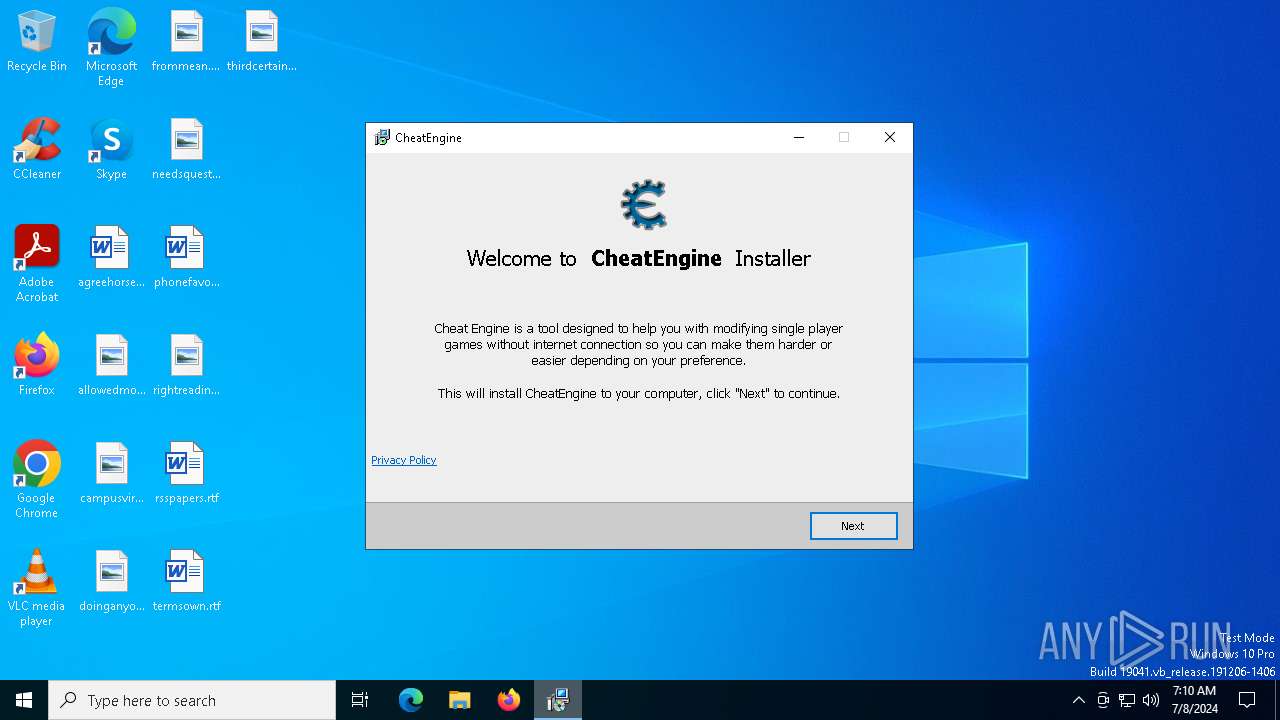
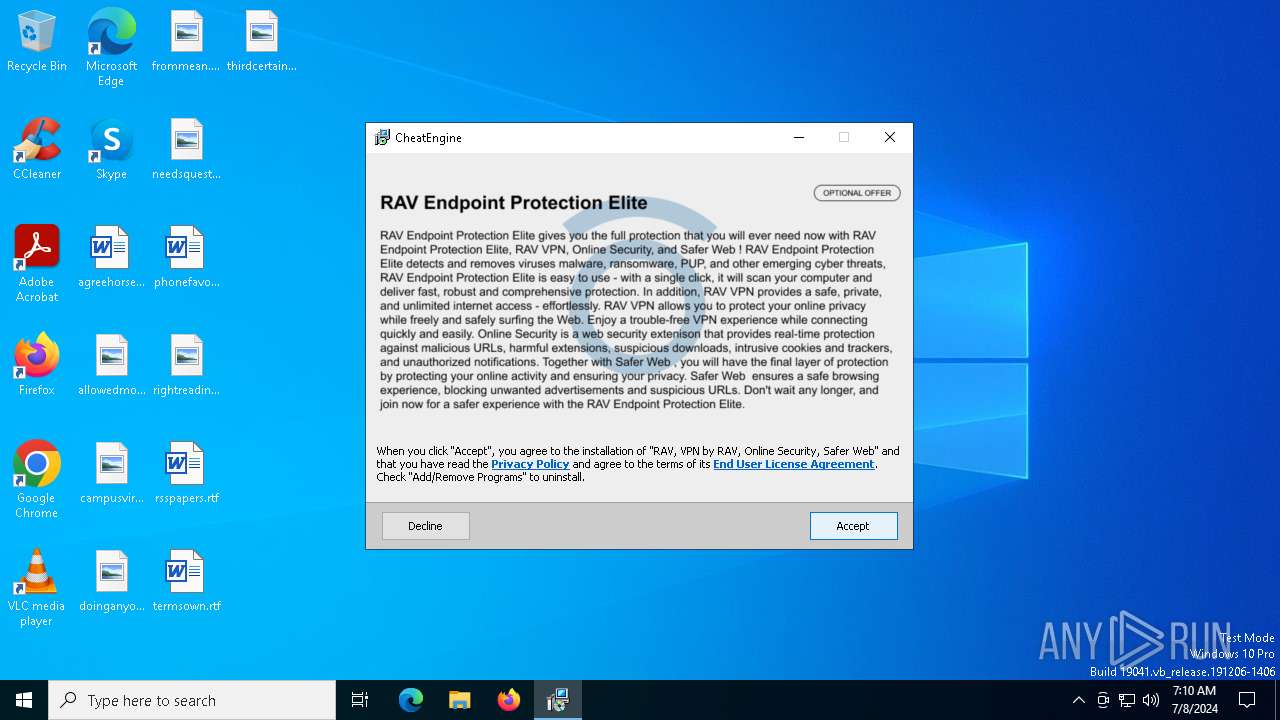
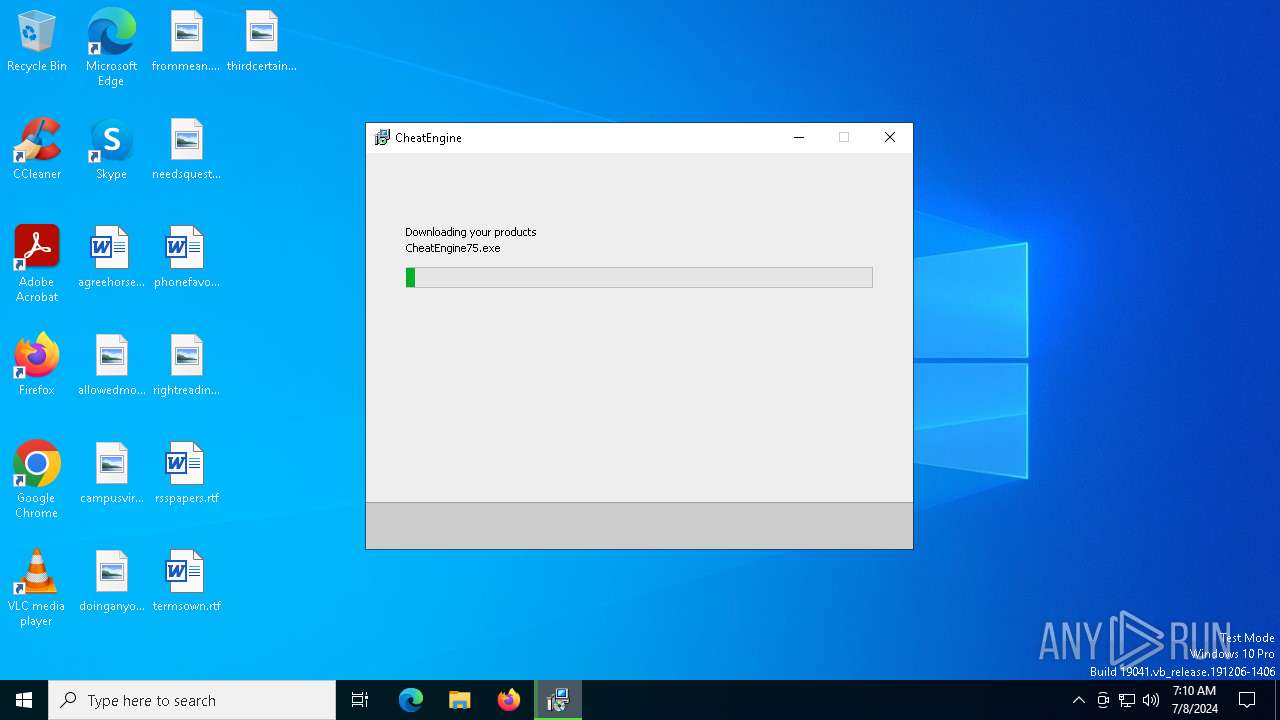
| download: | /installer/63950252086695844364/6111090 |
| Full analysis: | https://app.any.run/tasks/91246e27-e519-403b-8a5c-9cbb9ddb6812 |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2024, 07:09:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 609FEA742D34DC1D53F0EEB4873B1A0A |
| SHA1: | 3232C52DA3CB8F47A870162A35CDD75FCAE60AEA |
| SHA256: | E2E15826B69778E381F25AC8F2B109A377B23F7CF79B5F482E81F4D28C30F95E |
| SSDEEP: | 98304:wSiW4opH4opH4op4U9tNz9RGa/xlbLP/h4:ZDBDBD1t3Hbb+ |
MALICIOUS
Drops the executable file immediately after the start
- 6111090.exe (PID: 1228)
- 6111090.exe (PID: 6176)
- 6111090.tmp (PID: 6464)
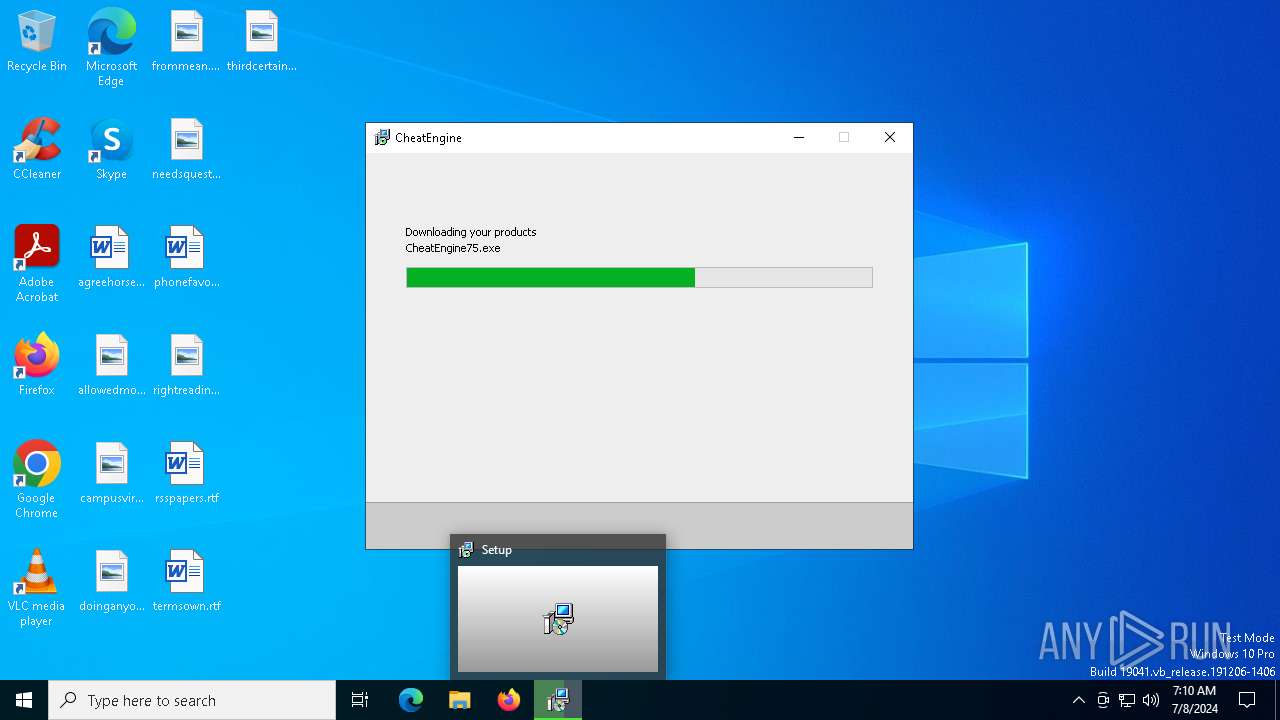
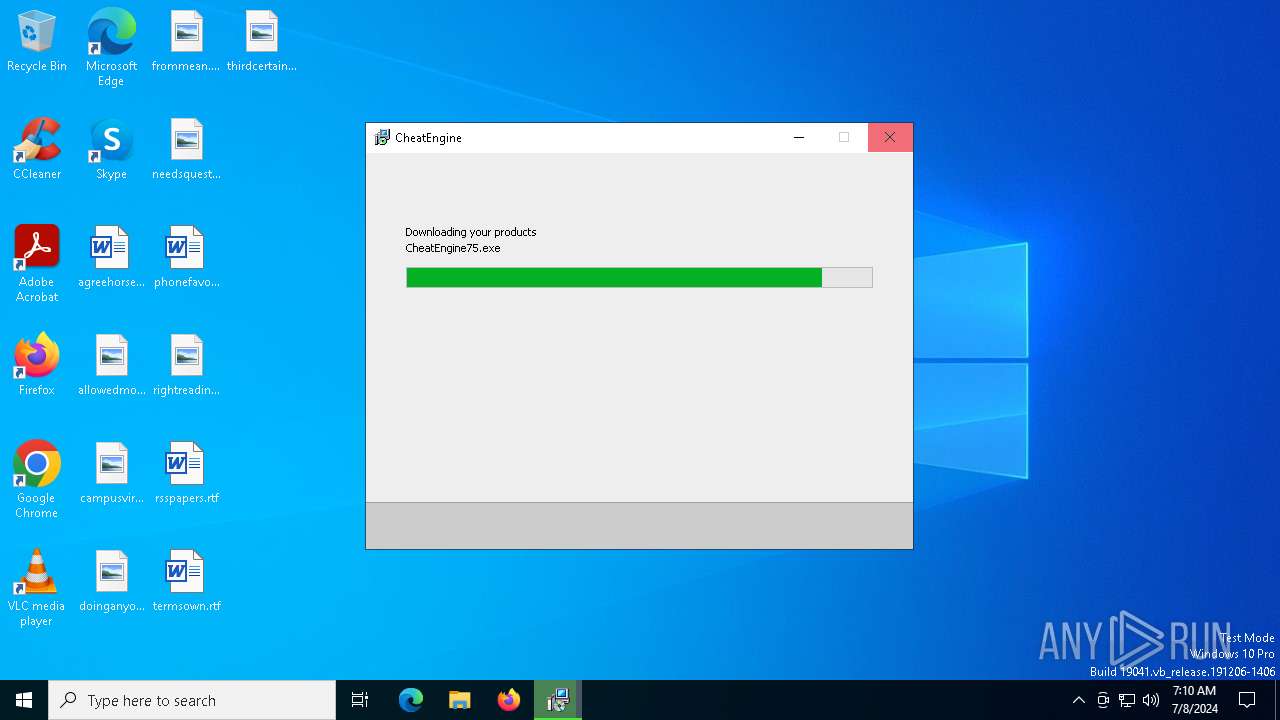
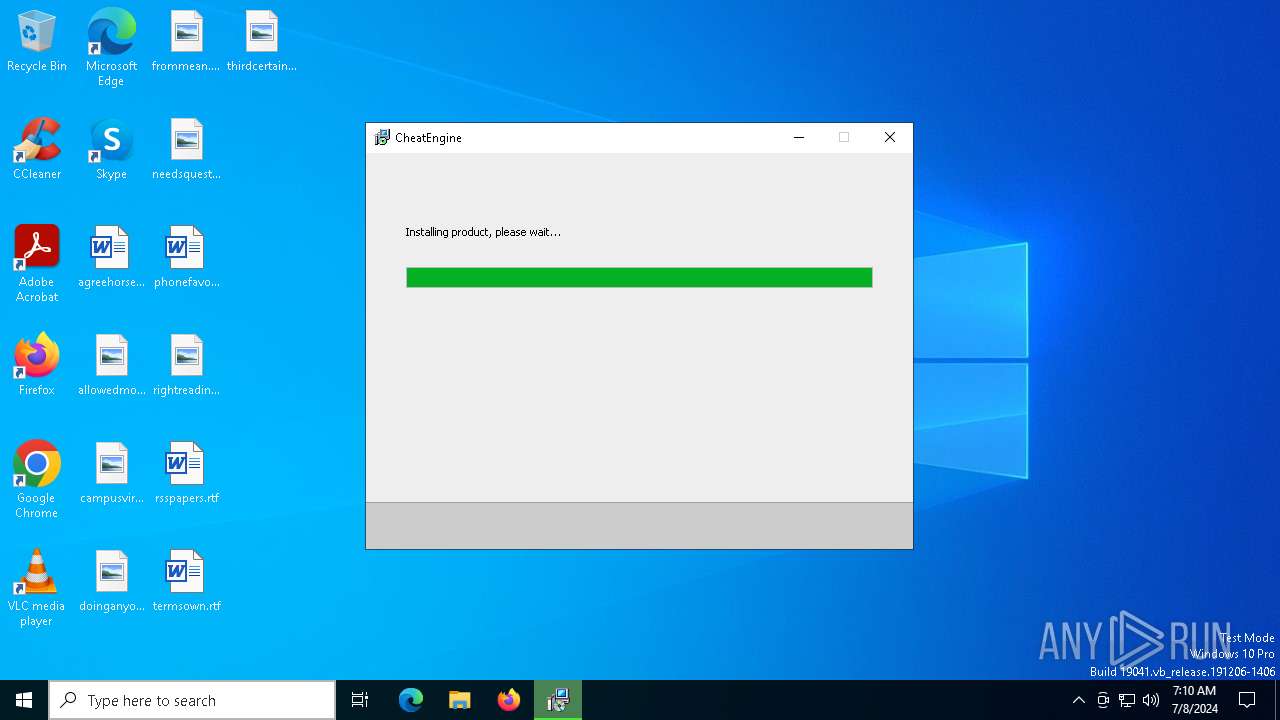
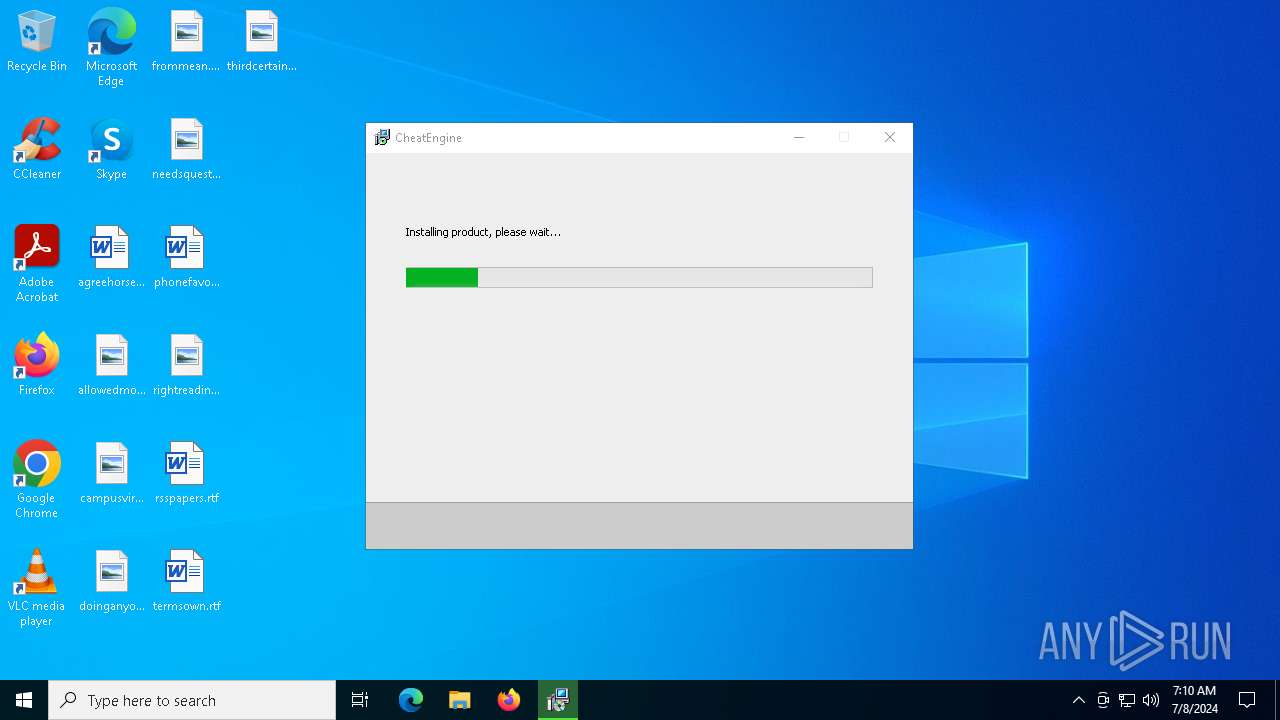
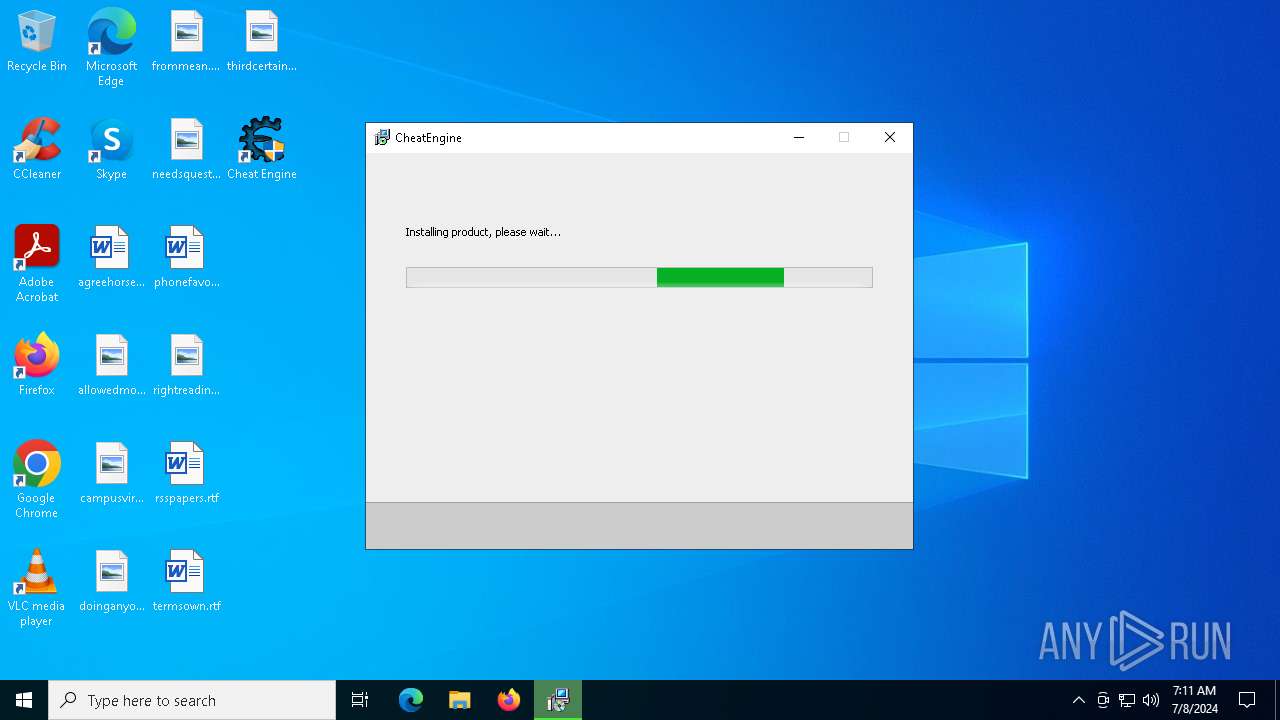
- CheatEngine75.exe (PID: 5840)
- prod0.exe (PID: 2652)
- CheatEngine75.tmp (PID: 2360)
- UnifiedStub-installer.exe (PID: 6616)
- awyihqxo.exe (PID: 3584)
Starts NET.EXE for service management
- CheatEngine75.tmp (PID: 2360)
- net.exe (PID: 3676)
- net.exe (PID: 2336)
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 6616)
SUSPICIOUS
Executable content was dropped or overwritten
- 6111090.exe (PID: 1228)
- 6111090.exe (PID: 6176)
- 6111090.tmp (PID: 6464)
- CheatEngine75.exe (PID: 5840)
- awyihqxo.exe (PID: 3584)
- prod0.exe (PID: 2652)
- CheatEngine75.tmp (PID: 2360)
- UnifiedStub-installer.exe (PID: 6616)
Reads security settings of Internet Explorer
- 6111090.tmp (PID: 5396)
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- Cheat Engine.exe (PID: 5532)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Reads the date of Windows installation
- 6111090.tmp (PID: 5396)
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- Cheat Engine.exe (PID: 5532)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Reads the Windows owner or organization settings
- 6111090.tmp (PID: 6464)
- CheatEngine75.tmp (PID: 2360)
Starts SC.EXE for service management
- CheatEngine75.tmp (PID: 2360)
Uses ICACLS.EXE to modify access control lists
- CheatEngine75.tmp (PID: 2360)
Process drops SQLite DLL files
- CheatEngine75.tmp (PID: 2360)
Process drops legitimate windows executable
- CheatEngine75.tmp (PID: 2360)
- awyihqxo.exe (PID: 3584)
- UnifiedStub-installer.exe (PID: 6616)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 6616)
Searches for installed software
- UnifiedStub-installer.exe (PID: 6616)
Executes as Windows Service
- rsSyncSvc.exe (PID: 5504)
Detected use of alternative data streams (AltDS)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Checks Windows Trust Settings
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Creates file in the systems drive root
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
There is functionality for communication over UDP network (YARA)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
INFO
Checks supported languages
- 6111090.exe (PID: 1228)
- 6111090.tmp (PID: 5396)
- 6111090.exe (PID: 6176)
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- CheatEngine75.exe (PID: 5840)
- CheatEngine75.tmp (PID: 2360)
- _setup64.tmp (PID: 5876)
- awyihqxo.exe (PID: 3584)
- UnifiedStub-installer.exe (PID: 6616)
- rsSyncSvc.exe (PID: 1068)
- rsSyncSvc.exe (PID: 5504)
- Kernelmoduleunloader.exe (PID: 5132)
- windowsrepair.exe (PID: 1192)
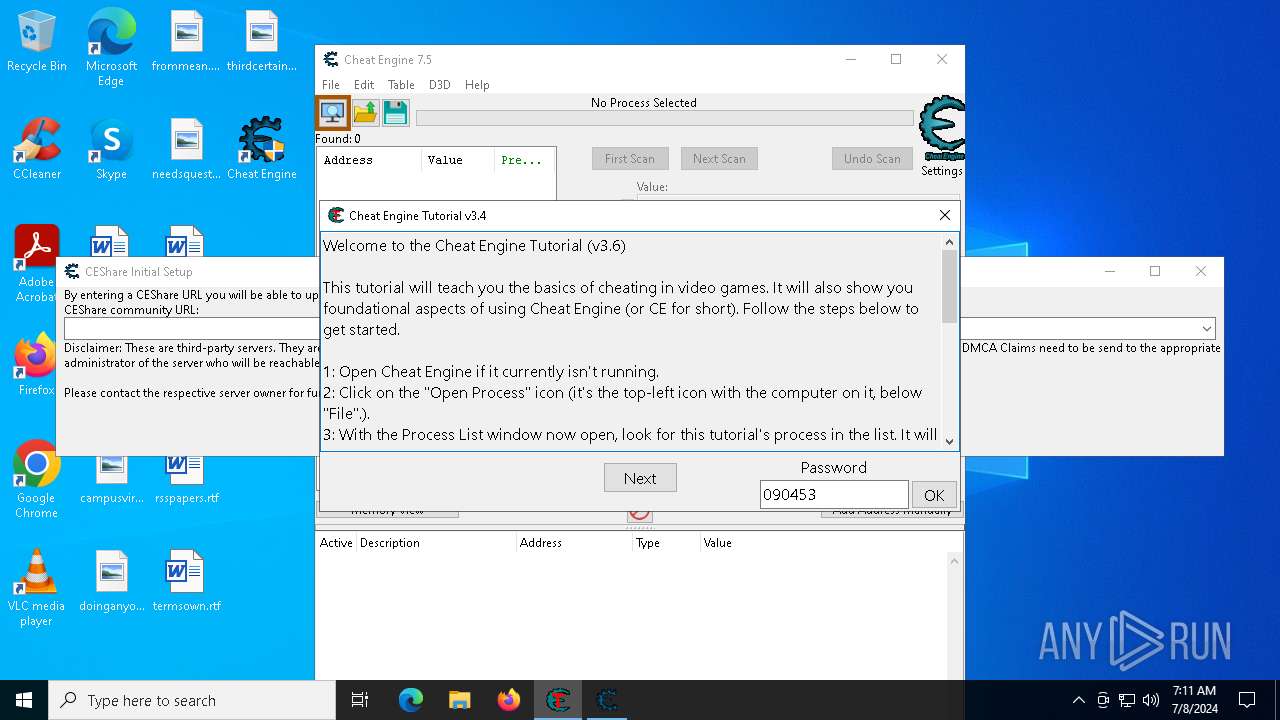
- Cheat Engine.exe (PID: 5532)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
- Tutorial-x86_64.exe (PID: 6912)
Reads the computer name
- 6111090.tmp (PID: 5396)
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- CheatEngine75.tmp (PID: 2360)
- UnifiedStub-installer.exe (PID: 6616)
- rsSyncSvc.exe (PID: 1068)
- Kernelmoduleunloader.exe (PID: 5132)
- Cheat Engine.exe (PID: 5532)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
- rsSyncSvc.exe (PID: 5504)
- Tutorial-x86_64.exe (PID: 6912)
Create files in a temporary directory
- 6111090.exe (PID: 1228)
- 6111090.exe (PID: 6176)
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- CheatEngine75.exe (PID: 5840)
- CheatEngine75.tmp (PID: 2360)
- awyihqxo.exe (PID: 3584)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
- UnifiedStub-installer.exe (PID: 6616)
Process checks computer location settings
- 6111090.tmp (PID: 5396)
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- Cheat Engine.exe (PID: 5532)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Reads the software policy settings
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- UnifiedStub-installer.exe (PID: 6616)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
- slui.exe (PID: 1920)
- slui.exe (PID: 6324)
Reads the machine GUID from the registry
- 6111090.tmp (PID: 6464)
- prod0.exe (PID: 2652)
- UnifiedStub-installer.exe (PID: 6616)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Reads Environment values
- prod0.exe (PID: 2652)
- UnifiedStub-installer.exe (PID: 6616)
Disables trace logs
- prod0.exe (PID: 2652)
- UnifiedStub-installer.exe (PID: 6616)
Checks proxy server information
- prod0.exe (PID: 2652)
- 6111090.tmp (PID: 6464)
- UnifiedStub-installer.exe (PID: 6616)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
- slui.exe (PID: 6324)
Creates files in the program directory
- CheatEngine75.tmp (PID: 2360)
- UnifiedStub-installer.exe (PID: 6616)
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
Creates a software uninstall entry
- CheatEngine75.tmp (PID: 2360)
Creates files or folders in the user directory
- cheatengine-x86_64-SSE4-AVX2.exe (PID: 5652)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 6616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.5.0.0 |
| ProductVersionNumber: | 7.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | EngineGame Installer |
| FileVersion: | 7.5.0 |
| LegalCopyright: | © EngineGame |
| OriginalFileName: | |
| ProductName: | EngineGame |
| ProductVersion: | 7.5.0 |
Total processes
181
Monitored processes
36
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe" -i -bn:ReasonLabs -pn:EPP -lpn:rav_antivirus -url:https://update.reasonsecurity.com/v2/live -dt:10 | C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe | — | UnifiedStub-installer.exe | |||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Security Synchronize Service Exit code: 0 Version: 1.7.2.0 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Cheat Engine 7.5\windowsrepair.exe" /s | C:\Program Files\Cheat Engine 7.5\windowsrepair.exe | — | CheatEngine75.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\AppData\Local\Temp\6111090.exe" | C:\Users\admin\AppData\Local\Temp\6111090.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: EngineGame Installer Exit code: 0 Version: 7.5.0 Modules
| |||||||||||||||
| 1776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | _setup64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2336 | "net" stop BadlionAntic | C:\Windows\System32\net.exe | — | CheatEngine75.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 754
Read events
25 566
Write events
156
Delete events
32
Modification events
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 40190000844EBFD705D1DA01 | |||
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 1A285904A22DD0E5A68CF9E92FD547033648DB59123899C67BC2CDB35494111F | |||
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6464) 6111090.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2652) prod0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\prod0_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2652) prod0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\prod0_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2652) prod0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\prod0_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
195
Suspicious files
116
Text files
415
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6464 | 6111090.tmp | C:\Users\admin\AppData\Local\Temp\is-RC612.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 1228 | 6111090.exe | C:\Users\admin\AppData\Local\Temp\is-IUFJ5.tmp\6111090.tmp | executable | |
MD5:1CDBF6DA4DEFE32C9CB5908968A02FAB | SHA256:87C1BB2236A874C97369B2CCA0D55559FA917707CEBDDF7A5EABC691F8302487 | |||
| 6464 | 6111090.tmp | C:\Users\admin\AppData\Local\Temp\is-RC612.tmp\finish.png | image | |
MD5:6B7CB2A5A8B301C788C3792802696FE8 | SHA256:3EED2E41BC6CA0AE9A5D5EE6D57CA727E5CBA6AC8E8C5234AC661F9080CEDADF | |||
| 6464 | 6111090.tmp | C:\Users\admin\AppData\Local\Temp\is-RC612.tmp\RAV_Cross.png | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 6464 | 6111090.tmp | C:\Users\admin\AppData\Local\Temp\is-RC612.tmp\is-GH396.tmp | image | |
MD5:CD09F361286D1AD2622BA8A57B7613BD | SHA256:B92A31D4853D1B2C4E5B9D9624F40B439856D0C6A517E100978CBDE8D3C47DC8 | |||
| 6464 | 6111090.tmp | C:\Users\admin\AppData\Local\Temp\is-RC612.tmp\error.png | image | |
MD5:6B7CB2A5A8B301C788C3792802696FE8 | SHA256:3EED2E41BC6CA0AE9A5D5EE6D57CA727E5CBA6AC8E8C5234AC661F9080CEDADF | |||
| 6176 | 6111090.exe | C:\Users\admin\AppData\Local\Temp\is-0OONT.tmp\6111090.tmp | executable | |
MD5:1CDBF6DA4DEFE32C9CB5908968A02FAB | SHA256:87C1BB2236A874C97369B2CCA0D55559FA917707CEBDDF7A5EABC691F8302487 | |||
| 6464 | 6111090.tmp | C:\Users\admin\AppData\Local\Temp\is-RC612.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 5840 | CheatEngine75.exe | C:\Users\admin\AppData\Local\Temp\is-OSEVF.tmp\CheatEngine75.tmp | executable | |
MD5:9AA2ACD4C96F8BA03BB6C3EA806D806F | SHA256:1B81562FDAEAA1BC22CBAA15C92BAB90A12080519916CFA30C843796021153BB | |||
| 2360 | CheatEngine75.tmp | C:\Users\admin\AppData\Local\Temp\is-4NEPJ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
83
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3656 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2072 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2072 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
6332 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6324 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
7136 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
7136 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
5652 | cheatengine-x86_64-SSE4-AVX2.exe | GET | 200 | 69.192.161.44:80 | http://x2.c.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2072 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2248 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2340 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3656 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.111.236.21:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3656 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
d2oq4dwfbh6gxl.cloudfront.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Kernelmoduleunloader.exe | Kernelmodule unloader |
Kernelmoduleunloader.exe | Running in wow64 |
Kernelmoduleunloader.exe | Setup. So do not show messages |
Kernelmoduleunloader.exe | attempting to unload |
Kernelmoduleunloader.exe | SCManager opened |
Kernelmoduleunloader.exe | count=0 |
Kernelmoduleunloader.exe | setup=true |
cheatengine-x86_64-SSE4-AVX2.exe | Lua thread terminated |