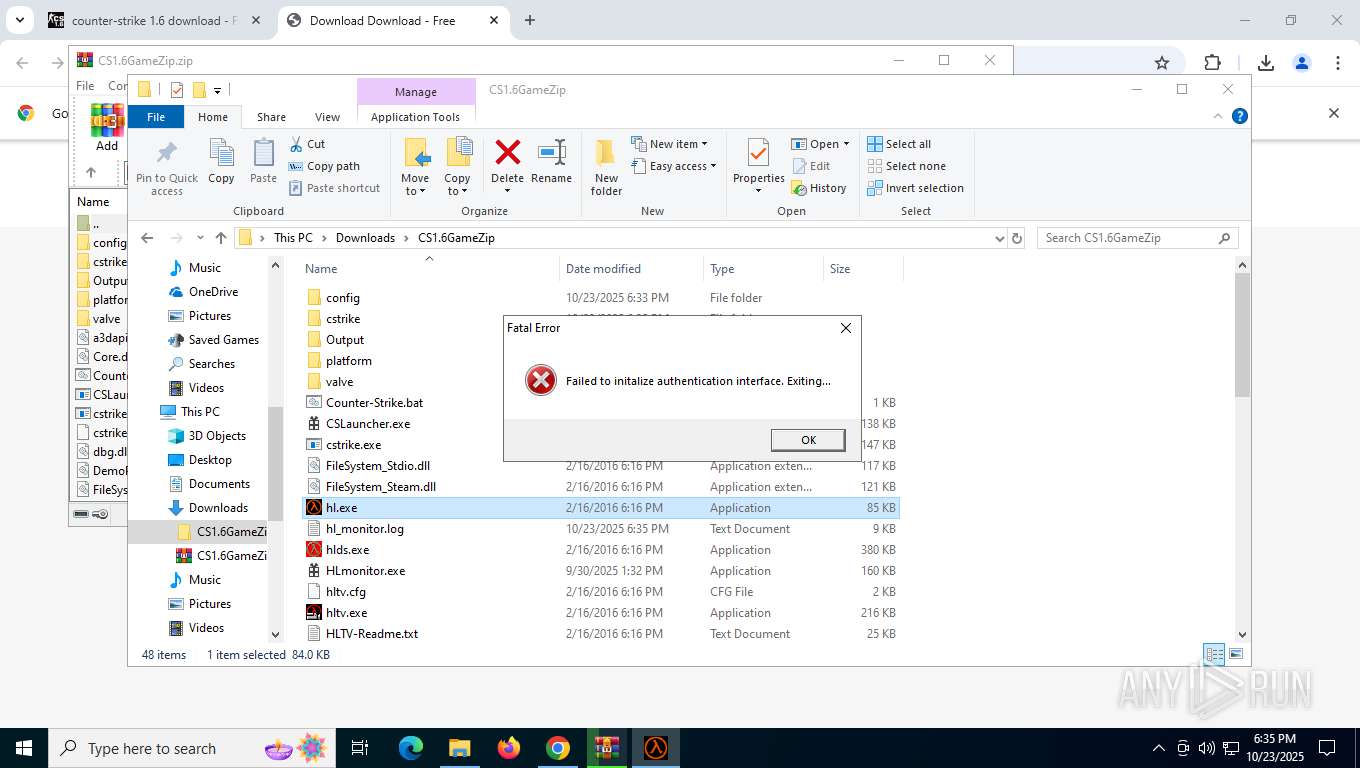
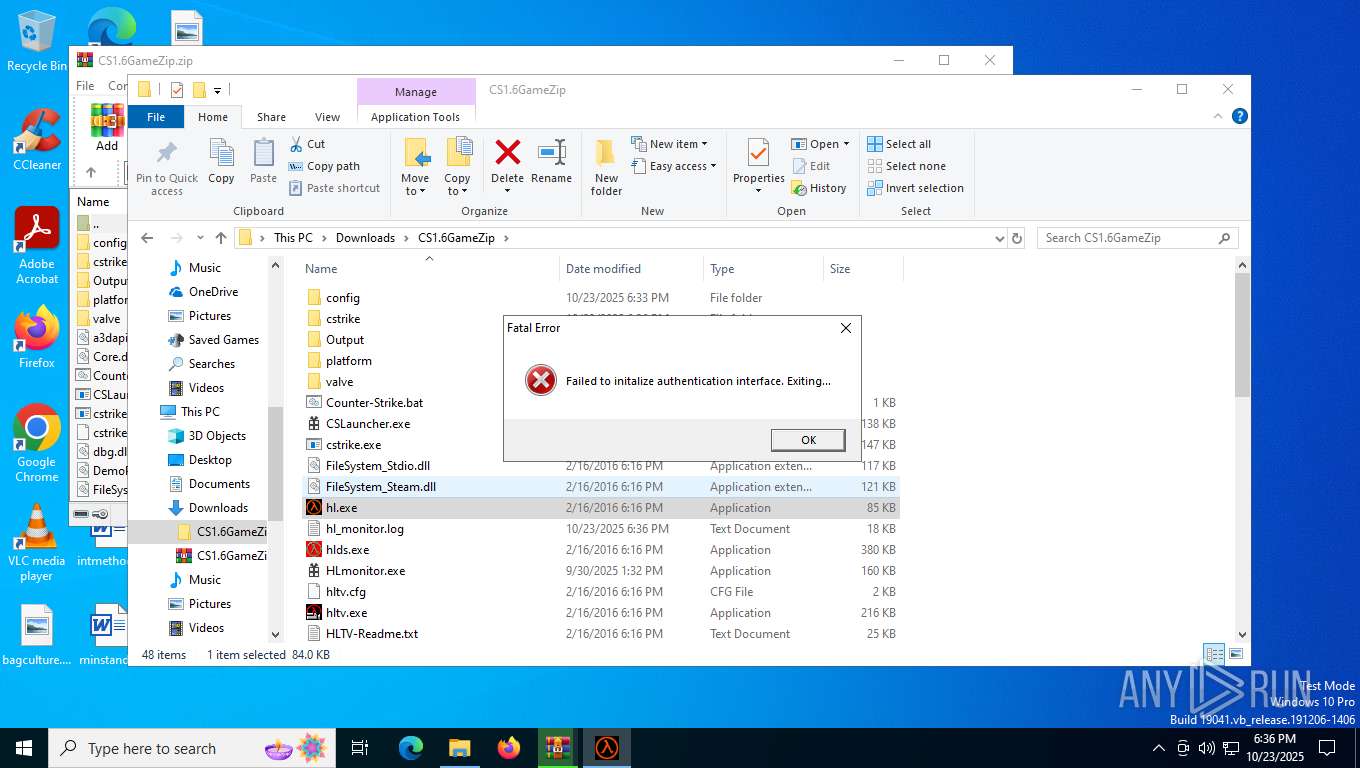
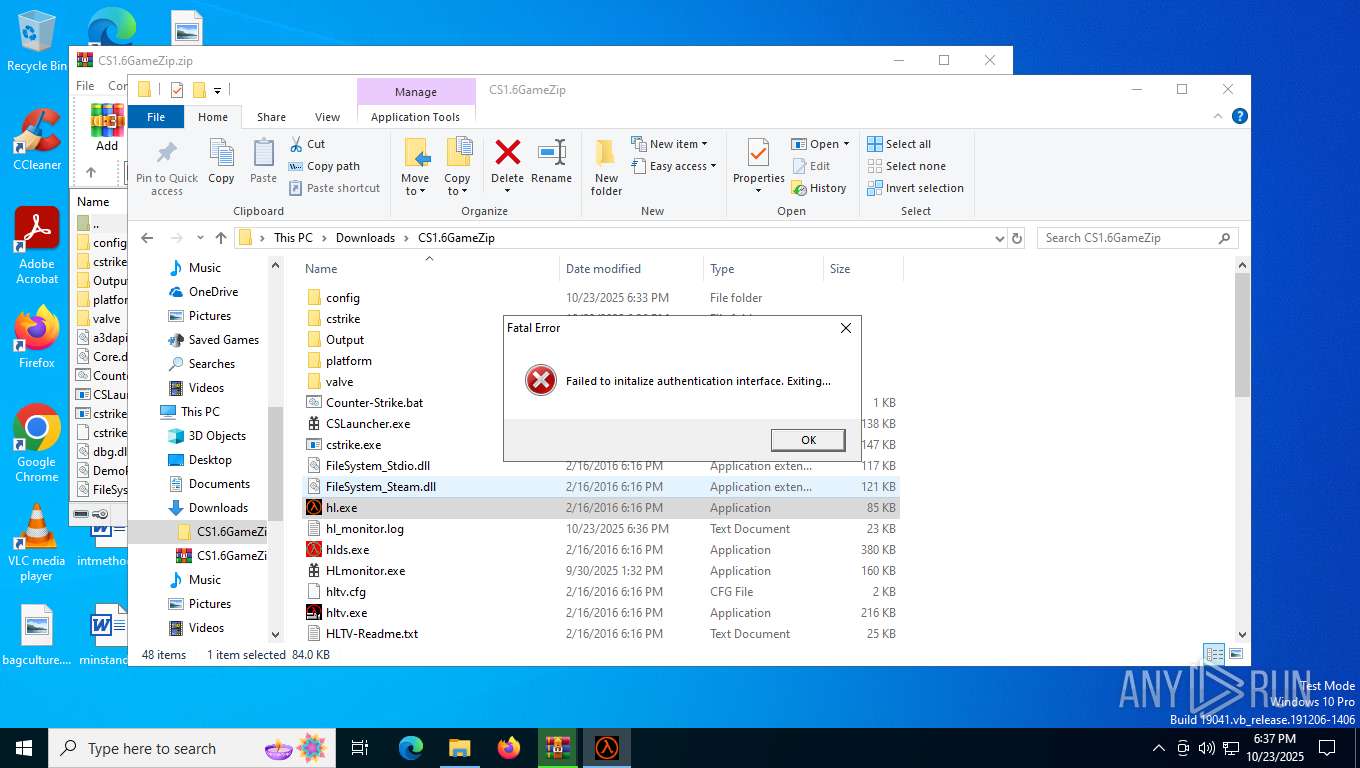
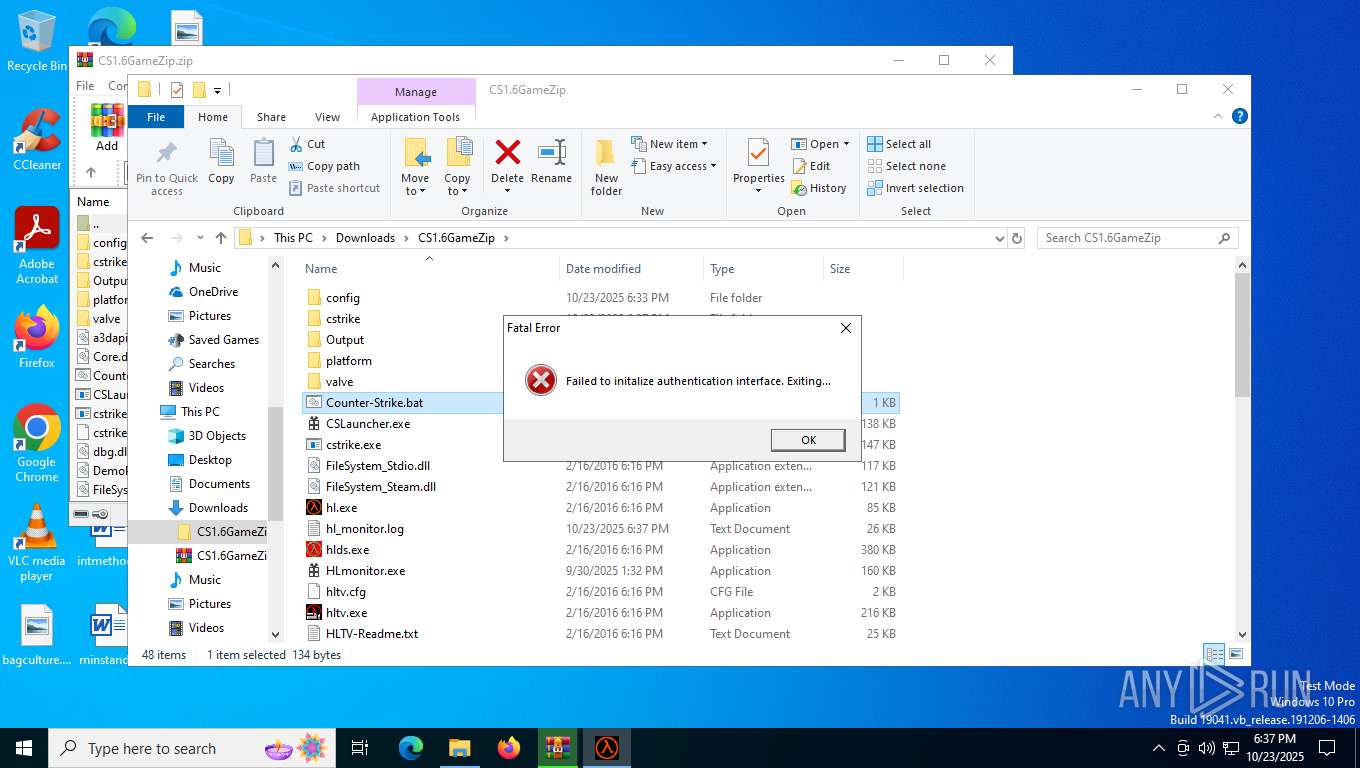
hl.exe | Failed to initalize authentication interface. Exiting...
|
hl.exe | [S_API FAIL] SteamAPI_Init() failed; unable to local a running instance of Steam, or a local steamclient.dll.
|
hl.exe | [S_API FAIL] SteamAPI_Init() failed; unable to local a running instance of Steam, or a local steamclient.dll.
|
hl.exe | Failed to initalize authentication interface. Exiting...
|
hl.exe | Failed to initalize authentication interface. Exiting...
|
hl.exe | [S_API FAIL] SteamAPI_Init() failed; unable to local a running instance of Steam, or a local steamclient.dll.
|
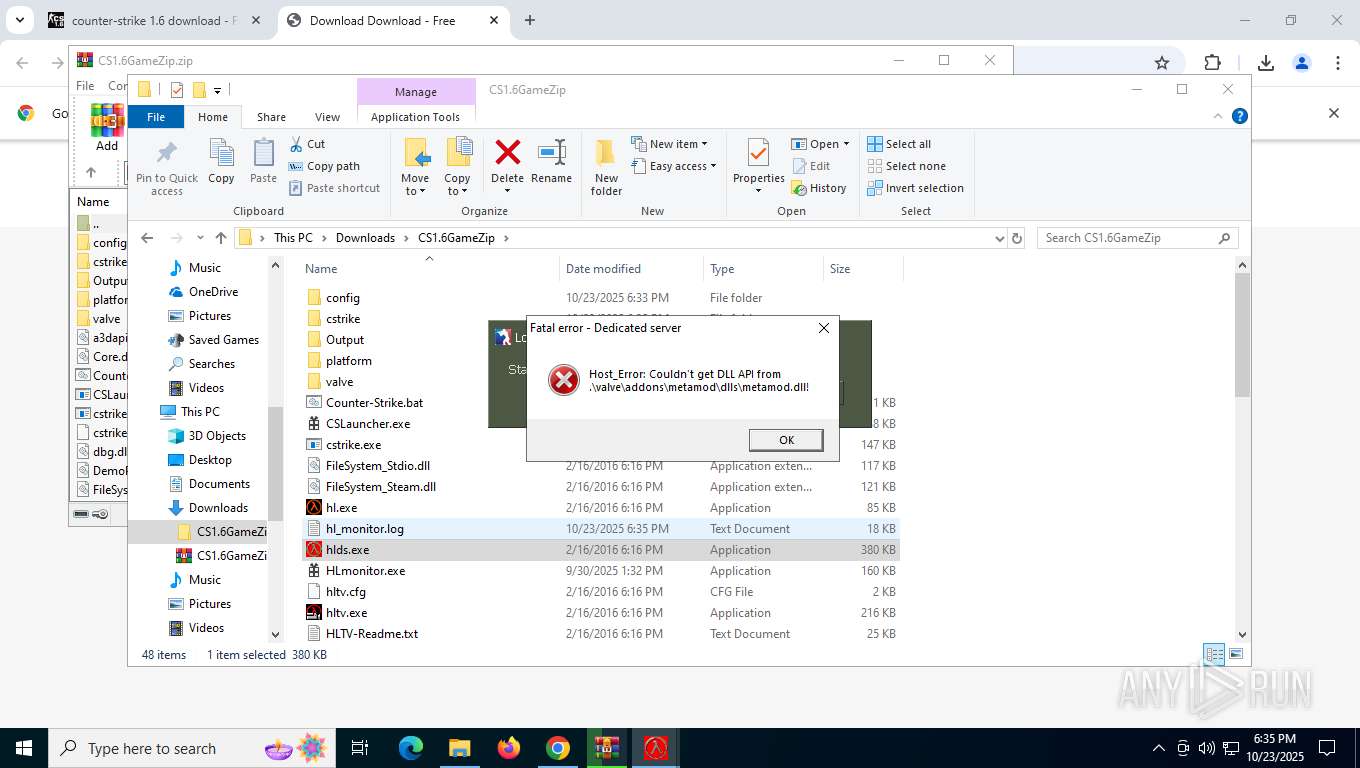
hlds.exe | LoadLibrary failed on .\valve\addons\metamod\dlls\metamod.dll (126)
|
hlds.exe | Host_Error: Couldn't get DLL API from .\valve\addons\metamod\dlls\metamod.dll!
|
hlds.exe | Exe build: 14:21:06 Mar 8 2010 (4554)
|
hlds.exe | Server IP address 192.168.100.5:27015
|