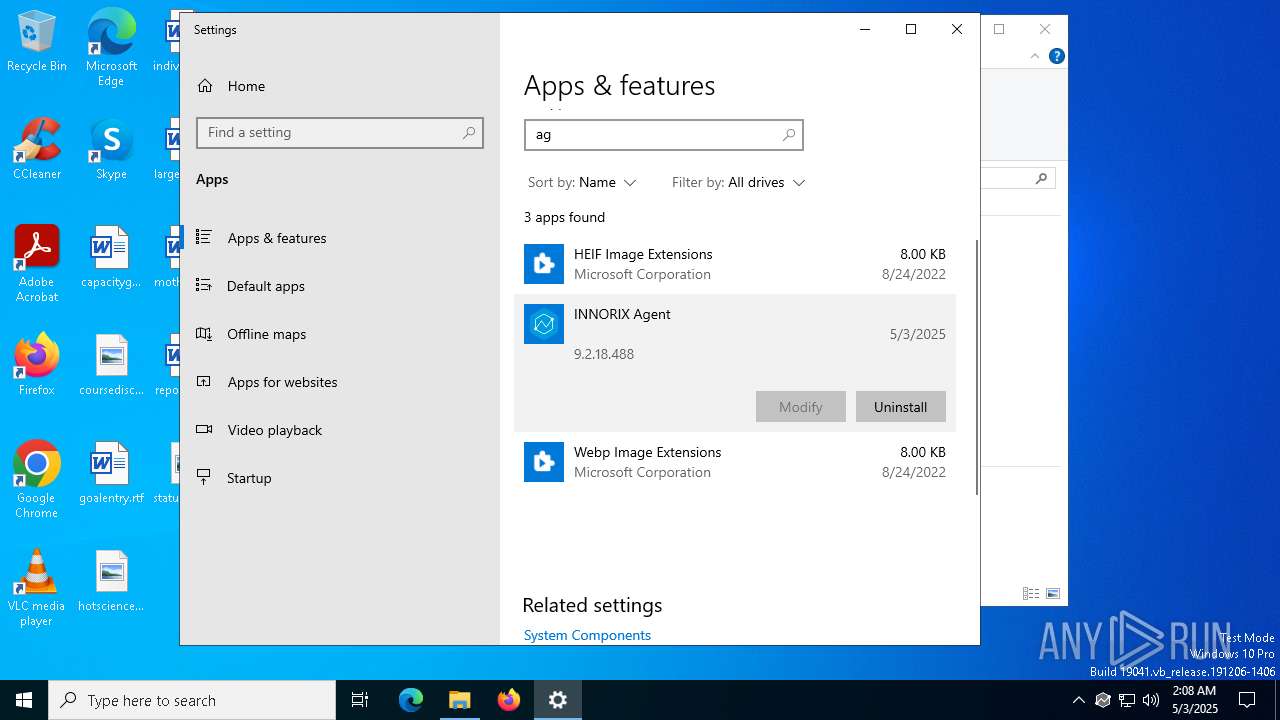
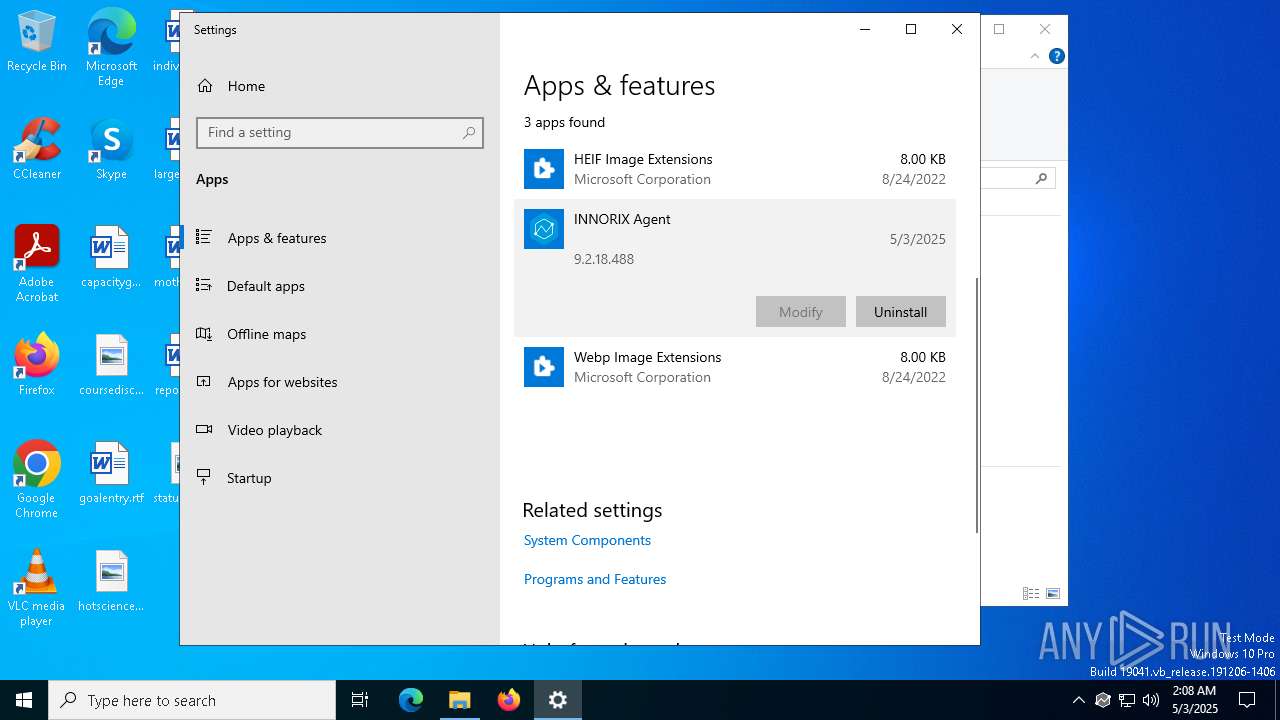
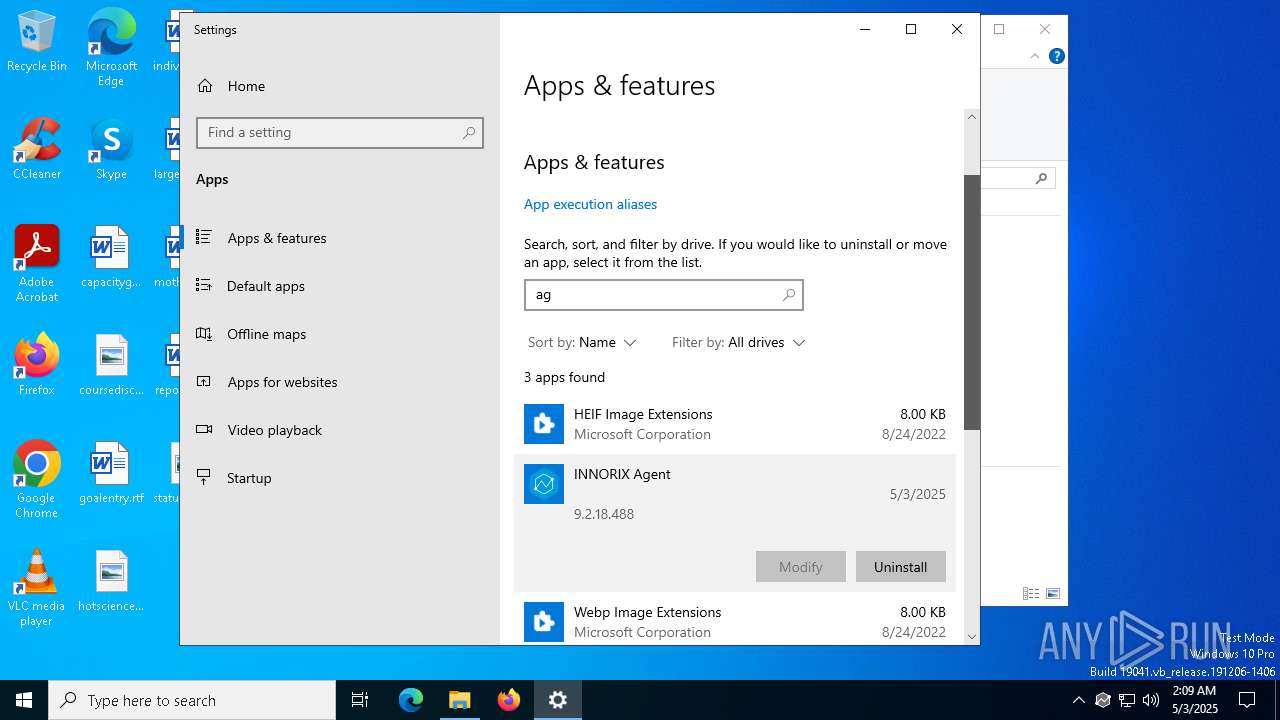
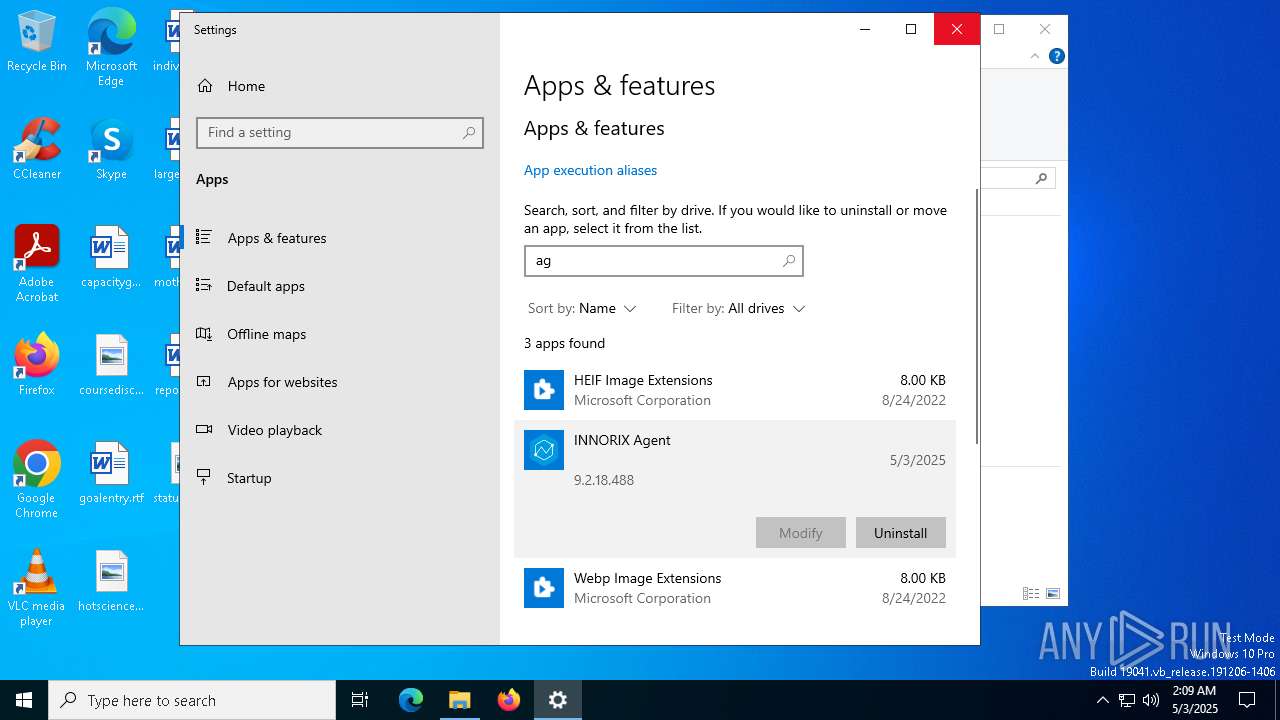
| File name: | INNORIX-Agent.exe |
| Full analysis: | https://app.any.run/tasks/79800101-7692-4d7b-99be-db775ef5b82c |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2025, 02:07:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 355B69E6B30A8A5413BF31B1A1B76C57 |
| SHA1: | 3FB47A921A33094F88FBECD50DF01E49BA164222 |
| SHA256: | E29AF1BA519EF85DA96EB801014A882DFA7ECE93090E778E4243BF6A144E2EB8 |
| SSDEEP: | 98304:Lsr0Jv+tRDTI41kl7Io65KlSHLMTWg6uZnNeq/pBbsHFTJC39BC2lWAwglU8jhQk:c3UM6yf0v+A4rEM85 |
MALICIOUS
Executing a file with an untrusted certificate
- INNORIX-Agent.exe (PID: 6044)
- INNORIX-Agent.exe (PID: 4448)
- innorixas.exe (PID: 7320)
- innorixam.exe (PID: 7480)
- innorixam.exe (PID: 7588)
- innorixas.exe (PID: 7780)
- innorixam.exe (PID: 7308)
- innorixam.exe (PID: 6640)
- innorixst.exe (PID: 5680)
- innorixas.exe (PID: 7740)
- innorixas.exe (PID: 5868)
- innorixam.exe (PID: 5956)
- innorixam.exe (PID: 5392)
- innorixam.exe (PID: 5668)
SUSPICIOUS
Reads security settings of Internet Explorer
- INNORIX-Agent.exe (PID: 4448)
Uses TASKKILL.EXE to kill process
- INNORIX-Agent.exe (PID: 4448)
Windows service management via SC.EXE
- sc.exe (PID: 8068)
- sc.exe (PID: 3100)
- sc.exe (PID: 8164)
- sc.exe (PID: 7036)
Creates a software uninstall entry
- INNORIX-Agent.exe (PID: 4448)
There is functionality for taking screenshot (YARA)
- INNORIX-Agent.exe (PID: 4448)
Executable content was dropped or overwritten
- INNORIX-Agent.exe (PID: 4448)
Adds/modifies Windows certificates
- certutil.exe (PID: 4620)
Executes as Windows Service
- innorixam.exe (PID: 7588)
- innorixas.exe (PID: 7740)
Starts CMD.EXE for commands execution
- innorixam.exe (PID: 7588)
- innorixas.exe (PID: 7740)
INFO
The sample compiled with english language support
- INNORIX-Agent.exe (PID: 4448)
Checks supported languages
- INNORIX-Agent.exe (PID: 4448)
- innorixam.exe (PID: 7308)
- innorixam.exe (PID: 7588)
- innorixas.exe (PID: 7320)
- innorixam.exe (PID: 7480)
- innorixam.exe (PID: 6640)
- innorixst.exe (PID: 5680)
- innorixas.exe (PID: 5868)
- innorixas.exe (PID: 7780)
- innorixas.exe (PID: 7740)
Create files in a temporary directory
- INNORIX-Agent.exe (PID: 4448)
Reads the computer name
- innorixas.exe (PID: 7320)
- INNORIX-Agent.exe (PID: 4448)
- innorixam.exe (PID: 7308)
- innorixam.exe (PID: 7480)
- innorixam.exe (PID: 6640)
- innorixam.exe (PID: 7588)
- innorixas.exe (PID: 7740)
- innorixas.exe (PID: 7780)
- innorixas.exe (PID: 5868)
The sample compiled with korean language support
- INNORIX-Agent.exe (PID: 4448)
Creates files in the program directory
- innorixas.exe (PID: 7740)
Manual execution by a user
- innorixam.exe (PID: 5668)
- innorixam.exe (PID: 5392)
- innorixam.exe (PID: 5956)
- notepad.exe (PID: 6640)
Reads the machine GUID from the registry
- innorixas.exe (PID: 7740)
Reads the software policy settings
- slui.exe (PID: 7192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:07:25 00:55:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x322b |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.2.18.488 |
| ProductVersionNumber: | 9.2.18.488 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| CompanyName: | INNORIX |
| CompanyWebsite: | http://www.innorix.com |
| FileDescription: | - |
| FileVersion: | 9.2.18.488 |
| LegalCopyright: | - |
| ProductName: | INNORIX Agent x86 |
| ProductVersion: | 9.2.18.488 |
Total processes
201
Monitored processes
57
Malicious processes
3
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | innorixam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | innorixam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | sc delete innorixam | C:\Windows\SysWOW64\sc.exe | — | INNORIX-Agent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | "C:\Users\admin\AppData\Local\Temp\INNORIX-Agent.exe" | C:\Users\admin\AppData\Local\Temp\INNORIX-Agent.exe | explorer.exe | ||||||||||||
User: admin Company: INNORIX Integrity Level: HIGH Exit code: 0 Version: 9.2.18.488 Modules
| |||||||||||||||
| 4620 | certutil -addstore -f ROOT C:\INNORIX_Agent\ca.crt | C:\Windows\SysWOW64\certutil.exe | — | INNORIX-Agent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | innorixam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5392 | "C:\INNORIX_Agent\innorixam.exe" | C:\INNORIX_Agent\innorixam.exe | — | explorer.exe | |||||||||||
User: admin Company: INNORIX Integrity Level: MEDIUM Description: INNORIX Agent Monitor Exit code: 4294967295 Version: 1.1.0.8 Modules
| |||||||||||||||
Total events
7 407
Read events
7 251
Write events
155
Delete events
1
Modification events
| (PID) Process: | (4448) INNORIX-Agent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\INNORIX Agent\Components |
| Operation: | write | Name: | Main |
Value: 1 | |||
| (PID) Process: | (4448) INNORIX-Agent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\INNORIX Agent |
| Operation: | write | Name: | Path |
Value: C:\INNORIX_Agent | |||
| (PID) Process: | (4620) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (4620) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (4620) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (4620) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 289E78F6132FB5D8533B2CC042F130B03CC0F40C |
Value: | |||
| (PID) Process: | (4620) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\289E78F6132FB5D8533B2CC042F130B03CC0F40C |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000289E78F6132FB5D8533B2CC042F130B03CC0F40C20000000010000003C0300003082033830820220A003020102020101300D06092A864886F70D01010B05003034310B3009060355040613024B523110300E060355040A0C07494E4E4F5249583113301106035504030C0A494E4E4F5249582E4341301E170D3138303731303039303633375A170D3238303730373039303633375A3034310B3009060355040613024B523110300E060355040A0C07494E4E4F5249583113301106035504030C0A494E4E4F5249582E434130820122300D06092A864886F70D01010105000382010F003082010A0282010100B70A73343AC3992EA1A9DD2F2D391959EFDC6CADF1EED1D10580DD363418CC7C580AB0193873C7B4BEC80C045D90BFA4E0C209FF0EDC756730C684D61B57851A059E26D02A608DF600553E17E4B5CF018CB4D323A7349F570C50A38A5EB202CBAC0AA276FA798CA707965FFFFD3CE70FFB16E3012BE1E22E30482885685FEBD97D5C1AE7ECAB6981F539DE1EFEFF55FD77D72F9A3F6903D02FC44C8CC5E89548F3B06FEE86778C16069EA4F7DB276738C3D140782D73E7D729AF90C96FF0D1B8E88E0441ED6DEB10911178BC946FE9FE0C0958BA7B2E1FB1DF75CFF41910C0FC91B5CE52BEFDF7FFB3C9381B0395CB5E25D1AB1125101D8242AF8AA73E20893B0203010001A355305330120603551D130101FF040830060101FF020100301D0603551D0E041604143DFDF00DB855A2CECDFD0599A2A4A10AAA7E392A300B0603551D0F040403020106301106096086480186F8420101040403020007300D06092A864886F70D01010B050003820101001E8E9DDCAA2502402B661AEA622629702FDA1C43FE1DBD5E6D880730F142F0B742D871918FF5E6675091EF604F5EBE6CE2B7C6972E3B7754E4BDB367251DA737D407A2F27FCE5A17688A56924B6ACF215C6FF833C8F2B829F28277360A79EF3F0C72D8EC534031F80E801B2D8FCC1D76C6797BBF51B2FE602591784B20EFB364F46F400D76D38A5A1FF12015FC66062910C0BEAE9DCD2F0D7C1C67551955A267213704BA35FB8736ADBBB393A126C17BFB5AA6AF58848AC0BF558258DE1D20CC2914256EB8A31718CDEF8CFBD51CD010740F6871477FE2E52E751655F26FDF902706B0D9510FEC2CF99855DD0B6F9987BD785C1F0587FD3506D057146A3356B2 | |||
| (PID) Process: | (4448) INNORIX-Agent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\INNORIX Agent |
| Operation: | write | Name: | DisplayName |
Value: INNORIX Agent | |||
| (PID) Process: | (4448) INNORIX-Agent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\INNORIX Agent |
| Operation: | write | Name: | DisplayVersion |
Value: 9.2.18.488 | |||
| (PID) Process: | (4448) INNORIX-Agent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\INNORIX Agent |
| Operation: | write | Name: | Publisher |
Value: INNORIX | |||
Executable files
9
Suspicious files
60
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | INNORIX-Agent.exe | C:\INNORIX_Agent\innorix.pem | text | |
MD5:45CBE8DF9229EEA1CB05BD566C2A827E | SHA256:562B4BF1094935979A9D10C38A7609516A4FA108809875F6FD53B7D134B75A05 | |||
| 4448 | INNORIX-Agent.exe | C:\Users\admin\AppData\Local\Temp\nswBB16.tmp\nsExec.dll | executable | |
MD5:B648C78981C02C434D6A04D4422A6198 | SHA256:3E3D516D4F28948A474704D5DC9907DBE39E3B3F98E7299F536337278C59C5C9 | |||
| 4448 | INNORIX-Agent.exe | C:\Users\admin\AppData\Local\Temp\nswBB16.tmp\SimpleSC.dll | executable | |
MD5:D63975CE28F801F236C4ACA5AF726961 | SHA256:E0C580BBE48A483075C21277C6E0F23F3CBD6CE3EB2CCD3BF48CF68F05628F43 | |||
| 4448 | INNORIX-Agent.exe | C:\INNORIX_Agent\innorixam.exe | executable | |
MD5:0A6C1B97A2F8E49E31DC084189316AC5 | SHA256:CA8338D302E8520406DC388B3B05419C1CAAF7B963B6829FD80F0F308C1F8C8D | |||
| 4448 | INNORIX-Agent.exe | C:\Users\admin\AppData\Local\Temp\nswBB16.tmp\nsProcess.dll | executable | |
MD5:FAA7F034B38E729A983965C04CC70FC1 | SHA256:579A034FF5AB9B732A318B1636C2902840F604E8E664F5B93C07A99253B3C9CF | |||
| 4448 | INNORIX-Agent.exe | C:\INNORIX_Agent\property.conf | binary | |
MD5:392EE6C636B21D9DDA55C91997C73488 | SHA256:F248D284A53970AF9D2FE64DF226651F8B217B55F7198F3E45A7E66594A19F37 | |||
| 4448 | INNORIX-Agent.exe | C:\INNORIX_Agent\innorixas.exe | executable | |
MD5:2D6E2160CF19C8A8B16C2A9DE4228BAB | SHA256:1BBE7754BF6D302F46A3AA714AB2780A535E70A65360E362EABB62D10F8FA649 | |||
| 4448 | INNORIX-Agent.exe | C:\INNORIX_Agent\resource\qqo.ico | image | |
MD5:3F9C2EC9973B136E93E84556DB249DC4 | SHA256:352AB83C3382EF60F4958E5E2CF09E7817997A48CFA2932A64FE07AC7AE7E597 | |||
| 4448 | INNORIX-Agent.exe | C:\Users\admin\AppData\Local\Temp\nswBB16.tmp\newadvsplash.dll | executable | |
MD5:7EE14DFF57FB6E6C644B318D16768F4C | SHA256:53377D0710F551182EDBAB4150935425948535D11B92BF08A1C2DCF989723BD7 | |||
| 7740 | innorixas.exe | C:\INNORIX_Agent\transferInfo\transferDownloadFileInfo-journal | binary | |
MD5:BD42C2E860A4328200AE69BDA702C5A3 | SHA256:D11C025DC7C529C704E05F988D3B6168E75BEC45EAA4D06546C2E0B37158837A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
49
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5404 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |