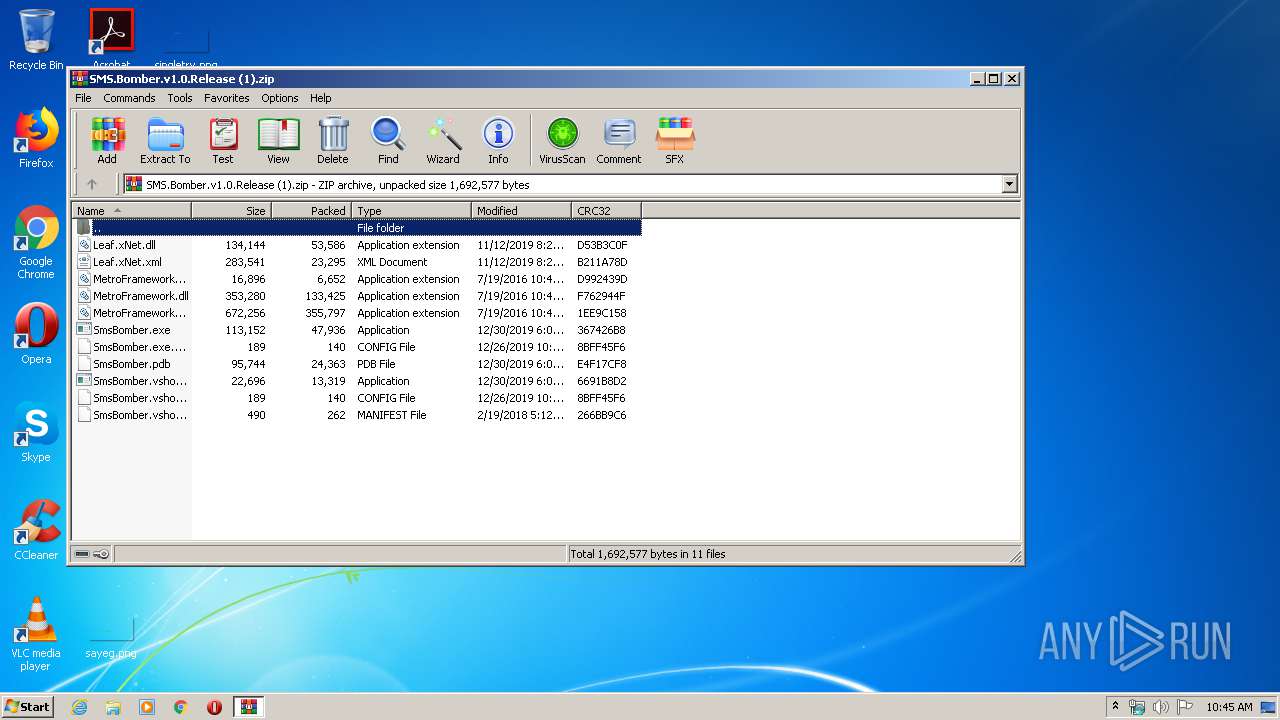
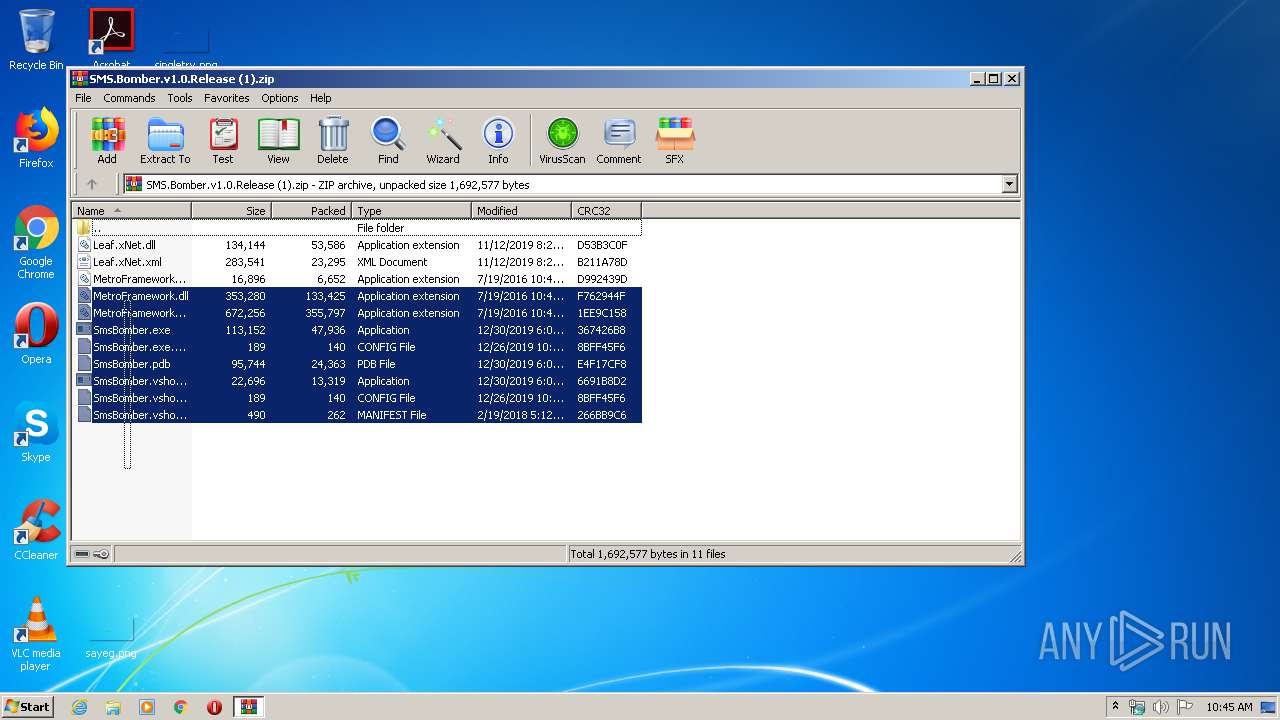
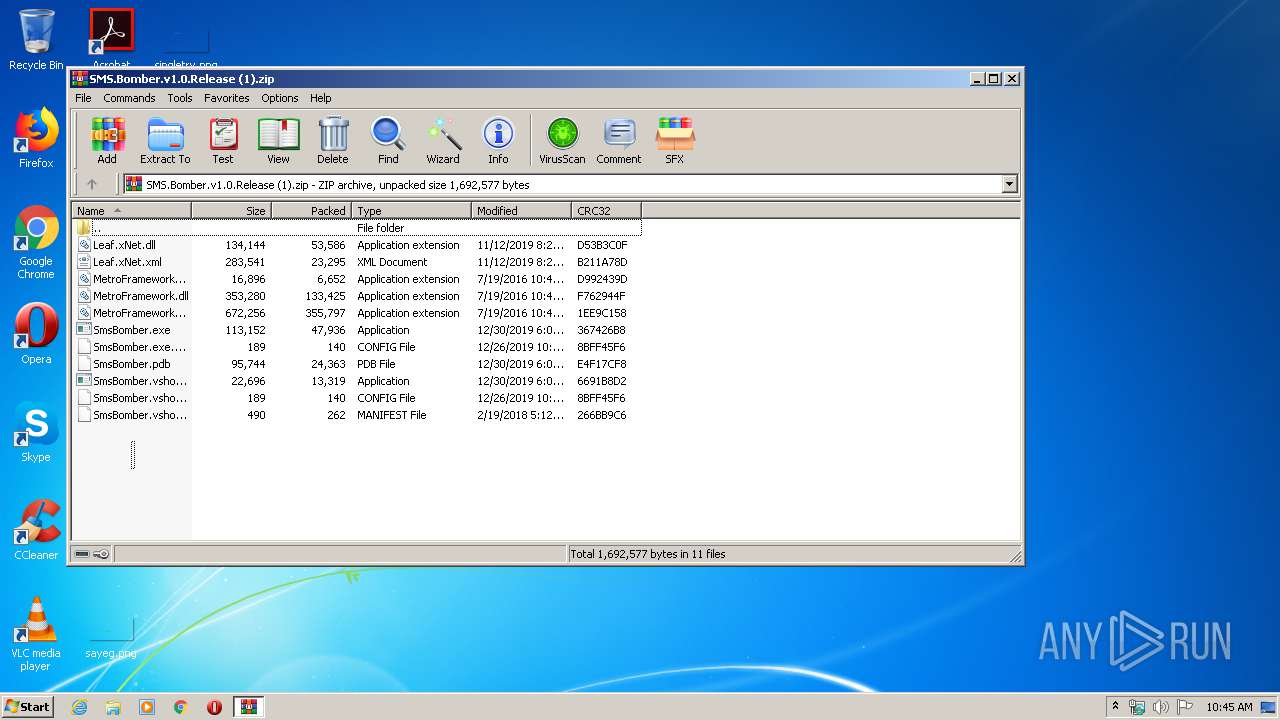
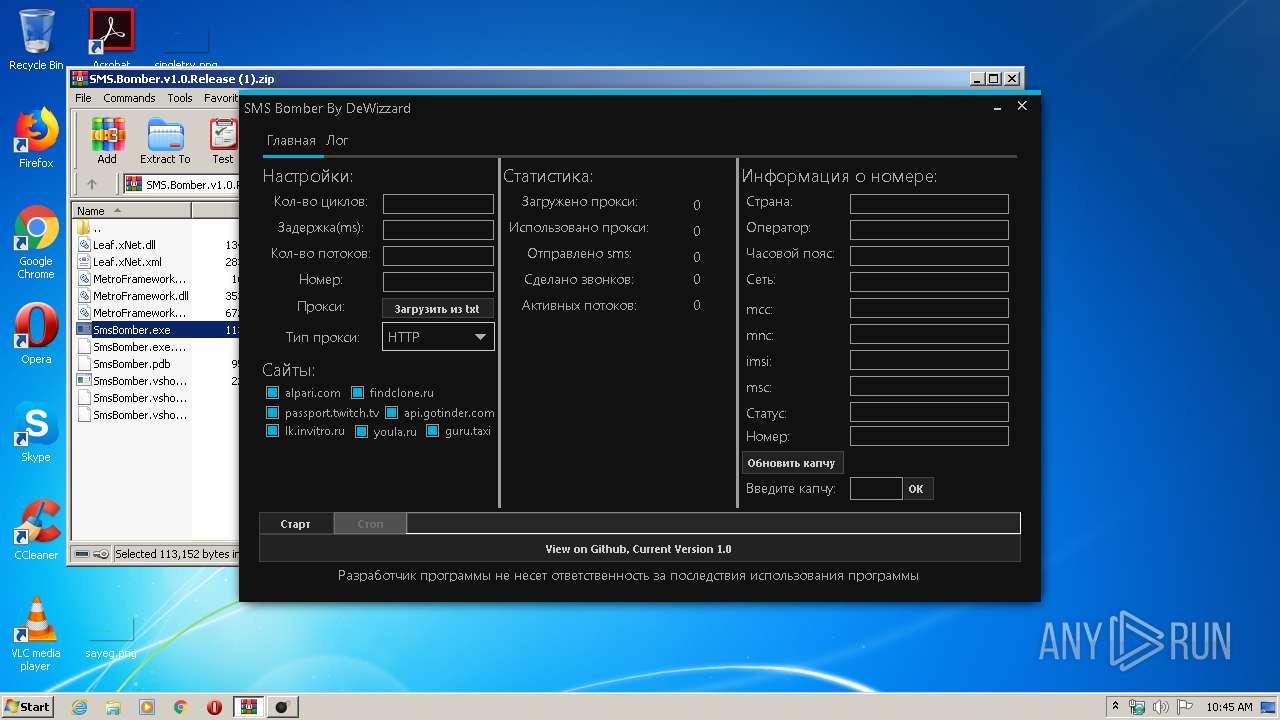
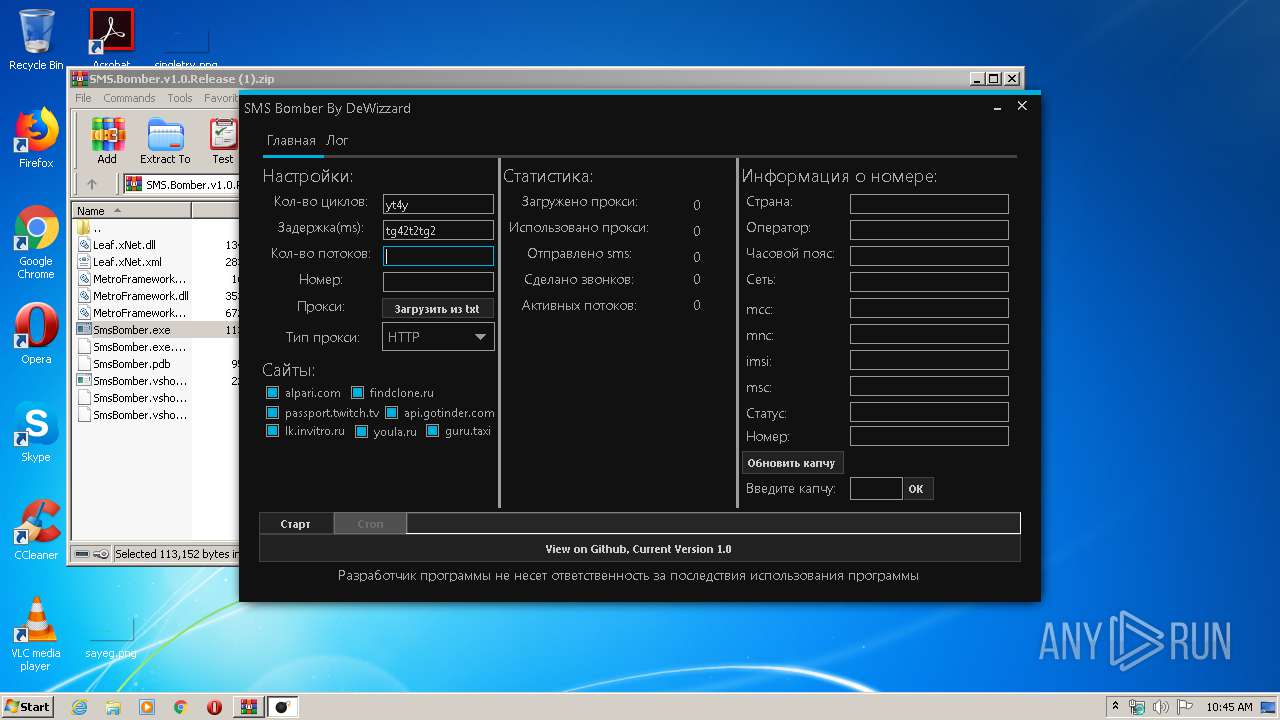
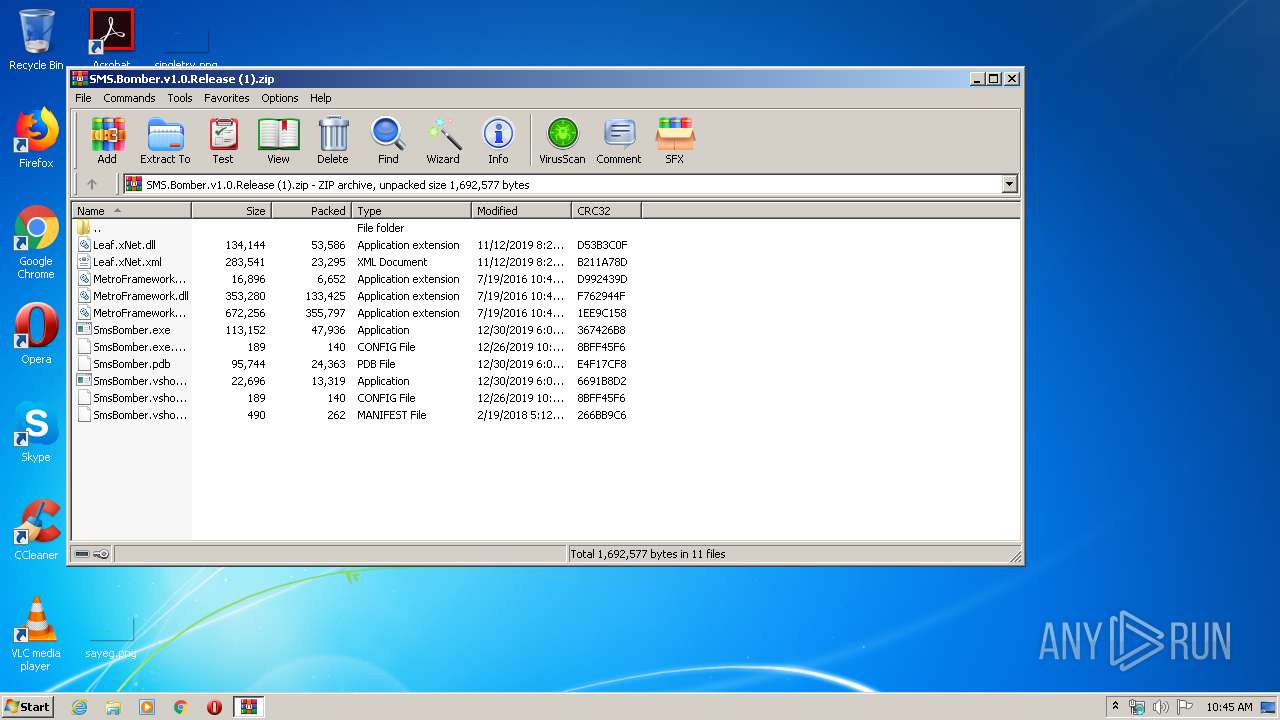
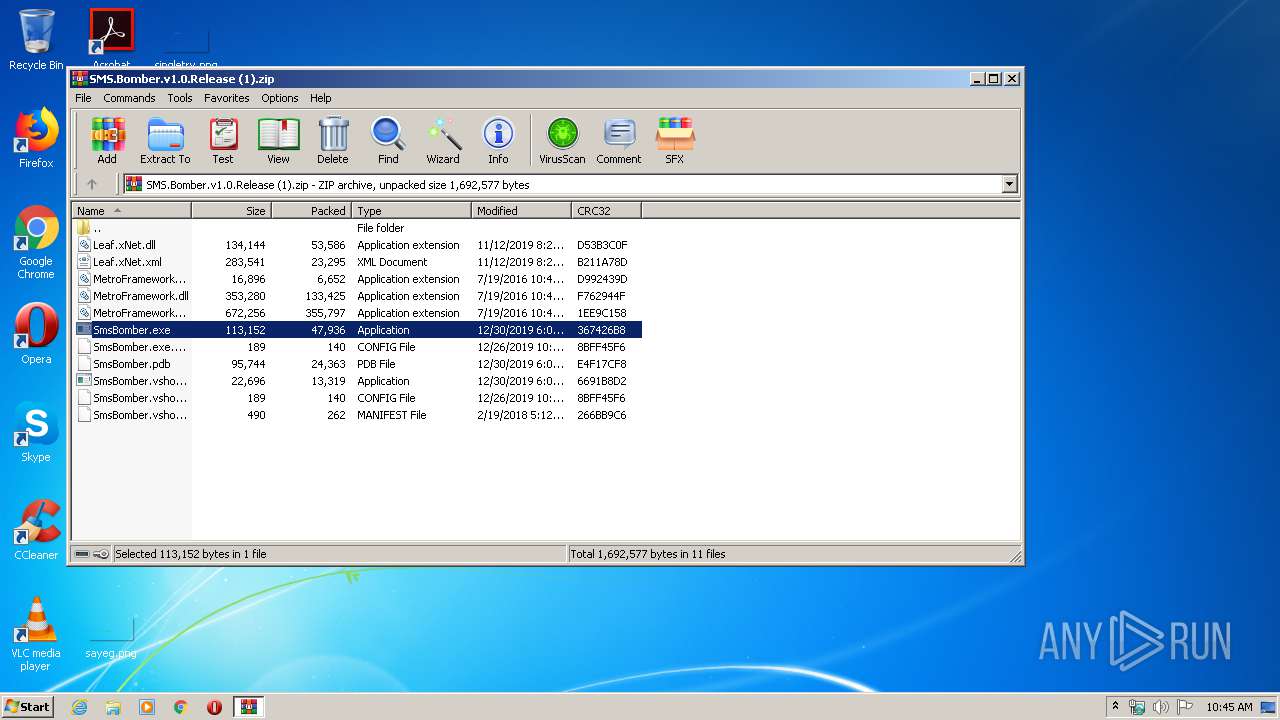
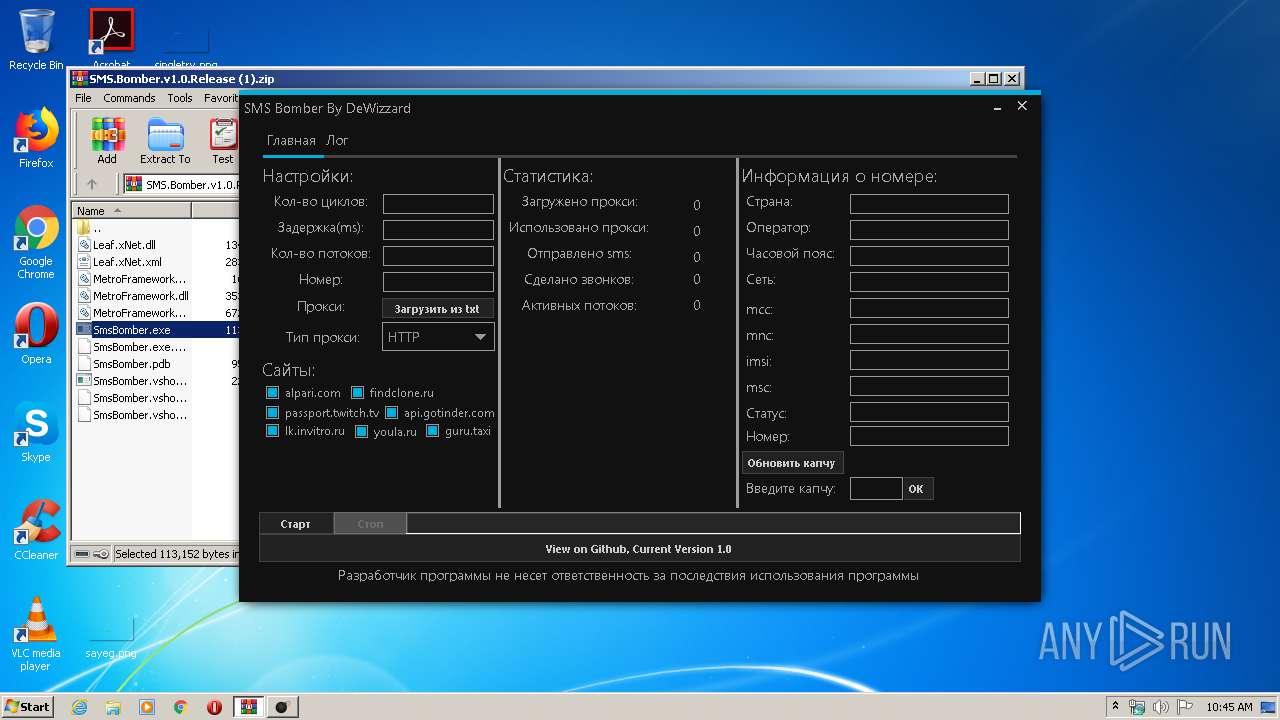
| File name: | SMS.Bomber.v1.0.Release (1).zip |
| Full analysis: | https://app.any.run/tasks/41082a55-5317-4c6b-a792-e71d716ba5da |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2020, 09:44:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4BA7153AB005AE8376A2E51F17555A0A |
| SHA1: | 00694EAC06526CC0ABD8B0FC415499D4461CAC69 |
| SHA256: | E2C5ADA0A675C66E39E4A30307A7210F80056035E0346B1A9957D3D99392EBBE |
| SSDEEP: | 12288:5AKKszDnqorsz/rw1+BqbkBm5yJ4M5FJy1dDj23qe1:5AaDqor/1tbkRJ55Fud3260 |
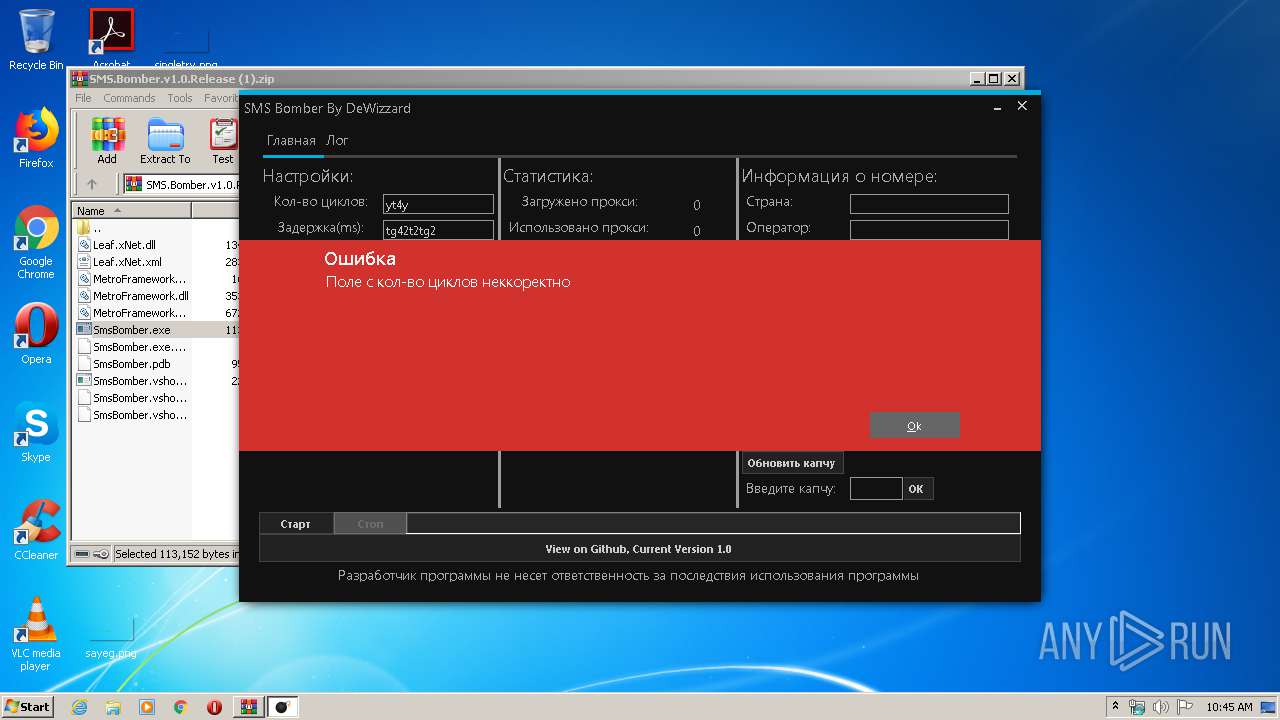
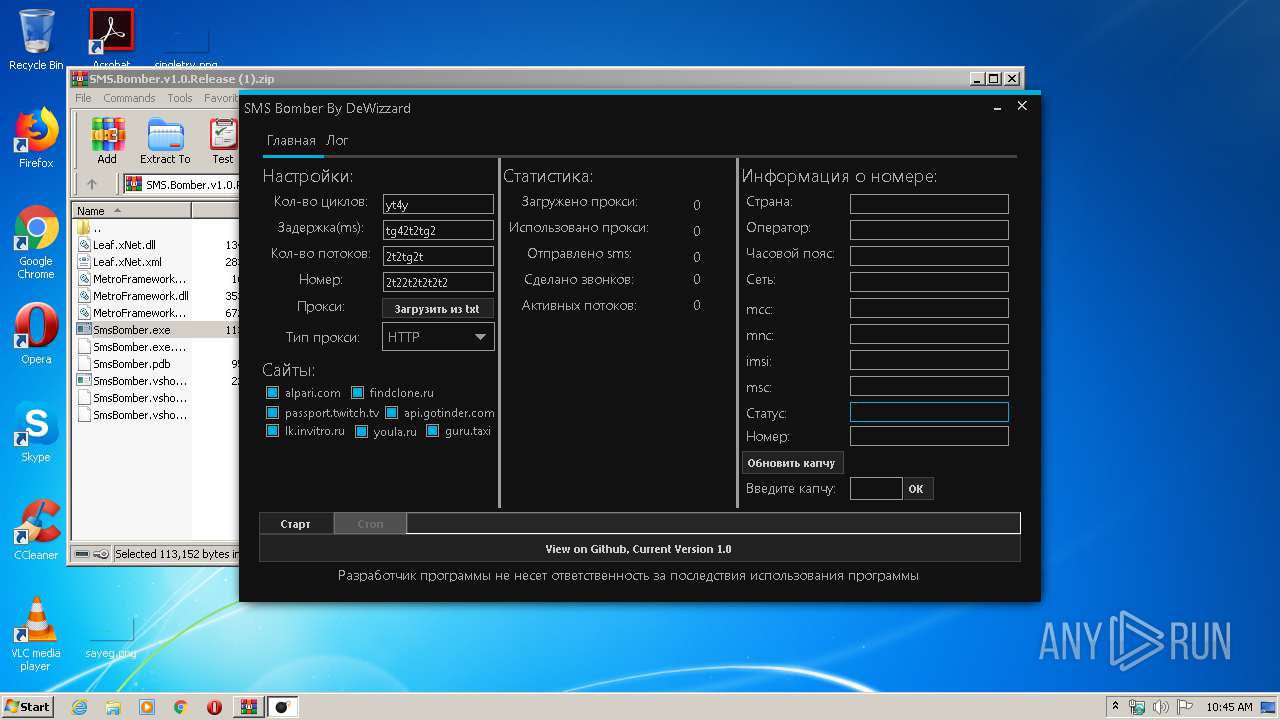
MALICIOUS
Loads dropped or rewritten executable
- SmsBomber.exe (PID: 1940)
- SmsBomber.exe (PID: 3624)
Application was dropped or rewritten from another process
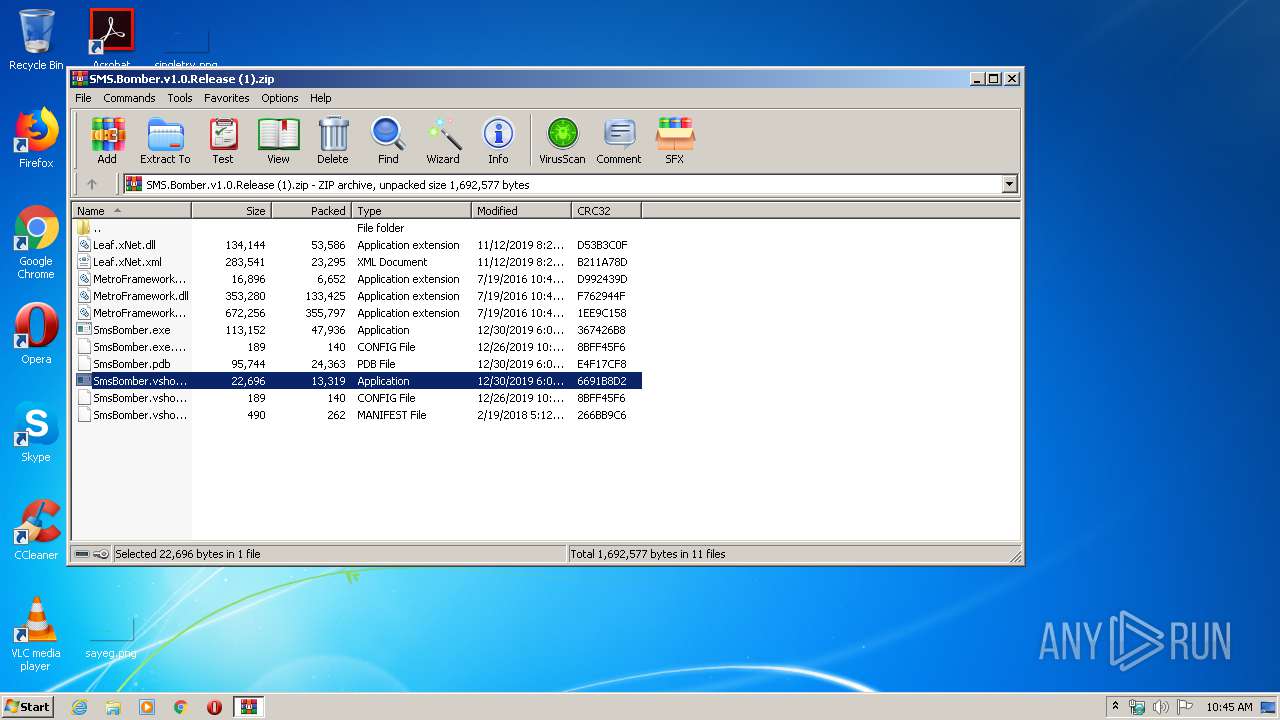
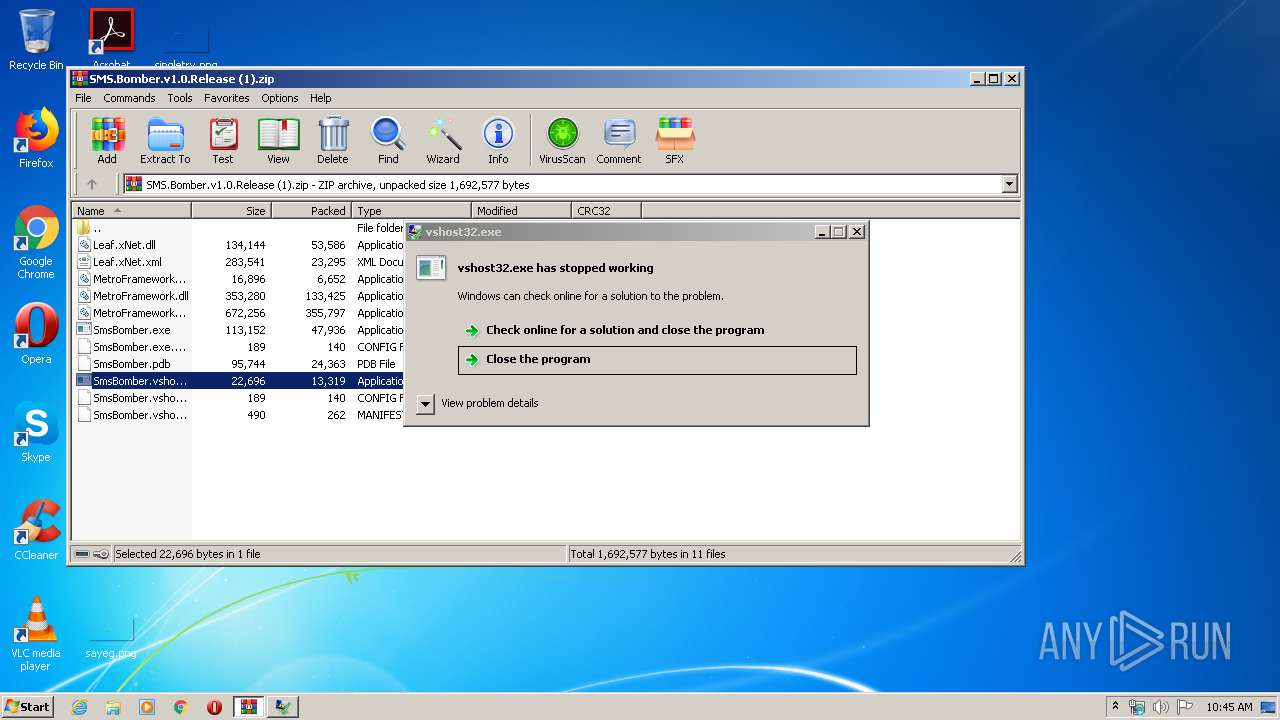
- SmsBomber.vshost.exe (PID: 3356)
- SmsBomber.exe (PID: 3624)
- SmsBomber.exe (PID: 1940)
SUSPICIOUS
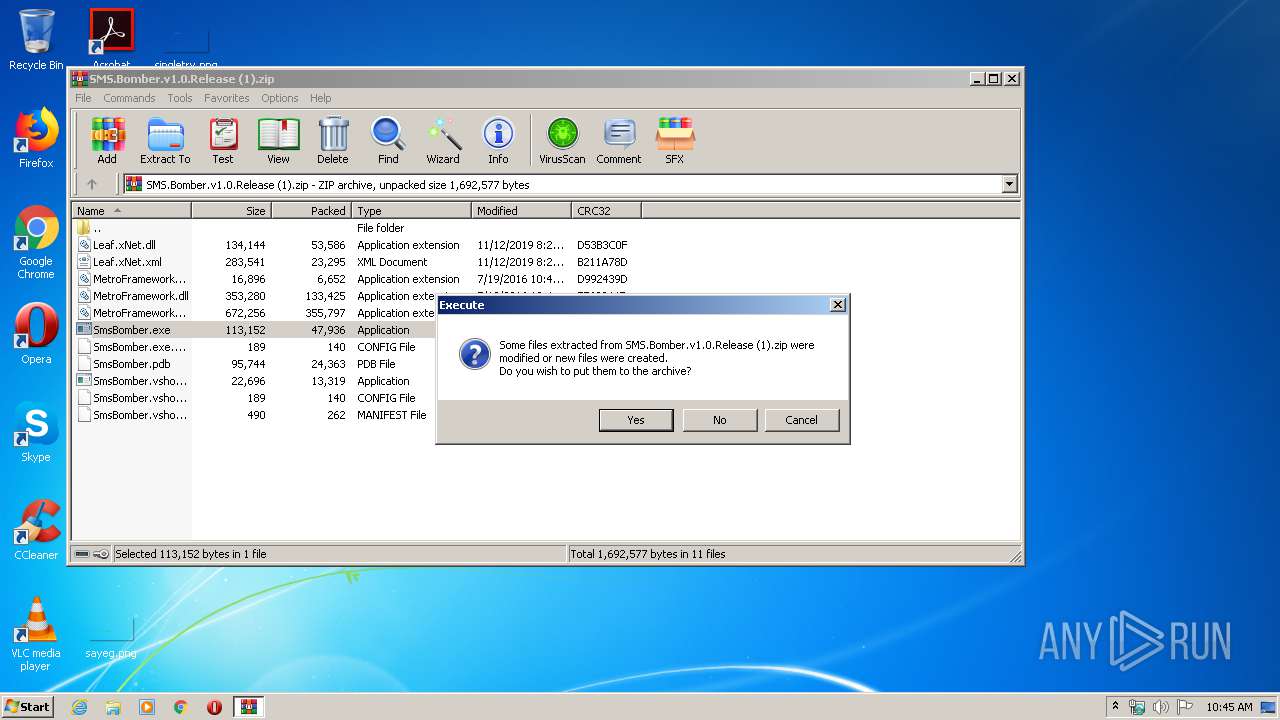
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2884)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:11:12 23:27:05 |
| ZipCRC: | 0xb211a78d |
| ZipCompressedSize: | 23295 |
| ZipUncompressedSize: | 283541 |
| ZipFileName: | Leaf.xNet.xml |
Total processes
38
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1940 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: SmsBomber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2884 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SMS.Bomber.v1.0.Release (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3356 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.47437\SmsBomber.vshost.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.47437\SmsBomber.vshost.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: vshost32.exe Exit code: 3762504530 Version: 14.0.23107.0 Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.48537\SmsBomber.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.48537\SmsBomber.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: SmsBomber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
573
Read events
541
Write events
32
Delete events
0
Modification events
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SMS.Bomber.v1.0.Release (1).zip | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
18
Suspicious files
0
Text files
12
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\Leaf.xNet.xml | xml | |
MD5:— | SHA256:— | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.exe | executable | |
MD5:— | SHA256:— | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.pdb | pdb | |
MD5:— | SHA256:— | |||
| 1940 | SmsBomber.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\Settings.txt | pi2 | |
MD5:— | SHA256:— | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.vshost.exe | executable | |
MD5:5A968502B84A268CA84018F1A9F6BB59 | SHA256:58D46A3801C280908698EF4FF789546427B9BE7CD78F61A7533CC2F56C1B881B | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.vshost.exe.manifest | xml | |
MD5:A19A2658BA69030C6AC9D11FD7D7E3C1 | SHA256:C0085EB467D2FC9C9F395047E057183B3CD1503A4087D0DB565161C13527A76F | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.47437\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 2884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2884.45046\SmsBomber.vshost.exe.config | xml | |
MD5:5A7F52D69E6FCA128023469AE760C6D5 | SHA256:498C7F8E872F9CEF0CF04F7D290CF3804C82A007202C9B484128C94D03040FD0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report