| File name: | WKE64.exe |
| Full analysis: | https://app.any.run/tasks/3b846549-6c0f-4d8c-8feb-b4369d1c7240 |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2024, 00:40:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, RAR self-extracting archive |
| MD5: | 6E59854F2FB878150375E208231B0DEF |
| SHA1: | 852B904DCFE3957102B7C95A6DF9F4CF090F395D |
| SHA256: | E2B39BB0F6048BFE35706E7780DC7227D428F3FE908FC9A8A068EE8A5A833009 |
| SSDEEP: | 98304:KjDu4vDH+AGiDPn+qRWrA5ZEQIVwFwiufqlEOyz1MpqElu/L2ful1zEvTeWZBYvc:64kWDjXcQ9XLoldU3k |
MALICIOUS
No malicious indicators.SUSPICIOUS
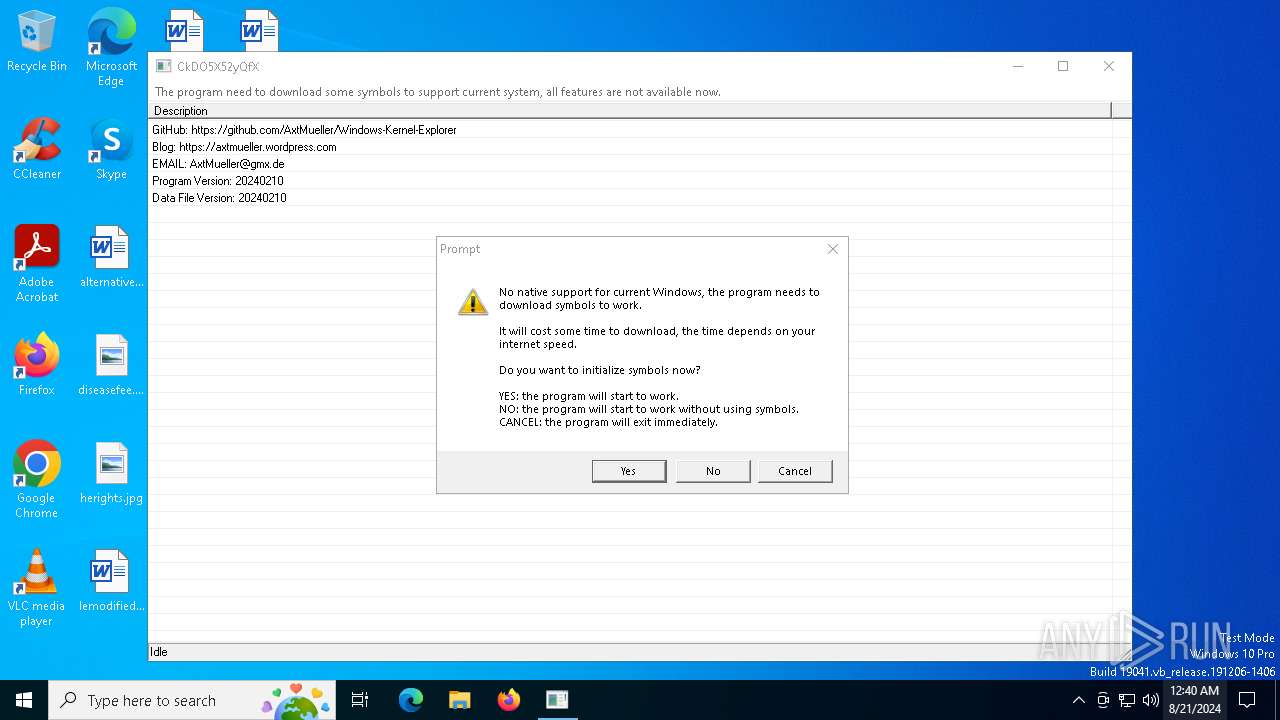
Drops the executable file immediately after the start
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
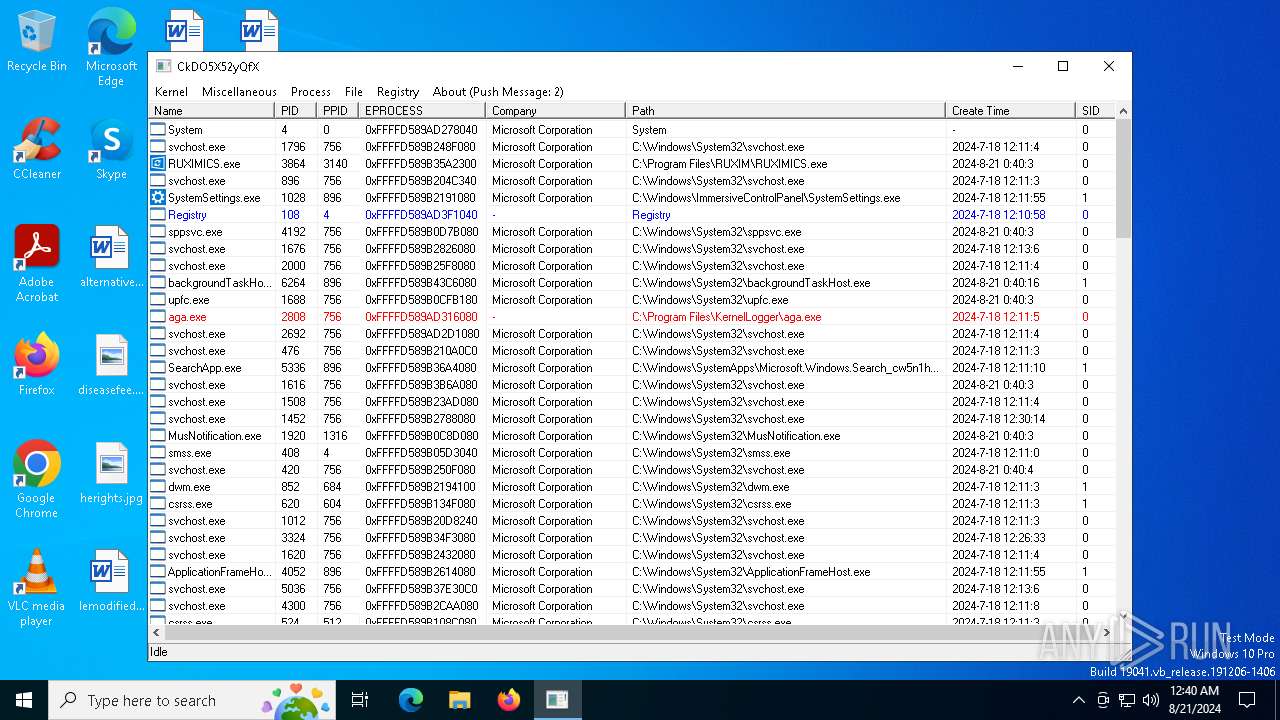
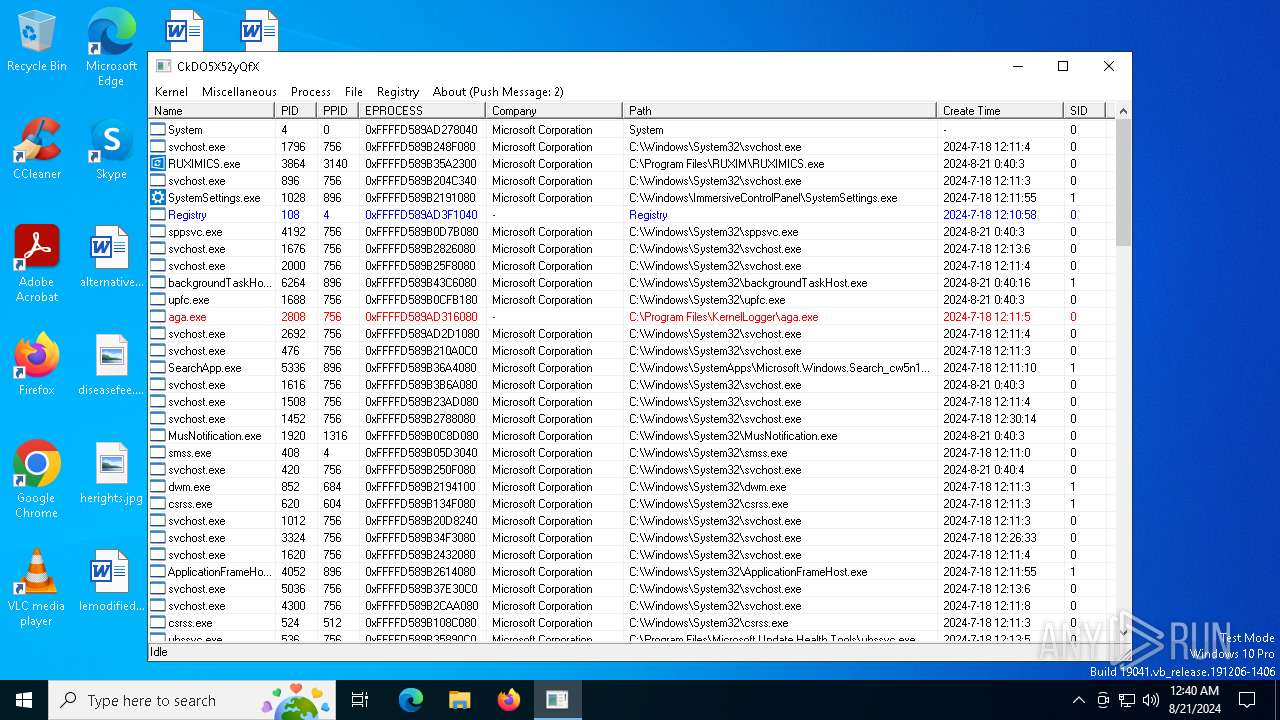
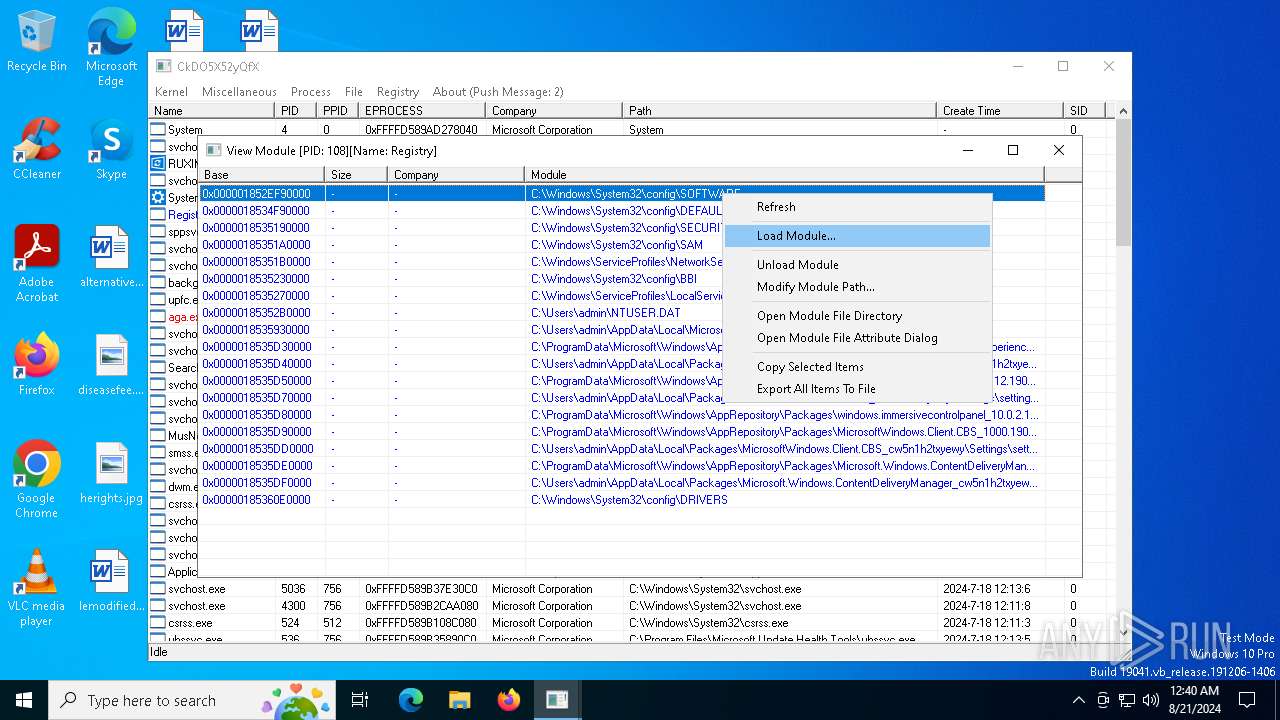
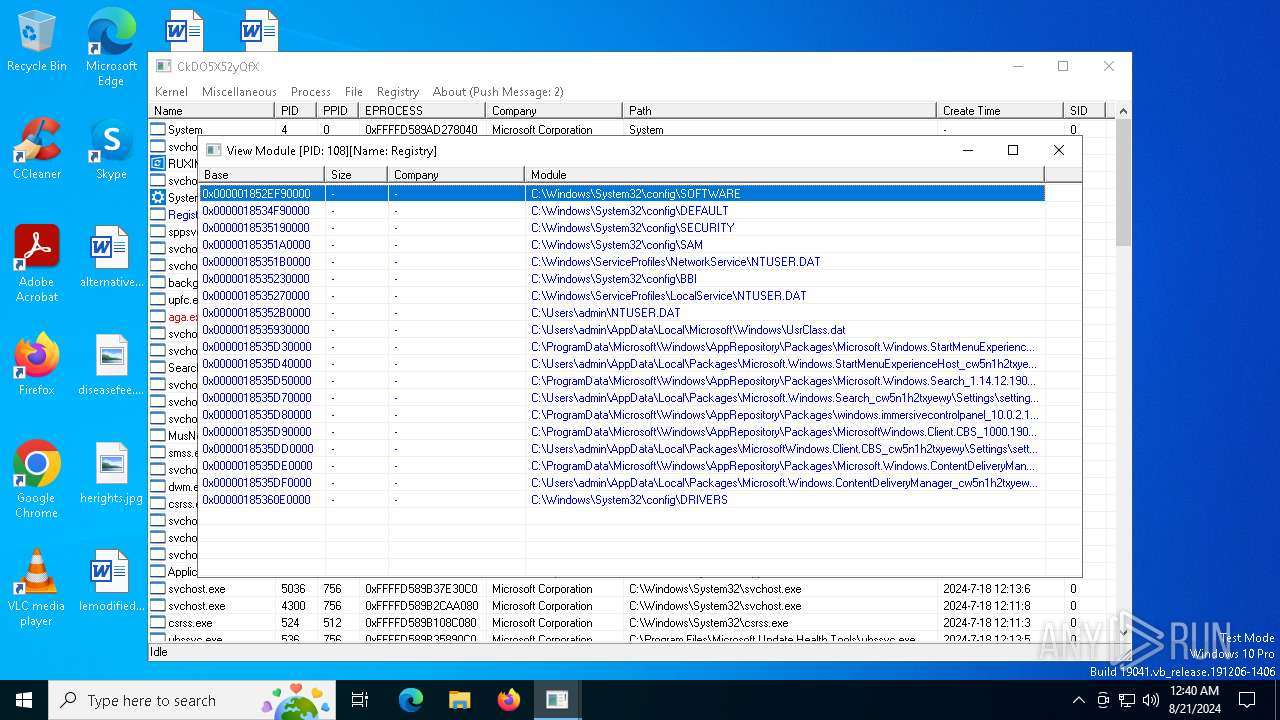
Drops a system driver (possible attempt to evade defenses)
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
The process creates files with name similar to system file names
- WKE64.exe (PID: 6708)
Process drops legitimate windows executable
- WKE64.exe (PID: 6708)
Executable content was dropped or overwritten
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
Reads security settings of Internet Explorer
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
Reads the date of Windows installation
- WKE64.exe (PID: 6708)
Checks Windows Trust Settings
- WindowsKernelExplorer.exe (PID: 7072)
INFO
Checks supported languages
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
Reads the computer name
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
Create files in a temporary directory
- WKE64.exe (PID: 6708)
- WindowsKernelExplorer.exe (PID: 7072)
Process checks computer location settings
- WKE64.exe (PID: 6708)
Checks proxy server information
- WindowsKernelExplorer.exe (PID: 7072)
Reads the machine GUID from the registry
- WindowsKernelExplorer.exe (PID: 7072)
Creates files or folders in the user directory
- WindowsKernelExplorer.exe (PID: 7072)
Reads the software policy settings
- WindowsKernelExplorer.exe (PID: 7072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2013:12:01 08:08:26+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 177152 |
| InitializedDataSize: | 166912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x222dc |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
130
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6708 | "C:\Users\admin\AppData\Local\Temp\WKE64.exe" | C:\Users\admin\AppData\Local\Temp\WKE64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7004 | "C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.exe" | C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.exe | — | WKE64.exe | |||||||||||
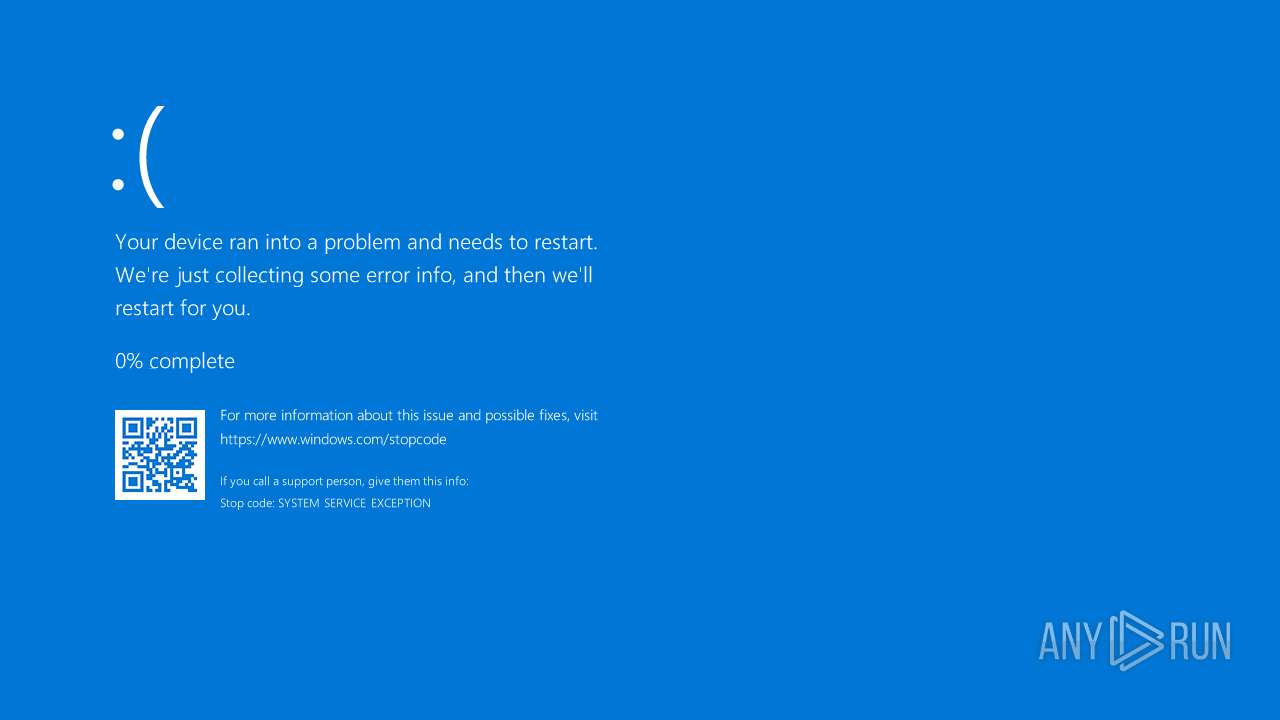
User: admin Company: Axt Mueller Integrity Level: MEDIUM Description: Windows Kernel Explorer Application Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 7072 | "C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.exe" | C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.exe | WKE64.exe | ||||||||||||
User: admin Company: Axt Mueller Integrity Level: HIGH Description: Windows Kernel Explorer Application Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
4 392
Read events
4 370
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6708) WKE64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6708) WKE64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6708) WKE64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6708) WKE64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7072) WindowsKernelExplorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE |
| Operation: | write | Name: | WindowsKernelExplorerDeviceAndSymbolicLinkName |
Value: 9j7u8i0931gH9w | |||
| (PID) Process: | (7072) WindowsKernelExplorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE |
| Operation: | write | Name: | WindowsKernelExplorerFalsifyDriverCharacteristic |
Value: 1 | |||
| (PID) Process: | (7072) WindowsKernelExplorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE |
| Operation: | write | Name: | WindowsKernelExplorerFilterAltitude |
Value: 421869 | |||
| (PID) Process: | (7072) WindowsKernelExplorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7072) WindowsKernelExplorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7072) WindowsKernelExplorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6708 | WKE64.exe | C:\Users\admin\AppData\Local\Temp\WKE64\symsrv.yes | — | |
MD5:— | SHA256:— | |||
| 6708 | WKE64.exe | C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.exe | executable | |
MD5:7718B5A3A7FB24678F0B29F48DADA238 | SHA256:A6A9FC48800F676713E4F1849E7D81269C865E880F3A2B484800ED215836EB4C | |||
| 6708 | WKE64.exe | C:\Users\admin\AppData\Local\Temp\WKE64\symsrv.dll | executable | |
MD5:65FB3391EB26F5AC647FC40501D8E21D | SHA256:C67BE7D3F54D44AC264A18E33909482F1F8CA7B7FBAAF5659EF71ED9F8092C34 | |||
| 7072 | WindowsKernelExplorer.exe | C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.ini | binary | |
MD5:C0E93FAD8D8A2E9C38F4F113FB633F31 | SHA256:6E660F6519E6FC3D402C5F8FEEA3CAAE7F233093E5ED4531BE347C81B669D6D1 | |||
| 7072 | WindowsKernelExplorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:29414AF98DEF8E3BEEF8C31811786737 | SHA256:E16382CDE9300AC3413FF25F1558C2A5FE796BE4C316A09A7334ED3F2DB166D6 | |||
| 6708 | WKE64.exe | C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.sys | executable | |
MD5:03F31E2C1B21FF5077D8456B0008A168 | SHA256:BD880010492D29B7EA382EEB76405E6251CF9F51AA8D1718D1225C34A6B52803 | |||
| 7072 | WindowsKernelExplorer.exe | C:\Users\admin\AppData\Local\Temp\WindowsKernelExplorer.sys | executable | |
MD5:03F31E2C1B21FF5077D8456B0008A168 | SHA256:BD880010492D29B7EA382EEB76405E6251CF9F51AA8D1718D1225C34A6B52803 | |||
| 7072 | WindowsKernelExplorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:EF251242C68DA9415B1B879B97034419 | SHA256:7623A12C25C58C08312B302C0A268CBA235F17E16B37BA56991AE5C5F2D47009 | |||
| 6708 | WKE64.exe | C:\Users\admin\AppData\Local\Temp\WKE64\WindowsKernelExplorer.dat | binary | |
MD5:0B55E3723C3AD03AB15544A717001D7D | SHA256:8352FE5BC5B7D2678155181EB74FB3D4745E4BCD2EB5B59E75BA4A455A3C7C3A | |||
| 6708 | WKE64.exe | C:\Users\admin\AppData\Local\Temp\WKE64\dbghelp.dll | executable | |
MD5:AB8C9F7E02B62CD2EE0365487FF9F133 | SHA256:7A57C9B709BD5A75E3A6B705CF49F6BAED0FFE771C17C187E6673F221958D4F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
24
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7072 | WindowsKernelExplorer.exe | GET | 200 | 192.229.211.108:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
420 | svchost.exe | GET | 200 | 192.229.211.108:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6264 | backgroundTaskHost.exe | GET | 200 | 192.229.211.108:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1616 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
3864 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7072 | WindowsKernelExplorer.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
7072 | WindowsKernelExplorer.exe | 192.229.211.108:80 | ocsp.digicert.com | EDGECAST | US | unknown |
1616 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
420 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |