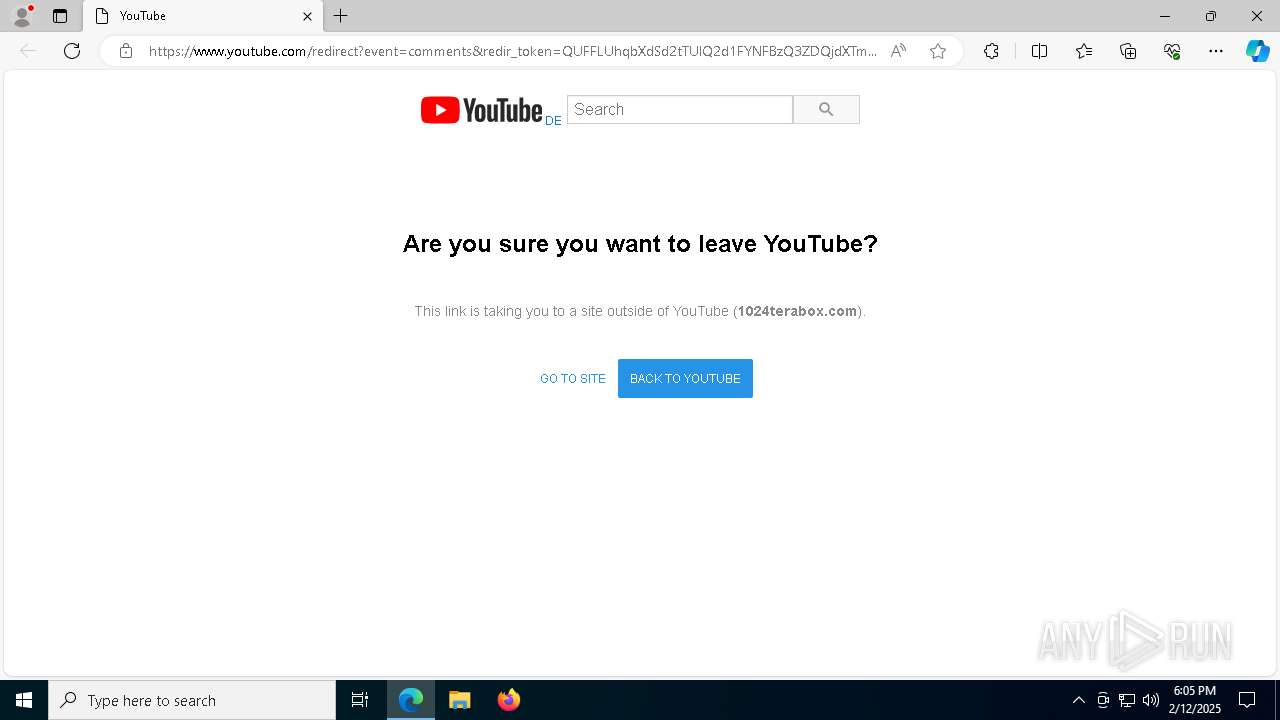
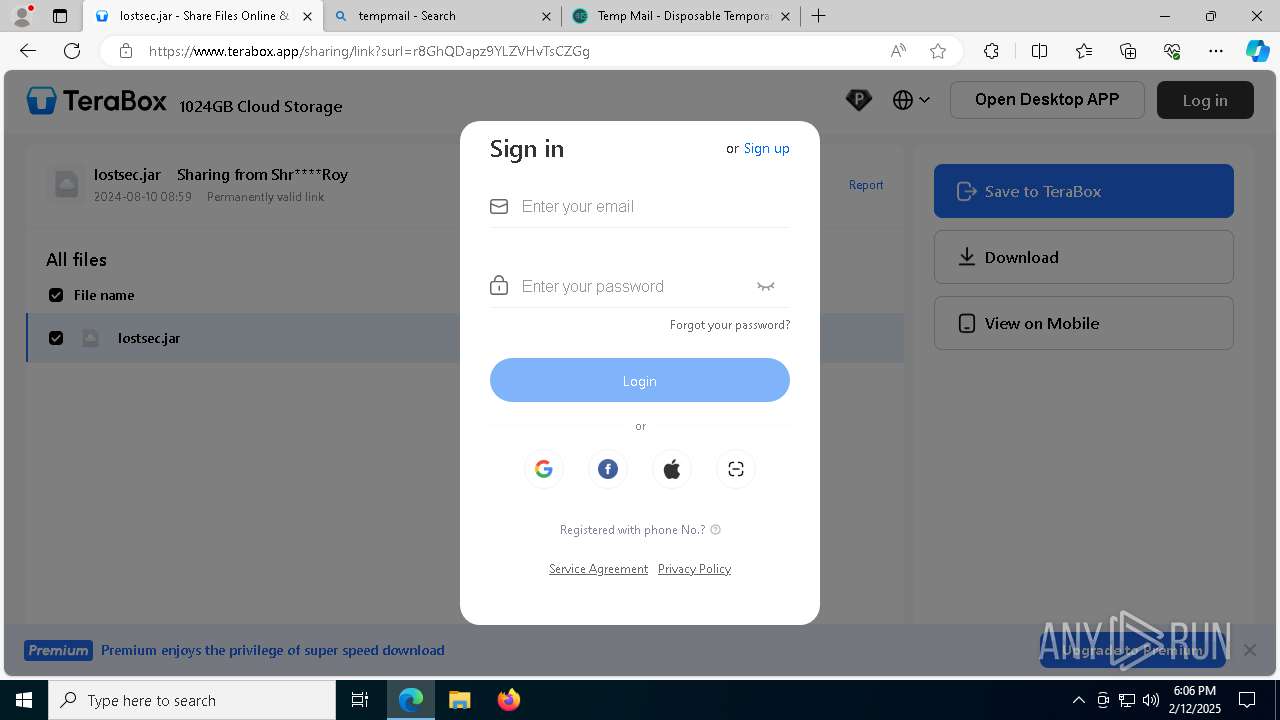
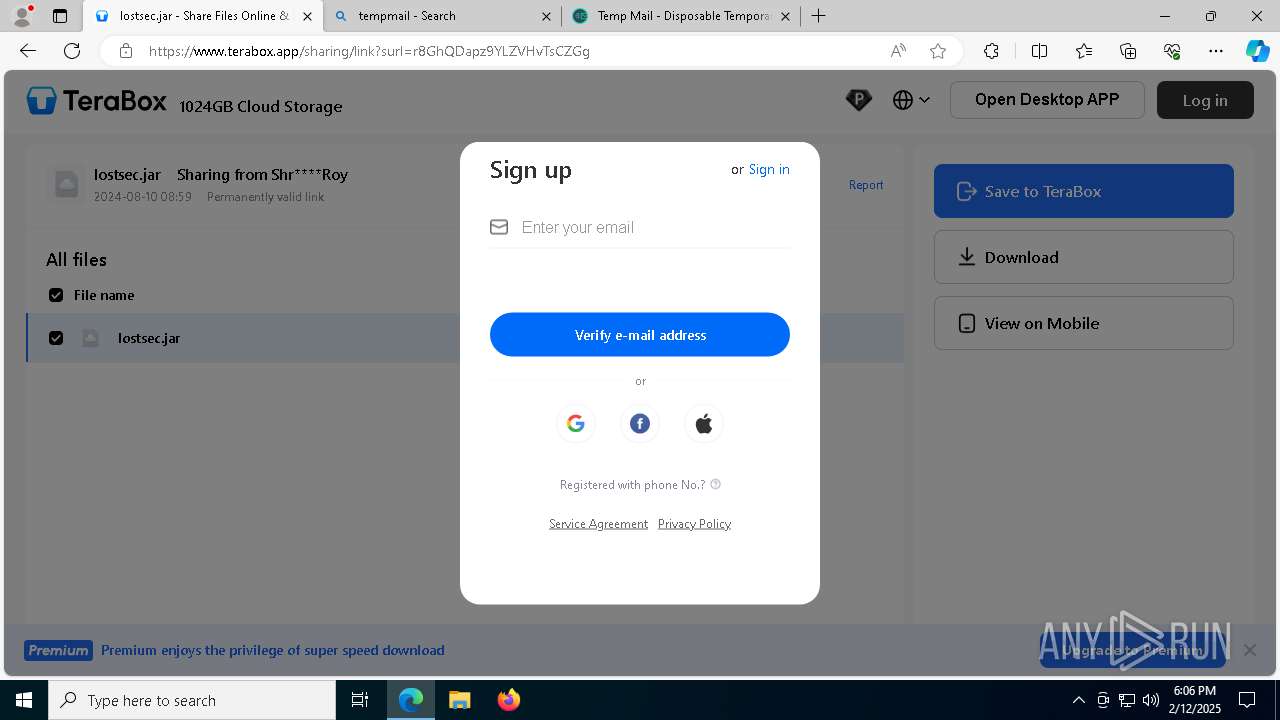
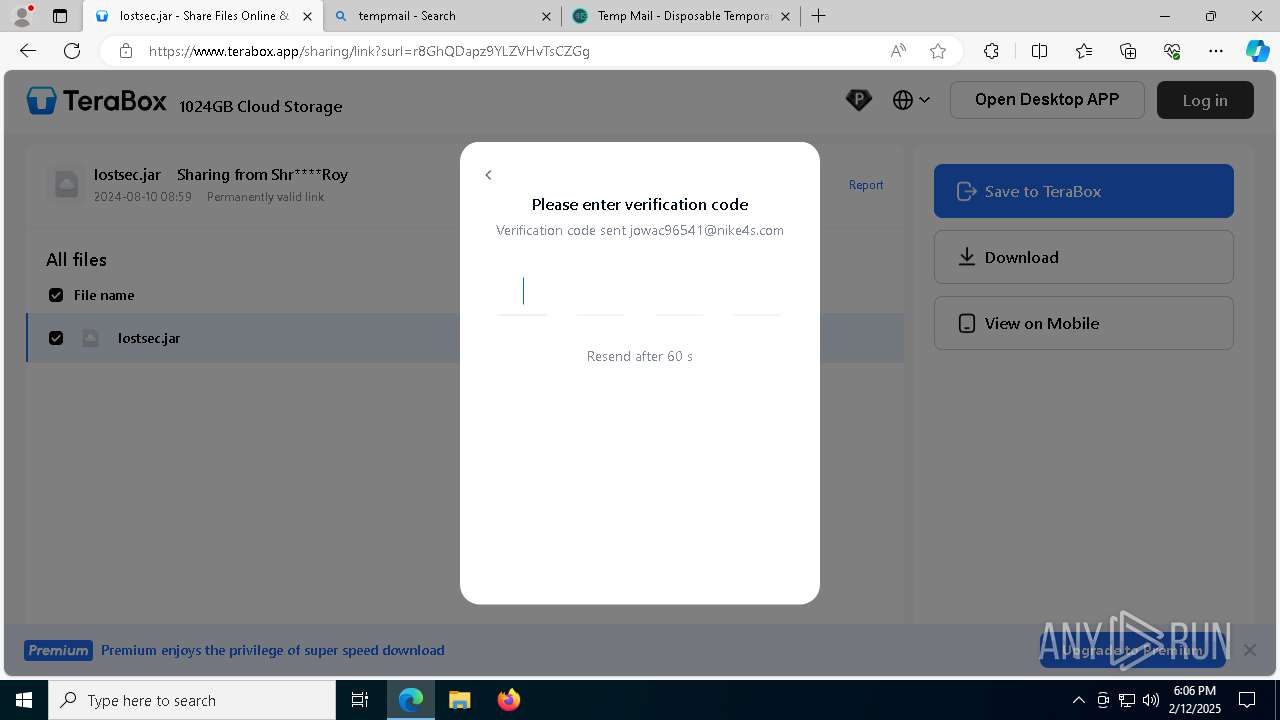
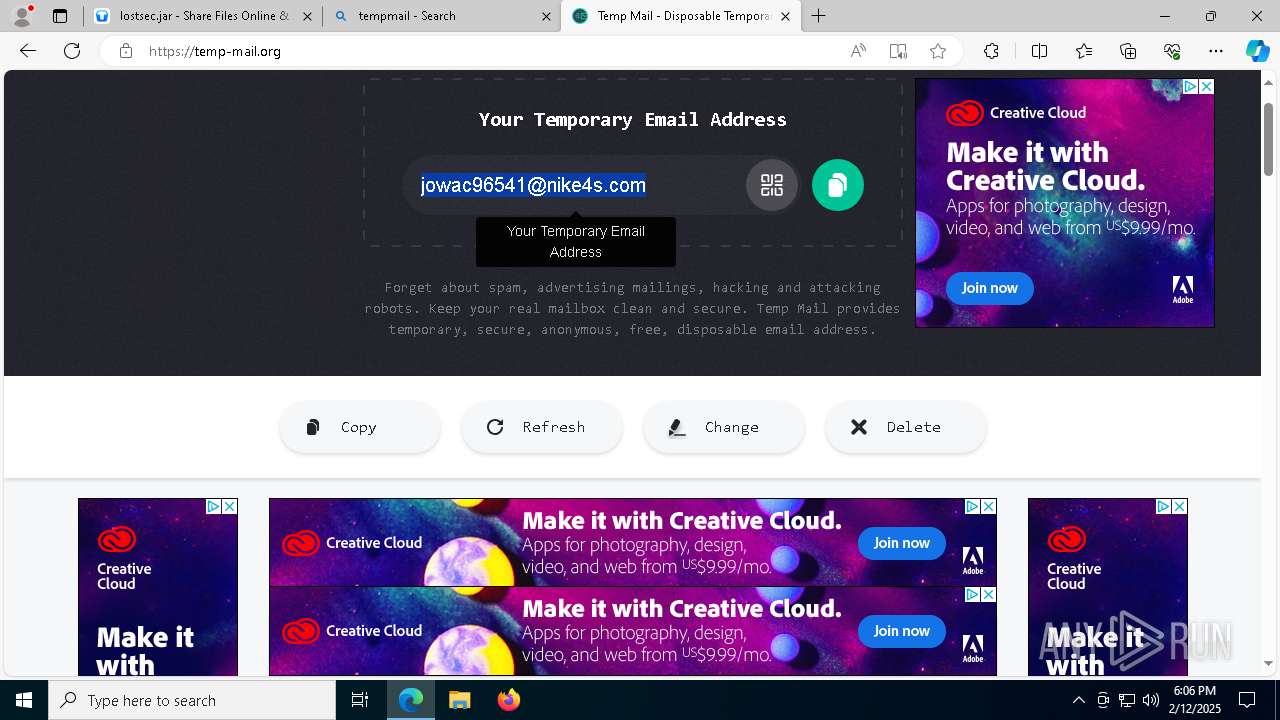
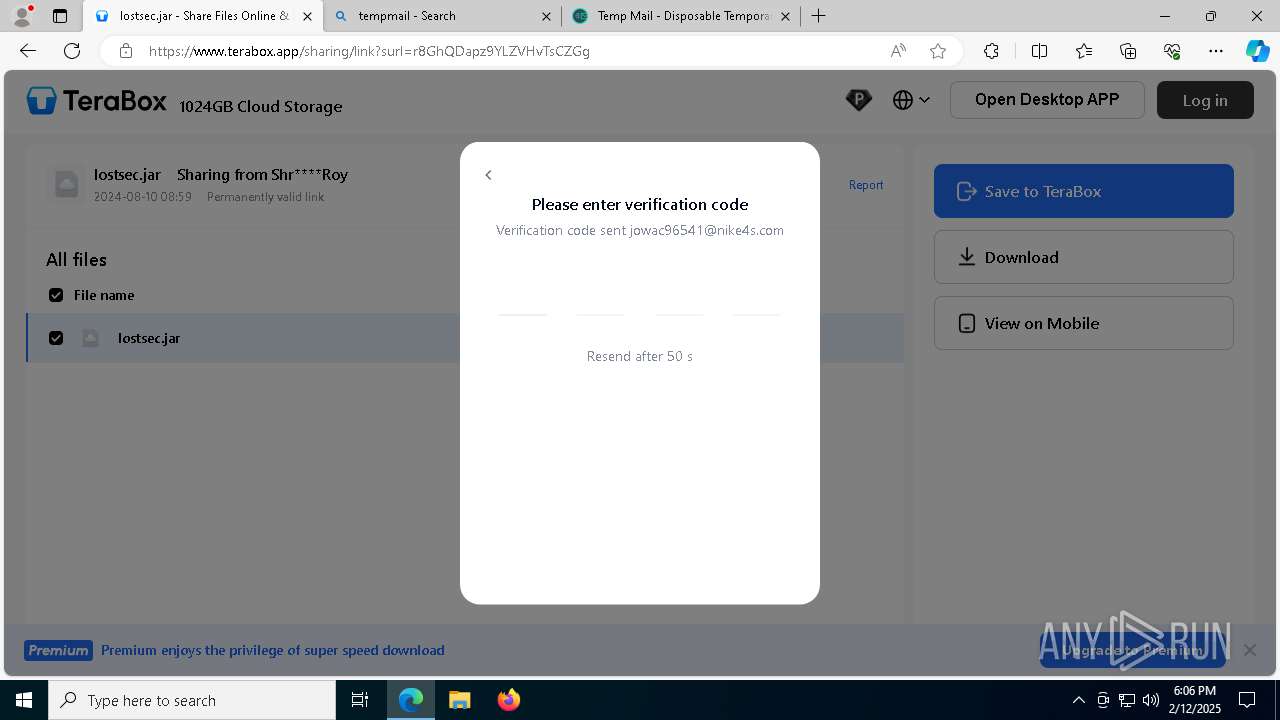
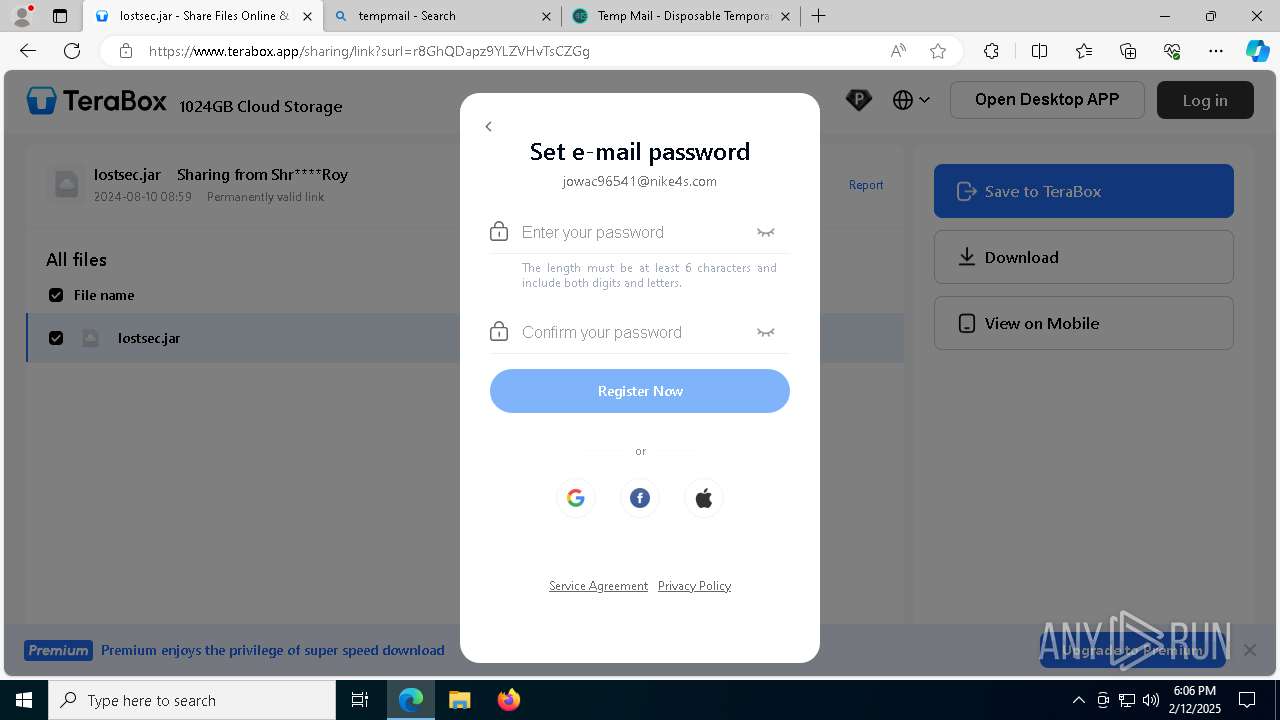
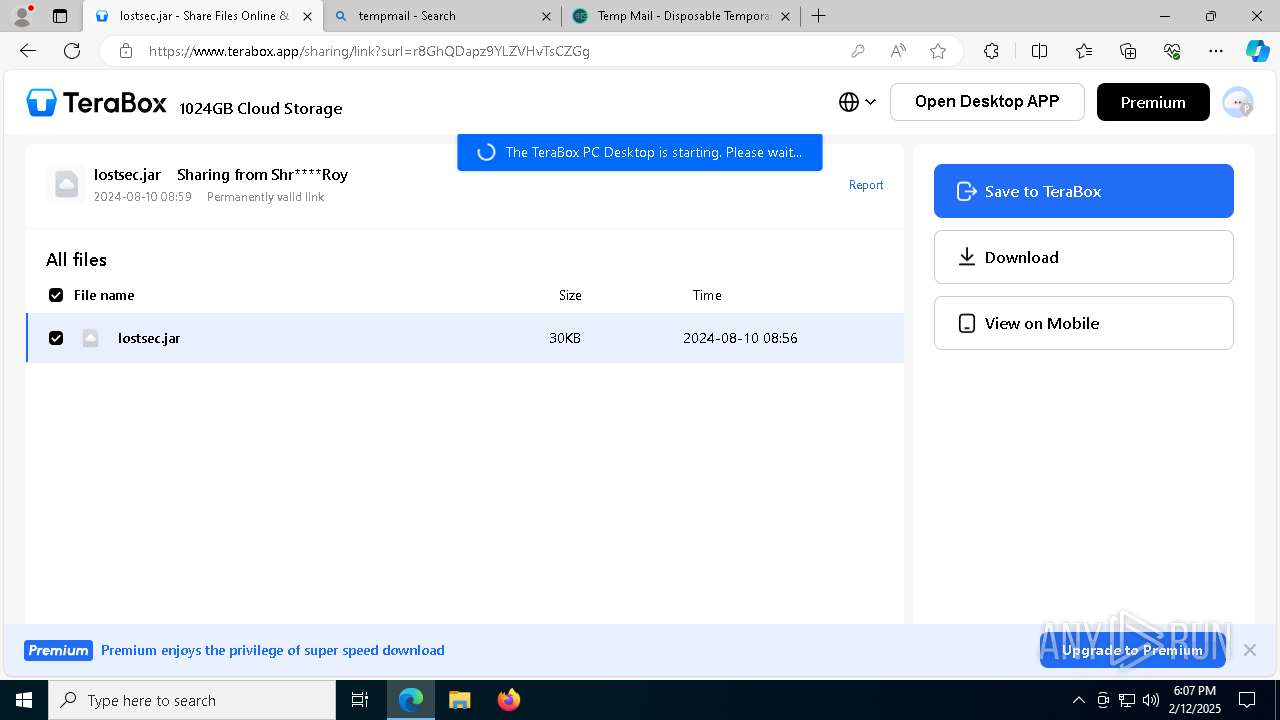
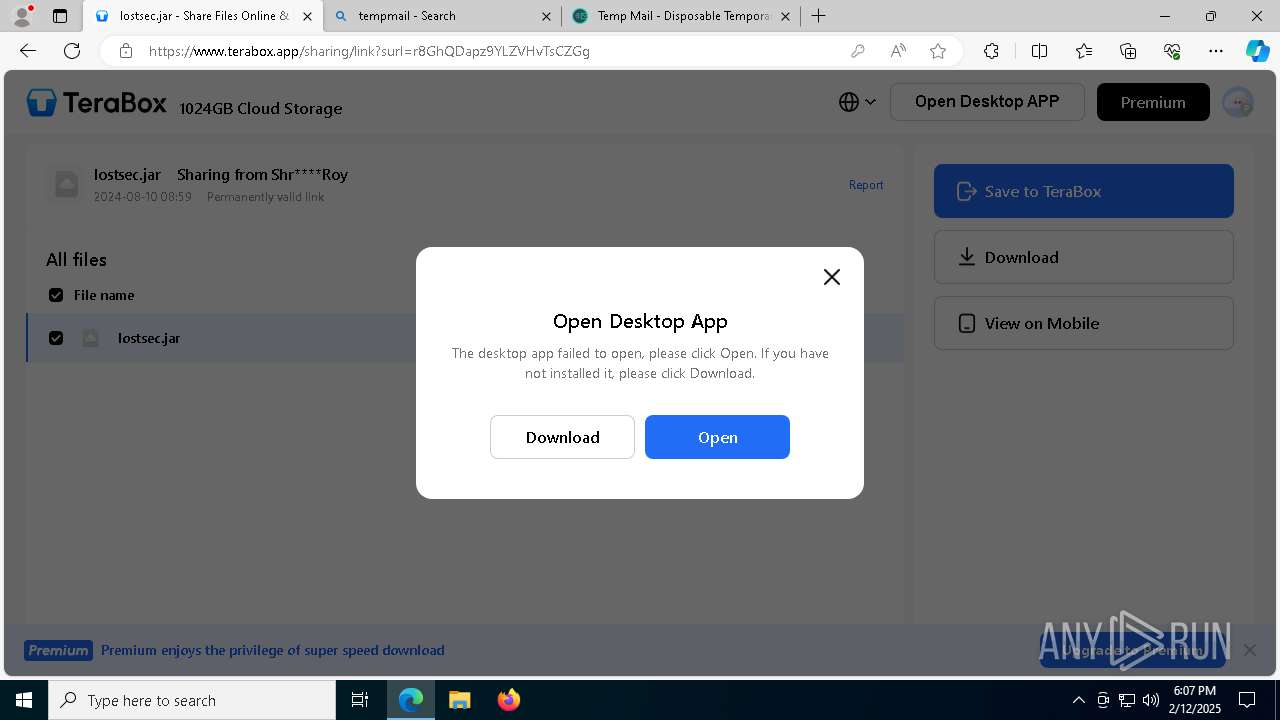
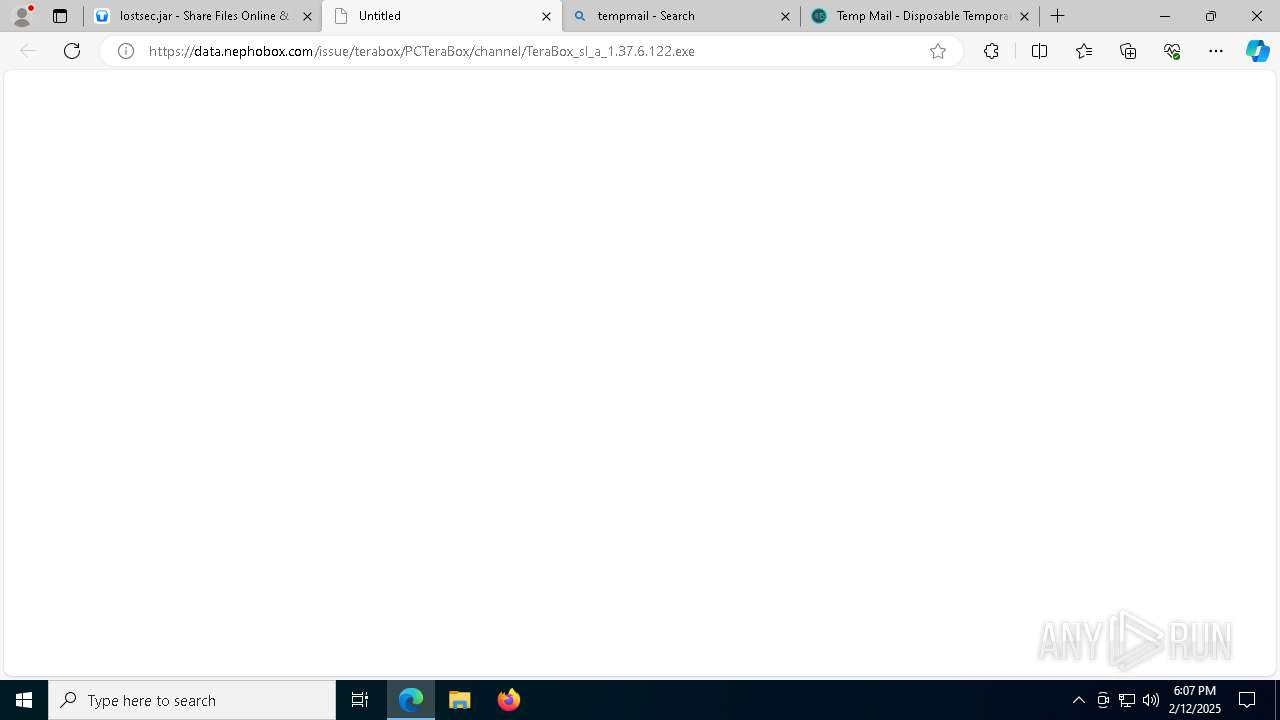
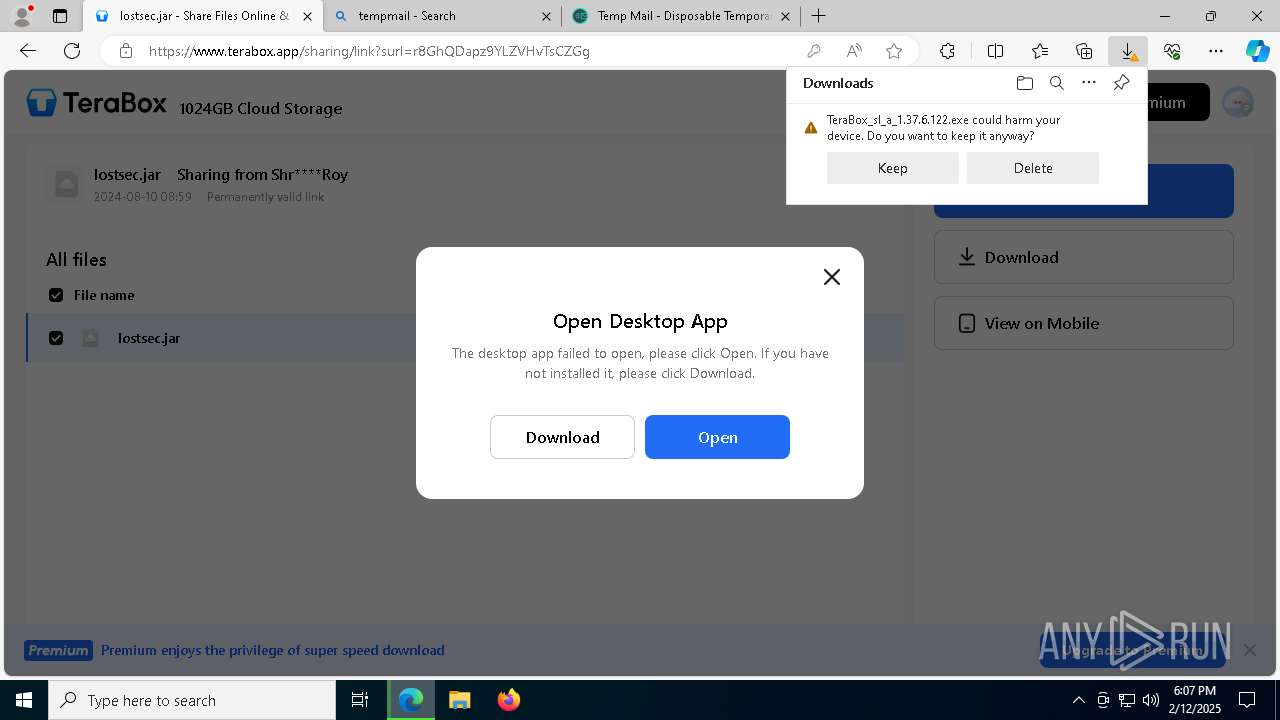
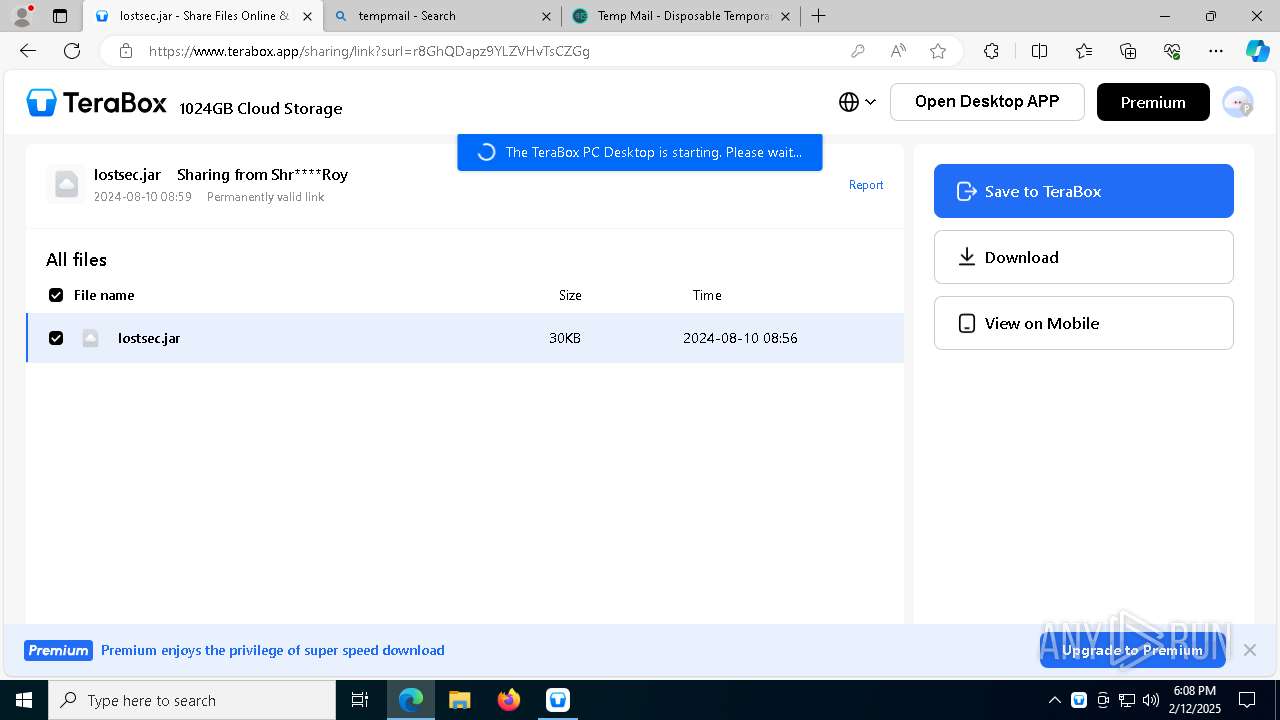
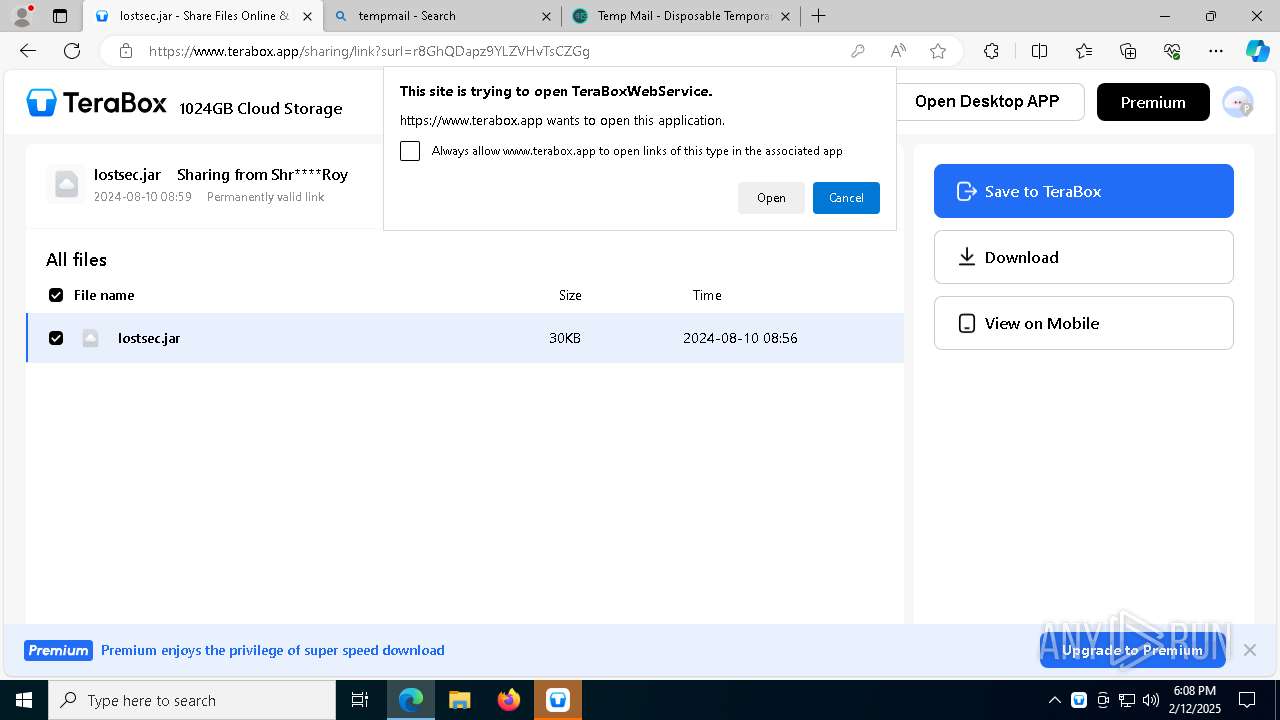
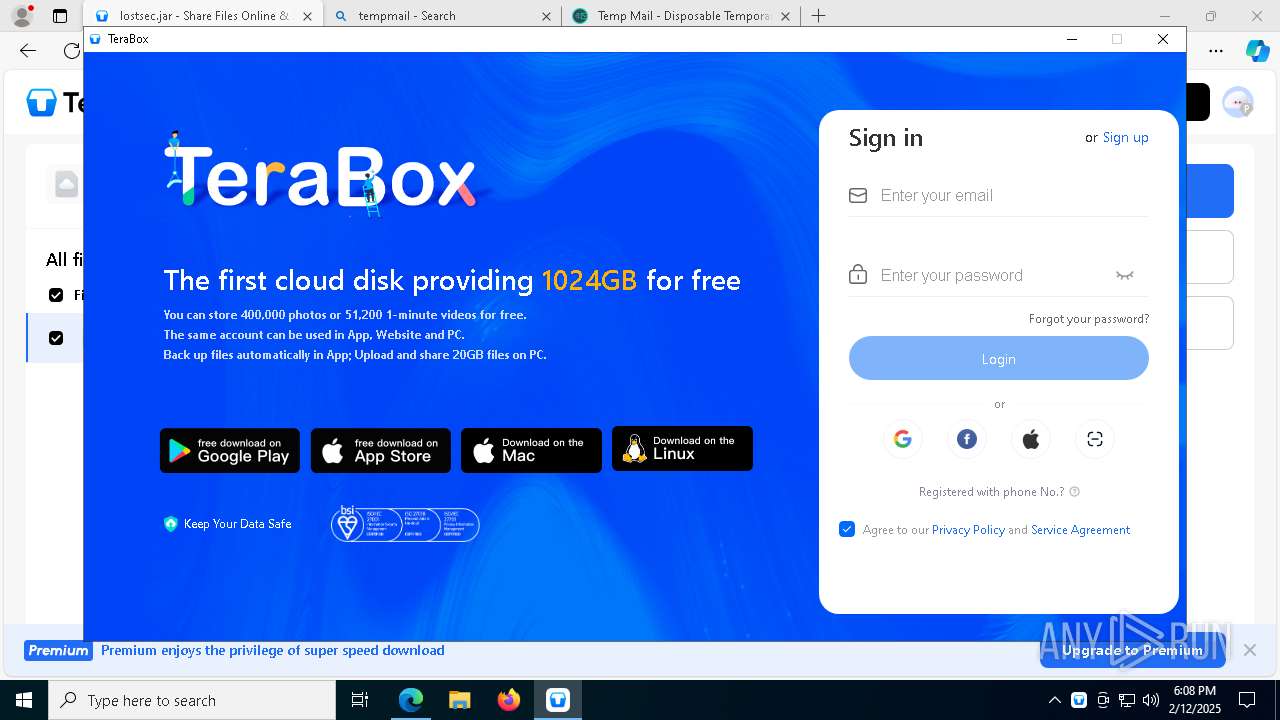
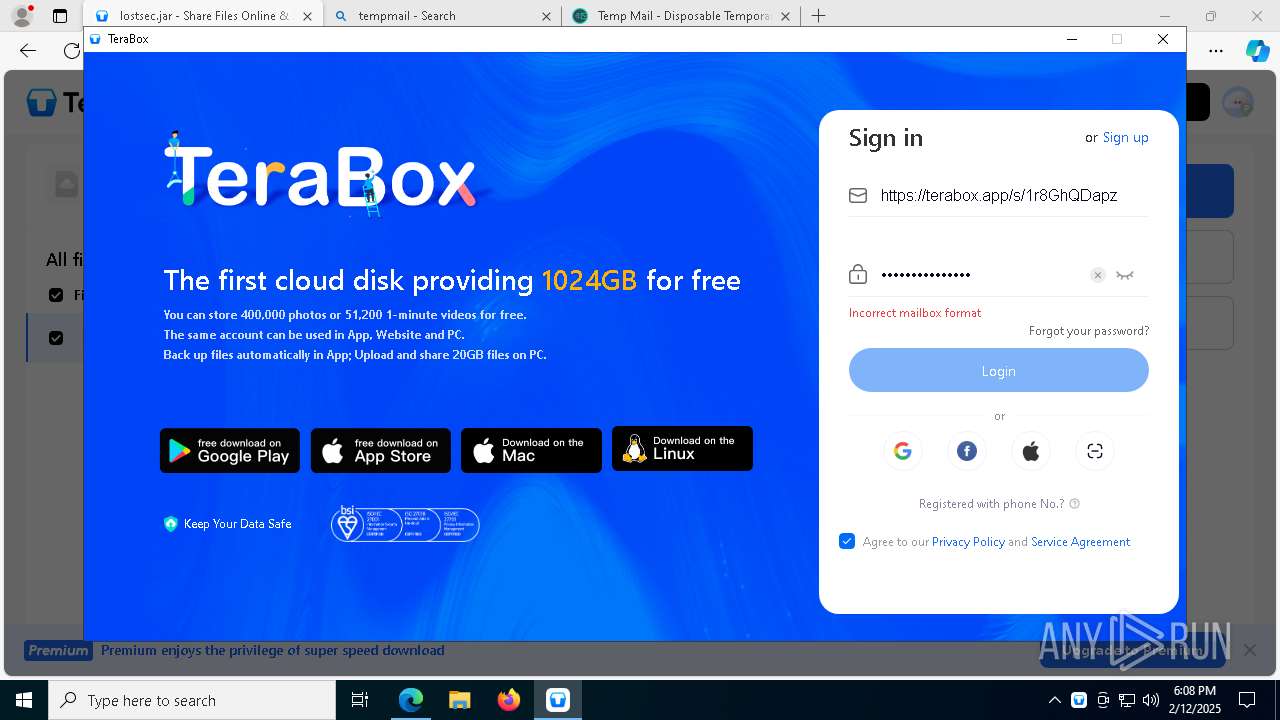
| URL: | https://www.youtube.com/redirect?event=comments&redir_token=QUFFLUhqbXdSd2tTUlQ2d1FYNFBzQ3ZDQjdXTm51MWhrZ3xBQ3Jtc0tsSUFyLWg3VXR1MEwzWEk0NlE1eGxiXzV6SjZfc1g4eHY4RFBpdExZYTUyeEh1SjF0RFlyVlMzcWVOenF3RzdXUlFRUllFWEFxeEhzRzJjazM2NEExdThUUnZaaGM2d2pDZzVmODRPeUhZM3l6N1JnTQ&q=https%3A%2F%2F1024terabox.com%2Fs%2F1r8GhQDapz9YLZVHvTsCZGg |
| Full analysis: | https://app.any.run/tasks/fc25ea17-138c-4a29-a551-6c52e968c5f2 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 18:05:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 66FB457B23CC5AB2DBED020E92D3AB34 |
| SHA1: | C3B96E32C4B4F3D64213C61807566DB8F1E16A99 |
| SHA256: | E2E819861204CC4A1F336F7F58F24935A6E58E5701F5C89320D533A2D39DCDC5 |
| SSDEEP: | 6:2OLUxGKmquxZqZPq1+HfDKBWUV6vjfxn0kVddrN33zWRFmRn:2jGRPPqruB1I7fxPppn6Yn |
MALICIOUS
Changes the autorun value in the registry
- TeraBox.exe (PID: 1016)
Registers / Runs the DLL via REGSVR32.EXE
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
SUSPICIOUS
The process creates files with name similar to system file names
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
Executable content was dropped or overwritten
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
- TeraBoxUnite.exe (PID: 8824)
- TeraBoxUnite.exe (PID: 7172)
Process drops legitimate windows executable
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
The process drops C-runtime libraries
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
Creates a software uninstall entry
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 4388)
- regsvr32.exe (PID: 8628)
- regsvr32.exe (PID: 6440)
Reads security settings of Internet Explorer
- TeraBoxWebService.exe (PID: 3060)
- TeraBox.exe (PID: 7196)
- TeraBoxUnite.exe (PID: 8824)
- Autoupdate.exe (PID: 9524)
Checks Windows Trust Settings
- TeraBox.exe (PID: 7196)
- Autoupdate.exe (PID: 9524)
Malware-specific behavior (creating "System.dll" in Temp)
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
Application launched itself
- TeraBoxUnite.exe (PID: 8824)
The process checks if it is being run in the virtual environment
- TeraBoxUnite.exe (PID: 8824)
INFO
Reads the computer name
- identity_helper.exe (PID: 7568)
- TeraBox.exe (PID: 1016)
- TeraBox.exe (PID: 7196)
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
- TeraBoxWebService.exe (PID: 3060)
- TeraBoxUnite.exe (PID: 8824)
- TeraBoxUnite.exe (PID: 8828)
- TeraBoxUnite.exe (PID: 1228)
- Autoupdate.exe (PID: 9524)
- TeraBoxHost.exe (PID: 9628)
- TeraBoxHost.exe (PID: 9728)
Checks supported languages
- identity_helper.exe (PID: 7568)
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
- TeraBox.exe (PID: 1016)
- TeraBoxWebService.exe (PID: 3060)
- TeraBoxUnite.exe (PID: 8828)
- TeraBoxWebService.exe (PID: 9048)
- TeraBox.exe (PID: 7196)
- TeraBoxUnite.exe (PID: 1228)
- TeraBoxUnite.exe (PID: 8824)
- TeraBoxUnite.exe (PID: 5008)
- TeraBoxUnite.exe (PID: 7172)
- TeraBoxUnite.exe (PID: 644)
- TeraBoxUnite.exe (PID: 7596)
- Autoupdate.exe (PID: 9524)
- TeraBoxHost.exe (PID: 9628)
- crashpad_handler.exe (PID: 9668)
- TeraBoxHost.exe (PID: 9728)
- TeraBoxUnite.exe (PID: 9816)
- TeraBoxWebService.exe (PID: 8804)
- TeraBoxUnite.exe (PID: 6464)
- TeraBoxUnite.exe (PID: 9324)
- crashpad_handler.exe (PID: 10040)
Executable content was dropped or overwritten
- msedge.exe (PID: 6328)
- msedge.exe (PID: 9892)
Creates files or folders in the user directory
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
- TeraBox.exe (PID: 1016)
- TeraBoxWebService.exe (PID: 3060)
- TeraBox.exe (PID: 7196)
- TeraBoxUnite.exe (PID: 8824)
- Autoupdate.exe (PID: 9524)
- TeraBoxHost.exe (PID: 9628)
- crashpad_handler.exe (PID: 9668)
- TeraBoxUnite.exe (PID: 7172)
- TeraBoxHost.exe (PID: 9728)
Create files in a temporary directory
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
- TeraBoxUnite.exe (PID: 8824)
- TeraBoxUnite.exe (PID: 1228)
- TeraBoxUnite.exe (PID: 7172)
Reads Environment values
- identity_helper.exe (PID: 7568)
The sample compiled with english language support
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
- msedge.exe (PID: 9892)
The sample compiled with chinese language support
- TeraBox_sl_a_1.37.6.122.exe (PID: 6272)
Reads the machine GUID from the registry
- TeraBox.exe (PID: 7196)
- TeraBoxUnite.exe (PID: 8824)
- Autoupdate.exe (PID: 9524)
- TeraBoxHost.exe (PID: 9728)
Checks proxy server information
- TeraBoxWebService.exe (PID: 3060)
- TeraBox.exe (PID: 7196)
- TeraBoxUnite.exe (PID: 8824)
- Autoupdate.exe (PID: 9524)
Reads the software policy settings
- TeraBox.exe (PID: 7196)
- TeraBoxUnite.exe (PID: 8824)
- Autoupdate.exe (PID: 9524)
Application launched itself
- msedge.exe (PID: 6328)
Process checks computer location settings
- TeraBoxUnite.exe (PID: 5008)
- TeraBoxUnite.exe (PID: 7172)
- TeraBoxUnite.exe (PID: 644)
- TeraBoxUnite.exe (PID: 7596)
- TeraBoxUnite.exe (PID: 9816)
- TeraBoxUnite.exe (PID: 8824)
- TeraBoxUnite.exe (PID: 6464)
- TeraBoxUnite.exe (PID: 9324)
Node.js compiler has been detected
- TeraBoxUnite.exe (PID: 8824)
Creates files in the program directory
- TeraBoxHost.exe (PID: 9728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
281
Monitored processes
139
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\WINDOWS\system32\regsvr32.exe" "/s" "C:\Users\admin\AppData\Roaming\TeraBox\YunOfficeAddin64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | TeraBox_sl_a_1.37.6.122.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\TeraBox\cache" --app-user-model-id=electron.app.TeraBoxUnite --app-path="C:\Users\admin\AppData\Roaming\TeraBox\resources\app.asar" --enable-sandbox --enable-blink-features --disable-blink-features --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3212 --field-trial-handle=1888,i,8153145641228589348,11014478286786438433,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe | — | TeraBoxUnite.exe | |||||||||||
User: admin Company: Flextech Integrity Level: LOW Description: TeraBoxUnite Exit code: 0 Version: 1.37.6.122 | |||||||||||||||
| 648 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=54 --mojo-platform-channel-handle=8692 --field-trial-handle=2344,i,15699850092751081172,9723568420492605108,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1016 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe" -install "createdetectstartup" -install "createshortcut" "0" -install "createstartup" | C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe | TeraBox_sl_a_1.37.6.122.exe | ||||||||||||
User: admin Company: Flextech Inc. Integrity Level: HIGH Exit code: 0 Version: 1.37.6.122 Modules
| |||||||||||||||
| 1216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5988 --field-trial-handle=2344,i,15699850092751081172,9723568420492605108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Local\Temp\TeraBox\cache" --mojo-platform-channel-handle=2116 --field-trial-handle=1888,i,8153145641228589348,11014478286786438433,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe | TeraBoxUnite.exe | ||||||||||||
User: admin Company: Flextech Integrity Level: MEDIUM Description: TeraBoxUnite Version: 1.37.6.122 Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=98 --mojo-platform-channel-handle=7748 --field-trial-handle=2344,i,15699850092751081172,9723568420492605108,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=10296 --field-trial-handle=2344,i,15699850092751081172,9723568420492605108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1688 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6860 --field-trial-handle=2344,i,15699850092751081172,9723568420492605108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1796 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=49 --mojo-platform-channel-handle=8516 --field-trial-handle=2344,i,15699850092751081172,9723568420492605108,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
24 739
Read events
24 479
Write events
197
Delete events
63
Modification events
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 9967B9108C8C2F00 | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5A00CB108C8C2F00 | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656082 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5CAE645A-6962-4246-A9F6-7CC5F1D655DE} | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656082 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7DDC9686-DAE6-4DC1-A607-A296512B34C2} | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656082 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {784A5195-E19B-44CB-9394-5F2A065FFC1C} | |||
| (PID) Process: | (6328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656082 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {61093344-92FE-49ED-A010-7345999120AD} | |||
Executable files
148
Suspicious files
1 602
Text files
192
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135874.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135883.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135883.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135883.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF135893.TMP | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
813
DNS requests
984
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
536 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8676 | svchost.exe | HEAD | 200 | 217.20.57.36:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6ca9004c-2afd-40c0-a9b1-4fec460952e5?P1=1739810276&P2=404&P3=2&P4=OI2VbadgY%2f9lkaOIU7g6xiTklPPyqX4ldpdP65OajPuzvwt7DC%2bHyaQuKAH7UgS8d3EA27gjUdwBBDUc29nULg%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7148 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6444 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7148 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6764 | msedge.exe | GET | 304 | 104.76.201.34:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
8676 | svchost.exe | GET | 206 | 217.20.57.36:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6ca9004c-2afd-40c0-a9b1-4fec460952e5?P1=1739810276&P2=404&P3=2&P4=OI2VbadgY%2f9lkaOIU7g6xiTklPPyqX4ldpdP65OajPuzvwt7DC%2bHyaQuKAH7UgS8d3EA27gjUdwBBDUc29nULg%3d%3d | unknown | — | — | whitelisted |
6764 | msedge.exe | GET | 304 | 104.76.201.34:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
8676 | svchost.exe | GET | 206 | 217.20.57.36:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6ca9004c-2afd-40c0-a9b1-4fec460952e5?P1=1739810276&P2=404&P3=2&P4=OI2VbadgY%2f9lkaOIU7g6xiTklPPyqX4ldpdP65OajPuzvwt7DC%2bHyaQuKAH7UgS8d3EA27gjUdwBBDUc29nULg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 23.15.178.184:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
536 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
536 | svchost.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6764 | msedge.exe | 142.250.186.174:443 | www.youtube.com | GOOGLE | US | whitelisted |
6328 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
www.youtube.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6764 | msedge.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |
6764 | msedge.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |