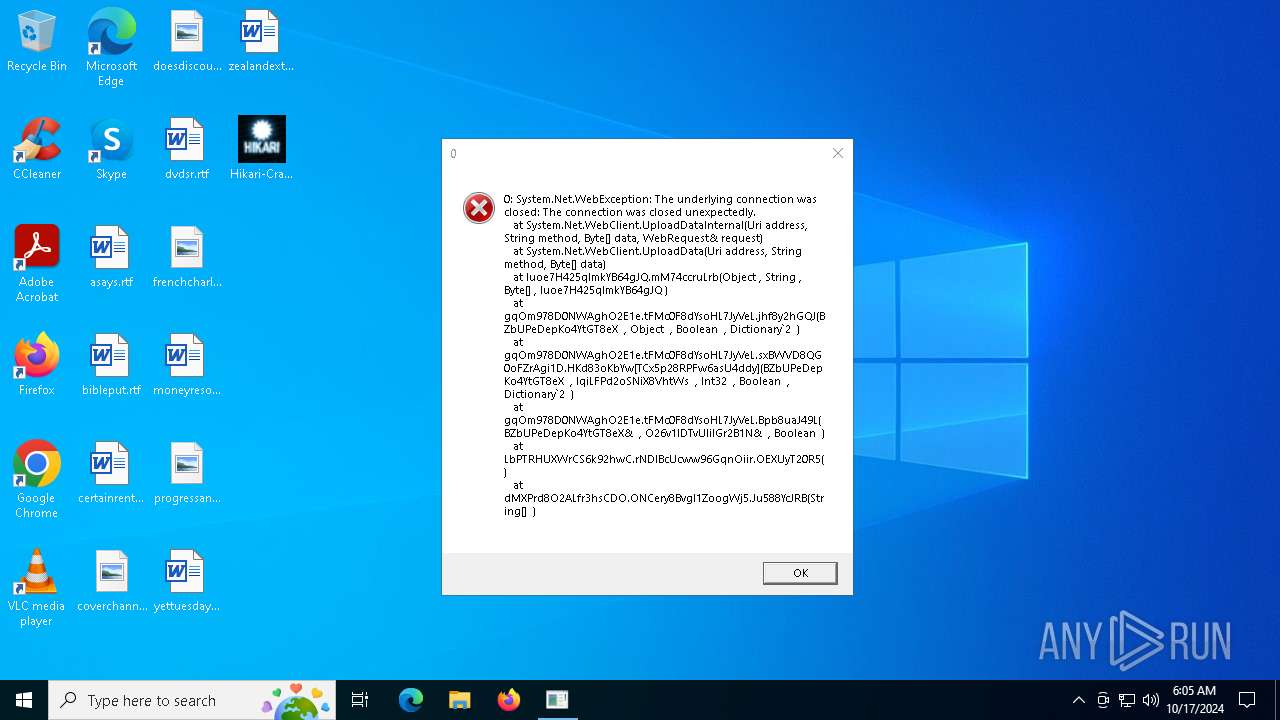
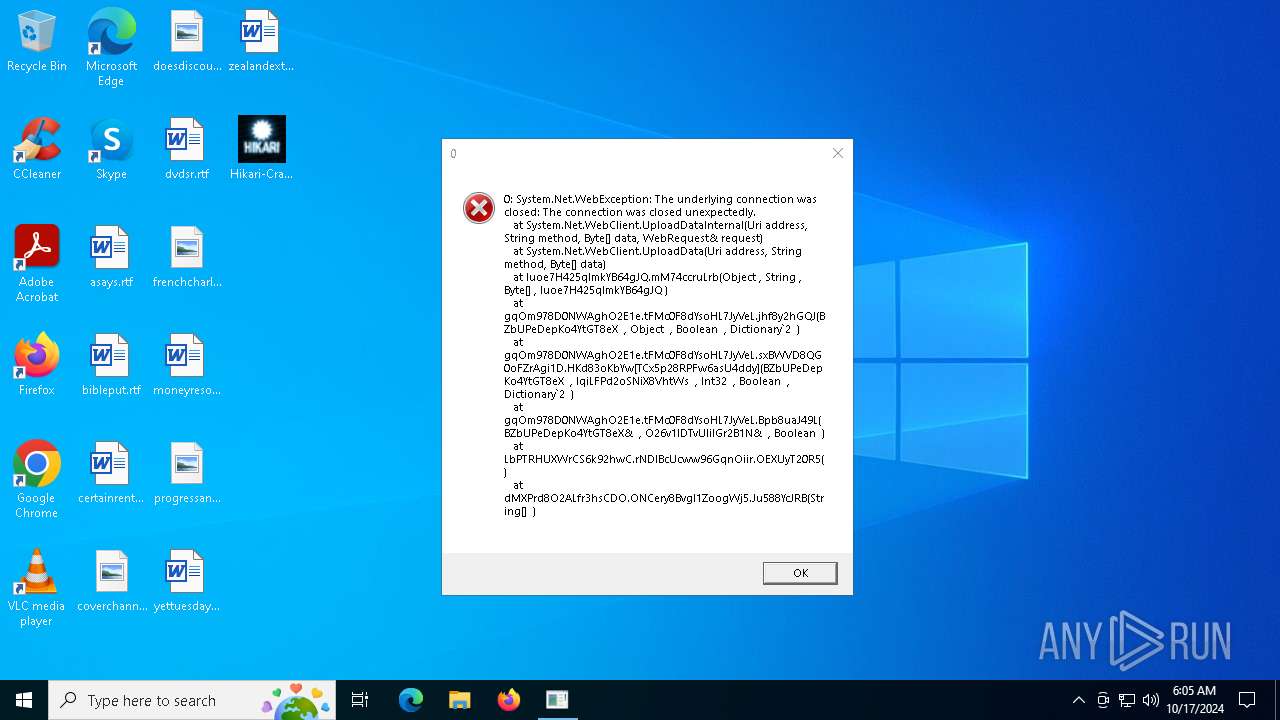
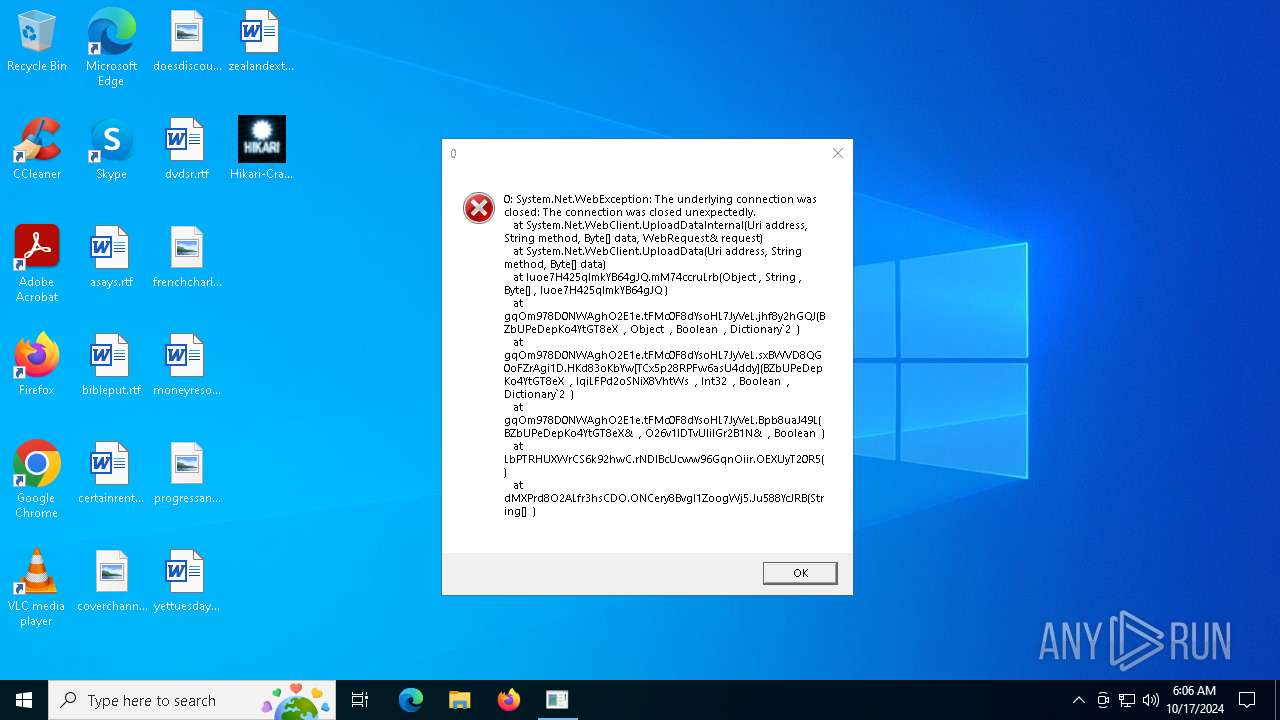
| File name: | Hikari-Cracked.exe |
| Full analysis: | https://app.any.run/tasks/22694042-713b-495e-929b-8bd824b31403 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | October 17, 2024, 06:04:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F43883A4547CD87E335BBC28A871A327 |
| SHA1: | 73519A1471972DF5D44B87941EDB9908E0670F81 |
| SHA256: | E2D84090FE7CB18110115D4E3D0368F6E1BD9BAE20B0BE018A5A9463D74A3D2D |
| SSDEEP: | 98304:Xyi3cGpQYi34Hg1NzKkFicA7xMgfPpm/fxQTHkiKEIQwsxHPcBxUrEzSMcqI45nV:PRnSuf3Od |
MALICIOUS
DARKCRYSTAL has been detected (SURICATA)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 4128)
- cmd.exe (PID: 5596)
DCRAT has been detected (YARA)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
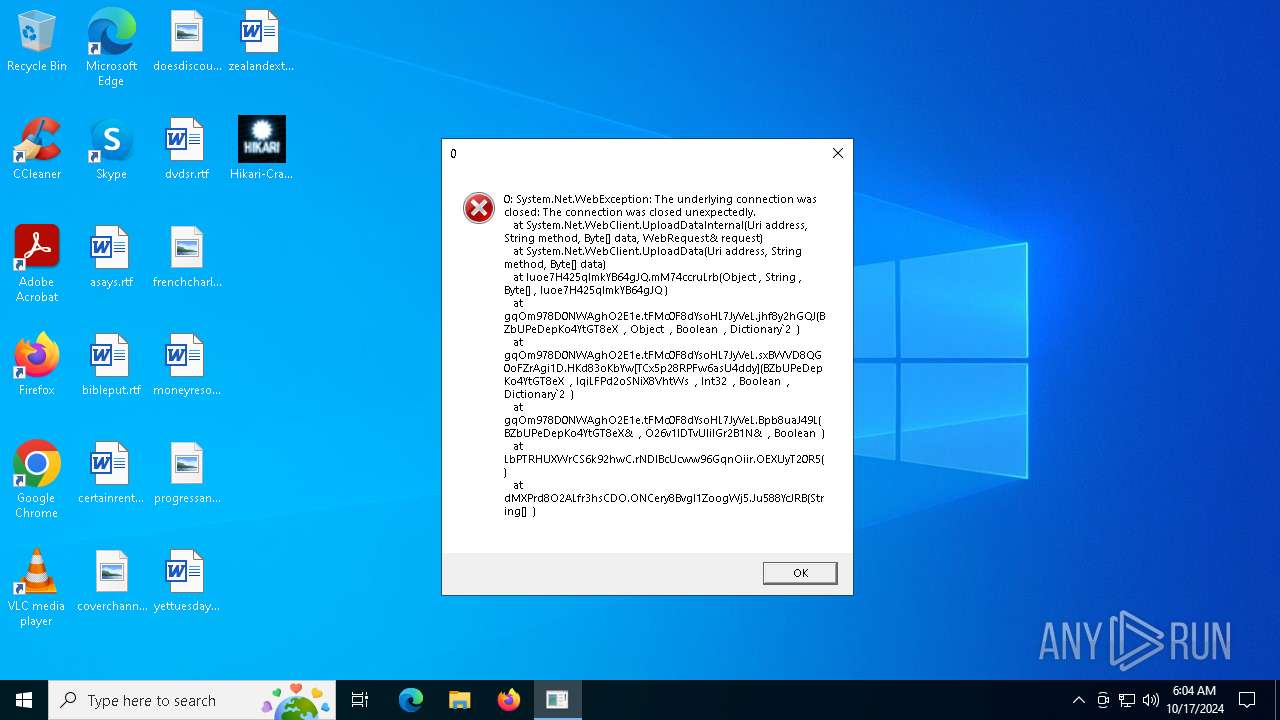
Connects to the CnC server
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 4128)
- cmd.exe (PID: 5596)
SUSPICIOUS
Executed via WMI
- schtasks.exe (PID: 7140)
- schtasks.exe (PID: 204)
- schtasks.exe (PID: 3792)
- schtasks.exe (PID: 7132)
- schtasks.exe (PID: 6024)
- schtasks.exe (PID: 6284)
- schtasks.exe (PID: 3276)
- schtasks.exe (PID: 3568)
- schtasks.exe (PID: 6168)
- schtasks.exe (PID: 2360)
- schtasks.exe (PID: 6156)
- schtasks.exe (PID: 6548)
- schtasks.exe (PID: 6436)
- schtasks.exe (PID: 6736)
- schtasks.exe (PID: 4996)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5616)
- Perfcommon.exe (PID: 7116)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
Reads security settings of Internet Explorer
- Hikari-Cracked.exe (PID: 6684)
Executable content was dropped or overwritten
- Hikari-Cracked.exe (PID: 6684)
- Perfcommon.exe (PID: 7116)
- csc.exe (PID: 2224)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
- cmd.exe (PID: 5596)
- cmd.exe (PID: 6296)
Process drops legitimate windows executable
- Perfcommon.exe (PID: 7116)
Executing commands from a ".bat" file
- wscript.exe (PID: 5616)
- Perfcommon.exe (PID: 7116)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 4128)
Starts application with an unusual extension
- cmd.exe (PID: 4128)
- cmd.exe (PID: 7148)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 6876)
Connects to the server without a host name
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
- cmd.exe (PID: 5596)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 7148)
INFO
The process uses the downloaded file
- Hikari-Cracked.exe (PID: 6684)
Process checks computer location settings
- Hikari-Cracked.exe (PID: 6684)
Checks supported languages
- Hikari-Cracked.exe (PID: 6684)
Reads the computer name
- Hikari-Cracked.exe (PID: 6684)
Changes the display of characters in the console
- cmd.exe (PID: 4128)
- cmd.exe (PID: 7148)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 6876)
.NET Reactor protector has been detected
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
Found Base64 encoded reference to WMI classes (YARA)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
Potential library load (Base64 Encoded 'LoadLibrary')
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- cmd.exe (PID: 4312)
- cmd.exe (PID: 6596)
- cmd.exe (PID: 4128)
- cmd.exe (PID: 6296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(4312) cmd.exe
C2 (1)http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads
Options
PluginConfigs
75400db8-4680-4af7-97bd-c8a76b65b9c4
0NRwTHkufxlJTzRtplqrBvzFGGtumEhem
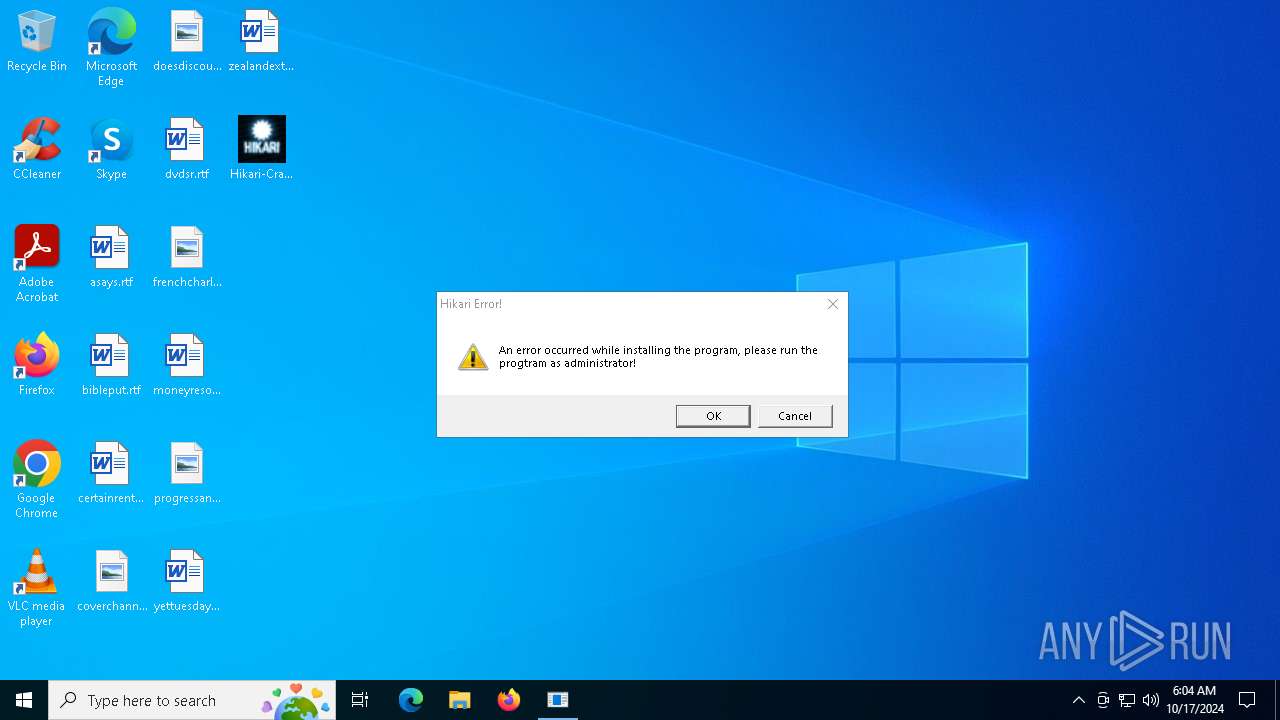
1Hikari Error!
2An error occurred while installing the program, please run the progtram as administrator!
3Warning
4OKCancel
20c484a2-7b5b-481d-bf01-55d423c9c2fd
0antivirus|w|r
31395ecd-4eed-48b9-a47f-81dbcc84ccdf
0True
1nkbihfbeogaeaoehlefnkodbefgpgknn:MetaMask
ejbalbakoplchlghecdalmeeeajnimhm:MetaMask
ibnejdfjmmkpcnlpebklmnkoeoihofec:TronLink
fnjhmkhhmkbjkkabndcnnogagogbneec:Ronin
kjmoohlgokccodicjjfebfomlbljgfhk:Ronin
fhbohimaelbohpjbbldcngcnapndodjp:BinanceChain
bfnaelmomeimhlpmgjnjophhpkkoljpa:Phantom
nphplpgoa...
2All Users
3True
2a025748-b498-4ae9-8f8c-b763dd8b5ffc
0Custom
1True
2True
3True
ff275d84-13f9-47b8-9de6-a3dfeab3ea1e
0Builds
1
Plugins (23)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAPze72QAAAAAAAAAAOAAAiELAQgAAJQAAAAGAAAAAAAAPrIAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAA5AwBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGve72QAAAAAAAAAAOAAAiELAQgAAHoAAAAGAAAAAAAAvpkAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAA3OEAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAHbb72QAAAAAAAAAAOAAAiELAQgAAIAAAAAGAAAAAAAAvp4AAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAzVsBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMvY72QAAAAAAAAAAOAAAiELAQgAAIYAAAAGAAAAAAAAHqUAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAhvEAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAG7c72QAAAAAAAAAAOAAAiELAQgAAJQAAAAGAAAAAAAA7rIAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAEroAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGH41GUAAAAAAAAAAOAAAiELAQgAAFgAAAAGAAAAAAAAHncAAAAgAAAAgAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAAAAAgAAAAAAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGra72QAAAAAAAAAAOAAAiELAQgAAK4AAAAGAAAAAAAAHs0AAAAgAAAA4AAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAgAQAAAgAAiGgBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMIE8GQAAAAAAAAAAOAAAiELAQgAAHwAAAAGAAAAAAAArpoAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAqtoAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDACLT72QAAAAAAAAAAOAAAiELAQgAAJYAAAAGAAAAAAAAbrUAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAEvAAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMzf72QAAAAAAAAAAOAAIiALAQgAAAoBAAAGAAAAAAAALikBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAAOPMBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAItzBmUAAAAAAAAAAOAAAiELAQgAAGYAAAAGAAAAAAAAXoQAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAh8EAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAPbXBGUAAAAAAAAAAOAAAiELAQgAAFYAAAAGAAAAAAAADnQAAAAgAAAAgAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAAAAAgAAC+gAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDANzW72QAAAAAAAAAAOAAAiELAQgAAH4AAAAGAAAAAAAAbpwAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAA9UcBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDANLV72QAAAAAAAAAAOAAAiELAQgAAJAAAAAGAAAAAAAAvq4AAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAA/8AAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAPHb72QAAAAAAAAAAOAAAiELAQgAAJoAAAAGAAAAAAAAzrgAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAA794AAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMXZ72QAAAAAAAAAAOAAIiALAQgAAPIAAAAGAAAAAAAAThABAAAgAAAAIAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAABgAQAAAgAARYYBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAC82/2QAAAAAAAAAAOAAAiELAQgAAHgAAAAGAAAAAAAALpYAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAPMkAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAOjQ72QAAAAAAAAAAOAAAiELAQgAAHYAAAAGAAAAAAAAbpQAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAACOMAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAbY72QAAAAAAAAAAOAAAiELAQgAALwAAAAGAAAAAAAA/tkAAAAgAAAA4AAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAgAQAAAgAA32UBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGPW72QAAAAAAAAAAOAAAiELAQgAAI4AAAAGAAAAAAAAHq0AAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAHroAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAOMi8WQAAAAAAAAAAOAAAiELAQgAAFYAAAAGAAAAAAAAvnUAAAAgAAAAgAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAAAAAgAAIkYBAAMAQIUA...
(PID) Process(6296) cmd.exe
C2 (1)http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads
Options
PluginConfigs
75400db8-4680-4af7-97bd-c8a76b65b9c4
0NRwTHkufxlJTzRtplqrBvzFGGtumEhem
1Hikari Error!
2An error occurred while installing the program, please run the progtram as administrator!
3Warning
4OKCancel
20c484a2-7b5b-481d-bf01-55d423c9c2fd
0antivirus|w|r
31395ecd-4eed-48b9-a47f-81dbcc84ccdf
0True
1nkbihfbeogaeaoehlefnkodbefgpgknn:MetaMask
ejbalbakoplchlghecdalmeeeajnimhm:MetaMask
ibnejdfjmmkpcnlpebklmnkoeoihofec:TronLink
fnjhmkhhmkbjkkabndcnnogagogbneec:Ronin
kjmoohlgokccodicjjfebfomlbljgfhk:Ronin
fhbohimaelbohpjbbldcngcnapndodjp:BinanceChain
bfnaelmomeimhlpmgjnjophhpkkoljpa:Phantom
nphplpgoa...
2All Users
3True
2a025748-b498-4ae9-8f8c-b763dd8b5ffc
0Custom
1True
2True
3True
ff275d84-13f9-47b8-9de6-a3dfeab3ea1e
0Builds
1
Plugins (4)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMzf72QAAAAAAAAAAOAAIiALAQgAAAoBAAAGAAAAAAAALikBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAAOPMBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMXZ72QAAAAAAAAAAOAAIiALAQgAAPIAAAAGAAAAAAAAThABAAAgAAAAIAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAABgAQAAAgAARYYBAAMAQIUA...
(PID) Process(6596) cmd.exe
C2 (1)http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads
Options
Plugins (21)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAPze72QAAAAAAAAAAOAAAiELAQgAAJQAAAAGAAAAAAAAPrIAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAA5AwBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGve72QAAAAAAAAAAOAAAiELAQgAAHoAAAAGAAAAAAAAvpkAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAA3OEAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAHbb72QAAAAAAAAAAOAAAiELAQgAAIAAAAAGAAAAAAAAvp4AAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAzVsBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMvY72QAAAAAAAAAAOAAAiELAQgAAIYAAAAGAAAAAAAAHqUAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAhvEAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAG7c72QAAAAAAAAAAOAAAiELAQgAAJQAAAAGAAAAAAAA7rIAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAEroAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGH41GUAAAAAAAAAAOAAAiELAQgAAFgAAAAGAAAAAAAAHncAAAAgAAAAgAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAAAAAgAAAAAAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGra72QAAAAAAAAAAOAAAiELAQgAAK4AAAAGAAAAAAAAHs0AAAAgAAAA4AAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAgAQAAAgAAiGgBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMIE8GQAAAAAAAAAAOAAAiELAQgAAHwAAAAGAAAAAAAArpoAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAqtoAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDACLT72QAAAAAAAAAAOAAAiELAQgAAJYAAAAGAAAAAAAAbrUAAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAEvAAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMzf72QAAAAAAAAAAOAAIiALAQgAAAoBAAAGAAAAAAAALikBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAAOPMBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAItzBmUAAAAAAAAAAOAAAiELAQgAAGYAAAAGAAAAAAAAXoQAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAh8EAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAPbXBGUAAAAAAAAAAOAAAiELAQgAAFYAAAAGAAAAAAAADnQAAAAgAAAAgAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAAAAAgAAC+gAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDANzW72QAAAAAAAAAAOAAAiELAQgAAH4AAAAGAAAAAAAAbpwAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAA9UcBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDANLV72QAAAAAAAAAAOAAAiELAQgAAJAAAAAGAAAAAAAAvq4AAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAA/8AAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAMXZ72QAAAAAAAAAAOAAIiALAQgAAPIAAAAGAAAAAAAAThABAAAgAAAAIAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAABgAQAAAgAARYYBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAC82/2QAAAAAAAAAAOAAAiELAQgAAHgAAAAGAAAAAAAALpYAAAAgAAAAoAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADgAAAAAgAAPMkAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAbY72QAAAAAAAAAAOAAAiELAQgAALwAAAAGAAAAAAAA/tkAAAAgAAAA4AAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAgAQAAAgAA32UBAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAGPW72QAAAAAAAAAAOAAAiELAQgAAI4AAAAGAAAAAAAAHq0AAAAgAAAAwAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAAAAAQAAAgAAHroAAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAOMi8WQAAAAAAAAAAOAAAiELAQgAAFYAAAAGAAAAAAAAvnUAAAAgAAAAgAAAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAAAAAgAAIkYBAAMAQIUA...
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 82432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
172
Monitored processes
48
Malicious processes
14
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | schtasks.exe /create /tn "csrssc" /sc MINUTE /mo 9 /tr "'C:\PortSurrogatewebBroker\csrss.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\qwbsadis.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | Perfcommon.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2280 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2360 | schtasks.exe /create /tn "OfficeClickToRunO" /sc MINUTE /mo 5 /tr "'C:\Users\All Users\PLUG\OfficeClickToRun.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3104 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\WwD8E48ugj.bat" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 717
Read events
14 690
Write events
27
Delete events
0
Modification events
| (PID) Process: | (6684) Hikari-Cracked.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (7116) Perfcommon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\0234b10fdff83d7ec741894095a1856d52fbd82d |
| Operation: | write | Name: | be18307bb23ac51b2ba308b44691ef8c6ae841a8 |
Value: H4sIAAAAAAAEAItWcraKiQnILyoJLi0qyk9PLEktT01yKsrPTi2KiUnOTdFLrUhV0sGvqriouJgIdUGp6ZnFJUWVRCgNTk0sSs5wLChAUhtanFpUHBPjmJOjAGUG+IS6x8T4p6VlJqc652QmZ4fkB5XmEWF8QGpRWnJ+bm4+RHEsAAoBUikGAQAA | |||
| (PID) Process: | (7116) Perfcommon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | cmd |
Value: "C:\PortSurrogatewebBroker\cmd.exe" | |||
| (PID) Process: | (7116) Perfcommon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | csrss |
Value: "C:\PortSurrogatewebBroker\csrss.exe" | |||
| (PID) Process: | (7116) Perfcommon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Registry |
Value: "C:\PortSurrogatewebBroker\Registry.exe" | |||
| (PID) Process: | (7116) Perfcommon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SearchApp |
Value: "C:\PortSurrogatewebBroker\SearchApp.exe" | |||
| (PID) Process: | (7116) Perfcommon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | OfficeClickToRun |
Value: "C:\Users\All Users\PLUG\OfficeClickToRun.exe" | |||
| (PID) Process: | (4312) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NRwTHkufxlJTzRtplqrBvzFGGtumEhem |
| Operation: | write | Name: | NRwTHkufxlJTzRtplqrBvzFGGtumEhem |
Value: NRwTHkufxlJTzRtplqrBvzFGGtumEhem | |||
| (PID) Process: | (4312) cmd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\cmd_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4312) cmd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\cmd_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
164
Suspicious files
3
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\kVYKXBVf.log | executable | |
MD5:D8BF2A0481C0A17A634D066A711C12E9 | SHA256:2B93377EA087225820A9F8E4F331005A0C600D557242366F06E0C1EAE003D669 | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\SIwFDgAQ.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 6684 | Hikari-Cracked.exe | C:\PortSurrogatewebBroker\Perfcommon.exe | executable | |
MD5:AC3D4CCF9A062C1009029F1FC3BBE153 | SHA256:ABC34B12B44B584EFD2B42E89121B70EDDC4BB83647B8960B5FE778342E612CF | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\jPNkXSgf.log | executable | |
MD5:E9CE850DB4350471A62CC24ACB83E859 | SHA256:7C95D3B38114E7E4126CB63AADAF80085ED5461AB0868D2365DD6A18C946EA3A | |||
| 6684 | Hikari-Cracked.exe | C:\PortSurrogatewebBroker\srxz0XiIXnuIYZ.vbe | binary | |
MD5:88C7F17F34EC06D7CB85AD4B524742E3 | SHA256:A59B97BAABC928445DDC928B0AED064FABA3552AFA6437E0A20F08CF57311C30 | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\YjSMSqLC.log | executable | |
MD5:16B480082780CC1D8C23FB05468F64E7 | SHA256:7A080D8BD178EC02C7F39F7F941479074C450C4FDD8E963C993D2FB5537C7708 | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\xlyykrAB.log | executable | |
MD5:A4F19ADB89F8D88DBDF103878CF31608 | SHA256:D0613773A711634434DB30F2E35C6892FF54EBEADF49CD254377CAECB204EAA4 | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\yrJZkbqB.log | executable | |
MD5:E84DCD8370FAC91DE71DEF8DCF09BFEC | SHA256:DD7AC164E789CAD96D30930EFE9BBA99698473EDEA38252C2C0EA44043FB1DB5 | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\fZWtQWfm.log | executable | |
MD5:5EE7E079F998F80293B3467CE6A5B4AE | SHA256:A3AE7E97703E694C479E3B460F89C16B4A511626E351145532D1A2F3BA051779 | |||
| 7116 | Perfcommon.exe | C:\Users\admin\Desktop\amEunZQy.log | executable | |
MD5:51B1964F31C557AE8C2B01EA164ABD9F | SHA256:AF584F142A9A5A79355B212F8D7A2E3793E33FF23D50FDE591FB2F3E49BF308C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
32
DNS requests
11
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7044 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7044 | RUXIMICS.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4312 | cmd.exe | POST | — | 213.159.64.146:80 | http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads.php | unknown | — | — | malicious |
5596 | cmd.exe | POST | — | 213.159.64.146:80 | http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads.php | unknown | — | — | malicious |
6296 | cmd.exe | POST | — | 213.159.64.146:80 | http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads.php | unknown | — | — | malicious |
4128 | cmd.exe | POST | — | 213.159.64.146:80 | http://213.159.64.146/5Generator/Processorline6/pipe6/7ProtonDbTemp/linuxWindows/mariadbpublic/3BetterWp/LocaluniversalWordpressdownloads/track/Universal/Secure5LocalGenerator/videoline_SecureDefaultsqlLinuxWindowsGeneratoruploads.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7044 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.212.110.186:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7044 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4312 | cmd.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4312 | cmd.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
6296 | cmd.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
6296 | cmd.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4128 | cmd.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4128 | cmd.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5596 | cmd.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5596 | cmd.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |