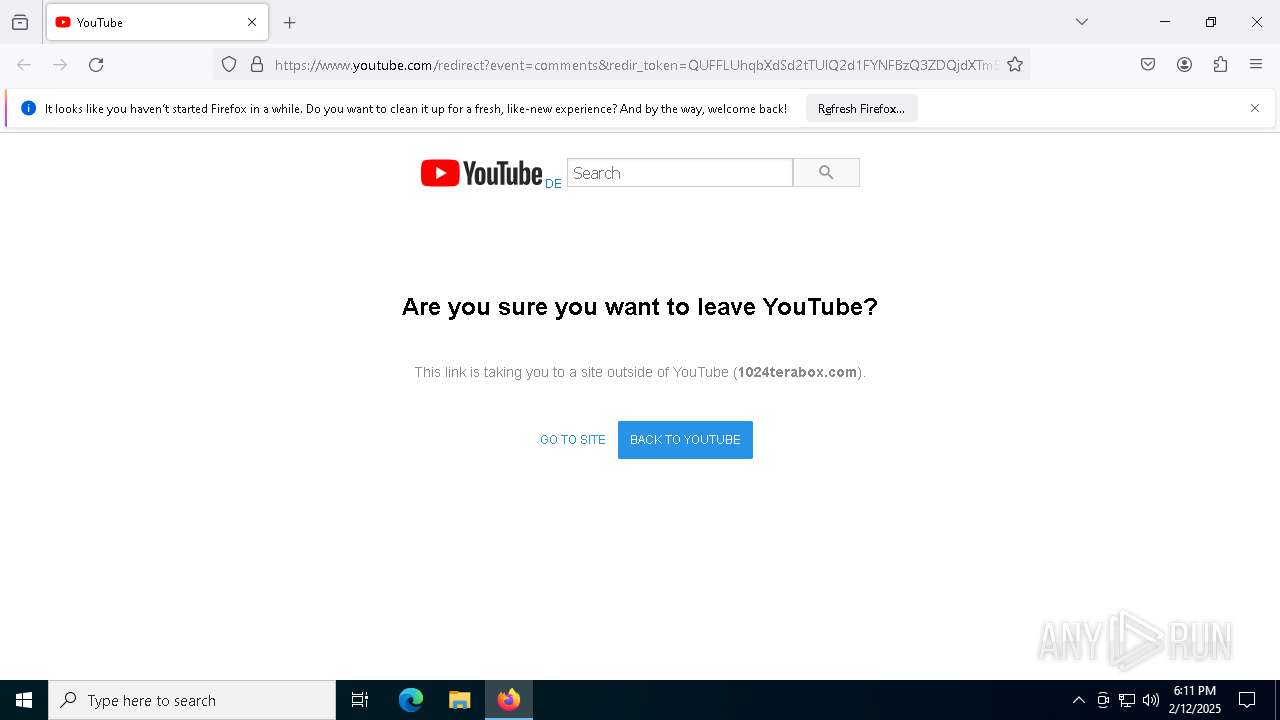
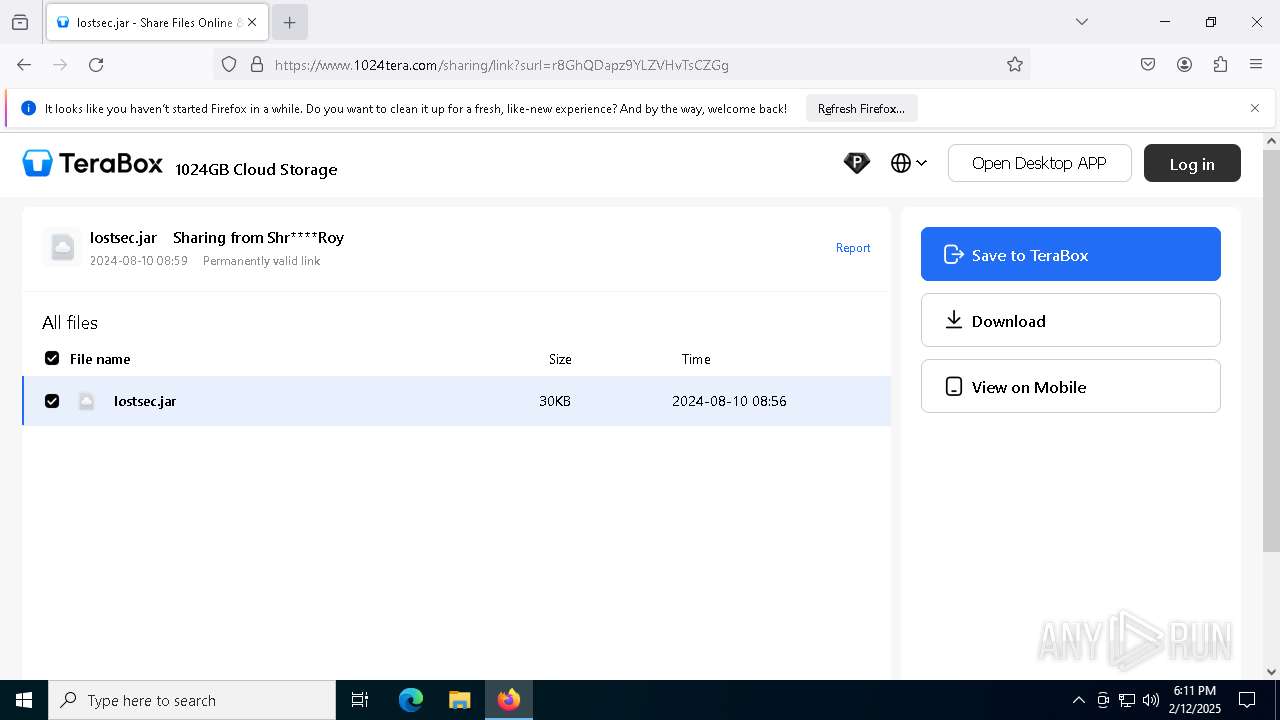
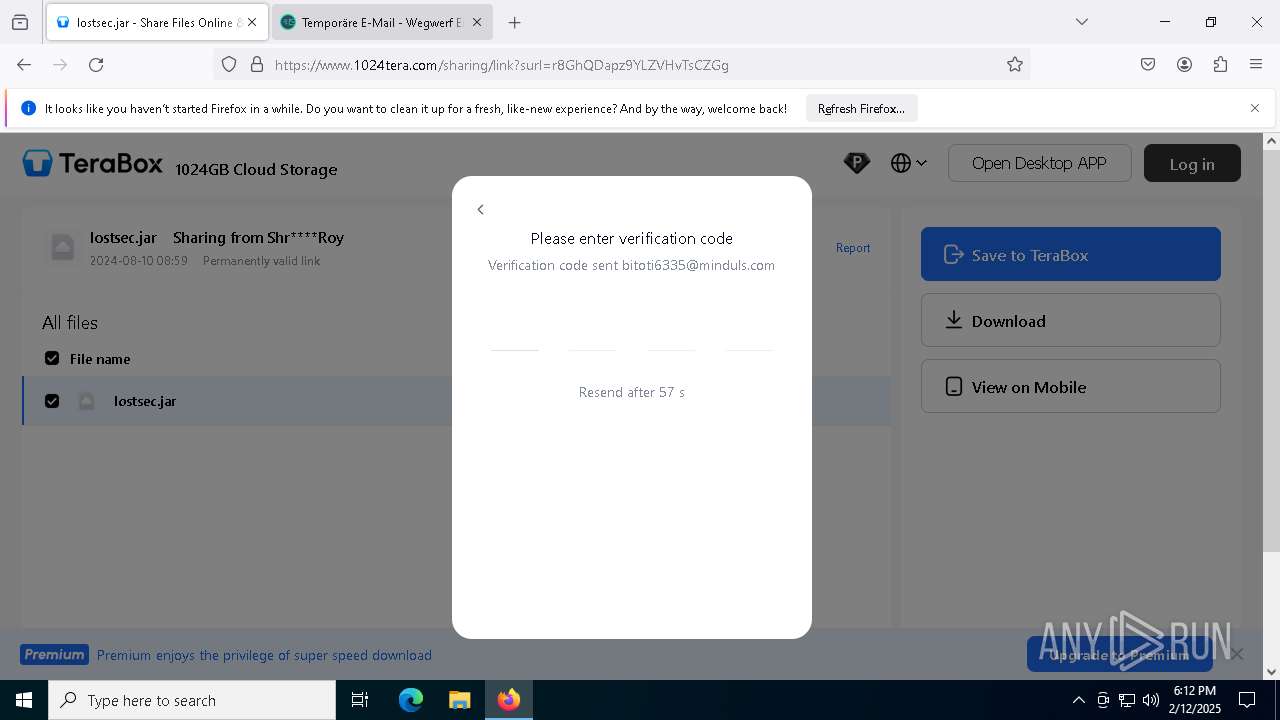
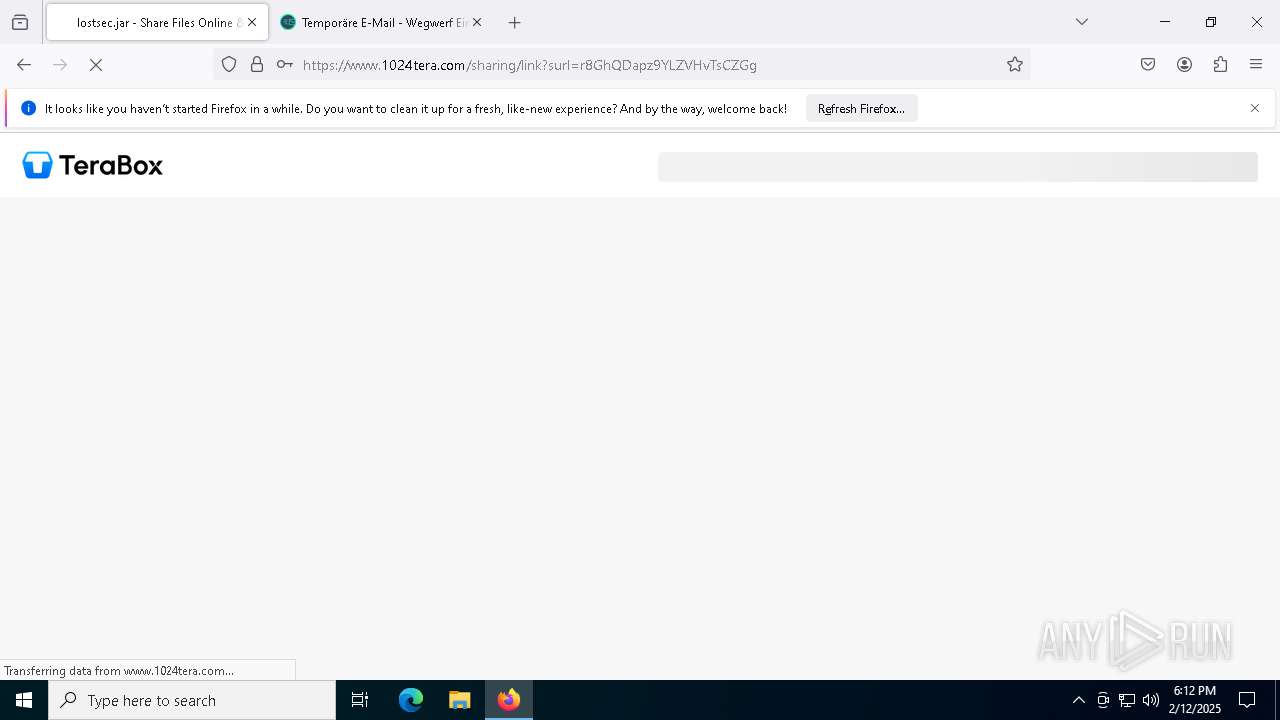
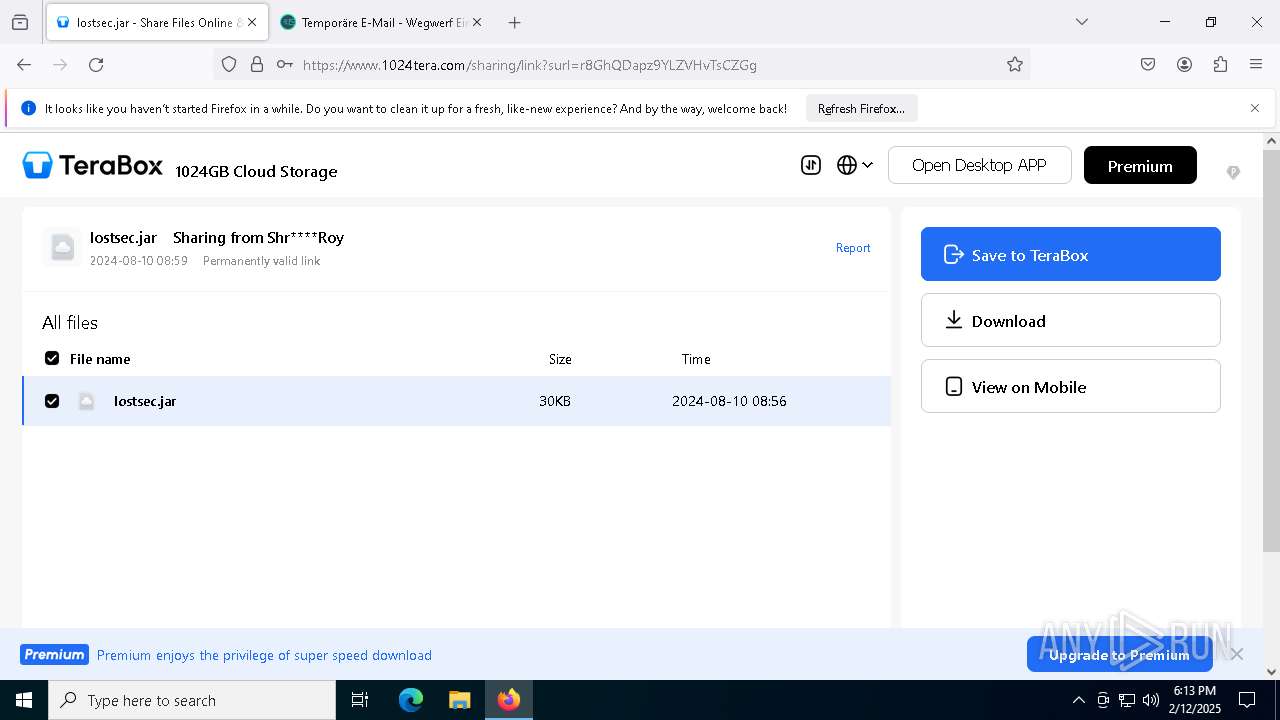
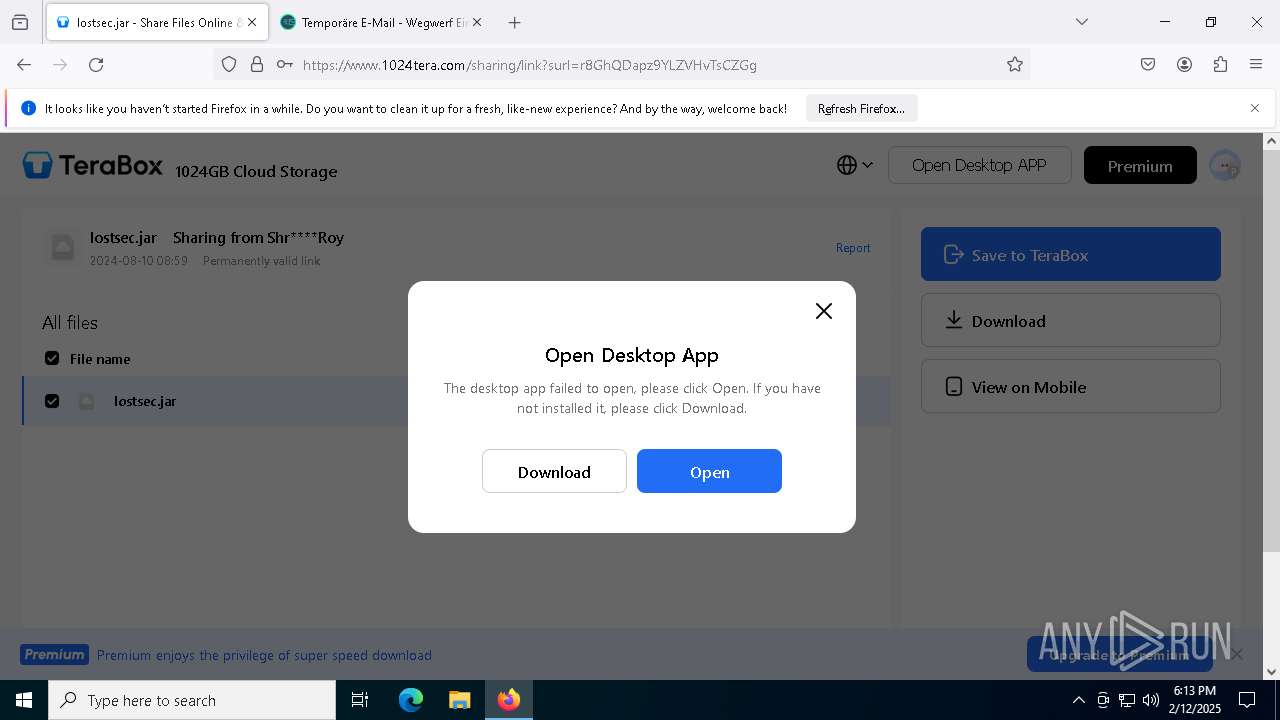
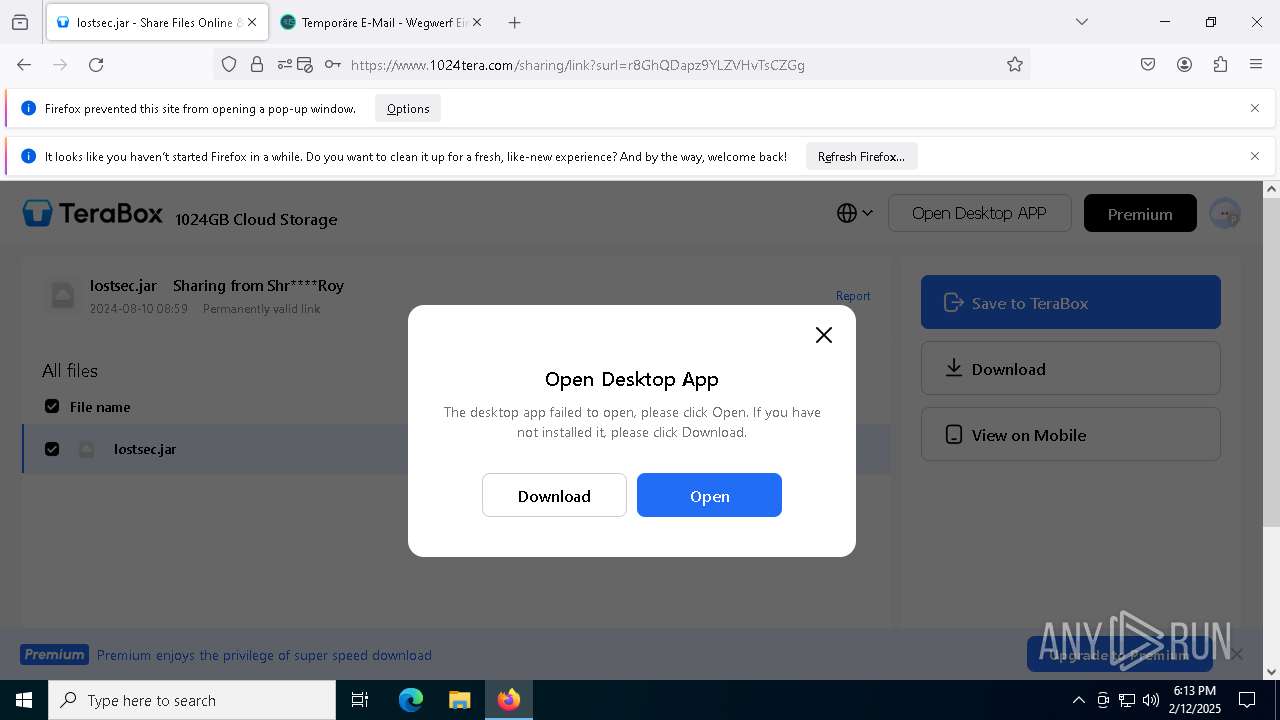
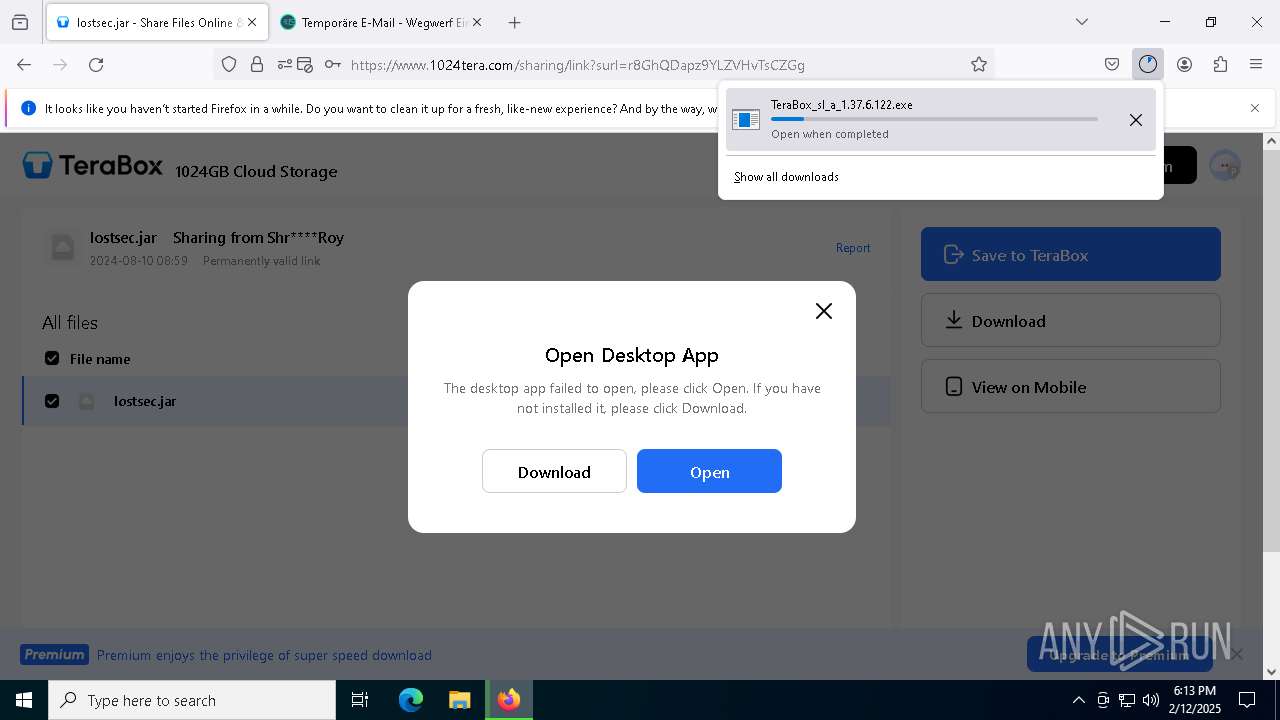
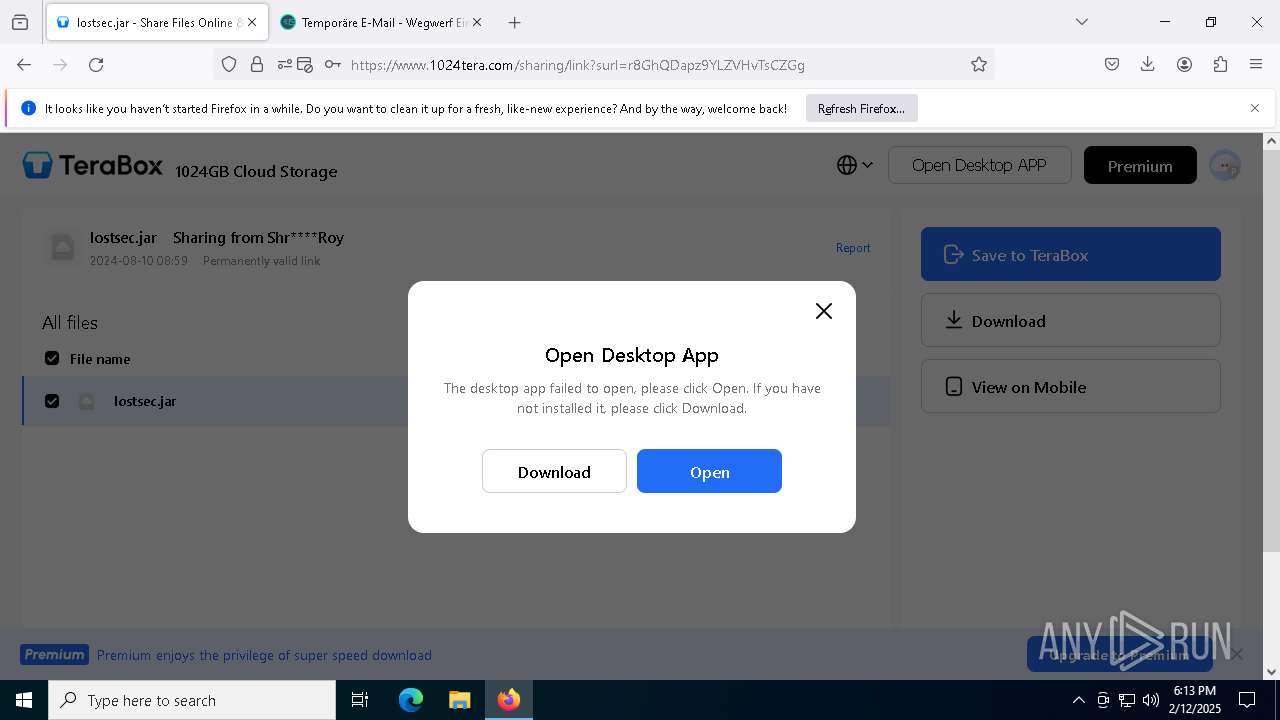
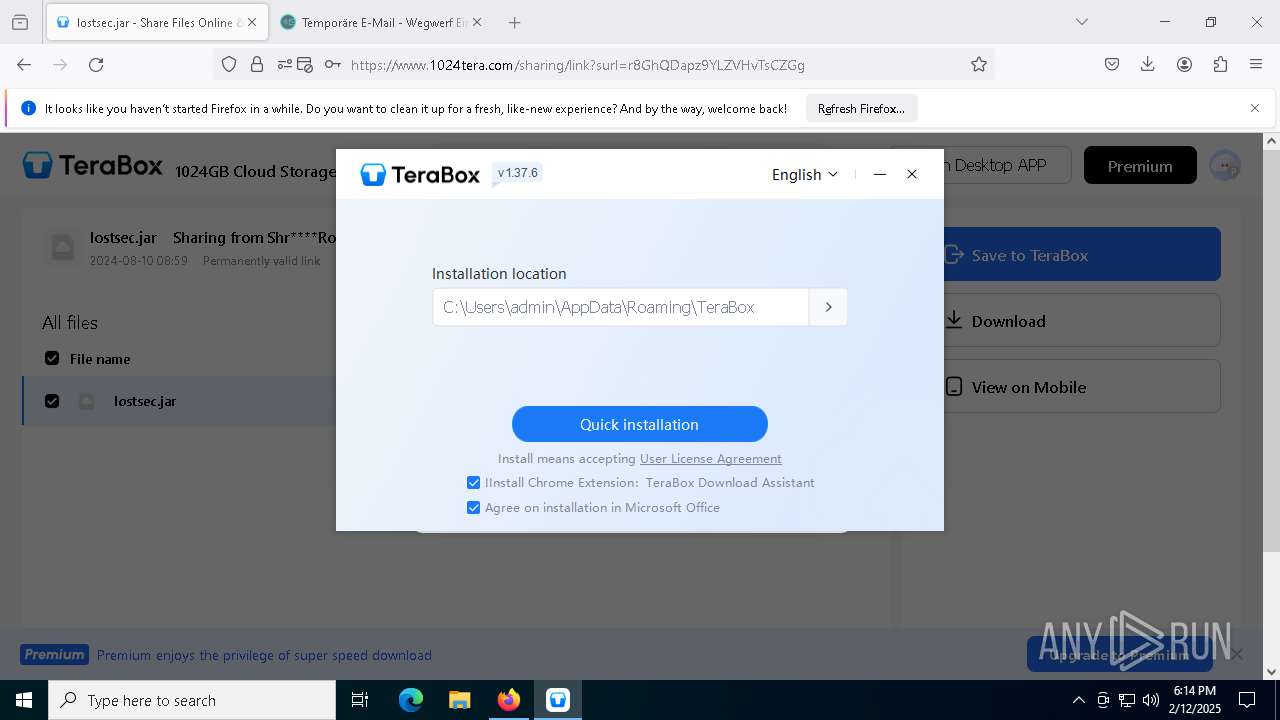
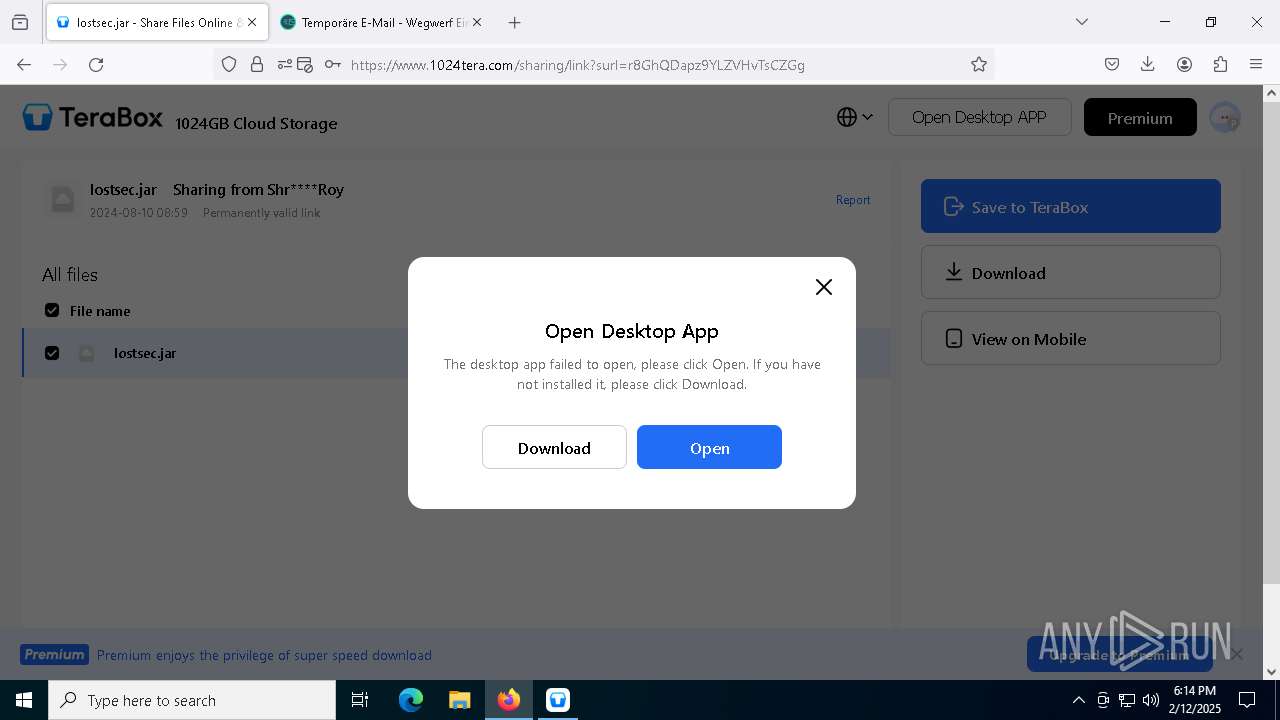
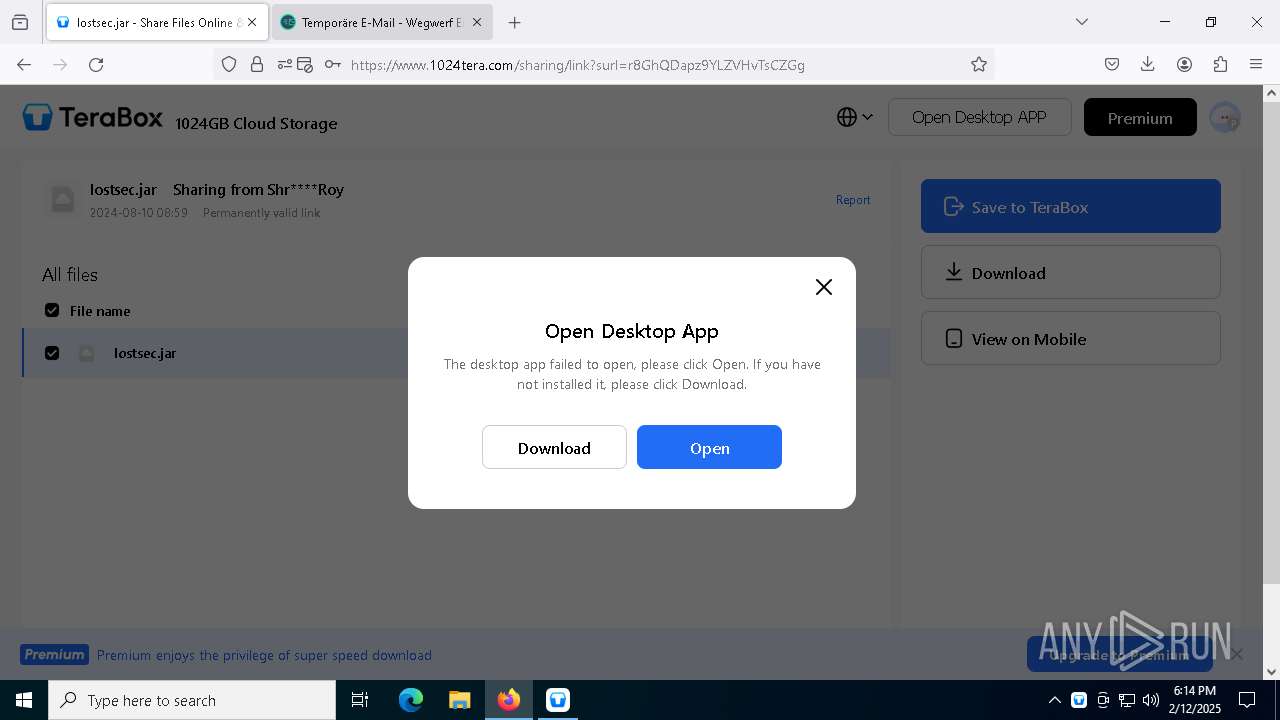
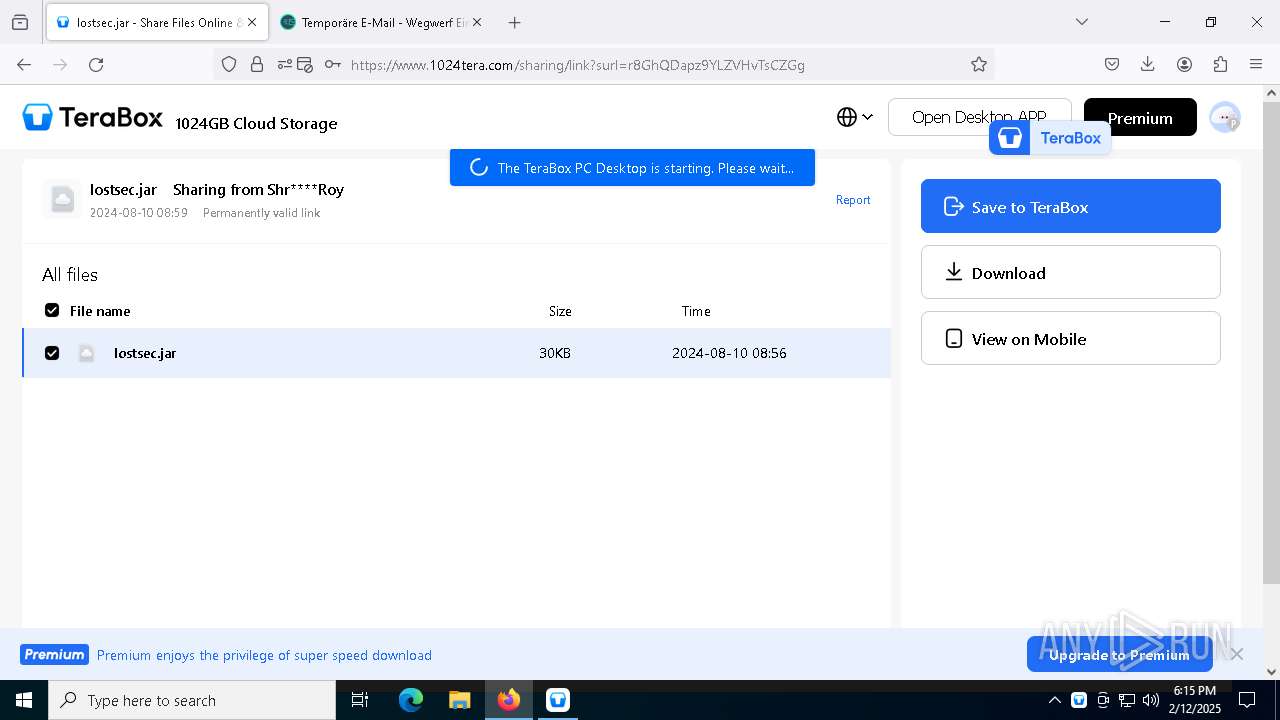
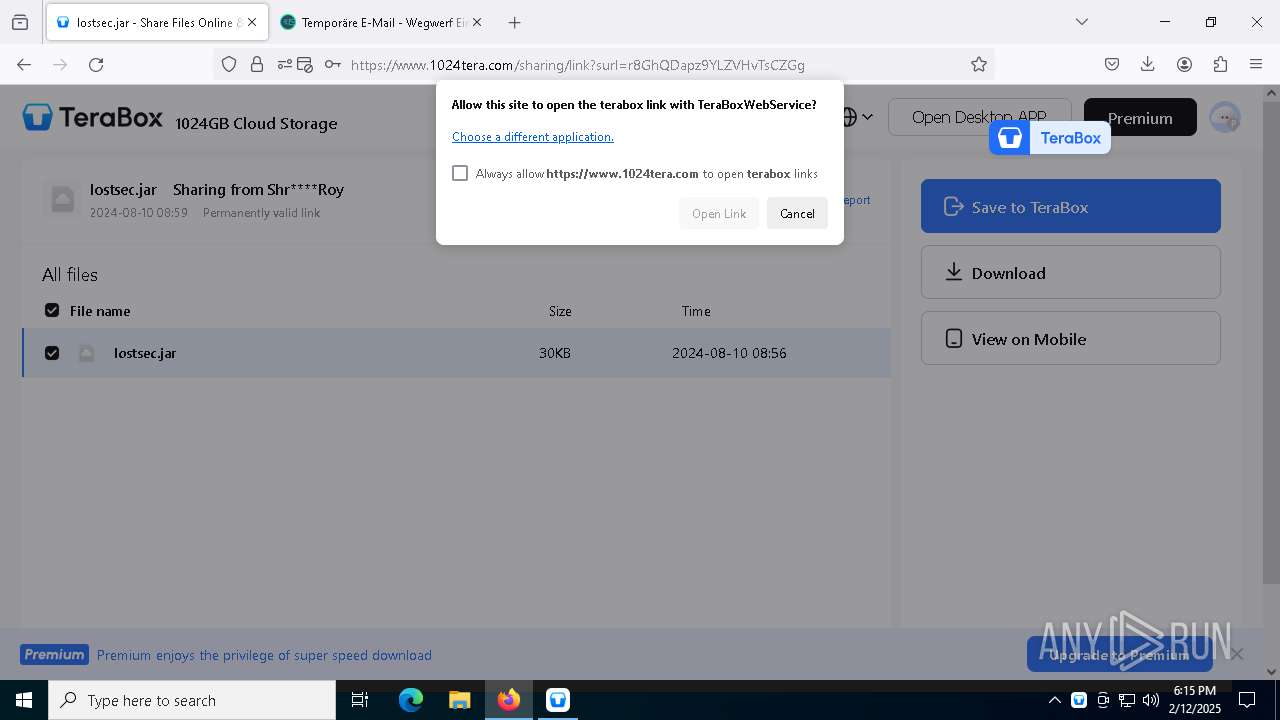
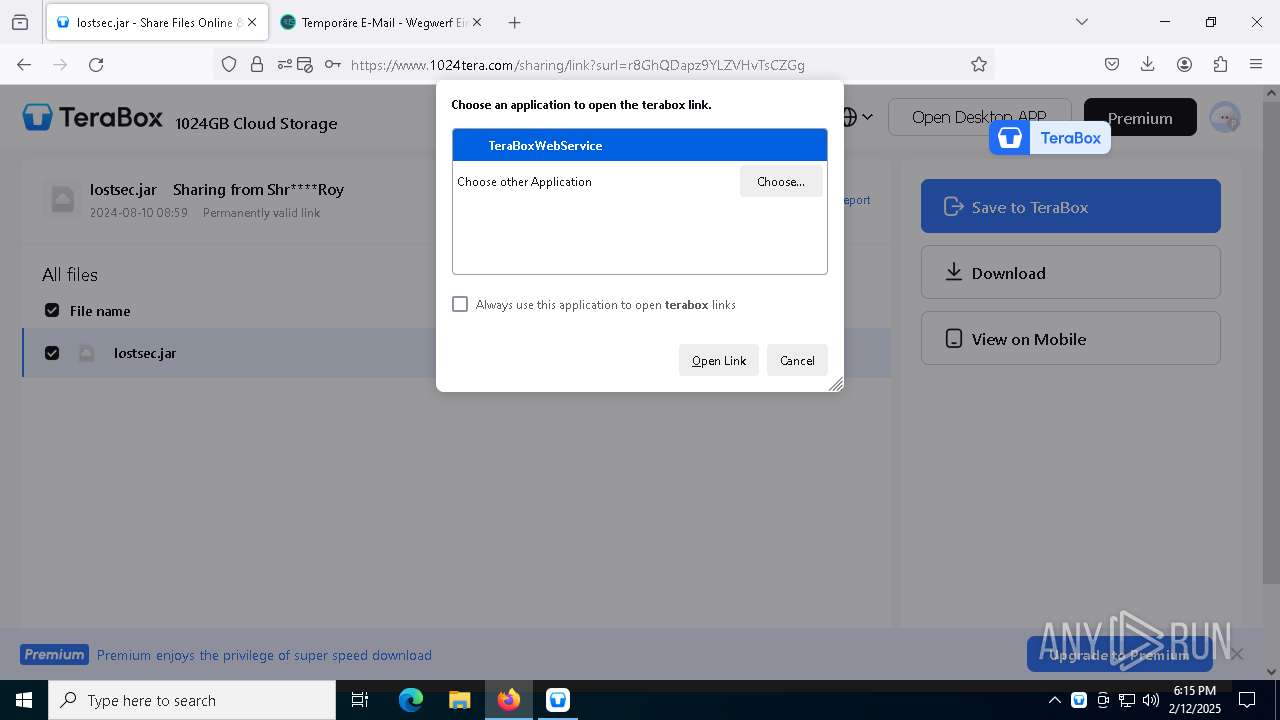
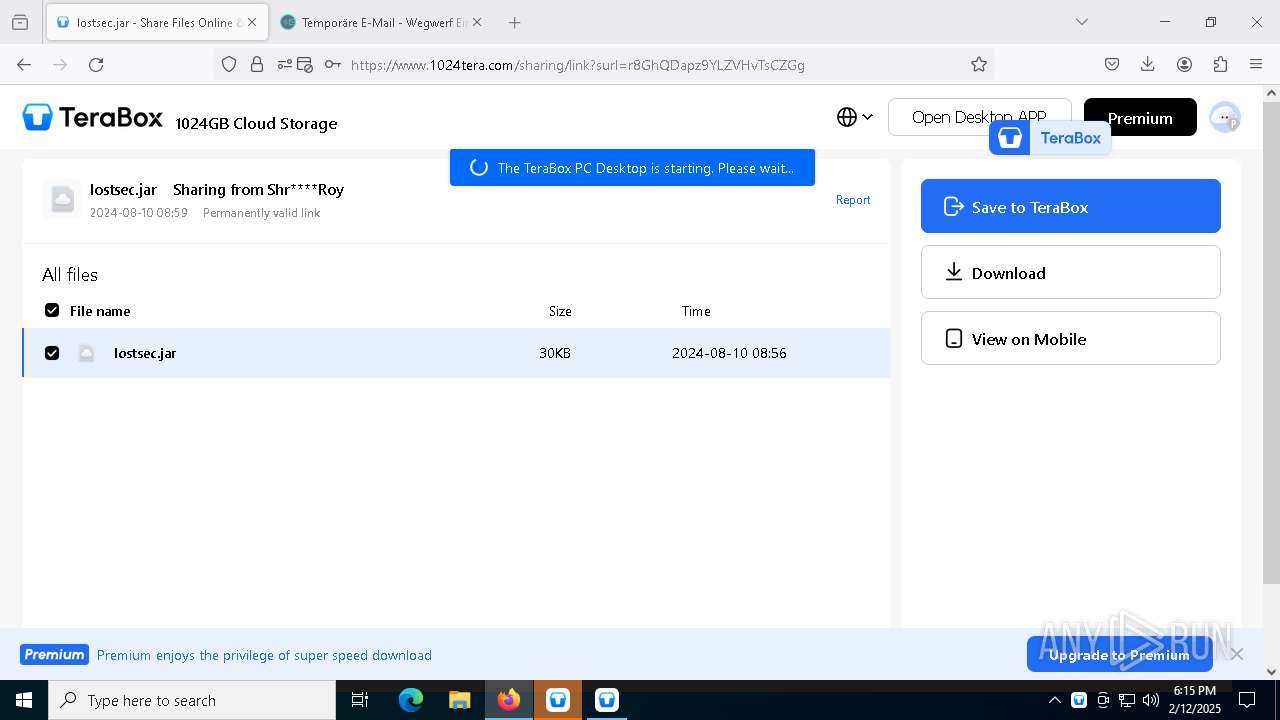
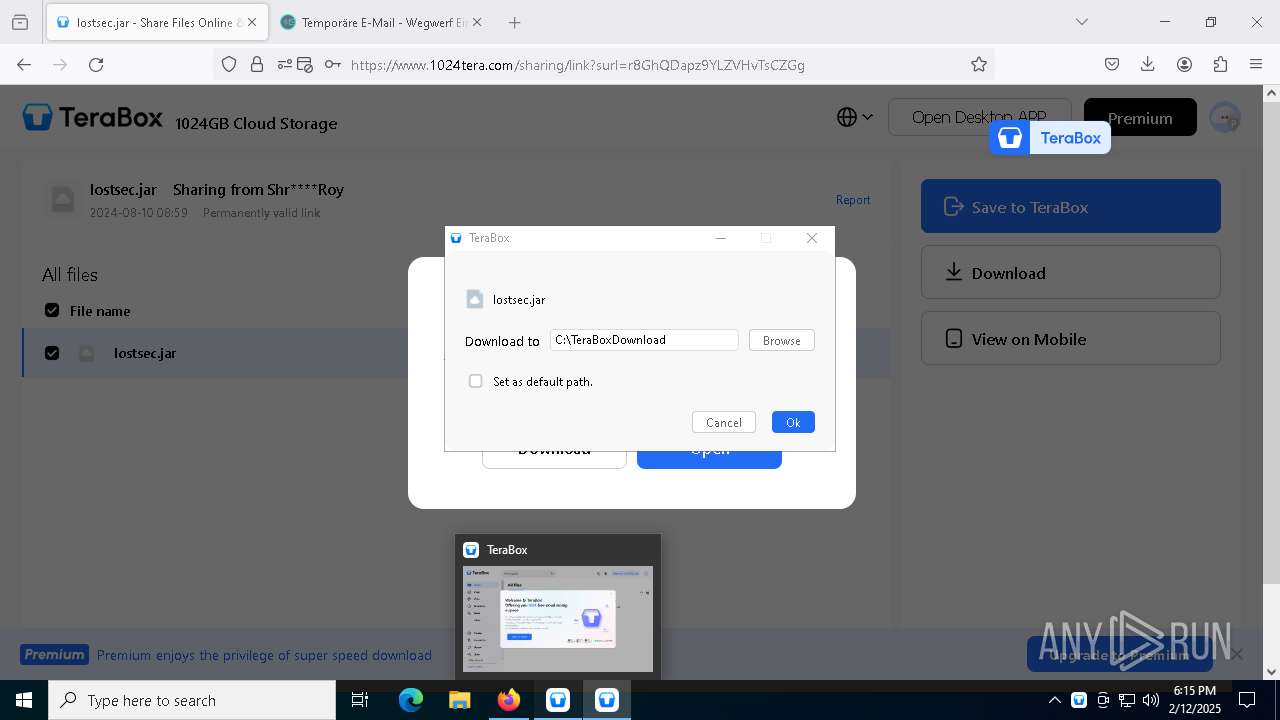
| URL: | https://www.youtube.com/redirect?event=comments&redir_token=QUFFLUhqbXdSd2tTUlQ2d1FYNFBzQ3ZDQjdXTm51MWhrZ3xBQ3Jtc0tsSUFyLWg3VXR1MEwzWEk0NlE1eGxiXzV6SjZfc1g4eHY4RFBpdExZYTUyeEh1SjF0RFlyVlMzcWVOenF3RzdXUlFRUllFWEFxeEhzRzJjazM2NEExdThUUnZaaGM2d2pDZzVmODRPeUhZM3l6N1JnTQ&q=https%3A%2F%2F1024terabox.com%2Fs%2F1r8GhQDapz9YLZVHvTsCZGg |
| Full analysis: | https://app.any.run/tasks/08e04e71-619b-4642-976c-63a8e12fe302 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 18:11:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 66FB457B23CC5AB2DBED020E92D3AB34 |
| SHA1: | C3B96E32C4B4F3D64213C61807566DB8F1E16A99 |
| SHA256: | E2E819861204CC4A1F336F7F58F24935A6E58E5701F5C89320D533A2D39DCDC5 |
| SSDEEP: | 6:2OLUxGKmquxZqZPq1+HfDKBWUV6vjfxn0kVddrN33zWRFmRn:2jGRPPqruB1I7fxPppn6Yn |
MALICIOUS
Changes the autorun value in the registry
- TeraBox.exe (PID: 1760)
Registers / Runs the DLL via REGSVR32.EXE
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
SUSPICIOUS
Process drops legitimate windows executable
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
Creates a software uninstall entry
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
Executable content was dropped or overwritten
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
- TeraBoxUnite.exe (PID: 2084)
- TeraBoxUnite.exe (PID: 1044)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 2396)
- regsvr32.exe (PID: 9052)
Reads security settings of Internet Explorer
- TeraBoxWebService.exe (PID: 3760)
- TeraBox.exe (PID: 8796)
- Autoupdate.exe (PID: 9812)
Checks Windows Trust Settings
- TeraBox.exe (PID: 8796)
Application launched itself
- TeraBoxUnite.exe (PID: 2084)
The process checks if it is being run in the virtual environment
- TeraBoxUnite.exe (PID: 2084)
The process creates files with name similar to system file names
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
Malware-specific behavior (creating "System.dll" in Temp)
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
The process drops C-runtime libraries
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
INFO
Application launched itself
- firefox.exe (PID: 6252)
- firefox.exe (PID: 6312)
Checks supported languages
- TeraBox.exe (PID: 1760)
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
- TeraBoxWebService.exe (PID: 4160)
- TeraBoxWebService.exe (PID: 3760)
- TeraBox.exe (PID: 8796)
- TeraBoxUnite.exe (PID: 7012)
- TeraBoxUnite.exe (PID: 2084)
- TeraBoxUnite.exe (PID: 3000)
- TeraBoxWebService.exe (PID: 6408)
- TeraBoxUnite.exe (PID: 1044)
- TeraBoxUnite.exe (PID: 8064)
- TeraBoxUnite.exe (PID: 8300)
- TeraBoxUnite.exe (PID: 9248)
- TeraBoxHost.exe (PID: 9444)
- TeraBoxUnite.exe (PID: 9692)
- TeraBoxUnite.exe (PID: 9988)
- javaw.exe (PID: 7532)
Creates files or folders in the user directory
- TeraBox.exe (PID: 1760)
- TeraBox.exe (PID: 8796)
- TeraBoxWebService.exe (PID: 3760)
- TeraBoxUnite.exe (PID: 2084)
- crashpad_handler.exe (PID: 9484)
- TeraBoxHost.exe (PID: 9444)
- TeraBoxUnite.exe (PID: 1044)
- TeraBoxHost.exe (PID: 9580)
- Autoupdate.exe (PID: 9812)
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
- javaw.exe (PID: 7532)
Reads the computer name
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
- TeraBoxWebService.exe (PID: 3760)
- TeraBox.exe (PID: 8796)
- TeraBoxUnite.exe (PID: 2084)
- TeraBox.exe (PID: 1760)
The sample compiled with english language support
- firefox.exe (PID: 6312)
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
The sample compiled with chinese language support
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
Executable content was dropped or overwritten
- firefox.exe (PID: 6312)
Create files in a temporary directory
- TeraBox_sl_a_1.37.6.122.exe (PID: 7820)
- TeraBoxUnite.exe (PID: 2084)
- TeraBoxUnite.exe (PID: 3000)
- TeraBoxUnite.exe (PID: 1044)
- javaw.exe (PID: 7532)
- java.exe (PID: 9268)
- java.exe (PID: 9836)
Reads the software policy settings
- TeraBox.exe (PID: 8796)
- TeraBoxUnite.exe (PID: 2084)
Checks proxy server information
- TeraBoxWebService.exe (PID: 3760)
- TeraBox.exe (PID: 8796)
- TeraBoxUnite.exe (PID: 2084)
- Autoupdate.exe (PID: 9812)
Reads the machine GUID from the registry
- TeraBox.exe (PID: 8796)
- TeraBoxUnite.exe (PID: 2084)
- TeraBoxHost.exe (PID: 9580)
- javaw.exe (PID: 7532)
Manual execution by a user
- TeraBoxWebService.exe (PID: 6408)
- TeraBoxWebService.exe (PID: 9964)
Process checks computer location settings
- TeraBoxUnite.exe (PID: 2084)
- TeraBoxUnite.exe (PID: 1044)
- TeraBoxUnite.exe (PID: 8300)
- TeraBoxUnite.exe (PID: 9692)
- TeraBoxUnite.exe (PID: 9988)
Node.js compiler has been detected
- TeraBoxUnite.exe (PID: 2084)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 1868)
Application based on Java
- javaw.exe (PID: 7532)
Creates files in the program directory
- javaw.exe (PID: 7532)
- TeraBoxHost.exe (PID: 9580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
225
Monitored processes
93
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5848 -childID 7 -isForBrowser -prefsHandle 5840 -prefMapHandle 5836 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1304 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {86e96ea1-4a52-4e4a-b920-0e1cfcc1aa6e} 6312 "\\.\pipe\gecko-crash-server-pipe.6312" 17709a70690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 640 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6872 -childID 18 -isForBrowser -prefsHandle 6840 -prefMapHandle 7852 -prefsLen 32060 -prefMapSize 244583 -jsInitHandle 1304 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b816aec8-48aa-4c6b-9dce-caa745bd0b3e} 6312 "\\.\pipe\gecko-crash-server-pipe.6312" 17709a70f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\TeraBox\cache" --app-path="C:\Users\admin\AppData\Roaming\TeraBox\resources\app.asar" --no-sandbox --no-zygote --node-integration-in-worker --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=3012 --field-trial-handle=1860,i,9316623127174814904,15934932849736374377,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe | TeraBoxUnite.exe | ||||||||||||
User: admin Company: Flextech Integrity Level: MEDIUM Description: TeraBoxUnite Version: 1.37.6.122 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=8492 -childID 32 -isForBrowser -prefsHandle 7616 -prefMapHandle 7632 -prefsLen 32060 -prefMapSize 244583 -jsInitHandle 1304 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {48cc26f3-b916-4247-af18-c1138b90d592} 6312 "\\.\pipe\gecko-crash-server-pipe.6312" 1770822bf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1292 | "/s" "C:\Users\admin\AppData\Roaming\TeraBox\YunShellExt64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7420 -childID 15 -isForBrowser -prefsHandle 7440 -prefMapHandle 7408 -prefsLen 32060 -prefMapSize 244583 -jsInitHandle 1304 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {11dde20b-ec53-4021-a570-b19ed63e2d72} 6312 "\\.\pipe\gecko-crash-server-pipe.6312" 1770822bf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe" -install "createdetectstartup" -install "createshortcut" "0" -install "createstartup" | C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe | TeraBox_sl_a_1.37.6.122.exe | ||||||||||||
User: admin Company: Flextech Inc. Integrity Level: HIGH Exit code: 0 Version: 1.37.6.122 Modules
| |||||||||||||||
| 1868 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2084 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxUnite.exe | TeraBox.exe | ||||||||||||
User: admin Company: Flextech Integrity Level: MEDIUM Description: TeraBoxUnite Version: 1.37.6.122 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7856 -childID 17 -isForBrowser -prefsHandle 7368 -prefMapHandle 7816 -prefsLen 32060 -prefMapSize 244583 -jsInitHandle 1304 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7d8e62b4-9f19-4eb8-b660-cddbc00e2be4} 6312 "\\.\pipe\gecko-crash-server-pipe.6312" 17709a70a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
80 330
Read events
80 211
Write events
101
Delete events
18
Modification events
| (PID) Process: | (6312) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6312) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7820) TeraBox_sl_a_1.37.6.122.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TeraBox |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (7820) TeraBox_sl_a_1.37.6.122.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\TeraBox |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (1760) TeraBox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | TeraBox |
Value: "C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe" AutoRun | |||
| (PID) Process: | (1760) TeraBox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | TeraBoxWeb |
Value: "C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxWebService.exe" | |||
| (PID) Process: | (1292) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\YunShellExt.DLL |
| Operation: | write | Name: | AppID |
Value: {B9480AFD-C7B1-4452-BE14-BB8A9540A05D} | |||
| (PID) Process: | (1292) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{6D85624F-305A-491d-8848-C1927AA0D790}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (1292) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{6D85624F-305A-491d-8848-C1927AA0D790} |
| Operation: | write | Name: | AppID |
Value: {B9480AFD-C7B1-4452-BE14-BB8A9540A05D} | |||
| (PID) Process: | (1292) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{1434B2F5-5B9C-44C2-938D-2A11E03CEED9}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
89
Suspicious files
549
Text files
80
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6312 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:17131BED3A7B4348244C4BFCA1049FD6 | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6312 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
198
TCP/UDP connections
806
DNS requests
1 291
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6312 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6312 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6312 | firefox.exe | POST | 200 | 142.250.185.67:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
6312 | firefox.exe | POST | 200 | 104.124.11.209:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2356 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2356 | svchost.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.youtube.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING DNS Query to File Sharing Domain (terabox .com) |
6312 | firefox.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |
6312 | firefox.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |
6312 | firefox.exe | Misc activity | ET FILE_SHARING Observed File Sharing Domain (terabox .com in TLS SNI) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |