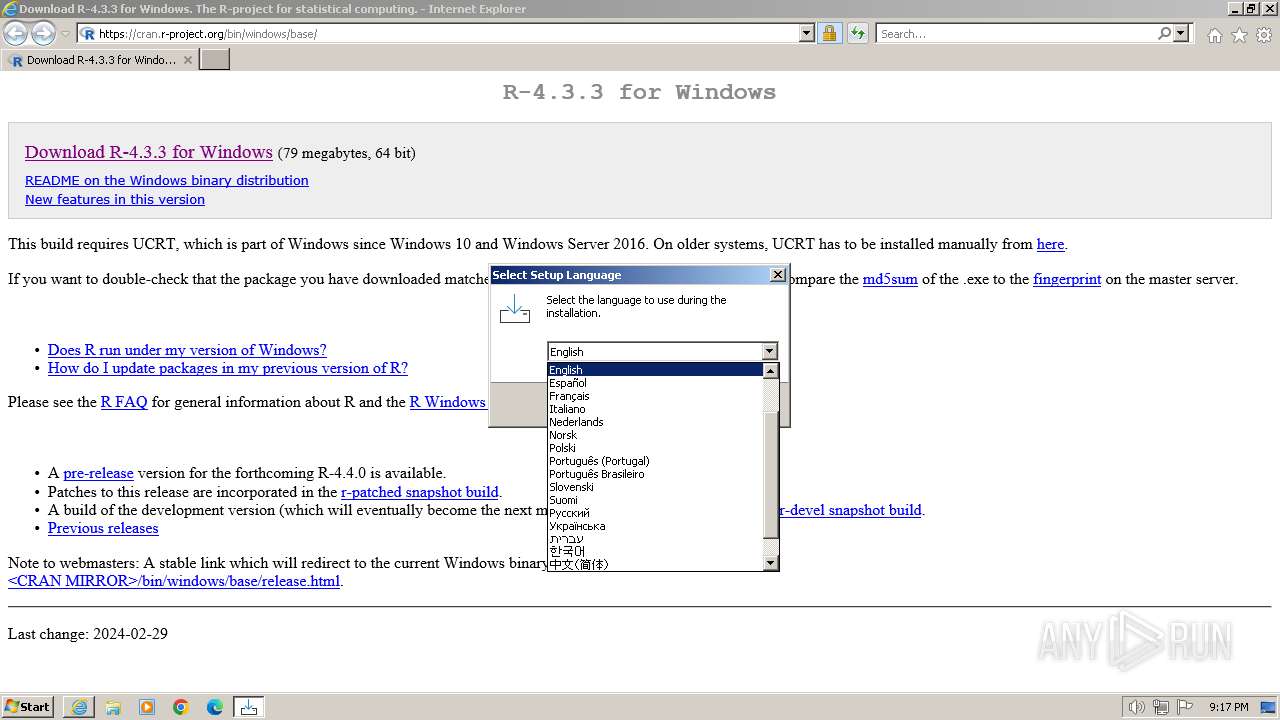
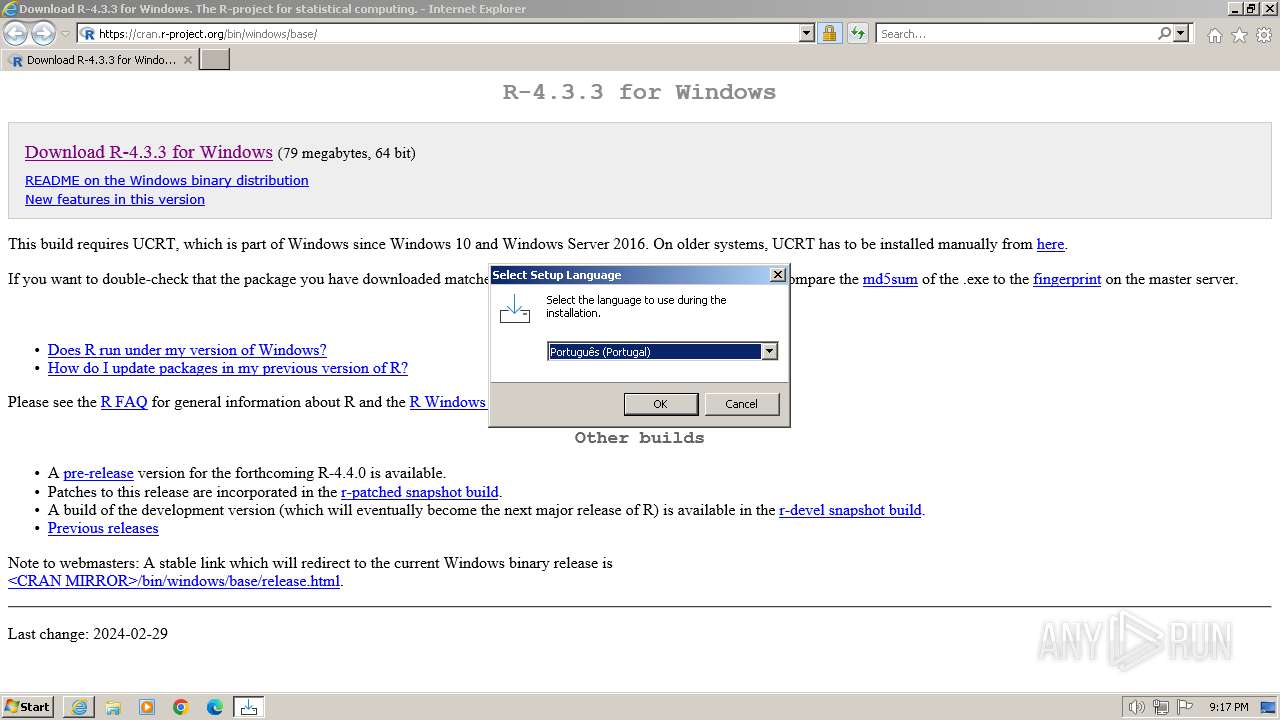
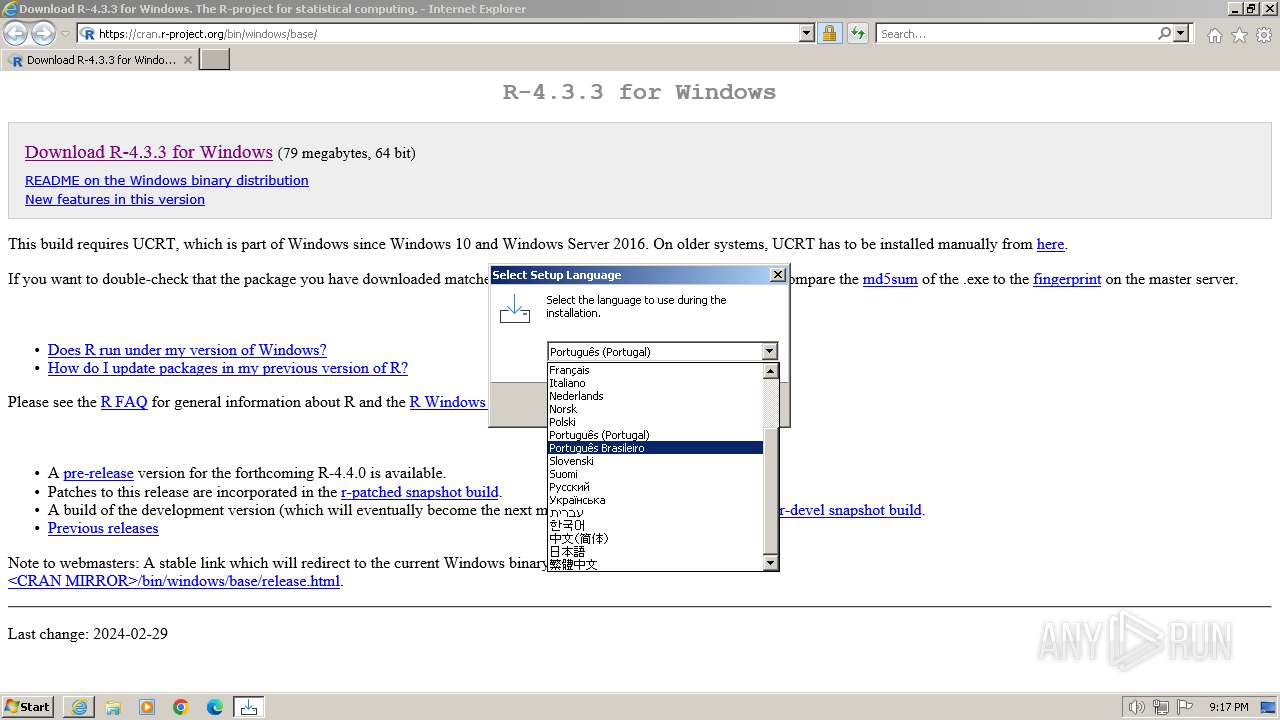
| URL: | https://cran.r-project.org/bin/windows/base/ |
| Full analysis: | https://app.any.run/tasks/a15b0f91-d402-40f9-9bd3-a2b31e34b311 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2024, 20:16:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B9DDC9A41CECA3CDAC778D077E32E037 |
| SHA1: | 69AA4D34309000242F3D03DB0575B7771356FF5B |
| SHA256: | E28FB3B8C02C992E40B017D3273354B87899421A4ADF1462D56A4E837DE59DF1 |
| SSDEEP: | 3:N8KXGR+XCtMLBKSIK:2KWRF0BK3K |
MALICIOUS
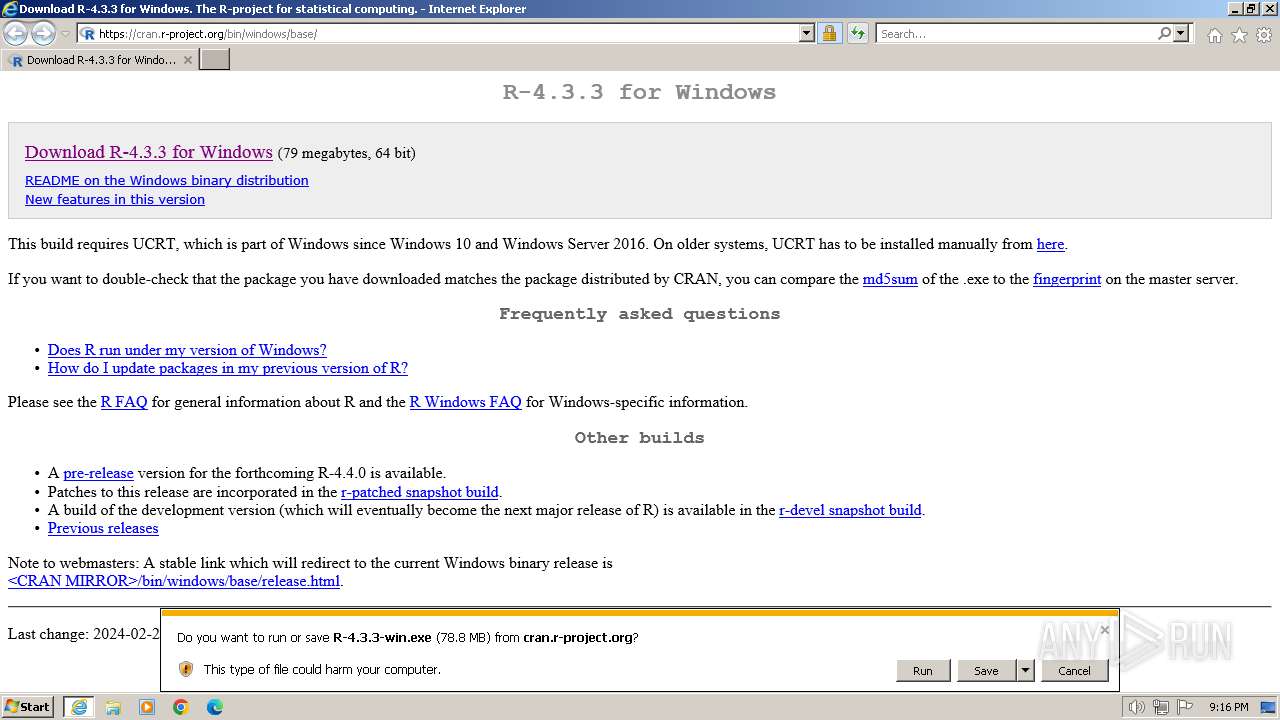
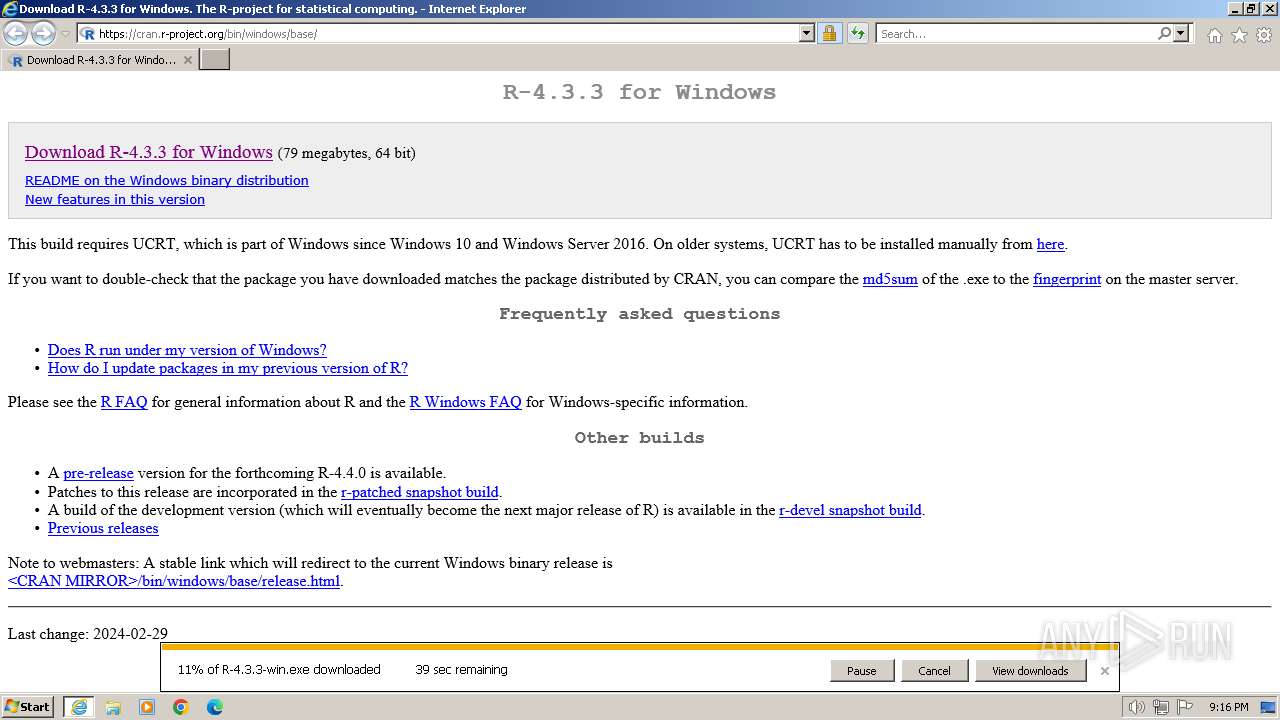
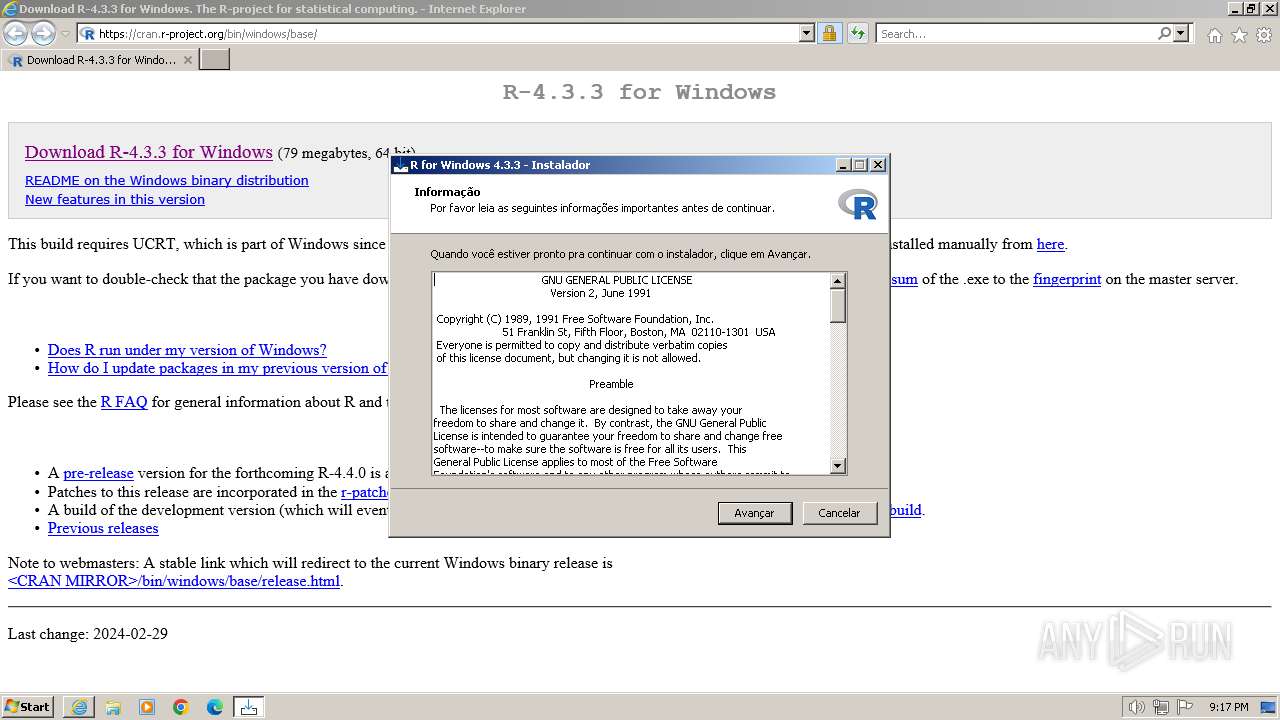
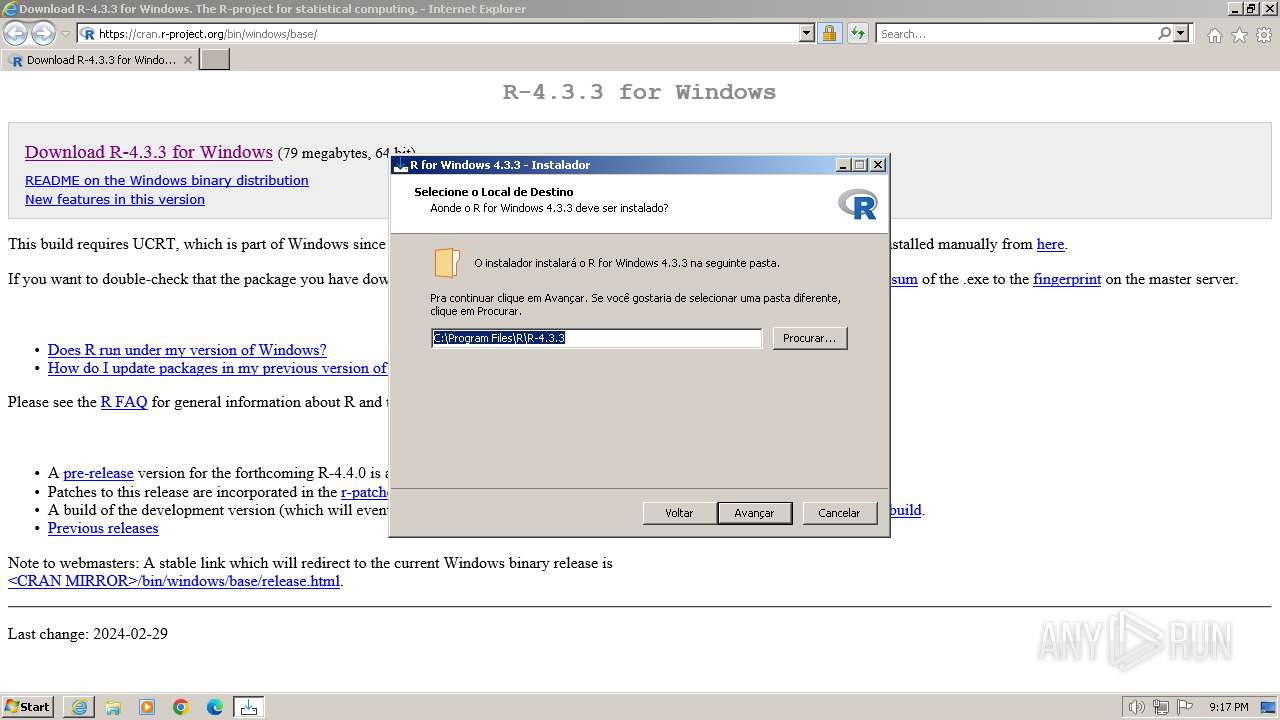
Drops the executable file immediately after the start
- R-4.3.3-win.exe (PID: 3324)
- R-4.3.3-win.exe (PID: 3992)
- R-4.3.3-win.tmp (PID: 3668)
SUSPICIOUS
Executable content was dropped or overwritten
- R-4.3.3-win.exe (PID: 3992)
- R-4.3.3-win.exe (PID: 3324)
- R-4.3.3-win.tmp (PID: 3668)
Reads the Windows owner or organization settings
- R-4.3.3-win.tmp (PID: 3668)
INFO
Checks supported languages
- R-4.3.3-win.exe (PID: 3324)
- R-4.3.3-win.exe (PID: 3992)
- R-4.3.3-win.tmp (PID: 1888)
- R-4.3.3-win.tmp (PID: 3668)
Create files in a temporary directory
- R-4.3.3-win.exe (PID: 3992)
- R-4.3.3-win.exe (PID: 3324)
Application launched itself
- iexplore.exe (PID: 1072)
Reads the computer name
- R-4.3.3-win.tmp (PID: 1888)
- R-4.3.3-win.tmp (PID: 3668)
The process uses the downloaded file
- iexplore.exe (PID: 1072)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2932)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1072)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2932)
Creates files in the program directory
- R-4.3.3-win.tmp (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cran.r-project.org/bin/windows/base/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1888 | "C:\Users\admin\AppData\Local\Temp\is-KRHB8.tmp\R-4.3.3-win.tmp" /SL5="$140190,81565144,831488,C:\Users\admin\Downloads\R-4.3.3-win.exe" | C:\Users\admin\AppData\Local\Temp\is-KRHB8.tmp\R-4.3.3-win.tmp | — | R-4.3.3-win.exe | |||||||||||
User: admin Company: R Core Team Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1072 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3324 | "C:\Users\admin\Downloads\R-4.3.3-win.exe" /SPAWNWND=$40204 /NOTIFYWND=$140190 | C:\Users\admin\Downloads\R-4.3.3-win.exe | R-4.3.3-win.tmp | ||||||||||||
User: admin Company: R Core Team Integrity Level: HIGH Description: R for Windows 4.3.3 Setup Version: 4.3.3.36002 Modules
| |||||||||||||||
| 3668 | "C:\Users\admin\AppData\Local\Temp\is-MMRBB.tmp\R-4.3.3-win.tmp" /SL5="$60238,81565144,831488,C:\Users\admin\Downloads\R-4.3.3-win.exe" /SPAWNWND=$40204 /NOTIFYWND=$140190 | C:\Users\admin\AppData\Local\Temp\is-MMRBB.tmp\R-4.3.3-win.tmp | R-4.3.3-win.exe | ||||||||||||
User: admin Company: R Core Team Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3992 | "C:\Users\admin\Downloads\R-4.3.3-win.exe" | C:\Users\admin\Downloads\R-4.3.3-win.exe | iexplore.exe | ||||||||||||
User: admin Company: R Core Team Integrity Level: MEDIUM Description: R for Windows 4.3.3 Setup Version: 4.3.3.36002 Modules
| |||||||||||||||
Total events
26 116
Read events
25 942
Write events
114
Delete events
60
Modification events
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 407906080 | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31102395 | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 707914830 | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31102395 | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
74
Suspicious files
1 268
Text files
1 643
Unknown types
185
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:F913A910843DA7DBF37F9E6C13A48350 | SHA256:4FF6347DD3D91A6A025146690A4056978963BD709BFF8486879D959114850DB2 | |||
| 1072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 1072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9291E9170D098DA0C555866918188C7B | SHA256:DB42FCC0F8321DB5C807EFD06E7D4A995747C09C01B477E513510740AECBBADC | |||
| 1072 | iexplore.exe | C:\Users\admin\Downloads\R-4.3.3-win.exe | — | |
MD5:— | SHA256:— | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\base[1].htm | html | |
MD5:08577CDE8465BD50F12B7360EEE0E42F | SHA256:1CE01A05F06931DF7ADD982AF800B725E97F80E45C64B447CDF2864AF5EBD5B8 | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:6625A3DB29BA509017744FD0A7357ABA | SHA256:D720EAB2BF828A5D34B18503F4F09078AD9BCB094900C3776C2AAF8654D16E67 | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DCF7BFD0377B820882107EB690D14403 | der | |
MD5:5BCA3132CBD584BCBC0A04AA57A8ECCF | SHA256:533D29166E334D1EBFFAA7965E22D2D1893E87E228CF8D7C9088C786B6DD69E5 | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:5DDF5A63CD3A20BDDA6B4064958D8292 | SHA256:63D920CE972C6133AB4C4E1B0F8DA7567A518F7E8B39E23B0FB51D1BE9016F6A | |||
| 2932 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DCF7BFD0377B820882107EB690D14403 | binary | |
MD5:38F028FC0BDE34C65ED6AB6EBAA831CB | SHA256:7522D912C8CE0EC1DE5D86F3FA01199FA31802DE55B36953C32FA194B21C3916 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
28
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2932 | iexplore.exe | GET | 304 | 184.24.77.193:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?378b9923119ef80e | unknown | — | — | unknown |
2932 | iexplore.exe | GET | 304 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e3969b55e300b10b | unknown | — | — | unknown |
2932 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC0KFjvdY%2B4qy%2BGAfIfUYk6 | unknown | — | — | unknown |
1072 | iexplore.exe | GET | 304 | 184.24.77.193:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b580a110354f7192 | unknown | — | — | unknown |
2932 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | unknown |
2932 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | unknown |
1072 | iexplore.exe | GET | 304 | 184.24.77.193:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?abc3609693924bbb | unknown | — | — | unknown |
1072 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1072 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 184.24.77.174:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0fcae8208d8731d8 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2932 | iexplore.exe | 137.208.57.37:443 | cran.r-project.org | WU (Wirtschaftsuniversitaet Wien) - Vienna University of Economics and Business | AT | unknown |
2932 | iexplore.exe | 184.24.77.193:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2932 | iexplore.exe | 184.24.77.205:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2932 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
2932 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
1072 | iexplore.exe | 137.208.57.37:443 | cran.r-project.org | WU (Wirtschaftsuniversitaet Wien) - Vienna University of Economics and Business | AT | unknown |
1072 | iexplore.exe | 184.24.77.193:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cran.r-project.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |