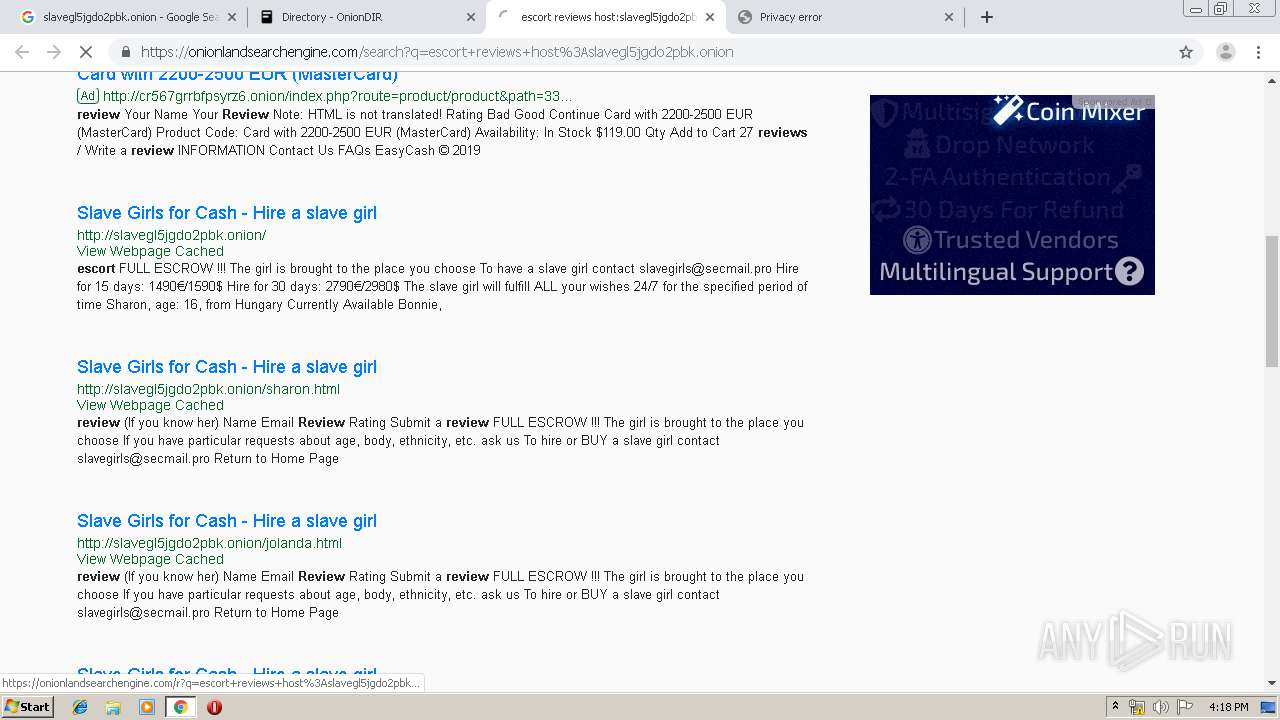
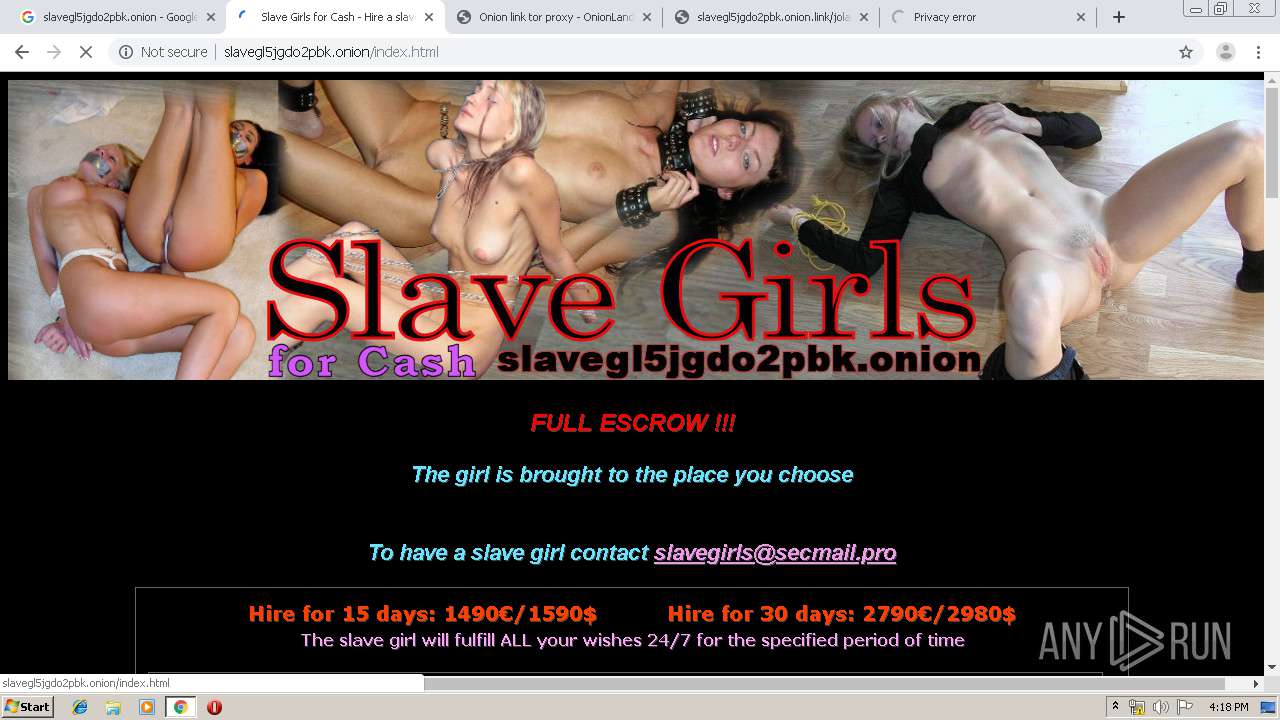
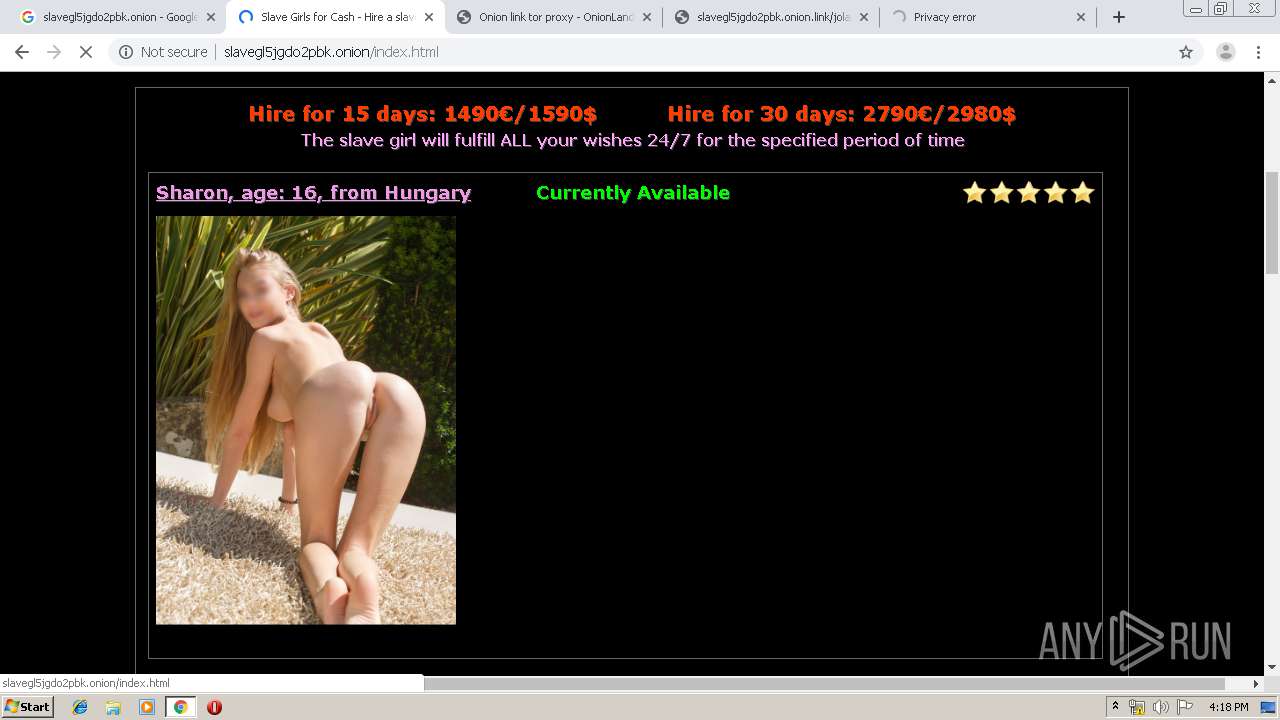
| URL: | https://www.google.com/search?sxsrf=ACYBGNTl6duI9ZAd-5ZuCLKmSZxnOl6-VA%3A1575907998958&ei=nnLuXfb8ObLl9AO3zKmoAg&q=slavegl5jgdo2pbk.onion |
| Full analysis: | https://app.any.run/tasks/ff19011a-b6be-4082-abe3-417f4d6498d9 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2019, 16:15:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 11D959D097FD4CCFCE25D240896B828B |
| SHA1: | 251E97859EC0B392E51A1AC0141A5D273AAC2F4F |
| SHA256: | E2C8B9F4ECF1F8D776196960CB6FCF1B1C8C10BE6E861AE11D41D1354138BA38 |
| SSDEEP: | 3:N8DSLIwAEXGrODYkm2V/pxLATIIAWSSbEdcQdcZLdYiJzG33FTn2VEQ/:2OLIwBGoYvyxL1SEdGKqzG33p2x |
MALICIOUS
Connects to CnC server
- chrome.exe (PID: 4048)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1648)
INFO
Reads the hosts file
- chrome.exe (PID: 1648)
- chrome.exe (PID: 4048)
Application launched itself
- chrome.exe (PID: 1648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
37
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8626912683514997187 --mojo-platform-channel-handle=3864 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1260884998876621524 --mojo-platform-channel-handle=3720 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11906020530833833163 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2512 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6d90a9d0,0x6d90a9e0,0x6d90a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=159215486012556266 --mojo-platform-channel-handle=4372 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2946166254184232124 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2248 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8636984836845526584 --mojo-platform-channel-handle=3472 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://www.google.com/search?sxsrf=ACYBGNTl6duI9ZAd-5ZuCLKmSZxnOl6-VA%3A1575907998958&ei=nnLuXfb8ObLl9AO3zKmoAg&q=slavegl5jgdo2pbk.onion" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2601158240051752060 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3800 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,1110404636015514688,11924670868073316883,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=15012216678681496531 --mojo-platform-channel-handle=4244 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
642
Read events
533
Write events
104
Delete events
5
Modification events
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1648-13220381753752125 |
Value: 259 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (1648) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
105
Text files
215
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\bae8441d-9b01-4888-99f4-5e3f4917818b.tmp | — | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF3995e1.TMP | text | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF399620.TMP | text | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF39963f.TMP | text | |
MD5:— | SHA256:— | |||
| 1648 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
97
DNS requests
50
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
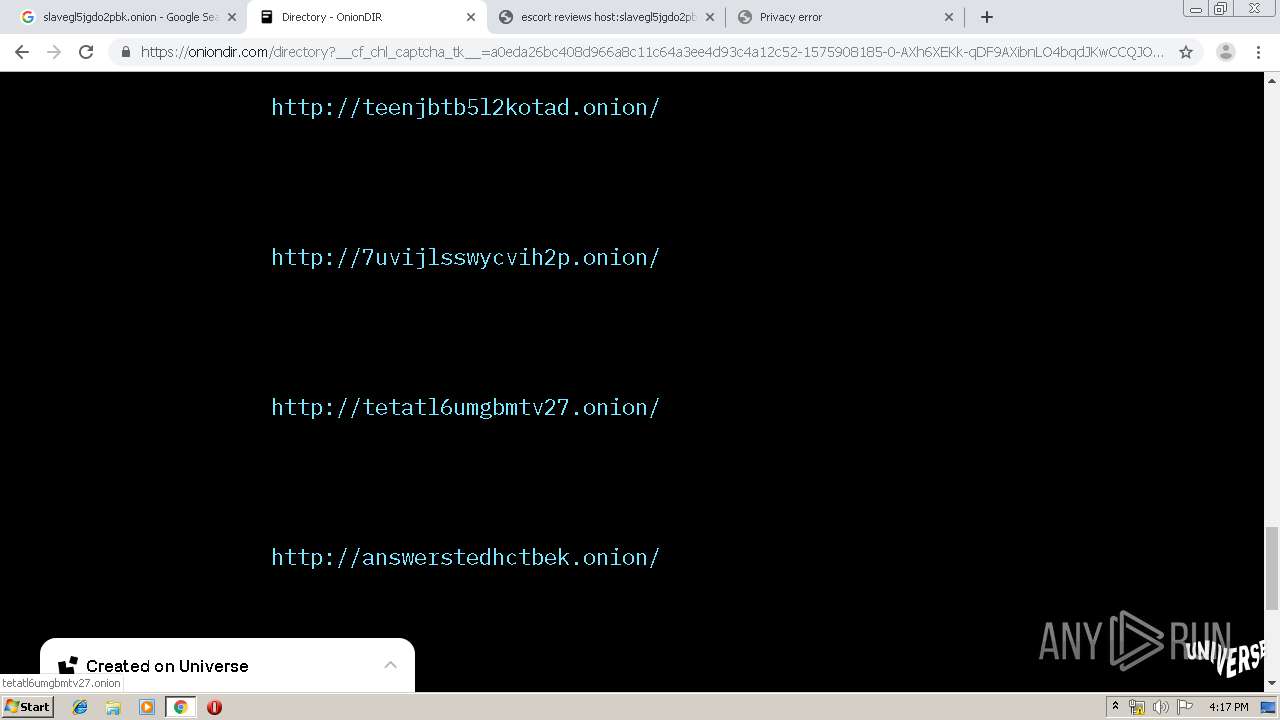
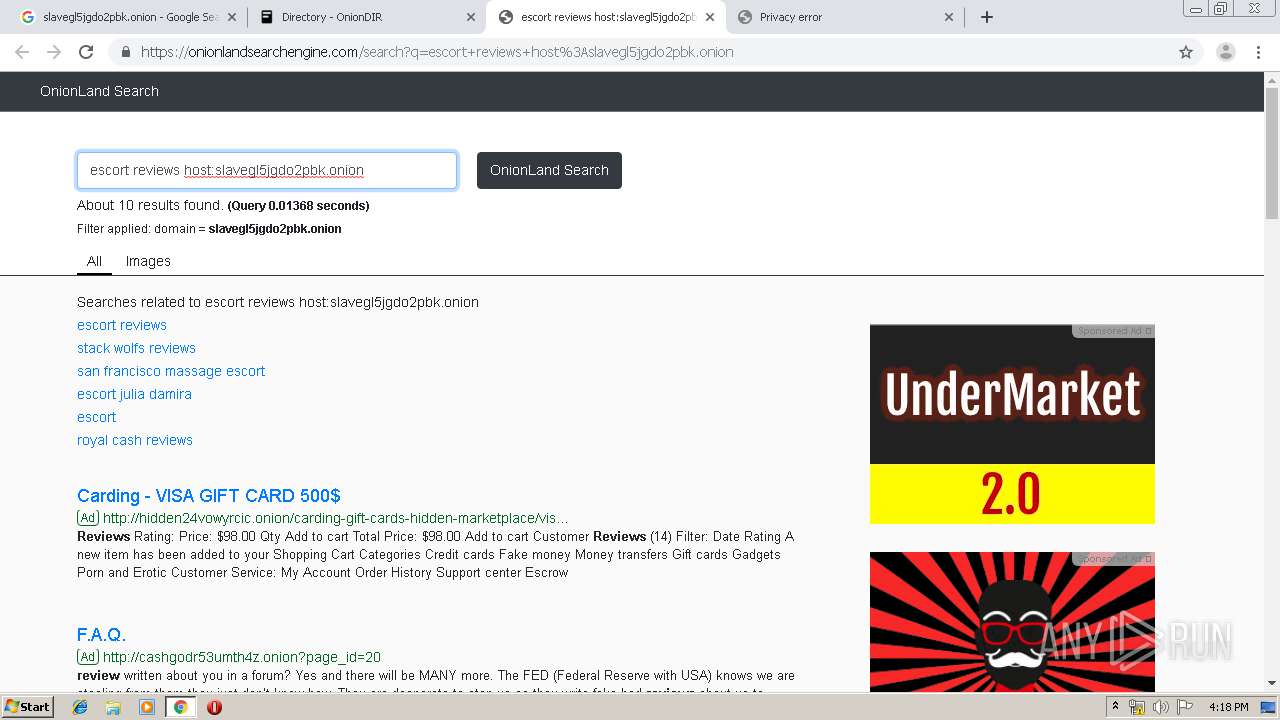
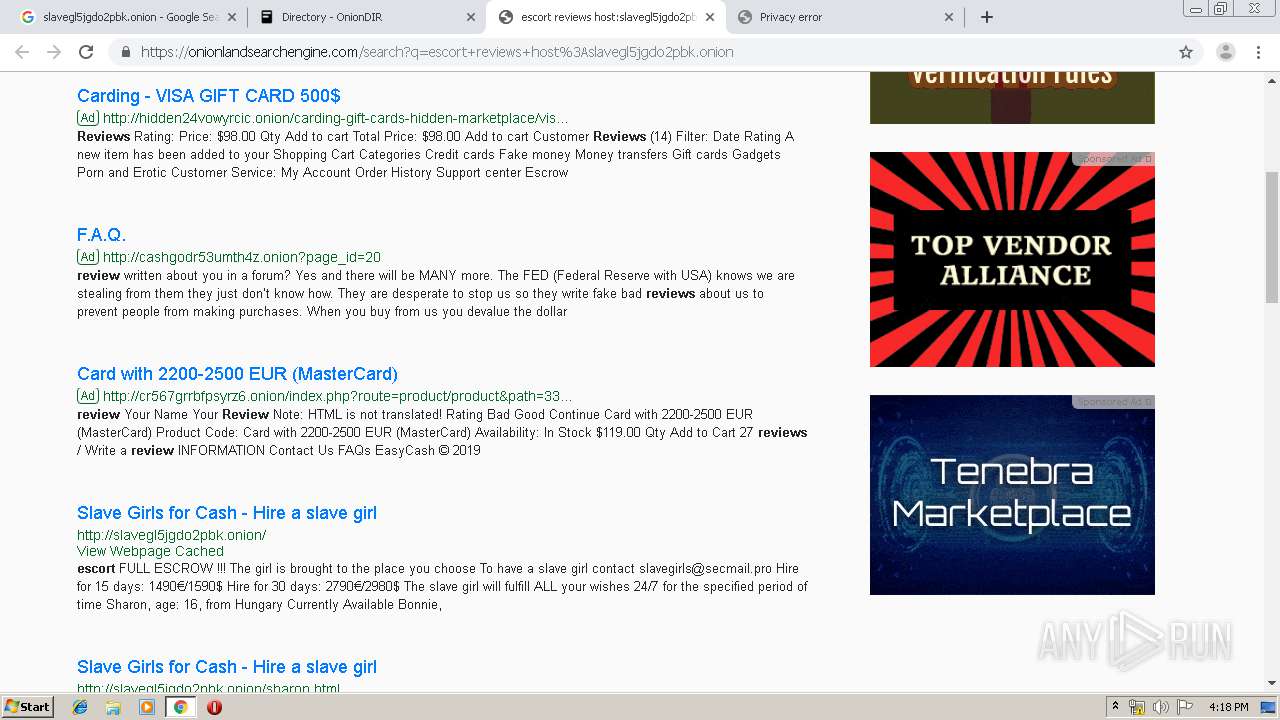
4048 | chrome.exe | GET | 200 | 103.198.0.111:80 | http://slavegl5jgdo2pbk.onion.link/favicon.ico | SG | — | — | malicious |
4048 | chrome.exe | GET | 204 | 172.217.169.163:80 | http://www.gstatic.com/generate_204 | US | — | — | whitelisted |
4048 | chrome.exe | GET | 200 | 103.198.0.111:80 | http://slavegl5jgdo2pbk.onion.link/jolanda.html | SG | — | — | malicious |
4048 | chrome.exe | GET | 302 | 216.58.206.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 522 b | whitelisted |
4048 | chrome.exe | GET | 200 | 10.248.44.225:80 | http://slavegl5jgdo2pbk.onion/H/Bonnie1.jpg | unknown | image | 118 Kb | unknown |
4048 | chrome.exe | GET | 302 | 216.58.206.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 517 b | whitelisted |
4048 | chrome.exe | GET | 200 | 10.248.44.225:80 | http://slavegl5jgdo2pbk.onion/index.html | unknown | html | 1.39 Kb | unknown |
4048 | chrome.exe | GET | 200 | 10.248.44.225:80 | http://slavegl5jgdo2pbk.onion/H/Sharon3.jpg | unknown | image | 248 Kb | unknown |
4048 | chrome.exe | GET | 200 | 10.248.44.225:80 | http://slavegl5jgdo2pbk.onion/H/Bonnie2.jpg | unknown | image | 123 Kb | unknown |
4048 | chrome.exe | GET | 200 | 10.248.44.225:80 | http://slavegl5jgdo2pbk.onion/Girls/back.jpg | unknown | image | 178 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4048 | chrome.exe | 172.217.169.100:443 | www.google.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 216.58.206.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 172.217.17.206:443 | apis.google.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 172.217.169.142:443 | ogs.google.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 172.217.17.194:443 | adservice.google.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 172.217.169.194:443 | adservice.google.com.ua | Google Inc. | US | unknown |
4048 | chrome.exe | 216.58.206.195:443 | id.google.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 172.217.17.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 216.58.206.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
4048 | chrome.exe | 151.101.129.140:443 | reddit.com | Fastly | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
adservice.google.com |
| whitelisted |
adservice.google.com.ua |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to .onion proxy Domain (onion.to) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
4048 | chrome.exe | A Network Trojan was detected | ET CNC Ransomware Tracker Reported CnC Server group 23 |
1080 | svchost.exe | A Network Trojan was detected | ET POLICY DNS Query to .onion proxy Domain (onion.link) |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |