| File name: | tinfoil_driver.exe |
| Full analysis: | https://app.any.run/tasks/71d1814f-05fc-45be-b0a7-c4c38267d61f |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2023, 23:47:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C6A3790A4064F7FD6663EC0F3F25158B |
| SHA1: | C7EFCB061C09BC41E20E2DC7CC8369DC39E63376 |
| SHA256: | E2A0B793E8890417CB1BBFF52A65F9A5B9399F1BD072168F1E0482002D80B821 |
| SSDEEP: | 98304:sSdxWsjVCn06dWuGCelS+tCPndMm8I2G6liOQphl0IC9iaQORVlcnzD2HoOtC1MS:FuIGf |
MALICIOUS
Drops the executable file immediately after the start
- tinfoil_driver.exe (PID: 3352)
- dpinst32.exe (PID: 2508)
- drvinst.exe (PID: 2948)
Creates a writable file in the system directory
- drvinst.exe (PID: 2948)
SUSPICIOUS
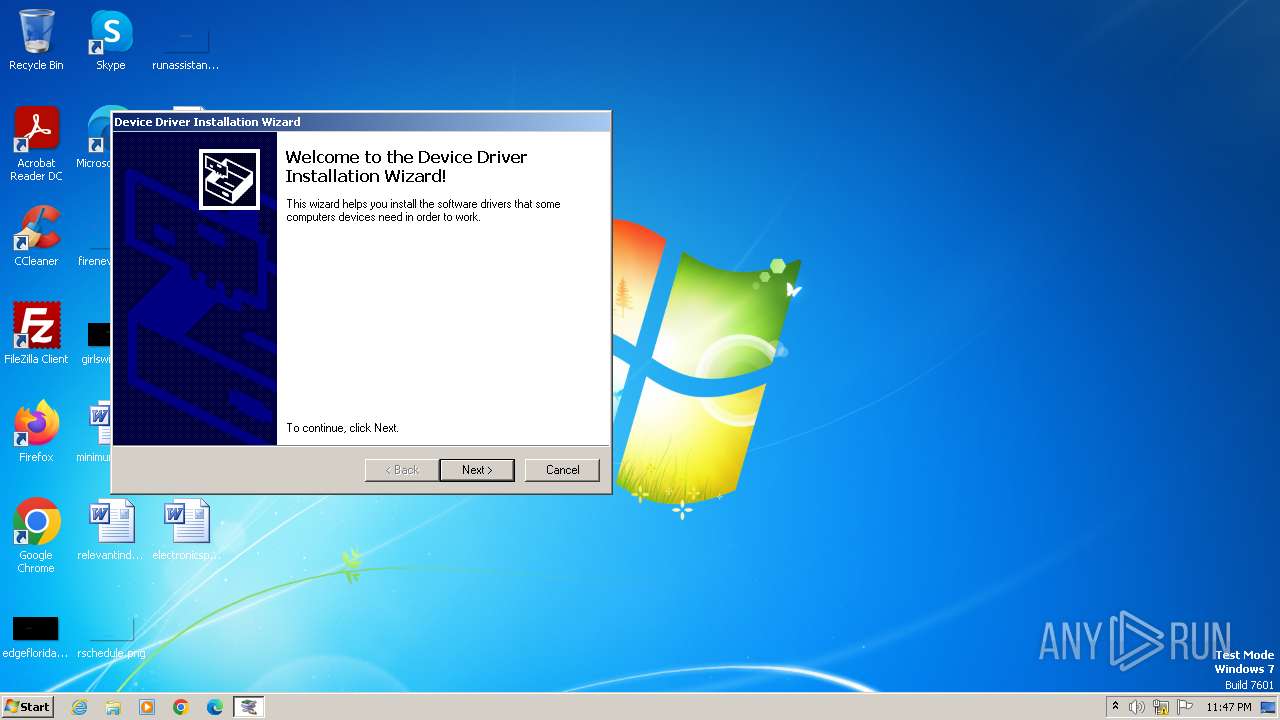
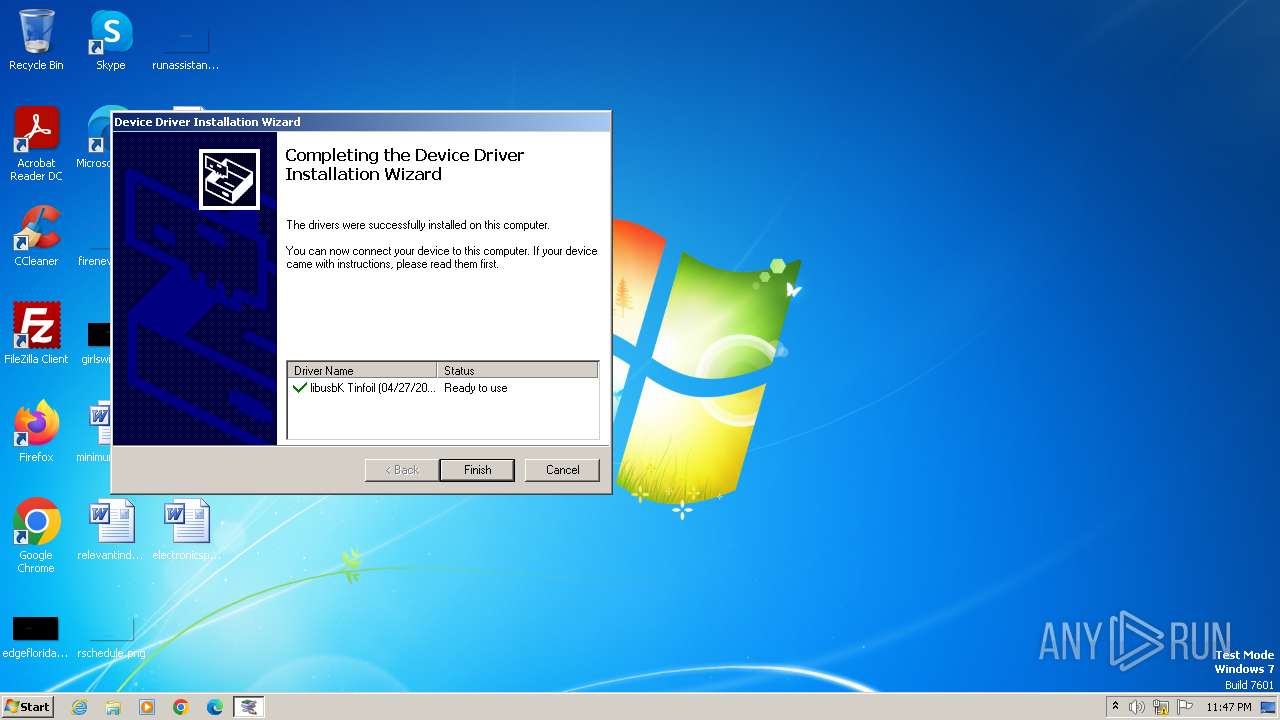
Drops a system driver (possible attempt to evade defenses)
- tinfoil_driver.exe (PID: 3352)
- dpinst32.exe (PID: 2508)
- drvinst.exe (PID: 2948)
Process drops legitimate windows executable
- tinfoil_driver.exe (PID: 3352)
- dpinst32.exe (PID: 2508)
- drvinst.exe (PID: 2948)
Reads settings of System Certificates
- dpscat.exe (PID: 2504)
Reads the Internet Settings
- tinfoil_driver.exe (PID: 3352)
Adds/modifies Windows certificates
- tinfoil_driver.exe (PID: 3352)
Executes as Windows Service
- VSSVC.exe (PID: 3120)
Checks Windows Trust Settings
- drvinst.exe (PID: 2948)
Creates files in the driver directory
- drvinst.exe (PID: 2948)
INFO
Create files in a temporary directory
- tinfoil_driver.exe (PID: 3352)
- dpscat.exe (PID: 2504)
- dpinst32.exe (PID: 2508)
Reads the computer name
- tinfoil_driver.exe (PID: 3352)
- dpscat.exe (PID: 2504)
- dpinst32.exe (PID: 2508)
- drvinst.exe (PID: 2948)
Checks supported languages
- tinfoil_driver.exe (PID: 3352)
- dpscat.exe (PID: 2504)
- dpinst32.exe (PID: 2508)
- drvinst.exe (PID: 2948)
Creates files in the program directory
- dpscat.exe (PID: 2504)
Reads the machine GUID from the registry
- dpscat.exe (PID: 2504)
- dpinst32.exe (PID: 2508)
- drvinst.exe (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:10 00:36:29+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 66560 |
| InitializedDataSize: | 31744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10def |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.1.2100 |
| ProductVersionNumber: | 1.4.1.2100 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Oleg N. Scherbakov |
| FileDescription: | 7z Setup SFX (x86) |
| FileVersion: | 1.4.1.2100 |
| InternalName: | 7ZSfxMod |
| LegalCopyright: | Copyright © 2005-2010 Oleg N. Scherbakov |
| OriginalFileName: | 7ZSfxMod_x86.exe |
| PrivateBuild: | April 28, 2011 |
| ProductName: | 7-Zip SFX |
| ProductVersion: | 1.4.1.2100 |
Total processes
45
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2504 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpscat.exe" | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpscat.exe | tinfoil_driver.exe | ||||||||||||
User: admin Company: http://libusb-win32.sourceforge.net Integrity Level: HIGH Description: Inf catalog and signing tool Exit code: 0 Version: 3.0.7.0 Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpinst32.exe" | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpinst32.exe | — | tinfoil_driver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\AppData\Local\Temp\tinfoil_driver.exe" | C:\Users\admin\AppData\Local\Temp\tinfoil_driver.exe | — | explorer.exe | |||||||||||
User: admin Company: Oleg N. Scherbakov Integrity Level: MEDIUM Description: 7z Setup SFX (x86) Exit code: 3221226540 Version: 1.4.1.2100 Modules
| |||||||||||||||
| 2948 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{03ca1643-5b8f-6a92-536c-9f1e46de091d}\tinfoil.inf" "0" "61128a813" "00000360" "WinSta0\Default" "00000388" "208" "c:\users\admin\appdata\local\temp\7zipsfx_000" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3120 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3352 | "C:\Users\admin\AppData\Local\Temp\tinfoil_driver.exe" | C:\Users\admin\AppData\Local\Temp\tinfoil_driver.exe | explorer.exe | ||||||||||||
User: admin Company: Oleg N. Scherbakov Integrity Level: HIGH Description: 7z Setup SFX (x86) Exit code: 256 Version: 1.4.1.2100 Modules
| |||||||||||||||
Total events
11 392
Read events
11 326
Write events
64
Delete events
2
Modification events
| (PID) Process: | (3352) tinfoil_driver.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3352) tinfoil_driver.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3352) tinfoil_driver.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3352) tinfoil_driver.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2504) dpscat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2504) dpscat.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF7 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF702000000010000004C0000001C0000000000000001000000200000000000000000000000020000006C006900620077006400690020006B0065007900200063006F006E007400610069006E006500720000000000000000000B000000010000000E0000006C0069006200770064006900000020000000010000008C02000030820288308201F1A003020102021045110CF1A683268B4F57415FB6896DA0300D06092A864886F70D010105050030433141303F06035504031E38006C00690062007500730062004B0020002800740069006E0066006F0069006C002E0069006E006600290020005B00530065006C0066005D301E170D3233313132363233343733375A170D3239303130313030303030305A30433141303F06035504031E38006C00690062007500730062004B0020002800740069006E0066006F0069006C002E0069006E006600290020005B00530065006C0066005D30819F300D06092A864886F70D010101050003818D0030818902818100AF959277AEC6CAC25E5818A8C944B25B467E890214B9683DAFDBD7F02F89C949FEB0A2398916FFBC6E63EAED3EF13484400AB07044BBA569A1B658A8994C8D006F3251819DC69EFB1E442A6BFB2AA06D820458CA9B81B0D0951CE957C1023CDEAAFD6E4F8CAB8DA958FC0A6522751E0CDBBBCFC9FBB3E286861DD3C515F4257B0203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D010105050003818100A5697EB89857E1647103A40004B3670BB18429A208C472E33594F930759C20F9CF35853963D1ED4ECB06D73DF2C887ABE3FB085CE63FA5A229F3815A991D23056920CEC2D59ACBDD6CF202292E496B9B3648F633A61B6EB80CF1F7629AF4EC7E77F5622572E6DED10395684BC99170A1FAFEB8FBEFCA38BA8F00EA401933E369 | |||
| (PID) Process: | (2504) dpscat.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF7 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2504) dpscat.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF7 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF720000000010000008C02000030820288308201F1A003020102021045110CF1A683268B4F57415FB6896DA0300D06092A864886F70D010105050030433141303F06035504031E38006C00690062007500730062004B0020002800740069006E0066006F0069006C002E0069006E006600290020005B00530065006C0066005D301E170D3233313132363233343733375A170D3239303130313030303030305A30433141303F06035504031E38006C00690062007500730062004B0020002800740069006E0066006F0069006C002E0069006E006600290020005B00530065006C0066005D30819F300D06092A864886F70D010101050003818D0030818902818100AF959277AEC6CAC25E5818A8C944B25B467E890214B9683DAFDBD7F02F89C949FEB0A2398916FFBC6E63EAED3EF13484400AB07044BBA569A1B658A8994C8D006F3251819DC69EFB1E442A6BFB2AA06D820458CA9B81B0D0951CE957C1023CDEAAFD6E4F8CAB8DA958FC0A6522751E0CDBBBCFC9FBB3E286861DD3C515F4257B0203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D010105050003818100A5697EB89857E1647103A40004B3670BB18429A208C472E33594F930759C20F9CF35853963D1ED4ECB06D73DF2C887ABE3FB085CE63FA5A229F3815A991D23056920CEC2D59ACBDD6CF202292E496B9B3648F633A61B6EB80CF1F7629AF4EC7E77F5622572E6DED10395684BC99170A1FAFEB8FBEFCA38BA8F00EA401933E369 | |||
| (PID) Process: | (2504) dpscat.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF7 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2504) dpscat.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF7 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000BF9F38DE807C9FCD7AD43A69FD3862FF5F66ACF720000000010000008C02000030820288308201F1A003020102021045110CF1A683268B4F57415FB6896DA0300D06092A864886F70D010105050030433141303F06035504031E38006C00690062007500730062004B0020002800740069006E0066006F0069006C002E0069006E006600290020005B00530065006C0066005D301E170D3233313132363233343733375A170D3239303130313030303030305A30433141303F06035504031E38006C00690062007500730062004B0020002800740069006E0066006F0069006C002E0069006E006600290020005B00530065006C0066005D30819F300D06092A864886F70D010101050003818D0030818902818100AF959277AEC6CAC25E5818A8C944B25B467E890214B9683DAFDBD7F02F89C949FEB0A2398916FFBC6E63EAED3EF13484400AB07044BBA569A1B658A8994C8D006F3251819DC69EFB1E442A6BFB2AA06D820458CA9B81B0D0951CE957C1023CDEAAFD6E4F8CAB8DA958FC0A6522751E0CDBBBCFC9FBB3E286861DD3C515F4257B0203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D010105050003818100A5697EB89857E1647103A40004B3670BB18429A208C472E33594F930759C20F9CF35853963D1ED4ECB06D73DF2C887ABE3FB085CE63FA5A229F3815A991D23056920CEC2D59ACBDD6CF202292E496B9B3648F633A61B6EB80CF1F7629AF4EC7E77F5622572E6DED10395684BC99170A1FAFEB8FBEFCA38BA8F00EA401933E369 | |||
Executable files
29
Suspicious files
16
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3352 | tinfoil_driver.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpinst.xml | text | |
MD5:83F46EF4F06D32F8B3201A2EA2189E19 | SHA256:127B6D24415B513C1F3B5FFE63AF1B395DBF868DAFEC44C4CBB367D81DB9AE0C | |||
| 3352 | tinfoil_driver.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\amd64\libusb0.dll | executable | |
MD5:1D8215F7F8CD02A553499B534CCFB4D5 | SHA256:4F18B5D2C28AA66B648C8683C6D09B52B92CBBEE85984BBEFAD5F38A64BC2A14 | |||
| 3352 | tinfoil_driver.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpscat.exe | executable | |
MD5:EB7409D7CD6E8D8EDEC5E3209385F88A | SHA256:7A40E13568D9A4E33FB7ED34DC0ABD21A9C097BEAE9C0E4ADE3B99F05A0F60D9 | |||
| 3352 | tinfoil_driver.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\tinfoil.inf | text | |
MD5:28F001699DA6C0920D4B2D73B7DBFC23 | SHA256:49CC5AF0BE44527245CA0CF9857CE238B91D7585A6CC2335D506E0A8AEB6ACEA | |||
| 3352 | tinfoil_driver.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx_000\dpinst32.exe | executable | |
MD5:30A0AFEE4AEA59772DB6434F1C0511AB | SHA256:D84149976BC94A21B21AA0BC99FCBDEE9D1AD4F3387D8B62B90F805AC300BA05 | |||
| 2508 | dpinst32.exe | C:\Users\admin\AppData\Local\Temp\{03ca1643-5b8f-6a92-536c-9f1e46de091d}\x86\libusbK.sys | executable | |
MD5:1F17DFE26285CF9971E55DDFF915877B | SHA256:6265AE9AE5C49F515613F0B749AD8390A1B34CA326203318BFFEB6C2C281D2D0 | |||
| 2508 | dpinst32.exe | C:\Windows\INF\setupapi.dev.log | text | |
MD5:D8F0C690A103497D2FA22421AE22A428 | SHA256:B723C3DC8F94025F8A30CC6086045C09788ADEF9BB13037A208ADEA59FDC153D | |||
| 2504 | dpscat.exe | C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\139ebeae3d8ebfe34996190e4d342621_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:8012ED87EBF2F220B0BE98944E867DC6 | SHA256:8BC31BFB62426C51102836451402C49823F93900B9A2D4F58D8553E205377CD5 | |||
| 2508 | dpinst32.exe | C:\Users\admin\AppData\Local\Temp\{03ca1643-5b8f-6a92-536c-9f1e46de091d}\x86\SETF45F.tmp | executable | |
MD5:1F17DFE26285CF9971E55DDFF915877B | SHA256:6265AE9AE5C49F515613F0B749AD8390A1B34CA326203318BFFEB6C2C281D2D0 | |||
| 2508 | dpinst32.exe | C:\Users\admin\AppData\Local\Temp\{03ca1643-5b8f-6a92-536c-9f1e46de091d}\x86\SETF460.tmp | executable | |
MD5:535779909A40B42F4F3E48598F5778A5 | SHA256:00CACA07869B19D10B370552AC7CC2F6F2EE246FC15DB11650F6CD3F4EF9B666 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
Threats
Process | Message |
|---|---|
dpscat.exe | |
dpscat.exe | Portions Copyright(c) Pete Batard. (LGPL)
|
dpscat.exe | Copyright(c) 2012 Travis Lee Robinson. (DUAL BSD/GPL)
|
dpscat.exe | Found Hwid: USB\VID_16C0&PID_27E2&MI_00
|
dpscat.exe | Actual section to install: LUsbK_DeviceGroup.NTx86
|
dpscat.exe | Hash calculated for: .\x86\libusbk.sys
|
dpscat.exe | Hash calculated for: .\x86\libusb0_x86.dll
|
dpscat.exe | Hash added..
|
dpscat.exe | Using PE guid..
|
dpscat.exe | Using PE guid..
|