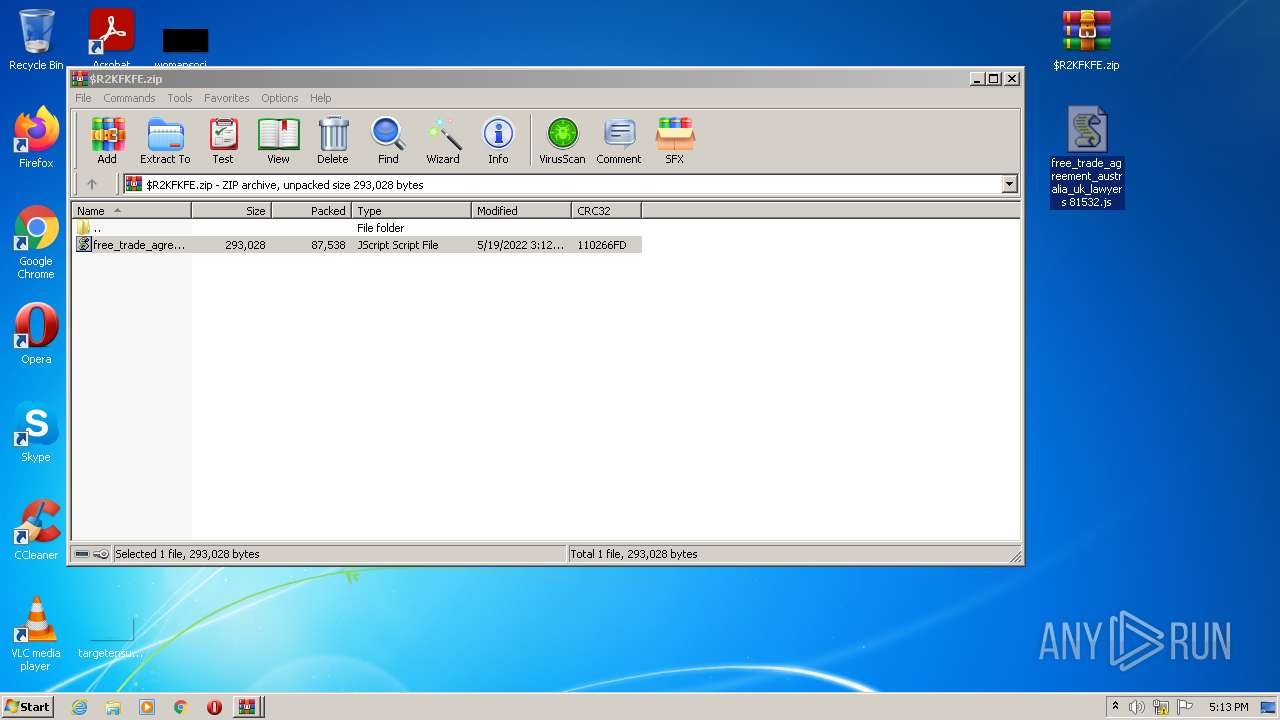
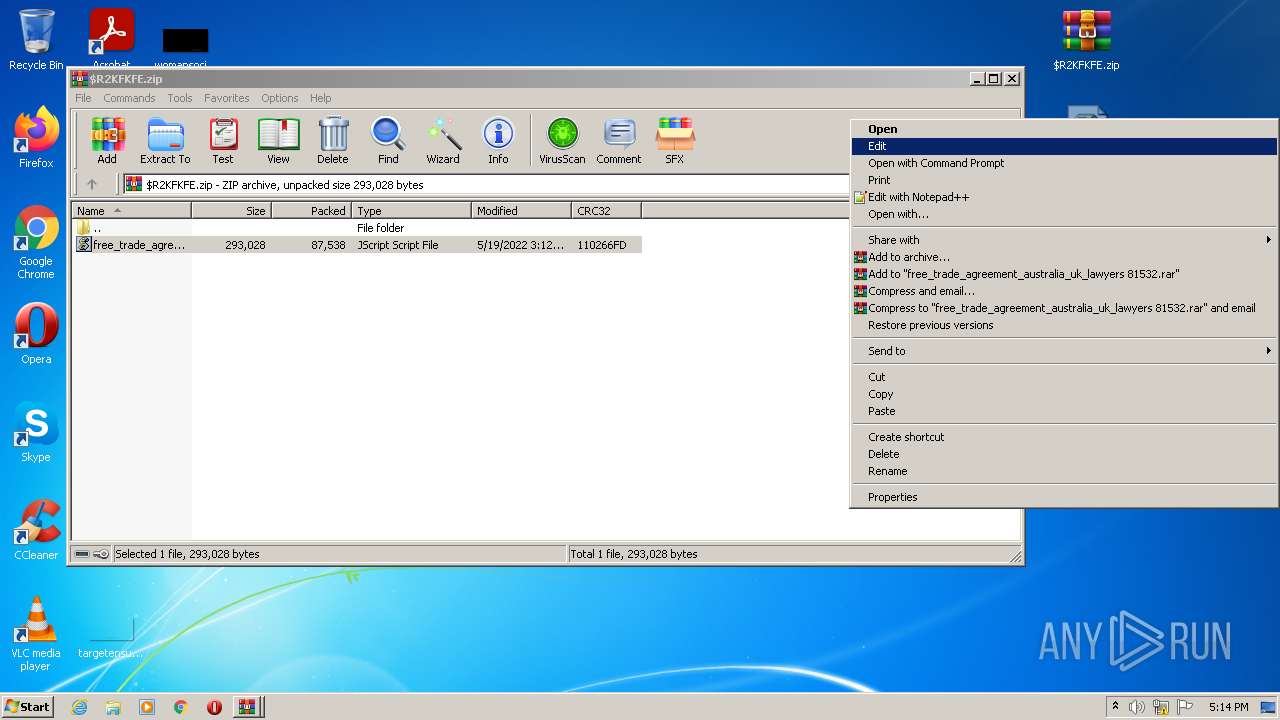
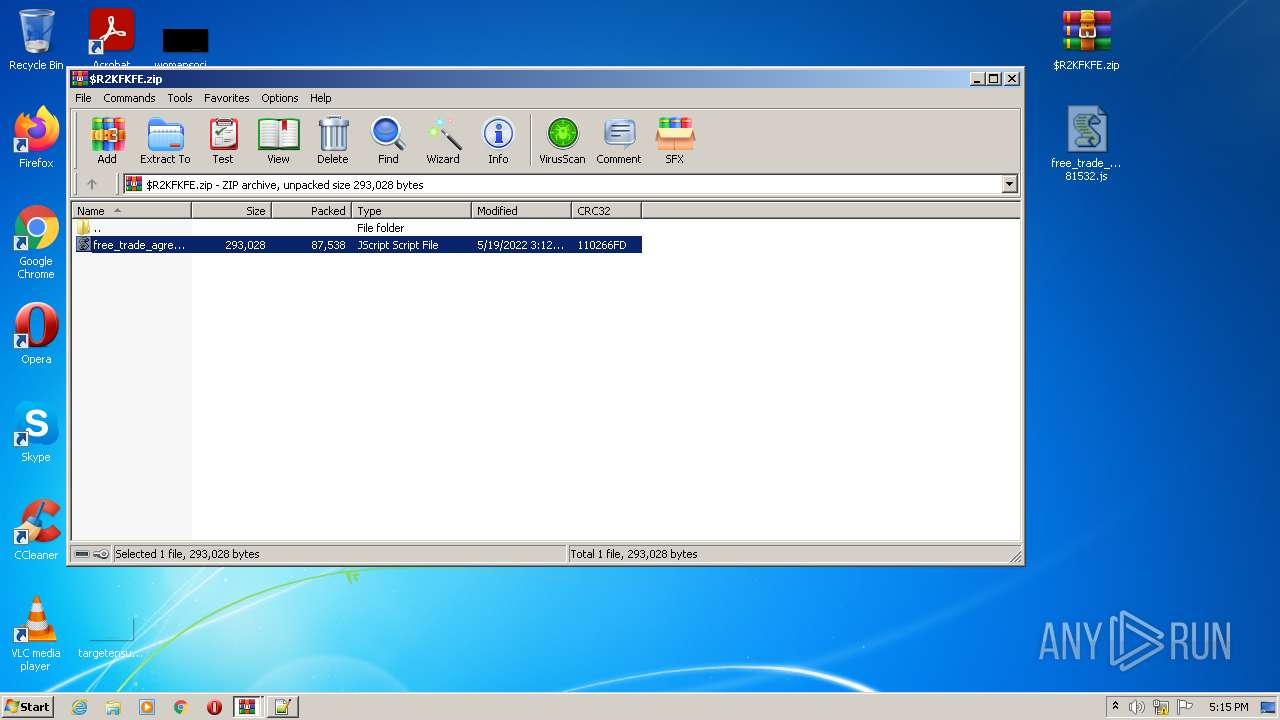
| File name: | $R2KFKFE.zip.7z |
| Full analysis: | https://app.any.run/tasks/590d47d3-e9cf-41b1-9572-fcf7d3b1ae62 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 16:13:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 80114163DFD386AC3CA5F26915FC7C85 |
| SHA1: | CF58D91B6FC990D5F771DBB2ECE24B34EC8B7A92 |
| SHA256: | E2D6D34E8F639EF470CF326673B70626FED6AF4EBF1FD0A226A024CFFBA11773 |
| SSDEEP: | 1536:gpZsjkG8QIvYZNHHv4bd1djVWUVrXWDeOMaji7LUHfKaGrLIR1MS79JfHbeD:WQkG8mnvijV/VrXieOLzHSjIRd79J/bI |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 2608)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 924)
- WinRAR.exe (PID: 2380)
- WScript.exe (PID: 2608)
- WScript.exe (PID: 1684)
Checks supported languages
- WinRAR.exe (PID: 924)
- WinRAR.exe (PID: 2380)
- WScript.exe (PID: 2608)
- WScript.exe (PID: 1684)
- notepad++.exe (PID: 1380)
Adds / modifies Windows certificates
- WScript.exe (PID: 2608)
INFO
Manual execution by user
- WinRAR.exe (PID: 2380)
- WScript.exe (PID: 2608)
- WScript.exe (PID: 1684)
- notepad++.exe (PID: 1380)
Checks Windows Trust Settings
- WScript.exe (PID: 2608)
- WScript.exe (PID: 1684)
Reads settings of System Certificates
- WScript.exe (PID: 2608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
40
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\$R2KFKFE.zip.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
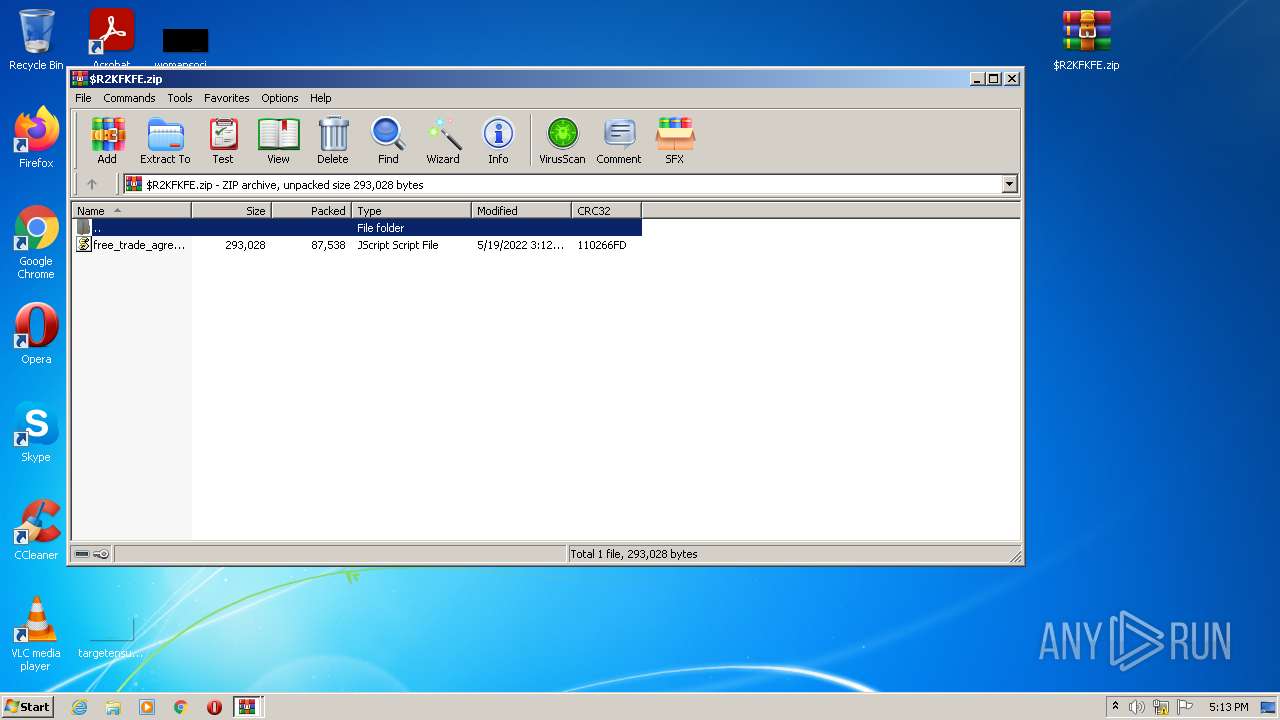
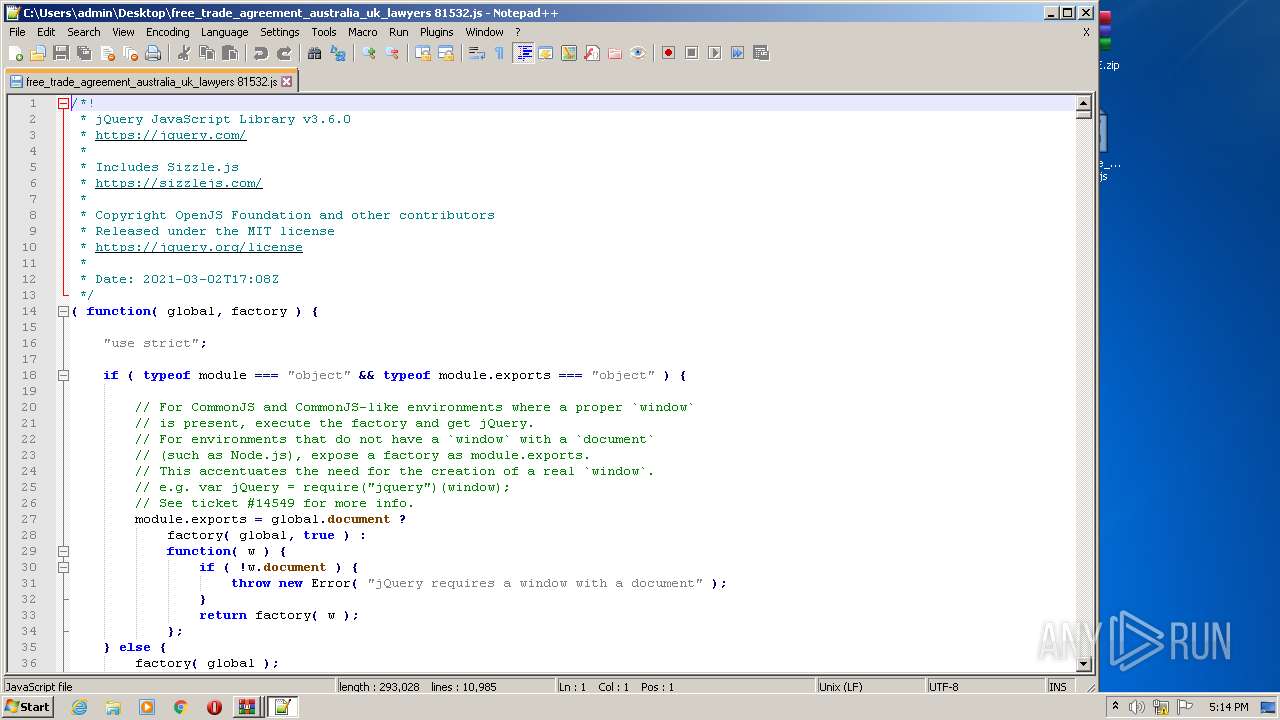
| 1380 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\free_trade_agreement_australia_uk_lawyers 81532.js" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1684 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\free_trade_agreement_australia_uk_lawyers 81532.js" | C:\Windows\System32\WScript.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\$R2KFKFE.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2608 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\free_trade_agreement_australia_uk_lawyers 81532.js" | C:\Windows\System32\WScript.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
5 822
Read events
5 760
Write events
59
Delete events
3
Modification events
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\$R2KFKFE.zip.7z | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2380.35637\free_trade_agreement_australia_uk_lawyers 81532.js | text | |
MD5:— | SHA256:— | |||
| 2608 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2608 | WScript.exe | C:\Users\admin\AppData\Local\Temp\Cab7022.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2608 | WScript.exe | C:\Users\admin\AppData\Local\Temp\Tar7023.tmp | cat | |
MD5:— | SHA256:— | |||
| 924 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb924.34556\$R2KFKFE.zip | compressed | |
MD5:— | SHA256:— | |||
| 2608 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2608 | WScript.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?412beb2394654c8f | US | compressed | 60.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | WScript.exe | 195.113.57.133:443 | www.labbunnies.eu | CESNET z.s.p.o. | CZ | unknown |
2608 | WScript.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
2608 | WScript.exe | 93.114.184.91:443 | www.lenovob2bportal.com | NetConnex Broadband Ltd. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.labbunnies.eu |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
www.lenovob2bportal.com |
| unknown |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|